
A Note on a CBC-Type Mode of Operation
George Tes¸eleanu
1,2 a
1
Advanced Technologies Institute, 10 Dinu Vintil
˘
a, Bucharest, Romania
2
Simion Stoilow Institute of Mathematics of the Romanian Academy, 21 Calea Grivitei, Bucharest, Romania
Keywords:
Mode of Operation, Cipher Block Chaining Mode, Block Cipher, Provable Security.
Abstract:
In this paper we formally introduce a novel mode of operation based on the cipher block chaining mode. The
main idea of this mode is to use a stateful block cipher instead of a stateless one. Afterwards, we show how to
implement our proposal and present a performance analysis of our mode. Next, we provide a concrete security
analysis by computing a tight bound on the success of adversaries based on their resources. The results of
our performance and security analyses are that this novel mode is more secure than the cipher block chaining
mode for large files, but the encryption/decryption time doubles/triples. Therefore, our novel mode is suitable
for encrypting large files, when higher security is required, but speed is not paramount. Note that the changes
required to transform the software implementations of the cipher block chaining mode into this new mode are
minimal, and therefore transitioning to this new mode is straightforward.
1 INTRODUCTION
One of the most popular classical mode of operation is
called Cipher Block Chaining (CBC) mode (Ehrsam
et al., 1978). The CBC mode is widespread and very
widely used, and therefore is standardised in (ISO,
2017; Dworkin, 2001; IEEE, 2018; IETF, 2003). Im-
plementations of CBC can be found in software li-
braries such as (Legion of the Bouncy Castle, 2023;
Trusted Firmware, 2023; Crypto++, 2022; OpenSSL
Technical Committee, 2023).
In this paper we introduce a novel CBC-based
mode of operation. More precisely, we use the CBC
mode with a stateful block cipher instead of a state-
less one. Specifically, rather of using the same key to
encrypt each block of data, we modify the key sched-
ule such that after generating the round keys neces-
sary for encryption it also generates an encryption
key
1
. Therefore, after encrypting the first block of
data, we memorize the encryption key generated by
the key schedule. The memorized key is then used to
encrypt the second block of data and the process is
repeated for the remaining blocks. After finishing all
the blocks, the key is reset to the original value and
the block cipher is now ready to encrypt the next set
a
https://orcid.org/0000-0003-3953-2744
1
Formed by concatenating one or more additional gen-
erated round keys depending on the size of the round and
encryption keys
of data. Note that resetting the key before each new
set of plaintexts avoids synchronisation problems.
After formalizing our novel CBC-based mode,
we provide some implementations details. We start
with describing two possible approaches for trans-
forming a stateless block cipher into a stateful one.
Since the second one is more suitable for all three ci-
phers implemented in Mbed TLS (Trusted Firmware,
2023), namely AES (Daemen and Rijmen, 2002),
ARIA (NSRI, 2005) and Camellia (Aoki et al., 2001),
we made the necessary implementation modifica-
tions needed to obtain a stateful cipher. To analyze
the performance of our mode, we also modified the
CBC implementation found in Mbed TLS (Trusted
Firmware, 2023). We observed that our mode’s en-
cryption/decryption time is two/three times slower
than that of classical CBC.
In the last part of the paper, we provide a tight
security bound. To achieve this we first compute an
upper bound and then we devise an attack that has a
success probability close to this bound. Therefore,
there is no significantly better bound than the one
given in this paper. Based on this security bound, we
conclude that this mode is more secure than CBC for
large files. Since modifying existing CBC implemen-
tations to use a stateful block cipher is straightfor-
ward, we recommend switching to this novel mode
for large files, when the additional processing time
does not lead to bottlenecks. An example of such a
Teŧeleanu, G.
A Note on a CBC-Type Mode of Operation.
DOI: 10.5220/0012059100003555
In Proceedings of the 20th International Conference on Security and Cryptography (SECRYPT 2023), pages 353-360
ISBN: 978-989-758-666-8; ISSN: 2184-7711
Copyright
c
2023 by SCITEPRESS – Science and Technology Publications, Lda. Under CC license (CC BY-NC-ND 4.0)
353

use case is the following: suppose you want to store
some sensitive data that is rarely accessed, such as
backup copies of surveillance footage. In this case,
the data is not accessed frequently, so the speed of ac-
cessing it is not crucial. However, security is essential
to ensure the confidentiality of the data.
Full Version. The full version of the paper can be
found here (Tes¸eleanu, 2023).
Structure of the Paper. We introduce notations and
definitions used throughout the paper in Section 2. In
Section 3 we formalize the Running Key CBC mode
of operation. Implementation details and a security
analysis are provided in Sections 4 and 5. We con-
clude in Section 6.
