
Combining the Spray Technique with Routes to Improve the Routing
Process in VANETS
Maur
´
ıcio Jos
´
e da Silva
1
, Fernando Augusto Teixeira
2
, Saul Delabrida
1
and Ricardo A. Rabelo Oliveira
1,∗
1
Department of Computing, Federal University of Ouro Preto, Ouro Preto, Brazil
2
Department of Computing, Federal University of S
˜
ao Jo
˜
ao Del Rey, Ouro Branco, Brazil
Keywords:
Wireless Networks, Vehicular Networks, Routing Protocols.
Abstract:
Vehicular networks represent a special type of wireless network that has gained the attention of researchers
over the past few years. Routing protocols for this type of network must face several challenges, such as high
mobility, high speeds and frequent network disconnections. This paper proposes a vehicular routing algorithm
called RouteSpray that in addition to using vehicular routes to help make routing decisions, uses controlled
spraying to forward multiple copies of messages, thus ensuring better delivery rates without overloading the
network. The results of experiments performed in this study indicate that the RouteSpray algorithm delivered
13.12% more messages than other algorithms reported in the literature. In addition, the RouteSpray algorithm
kept the buffer occupation 73.11% lower.
1 INTRODUCTION
Vehicular ad hoc networks (VANETs) represent a spe-
cial type of wireless network that has gained the at-
tention of researchers over the past few years. This
type of network offers, through Intelligent Transport
Systems (ITS), such services such as driver assis-
tance, entertainment and dissemination of informa-
tion (Taysi and Yavuz, 2012).
In VANETs, the high mobility of vehicles causes
frequent disconnections among network nodes, which
partitions networks and prevents the use of rout-
ing protocols designed for ad hoc networks. How-
ever, some features of VANETs can be used to as-
sist in routing, such as mobility patterns limited by
roads, the tendency of vehicles to move in groups and
the integration of sensors into vehicles (Toor et al.,
2008) (Li and Wang, 2007). There are several routing
algorithms that have been proposed for VANETs, but
recent technological achievements and their popular-
ization, such as GPS, have opened up the possibility
of proposing even more efficient protocols.
This article introduces the RouteSpray algorithm.
This algorithm combines four important concepts in
∗
The authors would like to thank to Federal University
of Ouro Preto, CAPES, FAPEMIG and SEVA for financial
support.
making routing decisions: (i) use of the store-carry-
and-forward technique (Zhao and Cao, 2008) to route
messages; (ii) transmission of messages based on di-
rect contact (Spyropoulos et al., 2008a); (iii) use
of the routes of the vehicles to assist in routing, as-
suming that the vehicles are equipped with GPS; and
(iv) use of the controlled spraying of messages tech-
nique (Spyropoulos et al., 2008b). Keeping in mind
that all the techniques mentioned above are studied in
the literature with the aim of improving the routing
process, the main contributions of RouteSpray are:
• To combine the controlled spray technique using
routes to improve the routing process;
• To explore the geographic routing for mobile des-
tinations;
• To offer a comparative study and a performance
analysis of the controlled spraying technique and
the use of routing information for routing.
Several protocols that aim to perform routing in
VANETs have been presented. The main difference
among these protocols is the information they con-
sider in routing (history of contacts among nodes, lo-
cation information, etc.) and the strategy they use to
forward messages (number of generated replicas for
each message). Nevertheless, there is a consensus
among the scientific community that there is no ideal
routing protocol that can be applied in all scenarios.
583
José da Silva M., Augusto Teixeira F., Delabrida S. and A. Rabelo Oliveira R..
Combining the Spray Technique with Routes to Improve the Routing Process in VANETS.
DOI: 10.5220/0004871005830590
In Proceedings of the 16th International Conference on Enterprise Information Systems (ICEIS-2014), pages 583-590
ISBN: 978-989-758-028-4
Copyright
c
2014 SCITEPRESS (Science and Technology Publications, Lda.)

The RouteSpray protocol aims to address scenarios
in which the routes of vehicles are previously known,
which has become common due to the popularization
of navigation devices, especially if we consider fleets
with controlled mobility, such as buses, trucks and
taxis. This protocol was designed to use the routes
of vehicles to make routing decisions, which is the
only premise it requires.
The RouteSpray protocol was validated through a
simulation of an urban environment where vehicles
run through routes that connect the points of interest
of a city. To ensure a more realistic simulation, the
OMNeT++ simulator (Varga, 1999) was used together
with the VeNeM software (Silva, 2012). The results
of the experiments show that the RouteSpray algo-
rithm delivered 13.12% more messages than other
proposals reported in the literature and kept the buffer
occupancy 73.11% lower.
