
High Performance and Privacy for Distributed Energy Management:
Introducing PrivADE
+
and PPPM
Daniel Brettschneider, Daniel Hölker and Ralf Tönjes
University of Applied Sciences Osnabrück, Osnabrück, Germany
Keywords:
Distributed Energy Management, Smart Grid, Privacy, Communication Performance, Robustness.
Abstract:
Distributed Energy Management (DEM) will play a vital role in future smart grids. An important and of-
ten overlooked factor in this concept is privacy. This paper presents two privacy-preserving DEM algorithms
called PrivADE
+
and PPPM. PrivADE
+
uses a round-based energy management procedure for switchable and
dynamically adaptable loads. PPPM utilises on the market-based PowerMatcher approach. Both algorithms
apply homomorphic encryption to privately gather aggregated data and exchange commands. Simulations
show that PrivADE
+
and PPPM achieve good energy management quality with low communication require-
ments and without negative influences on robustness.
1 INTRODUCTION
Future concepts envision the smart power grid as a
distributed system of manifold stakeholders. Integrat-
ing communication technology into the former static
power grid provides interconnectivity. In such a sce-
nario, the smart grid can be understood as an Internet
of Energy, where many varying devices and partic-
ipants distribute and communicate their capabilities
and resources. Understanding and implementing the
smart grid as such a distributed system or Internet
of Energy will lead to Distributed Energy Manage-
ment (DEM), which will enhance and stabilise energy
consumption and generation for an increasing share of
renewable energy sources.
Often overlooked factors in DEM are communi-
cation performance and privacy. Despite performing
high-quality energy management, a DEM algorithm
might require a high data rate or extensive data vol-
ume. Thus, in DEM an additional key performance
is the distributed systems aspect. Many participants
work together to reach a high-quality energy manage-
ment and rely on fast convergence times, minimum
latencies, low computational requirements, as well as
robustness.
Furthermore, privacy will play a vital role in fu-
ture DEM systems. A DEM algorithm relies on ex-
tensive information flows, which might even be avail-
able to all participants in the system. Thus, everyone
is capable of tracking consumption profiles or device
states of others in detail. Preserving privacy resem-
bles another key performance indicator.
In summary, the key performance indicators are
energy management quality, communication perfor-
mance, computation performance, robustness and pri-
vacy.
The remainder of the paper is structured as fol-
lows: section 2 shows the related work. Section 3
presents the main objectives of the paper. A detailed
description of PrivADE
+
is given in section 4. Sec-
tion 5 shows PowerMatcher and describes a new pri-
vacy preserving approach for this algorithm. Both al-
gorithms will be evaluated in section 6. Finally, sec-
tion 7 concludes the paper.
2 RELATED WORK
Energy management in smart grids resembles a well-
investigated topic. However, most of them focus on
energy management. This section highlights a few
examples regarding the stated performance indicators.
Hinrichs et al. present COHDA (Hinrichs et al.,
2013), a heuristic for distributed agents. These agents
exchange consumption profiles to perform day-ahead
load scheduling. The consumption profiles find their
way to all participants through a small world topology
and the agents adapt their loads accordingly while dis-
tributing adapted profiles. The heuristic leads to equi-
librium state. The communication aspects are only
described roughly and the massive information ex-
182
Brettschneider, D., Hölker, D. and Tönjes, R.
High Performance and Privacy for Distributed Energy Management: Introducing PrivADE+ and PPPM.
DOI: 10.5220/0006693701820189
In Proceedings of the 7th International Conference on Smar t Cities and Green ICT Systems (SMARTGREENS 2018), pages 182-189
ISBN: 978-989-758-292-9
Copyright
c
2019 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

change impacts privacy.
Kok et al. describe PowerMatcher (Kok et al.,
2005), a multi-agent system for market-based supply
demand matching. Device agents generate bids (en-
ergy price / planned consumption) which are gathered
by an auctioneer agents, who determines the equilib-
rium energy price. The authors evaluate communica-
tion aspects, but do not show simulations with specific
technologies. Furthermore, privacy is not analysed in
the publication.
In (Brettschneider et al., 2017) the authors of this
paper present PrivADE, a previous version of the al-
gorithm presented in this paper. Households are ar-
ranged in a ring overlay network and privately man-
age shiftable, switchable and adaptable devices based
on a round-based algorithm and homomorphic en-
cryption. However, the ring overlay network is prone
to latency and robustness issues.
Mohsenian-Rad et al. introduce a DEM algorithm
based on game theory in (Mohsenian-Rad et al.,
2010). At random times a player optimises its own
consumption schedule based on all available informa-
tion and broadcasts an improved result to all other
players. The authors evaluate the algorithm using a
Local Area Network. However, a smart grid typically
resembles a Wide Area Network.
3 OBJECTIVES
In conclusion, most papers regarding DEM miss out
on one or more key performance indicators. Thus, this
paper introduces PrivADE
+
, a DEM algorithm which
specifically not only focusses on energy management
quality, but also communication performance, com-
putation performance, robustness and privacy. It is
compared and evaluated against the well-known Pow-
erMatcher (Kok et al., 2005). Furthermore, the pri-
vacy scheme of PrivADE
+
is also applied to Power-
Matcher.