2 PRELIMINARIES
Notations and Conventions. Throughout the paper
|b| will denote the bit size of b and ⊕ the bitwise xor
operation. By x∥y we understand the concatenation
of the strings x and y. Also, we define 0
s
and 1
s
as a
string of s zeros and ones, respectively. We use the no-
tation x
$
←−X when selecting a random element x from
a sample space X . We denote by x ←y the assignment
of the value y to the variable x. The probability that
event E happens is denoted by Pr[E]. Hexadecimal
strings are marked by the prefix 0x. The most ℓ sig-
nificant bits of Q are denoted by MSB
ℓ
(Q).
For all complexity measures we work in the ran-
dom access model and all the adversaries are prob-
abilistic polynomial time machines (PPT). When we
talk about the running time of an opponent, we will in-
clude the actual running time plus the length of the ad-
versary’s description (i.e. the length of the random ac-
cess machine program that describes the adversary).
Also, queries are answered in one unity of time.
2.1 PRF/PRP
We start by defining the security notions commonly
used to quantify the security of a block cipher (Rog-
away, 2011) and then we provide the link between the
two notions (Bellare and Rogaway, 2006).
Definition 2.1 (Pseudorandom Function - PRF, Pseu-
dorandom Permutation - PRP). A function F :
{0,1}
n
× {0, 1}
k
→ {0,1}
n
is a PRF or PRP if for
any PPT algorithm A which makes at most q oracle
queries, the following advantages
ADV
PRF
F
(A) =
Pr[A
F
K
(·)
= 1|K
$
←− {0,1}
k
]
−Pr[A
ρ(·)
= 1|ρ
$
←− F ]
,
ADV
PRP
F
(A) =
Pr[A
F
K
(·)
= 1|K
$
←− {0,1}
k
]
−Pr[A
π(·)
= 1|π
$
←− P ]
are negligible, where F
K
(X) = F(X, K), and F and P
denote the sets of all functions and permutations from
n-bit strings to n-bit strings.
Lemma 2.1 (PRP/PRF Switching Lemma). Let F :
{0,1}
n
×{0,1}
k
→ {0,1}
n
be a function. Also, let
A be an adversary that asks at most q oracle queries.
Then
Pr[A
ρ(·)
= 1|ρ
$
←− F ] −Pr[A
π(·)
= 1|π
$
←− P ]
≤
q(q −1)
2
n+1
.
As a consequence, we have that
ADV
PRF
F
(A) −ADV
PRP
F
(A)
≤
q(q −1)
2
n+1
.
2.2 Symmetric Key Encryption
We further define symmetric key encryption schemes
(Bellare and Rogaway, 2005) and provide one of the
security notions commonly used to model chosen-
plaintext attacks (Bellare and Rogaway, 2006; Rog-
away, 2011).
Definition 2.2 (Symmetric Key Encryption - SKE). A
symmetric key encryption (SKE) scheme usually con-
sists of three PPT algorithms: Setup, Encrypt and De-
crypt. The Setup algorithm takes as input a security
parameter and outputs the secret key. Encrypt takes
as input the secret key and a message and outputs
the corresponding ciphertext. The Decrypt algorithm
takes as input the secret key and a ciphertext and out-
puts either a valid message or an invalidity symbol (if
the decryption failed).
Definition 2.3 (Indistinguishability under Chosen
Plaintext Attacks - IND-CPA). The security model
against chosen plaintext attacks for a SKE scheme S E
is captured in the following game:
Setup(λ): The challenger C generates the secret key
K
$
←− {0, 1}
k
and a bit b
$
←− {0, 1}.
Queries: Adversary A sends C two messages
m
0
,m
1
∈ {0, 1}
∗
of the same length. The chal-
lenger encrypts m
b
and obtains the ciphertext c
b
=
S E(m
b
,K). The value c
b
is sent to the adversary.
Guess: After making a polynomial number of
queries, the adversary outputs a guess b
′
∈ {0, 1}.
He wins the game, if b
′
= b.
SECRYPT 2023 - 20th International Conference on Security and Cryptography
354
The advantage of an adversary A which runs in time
t, makes at most q oracle queries, these totaling σ bits
and is attacking a SKE scheme is defined as
ADV
IND-CPA
S E
(A) = |2Pr[b = b
′
] −1|
where the probability is computed over the random
bits used by C and A. A SKE scheme is IND-CPA
secure, if for any PPT adversary A the advantage
ADV
IND-CPA
S E
(A) is negligible.
We further present the CBC encryption algorithm
in Algorithm 1 and then we present its security mar-
gins as stated in (Rogaway, 2011; Bellare and Rog-
away, 2005). Let K be an k-bit random key, P a plain-
text and C a ciphertext.
Algorithm 1: CBC Mode of Operation.
