
An Infrastructure-Based Trust Management Framework for Cooperative
ITS
Rihab Abidi
1,4 a
, Nabil Sahli
2 b
, Wassim Trojet
3 c
, Nadia Ben Azzouna
1 d
and Ghaleb Hoblos
4 e
1
University of Tunis, ISG, SMART Lab, Av. de la Liberte, Tunis, Tunisia
2
Computer Science Department, German University of Technology (GUtech), Muscat, Oman
3
Higher College of Technology UAE, Abu Dhabi, U.A.E.
4
Normandy University, UNIROUEN, ESIGELEC, IRSEEM, Av. Galilee, Normandie, France
Keywords:
Intelligent Transportation System, Trust Management, Infrastructure-Based Architecture.
Abstract:
Intelligent Transportation Systems (ITSs) have been exploited by developed countries to enhance the quality
of transportation services. However, these systems are still facing major bottlenecks to be addressed such
as the data density, precision and reliability of perceived data and computational feasibility of the nodes.
Trust management is a mechanism applied to secure the vehicular networks. However, most of the proposed
trust models that are applied to Vehicular Ad-hoc NETwork (VANET) do not address all the aforementioned
challenges of ITS. In this paper, we present a comprehensive framework of trust management specifically
designed for ITS applications. The proposed framework is an infrastructure-based solution that relies on
Smart Road Signs (SRSs) to assess the trustworthiness of traffic data and nodes of the network. The idea of
the framework is to use autonomous SRSss that are able to collect raw data and evaluate it in order to alert
the drivers with reliable traffic information in real time. We adopt a hierarchical architecture that exploits a
two-level trust evaluation to ensure accuracy, scalability, security and high reactivity of ITS applications. A
discussion of the framework and its strengths is presented.
1 INTRODUCTION
With the growth of traffic volume, the modern society
faces major transportation challenges that may cause
serious and harmful consequences, such as accidents,
congestions, environmental consequences and even
economic impacts. Intelligent Transportation Sys-
tems (ITSs) are a promising solution that helps im-
prove the traffic management by deploying sustain-
able and innovative platforms (Guerrero-Ibanez et al.,
2015).
Despite its development over the last decade, the
ITS field still faces some challenges and bottlenecks,
mainly, precision, security and computational issues
(Lin et al., 2017). Traditional solutions that are based
on Public Key Infrastructure (PKI) are not able to se-
a
https://orcid.org/0000-0002-6108-7854
b
https://orcid.org/0000-0002-9805-6859
c
https://orcid.org/0000-0001-7792-4402
d
https://orcid.org/0000-0002-6953-2086
e
https://orcid.org/0000-0003-3268-5270
cure the network from legit nodes that could disturb
the network and send untrustworthy data. Trust man-
agement models are thus used to secure the network
and evaluate the precision and relevance of the shared
data. In fact, trust management models refer to the
evaluation of the accuracy and relevance of a trustee
node or data by a trustor node using quantified beliefs
in order to mitigate and reduce the impact of attackers
(Hbaieb et al., 2022).
In this regard, we propose a trust framework
to support the ITS applications. We propose an
infrastructure-based solution that uses Smart Road
Signs (SRSs) for cooperative ITS. Several architec-
tures of SRSs have been proposed in the literature.
For instance, the project proposed in (Czy
˙
zewski
et al., 2019) is based on intelligent road signs to man-
age the road traffic and prevent highway collisions.
The intelligent road signs are able to collect data
from sensors and exchange it, using LTE and LoRa
WAN technologies. However, while dynamic mes-
sage signs (DMSs) are employed in different coun-
tries, these DMSs remain passive and display traffic
Abidi, R., Sahli, N., Trojet, W., Ben Azzouna, N. and Hoblos, G.
An Infrastructure-Based Trust Management Framework for Cooperative ITS.
DOI: 10.5220/0011971600003479
In Proceedings of the 9th International Conference on Vehicle Technology and Intelligent Transport Systems (VEHITS 2023), pages 329-336
ISBN: 978-989-758-652-1; ISSN: 2184-495X
Copyright
c
2023 by SCITEPRESS – Science and Technology Publications, Lda. Under CC license (CC BY-NC-ND 4.0)
329

information issued from traffic management centers.
In this framework, we rely on the SRSs to take ad-
vantage of their intelligence which lies in their auton-
omy, proactivity and their ability to process data with-
out the intervention of third parties (Hamdani et al.,
2022). The aim of the proposed framework is to use
autonomous and SRSs that collect real-time data from
different sources and collaborate to evaluate its trust-
worthiness.
