
A Scalable Decentralized and Lightweight Access Control Framework
Using IOTA Tangle for the Internet of Things
Tariq Alsboui
1
, Muhammad Hussain
1
, Hussain Al-Aqrabi
2
, Richard Hill
1
and Mohammad Hijjawi
3
1
University of Huddersfield, U.K.
2
Higher Colleges of Technology, U.A.E.
3
Applied Science Private University, Jordan
Keywords:
Internet of Things (IoT), Access Control, IOTA Tangle, Masked Authenticated Messaging (MAM), Restricted
Mode.
Abstract:
With the vast development of Internet-of-Things (IoT) ecosystem, various types of information, such as health-
care records and physical resources, are integrated for different types of applications. Due to the sheer number
of connected IoT devices, which generate a large amount of data, Distributed Ledger Technology, such as
Blockchain and IOTA have been recently applied in developing access control models, yet they involve signif-
icant energy due to mining, low throughput, non-scalable, and computational overhead that is not acceptable
for IoT resource-constrained devices. In this paper, we propose a Scalable Decentralized and Lightweight
Access Control framework (SDAC) by using the IOTA platform. IOTA is an emerging distributed ledger
technology that has significant features for IoT, such as zero fees transactions, scalability, security and energy
efficiency. The proposed SDAC aims to improve security, authorize, and authenticate users when accessing
data by using the IOTA Masked Authenticated Messaging (MAM) protocol. MAM ensures access control
by encrypting and granting permission to only authorized users. The experimental results indicate that IOTA
MAM is a feasible solution that can be used for managing authorization in the IoT domain.
1 INTRODUCTION
Over the last few years, various branches of Artifi-
cial Intelligence, have been widely adopted for deliv-
ering services across numerous domains, from indus-
trial defect detection (Hussain et al., 2022c), health-
care (Hussain et al., 2022d) renewable energy (Hus-
sain et al., 2022a), intelligent transportation (Perera
et al., 2017; Sumalee and Ho, 2018) and preserva-
tion of food quality (Hussain et al., 2022b). Inter-
net of Things (IoT) interconnects heterogeneous de-
vices with diverse functionalities to meet the evolving
requirements of the earlier mentioned domains (Al-
Fuqaha et al., 2015). IoT devices are characterised by
limited resources, such as power consumption, mem-
ory and processing (Alsboui et al., 2021a). Research
reports estimate the rapid growth of IoT; in the or-
der of 125 billion devices connected to the Internet in
2030 (Cisco, 2016; Gartner, 2013; Research, 2013).
Consequently, this presents many challenges with re-
gards to data that comes in greater volume, velocity
and variety, timely processing, privacy and scalabil-
ity (Al-Aqrabi et al., 2019; Alsboui et al., 2020).
IoT devices, in particular sensors are usually de-
ployed without careful security consideration. This
results in critical security issues. It has been reported
that one issue related to security is unauthorized ac-
cess to the IoT resources, which has been extensively
studied in (Neshenko et al., 2019). As IoT data con-
tains personal information and IoT devices equipped
with sensors are often deployed in close proximity to
human bodies, without providing an appropriate ac-
cess control mechanism to the IoT resources, our data
and safety would be significantly threatened.
Authorization and access control are fundamen-
tal challenge determining the successful implemen-
tation of many IoT applications. Authorization can
be defined as the process of enabling the right access
to authorized users. Access control is considered as
the backbone technology to ensure information secu-
rity. It provides the opportunities to overcome some
of the IoT technical challenges. It can be defined as
a technique that restricts access to resources (i.e., ob-
jects) to only the authorized users (i.e., subjects). Ac-
cess control will ultimately monitor the access of re-
sources and prevent the unauthorized flow of informa-
178
Alsboui, T., Hussain, M., Al-Aqrabi, H., Hill, R. and Hijjawi, M.
A Scalable Decentralized and Lightweight Access Control Framework Using IOTA Tangle for the Internet of Things.
DOI: 10.5220/0011963600003482
In Proceedings of the 8th International Conference on Internet of Things, Big Data and Security (IoTBDS 2023), pages 178-185
ISBN: 978-989-758-643-9; ISSN: 2184-4976
Copyright
c
2023 by SCITEPRESS – Science and Technology Publications, Lda. Under CC license (CC BY-NC-ND 4.0)

tion. However, traditional access control methods and
techniques cannot fully solve the access control prob-
lems faced by the IoT due to centralization, which
represents a single point of failure (Qiu et al., 2020).
Distributed Ledger Technology (DLT) is an
emerging development that shares data among dif-
ferent participants deployed over various locations all
over the world. This technology provides several ben-
efits to various IoT applications. Literature reveals
a growing interest of relevant research community in
DLT, considering it one possible solution to address
some of the IoT related challenges, such as scalability,
access control, security and privacy. (Alsboui et al.,
2020; Fan et al., 2019).
