
ALGORITHMS FOR BINARIZING, ALIGNING AND
RECOGNITION OF FINGERPRINTS
A. Pillai, S. Mil’shtein and M. Baier
Advanced Electronic Technology Center, ECE Dept.,University of Massachusetts, 1 University Ave, Lowell, MA U.S.A.
Keywords: Fingerprints recognition, Binarizing, Alignment, Fourier transform.
Abstract: Minutiae based algorithms are widely used today for fingerprint authentication. In this study, we report the
use of the Fast Fourier Transform (FFT) as a base principle for our recognition method, and have also
developed image normalization methods. We also developed a novel method to align fingerprints to a
common reference orientation based on the Fourier Mellin Transform. Two methods for image recognition
are described. The first method uses image subtraction techniques in conjunction with a thresholding
scheme. The second method, which is currently in development, utilizes multiple neural networks running
in parallel. This technique is expected to be able to run image comparisons on large databases in real-time
through the use of modern parallel processing technology. In this study we analyzed 720 fingerprints
generated by wet-ink, flat digital scanners, and by a novel touch less fingerprinting scanner. For the image
subtraction method comparing high quality fingerprints (prints taken in touch less way), the rate of success
is 97%. For poorer quality prints, (those taken with wet-ink) the rate of success dropped to 93%.
Recognition statistics are not currently available for the neural network based image recognition method as
it is currently in development.
1 INTRODUCTION
Fingerprints offer a unique method for personal
identification. Fingerprints afford an infallible
means of personal identification, because the ridge
arrangement on every finger of every human being
is unique and does not alter with growth or age.
Fingerprint authentication is the most preferred
method because of their distinctiveness and
persistence over time as specified by Maltoni
(2003). The individuality of fingerprints has been
discussed in detail by Pankati (2001). It has served
almost all the governments worldwide over many
years to provide accurate identification of criminals.
No two fingerprints have been found to be the same
in the billions of comparisons that have been done to
date unless they belong to the same person. It
outperforms DNA and other human identification
systems to identify more number of criminals.
The minutiae algorithm is widely used for
fingerprint authentication. Minutiae points are local
ridge characteristics that appear as either a ridge
ending or a ridge bifurcation. A complete fingerprint
consists of about 100 minutiae points in average.
The measured fingerprint-area consists in average of
about 30-60 minutiae points depending on the finger
and on the sensor area. These minutiae points are
represented by a cloud of dots in a coordinate
system. They are stored together with the angle of
the tangent of a local minutiae point in a fingerprint-
code or directly in a reference template. A template
can consist of more than one fingerprint-code to
expand the amount of information and to expand the
enrolled fingerprint area. In general this leads to a
higher template quality and therefore to a higher
similarity value of the template and the sample. To
overcome the drawbacks of minutiae, hybrid
methods have been proposed in Jain (2001).
There are many challenges that need to be
overcome when developing an algorithm which is to
be used for reliable recognition of fingerprints
recorded by different technologies. This is because
different fingerprint capture techniques create
different representations of a given finger. These
challenges include different format size of images,
non-linear distortions of fingerprint ridges,
differences in orientation, and variation of gray scale
values.
In the current study, we use the Fast Fourier
Transform (FFT) as a base principle for our novel
426
Pillai A., Mil’shtein S. and Baier M..
ALGORITHMS FOR BINARIZING, ALIGNING AND RECOGNITION OF FINGERPRINTS.
DOI: 10.5220/0003362104260432
In Proceedings of the International Conference on Computer Vision Theory and Applications (VISAPP-2011), pages 426-432
ISBN: 978-989-8425-47-8
Copyright
c
2011 SCITEPRESS (Science and Technology Publications, Lda.)

recognition method. We have also developed a new
binarization method that is used to eliminate
variations in gray scale levels of each image, leaving
the resulting images looking like a traditional ink
rolled fingerprint. In this study we analyze 720
fingerprints generated by wet-ink, flat digital
scanners, taken from FVC 2004 and by the novel
contactless fingerprinting scanner described in
Palma (2006) and Mil’shtein (2008). In section 2,
we describe the binarization steps, section 3 contains
description about the fingerprint alignment process
and section 4 contains information about the
recognition procedure.
2 BINARIZATION PROCEDURE
Most fingerprint recognition algorithms currently
being used, including the widely used minutiae
algorithm, rely on the specificity of ridge endings
and ridge bifurcations. Because of this, it is
necessary to clearly define the fingerprint ridges and
valleys using only two distinct values, this process is
called binarization, and is one of the most important
steps that precede the recognition stage. Regardless
of the quality of any image recognition algorithm, a
poorly binarized image can compromise its
recognition statistics.
