
Secure Authentication Solution for Cloud-based Smart City
Surveillance System
Yosra Ben Dhief, Yacine Djemaiel, Slim Rekhis and Noureddine Boudriga
Communication Networks and Security Research Lab, University of Carthage, Tunisia
Keywords: Smart City, Physical Unclonable Functions, Sensor Authentication, Cloud, Virtual Sensor.
Abstract: With the emergence of physical monitoring systems and their use for smart cities, new security concerns
arise due to the sensitive nature of the data produced by the sensor devices of these systems, which makes
the smart city applications a prime target for cyber attacks. However, securing these devices is very
challenging given the fact that they are resource-constrained, and deployed in physically unsecured
environments. In this paper, we propose a secure scheme for cloud-based smart city surveillance system
providing a lightweight sensor authentication protocol based on Physical Unclonable Functions and
securing the exchanged data through the different components of this infrastructure.
1 INTRODUCTION
With the emergence of smart cities over the world,
there is a great need for services that ensure the
protection of citizens and cities' assets. In fact, these
services run in a dynamic environment containing
sets of physical supervisory systems, which in turn
can be managed by different providers to serve
several actors. However, the inherent complexities
of such environments raise several challenges for the
implementation of smart city applications. These
challenges are mostly caused by the massive amount
of data that are generated by the sensors. The cloud
technology presents an attractive solution to face this
challenge since it provides powerful computing
resources and elastic storage capacities (Schleicher,
et al., 2016).
Despite the benefits of the cloud, the smart city
applications are still suffering from security threats
given the fact that the sensitive nature of sensor data
makes them a prime target for cyber attacks.
Therefore, implementing security solutions is very
crucial to ensure efficient and reliable services for
smart cities. In particular, authentication and
encryption services are required to provide both
device and data exchange security. However, the
sensor devices are endowed with limited processing,
memory, and energy resources which make them
unable to support complex security mechanisms
(Wallrabenstein, 2016). In this context, several
works considered Elliptic Curve Cryptography
(ECC) as an effective solution for resource-
constrained devices that requires lower
computational and storage capabilities. In (Kalra &
Sood, 2015), the authors presented an ECC based
mutual authentication protocol for secure
communication between embedded devices and
cloud servers. In (Hu, et al., 2017), the authors
proposed a secure cloud-based architecture for
health monitoring using IoT devices which achieves
authentication and data security using ECC digital
signature.
However, the aforecited schemes call for the
storage of the secret key inside the Non-Volatile
Memory (NVM) of devices, while the sensors can be
deployed in a hostile environment and be the target
of many physical attacks. To thwart these attacks,
the sensor devices can be equipped with tamper
resistant hardware. However, theses solutions can be
too expensive to be practical in many smart city
applications. Several researches were proposed (Lao,
et al., 2017), (Wallrabenstein, 2015), (Aman, et al.,
2017) and (Wallrabenstein, 2016) focusing on the
use of a low-cost solutions to protect sensor devices
from tampering. These solutions are based on the
use of a Physical Unclonable Function (PUF) which
consists in an on-demand extraction of secrets from
complex properties of hardware, rather than storing
them in a NVM. In fact, a PUF produces to a given
input (or challenge) an output (or response) which is
unique due to inter-chip variation that is difficult or
impossible to model. The challenge and response
502
Dhief, Y., Djemaiel, Y., Rekhis, S. and Boudriga, N.
Secure Authentication Solution for Cloud-based Smart City Surveillance System.
DOI: 10.5220/0006867005020507
In Proceedings of the 15th International Joint Conference on e-Business and Telecommunications (ICETE 2018) - Volume 2: SECRYPT, pages 502-507
ISBN: 978-989-758-319-3
Copyright © 2018 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

pairs (CRPs) of a PUF are used to generate chip-
unique signatures for an authentication system (Lao,
et al., 2017).