The remainder of the paper is organized as fol-
lows: in Section 2, related studies are presented. In
Section 3, the operation of the RouteSpray algorithm
is described. In Section 4, the simulation environment
and the experimental results are presented. Finally,
in Section 5, conclusions and future studies are dis-
cussed.
2 RELATED WORKS
Over the past few years, several algorithms such as the
DSR (Dynamic Source Routing) (Johnson and Maltz,
1996) and the AODV (Ad-hoc On-demand Distance
Vector) (Perkins and Royer, 1999) algorithms have
been proposed to solve the routing problem associ-
ated with ad hoc networks. Both protocols initiate
data transmission only after establishing a path be-
tween source and destination, a characteristic that is
often not satisfied in VANETs because this type of
network suffers frequent disconnections caused by the
high speed and high mobility of vehicles. To avoid
data loss, routing protocols for VANETs consider the
use of the store-carry-and-forward technique (Lee and
Gerla, 2010).
Another characteristic that can benefit routing al-
gorithms for VANETs is the use of location informa-
tion of network nodes, which has become possible
due to the incorporation of Navigation Systems (NS)
into vehicles. Routing protocols that use this tech-
nique are classified as position-based or geographic-
based (Allal and Boudjit, 2012).
Opportunistic transmission and context infor-
mation can both be used in VANETs to improve
the routing process. One of the main algorithms
for vehicle routing is the GeOpps (Leontiadis and
Mascolo, 2007). The GeOpps is a single copy
algorithm, which aims to route data messages to a
specific geographic region. Its operation is based
on calculating the estimated minimum time to the
message delivery. To achieve this it explores the data
provided by the navigation systems. The calculation
of METD is done as follows: The algorithm traverses
the route of the vehicle looking for the nearest point
to the destination; after the NP is discovered, the
algorithm queries the NS to get the estimated travel
time from your current position to the NP; finally, the
algorithm adds the time returned by the NS to the
estimated time for the vehicle to travel in a straight
line from the NP to the destination. In general, the
METD can be calculated as follows:
MET D = ETA to NP + ETA f rom NP to D
The GeOpps algorithm was designed for vehicular
networks, and uses the vehicle routes to route mes-
sages toward the destination. However, the fact that
it does not explore alternative paths using multiple
copies of the message causes major delays in the de-
livery of the message, making it unviable for practical
use.
Another scheme that explores opportunistic trans-
mission combined with multiple copies of the mes-
sage to ensure better delivery rates, is called Epidemic
routing (Vahdat et al., 2000). The Epidemic algo-
rithm uses the store-carry-and-forward technique to
improve data delivery rates. It stores received mes-
sages in a buffer and takes advantage of opportunistic
contact to replicate the stored messages to the other
nodes of a network. This technique causes the net-
work to flood with messages and ensures that one of
the replicas of the message follows the shortest ex-
isting path to the destination. Hence, the Epidemic
algorithm achieves a high message delivery rate and
low delay for messages transmitted to the destination.
Nevertheless, due to the excessive number of message
replicas, this type of routing causes network degrada-
tion, abusive consumption of electricity and a large
occupancy of buffers. Such characteristics make the
Epidemic algorithm unusable in various scenarios.
To solve the problems associated with the Epi-
demic algorithm, an algorithm called Spray and Wait
was proposed in (Spyropoulos et al., 2008b). The
Spray and Wait algorithm uses the spray technique to
decrease the number of replicas of messages sprayed
over a network. Although the authors introduced the
use of the algorithm in sparse networks, the spray
technique was first used in cellular networks. This
technique aimed to spray messages among the points
that are most frequently visited by users (Tchakountio
and Ramanathan, 2001). The Spray and Wait algo-
ICEIS2014-16thInternationalConferenceonEnterpriseInformationSystems
584

rithm is divided into two phases. In the spray phase,
the source node calculates the number of copies that
must be sprayed. This calculation is based on the
number of network nodes and on the desired de-
lay time for the message to reach the destination.
These copies are sprayed in an opportunistic manner
among the nodes that enter the transmission area of
the source node. If the message is not delivered to the
destination in the spray phase, the nodes initiate the
wait phase. In the wait phase, each node keeps the
message in its buffer until it comes across the destina-
tion node, and only then does it deliver the message.
