
Using RFID Technology for Supporting Document
Management
Thierry Bodhuin, Rosa Preziosi and Maria Tortorella
RCOST - Research Centre on Software Technology
Department of Engineering, University of Sannio
Via Traiano, Palazzo ex-Poste – 82100, Benevento, Italy
Abstract. Integrating RFID and document management systems can provide a
better awareness regarding the state of the enterprise context and, then, bring
new benefits. The activity flow characterizing a business process depends on
the moving of a definite sequence of paper documents from a given organiza-
tion’s office to another one. If the document circulation is monitored and man-
aged by using RFID technology, additional data can be captured from the or-
ganization information system enriching the set of data produced by a tradi-
tional document management system. By extracting information from this data,
an organization can improve its knowledge regarding its activity flows. As a re-
sult, less time for performing a business process is spent, capability to planning
and make decision increases, evaluation errors decreases and economic advan-
tages are obtained. This paper describes an RFID design, addressing this thesis.
1 Introduction
Current business process automation systems are focused on the activities of a busi-
ness process rather than on the involved business entities, such as documents and
persons. These entities are not monitored and the impact on the information system of
the widespread mobility and traceability of the enterprise resources is not considered.
Information does not always exist regarding their causal relations, topographical
localization and movement in the surrounding space. Therefore, uncertainty exists
regarding business processes. Planning and decisions making capability reduces and
evaluation errors increase. Likewise, business process executors consume more time
for performing their tasks and customer satisfaction decreases. Document manage-
ment area is sensible to these drawbacks. Even if organizations have automated their
business processes and provided them a global visibility, they continue to use paper
documents often representing central business entities of the organization. A major
control on their causal relations and circulation improves the organization’s business.
Document management is emerging as an important IT issue for improving busi-
ness processes. It represents an integral part of business continuity planning area and
requires the integration and management of existing and new technologies in innova-
tive solutions. A transition from traditional documents to digital ones is taking place,
and standard ways for electronically managing documents are diffusing. XML or
Bodhuin T., Preziosi R. and Tortorella M. (2007).
Using RFID Technology for Supporting Document Management.
In Proceedings of the 1st International Workshop on RFID Technology - Concepts, Applications, Challenges, pages 14-24
DOI: 10.5220/0002433000140024
Copyright
c
SciTePress

PDF formats are examples. However, digitalization is not always suitable. Some
documents having legal value must be recorded, kept and inventoried in the paper
format, and cannot be completely replaced by digital documents. Technologies, such
as bar codes, can be used. It supports recording and inventorying tasks, but it is not
useful for documents tracking. Radio Frequency Identification (RFID) technology
permits to overcome this limitation. Multiple RFID tags can be read once and they
can be detected without passing each document on a scanner as for the bar code. In
addition, an RFID tag can keep useful information in its on-board memory and be
used for detecting and tracking the document.
The integration of RFID and document management systems brings the following
new benefits to the organizations: (a) enrichment of the organization knowledge with
information obtained from the tracking of RFID tagged documents; (b) enhancement
of the global visibility of an organization, as remote authorized users can monitor the
procedures involving RFID tagged documents; (c) new opportunities for RFID-based
services and administrative e-services. An automatic ubiquitous system integrating
the RFID technology has a certain intelligence level useful for supervising the activi-
ties carried out in the organization hosting it. It allows an authorized user to discover
problems in the expected status of its requests in a business process, as documents are
not anymore disconnected from the company information system. For instance, an
employee can search a document and ask information regarding it without moving
from his desk, even if the document has not been digitalized. Moreover, all the docu-
ments related to a specific topic or project can be quickly found. Periodic report can
be generated for indicating outdated documents to be localized and cancelled from
the company archives. Currently, RFID technology and document management are
not widely integrated. Indeed, many organizations still have doubts regarding the real
benefits and require evaluation, case studies with empirical evidence before adopting
the RFID technology. This paper investigates the challenges RFID introduces for the
document processing. In particular, this work aims at solving some malfunctions in
the public administrations and at supporting the interest of the National Center for
Computing in the Public Administration (CNIPA), in Italy, with reference to the
adoption of the RFID technology [3]. With this in mind, an approach using the RFID
technology for document management is proposed. In addition, a business case is
proposed .