A good binarization algorithm would give an
image which would have very clear and uniform
black ridges on a white background even if the
image is overexposed to a certain degree. In the
current study the following binarization techniques
are used:
1) Region-Based thresholding
2) Filter-Based mentioned in Meenen (2005)
The first step is to divide the image into an N by
N grid of smaller blocks. Then the ridges like
regions within these smaller blocks are determined.
This is done by taking the gradients in the X and Y
direction and then finding the co-variance data for
the image gradients. Once this step is completed, the
orientation of ridges is computed. Estimation of
ridge frequencies in these blocks follows. For this,
first the mean orientation within the block is
obtained. Then the image block is rotated so that the
ridges are vertical. The rotated image is then
cropped so that it does not contain any invalid
regions. A projection of the grey values, down the
ridges, is obtained by summing down the columns.
Peaks in projected grey values are found by
performing grayscale dilation and then finding
where the dilation equals the original values. The
spatial frequency of the ridges is determined by
dividing the distance between the 1st and last peaks
by the number of peaks. If no peaks are detected, or
the wavelength is outside the allowed bounds, the
frequency image is set to 0. The ridges are then
enhanced with the help of a median filter. The image
obtained after this process is thresholded to obtain
the binary fingerprint. The threshold for binarization
depends on the resolution for the image.
We found that this technique works best with the
images that are obtained from the contactless
fingerprinting system described in Mil’shtein
(2008). This binarization technique is largely
invariant to inconsistencies in brightness levels
throughout the image, and results in a binary image
that has consistent information throughout. It should
be mentioned at this point that the downside of this
process is that a relatively large number of
calculations are needed, which adds to the time
needed for the overall recognition algorithm to
complete. In section 6 we give recommendations on
image registration procedures, but for now it is
recommend that all images that are to be stored in a
database be stored (at minimum) in their binary
forms to reduce computations when comparing