Although dense networks are beneficial to the op-
eration of the Spray and Wait algorithm, in vehicular
networks, density becomes a trap and compromises
the performance of the algorithm. This negative ef-
fect occurs because the flow of vehicles becomes con-
centrated at intersections and traffic lights then spread
along different directions that vehicles may follow.
Such behavior causes some copies of the message to
be taken away from the destination. As a solution, the
Route Spray algorithm uses the routes of vehicles to
determine the best route through which to send a mes-
sage. The algorithm sprays messages only among the
nodes that will encounter the destination node, thus
preventing the messages from being sprayed among
nodes that can never deliver them.
3 ROUTESPRAY ALGORITHM
To perform routing, the RouteSpray protocol assumes
that vehicles are equipped with GPS and that in addic-
tion to knowing their route, they also know the route
of the message destination. Those are premises of all
position-based algorithms (Mauve et al., 2001). The
RouteSpray algorithm, however, differs from the oth-
ers for predicting the mobility of the destination node.
Furthermore, there is no need for a fixed network in-
frastructure; that is, it is possible to perform the rout-
ing among vehicles in a completely ad hoc manner.
The operation of the protocol is based on the use
of two types of messages: control messages and data
messages. Control messages are used to maintain the
state of a network, which is achieved by sending con-
text information to neighboring nodes. In order to
avoid conflicts of messages created at the same time,
each message generated in the network has a unique
identifier, which consists of the address of the source
node, the creation time of the message and a counter.
The process of information exchange and the rout-
ing decision making can be divided into three dis-
tinct stages. In the first stage, communication is ini-
tiated by a handshake, when nodes exchange infor-
mation about the packages that have already been de-
livered over the network, allowing for the control of
messages stored in the buffer, which is achieved by
deleting those that have already been delivered. In
the second and third stages, the nodes exchange in-
formation about the state of the buffer. The source
node sends its neighbor a list containing an identi-
fier and the destination of each message in its buffer.
With this information, the neighbor calculates, using
the pre-established routes, the time in seconds that it
will take to deliver each message. After the source
node receives a response from the neighboring node,
it is able to determine which is the best carrier for the
message. More details about the routing stages are
presented below.
Whereas node X entered the broadcast area of the
node Y, the three stages would be as follows:
In the first stage, X sends Y a handshake message
that carries the list of messages that had already been
delivered in the network. Upon receiving this infor-
mation, Y is able to go through its buffer deleting the
messages listed as delivered. At the end of this pro-
cess, with a consistent buffer, Y delivers the messages
addressed to X and sends X a list of the messages it
has in its buffer.
In the second stage, when X receives the list of
messages in the buffer of Y, X calculates the time
it needs to deliver each of these messages. Then, it
sends Y a list containing the identifier and the time
required to deliver each message. To calculate the de-
livery time of the message, X travels the destination
route of the message looking for a intersection point
with its route. At the end of this process, if X finds a
point of intersection, it returns the time in seconds it
takes to go from its current position to that point. If
such intersection point does not exist, the algorithm
returns a negative value, indicating that X is not able
to deliver the message.
Finally, in the third stage, when Y receives infor-
mation about the estimated time that X takes to deliver
each message, it is able to decide which is the best car-
rier for the message. To make this decision, Y needs
to estimate the time it takes to deliver the message it-
self and compare it to the estimated time returned by
X. If Y has more than one copy of the message, it will
use the binary spray technique to spray those copies
to X. If the estimated delivery time returned by X is
shorter than the estimated delivery time returned by Y,
Y forwards the messages to X, making it responsible
for delivering the message to its destination.
The entire routing process described above is pre-
sented in greater detail in pseudo-code:
input: message
CombiningtheSprayTechniquewithRoutestoImprovetheRoutingProcessinVANETS
585
if( received control message ) then
{
if( handshake message ) then
{
Clean Buffer;
Update Delivered Messages List;
Delivers Messages Addressed To Source;
Responds Messages List In Buffer;
}
else
{
if( response to handshake message ) then
{
Receives List Of Messages From Neighbour;
Sends Message Contact Time;
}
else
{
Processes Response Contact Time;
Decides For Better Transmitter;
}
}
}
else
{
if( received data message ) then
{
if( message addressed to me ) then
{
Process Message;
}
else
{
Store In Buffer;
}
}
}
The improvement in performance afforded by the
RouteSpray algorithm is due to the combination of
two important concepts: (i) use of routes to obtain
prior knowledge of contacts among nodes and (ii) use
of the Binary Spray technique. This combination en-
sures better delivery rates without overloading net-
works. Both concepts are explained in greater detail
below.
