
APPLICABILITY OF MULTIPARTY COMPUTATION SCHEMES
FOR WIRELESS SENSOR NETWORKS
Position Paper
Manuel Koschuch, Matthias Hudler, Michael Kr¨uger
Competence Centre for IT-Security, FH Campus Wien, University of Applied Science, Favoritenstrasse 226, Vienna, Austria
Peter Lory
Institut f¨ur Wirtschaftsinformatik, Universit¨at Regensburg, Universit¨atsstrasse 31, Regensburg, Germany
J¨urgen Wenzl
TMMO GmbH, Vilsgasse 25, Kallm¨unz, Germany
Keywords:
Sensor networks, Threshold cryptography, Efficient implementation, Multiparty computations.
Abstract:
Wireless Sensor Networks pose special requirements to the deployed security algorithms, due to their unique
properties: a single sensor node has great restrictions in terms of computing power, available memory and
available energy. It is nevertheless desirable for the messages exchanged over the air interface to be secure
against eavesdropping and forging. Since a single sensor node can be captured and removed very easily and
almost undetectable, cryptographic schemes that do not rely on a single master secret present in every node,
like those based on, for example, multiparty computations, seem to be a promising alternative in this setting.
We are currently investigating the applicability of a modified implementation of the Gennaro-Rabin-Rabin
multiparty multiplication protocol for sensor networks, with a special focus on the number of messages that
have to be exchanged and the additional load put on every node by this protocol. This paper gives a short
overview of our work and lists some preliminary results.
1 INTRODUCTION
Wireless Sensor Networks can be used for a wide va-
riety of applications: from environmental monitoring
to energy plant surveillance, the huge number of inex-
pensive sensors, covering a wide area and communi-
cating measurements in a hop-to-hop fashion allows
many new approaches not suitable for common net-
work infrastructures. The main problem when design-
ing and deploying such networks lies in the security
requirements: messages are transmitted over the air
interface and are thus susceptible to eavesdropping,
modification or forging. To prevent such attacks, suit-
able cryptographic protocols and algorithms have to
be employed. The majority of currently deployed sen-
sor networks use symmetric cryptography, due to the
resource constraints of the individual nodes, to secure
the communication between the network elements,
although the suitability of asymmetric cryptography
utilizing elliptic curves for this environment is a big
current research topic.
When using symmetric cryptography, the problem
of key distribution arises: what mechanisms are em-
ployed to ensure that two adjacent nodes share a com-
mon key? Giving every node in the entire network
the same key has obvious security implications, since
capture and analysis of a single node (which is usually
easy to do and stays almost completely undetected,
given a large enough network) compromises the key
used in the entire network.
Another approach is the use of heuristic algo-
rithms, where every node is preloaded with a subset
of keys taken from one large keypool, hoping that
when trying to communicate with an adjacent node
both nodes find one common key in their respective
sets. Using this method, there is no single key for the
entire network, which an attacker could obtain from
capturing a single node, although he can still compro-
mise a certain subset of the network (see also (Merwe
et al., 2007) for an overview of different key manage-
125
Koschuch M., Hudler M., Krüger M., Lory P. and Wenzl J. (2010).
APPLICABILITY OF MULTIPARTY COMPUTATION SCHEMES FORWIRELESS SENSOR NETWORKS - Position Paper.
In Proceedings of the International Conference on Data Communication Networking and Optical Communication Systems, pages 125-128
DOI: 10.5220/0003032901250128
Copyright
c
SciTePress

ment techniques for wireless sensor networks).
In this setting, the use of some sort of threshold
cryptography seems promising: instead of relying on
the integrity of every single node, a certain number of
uncompromised nodes is required to produce a valid
result, and no single node knows the entire secret re-
quired to produce this result. The amount of nodes
that have to cooperate in order to create the secret is
equivalent to the number of nodes an attacker has to
successfully compromise before gaining access to the
communication in the network.
Our work now tries to quantify the applicability of
threshold cryptography for wireless sensor networks
in general, with a first focus on multiparty computa-
tions utilizing the Gennaro, Rabin and Rabin (Gen-
naro et al., 1998) protocol, with some numeric opti-
mizations. The remainder of this paper is structured
as follows: Section 2 gives a general introduction to
Multiparty computations and the Gennaro, Rabin and
Rabin protocol. Section 3 then sums up our current
experimental results, while finally Section 4 details
our next steps.
2 MULTIPARTY
COMPUTATIONS
Protocols for multiparty multiplication of two poly-
nomially shared values over Z
q
with a public prime
number q are important cryptographic primitives in
various application fields.
