
Improvement of Winternitz OTS with a Novel Fingerprinting Function
Motonari Honda and Yuichi Kaji
Nagoya University, Furo-cho, Chikusa-ku, Nagoya, 464-8601, Japan
Keywords:
Winternitz OTS, Hash-Based Signature, Post-Quantum Security, Fingerprinting Function, Security Proof.
Abstract:
Winternitz one-time signature (OTS) plays a core role in practical hash-based digital signature schemes includ-
ing SPHINCS+, one of PQC standardizations selected by NIST. This study focuses on the security mechanism
of Winternitz OTS and improves the scheme by introducing a novel fingerprinting function. The proposed
scheme has provable security of strongly existential unforgeability and reduces by about 10% of the computa-
tional costs for operations in Winternitz OTS. The improvement is combinable with other investigations such
as WOTS+, and gives the contribution to the study of practical quantum secure digital signatures.
1 INTRODUCTION
1.1 Background and Related Studies
A digital signature is one of the most essential com-
ponents in today’s digital communication. However,
there is a growing concern for the security of digi-
tal signatures due to the rapid progress of the real-
ization of quantum computers. There is a quantum
algorithm that efficiently solves number theory prob-
lems such as discrete logarithm and integer factor-
ing(Shor, 1997), and quantum computers can bring
a fatal collapse of digital signatures that are widely
used today. To avoid the tragic scenario, a lot of ef-
forts have been devoted to realizing quantum secure
digital signatures.
A hash-based digital signature is a digital sig-
nature scheme that uses cryptographic hash func-
tions instead of number theory problems(Buchmann
et al., 2011a; Dods et al., 2005). In the PQC
(Post-Quantum Cryptography) standardization pro-
cess of NIST, a hash-based scheme that is named
SPHINCS+(Aumasson et al., 2020) has been selected
as one of three digital signature algorithms that are
regarded as quantum secure and will be standard-
ized(Nat. Inst. of Standards and Technology, 2022).
The idea of using cryptographic hash functions for
a signature-like purpose can be found in an old pa-
per by Lamport(Lamport, 1979). The study is fol-
lowed by (Merkle, 1989), which proposes an im-
provement of the Lamport scheme and the usage of
a tree structure that is now known as the Merkle
tree. In this framework, a key pair can be used only
once to ensure security, and the schemes are often
referred to as one-time signatures or OTS. The one-
time nature is not preferable in practice, but the is-
sue can be mitigated by using the Merkle tree. The
paper (Merkle, 1989) also introduces another OTS
scheme that was, Merkle writes, “suggested” by Win-
ternitz. This Winternitz OTS became the core of sub-
sequent studies of hash-based digital signatures, even
though many hash-based OTS were proposed there-
after(Bleichenbacher and Maurer, 1996b; Bleichen-
bacher and Maurer, 1996a; Dods et al., 2005; Perrig,
2001; Reyzin and Reyzin, 2002). WOTS+(Hulsing,
2013) is a slightly modified Winternitz OTS and is
used as an internal component of practical hash-based
digital signature schemes such as XMSS(Buchmann
et al., 2011b), SPHINCS(Bernstein et al., 2015), and
aforementioned SPHINCS+. Thus the security and
the efficiency of Winternitz OTS have a relation to the
discussion of practical quantum secure technologies.
Winternitz OTS realizes all components of digital
signatures by using w hash chains with length l − 1
each, where w and l are integer parameters that sat-
isfy certain security criteria. The parameters w and
l quantify the computational costs for operations in
Winternitz OTS, but we cannot reduce both w and l
because of the trade-off relation between the two pa-
rameters.
Under this constraint, there are two approaches for
improving the efficiency of Winternitz OTS. The first
approach is to shorten the length of each hash value
without sacrificing the security. In WOTS+, the hash
chains are constructed by using a keyed hash function
instead of a single fixed hash function. This change
Honda, M. and Kaji, Y.
Improvement of Winternitz OTS with a Novel Fingerprinting Function.
DOI: 10.5220/0012049100003555
In Proceedings of the 20th International Conference on Security and Cryptography (SECRYPT 2023), pages 303-311
ISBN: 978-989-758-666-8; ISSN: 2184-7711
Copyright
c
2023 by SCITEPRESS – Science and Technology Publications, Lda. Under CC license (CC BY-NC-ND 4.0)
303

strengthens the security of hash chains and allows the
use of shorter hash values without sacrificing the se-
curity. Even though we cannot reduce the values of w
and l in this approach, shorter hash values contribute
to reducing the length of keys and signatures.
The second approach for improving Winternitz
OTS is to change the fingerprinting function that is
used in the scheme. It is essential in Winternitz OTS
that a fingerprint is augmented with a check-sum that
prevents the scheme from generating “weak” signa-
tures.
The study (Kaji et al., 2018) tries to replace this
mechanism by introducing a new fingerprinting func-
tion and succeeds in reducing the cost for signature
verification at the sacrifice in the increase of other
costs. The result is not satisfactory but suggestive be-
cause it showed that the check-sum mechanism is not
the sole means to ensure the security of the scheme.
1.2 Contribution of This Paper
This study improves the efficiency of Winternitz OTS
based on the second approach described above. We
replace the check-sum mechanism of Winternitz OTS
by a novel fingerprinting function that we call a zero-
sum fingerprinting function.