3.1 Use of Routes
Geolocation information in a network makes it pos-
sible to have prior knowledge about the position of
the network’s nodes. This feature enables package
forwarding in the direction of the destination and im-
proves data delivery rates. The use of the routes of ve-
hicles ensures that the algorithm can predict the con-
tacts among the network nodes. Thus, the algorithm
can make the best forwarding decision.
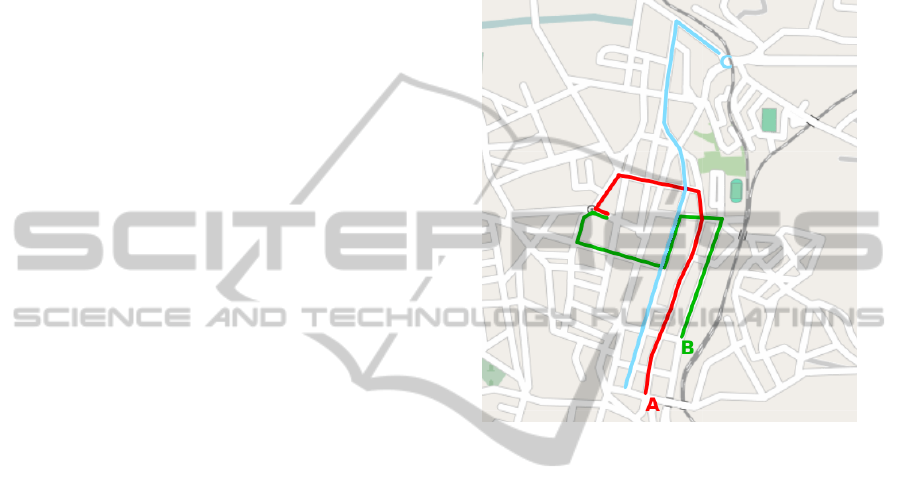
Consider three vehicles that follow pre-
established routes (Figure 1), where vehicle B
has a package addressed to vehicle C. Although the
route of vehicles B and C intersect, vehicle B will
choose vehicle A as the best carrier of the message to
the destination because vehicle A will meet vehicle
C before vehicle B does. This process ensures that
the message will be delivered in the shortest time
possible.
Figure 1: Pre-established routes for three vehicles.
3.2 Binary Spray
Routing schemes based on a single copy of a mes-
sage cause major delays in delivery. On the other
hand, routing schemes based on flooding cause net-
work degradation. To obtain the lowest delay in de-
livery without degrading a network, in (Spyropoulos
et al., 2008b), the authors proposed the ”spray“ tech-
nique, which consists in generating a number of con-
trolled copies of messages and spraying them among
the nodes of a network. When a vehicle wants to
transmit a message, it generates a controlled number
of copies (L). To calculate the value of L, the exist-
ing number of nodes in the network and the desired
delay time for the message to reach its destination are
taken into account. Spraying can occur in two differ-
ent ways, which are referred to the authors as Source
Spray and Binary Spray.
In spraying based on Source Spray, the source
node forwards L copies of the message to the first dis-
tinct L nodes it finds. In Binary Spray, the source node
starts with L copies; while node A has n > 1 copies (is
the source or the carrier) and meets another node B
(that does not have any copies), it will deliver to node
B b(n/2)c copies and keep d(n/2)e copies for itself;
ICEIS2014-16thInternationalConferenceonEnterpriseInformationSystems
586

when the node has only one copy, it will choose direct
contact to perform the delivery.
Another feature of the Source Spray technique is
that a message requires only two hops to reach the
destination; that is, the source forwards the message
to the carrier, which becomes responsible for deliver-
ing it to the destination. This feature causes delays in
the delivery of messages in networks with controlled
mobility, which makes such a technique unusable in
VANETs. In Binary Spray, on the other hand, the fact
that the carrier node receives more than one copy of
the message and forwards them in future contacts in-
dicates that this technique performs routing based on
multiple hops, reducing the delivery time of the mes-
sage. Therefore, Binary Spray was chosen as the mes-
sage routing method for the RouteSpray algorithm.
4 PERFORMANCE ANALYSIS
Although the evaluation of routing protocols in real
environments is desirable, the high cost of implemen-
tation and the difficulty of mobilizing enough staff
to perform the experiments make such implementa-
tion unfeasible. Consequently, the scientific commu-
nity evaluates routing protocols through simulations.
RouteSpray performance was evaluated through sim-
ulations, comparing it with the Epidemic, Spray and
Wait and GeOpps protocols, which are the main rout-
ing protocols used for sparse and vehicular networks.
