
Griffin: Towards Mixed Multi-Key Homomorphic Encryption
Thomas Schneider
a
, Hossein Yalame
b
and Michael Yonli
ENCRYPTO Group, Technical University of Darmstadt, Darmstadt, Germany
Keywords:
Secure Computation, Multi-Key Homomorphic Encryption.
Abstract:
This paper presents Griffin, an extension of the mixed-scheme single-key homomorphic encryption framework
Pegasus (Lu et al., IEEE S&P’21) to a Multi-Key Homomorphic Encryption (MKHE) scheme with applica-
tions to secure computation. MKHE is a generalized notion of Homomorphic Encryption (HE) that allows
for operations on ciphertexts encrypted under different keys. However, an efficient approach to evaluate both
polynomial and non-polynomial functions on encrypted data in MKHE has not yet been developed, hindering
the deployment of HE to real-life applications. Griffin addresses this challenge by introducing a method for
transforming between MKHE ciphertexts of different schemes. The practicality of Griffin is demonstrated
through benchmarks with multiple applications, including the sorting of sixty four 45-bit fixed point numbers
with a precision of 7 bits in 21 minutes, and evaluating arbitrary functions with a one-time setup communica-
tion of 1.4 GB per party and 2.34 MB per ciphertext. Moreover, Griffin could compute the maximum of two
numbers in 3.2 seconds, a 2× improvement over existing MKHE approaches that rely on a single scheme.
1 INTRODUCTION
As data collection reaches unprecedented volumes
and consumer awareness and apprehension regard-
ing the usage of their personal information grow,
the implementation of efficient privacy protection
measures gets more and more important. Secure
multi-party computation techniques (MPC) (Yao,
1986; Goldreich et al., 1987) allow to address this
problem efficiently in a variety of real-world applica-
tions, including privacy-preserving machine learning
(PPML) (Riazi et al., 2018; Boemer et al., 2020;
Patra et al., 2021a; Br
¨
uggemann et al., 2023), cluster-
ing (Hegde et al., ; Keller et al., 2021), and federated
learning (Nguyen et al., 2022; Fereidooni et al., 2021;
Gehlhar et al., 2023). One promising approach is
Homomorphic Encryption (HE), which allows for
performing arbitrary computations over encrypted
data. HE has been used as a building block in various
applications such as PPML (Juvekar et al., 2018;
Boemer et al., 2020; Mishra et al., 2020). Compared
to traditional MPC methods, HE-based methods have
the advantage of lower communication and round
complexity (Chen et al., 2019b), but they come at the
cost of higher computational complexity and runtime.
Existing HE schemes can be broadly categorized
a
https://orcid.org/0000-0001-8090-1316
b
https://orcid.org/0000-0001-6438-534X
into two types: binary schemes such as FHEW (Ducas
and Micciancio, 2015) and TFHE (Chillotti et al.,
2020), and arithmetic schemes such as BFV (Fan
and Vercauteren, 2012), BGV (Brakerski et al.,
2014), and CKKS (Cheon et al., 2017). Arithmetic
schemes typically support Single Instruction Multiple
Data (SIMD) operations and are well-suited for eval-
uating functions which can be easily represented as
a polynomial. However, evaluating non-linear func-
tions, such as square roots or finding the minimum
of two elements, requires numerical approximations,
which can be very expensive to compute due to the
need for deep circuits to achieve accurate results. On
the other hand, binary schemes can easily evaluate
binary circuits and even support lookup table (LUT)
evaluation, making them more suitable for non-linear
functions. However, they are less efficient for
addition and multiplication circuits, as demonstrated
in (Lou et al., 2020, Tab. 1). To overcome this lim-
itation, Pegasus (Lu et al., 2021) recently proposed
a framework that can switch between an arithmetic
CKKS ciphertext and corresponding binary FHEW
ciphertexts. This allows for the evaluation of arith-
metic functions using CKKS and LUTs using FHEW.