Researchers proposed several trust models for Ve-
hicular Ad-hoc NETwork (VANET). However, most
trust models cover at most few challenges of the ITS
applications. In fact, studies show that achieving
the optimal performance of ITS applications lies in
combining several characteristics and requirements.
Mainly, the ITS applications are meant to provide
accurate information in real-time performance while
managing the message overheads and ensuring the se-
curity and privacy of the network (Ben Hamida et al.,
2015).
To the best of our knowledge, there is no model
that meets the most crucial requirements of the ITS,
namely, accuracy, scalability, security, reactivity, and
privacy.
In this context, we propose a comprehensive
framework of a trust management model that en-
hances the performance of ITS applications. The aim
of the proposed framework is to evaluate the trustwor-
thiness of reported traffic events and the data sources.
Our aim is to ensure that the trust model responds to
the crucial requirements of ITS at once. In fact, we
exploit multi-sourcing of traffic-related data to ensure
the overall visibility of the environment. These data
may be sensed from different transportation nodes
such as vehicles, travellers, infrastructure and even
social media. Moreover, we adopt a decentralized ar-
chitecture to reduce the communication and compu-
tation overhead.
The rest of the paper is organized as follows. Sec-
tion 2 presents the related works. Section 3 introduces
the network model. Section 4 describes the proposed
framework. We discuss the design goals in section 5.
Section 6 concludes the paper.
2 RELATED WORKS
Different trust models have been proposed to evaluate
the trustworthiness of traffic data and/or nodes. Gen-
erally, researchers review the proposed trust model
according to the subject of trust: entity-centric, data-
centric, and hybrid models. In this paper we focus on
the addressed requirements of the trust model.
For instance, Bhargava and Verma propose in
(Bhargava and Verma, 2022) trust management model
which ensures accuracy and security requirements. In
fact, the authors consider the uncertainty of the data
to increase the precision. They use Dempster–Shafer
theory (DST) to aggregate direct and indirect trust
of the vehicles. In order to increase the precision
of the trust evaluation, the authors use contextual
information to define the type of the messages that
are attacked by the malicious vehicles. The con-
sidered messages are Lane Change warning (LCW),
Stopped Vehicle Warning (SVW), and Emergency
Brake warning (EBW). Moreover, the authors use ad-
ditional functions to enhance the precision of the trust
evaluation and boost the security of the model. The
used functions are the penalty, the forgetting, the re-
warding, and the forgiving functions.
Forgetting function is also used in (Zhang et al.,
2020b) by Zhang et al. and it is introduced with a de-
cay factor to cope with the On-Off attacks (OOA) and
the Newcomer attacks (NA). The idea of using these
factors is to prevent the quick increase of the trust
value of the nodes. This technique helps to encour-
age the nodes to present a good behaviour in order to
maintain their trust values. In addition, the authors
take advantage of the contextual information about
the vehicles, such as vehicle type, vehicle age, braking
performance, handling stability, etc. and the drivers’
characteristics to achieve the accuracy requirement of
the trust evaluation.
The security and privacy requirements are tackled by
Ahmed et al. in (Ahmed et al., 2022). The authors
use the blockchain technology to check the legitimacy
and authenticity of the nodes joining the network. The
new nodes that join the network for the first time are
registered in the blockchain by the Trusted Authority.
Then, the Road Side Units (RSUs) evaluate the trust-
worthiness of the vehicles and add their updated trust
values to the blockchain ledger.
Zhang et al. in (Zhang et al., 2020a) consider
the accuracy, the security and the reactivity of their
trust model. They propose a learning approach that
uses a Feedforward Neural Network algorithm (FNN)
to estimate the local and global trust values. They
use several contextual information as an input to the
FNN, such as the type, the location of the traffic inci-
dent, and location of the reporting vehicle. The pro-
posed model is designed to cope with Bad Mouthing
attack (BMA), On-Off Attack (OOA), and Simple At-
tack (SA). In fact, the authors combine the deep learn-
ing technique with the blockchain technology to learn
the correlation between the malicious nodes and to
predict their behaviour. Moreover, the blockchain is
used to enhance the security by checking the authen-
ticity of the vehicles and the reported events. The
VEHITS 2023 - 9th International Conference on Vehicle Technology and Intelligent Transport Systems
330
blockchain is managed by the RSUs instead of the ve-
hicles in order to ensure the scalability of the model.