The performance of the RouteSpray protocol was
evaluated according to the following metrics: (i) mes-
sage delivery rate; (ii) occupancy of buffers; (iii)
number of messages sent over a network; and (iv) av-
erage delay of message delivery. The message deliv-
ery rate refers to the number of messages delivered to
the destination and is important in determining the ef-
fectiveness of a protocol. The occupancy of buffers is
defined as the sum of all messages stored in the nodes
of a network. Occupancy must be considered because
devices that are used in mobile networks have restric-
tions regarding storage. The number of messages sent
over a network is the sum of all messages sent, includ-
ing the control messages, and indicates the numbers
of transmissions needed to ensure the delivery of the
messages. The average delay for message delivery is
useful to indicate the efficiency of the algorithm to
perform routing.
For the simulation scenario, 16 routes were gener-
ated between the points of interest of Barbacena city,
in Brazil. Because its a city that emerged and de-
veloped without proper planning, its streets and av-
enues arose haphazardly. Thus the graph that repre-
sents such scenario has no standard, unlike the graph
of Manhattan (Bai et al., 2003). For the simulation,
the number of vehicles in the network varied between
5 and 100, generating networks with different densi-
ties. For simulations in which the number of vehicles
is greater than the number of routes, more than one
vehicle travels the same route. In this case, in addi-
tion to the vehicles being distributed evenly among
the routes, the vehicles leave at different times. The
transmission speed was also considered to be higher
than the locomotion speed.
The MiXiM framework (K
¨
opke et al., 2008),
an extension to the OMNeT++ Network Simula-
tor (Varga, 1999), was used for the simulation. Ve-
hicular mobility simulations based on random mobil-
ity models do not correspond to reality because the
movement of vehicles is limited to the restrictions of
streets and avenues (Gamess et al., 2012). Further-
more, parameters such as speed and direction suffer
variations. For this reason, vehicular mobility was
generated using the VeNeM software (Silva, 2012).
The parameters used in the simulation are pre-
sented in Table 1.
Table 1: Parameters used in the simulation.
Parameters Values
Simulation time 2700 seconds
Playground X 1.49 miles
Playground Y 2.51 miles
Amount of nodes 5, 10, 25, 50, 75, 100
L Values 2, 3, 6, 8, 12, 20
Band frequency 2.4 GHz
Transmission power 110.11 mW
Signal attenuation -70 dBm
Package size 512 bits
In the simulation time parameter, the value 2700
seconds was used because it corresponds to the time
required for the vehicle to undertake a circular route,
passing through some points of interest in the city.
For the Playground size parameters, it was used the
values returned by the software VeNeM, that corre-
spond to the size needed to cover all the rotes. The
L Values parameter varies according to the number of
network nodes and respects the minimum limits sug-
gested by (Spyropoulos et al., 2008b). The param-
eters related to the physical environment which are:
frequency band, transmission power, signal attenua-
tion and size of the package, were configured with
values used by the 802.11b standard. The 802.11b
standard was chosen because the 802.11p, that was
designed to be used in vehicular networks, was dis-
continued (IEEE, 2010).