Most recently, IOTA technology, a paradigm shift,
is changing the infrastructure for the major applica-
tion areas of IoT by enabling a decentralized envi-
ronment with anonymous and trustful transactions.
The combination of IoT and IOTA technology brings
many benefits including less operational cost, decen-
tralized resource management, scalability, and robust-
ness against attacks. This indicates that the conver-
gence of IoT and IOTA technology will ultimately
overcome the significant challenges identified in the
IoT domain.
In this paper, we propose a Scalable Decentralized
and Lightweight Access Control framework by using
the IOTA Masked Authenticated Messaging (MAM)
(See Section 2 for Further Details) as a suitable so-
lution to tackle the scalability, and authorization is-
sues for IoT applications. MAM is a second layer
data communication protocol that is used to authenti-
cate, and encrypt data streams via the use of a set of
operations, such as public, private, and restricted.
Contributions. In this paper, we propose a system
architecture for IoT, called Scalable Decentralized
and Lightweight Access Control framework (SDAC).
This framework addresses access control issues in
IoT, whilst supporting the popular proof-of-work
(PoW) mechanism in an energy-efficient way. The
key contributions can be summarized as follows:
• A Scalable decentralized and lightweight access
control framework that ensures scalability and ef-
ficiency in authorizing access to data by using the
IOTA MAM protocol with a set of operations.
• Evaluation of an existing Proof of Work (PoW)
offloading mechanism for efficacy with regard to
energy efficiency and transaction throughput.
• Preliminary experimental results to verify the ef-
fectiveness and scalability of the proposed frame-
work.
The rest of this paper is organized as follows: Sec-
tion 2 presents an overview of the IOTA platform
and a detailed description of the masked authenticated
messaging. Section 3 presents the recent research
efforts in access control models in the IoT domain.
In Section 4, we describe our scalable decentralized
and lightweight access control framework. Section 5
presents an implementation of the proposed frame-
work and analysis of the results. Finally, in Section
6, we conclude the paper and discuss future work.
2 IOTA PLATFORM: AN
OVERVIEW
Currently, IOTA is scheduled to undergo a two-part
protocol upgrade, IOTA 1.5 (Chrysalis), which is the
current network and IOTA 2.0 (Coordicide), aimed
at implementing a series of major DLT technology
advancements to improve network functionality and
achieve greater decentralization. The IOTA 1.5 in-
troduces a protocol enhancements that enable smart
contract functionality, tokenized assets and stable
coins, which could enable new use cases for consumer
and enterprise IoT applications, an implementation
of product features including: reusable addresses,
UTXO, new Firefly wallet, and new libraries and Ap-
plication Programming Interface (APIs) for an im-
proved developer experience. The IOTA 2.0, imple-
ments a new consensus mechanism that aims to im-
prove IOTA’s scalability, security, and decentraliza-
tion by removing the centralized Coordinator node.
The architecture of the IOTA tangle is an evolv-
ing DLT platform aimed at addressing transaction
costs, mining and scalability issues (in the context of
Blockchain technology) (Zhang and Jacobsen, 2018),
that are related to IoT. The architecture of a Tan-
gle (Serguei, 2017), which is central to IOTA, a DAG
that offers a potentially scalable IoT-enabled applica-
tions. Tangle can be used to build IoT applications.
However, tangle has the advantages of being intu-
itively understandable.
IOTA technology offers the necessary data access
authorization for IoT applications. In the context
of transactions, IOTA may promote IoT interactions.
This approach radically changes the overall design,
development, implementation and management pro-
cess of IoT systems.
