
Knowledge Management Technology Implementation
Bridging the Gap between Theory and Practice
Saravanan Muthaiayh
Faculty of Management, Multimedia University, Jalan Multimedia, 63100 Cyberjaya, Selangor, Malaysia
Keywords: Knowledge Management, Knowledge Management Technologies, E-Knowledge Management.
Abstract: This paper presents methods employed for the teaching and learning of Knowledge Management
technologies classified under KM lifecycle i.e. knowledge identification, knowledge capture, knowledge
codification, knowledge storage, knowledge dissemination and sharing. The process was employed for
teaching of a Knowledge Management (KM) course called E-KM (Electronic Knowledge Management) in
Multimedia University (MMU), Cyberjaya, Malaysia. Given that textbooks were only available for
theoretical KM courses and that all teaching materials had to be created from scratch for this course, the
idea was to test if KM technologies can be successfully taught and be implemented in class to bridge the gap
between theory and practise. Empirical data provided in this paper validates that there was a significant
improvement in the learning and understanding amongst postgraduate students especially in appreciation of
knowledge codification, ontology design, schema classification, taxonomy construction, implementation
and assignment of rule generation for firing rules via reasoning engines. The process was tested over seven
cohorts totalling 300 students. Students who took this course never had any formal training before and this
was the first technical KM course for them in their postgraduate programme. Empirical data suggests that
the methods used were effective for all six classifications of KM lifecycle taught.
1 INTRODUCTION
KM is usually taught as a non-technical course
which covers softer issues that are behavioural. The
implementation of KM technologies to support KM
lifecycle i.e. knowledge identification, knowledge
capture, knowledge codification, knowledge storage,
knowledge dissemination and sharing are indeed
rare. Most curriculum taught today, does not prepare
students with the technical knowledge engineering
and design skills in relation to KM systems. The
question of how can one identify, capture, codify
and store knowledge in practice is still a gap that
exists in our curriculum today.
As part of our KM research, we wanted to
understand how this gap can be minimized in a
significant way so as to bridge the gap between
theory and practice of KM technology
implementation. The aim of this paper was to
evaluate the overall effectiveness of the process
methodology adopted and utilization of teaching
tools to minimize any gap that could have existed
between theory and practice of KM lifecycle
implementation. A parallel objective of this study
was to understand the strengths and weaknesses (if
any) of the process methodology that was designed
by the instructor in the effort towards improving the
content and providing a model that other institutions
could possibly adopt for the delivery of technical
KM courses. A wide variety of tools were adopted
for this study. Many were open source and free for
educational purposes. The tools that were used for
were: Protégé, Jess, SPARQL, SWOOGLE, UML
(Unified Modelling Language) and reasoning tools
such as: CLIPS, PAL, SWRL, Racer Pro and
Algernon. An experiment was carried out as to how
well students progressed from theory to practice. A
total of 300 postgraduate students were involved in
this study. The instructor taught the same E-KM
course for seven cohorts over three years with the
same process methodology, teaching design,
content, assessment, assignments, projects and
competency tests so as to maintain consistency and
eliminate biasness of the study. The rest of this
paper is organized as follows. Section 2 presents
KM lifecycle review of literature. Section 3 presents
the survey and section 4 presents preliminary
discussion as well as the hypothesis. Finally section
5 presents the analysis and findings.
393
Muthaiyah S..
Knowledge Management Technology Implementation - Bridging the Gap between Theory and Practice.
DOI: 10.5220/0005156403930399
In Proceedings of the International Conference on Knowledge Management and Information Sharing (KMIS-2014), pages 393-399
ISBN: 978-989-758-050-5
Copyright
c
2014 SCITEPRESS (Science and Technology Publications, Lda.)

2 LITERATURE REVIEW
Based on literature review using keyword search of
“KM lifecycle” from the Elsevier SDOS online
database, we found 10,014 articles on this topic.
This was done on June 1, 2014. After topic filtering,
only 73 articles covered the scope of this paper and
were KM technology specific and supported KM
lifecycle processes i.e. knowledge identification,
knowledge capture, knowledge codification,
knowledge storage, knowledge dissemination and
sharing. Several tools were introduced to support
KM technology implementation with regards to KM
lifecycle stages. In summary, based on the 73
articles mentioned earlier, we used Protégé for
knowledge identification, codification and capture
based on theory (Nonaka et al, 2001), (Wiig et al,
1997), (Fernandez-Breis, 2000), (Allsopp et al,
2002) and Wilkins et al (1997).