CombiningtheSprayTechniquewithRoutestoImprovetheRoutingProcessinVANETS
587
4.1 Results
When a scenario imposes no storage constraints, the
Epidemic algorithm delivers all messages that are
sent, which makes it an important tool for comparing
routing algorithms. Another algorithm that achieves
delivery rates similar to those of the Epidemic al-
gorithm and also causes less network degradation is
the Spray and Wait algorithm. Although both algo-
rithms are good sources of reference rather than re-
ferrals., they are designed for sparse networks, and do
not benefit from the characteristics of vehicular net-
works. Therefore, in addition to being compared with
these two algorithms, the RouteSpray is also com-
pared with the GeOpss algorithm, which takes ad-
vantage of the routes of the vehicles to perform mes-
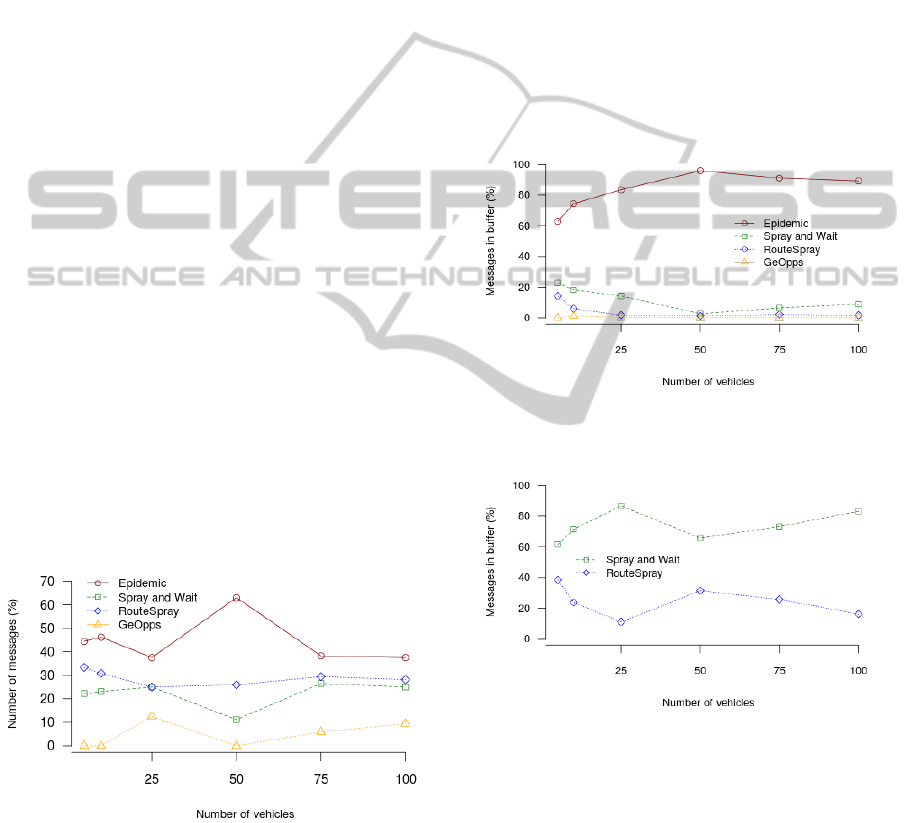
sage routing. Assuming the Epidemic algorithm de-
livers 100% of messages sent over the network, the
RouteSpray, Spray and Wait and GeOpps algorithms
delivered 57.66%, 44.23% and 13.11% of messages,
respectively. The values obtained are presented in
greater detail in Figure 2.
The best message delivery rate is achieved by the
RouteSpray algorithm, as a consequence of the use of
the routes of the vehicles combined with the pulver-
ization of multiple copies of messages. The GeOpps
algorithm had the lowest performance on the num-
ber of messages delivered. This result shows that the
algorithms that use multiple copies of messages out-
performs the algorithms that use routing information.
However, the combination of the two characteristics
has proven more effective than using each one indi-
vidually.
Figure 2: Delivered messages on the network.
As shown in Figure 3, the Epidemic algorithm re-
quires that the nodes have large storage capacities be-
cause each network node stores a copy of each trans-
mitted message. This feature can be perceived more
clearly by observing the transmissions required in a
network with 75 nodes in which, to deliver 15 mes-
sages, the Epidemic algorithm stored 1035 copies of
the messages. The GeOpps algorithm does not make
replicas of the message, therefore its use has no im-
pact in the buffers of the nodes. This characteristic
can be proven by looking at the figure 3. The Spray
and Wait and the RouteSpray algorithms caused little
buffer occupancy, demonstrating the efficiency of the
spray technique, as shown in Figure 4. The Route-
Spray algorithm achieved a buffer occupancy 73.38%
lower than that achieved by the Spray and Wait algo-
rithm because it controls the messages stored in the
buffer, deleting those that have already been deliv-
ered. In the RouteSpray algorithm, the presence of
messages in the buffers of the nodes indicates that the
information that the message was delivered has not
spread enough to reach all the nodes.
Figure 3: Comparison of the buffer occupancy of the three
algorithms.
Figure 4: Improvement in the buffer occupancy by spray
technique.
As previously discussed, the use of control mes-
sages by the RouteSpray algorithm improves data de-
livery rates and controls the buffer occupancy. How-
ever, an additional cost is introduced into the network,
causing a greater number of message transmissions.
This effect is demonstrated in Figure 5. Although the
RouteSpray algorithm results in more message trans-
missions than the Epidemic algorithm, it causes less
overhead in the network because the control messages
have no payload data.