In the following, Section 2 considers drawbacks, benefits of the RFID technology.
Section 3 introduces the business case, Section 4 describes the proposed RFID solu-
tion, Section 5 discusses its deployment. Conclusions are given in the last section.
2 Drawbacks and Benefits of RFID Technology
RFID technology supports a variety of application contexts. Its broad applicability
favored an increasing interest, and provided benefits but also worries. In the follow-
ing, an overview of the most common drawbacks and benefits is given.
15

Drawbacks
RFID affects applications, infrastructure, business processes and personnel. It is a
part of IT. It is not simply another application [18], not a single, simple piece of tech-
nology, but it requires millions of tags containing standardized and coded data, and
thousands of tags readers. The tags transmit relevant data to multiple software appli-
cations, including middleware, databases, legacy systems and new applications [15].
Malwares may also be transmitted and safe programming practices and techniques are
needed for fighting database and web based attacks [14, 16]. Reading the properties
of an RFID tag without authorization could violate users’ privacy. Therefore, the use
of antennas with high reception capability should be limited and/or blocker tags [12],
or expensive techniques of cryptography within tags, or tags with short range of ac-
tion for reducing their interception should be used. Implementing an RFID system is
complex and expensive, as it required the acquisition of new components. Then, its
adoption must be also motivated and a concrete business purpose and a market need
are necessary for justifying its use.
Benefits
The RFID technology increases the ability of an organization of acquiring and storing
in a database a vast array of data regarding the location and properties of any entities
physically tagged and wirelessly scanned. It allows the tagged entities to become
mobile, intelligent, communicating component of the organization’s information
infrastructure [10]. It realize the linkage between the physical world and the Informa-
tion Technology (IT) and enables organizations to automatically monitor, decide, and
take actions [2].
The Wal-Mart Stores were among the first practitioners to engage a real RFID ex-
perience. Their RFID system, implemented in January 2005, was applied to supply
chain management. Afterward, many other enterprises (e.g., HP, Sun, IBM, Win-
dows, Intel, …) applied RFID in supply chain management. By using the RFID tech-
nology, the Wal-Mart Stores obtained an interesting Return On Investment (ROI) in
terms of a decrease of the number of rejects of perishable goods and employees for
checking them. Wall-Mart is continuing to consider RFID initiatives and encourage
suppliers and partners to use this technology [17]. Ford Motor Co. uses the RFID for
improving the efficiency of its supply chain. Ford had also an important impact on
safety and security, as well as on product sales and inventory management [11].
Medical organizations are particularly interested in the impact of RFID usage for
safety reasons [4]. They use RFID for tracking medical instruments, patients and
hospital personnel. An hospital in Taiwan used RFID technology for a medical appli-
cation [18], highlighting that RFID is a part of the IT infrastructure and its value is
delivered only through its business applications.
The idea of a possible impact of the RFID technology on security, allowed NEC
Corp. to obtain a contract with a Japanese bank for an RFID-based document man-
agement system in 2004. Bank of Nagoya Ltd. introduced the system in April 2005.
Antennas attached to bookshelves and filing cabinets were used. They communicated
data from RFID tags embedded in documents to a software system offered real-time
document tracking. Moreover, it could be combined with the employees’ identifica-
tion systems. Bank of Nagoya is having evidence of RFID solution benefits in terms
of cost reduction coming from the reduction of personnel [13].
16

3 The Business Case
The design of the business case regarded the following actors: the personnel of the
selected organization working with sensitive documents, process analysts and experts
in Ubiquitous Computing (UbiComp) technologies and methodologies. The coopera-
tion among these actors allowed the determination of:
- short-term requirements, oriented to improve the staff’s performances;
- long-term expectations, coming from the RFID use.