1 Function Encrypt(P, K):
2 if |P| mod n ̸≡ 0 or |P| = 0 then return ⊥;
3 P
1
∥. ..∥P
m
← P where |P
i
| = n;
4 IV
$
←− {0,1}
n
and C
0
← IV ;
5 foreach i ∈[1,m] do C
i
← E
K
(P
i
⊕C
i−1
) ;
6 C ←C
1
∥. ..∥C
m
;
7 Function Decrypt(IV , C, K):
8 if |C| mod n ̸≡0 or |C| = 0 then return ⊥;
9 C
1
∥. ..∥C
m
←C where |C
i
| = n;
10 C
0
← IV ;
11 foreach i ∈[1,m] do P
i
← E
−1
K
(C
i
) ⊕C
i−1
;
12 P ←P
1
∥. ..∥P
m
;
Theorem 2.2 (Upper Bound on Security of CBC Mode
Using a Block Cipher). Let E : {0, 1}
n
×{0,1}
k
→
{0,1}
n
be a block cipher. Let A be a PPT adversary
against the IND-CPA security of CBC that runs at most
time t and queries at most σ n-bit blocks. Then there
exists an adversary B against the PRP security of E
such that
ADV
IND-CPA
CBC
(A) ≤ ADV
PRP
E
(B) +
2σ
2
2
n
,
and where B makes at most σ queries and runs in time
at most t + O(nσ).
Theorem 2.3 (Lower Bound on Security of CBC
Mode Using a Block Cipher). Let E : {0,1}
n
×
{0,1}
k
→ {0,1}
n
be a block cipher and let σ ∈
[1,
√
2
n+1
]. Then there exists an adversary A against
the IND-CPA security of CBC such that
ADV
IND-CPA
CBC
(A) ≥
0.15σ
2
2
n
,
and which asks one query consisting of σ n-bit blocks
and runs in time at most O(nσ logσ).
3 RUNNING KEY CBC SKE
Let E : {0,1}
n
× {0, 1}
k
→ {0,1}
n
be a block ci-
pher. Instantiating the running key CBC (denoted
RK-CBC) with E and with a random initialisation
vector (denoted IV ) leads to a stateless symmetric en-
cryption scheme. Let K
f
= {K
i
}
i>0
be a family of
distinct k-bit random keys, P a plaintext and C a ci-
phertext. We present in Algorithm 2 the exact detail
of RK-CBC.
Algorithm 2: Running Key CBC Mode of Opera-
tion.
1 Function Encrypt(P, K
f
):
2 if |P| mod n ̸≡ 0 or |P| = 0 then return ⊥;
3 P
1
∥. ..∥P
m
← P where |P
i
| = n;
4 IV
$
←− {0,1}
n
and C
0
← IV ;
5 foreach i ∈[1,m] do C
i
← E
K
i
(P
i
⊕C
i−1
) ;
6 C ←C
1
∥. ..∥C
m
;
7 Function Decrypt(IV , C, K
f
):
8 if |C| mod n ̸≡0 or |C| = 0 then return ⊥;
9 C
1
∥. ..∥C
m
←C where |C
i
| = n;
10 C
0
← IV ;
11 foreach i ∈[1,m] do P
i
← E
−1
K
i
(C
i
) ⊕C
i−1
;
12 P ←P
1
∥. ..∥P
m
;
4 IMPLEMENTATION DETAILS
When studying the security of iterated block ciphers
(Lai et al., 1991), it is assumed that the cipher’s round
sub-keys are independent. This assumption is reason-
able in practice (Biham and Shamir, 1991; Knudsen
and Mathiassen, 2004; Vaudenay, 2005). Using this
assumption, we can transform a stateless block cipher
into a stateful one using two methods.
In the first method we simply memorize the initial
key into a buffer and then we continuously run the key
schedule algorithm until all data blocks are encrypted
(see Figure 1). More precisely, for an r round cipher
2
and an m block plaintext the key schedule algorithm
will generate (r + 1)m keys. Since we assumed that
the round sub-keys are independent, we obtain m in-
dependent instantiations of the iterated block cipher.
Therefore, we can use it to implement the RK-CBC
mode. Unfortunately, not all key schedules can be
easily modified to support continuous generation. For
example, the AES (Daemen and Rijmen, 2002) and
ARIA (NSRI, 2005) key schedules support this out of
the box, but for the Camellia (Aoki et al., 2001) key
schedule we could not devise a suitable modification.
In the second method we modify the key schedule
to generate a few additional round keys after comput-
ing the round keys needed for encryption. Then we
concatenate the additional round keys to obtain a new
encryption key, that is used to encrypt the next block
of data. The process continues until all blocks are pro-
2
We consider that an r round cipher uses r+1 sub-keys.
A Note on a CBC-Type Mode of Operation
355

ENC
P
1
KS
...
C
1
k
1
k
r+1
state
1
ENC
P
2
KS
...
C
2
k
r+2
k
2r+1
state
2
ENC
P
3
KS
...
C
3
k
2r+2
k
3r+1
K
1
IV
Figure 1: The First Method for Implementing RK-CBC
when m = 3.
cessed. For example, if n = k we generate only one
additional round key k
r+2
and set K
2
= k
r+2
(see Fig-
ure 2).