Polynomial sharing refers to the threshold scheme
originally proposed by Shamir (Shamir, 1979), which
assumes that n players share a secret α in a way that
each player P
i
(1 ≤ i ≤ n) owns the function value
f
α
(i) of a polynomial f
α
with degree at most t and
α = f
α
(0). Then any subset of t + 1 participants can
retrieve the secret α (for example by Lagrange’s in-
terpolation formula) but no subset of, at most, t par-
ticipants can do so.
At the beginning of the multiplication protocol
each player P
i
holds as input the function values f
α
(i)
and f
β
(i) of two polynomials f
α
and f
β
with maxi-
mum degree t and α = f
α
(0), β = f
β
(0). At the end
of the protocol each player owns the function value
H(i) of a polynomial H with maximum degree t as
his share of the product αβ = H(0).
Lory (Lory, 2007) and (Lory, 2009) has presented
protocols for this task. They accelerate the technique
of Gennaro, Rabin and Rabin (Gennaro et al., 1998),
which was known for its efficiency among its contem-
porary competitors (see e.g. Cramer and Damg˚ard
(Cramer and Damg˚ard, 2005)). All these protocols
consist of two steps. In a first step, each player P
i
with 1 ≤ i ≤ 2t + 1 computes f
α
(i) f
β
(i) and shares
this value with the other participants using a polyno-
mial h
i
(x) of maximum degree t . He sends player P
j
with 1 ≤ j ≤ n the value h
i
( j) . Here, it is assumed
that the n parties with n ≥ 2t + 1 are connected by
secure point-to-point channels. When used in the en-
vironment of sensor networks, this task could be done
when producing the actual sensor nodes, before de-
ployment into the field.
In a second step, each of these players computes
his share H( j) of αβ by combining the values h
i
( j)
for i = 1, 2, . . . 2t + 1 . The approach is (uncondition-
ally) secure against an adversary, who can corrupt
at most t of the players under the so-called “honest-
but-curious” model. This means that the adversary is
passive and can read the memories of the corrupted
players but not modify their behavior. For details the
reader is referred to the original papers.
The first step of the multiplication protocol of
Gennaro, Rabin and Rabin (Gennaro et al., 1998) re-
quires O(n
2
klogn) bit-operations per player, where k
is the bit size of the prime q and n is the number of
players.
In the correspondingmodified step of (Lory, 2007)
this complexity is reduced to O(n
2
k). The second
step of the protocol in (Gennaro et al., 1998) requires
O(nk
2
) bit-operations per player. The corresponding
step in (Lory, 2009) has a complexity of O(n
2
k) . Of
course, the latter is an improvement only, if the num-
ber of players is considerably smaller than k . This is
true in many cases, because k ≥ 1024 in many prac-
tical situations. All the protocols need one round of
communication (in the first step).
The above complexities are valid under the as-
sumption that all multiplications are performed in
the classical manner, i. e. a multiplication of an l
1
-
bit-integer and an l
2
-bit-integer requires O(l
1
l
2
) bit-
operations. This is realistic, if the bit-lengths are not
too large. For very large numbers, other methods
like the algorithm of Karatsuba, the Toom–Cook al-
gorithm or discrete Fourier transformation based al-
gorithms are faster (see Knuth (Knuth, 1998)). Care-
ful numerical experiments by Wenzl (Wenzl, 2010),
whose implementation was the base for our research,
demonstrate, that also in these cases considerable re-
ductions in computing time can be achieved by the
methods of (Lory, 2007) and (Lory, 2009).
3 PRELIMINARY RESULTS
In our first approach we were interested in two things:
how does the improved protocol scale in comparison
to the unmodified Gennaro, Rabin, and Rabin version
DCNET 2010 - International Conference on Data Communication Networking
126
when altering the number of players and the num-
ber of bits in the underlying field, and how many cy-
cles are used on actual hardware. The following re-
sults were obtained using the software implementa-
tion from (Wenzl, 2010). For the required long inte-
ger arithmetic, the GNU multiple precision arithmetic
library
1
in version 5.0.1 was utilized. We ran the im-
plementation on an AMD Athlon64 X2 5200+ with
one physical core deactivated, fixed to 2.7GHz. The
cycles achieved on this machine can obviously not be
compared to the ones that can be expected on an ac-
tual sensor node, but if the cycle numbers achieved on
the Athlon are already far too high, successful imple-
mentation on a sensor node seems unlikely.