Jess (Java Expert Shell System) was applied in
the context of knowledge representation (Cauvin,
1996), Kim et al (2000) and knowledge capture
(Wielinga et al, 1997). SWOOGLE was used in the
context of search (Knight and Ma, 1997) and
indexing (Jiang el al, 1999). CLIPS and PAL
(Protégé Axiom Language), Algernon and SWRL
(Semantic Web Rule Language) assisted with
knowledge representation (Cauvin, 1996), Kim et al
(2000) and machine leaning (Zhong and Ohsuga,
1996). External reasoning engine (i.e. Racer Pro)
was applied for executing rules, checking
consistency and integrity in the Ontology
implemented. Description of each tool and how they
were used to meet the assignments assigned and
overall curriculum objectives are elaborated in the
following sections.
2.1 Protégé
Protégé is an open source platform-independent
ontology editor developed by Stanford University.
It’s a very useful tool for creating and editing
ontologies (Wiig et al, 1997), (Fernandez-Breis,
2000), (Allsopp et al, 2002) and Wilkins et al (1997)
and knowledge bases from scratch. The following
features in Protégé are reasons that make it
appropriate for Protégé to be used as a classroom
technology for E-KM:
a) Easy to use graphical user interface (GUI).
b) The ability to scale up with virtually no
performance degradation even if several
hundreds of frames are loaded into its
database all at the same time.
c) Several additional plug-ins can be easily
added into the Protégé framework as
components that perform reasoning,
matching, alignment and graphical
representation. To the best of my knowledge
I have not known any other tool that can
perform the same functions as Protégé does.
Students were first taught for several weeks
(about 20 face-to-face contact hours) on the concepts
and actual implementation process of a knowledge
base from scratch. The instructor used several
examples from the Protégé sample ontologies
available in this tool. The wine, newspaper and pizza
ontologies helped to provide a better understanding
of classes, sub classes, slots, inverse slots, instances,
data type definitions and relationships. In the first
assignment, a student was given three weeks to build
and implement ontology of their choice based on
principles taught in the face-to-face session. The
Protégé version used for assignment 1 was an earlier
version i.e. 3.4.1 so as not to confuse students with
OWL (Web Ontology Language) definitions which
they were not ready to comprehend. Assignments 2
and 3 were based on the 3.4.2 version.
2.2 JESS
Jess (Java Expert Shell System) is a rule engine and
scripting tool developed by Ernest Friedman-Hill at
Sandia Laboratories. Since Jess was always free for
educational purposes, it became an ideal choice to be
used in this course. Protégé provides a component
plug-in i.e. Jess Tab that can easily be configured for
executing Jess rules (Cauvin, 1996), within the
Protégé environment. Jess is an effective tool for
building intelligence into an existing knowledge
base. This can be done via an expert system rule
engine (Zhong and Ohsuga, 1996) that applies rules
on a collection of facts. Jess uses a special algorithm
i.e. Rete to match rule to given facts. This tool was
introduced to the students in subsequent meetings to
meet the requirements of assignments 2 and 3.
Students were first trained to use Jess for two
meetings before they could use it. Jess allows
forward and backward chaining and supports LISP
(LISt Processing) like syntax. Students were given
other options such as SWRL and PAL to implement
rules into their ontology if they did not want to use
Jess for any reason. An example of SWRL Jess Tab
is shown below.
2.3 SPARQL
SPARQL (SPARQLProtocol and RDF Query
KMIS2014-InternationalConferenceonKnowledgeManagementandInformationSharing
394

Language) is an RDF (Resource Description
Framework) query language which became an
official W3C recommendation. It allows students to
write queries for the following purposes i.e.
SELECT query, CONSTRUCT query, ASK query
and DESCRIBE query (Knight and Ma, 1997). This
tool was introduced to the students to meet the
requirements of assignment 3.
2.4 SWOOGLE
SWOOGLE is a Semantic Web search engine
developed and hosted by the eBiquity group at the
University of Maryland, Baltimore County (UMBC).
The purpose for the introduction of SWOOGLE is to
give an appreciation of how queries can be
processed across ontologies with the RDF query
language which incorporates SELECT query,
CONSTRUCT query, ASK query and DESCRIBE
query. This tool was introduced to the students to
meet the requirements of assignment 3.