2.1 The Tangle
The IOTA Tangle was developed to cope with the re-
quirements of IoT applications such as privacy, and
security. Tangle is built upon a Directed Acyclic
Graph (DAG), which is considered to be the ledger
that stores transactions. The Tangle is the data
A Scalable Decentralized and Lightweight Access Control Framework Using IOTA Tangle for the Internet of Things
179
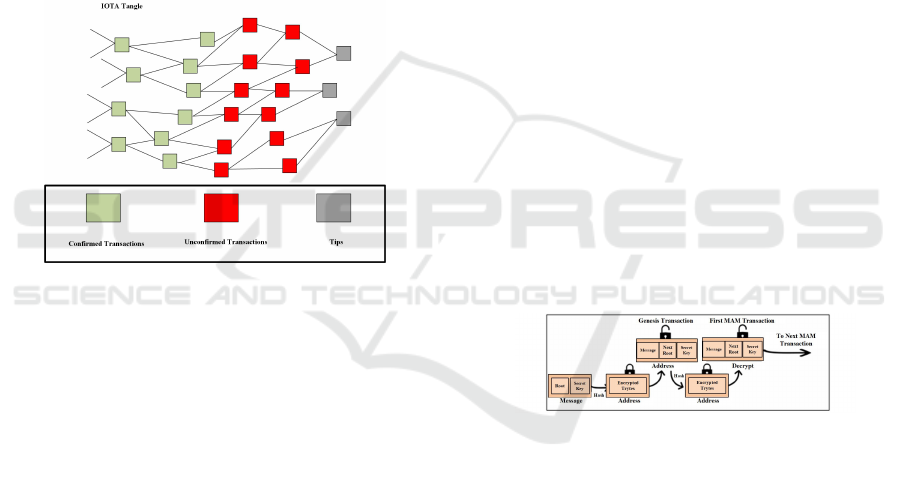
structure that consists of a collection of sites and
edges (Serguei, 2017) as shown in Fig. 1. In or-
der to issue a transaction by a node, the node should
work to approve two previous transactions. Choos-
ing the two previous transactions is done by using
the tip selection technique whereby default is the
Markov Chain Monte Carlo (MCMC) technique (Ser-
guei, 2017). Fig. 1 shows that the green boxes rep-
resent confirmed transactions, while the red boxes are
unconfirmed transactions and the grey boxes repre-
sent tips without any validation. The main aim of the
Tangle network is to make all the transactions to be
confirmed and to make all the unconfirmed transac-
tions to confirmed transactions. The MCMC tech-
nique is executed n number of times Genesis is the
first transaction of the network, which is approved di-
rectly or indirectly by the other transactions.
Figure 1: IOTA Tangle is based on a Directed Acyclic
Graph (DAG).
The IOTA Tangle is designed in a way to enable
transactional settlement to be more scalable, more the
transactions made more secure and efficient the tangle
gets (Serguei, 2017).
2.2 Masked Authentication Messaging
IOTA developed a second layer data communication
protocol, called Masked Authenticating Messaging
(MAM) (Handy, 2017), which is responsible for
masking, authenticating, and encrypting data streams.
Consequently, data streams are broadcasted and re-
trieved through the Tangle as zero fee transactions.
Given these properties, MAM fulfills an important
need in which integrity and access control are re-
quired.
Every MAM data transaction is linked with an ad-
dress in which a user can refer to the transaction. Data
transactions would be transmitted using the MAM
protocol at any point in time, but a small amount of
Proof of Work (PoW) is needed in order to broad-
cast data streams to the IOTA network. Transaction
data broadcasted using MAM are linked together in
chronological order. Furthermore, a signature of the
user is attached to all MAM data streams. This en-
sures that subscribers are required to verify the au-
thenticity of the user. By adopting MAM, users will
certainly ensure safety when exchanging data to the
Tangle.
MAM transactions can be broadcasted and fetched
from the IOTA Tangle, by communicating with a fully
functional node. This indicates that an IoT device will
be able to transmit encrypted data streams using the
IOTA MAM protocol.
2.2.1 MAM Privacy and Encryption Operations
MAM enables encryption to occur through several op-
erations including: public, private, and restricted. In
public operation, the user uses the tree’s root as the
address of the transaction that the message is pub-
lished to. A user will be able to decode it by using
the address of the message. Public operation enables
any user to read the content of the data, but it adds
immutability and data integrity.
In the case of private operation, there is an added
level of security that controls the access in order to
be able to read the content of the transaction data. It
enables access to users who have only the hash of the
channel key. The users would request the tangle for
the hash of the channel key. Then, it would enable
them to decode the transaction data by using the chan-
nel key.
Figure 2: The process of publishing transaction using re-
stricted operation.
In the case of restricted operation, it adds an au-
thorization key to the private operation. The address
used to attach to the network is the hash of the autho-
rization key and the Merkle root. It also offers granu-
lar access to users who have the secret key. Therefore,
access would be revoked from users if needed. If the
secret key change, the new authorized key is required
and should be distributed to the users that needs to
gain access to the data. Fig. 2 describes the process
of sending data using the restricted operation.
3 RELATED WORK
There has been sustained research into access control
models for IoT over the last few years. In a recent
IoTBDS 2023 - 8th International Conference on Internet of Things, Big Data and Security
180

publication (Ravidas et al., 2019), the authors classi-
fied access control models into six categories includ-
ing: Discretionary Access Control (DAC), Mandatory
Access Control (MAC), Role-based Access Control
(RBAC), Organization-Based Access Control (Or-
BAC), Attribute-based Access Control (ABAC), and
Usage Control (UCON). For a comprehensive and re-
cent literature review, we refer the interested readers
to (Ravidas et al., 2019) and the references therein.
Such research efforts focused on developing access
control models for IoT. However, there has been little
attention on how to manage the scalable IoT infras-
tructure.
Recently, the authors in (Shafeeq et al., 2019) in-
troduced a new decentralized access control system
based on the Tangle. The system empowers the users
to dictate the access to their resource. The proposed
decentralized access control model allows the poli-
cies and access rights to be published on the Tan-
gle. Therefore, it guarantees distributed auditability
and prevents the user from fraudulently denying the
granted access rights. The proposed system is scal-
able, introduces low delays, and has zero transaction
fees. However, resource constraints of IoT devices
such as power consumption is not taken into consid-
eration.