The zero-sum fingerprinting function can be re-
alized by combining an existing fingerprinting func-
tion such as SHA-256 and an efficiently computable
mapping that converts integers to zero-sum finger-
prints. The obtained zero-sum fingerprinting func-
tion inherits cryptographic properties such as one-
way and collision-resistant properties from the base
fingerprinting function.
In this paper, it is shown that this newly pro-
posed scheme is strongly existential unforgeable and
thus has provable security. Our modification changes
the trade-off relationship of parameters in the original
Winternitz OTS, and allows using smaller values for
w (the number of hash chains) and l (the length of a
hash chain) without sacrificing the security of OTS.
This contributes to reduce the computational costs for
all major operations in digital signatures, namely, key
generation, signature computation and signature veri-
fication.
It is also noted that our modification of Winter-
nitz OTS can be made independently from the con-
struction of hash chains, and thus combinable with
WOTS+. The improvement of the efficiency made in
this study, therefore, contributes to reducing the op-
erational costs in XMSS, SPHINCS, and SPHINCS+
that use WOTS+ as an internal component.
2 PRELIMINARY
In an intuitive discussion, a function h is said to be
one-way if it is easy to compute y = h(x) for a given
x but it is difficult to find x that satisfies y = h(x) for a
given y. A function h is said to be collision-resistant
if it is difficult to find z and z
′
satisfying h(z) = h(z
′
).
A digital signature consists of three algorithms,
KeyGen for generating a signing key SK and a veri-
fication key VK, Sign for the computation of signa-
tures, and Verify for the verification of signatures.
A digital signature scheme is said to be secure if it
does not allow an adversary to create a signature for
a forged message without accessing the signing key
SK.
A one-time siganture (OTS) is a digital signature
scheme that ensures the security under the condition
that a key pair is used only once.
In a formal discussion and security proofs, the
above notions must be defined rigorously in terms of
probabilistic polynomial-time algorithms. The fol-
lowing definitions come from (Goldwasser and Bel-
lare, 2008), though notations are slightly modified.
Definition 1. A real value function µ is said to be
negligible if for any positive integer c there exists N
c
such that |µ(x)| < 1/x
c
for all x > N
c
.
Definition 2. A function h is one-way if
Pr
y = h(x
′
) : x ← {0, 1}
∗
;y ← h(x); x
′
← A(y)
is negligible for any polynomial-time algorithm A.
A value x that makes y = h(x) is called a pre-image of
y.
Definition 3. A function h is collision-resistant if
Pr
h(z) = h(z
′
) : (z, z
′
) ← A
is negligible for any polynomial-time algorithm A.
We say that a pair (z, z
′
) with z , z
′
causes a collision
if h(z) = h(z
′
).
There are several formal definitions for the secu-
rity of digital signatures, and we focus strongly ex-
istential unforgeability that is defined in terms of an
interactive game between a challenger and an adver-
sary(Boneh et al., 2006). The game consists of three
phases: Setup, Query, and Output.
Setup. The challenger runs KeyGen and provides the
public verification key VK to the adversary. The
signing key SK is kept secret by the challenger.
Query. The adversary requests the challenger to
compute the signatures σ
1
,... ,σ
q
for adaptively
chosen query messages m
1
,. .. ,m
q
.
SECRYPT 2023 - 20th International Conference on Security and Cryptography
304

In an OTS, the number of queries is restricted to
one (i.e., q = 1) because a key pair is used only
once.
Output. The adversary outputs (m
′
,σ
′
), expecting
that σ
′
is a valid signature for m
′
.
It is required that (m
′
,σ
′
) , (m
i
,σ
i
) for 1 ≤ i ≤ q.
The adversary wins the game if (m
′
,σ
′
) is ac-
cepted by the Verify algorithm.
Definition 4. A signature scheme is strongly existen-
tial unforgeable if there is no polynomial-time algo-
rithm that plays the role of the adversary and wins the
game with non-negligible probability.
3 WINTERNITZ OTS
In Winternitz OTS, the three algorithms of a digital
signature are implemented as follows.
• KeyGen(1
n
):
Select a hash function h : {0,1}
∗
→ {0,1}
L
where
L is the bit length of the hash value of h, and a fin-
gerprinting function f : {0, 1}
∗
→ {0,1}
n
. Note
that the given security parameter n is used as the
bit length of the fingerprint that is generated by
f . The hash function h and the fingerprinting
function f are public information, and all players
know h and f .
Choose a positive integer parameter l and define
w = w
1
+ w
2
, where
w
1
=
⌈
nlog
l
2
⌉
and w
2
=
⌊
log
l
(w
1
(l − 1))
⌋
+ 1.
Select s
1
,. .. ,s
w
uniformly from {0,1}
L
at random
and compute v
i
= h
l−1
(s
i
) for 1 ≤ i ≤ w. The
signing key and the verification key are defined
as SK = (s
1
,. .. ,s
w
) and VK = (v
1
,. .. ,v
w
), re-
spectively. We call the sequence of hash values s
i
,
h(s
i
), h
2
(s
i
), . . . , h
l−1
(s
i
) a hash chain (of length
l − 1) that originates from s
i
.
• Sign(SK,m):
Compute the fingerprint f (m) for the given mes-
sage m, and convert f (m) to an l-ary representa-
tion (a
1
,. .. ,a
w
1
) by regarding f (m) as an n-bit
binary integer.
Compute the check-sum
C = w
1
(l − 1) −
w
1
∑
i=1
a
i
, (1)
and let (c
1
,. .. ,c
w
2
) be the l-ary representation of
C.