3
If n = 2k we have to generate two additional
round keys k
r+2
,k
r+3
and set K
2
= k
r+2
∥k
r+3
. Using
this method we managed to modify all three block ci-
phers implemented in Mbed TLS (Trusted Firmware,
2023). The technical details of the changes can be
found in (Tes¸eleanu, 2023).
ENC
P
1
KS
...
C
1
k
1
k
r+1
k
r+2
ENC
P
2
KS
...
C
2
k
1
k
r+1
k
r+2
ENC
P
3
KS
...
C
3
k
1
k
r+1
K
2
K
3
K
1
IV
Figure 2: The Second Method of Implementing RK-CBC
when m = 3 and n = k.
Taking into account the above discussions, we can
transform a CBC implementation into a RK-CBC one
by simply resetting the key before encrypting each
block of plaintexts and by using either stateful block
cipher described above. Note that, compared to CBC,
RK-CBC needs an extra buffer to memorize the initial
key.
Let t
ks
be the time needed run the key schedule
once and t
enc
be the time needed to compute a block
cipher encryption without taking into account t
ks
. In
terms of performance, the time required to encrypt an
m-block of data using CBC is O(m ·t
enc
).
4
On the
other hand, the time required by the RK-CBC is O(m ·
(t
ks
+ t
enc
)). Therefore, CBC is O((t
ks
+ t
enc
)/t
enc
)
faster than RK-CBC.
To compute the exact slowdown for Mbed TLS
(Trusted Firmware, 2023), we implemented the RK-
CBC mode and run the Mbed TLS benchmark pro-
gram on a CPU Intel i7-4790 4.00 GHz. Note that to
compute the rate of kilobytes per second, Mbed TLS
first sets an internal alarm to 1 second and then in-
crements a counter for each 1024 bytes block that is
3
Figures 1 and 2 are based on the TikZ found in
(Maimut¸, 2017).
4
Usually, the key schedule is run once at the beginning
and the round keys memorized for the duration of encryp-
tion, and thus t
ks
can be ignored.
processed, until the alarm is set off. The counter rep-
resents the given rate. In the case of the cycle per
byte rate, the benchmark program computes the num-
ber of cycles needed to process 1024 blocks of size
1024 bytes. Then it divides the resulting number by
1024 ·1024 and outputs the rate. The results of our
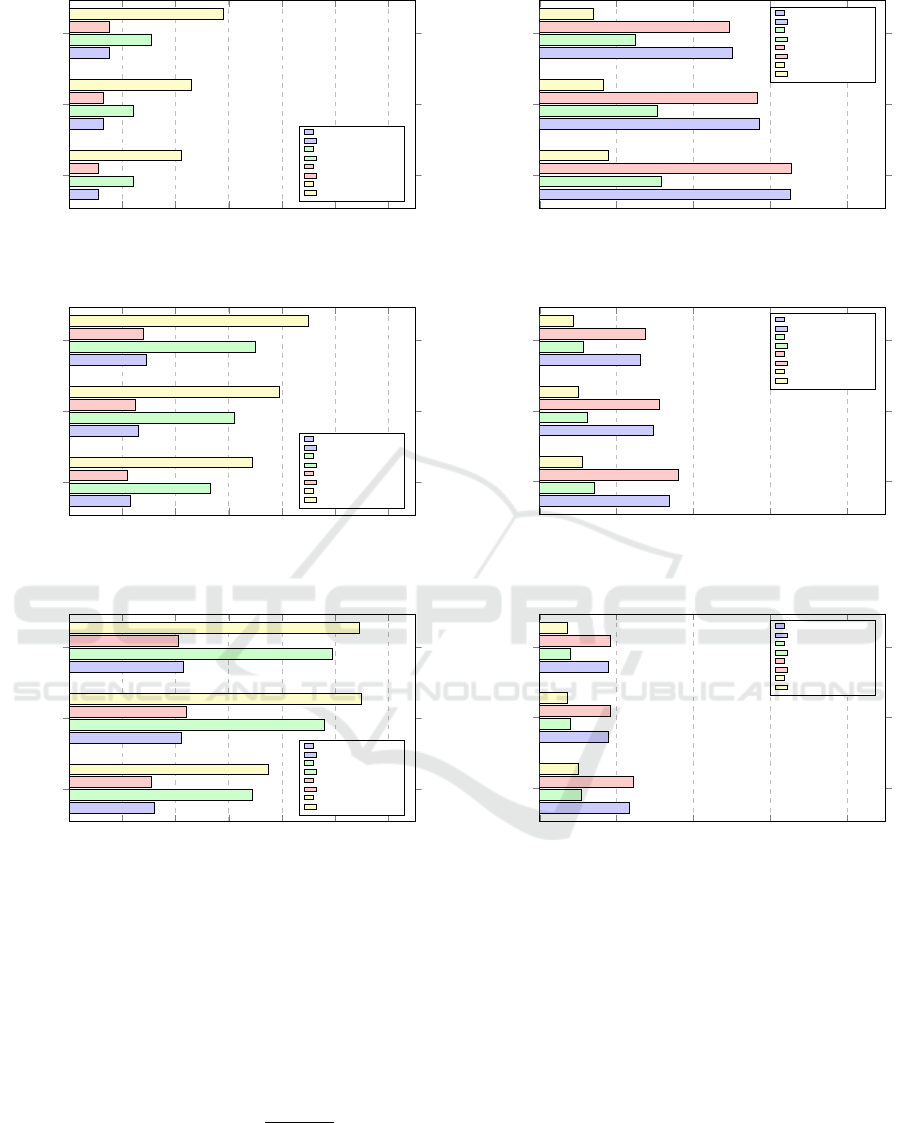
experiments can be found in Figure 3 to 8. Compared
to RK-CBC encryption/decryption, classical CBC en-
cryption is 2x/3.5x faster for AES
5
, 2.3x/3.2x faster
for ARIA and 2.2x/2.5x faster for Camellia.