However, Pegasus only supports a single secret
key, making it unsuitable for secure computation
applications with multiple data providers, such as
federated learning (McMahan et al., 2017; Fereidooni
et al., 2021; Schneider et al., 2023).
Schneider, T., Yalame, H. and Yonli, M.
Griffin: Towards Mixed Multi-Key Homomorphic Encryption.
DOI: 10.5220/0012090200003555
In Proceedings of the 20th International Conference on Security and Cryptography (SECRYPT 2023), pages 147-158
ISBN: 978-989-758-666-8; ISSN: 2184-7711
Copyright
c
2023 by SCITEPRESS – Science and Technology Publications, Lda. Under CC license (CC BY-NC-ND 4.0)
147
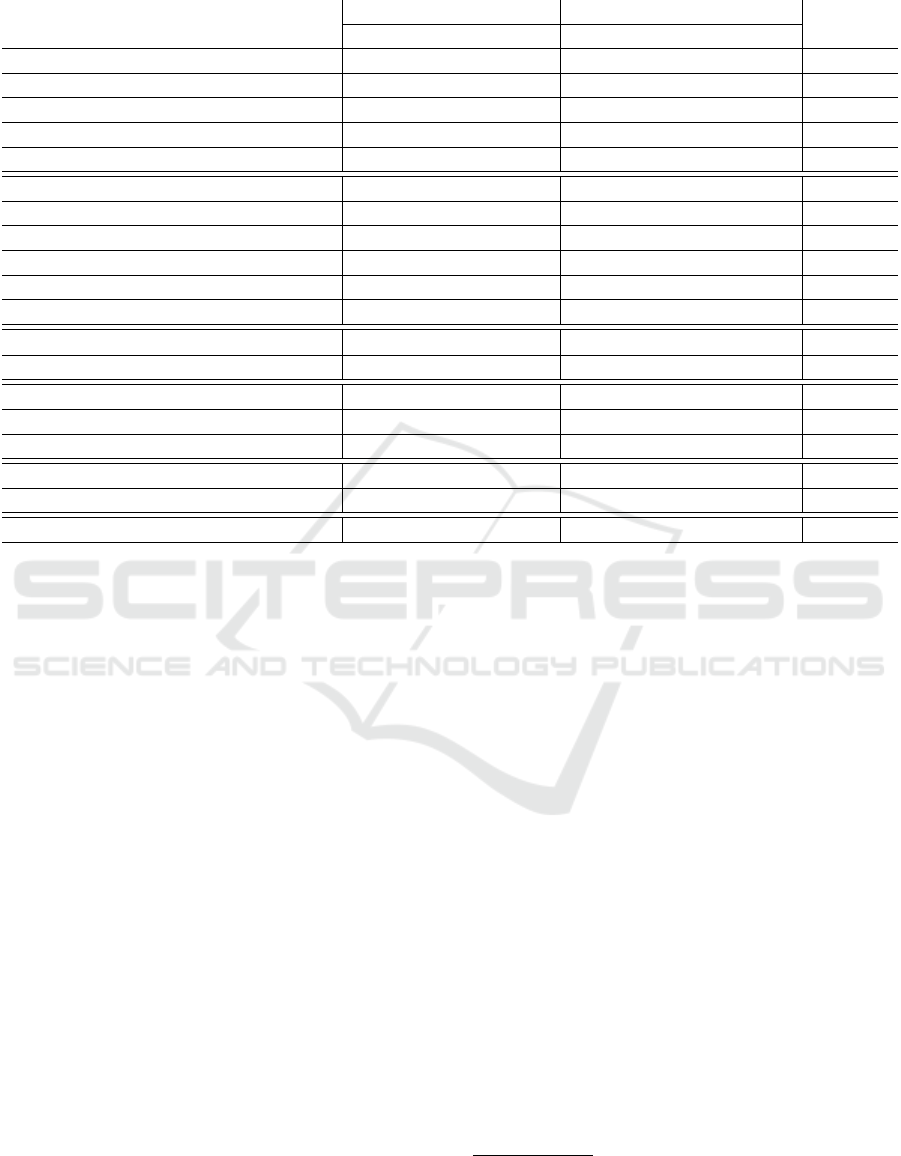
Table 1: Overview of existing homomorphic encryption protocols and compilers.