Write ( f
1
,. .. , f
w
) = (a
1
,. .. ,a
w
1
,c
1
,. .. ,c
w
2
) and
call the tuple as a check-summed fingerprint for
Table 1: Parameters of Winternitz OTS for L = n = 256.
l w
1
w
2
w
bit length
wL
costs
w(l − 1)
32 52 3 55 14,080 1,705
64 43 2 45 11,520 2,835
128 37 2 39 9,984 4,953
256 32 2 34 8,704 8,670
the message m. The signature σ for the message
m is determined as σ = (h
f
1
(s
1
),. .. , f
f
w
(s
w
))
by using the check-summed fingerprint and the
signing key SK = (s
1
,. .. ,s
w
).
• Verify(VK, m,σ):
Compute the check-summed fingerprint
( f
1
,. .. , f
w
) for the message m. Accept m
and σ = (σ
1
,. .. ,σ
w
) if and only if the veri-
fication key VK = (v
1
,. .. ,v
w
) coincides with
(h
l−1− f
1
(σ
1
),. .. ,h
l−1− f
w
(σ
w
)).
The signing key, the verification key, and the sig-
natures of Winternitz OTS are all w-tuples of hash val-
ues of L-bits each, and hence wL-bits in bit length.
The computational cost (or simply the cost) for an
algorithm is measured by the number of computations
of the hash function h performed in the algorithm.
The cost for KeyGen is w(l −1) because the algorithm
constructs w hash chains of length l − 1 each. The
costs for Sign and Verify depend on the value of the
fingerprint for the message; they are upper-bounded
by w(l − 1) and expected to be w(l − 1)/2 in average.
Concrete values of w and l are determined from
the security parameter n, which is used to specify the
bit length of a fingerprint. If we use SHA-256 as
the realization of both the hash function h and the
fingerprinting function f , then L = n = 256. With
this setting, parameter values of Winternitz OTS for
l = 32,64,128,256 are shown in Tab. 1. The table
also shows the bit length wL of keys and signatures,
and the value of w(l −1) which is the cost for KeyGen
and the upper-bounds of the costs for Sign and Verify.
We can see a trade-off relation between the number w
and the length l of hash chains, and another trade-off
relation between the length of keys (signatures) and
operational costs.
4 PROPOSED SCHEME
4.1 Mutually Unordered Set
The check-sum mechanism of Winternitz OTS plays
a crucial role to make the scheme secure, but using a
check-sum is just a means. There is a mathematical
aspect that is necessary to make the OTS secure, and
Improvement of Winternitz OTS with a Novel Fingerprinting Function
305

appending a check-sum is one of many means to ob-
tain that aspect. In this section, we characterize the
needed aspect in terms of a mutually unordered set.
For tuples of integers a = (a
1
,. .. ,a
w
) and b =
(b
1
,. .. ,b
w
), we write a ≤ b if a
i
≤ b
i
for all 1 ≤ i ≤ w,
and a < b if a ≤ b and a , b. Two different tuples a
and b are said to be unordered if neither a < b nor
a > b holds. We say that a set T of tuples (of the
same length) are mutually unordered if any two dif-
ferent a, b ∈ T are unordered.
Consider a Winternitz-style OTS which converts
a message m to an integer tuple f = ( f
1
,. .. , f
w
)
and then determines the signature for m as σ =
(h
f
1
(s
1
),. .. ,h
f
w
(s
w
)).
Lemma 5. To make a Winternitz-style OTS secure,
the set of legitimate integer tuples must be mutually
unordered.
Proof:
Let f = ( f
1
,. .. , f
w
) and f
′
= ( f
′
1
,. .. , f
′
w
) be inte-
ger tuples for messages m and m
′
, respectively. Also,
write σ
i
(resp. σ
′
i
), 1 ≤ i ≤ w, for the i-th component of
the signature σ (resp. σ
′
) for m (resp. m
′
). If f < f
′
,
then f
′
i
− f
i
≥ 0 for all 1 ≤ i ≤ w and σ
′
i
is computed
from σ
i
as σ
′
i
= h
f
′
i
− f
i
(σ
i
). This suggests that anyone
who has obtained the signature σ can forge the signa-
ture σ
′
of another message m
′
. Therefore, the set of
legitimate integer tuples must be mutually unordered.
□
Notice that the set of legitimate check-summed
fingerprints in Winternitz OTS is mutually unordered.
4.2 v-sum Sets
In constructing a mutually unordered set of integer
tuples, we investigate a different approach from the
check-sum computation in Winternitz OTS. The con-
structed set will be used as the range of a fingerprint-
ing function in the next section.
For positive integers w and b and a (possibly non-
positive) integer v, define
D
v
w,b
= {(t
1
,. .. ,t
w
) : t
i
∈ [−b,b],t
1
+ ··· + t
w
= v},
and call the set as a v-sum set ([x,y] stands for the
set of integers {x,...,y}).
The next lemma follows immediately from the
definition of v-sum sets.
Lemma 6. A v-sum set is mutually unordered. □
We will consider using D
0
w,b
, a v-sum set with
v = 0, as the space of fingerprints in a Winternitz-style
OTS. In that context, we need to determine the num-
ber of elements (tuples) in D
v
w,b
for given parameters
w,b and v.
Write T
v
w,b
for the number of elements in D
v
w,b
.
There is no closed-form expression of T
v
w,b
, but the
following equations hold.