In this work, we propose a security scheme for
cloud-based smart city surveillance architecture
leveraging an extension of the PUF-based
authentication system proposed in (Wallrabenstein,
2016). The architecture was presented by our work
in (Yosra, et al., 2018) that provides global
monitoring services () for smart cities built on
virtual sensors (), which are created by different
brokers. A provides an indirect measurements by
processing data collected by physical sensors ()
deployed by different physical supervisory systems
(). The main goal of this paper is to design a
lightweight scheme involving more than two actors
(i.e., sensor devices, broker and provider) to perform
secure authentication and key management for
sensors in cloud-based environment, in addition to
guaranteeing sensors’ anonymity. The proposal
exploits, firstly, the ECC to enable the sensor device
to generate pair of asymmetric key and the PUF
hardware to secure the private key from tampering,
and then the Zero knowledge Proof (ZKP) to prove
the authenticity of the generated public key. The
generated asymmetric keys are used to encrypt and
sign the exchanged data.
The main contribution of this paper is four fold:
) A lightweight authentication scheme for sensor
devices that preserves their anonymity in cloud
environment; ) A low cost tamper resistance
solution for sensor devices based on the use of
unclonable function; ) The proof of the real
involvement of sensors in data collection; and )
The integrity and confidentiality of the exchanged
data in a cloud sensor based architecture.
The remaining part of the paper is organized as
follows. Section discusses the security
requirements for cloud-based smart city surveillance
system. Section details the proposed architecture
and the functions ensured by its components.
Section presents our proposed authentication and
key distribution scheme. The next section provides a
security analysis and validation of the proposed
scheme. Section concludes the paper.
2 SECURITY REQUREMENTS
FOR CLOUD-BASED SMART
CITY SURVEILLANCE
In this section, we detail the security requirement to
design sensor authentication scheme in cloud-based
smart city surveillance system.
Anonymous Sensor Authentication. The
virtualization enables GMS to make use of different
without knowing their identity. However, it is
required to prove that the used data are collected by
a trusted sensor. Thus, sensor devices should be
authenticated anonymously.
Low Computational and Energy Operation. The
computation power and the battery capacity of
sensor are limited and may be insufficient for the
processing of security algorithms. Therefore, a
security scheme for sensor devices should involve
low resource and energy consumption.
Tamper Resistance. Given the fact that the sensor
devices can be deployed in remote unattended
places, security solution should be able to detect any
attempt to tamper with them.
Freshness and Integrity of Sensing Data. The