Gazdar et al. in (Gazdar et al., 2022) take advan-
tage of the blockchain technology to enhance the se-
curity of the vehicular network. The authors consider
mainly the BMA. Indeed, they affirm that the features
of the blockchain ensure the data integrity and avail-
ability. Moreover, they address the cold start prob-
lem by assigning an initial value to the new nodes that
join the network and saving their updated trust values
in the blockchain ledger. The authors consider also
the reactivity requirement to cope with time-sensitive
applications. In fact, they employ a lightweight tier-
based technique to compute the trustworthiness of
vehicles in order to reduce communication overhead
(Alboqomi et al., 2020).
A decentralized trust model is proposed by Chen
et al. in (Chen et al., 2020). The authors use an in-
centive mechanism to encourage nodes to participate
in the trust management process, thus increasing the
accuracy of the trust evaluation. Hence, the nodes are
either rewarded or punished based on the quality and
the workload of their contribution. Moreover, the in-
centive mechanism helps the model to cope with the
BMA by encouraging the nodes to be honest. More-
over, vehicles encrypt and sign exchanged data using
a unique and a unique key pair in order to cope with
the Sybil attack (SyA). The proposed model consid-
ers also the reactivity and scalability requirements by
designing a hierarchical architecture to reduce the la-
tency of the model. In fact, the authors employ a
decentralized consensus mechanism executed on two
layers in a parallel manner: the transaction validation
and the block verification and consensus.
Guo et al. propose a trust model in (Guo et al.,
2020) that cope with malicious attacks. The pro-
posed model addresses mainly the accuracy require-
ment. The authors use the Reinforcement learning to
dynamically adjust the trust evaluation strategy based
on the scenario. Thus, they employ contextual infor-
mation such as time of event occurrence and loca-
tion of the event. The trust information based on in-
ternal information (direct sensing and self-experience
information) and external information (information
reported by other entities).
As presented in table 1, the beforementioned trust
management models consider, at most, one or few
requirements of the ITS applications. For instance,
few works consider only the accuracy and security
requirements, such as in (Li and Song, 2015), and
(Zhang et al., 2020b), while (Bhargava and Verma,
2022) consider also the reactivity. Moreover, we no-
ticed that the accuracy and security requirements are
the most considered among the addressed require-
ments. To the best of our knowledge, there is not a
general trust model that considers all the requirements
at once. However, the mentioned requirements are
crucial for ITS applications. In particular, accuracy
and security are critical requirements, especially for
congestion control applications (Alam et al., 2016),
(Ben Hamida et al., 2015). Indeed, the diffusion of
erroneous information, due to inaccuracy of raw data
or attacks by malicious nodes, may cause severe con-
sequences such as high congestion or even road acci-
dents. High reactivity is also a key requirement for
time sensitive applications. In case of congestion, the
drivers should be alerted in real-time to avoid traffic
bottlenecks. Therefore, we propose a generic frame-
work of a trust model that may be used by ITS ap-
plications. The aim of this work is to provide a trust
framework that fulfils all the crucial requirements of
the ITS applications in order to enhance the provided
services.
3 OVERVIEW
The proposed framework relies on a hierarchical
infrastructure-based vehicular network where the
smart road signs are the core components. This ar-
chitecture enables a real-time dissemination of traffic
information and monitoring of the Intelligent Trans-
portation Systems.