T
v
1,b
=
(
1 if v ∈ [−b,b],
0 if v < [−b,b],
T
v
w,b
=
i=b
∑
t
1
=−b
T
v−t
1
w−1,b
for w > 1.
(2)
The basis (2) follows since D
v
1,b
contains only one
element (v) if v ∈ [−b,b], while D
v
1,b
=
/
0 if v < [−b,b].
The recursion (4.2) is obtained because
D
v
w,b
=
b
[
t
1
=−b
n
(t
1
,t
2
,. .. ,t
w
) : (t
2
,. .. ,t
w
) ∈ D
v−t
1
w−1,b
o
.
Note also that the second equation in the basis (2)
can be generalized as
T
v
w,b
= 0 if v < [−wb, wb], (3)
because the sum of w integers each within [−b,b]
cannot be smaller than −wb nor greater than wb.
The number of tuples in D
v
w,b
can be determined
by using these equations. For example, we can con-
firm that T
0
45,29
> 2
256
by choosing w = 45, b = 29
and v = 0, which means that D
0
45,29
contains more el-
ements than all SHA-256 fingerprints.
4.3 Zero-Sum Fingerprinting Function
Consider a fingerprinting function that has D
0
w,b
as
its range, and call the function as a zero-sum finger-
printing function. There is no zero-sum fingerprint-
ing function known so far, but we can realize it by
combining an existing fingerprinting function such as
SHA-256 and a mapping z
v
w,b
that converts an integer
i ∈
h
0,T
v
w,b
− 1
i
to the integer tuple that comes to the
i-th place when all tuples in D
i
w,b
are ordered in as-
cending dictionary manner.
Tab. 2 illustrates the mappings z
0
3,2
(left and mid-
dle) and z
3
3,2
(right).
To discuss the computation of the mapping z
v
w,b
,
assume w > 1 meanwhile and consider the list of all
tuples in D
v
w,b
where tuples are ordered in ascending
dictionary manner. The list must start from tuples
that are written as (−b,t
2
,. .. ,t
w
) with (t
2
,. .. ,t
w
) ∈
D
v+b
w−1,b
, and the number of such tuples is T
v+b
w−1,b
.
The tuples are then followed by T
v+b−1
w−1,b
tuples
(−b + 1,t
2
,. .. ,t
w
) with (t
2
,. .. ,t
w
) ∈ D
v+b−1
w−1,b
, and so
on.
From this observation, it is understood that the
first component t
1
of the mapping result (t
1
,. .. ,t
w
) =
z
v
w,b
(i) is an integer t that satifies S
t−1
≤ i < S
t
where
SECRYPT 2023 - 20th International Conference on Security and Cryptography
306
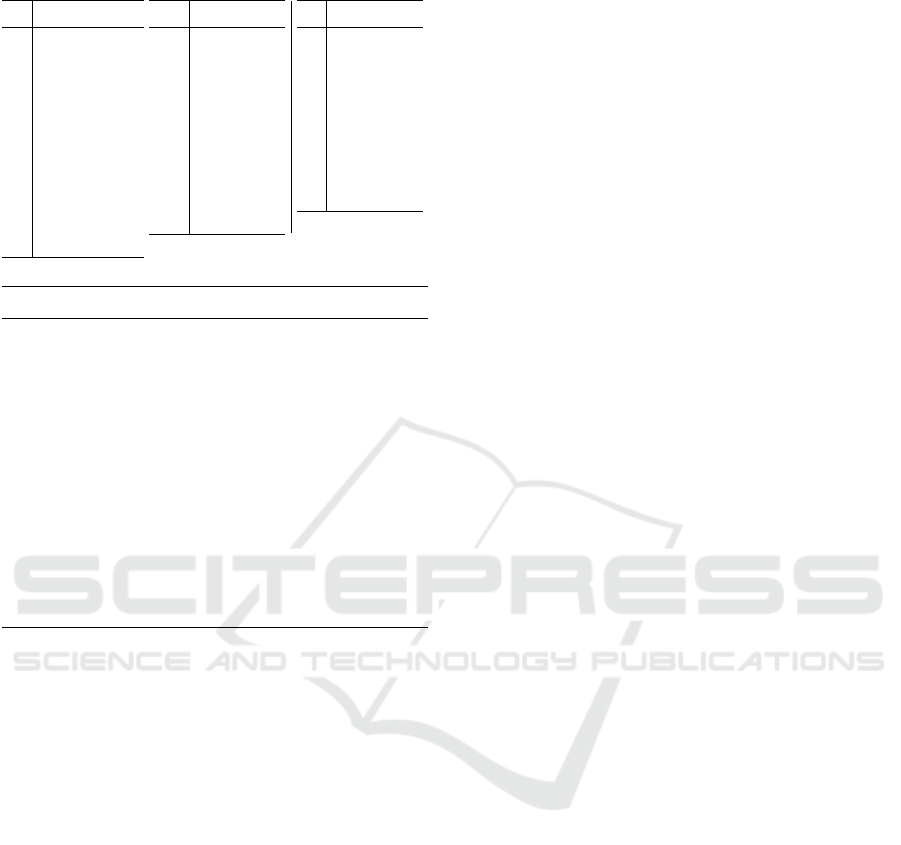
Table 2: The mapping z
0
3,2
.
i z
0
3,2
(i)
0 (−2,0, 2)
1 (−2,1, −1)
2 (−2,2, 0)
3 (−1,−1, 2)
4 (−1,0, 1)
5 (−1,1, 0)
6 (−1,2, −1)
7 (0,−2, 2)
8 (0,−1, 1)
9 (0,0, 0)
i z
0
3,2
(i)
10 (0,1, −1)
11 (0,2, −2)
12 (1,−2, 1)
13 (1,−1, 0)
14 (1,0, −1)
15 (1,1, −2)
16 (2,−2, 0)
17 (2,−1, 1)
18 (2,0, −2)
i z
3
3,2
(i)
0 (−1,2, 2)
1 (0,1, 2)
2 (0,2, 1)
3 (1,0, 2)
4 (1,1, 1)
5 (1,2, 0)
6 (2,0, 1)
7 (2,1, 0)
Algorithm 1: z
v
w,b
(i).