Short-Term Requirements
The personnel working with sensitive documents evidenced some inefficiencies of
the current document management system, common to other organizations. Some of
them could be overcome by the existent automated document management systems
and use of electronic mails. Unfortunately, this is not enough, as:
- the accounting office is legally obliged to keep payment receipts, faxes, invoices
and other documents some years. So, valuable staff time is spent for identifying
them and eliminating them when the office is not obliged to keep them;
- staff’s private information (e.g., curriculum, contracts) is stored in folders. They are
often kept on shelves and guarantees for their secure access is required;
- legal offices often move their dossiers outside the organization and can lose them. In
addition, a mechanism for rapidly finding them is needed;
- some administrative procedures have to follow a given bureaucratic course. Some
written and signed orders have to cross various bureaus and managers, and a user
could need to know the state of the procedures before taking his/her decisions.
The adoption of a document management system integrating RFID, could help to
overcome these limitations, with the following requirements: reduction of labor time;
increase of guarantees for security access; increase of capability of quickly locating
documents; increase of project managers awareness and users’ satisfaction. The same
benefits cannot be obtained by adopting other technology like bar code, documents
digitalization or documental workflow. Bar code technology allows to identify docu-
ments but not to trace their movements. The identification of a document is achieved
by passing it on a scanner for reading its bar code and it cannot be remotely per-
formed. Likewise, a digitalized document may be remotely consulted only if the
document is indexed and an information retrieval system is used, but information are
not provided regarding its physical location. The digitalization technology cannot
provide information for monitoring a business process or obtaining quality measures
from its execution. Analogously, the adoption of documental workflow can help to
monitor a business process, but such system is static and is designed without pro-
activeness. It is not able to autonomously capture illegal state changes in the work-
flow execution.
Then, in the business case, the application of RFID passive tags on documents was
considered Antennas placed in strategic points generate the magnetic field activating
RFID tags. When a tag is activated, it sends information to or receives information
from a reader. Passive tags have memory on board and are univocally identifiable by
means of a factory defined Unique Identifier (UID). In particular, the RFID available
memory was used for storing the name of the organization managing the document,
email address and phone number of the office responsible for attaching the RFID tag
17

on the document. In this way, whoever, outside or inside the organization, finds a lost
tagged document, could contact its responsible accessing an RFID antenna for read-
ing the information written on the tag.
Long-terms RFID Expectations
A document can be linked to a variety of additional informative parameters such as:
document description; office to which the document is destined; office responsible for
its storage; beneficiary of the procedure; production date; expiration date; priority;
access authorization; tags’ UIDs referencing other documents; etc. This information
can be kept into a database and those related to a document can be identified by
means of the UID of its tag. The wealth of the database represent a key element of the
success of RFID technology in the document management area. The database could
allow obtaining the workflow history of the tagged documents. The information kept
in the database could be linked to business intelligence tools, and/or UbiComp system
for improving enterprise performances.