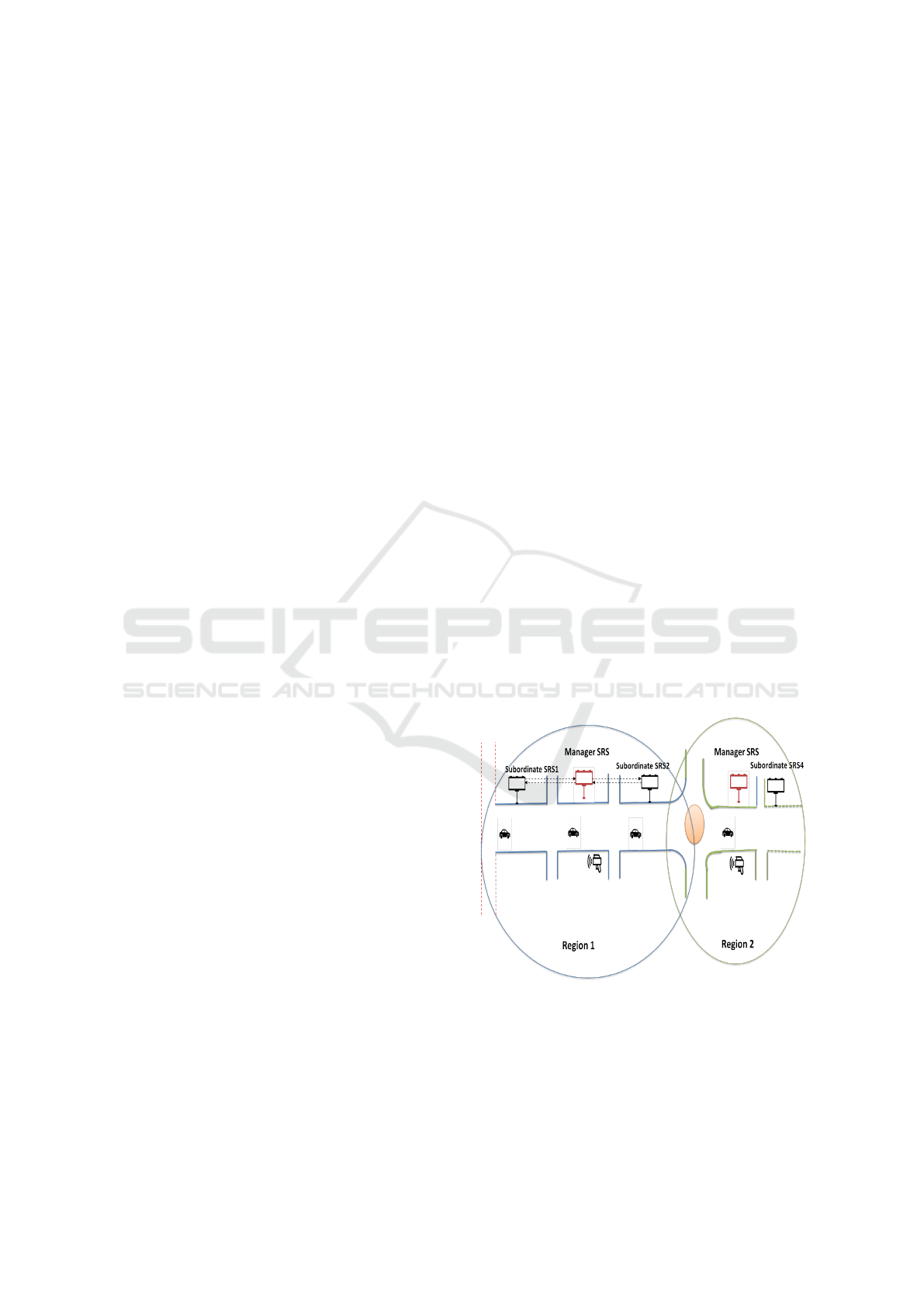
First, we consider that the traffic roads are parti-
tioned into smaller regions, as shown in figure 1.
Figure 1: Region-based vehicular network.
Each region is a set of connected roads that en-
compasses several nodes that manage the traffic infor-
mation in these roads. Nodes include smart road signs
(SRS) as well as traffic/environment data sources.
Smart road signs can be Manager or Subordinate as
defined in (Sahli et al., 2022) as Master and Slave.
An Infrastructure-Based Trust Management Framework for Cooperative ITS
331

Table 1: The considered requirements of the surveyed trust models.
Paper Accuracy Security Reactivity Scalability Privacy
(Bhargava and Verma, 2022) ✓ ✓
(Zhang et al., 2020b) ✓ ✓
(Ahmed et al., 2022) ✓ ✓
(Zhang et al., 2020a) ✓ ✓ ✓
(Gazdar et al., 2022) ✓ ✓ ✓
(Chen et al., 2020) ✓ ✓ ✓ ✓
(Guo et al., 2020) ✓ ✓
A Manager SRS is in charge of collecting data from
Subordinates. Each region includes many subordi-
nates and one Manager. Data sources can be con-
nected vehicles, surveillance cameras, radar, etc. Let
us consider a region composed of one manager SRS,
n subordinates, and m data sources. In particular,
when a road is congested the data sources alert the
nearest SRSs about the traffic state. Hence, the sub-
ordinate SRSs evaluate the trustworthiness of the re-
ported event and alert the drivers about possible traffic
congestion. The evaluations of the subordinate SRSs
are then transmitted to the manager SRS to aggregate
them. The final warning message will be sent to the
subordinate SRSs to update the displayed alert mes-
sages.
Figure 2 presents the general architecture of our
network system and the dissemination of the data
flow. In what follows, we present the major compo-
nents of our framework.
Figure 2: General architecture of the trust model.