Require: i ∈
h
0,T
v
w,b
− 1
i
1: right ← 0
2: j ← −b − 1
3: repeat
4: j ← j + 1
5: left ← right, right ← left + T
v− j
w−1,b
6: until left ≤ i < right
7: t
1
← j
8: if w > 1 then
9: (t
2
,. .. ,t
w
) ← z
v− j
w−1,b
(i − left)
10: end if
11: return (t
1
,. .. ,t
w
)
Figure 1: Computation of the mapping z
v
w,b
(i).
S
t
=
t
∑
j=−b
T
v− j
w−1,b
.
It is also understood that the tuple (t
2
,. .. ,t
w
) of
the remaining w−1 components is the one that comes
to the (i − S
t−1
)-th place when tuples in D
v−t
1
w−1,b
are
dictionary ordered, that is,
(t
2
,. .. ,t
w
) = z
v−t
1
w−1,b
(i − S
t−1
).
and hence z
v
w,b
can be computed in a recursive
manner.
For the case of w = 1,
we have z
v
1,b
(0) = (v) for v ∈ [−b,b], while z
v
1,b
(i)
is not defined if i , 0 or v < [−b, b].
If we regard T
0
0,b
= 1 and T
v
0,b
= 0 for v , 0, then
the computation of z
v
1,b
(i) can be explained in the
same manner as the case for w > 1
Based on the above discussion, the computation of
z
v
w,b
can be described as the pseudo-code in Fig. 1.
The running time of the pseudo-code in Fig. 1 for
computing z
0
w,b
(i) is in O(wb) because the computa-
tion goes down to the depth w of recursion (the call
of z
0
w,b
is regarded as the recursion of depth 1), and at
most 2b +1 iterations are performed in each recursion
depth.
One concern in the computation of the pseudo-
code is that we need the values of T
v
w,b
for various
combinations of w, b and v, but T
v
w,b
does not have a
closed-form expression that enables efficient compu-
tation of T
v
w,b
. To avoid spending much computation
for computing T
v
w,b
, we consider calculating needed
values of T
v
w,b
in advance and store them in a lookup-
table.
To estimate the size of the lookup-table, revisit
the pseudo-code in Fig. 1 and consider the calcula-
tion steps that are performed in the computation of
z
0
w,b
(i). At the depth d of recursion, 1 ≤ d ≤ w, the
pseudo-code may access the values of T
v
w−d,b
with
v ∈ [−db, db]. On the other hand, (3) guarantees that
T
v
w−d,b
= 0 if v < [−(w−d)b, (w−d)b], and we do not
have to store the values of those T
v
w−d,b
in the lookup-
table.
Note also that T
v
w−d,b
= T
−v
w−d,b
, and therefore, the
values that must be stored in the lookup-table are
those T
v
w−d,b
with 1 ≤ d ≤ w and v ∈ [0,min(db,(w −
d)b)].
This implies that 1+ min(db,(w − d)b) values are
necessary for the recursion of depth d, and the number
of values that are stored in the lookup-table is
∑
w
d=1
(1 + min(db,(w − d)b)) = w + b
∑
w
d=1
min(d, w − d).
(4)
It is verified that (4) is upper-bounded by w
2
b/4+
wb/2 +w, which is the size of the lookup-table that is
used by the mapping z
0
w,b
.
We have seen in the previous section that the pa-
rameter choice (w,b) = (45,29) makes T
0
w,b
≥ 2
256
.
For this parameter choice, the size of the lookup-table
is only 15,379.
Now we shall resume the construction of a zero-
sum fingerprinting function. Let f be a fingerprint-
ing function that produces n-bit binary fingerprints.
Choose w and b in such a way that T
0
w,b
≥ 2
n
, and de-
fine f
w,b
(m) = z
0
w,b
( f (m)) for m ∈ {0,1}
∗
. Note that
f
w,b
is a zero-sum fingerprinting function that maps
messages to tuples in D
0
w,b
.
We call f
w,b
(m) the zero-sum fingerprint for the
message m.
The new fingerprinting function f
w,b
inherits all
statistical properties of the base fingerprinting func-
tion f , and if the base fingerprinting function f is
collision-resistant, then so is the zero-sum fingerprint-
ing function f
w,b
.
Improvement of Winternitz OTS with a Novel Fingerprinting Function
307

4.4 Proposed Scheme
Replace the check-sum computation of Winternitz
OTS with the zero-sum fingerprinting function. The
proposed OTS is then summarized as follows.
• KeyGen(1
n
):
Given the security parameter n, select w and b
so that T
0
w,b
≥ 2
n
and define a zero-sum finger-
printing function f
w,b
. The signing key SK =
(s
1
,. .. ,s
w
) is a w-tuple of randomly selected hash
values, and the verification key is defined as VK =
(h
2b
(s
1
),. .. ,h
2b
(s
w
)).