For starting
to fill an
authorized
request
Researcher
resource
request
For starting
a procedure to
proclaim a
purchase
competition
Purchase
competition
request
[else]
For
completing
purchase
competition
Supply order
[resource
cost > fixed
threshold]
[available
resource]
[else]
Cash slip
Storing
Storing
Storing
For
knowing who
uses the
resource
For
inventorying
the resource
[the purchase
is feasible]
[else]
For starting
a procedure
of purchase
For finishing
to fill an
authorized
request
Signed supply
order
For starting
a procedure
of purchase
Purchase order
Loan for use
request
For starting
a request of
loan for use
Signed pur chase
order
Signed purchase
order
Signed pur chase
order
For executing
a procedure
of supply
Signed
packing
slip
For starting
a procedure
of testing
Signed
notification
of testing
[else]
[test
OK
]
For starting
a procedure
of payment
Signed order to pay
Researcher
Director
Administration
Administrative
Secretary
Accounting
Office
Store
Legal
Office
Suppliers
12
5a
6a
6b
7
11
Storing
Storing
Storing
Invoice
Storing
13
5b
For starting
a procedure
of invoicing
Storing
Signed resource
request
Signed resource
request
For starting a
procedure to
refund bore
expenses
4
3
8a
8b
9
10
Storing
User Supervisor Executors
Inside Actors
Outside Actors
Signed
delivery order
Storing
Purchase
note
Storing
12
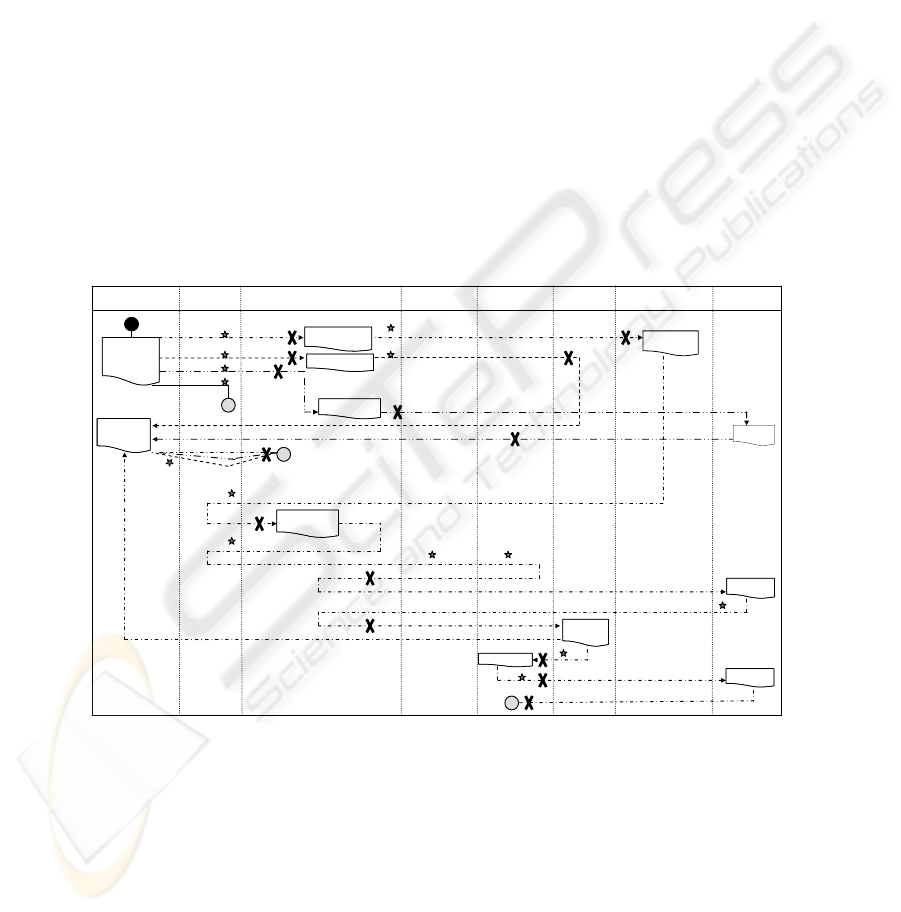
Fig. 1. Document diagram for the resource supply process.
4 The Pilot Experience
On the basis of interviews to the analyzed organization’s personal and the exam of
the existent Quality Manual conformed to the UNI EN ISO 9001:2000 standard the
pilot process was chosen. The process regarded the resource supply and, in particular,
Document
Alternative
Document
destination
Note
Linkage to
note
Start label
Stop label
Ball
18

the filling of the orders for purchasing the resources needed for the organization ac-
tivities. The documents produced during the selected business process are represented
in the document diagram shown in Fig. 1. The following subsections provide a
greater detail of the selected process, the designed RFID solution and the environ-
ment supporting it.