In (Nakanishi et al., 2020), a novel access control
framework based on IOTA and the Ciphertext Policy
Attribute-based Encryption (CP-ABE) CP-ABE tech-
nology is proposed. The framework works accord-
ing to three phases including: token structure, access
right authorization, and access right verification. In
token structure, a token contains a unique ID, the is-
suer, the address it is linked with on the Tangle, the
policy that must be satisfied to decrypt the token, and
a list of access rights. In the authorization phase, the
object owner first decides the policy embedded into
the token and the corresponding access rights to spec-
ify which group of subjects can perform what actions
to the object. Finally, the access right verification Af-
ter successfully decrypting the token, a subject can
send the object owner an access request. The request
is also encrypted using CP-ABE and there is no need
to establish a secure communication channel between
the subject and the object owner. The proposed sys-
tem is scalable and has zero transaction fees. How-
ever, the system does not take into consideration the
limited energy consumption and computation of IoT
devices.
Similarly, an access control mechanism called,
Decentralized Capability-Based Access Control
framework (DCACI) is introduced in (Pinjala and
Sivalingam, 2019). The DCACI framework enables
complete privacy and integrity of the capability to-
kens using IOTA’s Masked Authenticated Messaging
(MAM) protocol. It enables device owners and
users to Grant, Update, Delegate and Revoke the
capability tokens. The proposed DCACI framework
is scalable, requires less delay, provides fine-grained
access control mechanism for IoT networks and
has zero transaction fees. However, the framework
does not take into consideration the limited energy
consumption and computation of IoT devices.
Different from the above is the work proposed
in (Maesa et al., 2017) in which a new approach based
on blockchain technology to publish the policies ex-
pressing the right to access a resource and to allow the
distributed transfer of such right among users. The
proposed system uses the policies and the rights ex-
changes, which are publicly visible on the blockchain.
The proposed solution allows distributed auditabil-
ity, preventing a party from fraudulently denying the
rights granted by an enforceable policy. However,
the system lacks scalability and is not specifically de-
signed for constrained IoT devices.
In (Andersen et al., 2017) the authors propose
WAVE an authorization scheme based on Ethereum
Smart Contracts. Wave uses Delegations of Trust
(DoTs) and Identity-Based Encryption (IBE). The
DoTs together form a global permission graph which
spans different trust domains. A proof of authoriza-
tion is a chain of DoTs. WAVE enables the relevant
parties to look up such proofs of delegation efficiently.
The IBE allows a party to encrypt a message using
a global public key and the identity of the receiver
instead of that receiver’s public key. In order to de-
crypt, the receiver must be granted a secret key for
his identity by a global trusted entity. The Wave ap-
proach provides a powerful means of federating net-
works of embedded networks and supporting the life
cycles of devices, services, smart environments, in-
frastructures, and individuals. However, it lacks sup-
port for resource constrained IoT devices.
4 PROPOSED APPROACH
Fig. 3 presents an abstract view of the system archi-
tecture of the proposed Scalable Decentralized and
Lightweight Access Control Framework (SDAC). It
shows all relevant components including IoT devices,
transaction data flow, Node JS with MAM, Gateway,