The moment of the message gets its destinantion is
ICEIS2014-16thInternationalConferenceonEnterpriseInformationSystems
588
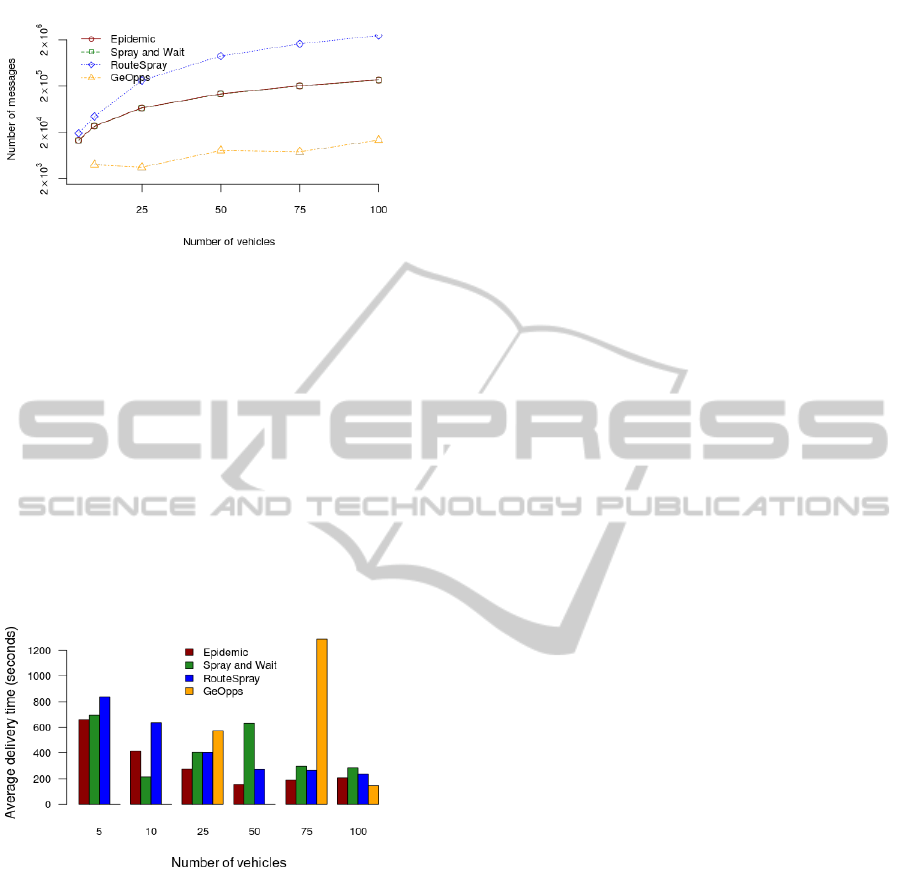
Figure 5: Messages sent over network.
another important feature to be analyzed. Such infor-
mation enable evaluate the efficiency of the algorithm
to perform routing. A shown in Figure 6, the algo-
rithm GeOpps has the worst performance, which is
expected because it is an single copy algorithm. The
epidemic algorithm achieves the best result due to a
message flooding algorithm. However, for the net-
work of 10 nodes, caused a bigger delay than other
algorithm due to the number of messages received.
The RouteSpray ensures better results than Spray and
Wait, losing only with sparses networks, of 5 and 10
vehicles. This causes a higher delivery rate and a ma-
jor impact over the average delay time.
Figure 6: Messages sent over network.
5 CONCLUSIONS
Routing in vehicular networks remains an unresolved
problem. Several algorithms continue to emerge for
use under specific conditions and scenarios. Because
VANETs have several features that are not found in
other types of networks, and such features make it
possible to obtain information that can be used in
routing without incurring an additional cost in a net-
work, the RouteSpray algorithm was proposed in this
study. This algorithm proved to be more efficient than
other algorithms designed for vehicular routing based
on vehicular routes presented to date by the scientific
community.
Despite the challenge of routing packets through
highly dispersed networks, which is common in
VANETs, the RouteSpray algorithm exhibited a good
message delivery rate, surpassing the performance
of algorithms with previously established efficien-
cies. In addition to a good message delivery rate,
the RouteSpray algorithm also requires little storage
space, which makes it applicable in devices with lim-
ited resources.
The RouteSpray algorithm is suitable for appli-
cation in networks in which the routes of vehicles
are known. One example of a good application of
the algorithm is in transportation companies, such as
bus, taxi or carrier companies. The RouteSpray al-
gorithm offers the possibility of dynamic communi-
cation, even in non-routine situations in which pro-
grammed routing would fail, such as when delays oc-
cur because of changes in traffic or flat tires.
ACKNOWLEDGEMENT
The authors would like to thank to UFOP, CAPES,
FAPEMIG and SEVA for financial support.
REFERENCES
Allal, S. and Boudjit, S. (2012). Geocast routing protocols
for vanets: Survey and guidelines. In 2012 Sixth Inter-
national Conference on Innovative Mobile and Inter-
net Services in Ubiquitous Computing (IMIS), pages
323–328.