The Document Diagram
The document diagram in Fig. 1 highlights which documents open and close the
business process through an attached symbol start and stop, represented by ● and ●,
respectively. A ball in the diagram shown in Fig. 1 explains the function of the docu-
ment in input and defines the starting of the activity flow characterizing a given pro-
cedure inside a given business process. The documents shown between two balls are
the documents produced during the given procedure. The diagram in Fig. 1 does not
explicitly show the complete activity flow of a procedure but focuses on the circula-
tion of business entities and, specifically, the circulation of paper documents. It high-
lights how a document is related to other documents and when each document is
moved between the offices of an organization.
The vertical lane to whom or which office a given document is assigned. In addi-
tion, the lanes allows highlighting that the office producing a document is not always
responsible for its storage. Finally, the Suppliers lane is related to business process’s
procedures that are outside an organization as documents produced by suppliers, such
as packing slip and invoices, are related to the start of internal procedures.
The Resource Supply Process
The pilot business process involves three main actors: researchers; Director (supervi-
sor of the processes) and staff of the administration offices (executors of the proce-
dures characterizing the selected business process). Four mutually exclusive paths
characterize the process of filling a resource purchase order:
a) the resource is available (see Fig. 1, path 1 2 3 4 5a …) and the staff’s Store can
deliver immediately the required resource to the researcher;
b) the resource is not available and has a value lower then a fixed threshold (see Fig.
1, path 1 2 3 4 5b 6a …) and the Store staff starts a procedure for purchasing and
delivering the requested resource;
c) the resource is not available and has a value higher than a fixed threshold, its pur-
chase is feasible (see Fig. 1, path 1 2 3 4 5b 6b 7 8b …) and a request for starting a
procedure to proclaim a purchase competition to legal office is sent. The procedure
is activated from a supply order (see Fig. 1, path 1 2 3 4 5b 6b 7 8b 9 10) and not
simply from the purchase note (see Fig. 1, path 1 2 3);
d) the resource is not available and has a value higher then a fixed threshold, its pur-
chase is not feasible (see Fig. 1, path 1 2 3 4 5b 6b 7 8a…) and a label of stop is ap-
plied on the signed resource request.
In short, the resource supply process finishes when the researcher resource request
is rejected or when it is delivered. In particular, if the resource purchase has followed
the c) path the resource supply process finishes when the filled invoice is also stored
from the administration office.
19
The Designed Solution
The activities of each procedure in Fig.1 can start only when a given document is
produced from an office and/or signed from a person in charge. Thus, a sequential
order exists among these documents and a finite number of their chains is clearly
identifiable. In particular, four potential chains of documents are present because four
mutually exclusive paths exist for satisfying the researcher resource request.
A waste of time can happen in the procedure execution when, for instance, a
document remains in an incorrect or long stack of other documents. The produced
delay can be a unforeseen delay and result harmless, force the re-planning of the
organization activities and be source of economic damages. If a team leader has
planned research activities for when the required resources are delivered and the
resources do not arrive on time as the purchase order (see Fig. 1, path 1 2 3 4 5b 6b 7
8b 9 10 11 12 13…) is lost, forgotten or delayed in the chain of signa-
tures/authorizations: a) the team leader could be obliged to pay the researchers with-
out they work because the required resources are not available and/or (b) could even
lose the reserved funds because the purchase procedure has not been completed
within the time limit.
RFID technology introduces a major control on documents by analyzing the chains
of documents.
Purchase
competition request
[resource cost > fixed
threshold]
Cash slip
Packing slip
Notification
of testing
Order to pay
Researcher
Director
Administration
Administrative
Secretary
Accounting
Office
Store
Legal Office
Supplier
Invo ice
Loan for use
request
[not feasible
purchase]
[resource cost <
fixed threshold]
[available
resource]
Resource request
<<
>>
<<
>>
Supply order
Purchase order
<<
>>
<<
>>
Delivery order
<<
Purchase note
<<
<<
<<
<<
>>
<<
Fig. 2. Chains of potential tagged paper documents.