We also carried a series of experiments to test
the validity of our assumption (i.e. the generated
key bits are independent and identically distributed).
Therefore, we set K
1
as either 0
s
or 1
s
, where s =
128/192/256 and we generated K
2
,K
3
... using the
second method. Then we applied the NIST test suite
(Turan et al., 2018; NIST, 2023) to check if the key
bits of K
2
,K
3
... are independent and identically dis-
tributed. We obtained that the samples pass all the
statistical tests, and have an entropy of 0.99 per bit
and 7.9 per byte. Thus, based on the results of the
experiments we conducted, we can safely assume the
generated keys are random and mutually independent.
5 SECURITY ANALYSIS
Before starting our analysis, some notations are re-
quired. Therefore, A will denote a PPT algorithm
which makes at most q oracle queries, these totaling at
most σ n-bit blocks, unless mentioned otherwise. Let
σ
′
= σ −q +1 and σ = αq + r, where r < q. For sim-
plicity, we denote by ρ
f
the oracle that responds to a
query of type (i,X) with ρ
i
(X), where {ρ
i
}
i∈[1,σ
′
]
is a
family of distinct random functions. Similarly, we de-
note by π
f
the oracle that responds with π
i
(X), where
{π
i
}
i∈[1,σ
′
]
is a family of distinct random permuta-
tions. Lastly, we denote by F
f
the oracle that responds
with F
K
i
(X
i
), where {K
i
}
i∈[1,σ
′
]
is a family of distinct
random k-bit keys and F : {0,1}
n
×{0,1}
k
→{0,1}
n
is a function.
For simplicity, we further assume that adversary
A never asks a query that is not composed of n-bit
blocks. In our case, queries that do not satisfy this
restriction generate error messages, and thus they are
pointless for A.
Now, we start our security analysis (see
(Tes¸eleanu, 2023) for the proofs) by first study-
ing the security of the RK-CBC mode instantiated
with random functions ρ
i
from F instead of E
K
i
. We
denote this version by RK-CBC(ρ
f
). Note that in
5
Note that we deactivated the AES-NI instructions for a
fair performance between the three block ciphers.
SECRYPT 2023 - 20th International Conference on Security and Cryptography
356
0 20 40
60
80 100 120
128
192
256
cycles/byte
key size
Enc CBC
Enc RK-CBC
Dec CBC
Dec RK-CBC
Figure 3: AES performance.
0 20 40
60
80 100 120
128
192
256
cycles/byte
key size
Enc CBC
Enc RK-CBC
Dec CBC
Dec RK-CBC
Figure 4: ARIA performance.
0 20 40
60
80 100 120
128
192
256
cycles/byte
key size
Enc CBC
Enc RK-CBC
Dec CBC
Dec RK-CBC
Figure 5: Camellia performance
this case, the decryption algorithm returns ⊥ with
probability 1 −2
−n
, since it does not have a correct
decryption property.
Lemma 5.1 (Upper Bound on Security of RK-CBC
Mode Using a Random Function). Let A be a PPT
adversary against the IND-CPA security of the RK-
CBC(ρ
f
) mode. Then
ADV
IND-CPA
RK-CBC(ρ
f
)
(A) ≤
αq
2
+ r
2
2
n
.
In order to make the switch from random function
to random permutation we need an equivalent of the
Switching Lemma (Lemma 2.1). We also introduce
an equivalent of Definition 2.1 that will be useful later.
0 1 2 3 4
·10
5
128
192
256
kilobytes/second
key size
Enc CBC
Enc RK-CBC
Dec CBC
Dec RK-CBC
Figure 6: AES performance.