fingerprint images.
3 FINGERPRINT ALIGNMENT
Fingerprint alignment is an important stage that
precedes fingerprint recognition. It is important
because no matter which algorithm is being used for
recognition, one must be sure that the regions being
compared are the same. Fingerprint alignment using
eight special types of ridges extracted from thinned
fingerprint image is reported in Hu (2008) . Other
alignment techniques based on phase correlation of
minutiae points as described in Chen (2007), using
line segments as pivots based on minutiae as
mentioned in Carvalho (2004) and using similarity
histogram detailed by Zhang (2003), have also been
reported. But their inherent dependence on minutiae
necessitates a need for a new novel alignment
technique not based on minutiae. In this study, an
alignment technique based on the Fourier Mellin
Transform will be described.
The Fourier-Mellin transform is a useful
mathematical tool in image processing because its
resulting spectrum is invariant in rotation, translation
and scale. The Fourier Transform itself (FT) is
translation invariant. By converting the resulting FT
to log-polar coordinates, we can convert the scale
and rotation differences to vertical and horizontal
ALGORITHMS FOR BINARIZING, ALIGNING AND RECOGNITION OF FINGERPRINTS
427
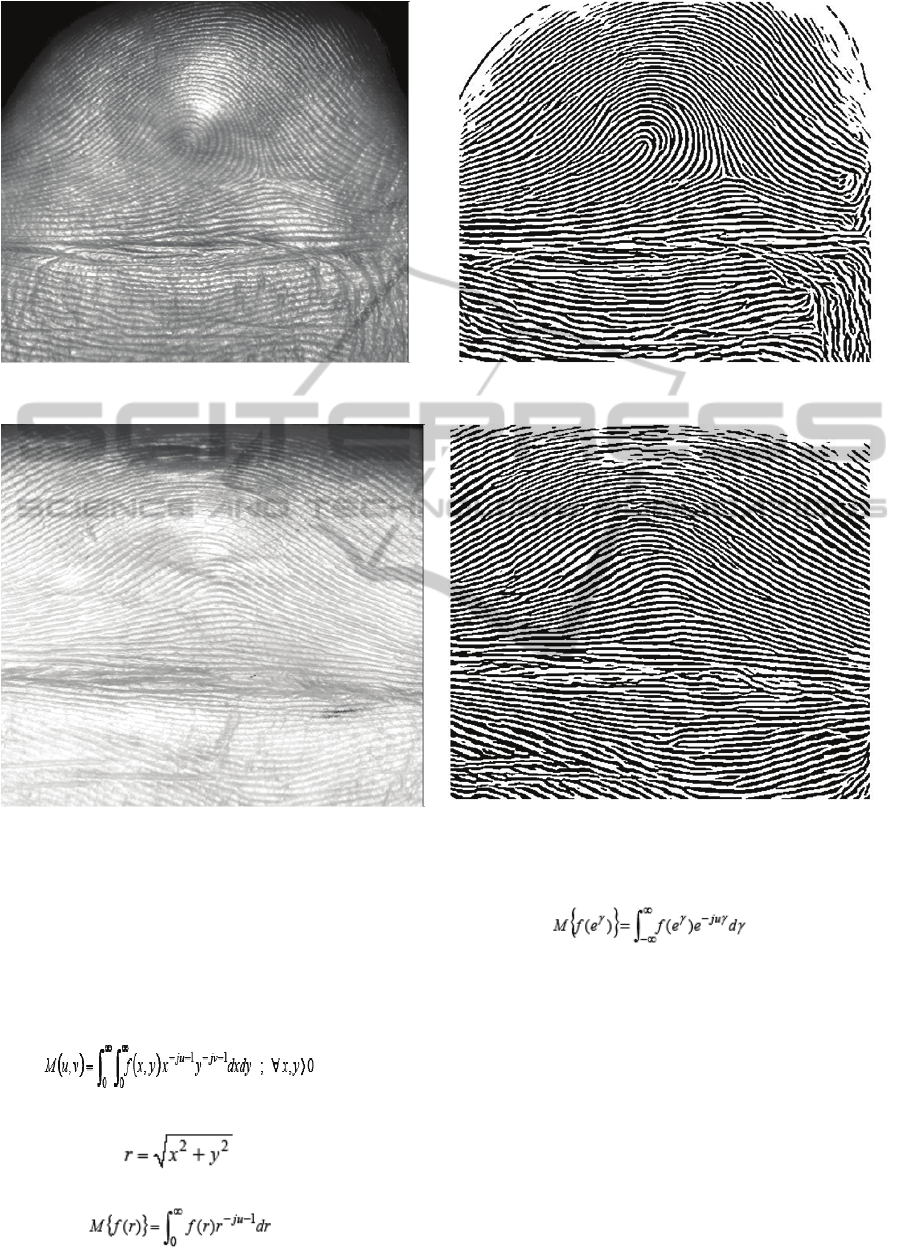
Figure 1: Grayscale image of a selected fingerprint (Left) and the corresponding binarized image (Right).
Figure 2: Strength of binarization even if the image is seemingly overexposed.
offsets that can be quantified. A second transform,
called the Mellin transform (MT), gives a transform-
space image that is invariant to translation, rotation
and scale. An application of the Fourier-Mellin
Transform for image registration can be found in
Guo (2005).
The Mellin transform can be expressed as:
(1)
Convert to polar coordinates using:
(2)
We now have:
(3)
Making r = e
ỳ
and dr = e
ỳ
d
ỳ we have :
(4)
By changing coordinate systems from Cartesian
to a Log-Polar system, we can directly perform a
DFT over the image to obtain the scale and rotation
invariant representation. The figures below show
some of the results of the alignment using the
Fourier-Mellin transform on images taken from
Palma (2006).
The inverse Fourier transform of the Mellin
Transformed images helps to see how well the
image is aligned with respect to the base image.