Fig. 2 shows the abstract of the document diagram shown in Fig. 1, depicted in
terms of document chains. In particular, a different oriented temporal line, labeled
with one or more of the following symbol, connects the documents of each chain: a
signature mark “*” shows who signs a document; a storage mark “X” represents
20

where a document is stored; a creation mark “<<” indicates where a document is
produced.
By automating the monitoring and management of the document chains, it is pos-
sible to obtain information regarding a document, such as who possesses it, if it is
outside fixed boundaries, moved along a non-correct or unauthorized path or an inter-
ruption or delay happen along the path. By means of this information who manages,
carries out and uses a business process can improve its knowledge regarding the ac-
tivity flows that circulate within the organization and gain the advantages cited above.
In conclusion, an engine supporting the short-term requirements and addressing
long-terms expectations from RFID use has been designed for:
a) communicating with the readers of the antennas attached to the desks and in some
strategic points for knowing if within a business process for each tagged document
exists another tagged document referring it. When this condition is violated, the ac-
tivities of the business process could be interrupted, an alert event can be launched
and a timer activated. When a fixed interval of time is spent and the engine does not
find a tagged document referring the tagged document in examination, an alarm can
be launched to the office to which the last one is destined. In this way, the personal
of this office can be pressed for resolving the cause of procedure interruption;
b) controlling that all the used RFID tags are within the reading range of an available
antenna. When an RFID tag is registered but it is not within the range of any anten-
nas, an alert event can be launched and a timer activated. If the condition is again
violated after a fixed interval of time and the related business process is open, an
alarm can be launched to the receiver of the examined tagged document, or to the
office responsible for its storage, if the related business process is closed. In this
way the accidental lost of documents can be avoided;
c) being on the alert that used RFID tags are not illegally destroyed. In this case, the
designed engine can just send an alarm when it is not anymore able to monitor the
related tagged document. Currently, there is still no strong guaranty that a RFID tag
attached to document papers is not illegally removed from the document itself.
Some work are done in the direction of being able to embed RFID tag directly in-
side the paper, like reducing the RFID tag size [7]
d) controlling if there are tagged documents with an urgent priority. When this condi-
tion is verified, a message is sent to the receiver of the tagged document, so that the
procedure managing the document is more quickly executed;
e) communicating with the readers of the antennas attached to bookshelves and draw-
ers for knowing if they store tagged documents that are expired and can be elimi-
nated. Each time this condition is verified, message can be sent to the responsible
for managing and inventorying the document, till when the tag is removed from the
expired document and all the documents that it refers, and an expiration label is
written in the database with reference to the UID of each disarmed tag;
f) communicating with the readers of the antennas attached near the entry/exit to/from
the considered organization and its offices for knowing if tagged documents are
brought outside them or authorized boundaries. Each time that the designed engine
verifies this condition, an alarm sending a vocal message can be launched, the lu-
minosity of the area of entry/exit is lighted and a camera near the alarm point is
turned on for filming who moves the document in an unauthorized area. This func-
tionality can be realized only if a mechanism of topographical localization has been
21

designed. Topographical localization provides logistic information with reference
to fixed geographical coordinates.
The Adopted UbiComp Platform
For addressing the short-term requirements and the long-terms expectations discussed
above, the engine to be implemented will be integrated as a service, named RFID
Document Management (RDM) service, into an already existing extensible and ubiq-
uitous platform [8, 9]. The services provided from this platform (a) has been con-
cretely implemented; (b) are accessible from multiple types of user interfaces (e.g.
Java/Java Web Start Application, Web browser, Jini browser); and (c) are used within
a simulated real environment.