4 PRIVADE
+
The Privacy-Preserving Algorithm for Distributed
Energy Management (PrivADE
+
) (Brettschneider,
2017) has been developed with the objective of pro-
tecting the privacy of its users without reducing en-
ergy management capabilities. Taking a look at the
loads in the smart grid, four main types can be iden-
tified: First, the base load, consisting of, for exam-
ple, lighting and stoves, cannot be influenced. Sec-
ond, activation times of shiftable loads, for exam-
ple, washing machines and driers, might be shifted
to a later time. Third, switchable loads, for exam-
ple, Heatpumps (HPs) and Micro Combined Heat and
Power Systems (µCHPs), might be switched on or off
entirely depending on their state. Fourth, adaptable
loads, for example, Battery Storages (BSs) and Elec-
tric Vehicles (EVs), offer dynamic adaptation of their
charge rates and might even feed into the power grid.
Thus, PrivADE
+
offers energy management for
shiftable, switchable, and adaptable loads while ad-
ditionally applying a privacy scheme, which are ex-
plained in the following sections.
4.1 Load Shifting
The algorithm for load shifting shifts the activation
of a device to a later point in time. Imagine a drier
being filled at 8 a.m. and turned on before going to
work. A deadline is defined at 5 p.m., so that it must
have finished its cycle after returning from work. The
algorithm computes the optimal activation times of all
devices with the stated constraints.
Taking a closer look, two problems arise. First,
finding an optimal schedule for several devices is a
NP-hard problem. Second, shifting an activation re-
quires knowledge of future behaviour. Thus, in a dis-
tributed approach participants have to exchange a lot
of information, for example a minute-based planned
consumption of the next 24 hours. To reduce the
complexity, a stochastic approach has been chosen,
which achieves similar energy management quality,
see (Brettschneider, 2017).
Initially, the expected future consumption e(t) is
distributed to all households h ∈ H. It can consist of,
for example, a standard load profile. If a household
h wants to shift a device d ∈ D, it defines an activa-
tion time t
a
, where the device is switched on, and a
deadline t
e
, where it must have finished its cycle. The
device runs for a duration t
d
with the load l(t, t
0
a
). A
load barrier b(t) represents the energy management
target. All possible activation times t
0
a
are stored in
the set
T
a
= {t
0
a
∈ N|t
a
≤ t
0
a
≤ t
e
−t
d
}. (1)
To determine the cost of an activation the function
c(t, t
0
a
)=
(
e(t)+l(t,t
0
a
), if e(t)+l(t, t
0
a
)≤b(t)
b(t)+ f ·(e(t) + l(t,t
0
a
)−b(t)), else,
(2)
is defined, where exceeding the barrier b(t) is pe-
nalised by a factor f . Activation times with a higher
cost than the one with the lowest cost
c
min
= argmin
t
0
a
t
e
−t
d
∑
t=t
a
c(t, t
0
a
) (3)
High Performance and Privacy for Distributed Energy Management: Introducing PrivADE+ and PPPM
183

gather data & shift
f!, ®, ¯, jAj, jBj, £g
❶
switch & adapt
f£
0
, ³, ±, ¢g
❷
adapt
f³, ±, ¢g
❸
repeat,
if necessary
▶ households
▷ state potential
▷ shift loads
▶ server
▷ calc. deviation from target
▷ determine switchables
▷ determine adaption share
▶ households
▷ adapt & state fulfillment
▶ server
▷ calc. remaining deviation
▷ determine adaption share
households ◀
switch loads ◁
adapt & state fulfillment ◁
server ◀
calc. remaining deviation ◁
determine adaption share ◁
Figure 1: Visualisation of the DEM algorithm.
multiplied with a factor f are excluded, resulting in
T
∗
a
= {t
0
a
∈ T
a
|
t
0
a
+t
d
∑
t=t
0
a
c(t, t
0
a
) ≤ f · c
min
}. (4)
Finally, an activation time is randomly chosen among
T
∗
a
. In conclusion, the device has been shifted to a
random optimal time-frame without any additional in-
teraction.
4.2 Load Switching and Adaptation
The algorithm for load switching and adaptation com-
bines two approaches in a distributed round-based
energy management procedure, see Figure 1 for an
overview. It can be applied to, for example, switch-
able HPs and µCHPs, as well as dynamically adapt-
able BSs and EVs. If, for example, the energy man-
agement target is superseded, the algorithm stimu-
lates either HPs to switch off or µCHPs to switch
on, or BSs and EVs to reduce their consumption. In
a first round necessary information is gathered and
used in the following rounds to fairly distribute the
required changes in energy consumption and genera-
tion to reach a stated goal.
Switchable devices are arranged in categories λ ∈
Λ, for example,
{
. . . , −750 W, −250 W,
250W, 750 W, 1250 W, . . .
}
.
(5)
Thus, every category has a specific range, for exam-
ple 750 W b= [500 W, 1000 W), and acts as a counter
for switchable devices within this consumption range.
In combination with priorities p ∈ P prioritised cat-
egories θ ∈ Θ can be formed, where Θ := P × Λ.