While this step is necessary to see the alignment
results, the Fourier transforms are stored in as
separate database as from here they are now the
VISAPP 2011 - International Conference on Computer Vision Theory and Applications
428
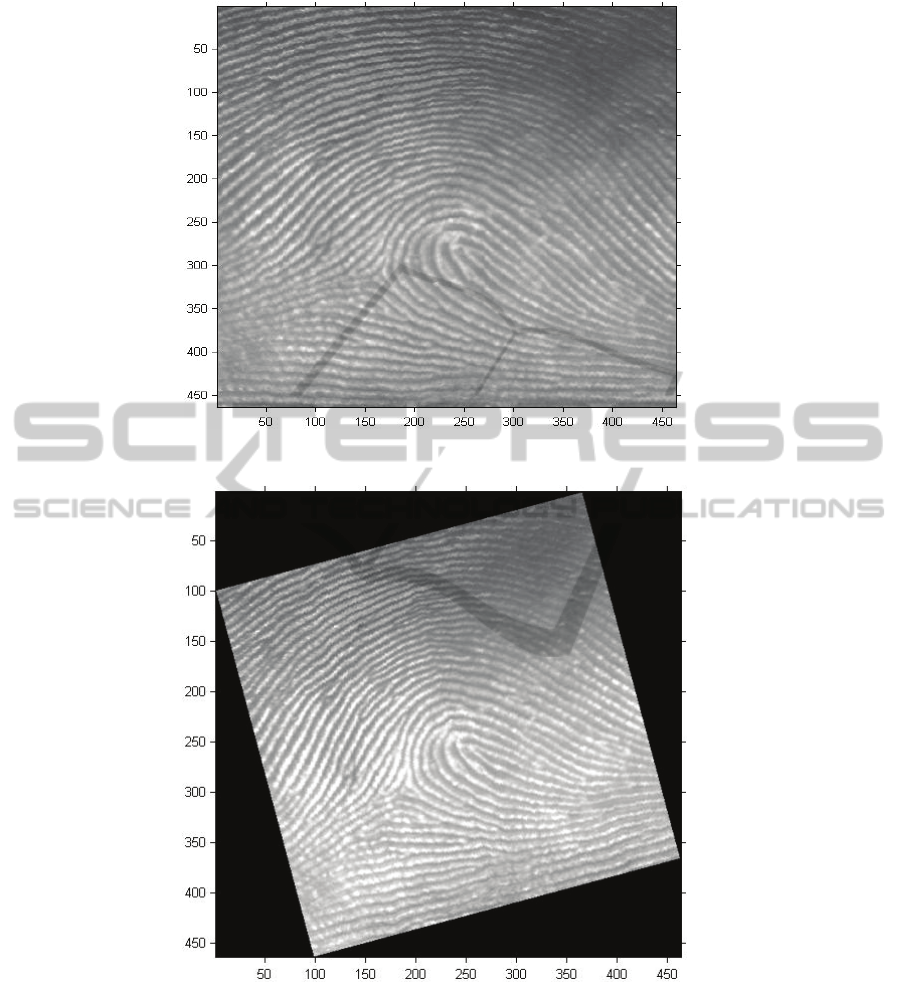
Figure 3: Image of the 1
st
fingerprint.
Figure 4: Image of 2
nd
fingerprint (In need of alignment).
templates that will be used for comparison. This will
eliminate the need to take again the FFT of the
aligned image and the base image when it comes to
comparing the fingerprints.
4 REGISTRATION
PROCEDURES
To run a fingerprint recognition system in its most
efficient state, steps should be taken within image
registration procedures to ensure that all possible
normalization of images and image transforms are
ALGORITHMS FOR BINARIZING, ALIGNING AND RECOGNITION OF FINGERPRINTS
429

Figure 5: Aligned 1
st
and 2
nd
images (Image 2 superimposed upon image 1).
done upon image registration and not at the time of
image recognition. This way when it is time for
actual image comparison, fewer calculations will
need to be preformed, greatly increasing the
throughput of the algorithm. For this reason, we
recommend the following image registration
procedures.
It should be the normalized frequency domain
image that should be stored in the database rather
than the original or binarized image. This allows the
pattern recognition engine to directly take the image
data for use in comparison without the need for any
preprocessing steps. We recommend that as a new
image is acquired, it is processed and stored as
shown in figure 6.
Figure 6: Image registration procedure.
5 RECOGNITION ALGORITHM
There are three types of algorithms used for
fingerprint matching briefly described by Prabhakar
of MSU:-
a) Correlation based Algorithm:-
Here two fingerprints are superimposed on each
other and the correlation at intensity level between
corresponding pixels is computed.
b) Minutiae based Algorithm:-
Minutiae points are first determined on a fingerprint.
In order to make a comparison, 21 points are needed.
Minutiae points are nothing but points where there is
a ridge ending or a ridge bifurcation. In this process,
the minutiae points are stored as sets of points in a
two dimensional template. Then the algorithm finds
the alignment between the template and the input set
of minutiae sets that result in maximum number of
pairings. This stage requires the operator
intervention.
c) Ridge Feature based Matching:-
Here fingerprints are compared based on the features
extracted from the fingerprints.
In this study we report on the development of an
algorithm based on taking the Fast Fourier
Transform (FFT) of images and using a thresholding
scheme for comparison. It should be mentioned here
VISAPP 2011 - International Conference on Computer Vision Theory and Applications
430

that there are drawbacks to using a thresholding
scheme, and we are currently developing a neural
network based pattern recognition engine which can
take advantage of modern day parallel processing.