Note that hash chains of length 2b are constructed
instead of hash chains of length l −1 in Winternitz
OTS.
• Sign(SK,m):
Compute ( f
1
,. .. , f
w
) = f
w,b
(m) for the message
m, and determine the signature for m as σ =
(h
f
1
+b
(s
1
),. .. , f
f
w
+b
(s
w
)).
• Verify(VK, m,σ):
Write σ = (σ
1
,. .. ,σ
w
). Compute ( f
1
,. .. , f
w
) =
f
w,b
(m) for m, and verify if VK coincides with
(h
b− f
1
(σ
1
),. .. , f
b− f
w
(σ
w
)).
The keys and signatures of the proposed OTS are
all w-tuples of hash values of L-bits each, and hence
wL-bits in bit length. The cost for KeyGen is 2wb, the
cost for Sign and Verify are both wb. These quantities
are instantiated and evaluated later in Sect. 6.
5 FORMAL SECURITY PROOF
It is shown that the proposed OTS is strongly existen-
tial unforgeable under reasonable assumptions on the
fingerprinting and hash functions.
Lemma 7. For tuples ( f
1
,. .. , f
w
) and ( f
′
1
,. .. , f
′
w
)
that are sampled from D
0
w,b
uniformly and indepen-
dently, and for an integer i sampled uniformly from
[1,w],
1
2
1 −
T
0
w−1,b
T
0
w,b
!
≤ Pr[ f
i
< f
′
i
] <
1
2
.
Proof:
Observe first that
Pr[ f
i
< f
′
i
] = Pr[ f
i
> f
′
i
] =
1
2
1 − Pr[ f
i
= f
′
i
]
because the two tuples are sampled uniformly
and independently. The upper-bounding inequality
Pr[ f
i
< f
′
i
] < 1/2 follows since Pr[ f
i
= f
′
i
] > 0.
To discuss the lower-bounding inequality, notice
that
Pr[ f
i
= f
′
i
] =
b
∑
j=−b
(Pr[ f
i
= j])
2
≤ max(Pr[ f
i
= j])
b
∑
j=−b
Pr[ f
i
= j]
= max(Pr[ f
i
= j]).
We have Pr[ f
i
= j] = T
− j
w−1,b
/T
0
w,b
because the tuple
is sampled uniformly from D
0
w,b
.
It is verified that the maximum of Pr[ f
i
= j] is
given by Pr[ f
i
= 0] = T
0
w−1,b
/T
0
w,b
and consequently
Pr[ f
i
= f
′
i
] ≤ T
0
w−1,b
/T
0
w,b
, which brings the lower-
bounding inequality of this lemma □
Theorem 8. If f
w,b
is collision-resistant and h is one-
way and collision-resistant, then the proposed OTS
scheme is strongly existential unforgeable.
Proof:
It is shown that if there is a polynomial-time ad-
versary A
1
that wins the game of the strongly exis-
tential unforgeability with non-negligible probability,
then we can construct a polynomial-time algorithm
A
2
that succeeds in the attack on f
w,b
or h with non-
negligible probability. The algorithm A
2
is given a
target hash value y of the hash function h and attempts
to achieve either one of the following three goals.
Goal 1. A
2
finds a collision of f
w,b
.
Goal 2. A
2
finds the pre-image of the target hash
value y of h.
Goal 3. A
2
finds a collision of h.
The goal to be achieved depends on how A
1
wins
the game. To make this possible, the algorithm A
2
plays the role of the challenger of the game and let A
1
output (m
′
,σ
′
). If A
1
wins the game, then the signa-
ture σ contains essential information that allows A
2
to
achieve either one of three goals.
The algorithm A
2
performs the following steps for
a given target hash value y.
1. Run KeyGen algorithm and obtain a signing key
SK = (s
1
,. .. ,s
w
) and a verification key VK =
(v
1
,. .. ,v
w
), where v
i
= h
2b
(s
i
) for 1 ≤ i ≤ w.
2. Choose an integer α uniformly at random from
[1,w]. Also, choose a message randomly, compute
the zero-sum fingerprint for the randomly chosen
message, and let define β as the α-th component
of the computed zero-sum fingerprint (and hence
−b ≤ β ≤ b).
Then prepare a modified verification key VK
′
=
(v
′
1
,. .. ,v
′
w
) with
SECRYPT 2023 - 20th International Conference on Security and Cryptography
308

e
6
.
.
.
6
u
6
e
6
.
.
.
6
e
v
′
α
y = y
′
x
′
σ
′
α
6
?
β − f
′
α
(b)-i (b)-ii
e
6
.
.
.
6
e
6
X
X
X
Xy
e e
6 6
.
.
.
.
.
.
6 6
u e
6
.
.
.
6
e
y
′
σ
′
α
v
′
α
y ,
z z
′
6
?
6
?
j
β − f
′
α
Figure 2: Relation among hash values.
v
′
i
=
(
v
i
if i , α,
h
b−β
(y) if i = α,
by using the target hash value y, and provide this
modified verification key VK
′
to the adversary A
1
in the Setup phase of the game.
3. Receive a query message m from A
1
in the Query
phase.
4. Compute the zero-sum fingerprint ( f
1
,. .. , f
w
) =
f
w,b
(m) for the query message m. If f
α
< β, then
abort this attack as a failure because A
2
is not able
to compute the signature for m. If f
α
≥ β, then
compute σ = (σ
1
,. .. ,σ
w
) where
σ
i
=
(
h
f
i
+b
(s
i
) if i , α,
h
f
i
−β
(y) if i = α,
and return σ as the signature for the query mes-
sage m. Confirm that σ is a valid signature for m
with respect to the modified verification key VK
′
.