If a household owns a HP which would consume
900 watts when switched on, it increments the counter
in the 750 watts category.
An adaptable device d is classified using three val-
ues: It wants to consume ω
d
and has the ability to in-
crease its consumption by α
d
or to decrease it by β
d
.
For example, an EV wants to charge its battery using
2 kW, but might increase it by 1 kW or decrease it by
4 kW, thus possibly feeding into the power grid.
The DEM algorithm gathers the potential of
households h ∈ H, which are connected the system, in
the first round. Thus, a server s, which might also be
called energy manager, creates a tree overlay network
households as leaves, aggregators a as nodes and the
server s as the root node. By using aggregators, the al-
gorithm offers scalability and sets a first cornerstone
for privacy. At the beginning of the first round every
household h combines its potential in the data packet
{
ω
h
, α
h
, β
h
, |A|
h
, |B|
h
, Θ
h
}
, where |A| counts the num-
ber of households which can increase their consump-
tion and |B| households which can decrease their con-
sumption. The data packet is sent upwards the tree
overlay network to an aggregator, which aggregates
all received data packets by adding the counters and
forwards the resulting data packet to the next layer in
the tree. In the end the server receives the aggregated
switching and adaptation potential of all households.
After the first round the server determines whether
the energy management target µ is violated. First,
switchable loads are managed to keep the deviation
from µ in [µ − α, µ + β]. Thus, the remaining devia-
tion can be eliminated by adaptable loads afterwards
by increasing (α) or decreasing (β) their consump-
tion. By randomly activating positive or negative cat-
egories, depending on whether the consumption is be-
low or above µ, the server increases or decreases the
overall consumption ω until µ−α or µ + β is reached.
This results in categories
Θ
0
⊆ Θ, (6)
which have to be switched and an adapted overall
consumption ω
0
. In this way the computational com-
plexity is kept low, because finding the optimal solu-
tion is an NP-hard problem. The remaining deviation
ν = µ − ω
0
has to be reduced by the adaptable loads.
Thus, the server defines a load share
ζ =
(
ν
|A|
, if ν > 0
ν
|B|
, else,
(7)
for the adaptable households A or B. By broadcast-
ing Θ
0
and ζ to all households, they can perform the
required energy management.
Upon receiving the data packet, a household
switches its devices according to Θ
0
. Additionally,
it tries to fulfil the load share ζ by increasing or de-
creasing its consumption according to the max-min
fairness principle. If it can only partially fulfil the
share, the residual unfulfilled share δ
h
is gathered.
Otherwise, remaining adaptation potential is stated by
incrementing a counter ∆. All households send this
information to the server using the stated procedure.
Thus, after the second round, the remaining deviation
δ can be further reduced depending on ∆ in additional
SMARTGREENS 2018 - 7th International Conference on Smart Cities and Green ICT Systems
184

rounds. This process continues until the consump-
tion observes predefined limits or until no adaptable
households remain.
In summary, switchable loads are managed based
on categories and adaptable loads are managed fairly
using the max-min fairness principle in a distributed
round-based energy management algorithm.
4.3 Privacy
Considering privacy, PrivADE
+
already achieves a
basic level of privacy through aggregation. However,
aggregators or internal attackers gain access to private
data of distinct households, even if encrypted commu-
nication is a prerequisite.
Thus, PrivADE
+
utilises a Homomorphic En-
cryption System (HES) to secure privacy of all par-
ticipants. To measure the level of privacy, the k-
anonymity principle is used. Reaching k-anonymity
means, that the information of one household cannot
be distinguished from k − 1 others.
The HES applies the Paillier cryptosystem (Pail-
lier, 1999), which enables homomorphic addition.
Additive homomorphic encryption of two plaintexts
m
1
and m
2
using an encryption function E and a de-
cryption function D is defined as
D(E(m
1
) ⊕ E(m
2
)) = m
1
+ m
2
, (8)
where ⊕ denotes the corresponding operation on the
ciphertext. The Paillier cryptosystem is chosen be-
cause of its efficient encryption and decryption and
its low message expansion factor of two. (Fontaine
and Galand, 2007)
At the beginning of each round, a household en-
crypts the data packet with the public key of the
server. To reduce the number of required encryptions,
all counters are bit-shifted into a single a value before
encryption. However, the Paillier cryptosystem does
not allow for negative numbers, which is required by
ω. Thus, ω is split into a consumption value ω
+
and
a generation value ω
−
. This results in
ε
h
= ω
+
h
or
ω
−
h
32
or (α
h
64) or (A
h
96)
or (β
h
128) or (B
h
160)
or (θ
h,1
168) or . . .
or
θ
h,
|
Θ
|
(160 + 8 ·
|
Θ
|
)
,
(9)
when using 32 bits for consumption counters and
8 bits for switchable categories. Depending on Θ, ε
has to be split into blocks, because m ∈ Z
n
. In this
case the number of blocks is
l
6·32+8·
|
Θ
|
υ
m
, where υ
represents the bit-size of n in the Paillier cryptosys-
tem, e.g. 2048 bits. All households h ∈ H encrypt
0
500
1000
1500
2000
0 0.1 0.2 0.3 0.4 0.5
price / €
consumption / W
array rep. bid point rep.