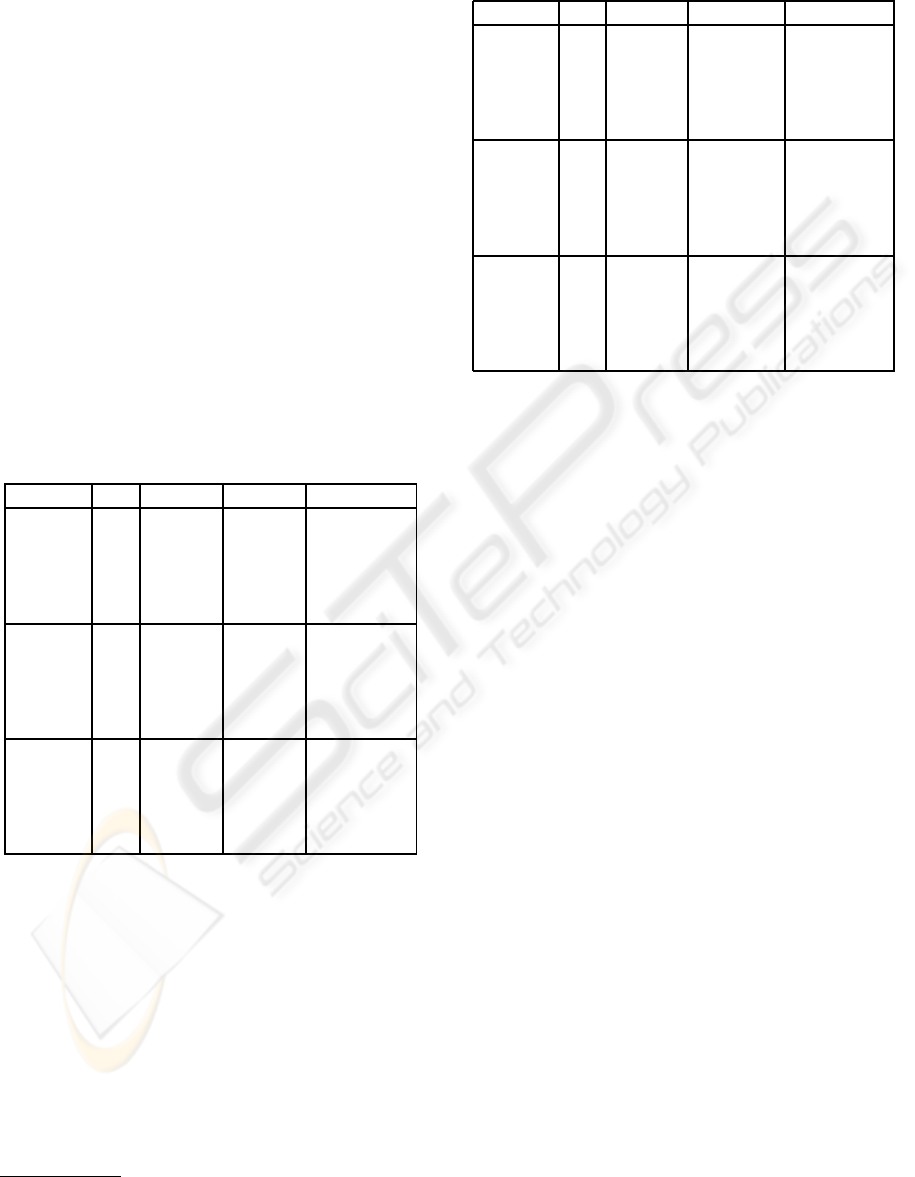
Table 1 gives a comparison of the cycle counts us-
ing the unmodified Gennaro, Rabin, and Rabin (GRR)
protocol, and the modification presented in (Lory,
2007) for different bitlengths and players. The results
are consistent with the theory, whereby the achieved
gain lowers with increased bitlength.
Table 1: Comparison of cycle counts, using the method
from (Lory, 2007).
# of Bits n GRR Lory1 Gain Lory1
160 5 5,420 4,602 15%
160 7 7,507 6,461 14%
160 9 10,051 8,190 19%
160 33 38,331 29,637 23%
160 129 190,935 152,109 20%
256 5 6,717 5,764 14%
256 7 9,504 7,981 16%
256 9 12,470 10,444 16%
256 33 47,514 38,250 19%
256 129 241,400 199,690 17%
1024 5 26,095 24,898 5%
1024 7 38,836 36,575 6%
1024 9 51,736 48,447 6%
1024 33 205,287 190,097 7%
1024 129 917,863 848,298 8%
Table 2 compares the unmodified GRR protocol
with the version utilizing the optimizations presented
in (Lory, 2009). The improvement is much more
pronounced than when only using the method from
(Lory, 2007), although, also according to the com-
plexity theoretic computations, with increasing num-
ber of participants the gain gets lower and eventually
even turns into a loss. The absolute cycle numbers
here are promising, 5,000 cycles for a computation
over a 256-bit field for 7 players (i.e. an attacker
would have to capture and analyze 7 nodes to success-
fully extract the secret) hint for an at least acceptable
time when implemented on a sensor node.