Name
Functions Conversion
MKHE
Arithmetic Boolean Arithmetic ←→ Boolean
Cingulata (Carpov et al., 2015) ✗ ✓ ✗ ✗
FHEW (Ducas and Micciancio, 2015) ✗ ✓ ✗ ✗
TFHE (Chillotti et al., 2020) ✗ ✓ ✗ ✗
Transpiler (Gorantala et al., 2021) ✗ ✓ ✗ ✗
Zama (Chillotti et al., 2021) ✗ ✓ ✗ ✗
HElib (Halevi and Shoup, 2014) ✓ ✗ ✗ ✗
HEAAN (Cheon et al., 2017) ✓ ✗ ✗ ✗
CHET (Dathathri et al., 2019) ✓ ✗ ✗ ✗
nGraph-HE (Boemer et al., 2019) ✓ ✗ ✗ ✗
EVA (Dathathri et al., 2020) ✓ ✗ ✗ ✗
SEAL (Microsoft Research, 2020) ✓ ✗ ✗ ✗
E
3
(Chielle et al., 2018) ✓ ✓ ✗ ✗
Lattigo (Mouchet et al., 2020) ✓ ✓ ✗ ✗
MKHE-CKKS (Chen et al., 2019b) ✓ ✗ ✗ ✓
MKHE-TFHE (Chen et al., 2019a) ✗ ✓ ✗ ✓
OpenFHE (Al Badawi et al., 2022) ✓ ✓ ✗ ✓
Chimera (Boura et al., 2020) ✓ ✓ ✓ ✗
Pegasus (Lu et al., 2021) ✓ ✓ ✓ ✗
Griffin (This work) ✓ ✓ ✓ ✓
In an orthogonal line of research, Multi-Key
Homomorphic Encryption (MKHE) schemes have
been developed to support operations on ciphertexts
encrypted using different keys (L
´
opez-Alt et al.,
2012; Chen et al., 2019a; Chen et al., 2019b).
These schemes also provide on-the-fly MPC, where
the circuit to be evaluated can be fixed after the
data providers upload their encrypted data and the
evaluation is non-interactive. However, to the best of
our knowledge, no previous works can switch back
and forth between different MKHE schemes. We
introduce Griffin, the first hybrid MKHE framework
that supports SIMD-style arithmetic operations while
simultaneously supporting non-linear functions over
binary circuits.
1.1 Our Contributions
The contributions of this paper are as follows:
• We introduce Griffin, the first MKHE scheme that
can evaluate both arithmetic functions and LUTs
on ciphertexts (§4).
• Griffin provides the on-the-fly MPC property,
where the circuit to be evaluated can be fixed after
the data providers upload their encrypted data.
• We introduce a new conversion similar to single-
key Pegasus (Lu et al., 2021) allowing for trans-
formation between MKHE ciphertexts of FHEW
and CKKS (Chen et al., 2019b). This allows
to compute the maximum of two numbers in
3.2 seconds, outperforming the existing solutions
of (Chen et al., 2019b) by ≈ 2× (§5).
• We implement Griffin on top of OpenPEGASUS
1
,
which is based on Microsoft SEAL
2
, and bench-
mark it against other HE solutions, showing its
benefits for different applications.
Tab. 1 provides a comparison of Griffin with pre-
vious works in terms of the features supported.
2 BACKGROUND
We define our parameters and notation in §2.1 and
provide an overview of the FHE schemes used in
Griffin in §2.2.