Figure 2: Array and point bid for a heatpump.
ε
h
and forward it to an aggregator. The aggregators
receive the encrypted data packets and perform the
homomorphic aggregation, which is basically a mul-
tiplication of the ciphertexts. At the end of a round,
the server receives encrypted data packets and can de-
crypt them using its private key. Thus,
ε
s
= D
E(ε
0
) ·
∏
h∈H
E(ε
h
)
!
mod n
2
!
. (10)
Because the token is split into υ blocks, υ decryptions
have to be performed accordingly. Finally, the server
extracts all counters using the appropriate bit-shift op-
erations. Thus, it only gains access to aggregated in-
formation of all households.
In summary, households encrypt their data packets
using the Paillier cryptosystem, aggregators aggregate
the ciphertexts, and the server receives them at the end
and decrypts them. In this way households and aggre-
gators do not have access to any plaintext information
of other participants. Only the server is capable of de-
cryption and does only gain access to aggregated data.
Thus, privacy is preserved. When using a tree overlay
network with a single aggregator at the second layer,
k-anonymity equals the number of households |H|.
5 POWERMATCHER
PowerMatcher (Kok et al., 2005) has been chosen as
a comparative DEM algorithm, because of its well-
documented behaviour and place in the state of art. It
implements a multi agent approach for market-based
supply demand matching. Agents form a tree struc-
ture and the energy management process can be sum-
marised as follows: Device agents create bids for de-
vices, concentrator agents gather and aggregate these
bids, before transmitting them to an auctioneer. The
auctioneer determines an optimal energy price ac-
cording to the energy management target and pub-
lishes it.
A device agent represents one device, e.g. a HP
or EV, and follows a predefined strategy. The agent
High Performance and Privacy for Distributed Energy Management: Introducing PrivADE+ and PPPM
185
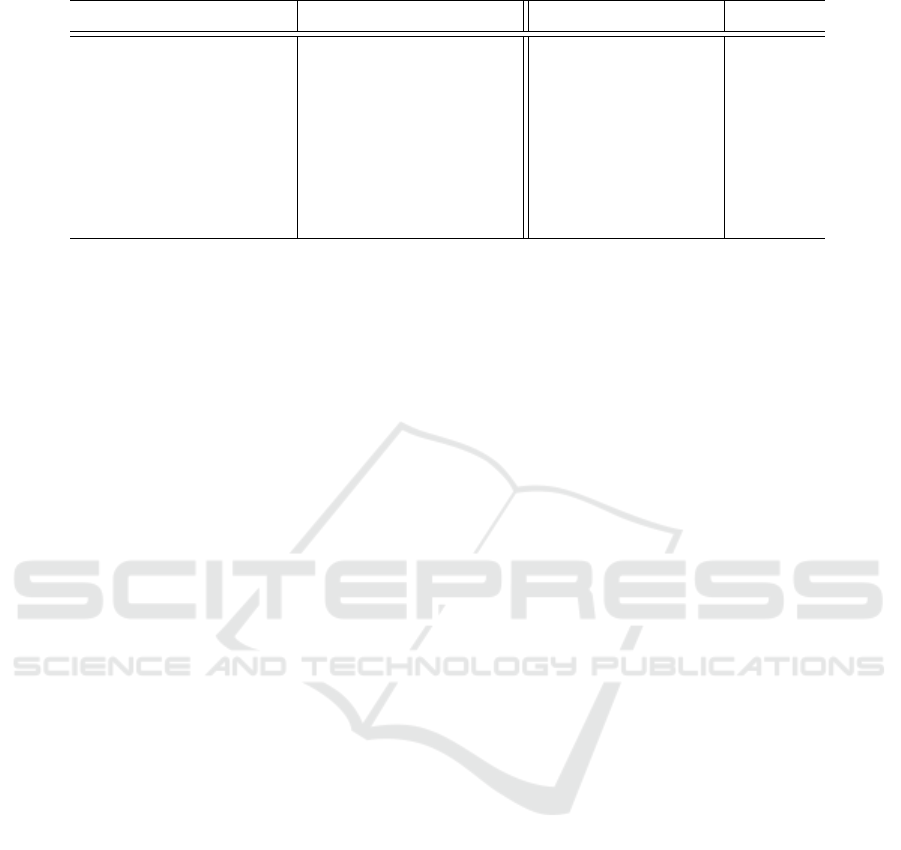
Table 1: Simulation Parameters.
Parameter Value Device Quantity
Households 1 to 100 Basic Devices all
DEM Function peak clipping Photovoltaic Systems 40 %
DEM Target 350 watts per household Heatpumps 20 %
Simulation Time 1/5/11 to 7/5/11 Electric Vehicles 20 %
Interval 5 minutes Battery Storages 20 %
Communication Network Internet-like topology
5 Mbps, 20 ms latency
creates a bid for the device depending on its current
state. Such a point-based bid consists of a validity
period t and a flexible list Φ
p
with pairs of energy
prices ϖ and consumption values ω.