5. Receive (m
′
,σ
′
) from the adversary A
1
in the Out-
put phase, and do either (a), (b), or (c). In the fol-
lowing, we write σ
′
= (σ
′
1
,. .. ,σ
′
w
) and f
w,b
(m
′
) =
( f
′
1
,. .. , f
′
w
).
(a) If m , m
′
and f
w,b
(m) = f
w,b
(m
′
), then output
(m,m
′
) as the pair of messages that causes col-
lision of f
w,b
(Goal 1 is achieved in this case).
(b) If f
w,b
(m) , f
w,b
(m
′
) and f
′
α
< β, then compute
y
′
= h
β− f
′
α
(σ
′
α
) and do either i or ii. (see also
Fig. 2 which illustrates the relation among hash
values).
i. If y = y
′
, then output x
′
= h
β− f
′
α
−1
(σ
′
α
) as the
pre-image of the target hash value y (Goal 2 is
achieved in this case).
ii. If y , y
′
, then find j such that h
j
(y) , h
j
(y
′
)
and h
j+1
(y) = h
j+1
(y
′
), and output (z, z
′
) =
(h
j
(y),h
j
(y
′
)) as the pair of messages that
causes collision of h (Goal 3 is achieved in this
case).
(c) If none of the above conditions holds, then
abort this attack as a failure because σ
′
does
not give A
2
essential information.
There are two scenarios in which the adversary A
1
wins the game of strongly existential unforgeability.
In the scenario-A, the adversary A
1
finds a message
m
′
such that m
′
, m and f
w,b
(m
′
) = f
w,b
(m). In this
case, A
1
wins the game with the output (m
′
,σ). We
write p
A
for the probability that A
1
wins the game
with this scenario-A. In the scenario-B, the adversary
outputs (m
′
,σ
′
) such that f
w,b
(m
′
) , f
w,b
(m) and σ
′
is
a valid signature that is accepted by the Verify algo-
rithm. We write p
B
for the probability that A
1
wins
the game with this scenario-B.
If A
1
wins the game with non-negligible probabil-
ity, then at least one of p
A
and p
B
is non-negligible.
Now we analyze the probability that the algorithm
A
2
succeeds in the attack. The algorithm A
2
aborts at
step 4 if f
α
< β, but the probability of this happens
is less than 1/2 by Lemma 7. The algorithm thus
proceeds to step 5 with probability 1/2 or more and
receives an output from the adversary A
1
.
If the adversary A
1
wins the game with scenario-
A, then sub-step 5(a) is selected.
The overall probability that sub-step 5(a) is per-
formed in the algorithm is therefore p
A
/2 or more.
In this case, the algorithm A
2
outputs a pair of
messages that brings collision of the fingerprinting
function f
w,b
, and achieves Goal 1.
If the adversary A
2
wins the game with scenario-
B, then we have further two cases; f
′
α
< β or f
′
α
≥ β.
The lower-bound inequality of Lemma 7 implies that
the probability of f
′
α
< β is
1 − T
0
w−1,b
/T
0
w,b
/2
or more, and thus the overall probability that the
sub-step 5(b) is performed in the algorithm is
1
2
× p
B
×
1
2
1 −
T
0
w−1,b
T
0
w,b
!
or more.
If y
′
= h
β− f
′
α
(σ
′
α
) equals to the target hash value
y, then
we can find the pre-image of y by selecting the
hash value that is just before y in the hash chain, and
Goal 2 is achieved in this case.
If y , y
′
, then y is not contained in the hash chain
that originates from σ
′
α
, but the chain must converge
with the hash chain that originates from y at some
point up to v
′
α
.
Improvement of Winternitz OTS with a Novel Fingerprinting Function
309

Table 3: Parameters and costs of two OTS.
w key & sig. length Winternitz proposed
wL l KeyGen Sign Verify b KeyGen Sign Verify
55 14,080 32 1,705 852 852 14 1,540 770 770
45 11,520 64 2,835 1,417 1,417 29 2,610 1,305 1,305
39 9,984 128 4,953 2,476 2,476 55 4,290 2,145 2,145
34 8,704 256 8,670 4,335 4,335 113 7,684 3,842 3,842
Find hash values just before the converging point
of the two chains, and the values give the collision of
the hash function h. Goal 3 is achieved in this case.
In summary, the probability that A
2
achieves either
one of three goals is
1
2
p
A
+
p
B
2
1 −
T
0
w−1,b
T
0
w,b
!!
or more, which is non-negligible if A
1
wins the
game with non-negligible probability.
This brings a contradiction to our assumptions,
and it is concluded that there is no polynomial-
time algorithm like A
1
that wins the game with non-
negligible probability. □
6 COMPARISON OF
EFFICIENCY
This section is to compare the efficiency of Winternitz
OTS and the proposed OTS. For the fairness of com-
parison, we first need to set up the two OTS so that
they have the same security level.
Fortunately, both Winternitz OTS and the pro-
posed OTS are provably secure, and it is likely no
attacking method can do better than the exhaustive at-
tack. The security of the OTS is thus determined by
the bit length of the hash and fingerprinting functions.