2.5 CLIPS
CLIPS (C Language Integrated Production System)
is a public domain software tool for building expert
systems. CLIPS manages rules and facts like other
expert system languages. This tool was introduced to
the students to meet the requirements of assignment
3.
2.6 PAL
PAL (Protégé Axiom Language) is a tool for
implementing constraints or business rules for
knowledge bases. The PAL component plug-in is
easily configured for executing within the Protégé
environment and is available as a component as
well. It is a constraint and query language as it can
enforce semantics as well as search for instances that
satisfy certain relationships. PAL constraint
elements include constraint names, constraint
descriptions, range of constraints and constraint
statements (Zhong and Ohsuga, 1996). EZPAL is
also a PAL tool authored by Johnson Hou which
uses fill-in-the blanks approach with the aid of a
template.pprj file. It is quite easy to use and deploys
rule constraints. This tool was also introduced to
students to meet the requirements of assignment 3.
2.7 SWRL
SWRL (Semantic Web Rule Language) combines
OWL and RuleML (rule mark-up language) based
on OWL DL (description logic) using Horn-like
rules to reason (Zhong and Ohsuga, 1996) about
OWL classes. Students were taught how to compose
rules for knowledge bases. This tool was introduced
to students to meet the requirements of assignment
3.
2.8 Racer Pro
Racer Pro (Reasoned ABox and concept Expression
Reasoner Professional) is an interactive reasoning
engine that uses the TCP/IP network interface to
connect to one or more RacerPro servers. It was
developed in Germany and authored by the Racer
team. Students were taught how to use Race Pro to
load knowledge bases, switch between taxonomies,
inspect instances, visualize A-Boxes and T-Boxes
and manipulate the server (Zhong and Ohsuga,
1996). A total of 10 hours face-to-face time was
allocated for this purpose. This tool was introduced
to students to meet the requirements of assignment
3.
2.9 Algernon
Algernon was authored by Michael Hewitt. The
Algernon rule based system is implemented in Java
and is interfaced with Protégé. It supports forward
and backward chaining rules much like CLIPS and
Jess which is needed for frame-based knowledge
bases. This tool was introduced to students to meet
the requirements of assignment 3.
3 MATERIALS AND METHOD
This study was purely exploratory, not much was
known about how to evaluate the effectiveness of
bridging the knowledge gap of KM technology
implementation, especially for the KM domain.
Since not much was known and information was
scarce on this research topic even in developed
countries, thus the study was conducted. For the
purpose of this study, primary source of data
gathering of data, an online questionnaire was setup
and students were instructed to answer the questions
and submit their responses online. The survey was
divided into two sections i.e. section A and B. In the
section A of the survey, respondents had to answer a
total of thirteen questions with options for selection
and one open ended question for suggestions as to
how to improve the E-KM course in the future. In
section B, the attitude and perception of the students
was examined. Specifically, this research was aimed
KnowledgeManagementTechnologyImplementation-BridgingtheGapbetweenTheoryandPractice
395
at addressing the objectives below:
i. To what extent have the tools assisted in
the end to end KM lifecycle
implementation?
ii. How did the process methodology produce
technically sound KM knowledge among
postgraduate students?
iii. What is the level of satisfaction of the
students after attending the fourteen week
long semester especially in mastering
technical tools for KM?
iv. What is the level of effectiveness of the E-
KM teaching and learning materials (i.e.
hand-outs, notes, slides, online courseware
and tutorials)?
v. What is the level of effectiveness
of assignment 1 (ontology design) in terms
of acquiring knowledge of designing
ontologies from scratch?
vi. What is the level of effectiveness
ofassignment 2 (understanding taxonomy
and ontology implementation design)?
vii. What is the level of effectiveness
ofassignment 3 (implementing business
rules in ontologies)?
4 HYPOTHESIS AND METRICS
The experiment for the study was aimed at
examining the following hypotheses (see table 1).
The focus group of this study was 300 carefully
selected postgraduate students representing weak,
average and good students as well as those who
represented all six semester groups over three years.
All 300 respondents answered the survey which
gives it a 100% response rate.