surveillance applications requires firstly, the
freshness of the used data to guarantee that it is very
much recent and no old data have been replayed.
Secondly, the integrity of the used data to guarantee
that it has not been altered in transit.
3 CLOUD-BASED SMART CITY
SURVEILLANCE SYSTEM
ARHITECTURE
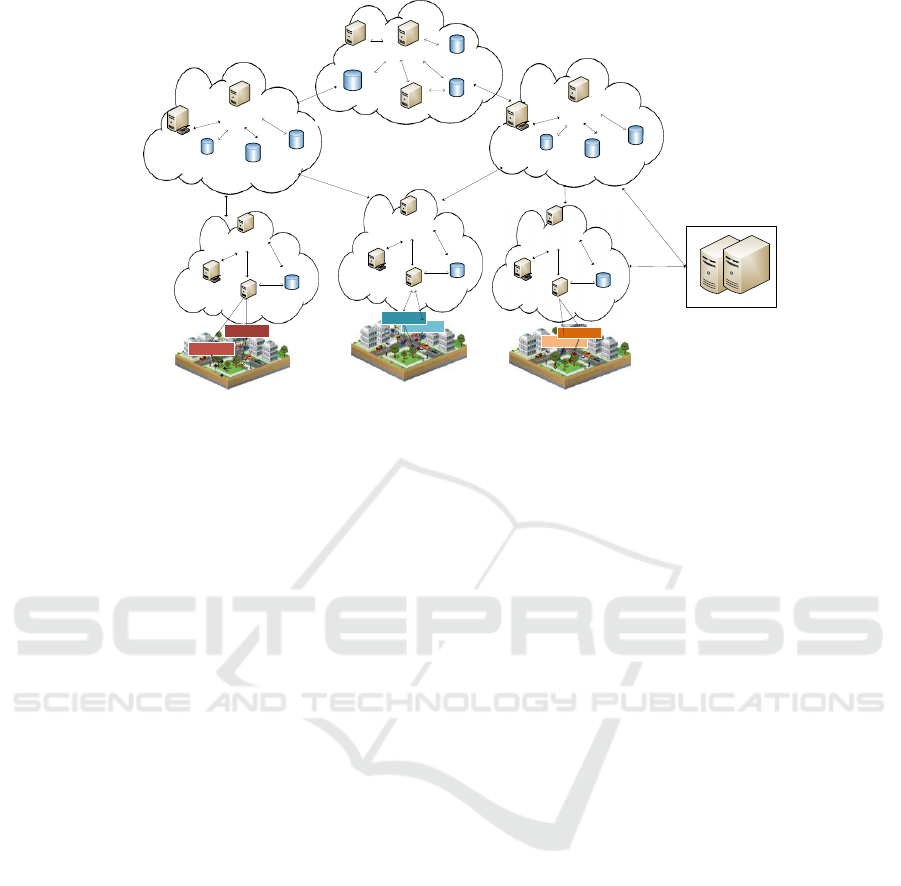
The proposed cloud-based smart city surveillance
architecture is composed of three actors: ) Physical
Supervisory System () /provider ) A broker of
and ) A Logical Supervisory System (). An
architectural map of the proposed architecture is
shown in Figure . In the following we detail the
role of each actor.
Physical Supervisory System / Provider
A typical is a centralized system that ensures
real-time monitoring of an infrastructure process
using a set of heterogeneous sensors. The acts
as a provider that allows the reuse of its by
different external systems with different
configurations. It also interacts with a trusted
Authentication System () to enroll and to
authenticate its . The is composed of
enrollment servers that ensure the authentication of
and the generation of shared keys to be used to
secure the data exchange.
Secure Authentication Solution for Cloud-based Smart City Surveillance System
503
Broker of virtual sensors
Local
directory
Control
server
Local
sensing data
repository
Provisoning
server
Broker of virtual sensors
Logical Supervisory System
Proxy server
Front end
server
Template
repository
PSS/Provider
Control center
PSS/Provider
Controller
2
Controller
1
Controller
1
Controller
1
Services data
repository
Active services
database
Controller
2
Physical
sensors
Local
directory
Control
server
Local
sensing data
repository
Controller
2
Proxy Provisoning
server
Brokering
directory
Sensing data
repository
Brokering
database
Active VS
database
Provisoning
server
Proxy Provisoning
server
Brokering
directory
Sensing data
repository
Brokering
database
Active VS
database
Local
directory
Control
server
Local
sensing data
repository
Provisoning
server
PSS/Provider
Enrollment servers
Authentciation system
Figure 1: Cloud-based smart city surveillance architecture.
Broker of Virtual Sensors
The broker of is the intermediary between the
/providers and the . According to the request
of , the broker selects providers to use their
with the appropriate configurations. It creates a
enabling the processing of the data generated by
the selected . The broker also maintains an
archive of the sensed data collected from the
different PSSs.
Logical Supervisory System
The provides s for heterogeneous and
distributed infrastructures making the use of
provided by different brokers of . The supervision
ensured by this is based on the analysis and the
processing of data produced by a set of .
4 SECURE DATA EXCHANGE IN
CLOUD-BASED SMART CITY
SYSTEM
This section describes the proposed PUF-based
authentication and key distribution scheme for
cloud-based smart city surveillance, in addition to an
overview about the PUFs concept.