1. SRSs: The SRSs are the main component in the
network model. They are equipped with digital
screens to alert drivers about the traffic state in
real-time (Sahli et al., 2022). These SRSs are
connected to the internet and endowed with pro-
cessing capabilities. Accordingly, they are able to
collect traffic-related data and evaluate their cred-
ibility, in order to estimate and communicate the
traffic state. Unlike the existing DMSs, which
display the traffic state estimated by traffic man-
agement centers, the SRSs are endowed with in-
telligence and autonomy allowing them to pro-
cess the sensed data without human intervention.
We adopt a hierarchical architecture based on two
types of SRSs:
(a) Manager SRSs: These SRSs are assumed to be
fully trusted by the neighbouring subordinate
SRSs. We suppose that the manager SRSs are
secured and equipped with higher storage and
communication capabilities. The main role of
manager SRSs is to aggregate the evaluations
of subordinate SRSs about the reported traffic
events. In general, the manager SRS controls
the subordinates localized in its region. Ac-
cordingly, it evaluates and updates their trust
values and stores them in the Subordinates-BC
blockchain. In fact, the Subordinates-BC is
used to keep track of the trustworthiness of the
subordinates.
(b) Subordinate SRSs: Unlike the manager SRSs,
we suppose that the subordinate SRSs may be
compromised. Hence, their credibility is evalu-
ated by the manager SRSs. However, they are
responsible for the evaluation of the trustwor-
thiness of the traffic events reported by the data
sources and updating the values of their trust
values. As shown in figure 2, the subordinate
SRSs contribute to the block validation to up-
date the trust values of the data sources in the
sources-BC blockchain.
2. Data sources: Data sources are a set of mo-
bile nodes, such as connected vehicles, and static
nodes, like surveillance cameras, radars, pneu-
matic tube sensors, and inductive loops. These
nodes are responsible for reporting traffic events
to the subordinate SRSs. The data sources may
communicate erroneous data due to physical fail-
ure or intentionally when hijacked by malicious
attackers.
VEHITS 2023 - 9th International Conference on Vehicle Technology and Intelligent Transport Systems
332

4 DETAILED DESIGN
In this section, we present the detailed design of the
proposed framework. In fact, the proposed model is
composed of five main modules:
1. Events classification
2. Lower layer trust evaluation
3. Higher layer trust evaluation
4. Reward/ punishment
5. Blockchain validation
4.1 Events Classification
We suppose that traffic event messages are sent to
the nearest subordinate SRS. Those messages will be
classified into groups of events according to spatio-
temporal information and semantic analysis. The idea
of the event classification module is to assemble the
messages that report the same event. Moreover, the
event classification module assigns a severity degree
to each group of event according to the frequency
of the reports and the type of the event. Therefore,
the group of events with the highest severity degree
will be processed before the group of events with
a lower severity degree. For instance, the module
will pay more attention to events of type “accidents”
than events of type “light congestion”. The aim is to
increase the reactivity of the model in the presence
of various traffic events and to avoid serious conse-
quences.
4.2 Lower Layer Trust Evaluation
The proposed framework uses the data reported by
several data sources in order to increase the visibil-
ity of the surrounding environment. However, the
data sources may be compromised and intentionally
provide erroneous data, or unintentionally in case
of physical failure. Accordingly, a trust evaluation
method will be used by the subordinate SRSs to es-
timate the trustworthiness of the provided data and/or
the node that reported it. Several trust methodologies
proposed in the literature may be used. For example,
plausibility checking using fuzzy logic may be a suit-
able approach to evaluate both the data and the node
trustworthiness such as in (Souissi et al., 2022). Other
methodologies such as game theory and belief theory,
and regression analysis also may be used to estimate
the trustworthiness of the provided data (Wang et al.,
2016), (Chen et al., 2016), (Kang et al., 2018).
4.3 Higher Layer Trust Evaluation
The final decision on whether to choose to trust or
ignore the reported events is made by the manager
SRS. Therefore, the manager SRS estimates the over-
all trust out of the evaluation of the subordinate SRSs
in the same region. Moreover, a manager SRS may
collaborate with nearby manager SRSs to estimate the
trustworthiness of events occurring on the edges of its
regions. The idea behind adding a second evaluation
of the reported events is that the manager SRS has a
general overview of the environment by combining
the estimations of the subordinate SRSs. Different
approaches may be used for the trust formation. For
example, static weighted sum and dynamic weighted
sum may be used to combine the trust evaluation of
the subordinate SRSs.