We expect to largely decrease the time necessary to
compare multiple images within a database,
hopefully opening up a door for large database, real-
time fingerprint recognition applications.
The Fourier Transform is an important image
processing tool which is used to decompose an
image into its sine and cosine components. The
output of the transformation represents the image in
the Fourier or frequency domain. The DFT is the
sampled Fourier Transform and therefore does not
contain all frequencies forming an image, but only a
set of samples which is large enough to fully
describe the spatial domain image. The number of
frequencies corresponds to the number of pixels in
the spatial domain image, i.e. the image in the
spatial and Fourier domain is of the same size.
For a square image of size N×N, the two-
dimensional DFT is given by:
(5)
Where f(a,b) is the image in the spatial domain
and the exponential term is the basis function
corresponding to each point F(k,l) in the Fourier
space. The equation can be interpreted as: the value
of each point F(k,l) is obtained by multiplying the
spatial image with the corresponding base function
and summing the result.
It is this frequency domain image that should be
saved as the reference information for registration of
a new fingerprint to a database. By saving this image
rather than the raw, oriented, or binarized images
which resulted from the previous steps one can
minimize the number of calculations necessary when
the time comes for actual fingerprint comparison.
Image comparison is currently done by comparing
the frequency domain images element by element to
see which have a similar value. Based on the
similarity of these values, a counter is incremented
and once this value crosses a statistically determine
threshold, a match is declared. We are working on
increasing the database so that we can provide ROC
and CMC datasets and curves and test the
performance on a wider database. For high quality
fingerprints (prints taken touch less way), the rate of
success is 97%. For poorer quality prints, (those
taken with wet-ink) the rate of success of our
algorithm is 93%. The advantage of this method of
comparison is that it is independent of minutiae
points and more reliant on the ridge patterns. If the
fingerprint is distorted with pressure induced
distortion then this algorithm can be used to
determine a match. We continue to increase the
database for analysis by our recognition algorithms.
A pattern recognition engine should be present in the
recognition stage to successfully compare an image
with a large database. The drawbacks of this
algorithm would be the time taken to come to a
decision and the requirement that the images
compared be of the same size.
We are currently developing a neural network
based approach for pattern recognition within
fingerprint images. Neural networks consist of
highly interconnected processing elements called
neurons which are all interconnected acting in
parallel to solve a common goal. This methodology
lends itself to parallel processing, and can take
advantage of modern day parallel processing
hardware, creating the opportunity for image
comparison in real-time even when comparing large
databases. The system in development currently
divides the images in a database into sets of
approximately 200 images, and trains one neural
network per image set utilizing an automated
training process described in Masters (1993). The
utilization of neural networks allows the system to
be optimized to run on high throughput graphics
processing units (GPU’s). By selecting the number
of neurons in the network to be equal to the number
of pixels in the frequency domain images being
compared, a direct image-to-image comparison can
be done in one GPU clock cycle. Each network is
capable of comparing approximately 200 images
accurately, and the number of networks in parallel is
limited by the number of GPU’s in the system. By
creating many neural networks, all autonomously
trained, we expect to be able to create a real-time
fingerprint recognition system for large-scale
databases.
In Gour (2010), the fingerprints are recognized
by using Monolithic and Modular Neural Network.
A monolithic neural network is one that takes an
input vector X and produces an output vector Y. The
relationship between X and Y is determined by the
network architecture. It generally consists of three
layers: one input layer, one output layer and more
than one hidden layer. The Backpropagation neural
network is an example of the monolithic network.
The training of a backpropagation network involves
three stages: the feedforward of the input training
patterns, the calculation and backpropagation of the
associated error and the weight adjustments.
Backpropagatin network is trained for query
ALGORITHMS FOR BINARIZING, ALIGNING AND RECOGNITION OF FINGERPRINTS
431

fingerprint to match it among a large number of
stored fingerprints as is evident in Jin (2002). The
average training time is 44.7 secs and the accuracy is
98%.
In the modular approach, one task is decomposed
into subtasks, and the complete solution requires the
contribution of all modules. To train a modular
neural network, which is having N number of
modules (feature points) in a particular fingerprint
requires two steps: Training of small modules and
training of intermediary modules. All the modules
are trained by using the backpropagation neural
network algorithm specified by Gour (2005). The
average time taken is 1.84 secs and the accuracy is
100%. Due to modularity, the modular neural
network gives better performance as compared to
monolithic networks.