For the purpose of analysis the data set of 300
students were divided into two groups of 150
students each i.e. those who took the earlier
curriculum and those who took the modified new
curriculum. All hypothesis were examined first with
a t-test analysis and showed significant results with
(p>0.05). Hypothesis 1 (H1) test resulted where 150
postgraduate students who took the E-KM course in
the last three semesters with the new instructor
designed E-KM content, assignments and projects
performed better than the 150 students of the
postgraduate students who took the E-KM course in
the first three semesters, i.e. a 93% improvement.
Hypothesis 2 (H2) test resulted in 92% of students
who took the new curriculum made fewer mistakes
during the development of a Knowledge Base (KB)
after completing all three assignments. Lastly,
Hypothesis 3 (H3) test resulted in 92% of students
who took the new curriculum were 95% more
competent in writing business rules in a very short
span of time compared to those who did not.
Table 1: Research Hypothesis.
Hypothesis Hypothesis Statement
H1
Students who went through new E-
KM curriculum did better in the exam
compared to those did not
H2
Students made fewer mistakes during
the development of a Knowledge
Base (KB) after completing all three
assignments
H3
Students who completed all lessons
on were more competent in writing
business rules in a very short span of
time
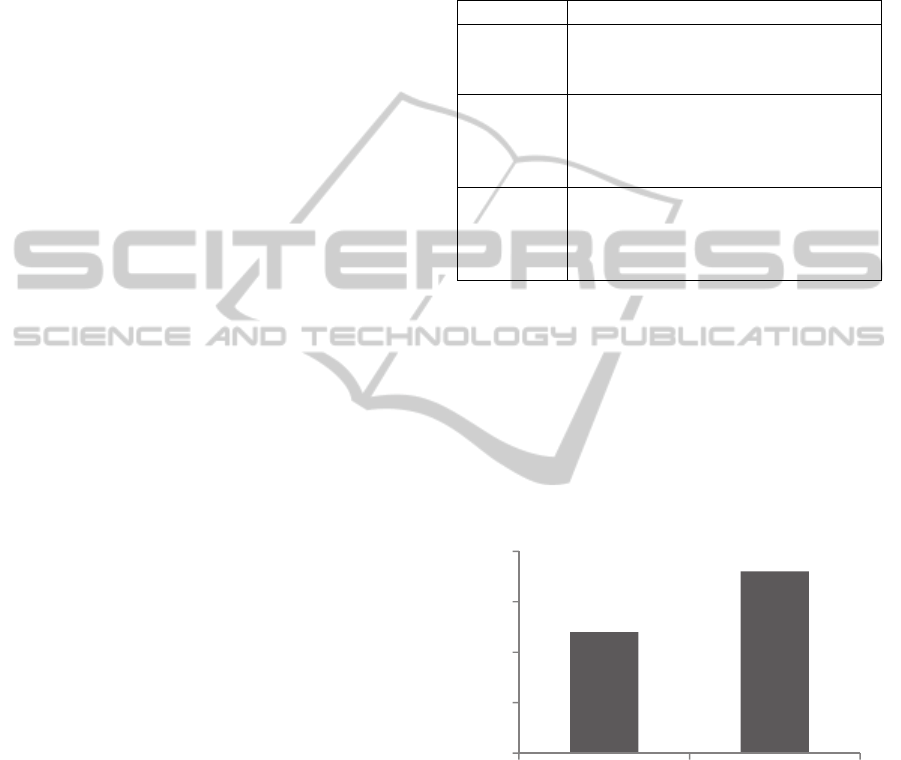
The first and second question were on demographics
i.e. age and gender respectively. From a total of 300
responses 180 were females and 120 were male.
Thus, females made up about 60% of the population
and males made up 40%. As for age, 1 respondent
was between 15 to 20 years old (3.8%), about 7
respondents were between 21 to 25 years old
(26.9%), 15 of them between 26 to 30 years old
(57.7%) and 3 were between 31 to 35 years old
(11.5%). The following charts depict this:
Figure 1: Response by gender (Total).