φ
p
= {t, Φ
p
= {(ϖ, ω), . . . }} (11)
Figure 2 shows an exemplary point-based bid
of a Heatpump, which is represented as Φ
p
=
{(0.29e, 2 kW), (0.29 e, 0 kW)}. Finally, the agent
sends the bid upwards the tree overlay network to a
concentrator agent.
A concentrator agent manages a cluster of device
agents or other concentrators. Upon receiving new
bids, it aggregates them into a single bid and sends it
upwards the tree.
The root node of the tree overlay network is called
the auctioneer. This agent receives the aggregated
bids, which represent the wishes of all device agents.
Based on this knowledge, the auctioneer calculates
the equilibrium energy price. The default goal of the
agent is supply demand matching. Finally, the auc-
tioneer sends the new energy price downwards the
tree.
Upon receiving a new energy price, all device
agents adapt their behaviour accordingly.
5.1 Privacy-preserving PowerMatcher
As privacy plays a vital role, PowerMatcher shows
significant privacy issues. A concentrator agent re-
ceives bids of device agents and is thereby capable
of tracking these device in detail. Thus, privacy is
at risk. However, the Homomorphic Encryption Sys-
tem can also be applied to PowerMatcher, resulting
in the Privacy-Preserving PowerMatcher (PPPM). In
general, device agents encrypt their bids with the pub-
lic key of the auctioneer using homomorphic encryp-
tion. Concentrators homomorphically aggregate re-
ceived bids and send them to the auctioneer. Only the
auctioneer is capable of decrypting the aggregated bid
using its private key. Thus, PPPM reaches the same
privacy-level of PrivADE
+
.
However, the bid representation has to be adapted,
because dynamic point-based bids cannot be aggre-
gated in such a way. Thus, bids are discretised and
consists of a fixed-size list Φ
a
with consumption val-
ues ω. The number |Φ
a
| ∈ N
≥2
of consumption values
ω is called the resolution and is constant in the entire
system. At the beginning, a price list ϒ with the same
resolution (|ϒ| = |Φ
a
|) has to be defined. This way
each device agent can assign its consumption values
to a corresponding price. The array based representa-
tion of the exemplary bid is defined as
ϒ={0.0e, 0.1 e, 0.2 e, 0.3 e, 0.4e, 0.5 e}
Φ
a
={2kW, 2 kW, 2 kW, 0 kW, 0 kW, 0kW}.
(12)
5.2 Multi-stage PPPM
The energy management quality is related to the reso-
lution |Φ
a
|. A low resolution might impact the quality
result. In other words, a higher resolution might im-
prove the energy management quality. However, this
also results in larger bids and a higher data amount.
To reduce the data amount, while keeping the
same level of energy management quality, a multi-
stage approach of PPPM can be applied. During the
first stage the auctioneer gathers all bids with a small
bid resolution and calculates a price range where the
equilibrium price is located in. Afterwards, it initiates
a new round by sending the new price range to all
participants. Thus, the multi-stage approach continu-
ously increases the price resolution while decreasing
the price range. Therefore, the total amount of sub-
mitted data can be reduced. Using this method, a vir-
tual resolution of (|Φ
a
| − 1)
ρ
+ 1 can be reached by
performing ρ stages. Thus, an initial bid resolution of
100, results in a virtual resolution of 9802, when two
stages are executed.
SMARTGREENS 2018 - 7th International Conference on Smart Cities and Green ICT Systems
186
-1500
-1000
-500
0
500
0 2 4 6 8 10 12 14 16 18 20 22 0 2 4 6 8 10 12 14 16 18 20 22
time of day / h
average consumption / W
total base switchable adaptable pv
Figure 3: Exemplary consumption curve (PrivADE
+
, day 2).
6 EVALUATION
In this section all presented DEM algorithm are evalu-
ated against the remaining key performance indicators
energy management quality, communication perfor-
mance and robustness. All simulations are executed
with SiENA, which offers a realistic data basis for the
smart grid, as well as communication, heat, and power
network simulations. (Brettschneider et al., 2016)
6.1 Scenario
The scenario represents an urban street with up to 100
households. The households own basic appliances,
as well as Photovoltaic Systems (PVs), BSs, EVs,
and HPs as shown in Table 1. The energy manage-
ment algorithms perform peak clipping with a target
of 350 watts per household. The participants of the al-
gorithms are connected to each other using an internet
topology. Please note, that this serves as an example
to show the capabilities of the algorithms. Further-
more, load shifting is not performed.
Figure 3 exemplarily shows the consumption of
the second day with PrivADE
+
. The base load (red)
cannot be influenced. PV systems (orange) offer
power during the day. HPs (purple) are switched on
when excess power is available. EVs return after work
and require charging. Thus, the DEM target would be
violated during the evening and PrivADE
+
reduces
the charging rate, when possible, and stimulates BSs
to provide the remaining deficit. As a result, the over-
all consumption does not exceed the DEM target dur-
ing the whole day.
The following sections evaluate the single-stage
PPPM with a resolution of 100 and 1000, the two-
stage PPPM with a resolution of 100 per stage, Pow-
erMatcher, and PrivADE
+
.
1
2
3
4
1 10 100
households
power / kW
PPPM-100 PPPM-1000
PPPM-100
2
PowerMatcher PrivADE⁺
Figure 4: Comparison of average maximum power per
household for all algorithms.