4.4 Reward/ Punishment
The reward/punishment module is proposed to be ap-
plied at two levels. At the higher layer, it is imple-
mented in the manager SRS in order to adjust the
trustworthiness of the subordinate SRSs. At the lower
layer, it is deployed in the subordinate SRS to adjust
the behaviour of the data sources and to boost their
cooperativeness.
4.5 Blockchain Validation
We propose to add two blockchain modules to save
and track the behaviour of the nodes in the network.
The first blockchain is used to save the trustworthi-
ness of the data sources. This ledger is shared be-
tween the subordinate SRSs. The second blockchain
is used to store the trustworthiness of the subordinate
SRSs. The second ledger is controlled by the manager
SRS.
The use of the blockchain technology ensures
the integrity of the saved data, hence increases the
data reliability. Different consensus mechanisms may
be used in this regard. In particular, Proof-of-stake
(PoS), is an efficient mechanism in terms of energy.
Other mechanisms such as Delegated Proof of Stake
(DPoD), Proof of Work (PoW), and Proof of Author-
ity (PoA) may be also used (Liu et al., 2019), (Chen
et al., 2020), (Gazdar et al., 2022).
The overall workflow of the trust framework is
shown in figure 3. Hereafter, we list the sequence of
steps performed by the framework.
1. The data sources report an event
2. The event classification module classifies the re-
ported events into groups
An Infrastructure-Based Trust Management Framework for Cooperative ITS
333

Figure 3: Component interaction diagram of the proposed
framework.
3. The lower layer trust evaluation module receives
the group of events to evaluate their trustworthi-
ness
4. The lower layer trust evaluation module requests
the trust values of the data sources from the
blockchain
5. The lower layer trust evaluation module receives
the necessary data from the blockchain
6. The lower layer trust evaluation module estimates
the trustworthiness of the reported event
7. The alert message is then sent to be displayed on
the SRSs
8. The assessments of the subordinate SRSs are sent
to the higher layer trust evaluation module to ag-
gregate their evaluations
9. The higher layer trust evaluation module re-
quests the trust values of the salve SRSs from the
blockchain ledger
10. The higher layer trust evaluation module receives
the necessary data from the blockchain
11. The higher layer trust evaluation module executes
the final trust evaluation of the reported event us-
ing the assessments of the subordinate SRS
12. The displayed alert message is updated accord-
ing to the final evaluation of the higher layer trust
evaluation module
13. The final trust assessment is then sent to the re-
ward/punishment module to evaluate the trustwor-
thiness of the data sources and the subordinate
SRS
14.(a) The reward/punishment module updates the
trust values of the subordinate SRSs and sent
it to be saved in the blockchain ledgers
(b) The reward/punishment module updates the
trust values of the data sources and sent it to
be saved in the blockchain ledgers
5 CASE STUDY
In this section, we present a case study to explain the
dissemination and the process of event alert messages
within the proposed framework. Figure 4 describes
the discussed case study.
Figure 4: Representation of the case study scenario.
We suppose that the considered region is com-
posed of a manager SRS, two subordinate SRSs, a
surveillance camera, radar and six vehicles. In this
context, we use the surveillance camera, the radar and
the vehicles as our data sources. In this scenario, we
suppose that an accident has occurred on a road tran-
scend between two vehicles, V1 and V2. We suppose
that vehicle V3 and V4 reported to the second SRS
the occurrence of a crash event to SRS2. We sup-
pose that V5 is a malicious node and reported to SRS2
that traffic flow is normal. We suppose also that the
surveillance camera detected the presence of the acci-
dent and reported it to SRS2. Moreover, we suppose
that vehicle V6 and the radar reported that there is a
light congestion to SRS1. Hereafter, we describe the
process of the evaluation of the alert messages.
1. The reported events will be classified into event
groups using the spatio-temporal information and
semantic analysis. Let us consider that V3, V4,
V6, the radar and the surveillance camera sent
the detected events approximately at the same
time and neighbouring localization. Moreover,
the module will identify that the light congestion
may be related to the crash event. Accordingly,
we will have two groups of events:
VEHITS 2023 - 9th International Conference on Vehicle Technology and Intelligent Transport Systems
334

• E1 that combines the accident report by V3,
V4, the surveillance camera and the light con-
gestion by V6 and the radar.
• E2 that reports a normal traffic flow by V5.
The group of events E1 will be assigned the high-
est severity degree because it reports an event of
type accident and has the highest number of re-
ports. Accordingly, it will be processed in priority.
Similarly, E2 will have the lowest severity degree.