and PoW computation offloading server. The IoT de-
vices are mainly responsible for transmitting trans-
action data using MAM client and sends transaction
data to a receiver, which is the gateway. The gate-
way is connected to the internet and transmits transac-
tions data to a server, which runs the Node JS Masked
A Scalable Decentralized and Lightweight Access Control Framework Using IOTA Tangle for the Internet of Things
181
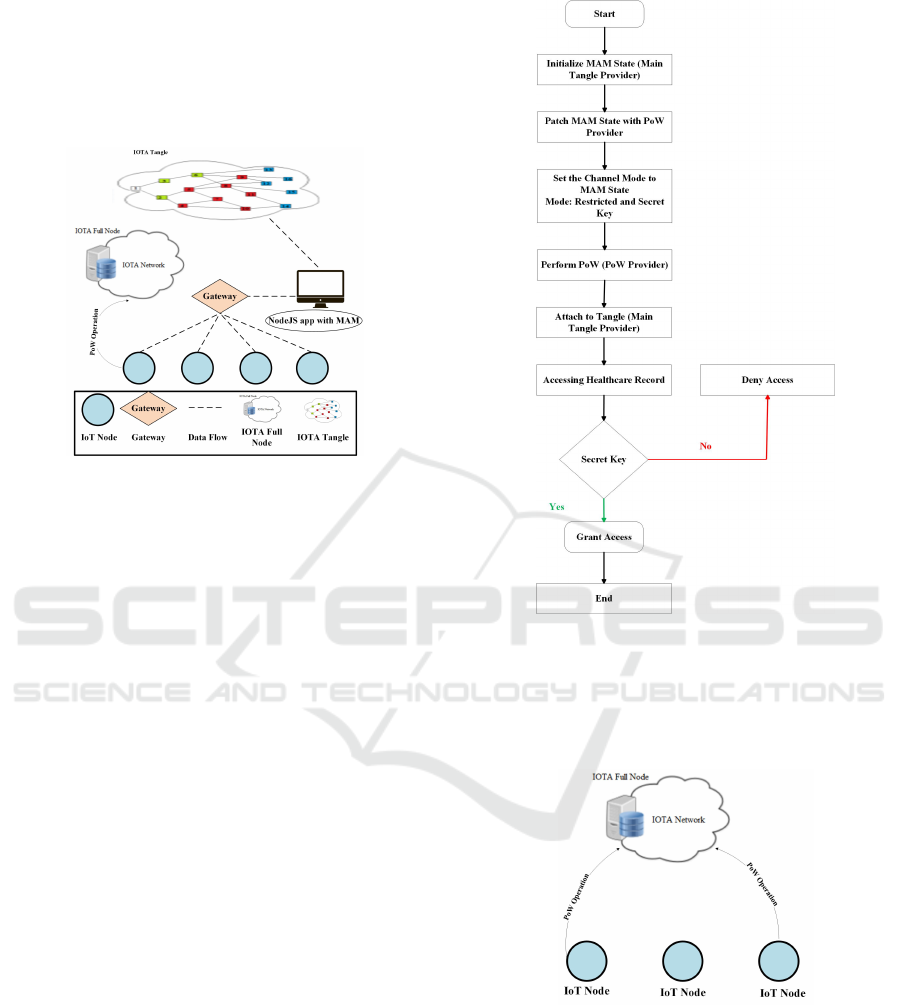
Authenticated Messaging (MAM) application. The
Node JS MAM is responsible for transmitting transac-
tion data to the IOTA Tangle. For example, the trans-
action data flow from IoT devices (e.g., dash lines)
represents the way how transaction data is transmit-
ted to the IOTA Tangle using MAM.
Figure 3: The proposed scalable decentralized and
lightweight access control framework (SDAC).
The PoW enabled server is concerned with per-
forming heavy computation tasks on behalf of con-
strained IoT devices.
The flowchart of the proposed SDAC framework
is shown in Fig. 4. First, the MAM state is initialized
using the main Tangle provider. After MAM state is
initialized, its patched with the Proof of Work (PoW)
for performing the PoW, which patches MAM sate
with the PoW Provider. Then, the channel mode is
set to restricted on the MAM state. Once this step
is completed, the payload is created and prepared to
be transferred to the main Tangle. Then, the PoW is
performed on the PoW provider. Once the PoW is
completed, the payload will be attached to the main
Tangle. In order for users to be able to access health-
care records, the root ID and the correct secret key
should be provided. Therefore, If the correct secret
key is provided, grant access to that user otherwise
deny access.
4.1 PoW Offloading
There are two types of offloading including: data of-
floading and computation offloading. Data offload-
ing refers to the use of novel network techniques to
transmit mobile data originally planned for transfer-
ring via cellular networks, while computation offload-
ing refers to offloading heavy computation tasks to re-
serve resources (Zheng et al., 2020). Fig. 5 illustrates
the PoW computation offloading mechanism used in
the SDAC framework. It shows how constrained IoT
Figure 4: Flowchart of the basic SDAC framework.
devices in terms of power are able to offload the PoW
computation to a node with higher resources. The se-
lected node is an IOTA full node, which is responsible
for performing the PoW as described in Fig. 5.
Figure 5: PoW Computation Offloading in SDAC frame-
work.
5 IMPLEMENTATION, RESULTS
AND ANALYSIS
In this section, we report the preliminary experimen-
tal findings of our proposed SDAC framework, which
indicate its effectiveness in terms of access control,
IoTBDS 2023 - 8th International Conference on Internet of Things, Big Data and Security
182

authorization, and scalability for IoT healthcare ap-
plication. Furthermore, we provide analysis and dis-
cussion of the results
5.1 Environment Setup
The implementation of our proposed SDAC frame-
work is based on Node JS. The functionality re-
lated to IOTA addresses, transactions, broadcasting,
and multi-signatures has been implemented using
iota.lib.js (Foundation, 2018), the official JavaScript
library of the IOTA MAM Distributed Ledger Techol-
ogy, which allows issuing and fetching MAM trans-
actions. We simulated a network using the IOTA de-
vnet
1
as clients, which in turn interacts with an IOTA
full node to issue and fetch data using MAM. In ad-
dition, another IOTA full node was deployed on a lo-
cal server dedicated for performing the Proof of Work
(PoW) operation.