20
40
60
1 10 100
households
quality / %
PPPM-100 PPPM-1000
PPPM-100
2
PowerMatcher PrivADE⁺
Figure 5: Comparison of average peak clipping quality for
all algorithms.
6.2 Energy Management Quality
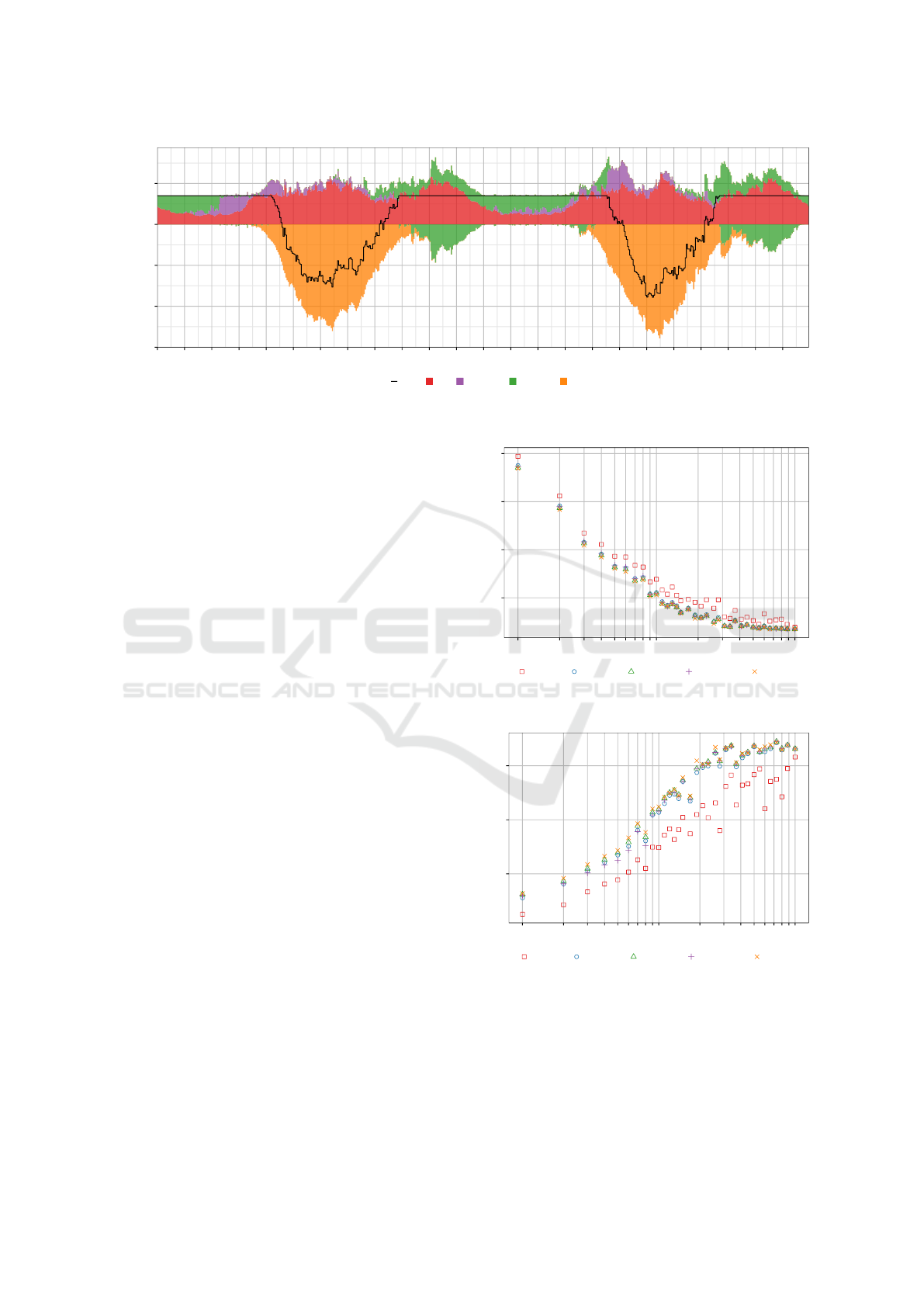
Regarding energy management quality, Figure 4
shows the average maximum power per household.
All DEM algorithms are configured to perform peak
clipping. They achieve similar results in all simu-
High Performance and Privacy for Distributed Energy Management: Introducing PrivADE+ and PPPM
187
0.1
1.0
1 10 100
households
average convergence time / s
PPPM-100 PPPM-1000
PPPM-100
2
PowerMatcher PrivADE⁺
Figure 6: Scaling comparison of convergence time per in-
terval for all algorithms.
lated scenarios, ranging from 1 to 100 households.
Only the PPPM algorithm with a resolution of 100
does not reduce the peaks as good as the other al-
gorithms. Increasing the resolution to 1000 or 9802
suffices to increase the peak clipping effectiveness to
a same level as PowerMatcher. In this scenario, the
DEM algorithms are capable of reducing all peaks to
the 350 watts target when more than 80 households
participate at the energy management.