4.1 Physical Unclonable Function
Overview
The PUF performs a mapping from a challenge to a
unique response which depends on the unique
characteristics of the physical hardware on which it
is executed. Several authentication schemes have
been proposed based on the PUF (Aman, et al.,
2017). They use the fact that only a user and a
sensor device know a CRP. To authenticate a sensor,
the user has to tell the device in clear his challenge
so that it can get the response. Thus a man in the
middle can hear the challenge, get the response from
the PUF device and use it to spoof the PUF device.
The Controlled PUF (Dijk, et al., 2008) (CPUF),
which is a combination of a PUF and an Integrated
Circuit (IC) bound together such that an attacker has
no access to the communication between the PUF
and the IC. Any attempt to force them apart will
damage the PUF. The IC completely governs the
PUF input and output and reveals only indirect
information derived from the output.
4.2 PUF-based Authentication and Key
Distribution Scheme
The proposed scheme is based on ECC which is a
suitable solution for resource-constrained sensors.
We define an elliptic curve over a field
of
prime order , and a base point of order , where
. The proposed scheme is also based on
a CPUF implemented by the used sensor devices and
a hash function denoted by . We assume that the
is a trusted entity that authenticates the actors of
SECRYPT 2018 - International Conference on Security and Cryptography
504
our architecture and that generates the secret keys to
be used during the data exchange. In addition, each
provider has a pair of keys
generated
by the and to be used during the exchange of
data with sensors.
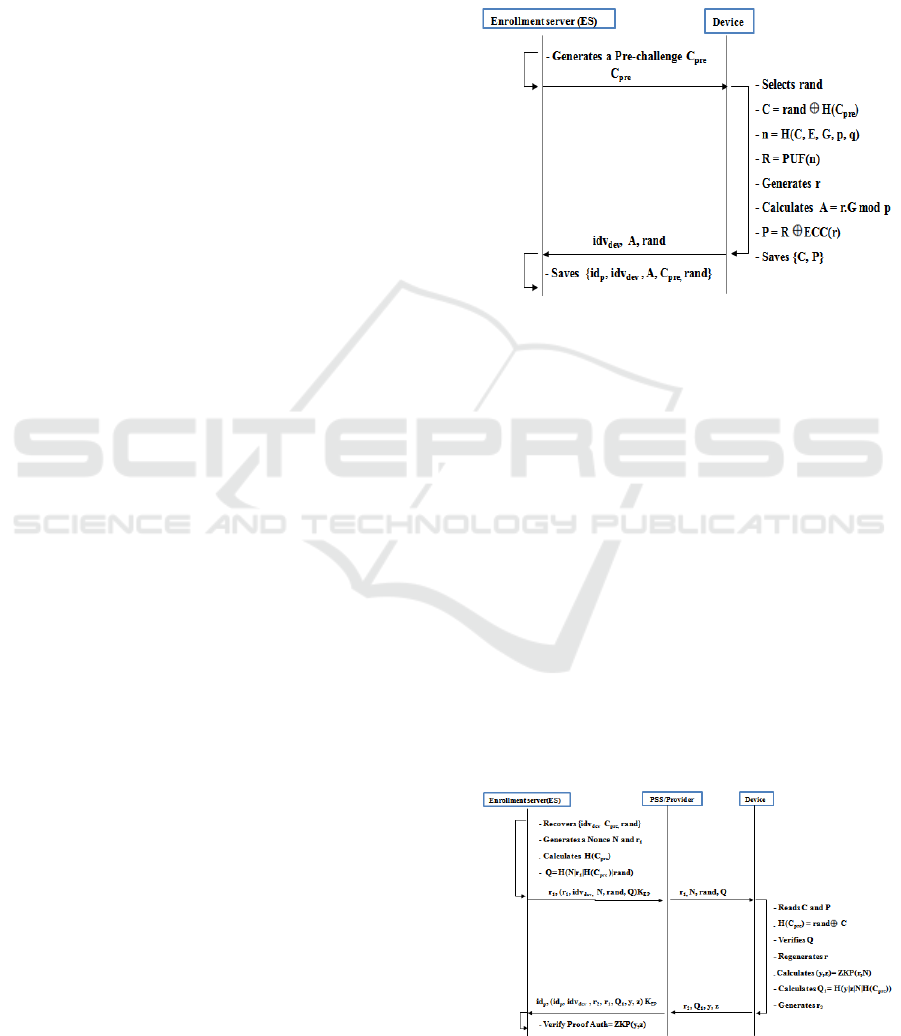
4.2.1 Enrollment Phase
This phase is executed in a secure environment by
the . The sensors are pre-configured with a virtual
identity
. Once the enrollment phase is
finished, the device deletes
from its memory.