2.1 Parameters and Notation
[k] refers to the set containing all non-negative inte-
gers smaller than k, i.e., {i|i ∈ N
0
,i < k}. We use
Z
q
to refer to Z/qZ. Let R := Z[X]/(X
N
+ 1). We
1
https://github.com/Alibaba-Gemini-Lab/
OpenPEGASUS
2
https://github.com/Microsoft/SEAL
SECRYPT 2023 - 20th International Conference on Security and Cryptography
148

use R
A
to refer to A[X]/(X
N
+ 1). If q is an inte-
ger, we define R
q
:= Z
q
[X]/(X
N
+ 1). B refers to the
subset of polynomials with binary coefficients of R .
Similarly, B refers to the set {0, 1}. For a ∈ R we
use [a]
q
to refer to a mod q where coefficients are re-
duced in (q/2, q/2]. We use ⟨·,·⟩ to denote the canon-
ical inner product. Vectors are typically bold such as
a
a
a ∈ B
n
. We refer to the j-th element of a vector with
a
j
. We use the notation ct ∈ SCHEME
p
s
(m) to ex-
press that ct is a ciphertext obtained by encrypting the
message m with key s in scheme SCHEME with pa-
rameters p. We omit s and p if the parameters and
the key are clear from the context. If χ is a distribu-
tion, then x ← χ expresses that x is sampled from χ.
If A is a set, then x ← A denotes that x is uniformly
randomly sampled from A. An extended RLWE ci-
phertext ct ∈
^
RLWE(m;g
g
g) of a message m is defined
by (c
i
)
i∈[d]
with c
i
∈RLWE(g
g
g[i]·m) (Lu et al., 2021).
Ecd refers to the CKKS encoding function.
2.2 FHE Schemes
We differ between Arithmetic schemes, which ei-
ther perform arithmetic over a plaintext space such
as Z/pZ (Fan and Vercauteren, 2012) or fixed point
complex vectors (Cheon et al., 2017), and Binary
schemes, which can evaluate binary gates such as
NAND on binary ciphertexts (Ducas and Miccian-
cio, 2015). Binary schemes are often based on the
Learning With Errors (LWE) assumption, whereas
Arithmetic schemes use the Ring Learning With Er-
rors (RLWE) assumption. LWE Assumption (Regev,
2005). Let n be the LWE dimension, q the cipher-
text modulus, and t ≥ 2 the plaintext modulus. A
key vector s
s
s ∈ Z
n
q
is sampled from a given key dis-
tribution. Let m ∈ Z
t
be the message that ought to
be encrypted. For each encryption, a vector a
a
a is uni-
formly randomly sampled from Z
n
q
, and a random
error e is sampled from Z
q
according to the error
distribution. A ciphertext consists of the elements
(a
a
a,b), where b = ⟨a
a
a,s
s
s⟩+ e + ∆m, and ∆ is the scal-
ing factor that depends on the scheme. Commonly
∆ = ⌊
q
t
⌉ is used. The LWE assumption states that this
tuple is indistinguishable from a tuple where b is sam-
pled from Z
q
uniformly at random.
RLWE Assumption (Stehl
´
e et al., 2009; Lyuba-
shevsky et al., 2010). Let M be an integer based
on the ciphertext modulus and the security parame-
ter. Let R := Z[X]/(Φ
M
(X)), where Φ
M
is the M-
th cyclotomic polynomial. Again, let q be the ci-
phertext modulus and t the plaintext modulus. The
key s ∈ R
q
is generated according to the key distribu-
tion. We encrypt a message m ∈ R
t
by sampling an
element a ∈ R
q
uniformly at random and calculating
b = as + m + e.