The implementation focuses on the public and re-
stricted operations of MAM. Public operation is uti-
lized to ensure authenticity, and data integrity, while
restricted operation enables users to control access to
healthcare records using the secret key. This is par-
ticularly useful for healthcare applications where per-
missions is required in order to gain access to sensi-
tive data.
5.2 Results and Analysis
Fig. 6 shows the result of sending transaction data to
the Tangle using public operation. It also shows the
output of fetching masked transaction data in which
the user would only require the root, which is the en-
cryption and decryption key. The transaction data sent
using public operation ensures authenticity and data
integrity i.e., confirming that the data is coming from
a particular IoT device. The public operation uses the
root as the address of the transaction that contains the
Figure 6: Publishing transaction data from IoT devices us-
ing Public Operation.
1
https://nodes.devnet.iota.org
MAM message (channel ID). Consequently, any user
can find and decrypt the message in a public operation
by using the address.
Sending Transactions with Restricted Operation.
Fig. 7 shows the result of publishing transactions data
using the restricted operation.
Figure 7: Publishing transactions from IoT devices using
Restricted operation.
Access Right Authorization. Restricted operation
enables granular access control to transaction data and
provides authorization to the transaction data stored
on the Tangle. It only allows participants who have
the secret key to decode the transaction data. Fig.
8 demonstrates the granular access control over the
transaction data stored on the Tangle. It also shows
that when a user fetches transaction data, access will
be authorized, and a user is allowed to decrypt the
transaction data by having the secret key. Therefore,
access will be authorized.
Figure 8: Accessing transaction data with right secret key
(Authorized Access).
Unauthorized Access. Fig. 9 demonstrates the use
of restricted operation with the wrong secret key. A
user who has the wrong secret key will be unable to
access the transaction data stored on the Tangle. It
also shows that when a user is attempting to fetch the
transaction data by having the wrong secret key, ac-
cess will be unauthorized. This is in turn useful in IoT
healthcare application in which users will have the
ability to control who can gain access to their health-
care records.
Figure 9: Accessing transaction data with wrong secret key
(Unauthorized Access).
A Scalable Decentralized and Lightweight Access Control Framework Using IOTA Tangle for the Internet of Things
183
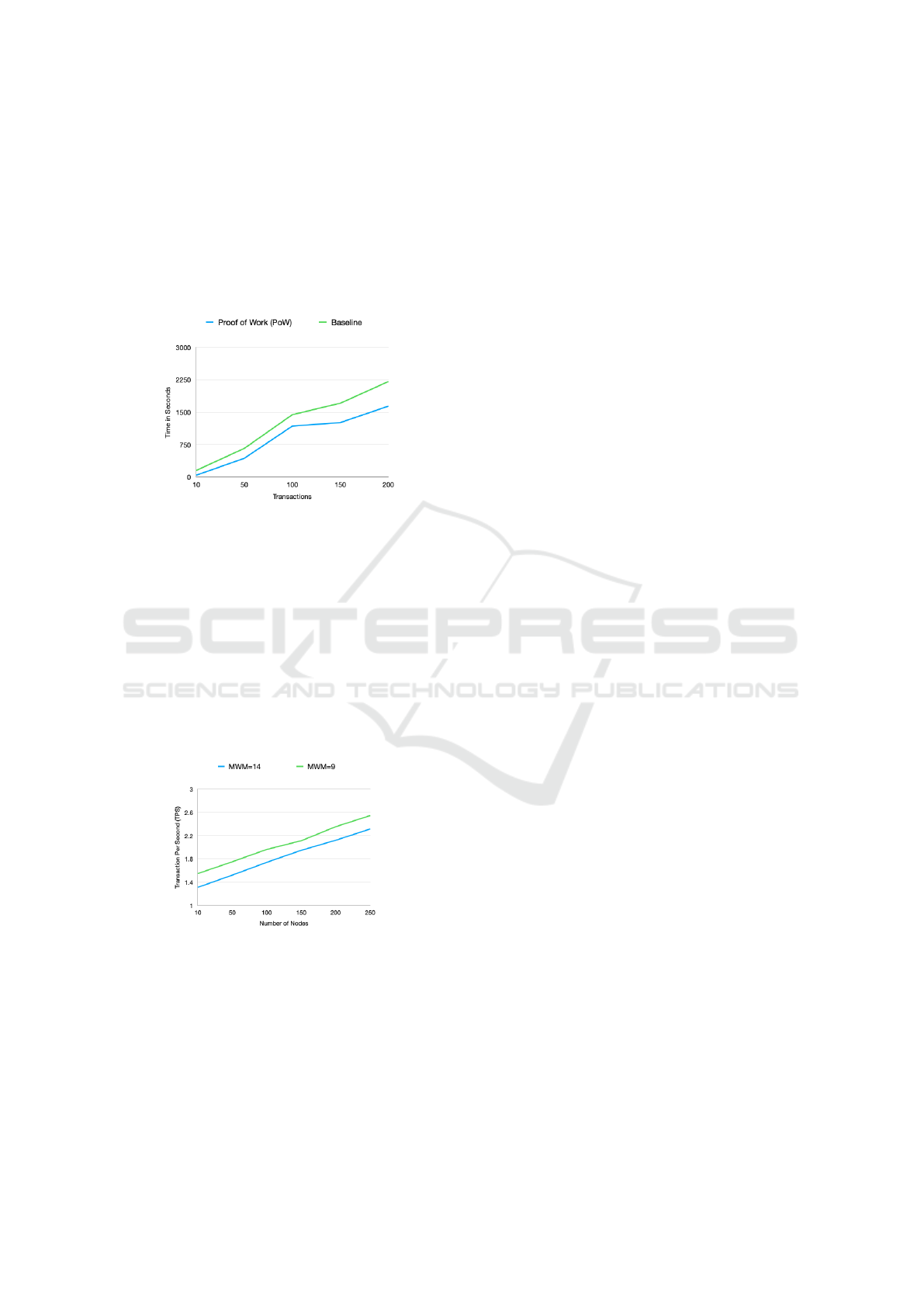
PoW Execution Time. Fig 10 shows the result of the
execution time when offloading the PoW compared to
the baseline. As it can be seen from Fig 10 that when
the number of sent transactions are 100, the execution
time of the PoW reaches 1177.5 second and the base-
line reaches 1440.1 second. This is because the PoW
is being offloaded to a dedicated node with higher re-
sources, while in the baseline the PoW is computed
on the same IoT device.