0 1 2 3 4
·10
5
128
192
256
kilobytes/second
key size
Enc CBC
Enc RK-CBC
Dec CBC
Dec RK-CBC
Figure 7: ARIA performance.
0 1 2 3 4
·10
5
128
192
256
kilobytes/second
key size
Enc CBC
Enc RK-CBC
Dec CBC
Dec RK-CBC
Figure 8: Camellia performance.
Definition 5.1 (Family of Pseudorandom Functions
- F-PRF, Family of Pseudorandom Permutation -
F-PRP). A function F : {0,1}
n
×{0,1}
k
→ {0,1}
n
is
a F-PRF or F-PRP if for any PPT algorithm A which
makes at most q oracle queries of type (i,·), these to-
taling at most σ n-bit blocks, the following advantages
ADV
F-PRF
F
(A) =
Pr[A
F
f
(·)
= 1|K
i
$
←− {0,1}
k
]
−Pr[A
ρ
f
(·)
= 1|ρ
i
$
←− F ]
,
ADV
F-PRP
F
(A) =
Pr[A
F
f
(·)
= 1|K
i
$
←− {0,1}
k
]
−Pr[A
π
f
(·)
= 1|π
i
$
←− P ]
are negligible.
A Note on a CBC-Type Mode of Operation
357

Remark. Note that when q = σ the F-PRF/F-PRP se-
curity notions are identical to the PRF/PRP ones.
Lemma 5.2 (F-PRP/F-PRF Switching Lemma). Let A
be an adversary that asks at most q oracle queries,
these totaling at most σ n-bit blocks. Then
Pr[switch] =
Pr[A
ρ
f
(·)
= 1|ρ
i
$
←− F ] −Pr[A
π
f
(·)
= 1|π
i
$
←− P ]
≤
0.5(αq
2
+ r
2
)
2
n
.
As a consequence, we have that
ADV
F-PRF
F
(A) −ADV
F-PRP
F
(A)
≤
0.5(αq
2
+ r
2
)
2
n
.
We further apply Lemma 5.2 to see what happens
if we use random permutations instead random func-
tion when instantiating the RK-CBC mode. We de-
note this version by RK-CBC(π
f
).
Corollary 5.2.1 (Upper Bound on Security of
RK-CBC Mode Using a Random Permutation). Let
A be a PPT adversary against the IND-CPA security of
the RK-CBC(π
f
) mode. Then
ADV
IND-CPA
RK-CBC(π
f
)
(A) ≤
2(αq
2
+ r
2
)
2
n
.
Theorem 5.3 (Upper Bound on Security of RK-CBC
Mode Using a Block Cipher). Let E : {0,1}
n
×
{0,1}
k
→ {0,1}
n
be a block cipher. Let A be a PPT
adversary against the IND-CPA security of RK-CBC
that runs at most time t. Then there exists an adver-
sary B against the F-PRP security of E such that
ADV
IND-CPA
RK-CBC
(A) ≤ ADV
F-PRP
E
(B) +
2(αq
2
+ r
2
)
2
n
,
and where B makes at most q queries of type (i,·) and
runs in time at most t + O(nσ).
Corollary 5.3.1 (Simplified Upper Bound on Security
of RK-CBC Mode Using a Block Cipher). Let E :
{0,1}
n
×{0,1}
k
→ {0,1}
n
be a block cipher. Let A
be a PPT adversary against the IND-CPA security of
RK-CBC that runs at most time t. Then there exists
an adversary B against the F-PRP security of E such
that
ADV
IND-CPA
RK-CBC
(A) ≤ ADV
F-PRP
E
(B) +
2qσ
2
n
,
and where B makes at most q queries of type (i,·) and
runs in time at most t + O(nσ).
We further provide an attack that gives A an ad-
vantage of around (αq
2
+ r
2
)/2
n
to break the IND-
CPA security of RK-CBC. This implies that there is no
significantly better bound than the one given in Theo-
rem 5.3 .
Theorem 5.4 (Lower Bound on Security of RK-CBC
Mode Using a Block Cipher). Let E : {0,1}
n
×
{0,1}
k
→ {0,1}
n
be a block cipher and let q ∈
[1,
√
2
n+1
]. Then there exists an adversary A against
the IND-CPA security of RK-CBC such that
ADV
IND-CPA
RK-CBC
(A) ≥
0.15(αq
2
+ r
2
)
2
n
,
and runs in time at most O(n(αq logq + r logr)).
Proof. Adversary A makes q queries of type (Z
i
,R
i
),
where for i ∈ [1, r] we have Z
i
← 0
n(α+1)
and R
i
$
←−
{0,1}
n(α+1)
, and otherwise we have Z
i
← 0
nα
and
R
i
$
←− {0,1}
nα
. If there exists two distinct queries q
i
and q
j
such that blocks v received from the challenger,
denoted B
v
(q
i
) and B
v
(q
j
), are identical then A selects
lexicographically the first such (q
i
,q
j
,v) and output 1
if B
v+1
(q
i
) ̸= B
v+1
(q
j
). Note that the running time of
A is dominated by the running time needed to sort the
data received from each oracle, and thus we obtain a
running time of O(n(αq logq + r logr)).