The third question was “how many times the student
had taken the E-KM course?”. Out of 300 responses,
288 students were taking the course for the first time
i.e. resulting in 96% who were beginners. The fourth
question was on “what was the student’s level of
satisfaction about the topics that were covered in the
E-KM class?” and the responses were as follows:
50% (150 students) were strongly satisfied, 45%
(135 students) were somewhat satisfied, 3.33% (10
0
50
100
150
200
Male Female
KMIS2014-InternationalConferenceonKnowledgeManagementandInformationSharing
396
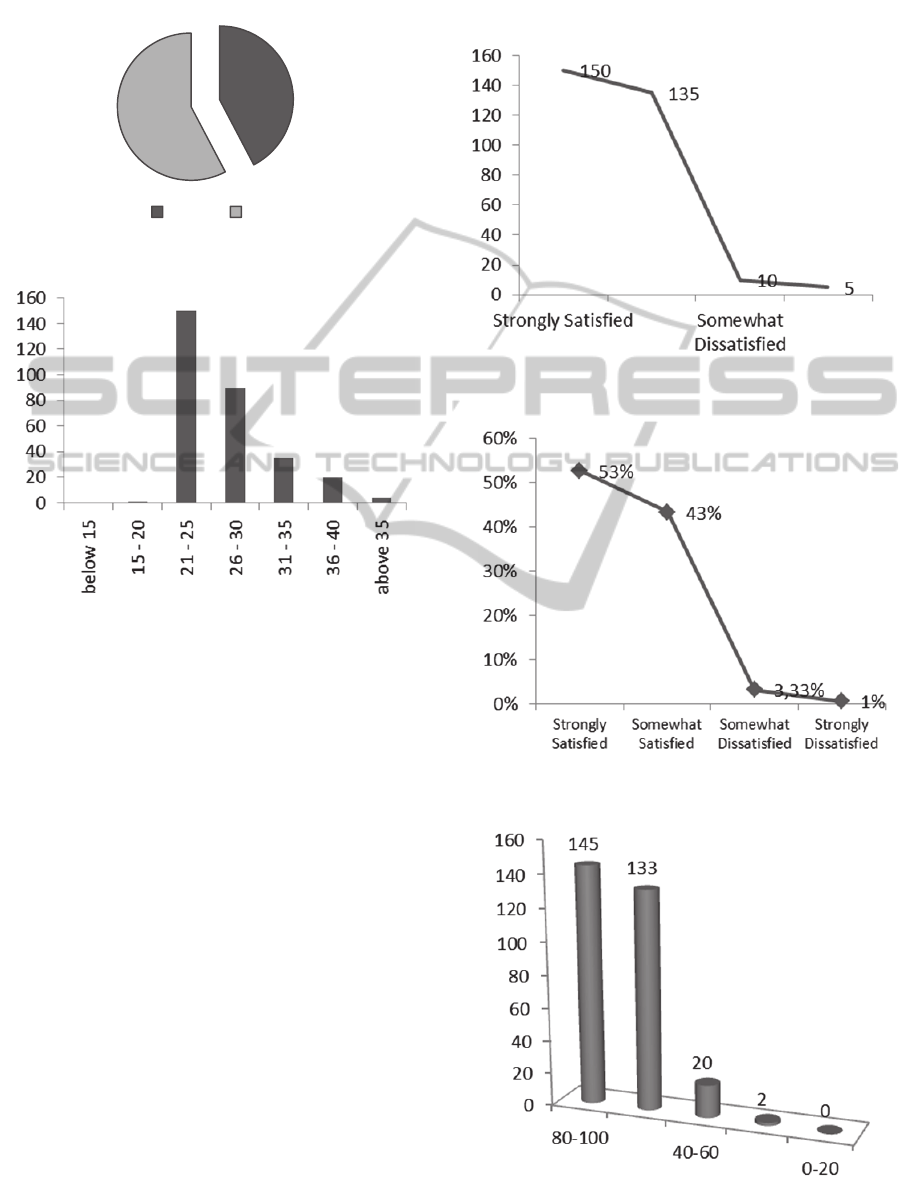
students) were somewhat dissatisfied and 1.7% (5
students) were strongly dissatisfied.
Figure 2: Response by gender (%).
Figure 3: Response by age.