We, therefore, consider Winternitz OTS and the pro-
posed OTS that are both set up for the same security
parameter n = 256 and consider to use the same hash
function that produces 256-bit hash values (L = 256).
Another point we need to remark on is that there is
a certain time-space trade-off in both Winternitz OTS
and the proposed OTS.
To avoid complications, we select parameter val-
ues so that the two OTS have the same key length
(the same signature length), and compare the costs for
KeyGen, Sign, and Verify.
Consider parameter values of Winternitz OTS that
have been shown in Tab. 1. For each value of w =
55,45, 39,34 in Tab. 1, we determined the value of b
that is necessary to make T
0
w,b
≥ 2
256
. Tab. 3 shows the
values of l and b, and the costs for three operations of
the two OTS, where average costs are shown for Sign
and Verify in Winternitz OTS.
We can see from the table that the proposed
scheme reduces by about 10% of the costs for opera-
tions in Winternitz OTS.
This improvement is made because the proposed
OTS uses shorter hash chains (length 2b) than Winter-
nitz OTS (length l −1), which is enabled by the use of
zero-sum fingerprints as a means to constitute a mutu-
ally unordered set. The set of zero-sum fingerprints is
“denser” than the set of check-summed fingerprints,
and short hash chains suffice to accommodate enough
fingerprints.
7 CONCLUSION
This study focused on the check-sum mechanism in
Winternitz OTS and characterized the security of the
scheme in terms of mutually unordered sets. Then
we investigated a zero-sum fingerprinting function as
a practical means to obtain fingerprints in a mutu-
ally unordered set. Investigations show that about a
10% reduction of the costs for operations is possible
by using the proposed OTS. We also showed that the
proposed scheme is strongly existential unforgeable
and thus has provable security, which is essential and
mandatory in the study of modern cryptology. These
results seem to suggest that there is little technical ad-
vantage in continuously using Winternitz OTS.
We also note that the approach taken in this study
is combinable with other investigations that try to
strengthen Winternitz OTS. For example, the pro-
posed zero-sum fingerprinting function can be in-
corporated in WOTS+(Hulsing, 2013), and in more
advanced scheme including SPHINCS+(Aumasson
et al., 2020), one of digital signature algorithms that
were selected in the PQC standardizations process of
NIST(Nat. Inst. of Standards and Technology, 2022).
REFERENCES
Aumasson, J., Daniel, J., et al. (2020). SPHINCS+. Sub-
mission to the NIST post-quantum project.
SECRYPT 2023 - 20th International Conference on Security and Cryptography
310

Bernstein, D., Hopwood, D., et al. (2015). SPHINCS: Prac-
tical stateless hash-based signatures. In EUROCRYPT
15, pages 368–397.
Bleichenbacher, D. and Maurer, U. (1996a). On the effi-
ciency of one-time digital signature schemes. In ASI-
ACRYPT 96, pages 145–158.
Bleichenbacher, D. and Maurer, U. (1996b). Optimal tree-
based one-time digital signature schemes. In Symp. on
Theoretical Aspects of Comp. Sci., pages 363–374.
Boneh, D., Shen, E., and Waters, B. (2006). Strongly un-
forgeable signatures based on computational diffie-
hellman. In Intl. Conf. on Theory and Practice of
Public-Key Crypto., pages 229–240.
Buchmann, J., Dahmen, E., et al. (2011a). On the secu-
rity of the Winternitz one-time signature scheme. In
AFRICACRYPT 11, pages 363–378.
Buchmann, J., Dahmen, E., and Hulsing, A. (2011b).
XMSS — a practical forward secure signature scheme
based on minimal security assumptions. In Intl. Conf.
on Post-Quantum Crypto., pages 117–129.
Dods, C., Smart, N., and Stam, M. (2005). Hash based
digital signature schemes. In Intl. Conf. on Crypto.
and Coding, pages 96–115.
Goldwasser, S. and Bellare, M. (2008). Lecture notes
on cryptography. https://cseweb.ucsd.edu/%7Emihir/
papers/gb.pdf (Accessed on Apr. 26, 2023).
Hulsing, A. (2013). W-OTS
+
— shorter signatures for
hash-based signature schemes. In AFRICACRYPT 13,
pages 173–188.
Kaji, Y., Cruz, J., and Yatani, Y. (2018). Hash-based signa-
ture with constant-sum fingerprinting and partial con-
struction of hash chains. In 15th Intl. Conf. on Security
and Crypto., pages 297–304.
Lamport, L. (1979). Constructing digital signatures from
a one-way function. Technical Report SRI-CSL-98,
SRI Intl. Computer Sci. Lab.
Merkle, R. (1989). A certified digital signature. In CRYPTO
89, pages 218–238.
Nat. Inst. of Standards and Technology (2022). NIST an-
nounces first four quantum-resistant cryptographic al-
gorithms. https://www.nist.gov/node/1699976 (Ac-
cessed on Apr. 26, 2023).
Perrig, A. (2001). The BiBa one-time signature and broad-
cast authentication protocol. In ACM Conf. on Com-
puter and Communications Security, pages 28–37.
Reyzin, L. and Reyzin, N. (2002). Better than BiBa: Short
one-time signatures with fast signing and verifying. In
Intl. Inf. Security and Privacy Conf., pages 1–47.
Shor, P. (1997). Polynomial-time algorithms for prime fac-
torization and discrete logarithms on a quantum com-
puter. SIAM J. of Computing, 26(5):1484–1509.
Improvement of Winternitz OTS with a Novel Fingerprinting Function
311