When b = 0, adversary A queries identical blocks,
and thus if a collision of type B
v
(q
i
) = B
v
(q
j
) occurs
we always have B
v+1
(q
i
) = B
v+1
(q
j
). Therefore, we
always have
Pr[A
RK-CBC(·)
= 1|b ←0] = 0,
and hence
ADV
IND-CPA
RK-CBC
(A) = Pr[A
RK-CBC(·)
= 1|b ←1].
When b = 1, encrypting a random block of data
using RK-CBC results in another block of random
data, since the image of a uniformly selected value
under a permutation remains uniform. Therefore,
we can apply the birthday paradox to compute the
probability of obtaining B
v
(q
i
) = B
v
(q
j
). The para-
dox states that the probability of obtaining a colli-
sion when making Q ∈ {q, r} queries to oracle v ∈
[1,α + 1] is at least 0.3Q
2
/2
n
, when Q ∈ [1,
√
2
n+1
].
Also, note that since B
v+1
(q
i
) and B
v+1
(q
j
) are ran-
dom, the probability of having B
v+1
(q
i
) = B
v+1
(q
j
) is
1/2
n
. Hence, we obtain that
Pr[A
RK-CBC(·)
= 1|b ←1] ≥
α
0.3q
2
2
n
+
0.3r
2
2
n
1 −
1
2
n
≥
0.15(αq
2
+ r
2
)
2
n
,
as desired.
5.0.1 CBC vs. RK-CBC
To better understand the security gap between the two
modes we further consider two scenarios. In the first
SECRYPT 2023 - 20th International Conference on Security and Cryptography
358

0
0.5
1
·10
20
0
0.5
1
·10
20
0
1
2
·10
29
q
c
c (bytes)
q
rk
Figure 9: The curve q
rk
= q
c
p
c/n when n = 16 bytes.
scenario we assume that we can only encrypt blocks
of data of a fixed size c = d ·n, where d > 0. There-
fore, the data requirement for both modes is σ = q ·d.
According to Theorem 2.2 we obtain
ADV
IND-CPA
CBC
(A) ≤ ADV
PRP
E
(B) +
2q
2
d
2
2
n
,
and to Theorem 5.3
ADV
IND-CPA
RK-CBC
(A) ≤ ADV
F-PRP
E
(B) +
2q
2
d
2
n
.
Therefore, the free term for RK-CBC is d times better
than the one for CBC. Hence, to obtain the same se-
curity margin we have to set the number of RK-CBC
queries to q
rk
= q
c
√
d (see Figure 9), where q
c
is the
number of CBC queries.
For example, if we consider TLS packages of
maximum record size 16 Kilobytes we obtain that
d = 1000, which means that we have to make 31x
more queries for RK-CBC. If restrict to encrypting
DVDs, we have that c = 4.37 Gibibytes and d ≃ 2
28
,
and thus we have to make 2
14
times more queries for
RK-CBC. Since RK-CBC is slower than CBC (see
Section 4) we consider that the security advantage be-
comes relevant only for large files (e.g. DVDs, Blu-
rays).
In the second scenario we consider that we can
encrypt files of any size. Let σ
c
and σ
rk
be the
data requirements from Theorem 2.2 and Corol-
lary 5.3.1. Then the security margins presented in
Corollary 5.3.1 coincide with the ones from Theo-
rem 2.2 only if σ
2
c
= q
rk
σ
rk
(see Figure 10). If we con-
sider that σ
c
= σ
rk
= σ, then we obtain that q
rk
= σ
. In this case, the only difference is that instead of
asking one query consisting of σ blocks (see Theo-
rem 2.2) we have to ask σ queries each consisting of
one block (see Corollary 5.3.1). One consequence of
this is that if we have an IND-CPA attacker for RK-
CBC that asks σ queries, then we can use this at-
tacker to break the IND-CPA security of CBC. More
precisely, we only send messages of one block to the
CBC oracle, forward the challenges to the RK-CBC
attacker and output the bit computed by the RK-CBC
attacker. The converse is not true. We can also con-
sider the other extreme case q
rk
= 1. This leads to
σ
rk
= σ
2
c
. Therefore, if we want to make one query as
in the case of CBC, we need σ
c
times more data for
RK-CBC.
6 CONCLUSIONS
In this work we presented a novel CBC-based mode
of operation. Then we provided some implementa-
tion details and a performance analysis. Finally, we
proved its security by giving an upper bound to poly-
nomial adversaries and, moreover, we showed that
this bound is the best possible, by showing a matching
attack.