2. SRS1 and SRS2 evaluate the trustworthiness of
the reported events in E1 while considering the
trustworthiness of the data sources stored in the
blockchain.
3. A warning message will be then displayed on
SRS1 and SRS2. Let us assume that the trust as-
sessment of SRS1 of the event E1 is 0.7. Hence,
the displayed message will be “70% chance that
there is an accident ahead”. The idea is to in-
crease the reactivity of the framework. Therefore,
the drivers will be aware of the possibility of the
presence of an accident, even before the final eval-
uation of the manager SRS.
4. The evaluations of SRS1 and SRS2 will be trans-
mitted to the manager SRS to aggregate them, and
provide the final trust value of the event while
considering the trustworthiness of the subordinate
SRSs that are registered in the blockchain.
5. The displayed messages will be updated after the
final evaluation of the manager SRS.
6. The final evaluation of the manager SRS will be
used to update the trustworthiness of the data
sources and the subordinate SRSs.
6 PERFORMANCE ANALYSIS
In this section, we discuss the presumptions we con-
sidered in the design of the framework of the trust
management framework to present its strengths.
1. Presumption 1: The proposed framework en-
sures the scalability of the trust model to follow
the continuous growth of the ITS environment.
Discussion: The decentralized architecture of the
framework will help to scale down the traffic over-
head of the network. The partitioning of the road
network into smaller regions limits the number
of messages exchanged between the nodes of the
network. Moreover, we propose an infrastructure-
based architecture without internal communica-
tion between the data sources.
2. Presumption 2: The proposed framework in-
creases the accuracy of the displayed traffic state.
Discussion: The multi-sourcing data fusion re-
duces the uncertainty of the environment obser-
vation. Moreover, the two-level trust evaluation
scheme helps to have a global vision of the reli-
ability of the reported traffic events. In the low
evaluation layer we exploit the data provided by
the data sources. In the upper evaluation layer we
use the assessments of the subordinate SRSs.
3. Presumption 3: The proposed framework en-
sures the integrity, the availability, and the privacy
of the data.
Discussion: The use of the blockchain technology
ensures that the stored data is immutable. Blocks
validation requires the validation of the majority
of nodes to ensure the integrity of the informa-
tion. The ledgers of the blockchain are replicated
and synchronized, which avoids single-point fail-
ure. Therefore, it ensures the availability of the
data. Moreover, blockchain ledgers can only be
accessed by SRSs which protect sensitive data
from being leaked.
4. Presumption 4: The proposed framework in-
creases the reactivity of the ITS.
Discussion: The classification of the reported
events and the evaluation of the severity of the
events using the frequency of the reports and their
types help to process the events of highest priority.
Moreover, the decentralized and hierarchical ar-
chitecture combined with the blockchain technol-
ogy reduces the communication overhead (Gazdar
et al., 2022). Hence, it reduces the response time
of the ITS.
5. Presumption 5: The proposed framework of the
trust model meets the requirements of the ITS ap-
plications.
Discussion: Due to the increasing number of the
ITS components and to the time sensitivity of
their applications, especially the traffic congestion
management applications, the architecture of the
ITS applications must be scalable, accurate and
reactive to the changes of the environment. As
discussed in the proposition above, the proposed
framework would be scalable and able to provide
accurate information in a short response time.
7 CONCLUSION
We propose in this paper an open framework for a
trust management model to be enforced in ITS. The
aim is to enhance the performance of ITS by ensur-
ing its scalability, accuracy, security and the reactiv-
ity. We presented the general modules that should be
An Infrastructure-Based Trust Management Framework for Cooperative ITS
335

enforced and we discussed their efficiency and bene-
fits. However, the proposed framework might be un-
suitable for rural environments. We intend to further
investigate and identify the appropriate techniques to
be applied in each module. Besides, we intend to run
validation experimentation to test the validity of the
hypotheses.
REFERENCES
Ahmed, W., Di, W., and Mukathe, D. (2022). Privacy-
preserving blockchain-based authentication and trust
management in vanets. IET Networks.
Alam, M., Ferreira, J., and Fonseca, J. (2016). Introduc-
tion to intelligent transportation systems. In Intelligent
transportation systems, pages 1–17. Springer.
Alboqomi, O., Gazdar, T., and Munshi, A. (2020). A new
blockchain-based trust management protocol for ve-
hicular ad hoc networks. In The 4th International
Conference on Future Networks and Distributed Sys-
tems (ICFNDS), pages 1–5.