This platform was written in Java and designed as a general UbiComp common
execution environment so that it is clearly reusable in different projects and for re-
designing business processes using RFID technology. In particular, three services
useful for the RDM service are included: INTELLICENCE, RFID and
LOCALIZATION. The INTELLIGENCE service allows the automatic creation of
rules by using a learning system developed on the top of the WEKA tool [6]. These
rules describe the relations between events and actions and are executed by the Jess
rule engine [5]. RFID service works with active or passive RFID tags and
LOCALIZATION service was implemented for locating people and objects.
5 The Deployment
The RFID technology can be introduced into the considered organization during
deployment phase. However, technological support is needed for integrating it into
business processes, as the technology is still not plug and play in existing applica-
tions.
The RDM service is designed for addressing this need and acting transversally to
existent enterprise solutions with the aim of avoiding the modification of existing
applications or architecture. In particular, the RDM service allows monitoring and
managing the activated chains of documents for each defined business process using
the required equipment for organization’s offices and documents. The UbiComp
experts defined the requirements: installation of the UbiComp environment on a PC
connected to a network and connection of the RDM service to the database; attach-
ment of passive RFID tags on the documents produced during the business process
depicted on the considered diagram; antennas and readers installation in each office
which is shown with a storage mark and in each entry/exit point to/from offices. Us-
ing the RFID service provided by the adopted UbiComp platform, the RDM service
has the potentiality of showing a real time view of the state of the activated chain of
RFID tagged documents for each business process allowing a lower level of errors,
improving planning capability and taking more careful decisions.
22

6 Conclusions
This paper presented an RFID investigation for supporting RFID document manage-
ment. It permitted to: (a) further confirm that formalizing business processes im-
proves their comprehension; (b) verify the real extensibility of an existing UbiComp
environment, and (c) obtain a further abstraction level of a business process with
reference to the document management. The abstraction at document level aims at
increasing the awareness on the state of a business process.
A clear understanding of individual business requirements and the presupposition
of a quantifiable ROI are necessary conditions for winning the main difficulty of
RFID technology and make convenient the implementation of a RFID system [1].
These conditions become also sufficient when RFID solution is justified from a busi-
ness case. In particular, this idea is widely shared from many experts. Deloitte devel-
oped the methodology RFID evaluator, oriented to evaluate the feasibility of imple-
menting a RFID project, in collaboration with Sun. While, IBM underlined that most
companies are adopting some hybrid of two approaches to the RFID use [2]:
- top down approach that starts with the project of a business case, and passes
through the preparation and execution of a pilot, since the deployment;
- learning by doing approach that starts with proofs or building of a simple trial,
passing through a pilot or business case for deciding if advancing with the deploy-
ment.
This paper presented a business case by following the first approach. The top
down RFID design in support of document management required the analysis of two
roles: process analysts and experts in UbiComp technologies and methodologies. The
process analysts had to depict the document diagrams for the selected business proc-
ess by interviewing the organization staff and consulting the existent Quality Manual.
The UbiComp experts have to obtain an abstract view of the depicted document dia-
grams and introduce an RDM service or customize an existing one. The integration of
an RDM service in an UbiComp environment was analyzed and the steps to be exe-
cuted during its deployment were defined by using the product abstract diagrams.
Future directions will regard improving the implementation aspects of the de-
signed RDM service. In addition, its experimentation in various real contexts will be
executed for obtaining an evaluation of its performances and the ROI improvement
with the introduction of RFID in an organization.
References
1. Guide to Understanding and Evaluating RFID: An Application White Paper. Ryzex Group
(September 2005). www.ryzex.com/pdf/RFID_Whitepaper.pdf.
2. IBM RFID solutions - RFID and the Electronic Product Code Perspectives on a Business
Driven Roadmap. CCGD & FCPMC RFID Conference (June 2004). www.fcpmc.com/
Member/resources/events/presentations/IBM.pdf.
3. CNIPA-RFID, Osservatorio RFID (2006). www.cnipa.gov.it/site/it-IT/Attivit%c3%a0/
Tecnologie_innovative_per_la_PA/RFID/Osservatorio_Rfid.