Figure 10: PoW execution time compared to the baseline.
Scalability. Fig 11 shows the result of the SDAC
framework in terms of scalability with different Min-
imum Weight Magnitude (MWM) settings, and dif-
ferent number of nodes. it is clear that as the num-
ber of nodes increases, the Transaction Per Second
(TPS) transaction speed increases linearly. Conse-
quently, the transaction speed has a good linear scal-
ability when the number of nodes increases. Also, its
clear that when 100 nodes are sending transactions,
the average TPS reaches 1.543 tx/s when the MWM
is set to 14, while the average TPS reaches 1.764 tx/s
when the MWM is set to 9.
Figure 11: Scalability in Tangle with 250 nodes.
6 CONCLUSION AND FUTURE
WORK
In this paper, we have addressed the issue of access
control in IoT by using the IOTA distributed ledger
technology. Specifically, we have employed the IOTA
MAM protocol using a set of operations, such as pub-
lic and restricted, to grant granular access to data. In
order to achieve access control and ensure scalability,
a scalable decentralized and lightweight access con-
trol framework, called SDAC, has been proposed.
There are a number of interesting directions for
future work. We plan to thoroughly investigate the re-
duction in energy consumption and improve the scal-
ability of the proposed approach by looking into pro-
cessing access requests per unit time that measures
the execution time of various processes such as, at-
tach, encrypt, and decrypt. Then, we plan to develop
an interactive model that enables the users to enter the
secret key to be able to access the data.
Finally, we plan to introduce the concept of mo-
bile agent (Alsboui et al., 2016), in particular multi-
mobile agent with a dynamic multi-mobile agent
itinerary planning mechanism (Alsboui et al., 2021b)
for data collection from healthcare sensors and em-
ploy techniques of information extraction (Alsbou
´
ı
et al., 2011) in order to further improve the perfor-
mance of the proposed SDAC framework.
REFERENCES
Al-Aqrabi, H., Pulikkakudi Johnson, A., Hill, R., Lane, P.,
and Liu, L. (2019). A multi-layer security model for
5g-enabled industrial internet of things. In 7th In-
ternational Conference on Smart City and Informa-
tization (iSCI 2019), Guangzhou, China, November
12-15, 2019, Lecture Notes in Computer Science,
Switzerland. Springer International Publishing AG.
Al-Fuqaha, A., Guizani, M., Mohammadi, M., Aledhari,
M., and Ayyash, M. (2015). Internet of things: A
survey on enabling technologies, protocols, and ap-
plications. IEEE Communications Surveys Tutorials,
17(4):2347–2376.
Alsboui, T., Alrifaee, M., Etaywi, R., and Jawad, M. A.
(2016). Mobile agent itinerary planning approaches in
wireless sensor networks- state of the art and current
challenges. volume 188, pages 143–153.
Alsbou
´
ı, T., Hammoudeh, M., Bandar, Z., and Nisbet, A.
(2011). An overview and classification of approaches
to information extraction in wireless sensor networks.
Alsboui, T., Qin, Y., Hill, R., and Al-Aqrabi, H. (2020). En-
abling distributed intelligence in the internet of things
with iota and mobile agents. Computing, xx.
Alsboui, T., Qin, Y., Hill, R., and Al-Aqrabi, H. (2021a).