1
http://gmplib.org/
Table 2: Comparison of cycle counts, using the method
from (Lory, 2009).
# of Bits n GRR Lory2 Gain Lory2
160 5 5,420 3,095 43%
160 7 7,507 5,080 32%
160 9 10,051 7,332 27%
160 33 38,331 61,798 -61%
160 129 190,935 813,058 -326%
256 5 6,717 3,282 51%
256 7 9,504 5,328 44%
256 9 12,470 7,861 37%
256 33 47,514 66,759 -41%
256 129 241,400 883,241 -266%
1024 5 26,095 4,787 82%
1024 7 38,836 7,582 80%
1024 9 51,736 11,012 79%
1024 33 205,287 95,900 53%
1024 129 917,863 1,252,135 -36%
4 OUTLOOK
Our next steps will be to exchange the GMP library,
which is far too big for an efficient use on sensor
nodes, with our own, custom built library, tailor made
for the requirements of constraint devices. If the re-
sults are still in an acceptable range, we will port the
algorithms to an actual sensor node and examine the
performance in this environment.
Finally, if it turns out that we still get reasonable
cycle counts, we will try incorporating the multiparty
computation approach into a dedicated security pro-
tocol for wireless sensor networks.
In addition to the aforementioned work, more
detailed analysis and a breakdown of the different
stages of the algorithm is planned, together with more
in depth comparison of the relationships between
bitlength, number of players and cycle count.
ACKNOWLEDGEMENTS
Manuel Koschuch, Matthias Hudler, and Michael
Kr¨uger are supported by the MA27 - EU-Strategie
und Wirtschaftsentwicklung - in the course of the
funding programme “Stiftungsprofessuren und Kom-
petenzteams f¨ur die Wiener Fachhochschul-Ausbil-
dungen”. Peter Lory is supported by the European
Regional Development Fund - Europ¨aischer Fonds
f¨ur regionale Entwicklung (EFRE).
APPLICABILITY OF MULTIPARTY COMPUTATION SCHEMES FORWIRELESS SENSOR NETWORKS - Position
Paper
127

REFERENCES
Cramer, R. and Damg˚ard, I. (2005). Multiparty compu-
tation, an introduction. In Catalano, D., Cramer,
R., Damg˚ard, I., Di Crescenco, G., Pointcheval, D.,
and Takagi, T., editors, Contemporary Cryptology,
Advanced Courses in Mathematics CRM Barcelona,
pages 41–87. Birkh¨auser, Basel.
Gennaro, R., Rabin, M. O., and Rabin, T. (1998). Simpli-
fied VSS and fast-track multiparty computations with
applications to threshold cryptography. In Proceed-
ings of the 17th ACM Symposium on Principles of Dis-
tributed Computing (PODC’98).
Knuth, D. (1998). The Art of Computer Programming, vol-
ume 2. Addison-Wesley, Reading.
Lory, P. (2007). Reducing the complexity in the distributed
multiplication protocol of two polynomially shared
values. In Proceedings of the 21st International Con-
ference on Advanced Information Networking and Ap-
plications (AINA’2007), volume 1, pages 404–408.
IEEE Computer Society.
Lory, P. (2009). Secure distributed multiplication of two
polynomially shared values: Enhancing the efficiency
of the protocol. In Proceedings of the Third Inter-
national Conference on Emerging Security Informa-
tion, Systems and Technologies (SECURWARE 2009),
pages 486–491. IEEE Computer Society.
Merwe, J. V. D., Dawoud, D., and McDonald, S. (2007).
A survey on peer-to-peer key management for mobile
ad hoc networks. ACM Computing Surveys (CSUR),
39(1):1–45.
Shamir, A. (1979). How to share a secret. Communications
of the ACM, 22(11):612–613.
Wenzl, J. (2010). Laufzeitanalyse dreier Versionen
eines Mehrparteien-Multiplikationsprotokolls. Re-
gensburger Diskussionsbeitr¨age zur Wirtschaftswis-
senschaft 440, Institut f¨ur Wirtschaftsinformatik, Uni-
versit¨at Regensburg.
DCNET 2010 - International Conference on Data Communication Networking
128