To measure the peak clipping quality a metric is
used, as defined in (Hölker et al., 2016). The met-
ric measures the reduction of the consumption peaks
related to a reference simulation without energy man-
agement. It ranges from −1 (worst) to 1 (best), where
0 indicates no change. Figure 5 shows that all algo-
rithms can decrease the peak power significantly.
In conclusion, PowerMatcher and PrivADE
+
achieve the same level of energy management qual-
ity. PPPM also performs well, when configured with
a suitable bid resolution.
6.3 Communication Performance
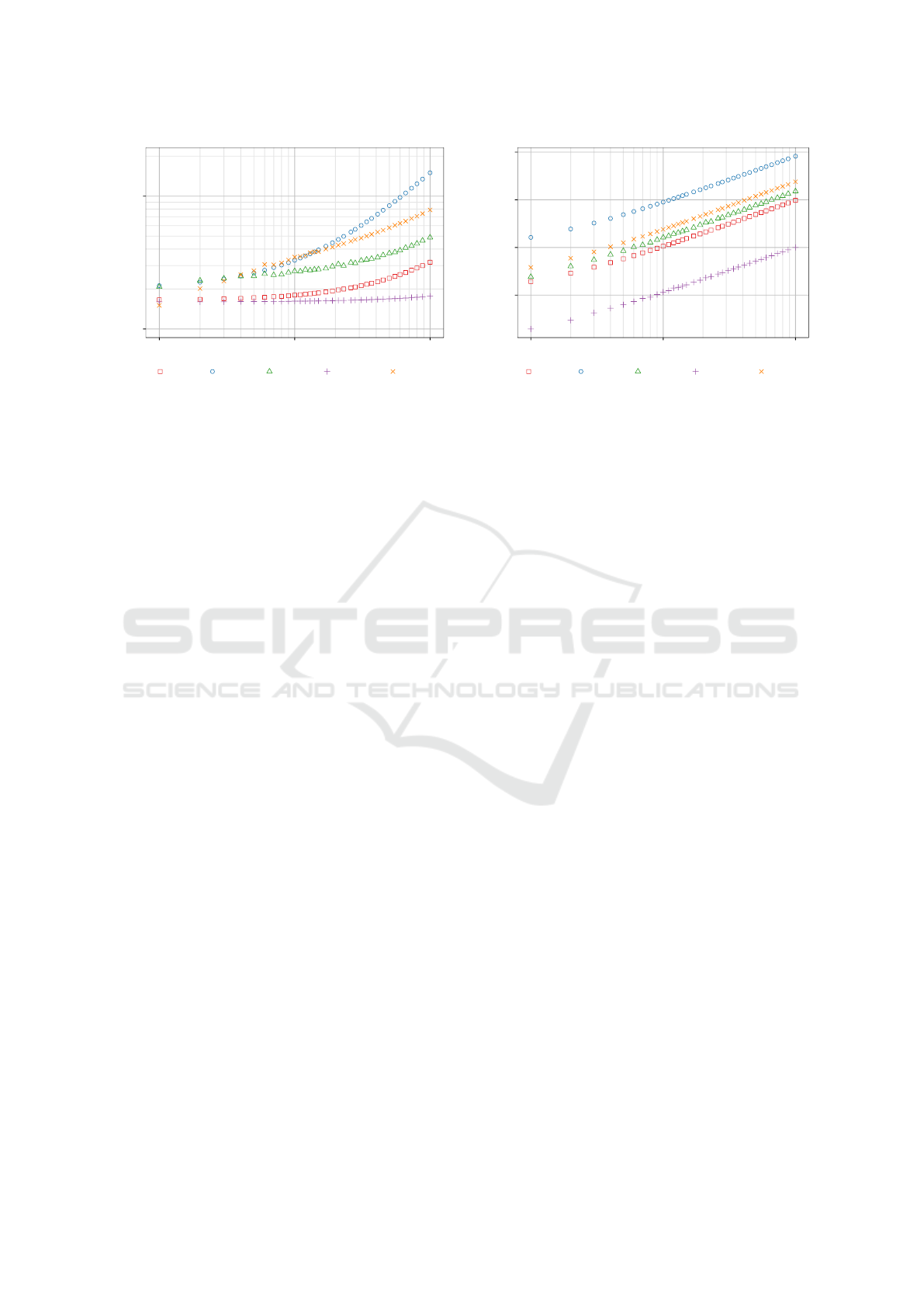
Regarding the communication performance, the sim-
ulation results show more differences. Figure 6 shows
the average convergence time per energy manage-
ment interval and Figure 7 the corresponding data
volume. PowerMatcher achieves the best results, be-
cause of its low bid size and the static energy man-
agement steps. The average convergence time is be-
low 200 ms for 100 households and the data volume
at 10 kB. PrivADE
+
requires more time and data vol-
ume for convergence because of its round-based pro-
cedure and larger message sizes. However, the con-
vergence time still does not reach one second and the
data volume stays well below one MB. The single-
stage PPPM with reasonable resolutions need higher
convergence times because of its larger messages.