6 CONCLUSIONS
We reported the development of a novel fingerprint
normalization and authentication algorithm which
has binarization, alignment, and recognition stages.
It is important to note that our method of fingerprint
image processing requires organization of database.
Structuring of database is orientation of all fingers
with regards to the position of the reference delta.
Although, we are suggesting a quality control in our
flow of processing to be done by Inverse Mellin
Transform, this step is more precautionary method.
Unlike, widely distributed minutiae based
fingerprint processing; our method does not require
interference of operator or final analysis by an
operator. We also continue to increase the database
so that we can provide ROC and CMC datasets and
curves and test the performance on a wider database.
Well known development of neural networks for
processing of massive image files can be easily used
in our method. The neural network is expected to
shorten the processing time significantly. We also
report the beginnings of a neural network based
recognition engine running on parallel GPU’s, which
is expected to enable real-time image recognition on
large databases. Finally, the recommended image
registration procedures are outlined which are
designed to optimize performance of the image
recognition algorithm by decreasing the number of
calculations necessary for image comparison.
REFERENCES
Maltoni, D., Maio D., Jain A. K., Prabhakar S., 2003,
Handbook of Fingerprint Recognition Springer-
Verlag, New York,
S. Pankanti, S. Prabhakar, A. K. Jain, CVPR 2001 Volume
1, 2001 pp I-805-I-812 vol.1. “On the individuality of
fingerprints” Proc of the 2001 IEEE Computer
Society Conference on Computer Vision and Pattern
Recognition.
Anil Jain, Arun Ross, Salil Prabhakar, 2001, pp. 282-285,
“Fingerprint Matching using Minutiae and Texture
Features” Proc. of international conference on Image
Processing.
Palma J, Liessner C, Mil’shtein S, 2006, “Contactless
Optical Scanning of Fingerprints with 180° View”
Scanning, 28, 6, pp 301-304
S. Mil’shtein, J. Palma, C. Liessner, M. Baier, A. Pillai,
and A.Shendye, 2008, "Line Scanner for Biometric
Applications" IEEE Intern. Conf. on Technologies for
Homeland Security, ISBN 978-1-4244-1978-4 P 205-
208.
P. Meenen, R. Adhami, 2005, “Approaches to image
binarization in current automated fingerprint
identification systems”, Proceedings of the Thirty-
Seventh Southeastern Symposium on System Theory,
ISBN: 0-7803-8808-9
C. Hu, J. Yin, E. Zhu, H. Chen, Y. Li, 2008, “Fingerprint
Alignment using Special Ridges” ISBN 978-1-4244-
2175-6
W. Chen, Y. Gao, 2007, “Minutiae-based Fingerprint
Alignment Using Phase Correlation”, Mechatronics
and Machine Vision in Practice, Springer Link, pp
193-198,
C. Carvalho, H. Yehia, 2004, “Fingerprint Alignment
using Line Segments”, Biometric Authentication,
Springer, pp 1-10
T. Zhang, J. Tian, Y. He, J. Cheng, X. Yang, 2003,
“Fingerprint alignment using similarity histogram”,
International conference on audio and video-based
biometric person authentication, pp 854-861
Xiaoxin Guo Zhiwen Xu Yinan Lu Yunjie Pang, Sep
2005, “An Application of Fourier-Mellin Transform in
Image Registration”, The Fifth International
Conference on Computer and Information
Technology, pp 619-623.
S. Prabhakar, A. Jain, “Fingerprint
Identification”,<http://www.cse.msu.edu/biometrics/fi
ngerprint.html>
Masters, Timothy, 1993, “Practical Neural Network
Recipies in C++” ISBN: 0-12-479040-2
B. Gour, T.K. Bandopadhyaya, R. Patel, 2010, “ART and
Modular Neural Network Architecture for multilevel
Categorization and Recognition of Fingerprints”,
2010 Third International Conference on Knowledge
Discovery and Data Mining, pp 536-539
A. L. H. Jin, A. Chekima, J. A. Dargham, L. C. Fan, 2002,
“Fingerprint Identification and Recognition using
Backpropagation Neural Network”, Proceeding of
Student Conference on Research and Development, pp
98-101
B. Gour, et. Al, 2005, “Fast Fingerprint Identification
System using Backpropagation Neural Network and
Self Organizing Map
”, Proc. Of Glow Gift.,
International Level Seminar.
VISAPP 2011 - International Conference on Computer Vision Theory and Applications
432