Figure shows the steps of this phase, which are
detailed in the following:
1. The generates a Pre-challenge
and sends
(
) to the sensor device.
2. The sensor selects rand from
and calculates a
challenge
and
which is used as input to the
PUF to generate the response . Next, it
generates a public key , where
the private key is selected from
It applies an
Error Correction Code (ECC) over the private
key, and blinds this value with , in a way that
the final helper value leaks
no information about the private key. The device
stores and in the NVM, and sends to the
the public key , the rand and its
.
3. The ES saves the public key and rand with the
correspondent
and the identity of its
provider
.
4.2.2 Sensor Authentication Phase
The device authentication is performed through a
ZKP protocol. In this phase, the verifies whether
the sensor can re-generate the private key involving
its PUF. Figure shows the steps of this phase,
which are detailed in the following:
1. The recovers the relevant public key ,
and using
. It generates a nonce
and
and calculates
and
. Next, the ES
encrypts
,
, , and using a
secret key
, which is shared between the ES
and the provider that owns the sensor device.
2. The PSS decrypts the received message with
and transfers to the relevant device
, ,
and .
3. The device reads from its memory and . It
calculates
and verifies
the received . This enables the sensor device
to authenticate the , given that it is the only
entity that knows the
and . Then, the
device calculates and gets
its correspondent response from its PUF. It
re-generates its private key using an error
decoding, It also calculates
its public key .
Figure 2: Enrollment phase.
4. After re-generating the asymmetric key pair, the
device selects from
and calculates
. Then, It calculates
and . It also
calculates
and
generates
. Finally, it sends
to the
/Provider.
5. The adds its identity
and the
to
the received message and encrypts them with
. It adds to the encrypted message in clear
its
and sends them to the .
6. Using
, the retrieves
and decrypts
the message. Then, it verifies
and calculates
) and
. The compares and . If they
are equal, it sends an acknowledge to the
provider. Else, it refuses to authenticate the
device.
Figure 3: Device authentication phase.
Secure Authentication Solution for Cloud-based Smart City Surveillance System
505
Once a sensor is authenticated, the parameters
used for sensor authentication can be renewed.
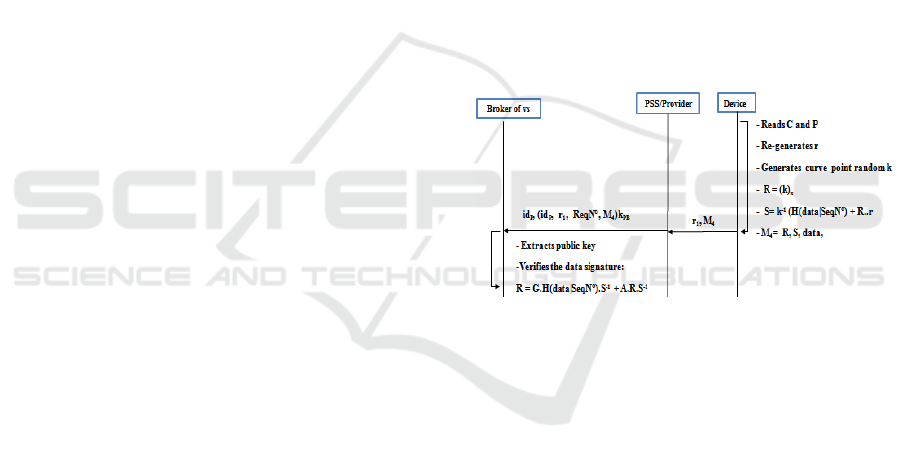
4.2.3 Data Transfer Phase
The data collected by a sensor are transferred to the
broker without revealing the sensor identity.