However, when a high bid resolution is required, the
1k
10k
100k
1M
1 10 100
households
average data volume / byte per interval
PPPM-100 PPPM-1000
PPPM-100
2
PowerMatcher PrivADE⁺
Figure 7: Scaling comparison of data volume per interval
for all algorithms.
two-stage PPPM can perform better. With a reso-
lution of 100, it reaches a 500 ms convergence time
for 100 households and a data volume comparable to
PrivADE
+
.
In conclusion, PowerMatcher achieves the best re-
sults regarding communication performance. How-
ever, PrivADE
+
and the multi-stage PPPM also
achieve good results with convergence times well be-
low one second and a corresponding data volume be-
low one MB. Thus, all algorithms can be deployed
when using Internet-based communication technolo-
gies like in this scenario.
6.4 Robustness
PrivADE
+
and PowerMatcher both use a star over-
lay network, where each household is connected to
a central unit. If a communication connection is in-
terrupted and a household cannot transmit its infor-
mation to a concentrator/aggregator or cannot receive
any commands, both algorithms have to make as-
sumptions about its energy consumption. However,
existing standard load profiles and historic data coun-
teract this lack of knowledge. Thus, the overall energy
management quality is only slightly influenced. To
reduce the impact on the convergence time a deadline
can be defined, after which a household is considered
offline. Thus, a concentrator/aggregator only has to
wait until it receives data from all households or until
the deadline is reached.
In conclusion, all algorithms achieve robustness
from a communicational and quality point of view
and the privacy mechanisms do not reduce the robust-
ness. Robustness issues regarding false data injection
can be counteracted using additional signage proto-
cols. However, this impacts privacy and therefore has
been disregarded in this paper.
SMARTGREENS 2018 - 7th International Conference on Smart Cities and Green ICT Systems
188

7 CONCLUSIONS
This paper introduced PrivADE
+
and the Privacy-
Preserving PowerMatcher (PPPM). Both DEM algo-
rithms focus on preserving the privacy of all partici-
pants without reducing the energy management capa-
bilities. They use a homomorphic encryption scheme
to perform private and secure data aggregation. The
PPPM extends the PowerMatcher algorithm where
households aggregate bids (price/consumption) and
where an auctioneer determines the best energy price.
PrivADE
+
combines the homomorphic data aggrega-
tion with a round-based scheduling for switchable and
adaptable loads. Both algorithms preserve the privacy
of all participants by only publishing encrypted and
aggregated information.
Regarding energy management quality PrivADE
+
achieves slightly better results. Considering commu-
nication performance, the multi-stage PPPM offers
faster convergence times.
In conclusion, the presented DEM algorithm
PrivADE
+
and PPPM achieve the goal of preserv-
ing the privacy of its participants without reducing en-
ergy management quality and communication perfor-
mance. Thus, both algorithms fulfil all requirements
for deployment.
REFERENCES
Brettschneider, D. (2017). Preserving Privacy in Dis-
tributed Energy Management. Shaker Verlag, Aachen.
Brettschneider, D., Hölker, D., Scheerhorn, A., and Tönjes,
R. (2017). Preserving privacy in Distributed Energy
Management. Computer Science - Research and De-
velopment, 32(1):159–171.
Brettschneider, D., Hölker, D., and Tönjes, R. (2016).
SiENA: Simulator for Energy Network Applications
combining Power, Heat and Communication. In Pro-
ceedings of VDE Kongress 2016. VDE.
Fontaine, C. and Galand, F. (2007). A Survey of Homomor-
phic Encryption for Nonspecialists. EURASIP Journal
on Information Security, 2007:15:1–15:15.
Hinrichs, C., Lehnhoff, S., and Sonnenschein, M. (2013).
COHDA: A Combinatorial Optimization Heuristic for
Distributed Agents. In Filipe, J. and Fred, A., edi-
tors, Agents and Artificial Intelligence, number 449
in Communications in Computer and Information Sci-
ence, pages 23–39. Springer Berlin Heidelberg.
Hölker, D., Brettschneider, D., Fischer, M., Tönjes, R., and
Roer, P. (2016). Quality-functions for an uniform and
comparable analysis of demand side management al-
gorithms. Computer Science - Research and Develop-
ment, 31(1):57–64.
Kok, J. K., Warmer, C. J., and Kamphuis, I. G. (2005).
PowerMatcher: Multiagent Control in the Electric-
ity Infrastructure. In Proceedings of the Fourth In-
ternational Joint Conference on Autonomous Agents
and Multiagent Systems, AAMAS ’05, pages 75–82.
ACM.
Mohsenian-Rad, A.-H., Wong, V., Jatskevich, J., and
Schober, R. (2010). Optimal and autonomous
incentive-based energy consumption scheduling algo-
rithm for smart grid. In Innovative Smart Grid Tech-
nologies (ISGT), 2010, pages 1–6.
Paillier, P. (1999). Public-Key Cryptosystems Based on
Composite Degree Residuosity Classes. In Stern, J.,
editor, Advances in Cryptology — EUROCRYPT ’99,
number 1592 in Lecture Notes in Computer Science,
pages 223–238. Springer Berlin Heidelberg.
High Performance and Privacy for Distributed Energy Management: Introducing PrivADE+ and PPPM
189