Let σ
c
be the data requirements from Theo-
rem 2.2, and let σ
rk
and q
rk
be the data and query
requirements from Corollary 5.3.1. From the security
analysis we can see that to match the IND-CPA upper
limit of CBC we need to have σ
2
c
= q
rk
σ
rk
. Therefore,
an IND-CPA adversary against the RK-CBC mode re-
quires either more data or more queries. Since obtain-
ing legitimate ciphertexts is problematic in practice,
we obtain that the RK-CBC is more secure that CBC.
Therefore, because converting existing CBC imple-
mentations into RK-CBC ones is straightforward and
due to the speed penalty incurred by RK-CBC, we
recommend using this novel mode instead of CBC
for encrypting large files when processing time is not
paramount.
0
0.5
1
·10
20
0
0.5
1
·10
20
0
0.5
1
·10
20
q
rk
σ
rk
σ
c
Figure 10: The curve σ
c
=
√
q
rk
σ
rk
.
A Note on a CBC-Type Mode of Operation
359

REFERENCES
Aoki, K., Ichikawa, T., Kanda, M., Matsui, M., Moriai,
S., Nakajima, J., and Tokita, T. (2001). Specifica-
tion of Camellia - A 128-bit Block Cipher. Technical
report, Nippon Telegraph and Telephone Corporation
and Mitsubishi Electric Corporation.
Bellare, M. and Rogaway, P. (2005). Introduction to Mod-
ern Cryptography. UCSD CSE.
Bellare, M. and Rogaway, P. (2006). The Security of Triple
Encryption and a Framework for Code-Based Game-
Playing Proofs. In EUROCRYPT 2006, volume 4004
of Lecture Notes in Computer Science, pages 409–
426. Springer.
Biham, E. and Shamir, A. (1991). Differential Cryptanal-
ysis of DES-like Cryptosystems. In CRYPTO 1990,
volume 537 of Lecture Notes in Computer Science,
pages 2–21. Springer.
Crypto++ (2022). Crypto++ Library. https://www.cryptopp.
com/.
Daemen, J. and Rijmen, V. (2002). The Design of Rijndael.
Springer.
Dworkin, M. (2001). Recommendation for Block Cipher
Modes of Operation: Methods and Techniques. Tech-
nical report, NIST Special Publication 800-38A.
Ehrsam, W. F., Meyer, C. H., Smith, J. L., and Tuchman,
W. L. (1978). Message Verification and Transmission
Error Detection by Block Chaining. US Patent No.
4,074,066.
IEEE (2018). IEEE Standard for Authenticated Encryption
with Length Expansion for Storage Devices. IEEE
Standard No. 1619.1.
IETF (2003). The AES-CBC Cipher Algorithm and Its Use
with IPsec. IETF Standard No. RFC3602.
ISO (2017). Information Technology - Security Tech-
niques - Modes of Operation for an n-bit Block Ci-
pher. ISO/IEC Standard No. 10116:2017.
Knudsen, L. R. and Mathiassen, J. E. (2004). On the Role of
Key Schedules in Attacks on Iterated Ciphers. In ES-
ORICS 2004, volume 3193 of Lecture Notes in Com-
puter Science, pages 322–334. Springer.
Lai, X., Massey, J. L., and Murphy, S. (1991). Markov Ci-
phers and Differential Cryptanalysis. In EUROCRYPT
1991, volume 547 of Lecture Notes in Computer Sci-
ence, pages 17–38. Springer.
Legion of the Bouncy Castle (2023). Bouncy Castle. https:
//www.bouncycastle.org/.
Maimut¸, D. (2017). TikZ for Cryptographers. https://www.
iacr.org/authors/tikz/.
NIST (2023). NIST SP 800-90B: Recommendation for
the Entropy Sources Used for Random Bit Gen-
eration. https://github.com/usnistgov/SP800-90B
EntropyAssessment.
NSRI (2005). Specification of ARIA. Technical report,
National Security Research Institute.
OpenSSL Technical Committee (2023). OpenSSL. https:
//www.openssl.org/.
Rogaway, P. (2011). Evaluation of Some Blockcipher
Modes of Operation. Technical report, Cryptography
Research and Evaluation Committees (CRYPTREC)
for the Government of Japan.
Tes¸eleanu, G. (2023). A Note on a CBC-Type Mode of Op-
eration. IACR Cryptology ePrint Archive, 2023/599.
Trusted Firmware (2023). Mbed TLS. https://tls.mbed.org/.
Turan, M. S., Barker, E., Kelsey, J., McKay, K., Baish, M.,
and Boyle, M. (2018). NIST SP 800-90B: Recom-
mendation for the Entropy Sources Used for Random
Bit Generation. Technical report, National Institute of
Standards and Technology.
Vaudenay, S. (2005). A Classical Introduction to Cryp-
tography: Applications for Communications Security.
Springer Science & Business Media.
SECRYPT 2023 - 20th International Conference on Security and Cryptography
360