In the fifth question, “what is your level of
satisfaction about materials (i.e. tools, notes, hand
outs, tutorials and notes) that were used in E-KM
class?” and the responses were as follows: 53%
respondent answered strongly satisfied, 43% were
somewhat satisfied, 3.33% were somewhat
dissatisfied and 1% were strongly dissatisfied. In
summary, 96% were satisfied with the materials
used. The sixth question was on “in your opinion
what do you think is the level of effectiveness of
assignment 1 (ontology design) in terms of acquiring
knowledge of designing an ontology from scratch?”
and the responses were as follows: 57.7%
respondents answered strongly effective, 34.6%
answered somewhat effective, none responded to
somewhat ineffective and 7.7% responded as
ineffective. In summary, 92.3% were satisfied with
the assignment 1
In the seventh question, “what do you rank as
effectiveness of assignment 2 (understanding
taxonomy and ontology implementation design)?”
and the responses were as follows: 48.3% (145
students) answered (80-100), 44.3% (133 students)
responded (60-80), and 6.7% (20 students) respon-
ded (40-60), 0.7% (2 students) answered (20-40) and
0% (none) answered as (0-20). In summary the
majority of students responded favourably to
Figure 4: Level of satisfaction of topics covered in E-KM
class.
Figure 5: Level of satisfaction of materials used in the E-
KM class.
Figure 6: Effectiveness ranking of assignment 2.
40%
60%
Male Female
KnowledgeManagementTechnologyImplementation-BridgingtheGapbetweenTheoryandPractice
397
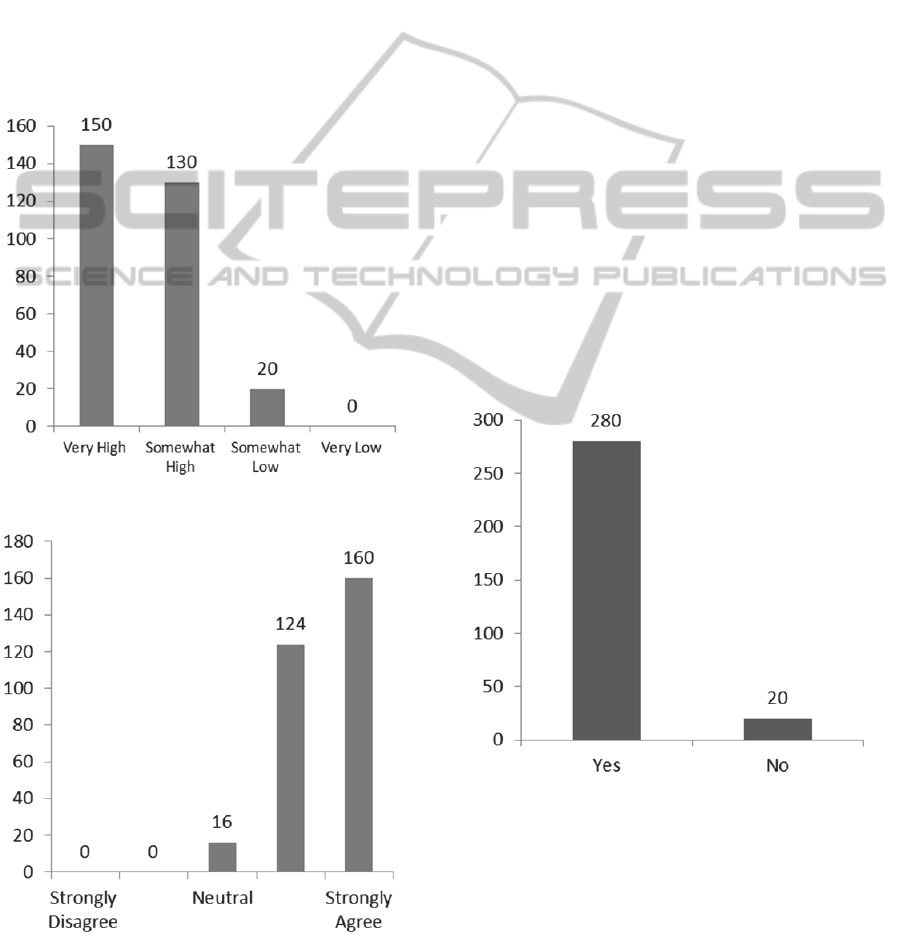
assignment 2. In the eighth question, “how do you
rank the level of effectiveness of assignment
3 (implementing business rules in ontologies) in
helping you to assign rules for your ontology?” the
responses were as follows: 50% answered very high,
38.5% responded somewhat high, 43.3% responded
somewhat low and 6.7% responded very low. In
summary, the majority of students responded
favourably to assignment 3. The remaining students
who responded unfavourably to this question really
did not have any prior understanding in one more of
these areas: description logic, programming,
databases, query writing, software design and
systems development at the undergraduate level.