However, the broker should make sure that the
received data are collected from an involved and an
authentic sensor. To this end, we proposed a
protocol that enables a broker to authenticate a
sensor through a digital signature without revealing
its identity. The sensor signs data with its private
key that it re-generates using its PUF. In the other
hand, the broker verifies the sensor's signature using
a public key provided by the . The validity of
the key pair ( ) is verified by the ES through the
sensor authentication described above.
The proposed signature protocol is based on the
ElGamal digital signature algorithm described by
(Wallrabenstein, 2016). Figure shows the steps of
this phase, which are detailed in the following:
1. The device reads from its memory and
and re-generates its private key and public
as described at step in the authentication phase.
It selects a random curve point from
. Next, it sets
where
denotes
the coordinate of the point . It also sets
where
is a sequence number which is initially
synchronized between the broker and the device.
The device creates the message
starting from
and data. It encypts the message
and a
random value
using the public key
of the
provider. It adds to the encrypted message
in
clear and sends them to its provider.
2. The provider decrypts the message its
and
adds and its identity
to the decrypted
message. Then, it encrypts them with the secret
key
shared with the concerned broker. It
also adds in clear its identity
. Finally, it
sends them to the broker.
3. Using
, it selects the appropriate
and
decrypts the message. Then, it retrieves the
public key using
and verifies the
signature by calculating
5 SECURITY ANALYSIS AND
SYSTEM VALIDATION
In this section, we will analyze and validate the
robustness of the proposed scheme against a set of
attacks.
Low Cost Tamper Resistant. The device uses
and with its PUF to regenerate its private
key instead of stored it in the NVM. Hence,
is physically obfuscated and only exists in
memory when needed for a cryptographic
operation. Besides, we use a CPUF that makes
an inseparable link between an IC and a PUF’s
input-output mapping, an attacker that attempts
to probe the circuit will irreversibly modify the
physical variations in the IC, which in turn
changes the PUF mapping and prevents
regeneration of the private key. Thus, PUF
circuits are a low-cost solution for tamper
resistance to resource-constrained devices.
Figure 4: PUF-based signature protocol.
Sensor Anonymous Authentication. The
broker authenticates a sensor device through the
verification of its signature using the public key
sent by the . is generated based on a
private key which is only known by the sensor
device given that the regeneration of requires
the involvement of its unique function PUF.
Based on this fact, the authenticates the
sensor using ZKP protocol. Besides, the sensor
device is identified by a virtual identity
which is only known by the provider and the
enrollment server. Thus, the broker
authenticates the sensor device without knowing
its identity and its physical specifications.
Resistance to Replay Attack. An attacker can
replay previous messages exchanged by the
sensor device to the broker. But, the broker can
detect the invalidity of the message because
messages are signed using the private key that
SECRYPT 2018 - International Conference on Security and Cryptography
506

can be generated only by e sensor using its
PUF and contain new sequence number
generated for new message. Besides, to prevent
replay attacks on the message exchanged
between actors, new nonces are generated to
guarantee the freshness of each session.
Resistance to Impersonation Attack. The
proposed scheme implements ZKP protocol to
authenticate a sensor device which allows the
to verify that the sensor knows the private
key without disclosing it. A sensor can prove
that it knows the correct by re-generating it
involving its implemented PUF. Given that the
PUF is unique for each device, an adversary
cannot re-generate to impersonate the .
Resistance to Man In the Middle Attack. an
attacker cannot perform a MITM attack in the
communication between the and a sensor
because at each time each one checks that the
other knows the and the
used to generate the challenge
saved by the sensor. An attacker is not also able
to decrypt several messages because they are
encrypted by a secret key already calculated by
the . On top of that, our scheme is based on
CPUF which prevents an attacker, even though
he determined the challenge saved by the
sensor, to probe the device and get the response.