4. RFID in the hospital. RFID Gazette (July 2004). http://www.rfidgazette.org/
2004/07/rfid_in_the_hos.html.
23

5. Sandia National Laboratories: Java Expert System Shell. http://herzberg.ca.sandia.gov/jess.
6. Waikato Environment for Knowledge Analysis Project, www.cs.waikato.ac.nz/~ml.
7. Hitachi develops RFID powder, www.pinktentacle.com/2007/02/hitachi-develops-rfid-
powder.
8. Bodhuin, T., Canfora, G., Preziosi, R., and Tortorella, M. An Extensible Ubiquitous Archi-
tecture for Networked Devices in Smart Living Environments. In Proceedings of Embed-
ded and Ubiquitous Computing, International Conference (Nagasaki, Japan, December 6-9,
2005). EUC ‘05, LNCS 3823, Springer-Verlag (2005) 21-30.
9. Bodhuin, T., Canfora, G., Preziosi, R., and Tortorella, M. Hiding complexity and heteroge-
neity of the physical world in smart living environments. In Proceedings of the 2006 ACM
Symposium on Applied Computing (Dijon, France, April 23 - 27, 2006). SAC '06. ACM
Press, New York, NY (2006) 1921-1927.
10. Curtin, J., Kauffman, R. J., Riggins, F. J. Making the most out of RFID technology: A
research agenda for the study of the adoption, usage and impact of RFID. Minneapolis, 11.
Carlson School of Management, University of Minnesota (October 30 2005).
www.misrc.umn.edu/workingpapers/fullpapers/2005/0522_103005.pdf.
11. Hamblen, M., RFID successes highlighted at Mobile&Wireless World. Computerworld
(May 2006), www.computerworld.com/action/article.do?command=viewArticleBasic& arti-
cleId =9000767.
12. Juels, A., Rivest, R. L., and Szydlo, M. The blocker tag: selective blocking of RFID tags
for consumer privacy. In Proceedings of the 10th ACM Conference on Computer and
Communications Security (Washington D.C., USA, October 27 - 30, 2003). CCS '03. ACM
Press, New York, NY (2003) 103-111.
13. Kallender, P., Japanese bank taps RFID for document security. InfoWorld (August 18,
2004). http://www.infoworld.com/article/04/08/18/HNjapanrfid_1.html [April 15 2007].
14. Kirk, J., RFID tags vulnerable to viruses, study says Attacks could soon come in the form
of a SQL injection or a buffer overflow attack. Computerworld (March 2006).
www.computerworld.com/mobiletopics/mobile/story/0,10801,109560,00.html.
15. Quaadgras, A. 2005. Who Joins the Platform? The Case of the RFID Business Ecosystem.
In Proceedings of the Proceedings of the 38th Annual Hawaii international Conference on
System Sciences (Hicss'05) - Track 8 - Volume 08 (January 03 - 06, 2005). HICSS. IEEE
Computer Society, Washington, DC (2005) 269.2.
16. Rieback, M. R., Crispo, B., and Tanenbaum, A. S. 2006. Is Your Cat Infected with a Com-
puter Virus?. In Proceedings of the Fourth Annual IEEE international Conference on Per-
vasive Computing and Communications (Pisa, Italy March 13 - 17, 2006). Percom'06.
IEEE Computer Society (2006).
17. Songini, M., Wal-Mart details its RFID journey. Computerworld (March 2006).
www.computerworld.com/industrytopics/retail/story/0,10801,109132,00.html?from=story_kc
18. Wang, S., Chen, W., Ong, C., Liu, L., and Chuang, Y. RFID Application in Hospitals: A
Case Study on a Demonstration RFID Project in a Taiwan Hospital. In Proceedings of the
39th Annual Hawaii international Conference on System Sciences - Volume 08 (January 04
- 07, 2006). HICSS. IEEE Computer Society, Washington, DC (2006).
24