Figure 7: Effectiveness ranking of assignment 3.
Figure 8: Instructor’s knowledge to teach E-KM.
In the tenth question, “do you think your knowledge
has increased after you have taken the E-KM
module?” the responses were as follows: 96.2%
answered “yes” and only 3.8% responded “no”. In
the tenth question, “do you think your knowledge
has increased after you have taken the E-KM
module?” the responses were as follows: 96%
answered “yes” and only 4% responded “no”. As a
result the success of any hard KM topics depends
strongly on the proper selection of students who
possess these skills or foundation courses should be
introduced in the early semesters to prepare the
students before they move on towards higher level
courses at the later stage of the programme. In the
ninth question, “do you think that the instructor’s
knowledge is sufficient to teach the E-KM class?”
the responses were as follows: 53% answered
strongly agree, 41% responded agree, 5% were
neutral and nobody (0%) disagreed and 0%
responded strongly disagree. In summary, the
majority of students almost all the students
responded favourably to this question. In the
eleventh question, “was the E-KM course effective
in increasing your knowledge in the KM domain?”
the responses were: 280 answered “yes” and only 20
only answered “no . In summary, more than 96% of
the students responded favourably to this question.
Figure 9: Has your knowledge increased after the E-KM
module.
5 CONCLUSIONS
In conclusion, the contribution of this paper is
twofold. Firstly, it highlights the effectiveness of
bridging KM technology implementation in a
postgraduate class. Secondly the effectiveness of
KMIS2014-InternationalConferenceonKnowledgeManagementandInformationSharing
398

teaching tools for the teaching and learning of E-KM
such as Protégé, Jess, SPARQL, SWOOGLE, UML,
CLIPS, PAL, SWRL, Racer Pro and Algernon. The
study also highlights the effectiveness of the
instructor’s methods in teaching of this course
including designing the curriculum aided in the
closure of the gap between theory based models and
actual knowledge engineering. Qualitative and
quantitative data obtained from the survey shows
that a majority of the students responded favourably
to almost all questions as discussed earlier. As such,
results of this experiment can be used by university
authorities to confirm effective teaching pedagogies
for teaching of technical courses at the postgraduate
or even undergraduate levels.
REFERENCES
Allsopp, D. J. ,Harrison, A., and Sheppard, C.(2002). A
database architecture for reusable CommonKADS
agent specification components. Knowledge-based
Systems, 15, 275-283.
Cauvin, S.(1996). Dynamic application of action plans in
the Alexip knowledge-based system. Control
Engineering Practice, 4(1), 99-104.
Fernandez-Breis, J.T., and Martinez-Bejar, R. (2000). A
cooperative tool for facilitating knowledge
management. Expert Systems With Applications, 18,
315-330.
Jiang., Berry, M.W., Donato, J. M., Ostrouchov, G., and
Grady, N.W (1999). Mining consumer product data
via latent semantic indexing. Intelligent Data Analysis,
3,377-398
Knight, B., and Ma, J.. (1997). Temporal management
using relative relative time in knowledge-based
process control. Engineering Applications Artificial
Inteeligence, 10(3), 269-280.
Nonaka, I., Reinmoller, P., and Toyama, R. (2001).
Integrated information technology systems for
knowledge creation. Handbook of Organizational
Learning and Knowledge, Dierkes, M. et al. (Eds.),
Oxford University Press, Oxford, 827-48
Wilkins, J.,Wegen, B., and Hoog, R.(1997).Understanding
and valuing knowledge assets: overview and method.
Expert Systems With Applications, 13(1), 55-72
Wiig, K.M., Hoog, R., and Spex, R. (1997). Supporting
knowledge management: a selection of methods and
techniques, Expert Systems With Applications, 13(1),
15-27
Wielinga, B., Sandberg, J., and Schreiber, G (1997).
Methods and techniques for knowledge management:
what has knowledge engineering to offer? Expert
Systems With Applications, 13(1), 73-84.
Zhong, N., and Ohsuga, S. (1996). System for managing
and refining structural characteristics discovered from
databases. Knowledge-based Systems, 9, 267-279.
KnowledgeManagementTechnologyImplementation-BridgingtheGapbetweenTheoryandPractice
399