6 CONCLUSION
We proposed in this paper a secure authentication
scheme for cloud-based smart city surveillance
system. The proposal solution exploits, firstly, ECC
to enable the sensor device to generate a pair of
asymmetric key and the PUF hardware to secure the
private key from tampering, and then ZKP to prove
the authenticity of the generated public key.
Moreover, the generated asymmetric keys are
leveraged to provide encryption and signature
mechanism to protect exchanged data with sensors
while coping with their resources-limitations. In
addition, our proposed solution enables to
authenticate anonymously a sensor in the cloud
environment. In a future work, we will extend our
proposed scheme to support the authentication of
virtual sensors created starting from a dynamic set of
mobile and heterogeneous sensor devices.
REFERENCES
Aman, M. N., Chua, K. C. & Sikdar, B., 2017. Secure
Data Provenance for the Internet of Things. In
Proceedings of the 3rd ACM International Workshop
on IoT Privacy, Trust, and Security, IoTPTS'17, pp.
11-14, Abu Dhabi, United Arab Emirates.
Dijk, B. G. a. M. V. et al., 2008. Controlled Physical
Random Functions and Applications. ACM
Transactions on Information and System Security
(TISSEC), 10(4), pp. 3:1--3:22.
Dijk, B. G. a. M. V. et al., 2008. Controlled Physical
Random Functions and Applications. ACM
Transactions on Information and System Security
(TISSEC), 10(4).
Hofer, C. B. a. M., 2012. Physical Unclonable Functions
in Theory and Practice. 1 ed. New York, USA:
Springer Publishing Company.
Hu, J.-X., Chen, C.-L., Fan, C.-L. & Wang, K.-h., 2017.
An Intelligent and Secure Health Monitoring Scheme
Using IoT Sensor Based on Cloud Computing.
Sensors, Volume 2017, p. 11.
Kalra, S. & Sood, S. K., 2015. Secure authentication
scheme for IoT and cloud servers. Pervasive and
Mobile Computing, 24(C), pp. 210 - 223.
Lao, Y., Yuan, B., Kim, C. H. & Parhi, K. K., 2017.
Reliable PUF-Based Local Authentication With Self-
Correction. IEEE Transactions on Computer-Aided
Design of Integrated Circuits and Systems, 36(2), pp.
201-213.
Schleicher, M. V. a. J. M., Inzinger, C., Dustdar, S. &
Ranjan, R., 2016. Migrating Smart City Applications
to the Cloud. IEEE Cloud Computing, 3(2), pp. 72-79.
Suárez-Albela, M., Fernández-Caramés, T. M., Fraga-
Lamas, P. & Castedo, L., 2017. A Practical Evaluation
of a High-Security Energy-Efficient Gateway for IoT
Fog Computing Applications. Sensors, 17(9).
Wallrabenstein, J. R., 2015. Implementing Authentication
Systems Based on Physical Unclonable Functions. In
Proceedings of the 14th IEEE International
Conference On Trust, Security And Privacy In
Computing And Communications, TrustCom-15, pp.
790-796, Helsinki, Finland.
Wallrabenstein, J. R., 2016. Practical and Secure IoT
Device Authentication Using Physical Unclonable
Functions. In Proceedings of the IEEE 4th
International Conference on Future Internet of Things
and Cloud (FiCloud 2016), pp. 99-106, Vienna,
Austria.
Yosra, B. D., Yacine, D., Slim, R. & Noureddine, B.,
2018. Cloud-based Global Monitoring System for
Smart Cities. In Proccedings of the 32nd IEEE
International Conference on Advanced Information
Networking and Applications Workshops, WAINA
2018, Cracow, Poland.
Secure Authentication Solution for Cloud-based Smart City Surveillance System
507