Ben Hamida, E., Noura, H., and Znaidi, W. (2015). Secu-
rity of cooperative intelligent transport systems: Stan-
dards, threats analysis and cryptographic countermea-
sures. Electronics, 4(3):380–423.
Bhargava, A. and Verma, S. (2022). Duel: Demp-
ster uncertainty-based enhanced-trust level scheme for
vanet. IEEE Transactions on Intelligent Transporta-
tion Systems.
Chen, X., Ding, J., and Lu, Z. (2020). A decentralized trust
management system for intelligent transportation en-
vironments. IEEE Transactions on Intelligent Trans-
portation Systems, 23(1):558–571.
Chen, Y., Weng, S., Guo, W., and Xiong, N. (2016). A game
theory algorithm for intra-cluster data aggregation in
a vehicular ad hoc network. Sensors, 16(2):245.
Czy
˙
zewski, A., Sroczy
´
nski, A.,
´
Smiałkowski, T., and Hoff-
mann, P. (2019). Development of intelligent road
signs with v2x interface for adaptive traffic control-
ling. In 2019 6th International Conference on Models
and Technologies for Intelligent Transportation Sys-
tems (MT-ITS), pages 1–7. IEEE.
Gazdar, T., Alboqomi, O., and Munshi, A. (2022). A decen-
tralized blockchain-based trust management frame-
work for vehicular ad hoc networks. Smart Cities,
5(1):348–363.
Guerrero-Ibanez, J. A., Zeadally, S., and Contreras-Castillo,
J. (2015). Integration challenges of intelligent trans-
portation systems with connected vehicle, cloud com-
puting, and internet of things technologies. IEEE
Wireless Communications, 22(6):122–128.
Guo, J., Li, X., Liu, Z., Ma, J., Yang, C., Zhang, J., and Wu,
D. (2020). Trove: A context-awareness trust model for
vanets using reinforcement learning. IEEE Internet of
Things Journal, 7(7):6647–6662.
Hamdani, M., Sahli, N., Jabeur, N., and Khezami, N.
(2022). Agent-based approach for connected vehicles
and smart road signs collaboration. Computing and
Informatics, 41(1):376–396.
Hbaieb, A., Ayed, S., and Chaari, L. (2022). A survey of
trust management in the internet of vehicles. Com-
puter Networks, 203:108558.
Kang, J., Yu, R., Huang, X., Wu, M., Maharjan, S., Xie,
S., and Zhang, Y. (2018). Blockchain for secure
and efficient data sharing in vehicular edge comput-
ing and networks. IEEE Internet of Things Journal,
6(3):4660–4670.
Li, W. and Song, H. (2015). Art: An attack-resistant
trust management scheme for securing vehicular ad
hoc networks. IEEE transactions on intelligent trans-
portation systems, 17(4):960–969.
Lin, Y., Wang, P., and Ma, M. (2017). Intelligent transporta-
tion system (its): Concept, challenge and opportunity.
In 2017 ieee 3rd international conference on big data
security on cloud (bigdatasecurity), ieee international
conference on high performance and smart comput-
ing (hpsc), and ieee international conference on intel-
ligent data and security (ids), pages 167–172. IEEE.
Liu, X., Huang, H., Xiao, F., and Ma, Z. (2019). A
blockchain-based trust management with conditional
privacy-preserving announcement scheme for vanets.
IEEE Internet of Things Journal, 7(5):4101–4112.
Sahli, N., Trojet, W., Zhang, Z., and Abdallah, N. O.
(2022). Towards a network of dynamic message signs
for congestion alerting. Computing and Informatics,
41(2):609–626.
Souissi, I., Ben Azzouna, N., Abidi, R., Berradia, T., and
Ben Said, L. (2022). Sp-trust: a trust management
model for speed trust in vehicular networks. In-
ternational Journal of Computers and Applications,
44(11):1065–1073.
Wang, Y., Cai, Z., Yin, G., Gao, Y., Tong, X., and Han,
Q. (2016). A game theory-based trust measurement
model for social networks. Computational social net-
works, 3(1):1–16.
Zhang, C., Li, W., Luo, Y., and Hu, Y. (2020a). Ait: An
ai-enabled trust management system for vehicular net-
works using blockchain technology. IEEE Internet of
Things Journal, 8(5):3157–3169.
Zhang, J., Zheng, K., Zhang, D., and Yan, B. (2020b).
Aatms: An anti-attack trust management scheme in
vanet. IEEE Access, 8:21077–21090.
VEHITS 2023 - 9th International Conference on Vehicle Technology and Intelligent Transport Systems
336