Bai, F., Sadagopan, N., and Helmy, A. (2003). Important:
a framework to systematically analyze the impact of
mobility on performance of routing protocols for ad-
hoc networks. In INFOCOM 2003. Twenty-Second
Annual Joint Conference of the IEEE Computer and
Communications. IEEE Societies, volume 2, pages
825–835 vol.2.
Gamess, E., Acosta, L., and Hernandez, D. (2012). Ana-
lyzing routing protocol performance versus bitrate in
vehicular networks. In 2012 Global Information In-
frastructure and Networking Symposium (GIIS), pages
1–4.
IEEE (2010). IEEE Standard Association.
Johnson, D. and Maltz, D. (1996). Dynamic source rout-
ing in ad hoc wireless networks. In Imielinski, T. and
Korth, H., editors, Mobile Computing, volume 353 of
The Kluwer International Series in Engineering and
Computer Science, pages 153–181. Springer US.
K
¨
opke, A., Swigulski, M., Wessel, K., Willkomm, D., Han-
eveld, P. T. K., Parker, T. E. V., Visser, O. W., Lichte,
H. S., and Valentin, S. (2008). Simulating wireless
and mobile networks in omnet++ the mixim vision.
CombiningtheSprayTechniquewithRoutestoImprovetheRoutingProcessinVANETS
589

In Proceedings of the 1st international conference
on Simulation tools and techniques for communica-
tions, networks and systems & workshops, Simutools
’08, pages 71:1–71:8, ICST, Brussels, Belgium, Bel-
gium. ICST (Institute for Computer Sciences, Social-
Informatics and Telecommunications Engineering).
Lee, K. and Gerla, M. (2010). Opportunistic vehicular rout-
ing. In 2010 European Wireless Conference (EW),
pages 873–880.
Leontiadis, I. and Mascolo, C. (2007). Geopps: Geograph-
ical opportunistic routing for vehicular networks. In
IEEE International Symposium on a World of Wire-
less, Mobile and Multimedia Networks (WoWMoM
2007), pages 1–6.
Li, F. and Wang, Y. (2007). Routing in vehicular ad hoc net-
works: A survey. IEEE Vehicular Technology Maga-
zine, 2(2):12–22.
Mauve, M., Widmer, J., and Hartenstein, H. (2001). A sur-
vey on position-based routing in mobile ad hoc net-
works. Network, IEEE, 15(6):30–39.
Perkins, C. and Royer, E. (1999). Ad-hoc on-demand dis-
tance vector routing. In Second IEEE Workshop on
Mobile Computing Systems and Applications (WM-
CSA), pages 90–100.
Silva, M. J. (2012). VeNeM: vehicular network mobility.
Spyropoulos, T., Psounis, K., and Raghavendra, C. (2008a).
Efficient routing in intermittently connected mobile
networks: The single-copy case. IEEE/ACM Trans-
actions on Networking, 16(1):63–76.
Spyropoulos, T., Psounis, K., and Raghavendra, C. S.
(2008b). Efficient routing in intermittently connected
mobile networks: the multiple-copy case. IEEE/ACM
Transactions on Networking, 16(1):77–90.
Taysi, Z. and Yavuz, A. (2012). Routing protocols for
geonet: A survey. IEEE Transactions on Intelligent
Transportation Systems, 13(2):939–954.
Tchakountio, F. and Ramanathan, R. (2001). Tracking
highly mobile endpoints. In Proceedings of the 4th
ACM international workshop on Wireless mobile mul-
timedia, WOWMOM ’01, pages 83–94, New York,
NY, USA. ACM.
Toor, Y., Muhlethaler, P., and Laouiti, A. (2008). Vehi-
cle ad hoc networks: applications and related techni-
cal issues. IEEE Communications Surveys Tutorials,
10(3):74–88.
Vahdat, A., Becker, D., et al. (2000). Epidemic routing for
partially connected ad hoc networks. Technical report,
Technical Report CS-200006, Duke University.
Varga, A. (1999). Using the omnet++ discrete event sim-
ulation system in education. IEEE Transactions on
Education, 42(4):11 pp.–.
Zhao, J. and Cao, G. (2008). Vadd: Vehicle-assisted data
delivery in vehicular ad hoc networks. IEEE Transac-
tions on Vehicular Technology, 57(3):1910–1922.
ICEIS2014-16thInternationalConferenceonEnterpriseInformationSystems
590