Distributed intelligence in the internet of things: Chal-
lenges and opportunities. SN Comput. Sci., 2(4):277.
Alsboui, T., Qin, Y., Hill, R., and Al-Aqrabi, H. (2021b).
An energy efficient multi-mobile agent itinerary plan-
ning approach in wireless sensor networks. Comput-
ing, 103(9):2093–2113.
Andersen, M. P., Kolb, J., Chen, K., Fierro, G., Culler,
D. E., and Popa, R. A. (2017). Wave: A decentral-
ized authorization system for iot via blockchain smart
IoTBDS 2023 - 8th International Conference on Internet of Things, Big Data and Security
184

contracts. University of California at Berkeley, Tech.
Rep.
Cisco (2016). Internet of things at a glance. (1).
Fan, C., Khazaei, H., Chen, Y., and Musilek, P. (2019).
Towards a scalable dag-based distributed ledger for
smart communities. In 2019 IEEE 5th World Forum
on Internet of Things (WF-IoT), pages 177–182.
Foundation, I. (2018). Iota javascript api library. (visited on
1-08-2021).
Gartner (2013). Gartner says the internet of things installed
base will grow to 26 billion units by 2020. (1).
Handy, P. (2017). Introducing masked authenticated mes-
saging. (1). (visited on 31-07-2021).
Hussain, M., Al-Aqrabi, H., and Hill, R. (2022a). Pv-
cracknet architecture for filter induced augmentation
and micro-cracks detection within a photovoltaic man-
ufacturing facility. Energies, 15(22).
Hussain, M., Al-Aqrabi, H., Munawar, M., and Hill, R.
(2022b). Feature mapping for rice leaf defect de-
tection based on a custom convolutional architecture.
Foods, 11(23).
Hussain, M., Al-Aqrabi, H., Munawar, M., Hill, R., and
Alsboui, T. (2022c). Domain feature mapping with
yolov7 for automated edge-based pallet racking in-
spections. Sensors, 22(18).
Hussain, M., Al-Aqrabi, H., Munawar, M., Hill, R., and
Parkinson, S. (2022d). Exudate regeneration for au-
tomated exudate detection in retinal fundus images.
IEEE Access.
Maesa, D., Mori, P., and Ricci, L. (2017). Blockchain based
access control. pages 206–220.
Nakanishi, R., Zhang, Y., Sasabe, M., and Kasahara, S.
(2020). Iota-based access control framework for
the internet of things. In 2020 2nd Conference on
Blockchain Research & Applications for Innovative
Networks and Services (BRAINS), pages 87–95.
Neshenko, N., Bou-Harb, E., Crichigno, J., Kaddoum, G.,
and Ghani, N. (2019). Demystifying iot security: An
exhaustive survey on iot vulnerabilities and a first em-
pirical look on internet-scale iot exploitations. IEEE
Communications Surveys & Tutorials, 21(3):2702–
2733.
Perera, C., Qin, Y., Estrella, J. C., Reiff-Marganiec, S., and
Vasilakos, A. V. (2017). Fog computing for sustain-
able smart cities: A survey. ACM Comput. Surv.,
50(3):32:1–32:43.
Pinjala, S. K. and Sivalingam, K. M. (2019). Dcaci: A de-
centralized lightweight capability based access con-
trol framework using iota for internet of things. In
2019 IEEE 5th World Forum on Internet of Things
(WF-IoT), pages 13–18.
Qiu, J., Tian, Z., Du, C., Zuo, Q., Su, S., and Fang, B.
(2020). A survey on access control in the age of
internet of things. IEEE Internet of Things Journal,
7(6):4682–4696.
Ravidas, S., Lekidis, A., Paci, F., and Zannone, N. (2019).
Access control in internet-of-things: A survey. Jour-
nal of Network and Computer Applications, 144:79–
101.
Research, A. (2013). More than 30 billion devices will wire-
lessly connect to the internet of everything in 2020.
(1).
Serguei, P. (2017). The tangle. (1).
Shafeeq, S., Alam, M., and Khan, A. (2019). Privacy aware
decentralized access control system. Future Genera-
tion Computer Systems, 101:420–433.
Sumalee, A. and Ho, H. W. (2018). Smarter and more
connected: Future intelligent transportation system.
IATSS Research, 42(2):67–71.
Zhang, K. and Jacobsen, H. (2018). Towards depend-
able, scalable, and pervasive distributed ledgers with
blockchains. In 2018 IEEE 38th International Con-
ference on Distributed Computing Systems (ICDCS),
pages 1337–1346.
Zheng, T., Wan, J., Zhang, J., Jiang, C., and Jia, G. (2020).
A survey of computation offloading in edge comput-
ing. In 2020 International Conference on Computer,
Information and Telecommunication Systems (CITS),
pages 1–6.
A Scalable Decentralized and Lightweight Access Control Framework Using IOTA Tangle for the Internet of Things
185