CKKS (Cheon et al., 2017). The CKKS idea is that
each multiplication consumes a level, and the parame-
ters are generated for a fixed level. So it is only possi-
ble to evaluate functions up to a given maximum mul-
tiplicative depth. A base p is fixed, and a modulus q
0
is chosen for the plaintext. We define q
ℓ
= p
ℓ
·q
0
for
0 < ℓ ≤ L. A ciphertext of level ℓ is a vector in R
k
q
ℓ
for fixed k. If binary operations are passed ciphertexts
of different levels, then a rescaling procedure is exe-
cuted to equalize the levels by lowering the level of
the higher ciphertext.
HWT(h) is the set of signed binary vectors in
{0,±1}
N
with Hamming weight h. DG(σ
2
) is a dis-
crete Gaussian distribution on Z
N
with standard de-
viation σ. ZO(p) is the distribution defined over
{0,±1}
N
, where each element is -1 with probability
p/2, +1 with probability p/2, and 0 with probabil-
ity 1 − p. We sample s ← HWT(h), a ← R
q
L
and
e ← DG(σ
2
) for the key generation. The secret key
sk is set as sk = (1,s) while the public key pk is set
to an encryption of 0. We also generate an evaluation
key, which is the encryption of Ps
2
for an integer P
that depends on the security parameter and modulus.
In order to encrypt a message m ∈ R
q
0
, we sample
v ← ZO(0.5) and (e
0
,e
1
) ← DG(σ
2
). Then output
ct = v ·pk + (m + e
0
,e
1
) (mod q
L
). Decryption con-
sists of outputting b + a ·s mod q
ℓ
for a given cipher-
text (b,a).
FHEW (Ducas and Micciancio, 2015). In FHEW,
a ← Z
n
q
and s are chosen uniformly at random or as
short vectors. Instead of using a separate error term,
a randomized rounding function χ : R → Z is used.
Encryption is defined as:
Enc
t/q
s
s
s
(m) = (a
a
a,χ(⟨a
a
a,s
s
s⟩+ mq/t) mod q) ∈ Z
n+1
q
.
Decryption is defined as:
Dec
t/q
s
s
s
(ct) = ⌊t(b −⟨a
a
a,s
s
s⟩)/q⌉ mod t ∈ Z
t
= m
′
.
Another technique that FHEW can use is key switch-
ing. Here, the components of the old key are de-
composed along a basis, and each decomposed part is
encrypted under the new key: k
k
k
i, j,v
= Enc
q,q
s
(vz
i
B
j
ks
)
for i ∈ [n], j ∈ [⌈log
B
ks
q⌉] and v ∈ [B
ks
]. A
key switch is then performed by first calculating
a
i, j
such that a
i
=
∑
j
a
i, j
B
j
ks
, and then calculating:
KeySwitch((a
a
a,b),K) = (0
0
0,b) −
∑
i, j
k
k
k
i, j,a
i, j
, where K
is the set of all k
k
k
i, j,v
.
3 RELATED WORK
In this section, we summarize existing MKHE
schemes and Pegasus (Lu et al., 2021), a conversion
Griffin: Towards Mixed Multi-Key Homomorphic Encryption
149

between single-key FHEW (Ducas and Micciancio,
2015) and CKKS (Cheon et al., 2017).
3.1 MKHE
MKHE schemes allow to perform operations on en-
crypted data under different keys. Thus, each party
can encrypt their data with their key and publish
the ciphertext. An evaluator can perform the de-
sired operations on the ciphertexts, and finally, the
involved parties can decrypt the ciphertext (Chen
et al., 2019b). Many MKHE schemes have in com-
mon that they require the Common reference string
(CRS) assumption (Chen et al., 2019b; Chen et al.,
2019a). Traditional MPC approaches have commu-
nication that is proportional to the product of the
complexity of the function and the number of par-
ties (Chen et al., 2019b). In contrast, the commu-
nication in MKHE approaches is independent of the
evaluated function. Another advantage is that the par-
ties in Multi-Party Computation (MPC) need to stay
online during the entire protocol execution. More-
over, MKHE approaches are more suitable for out-
sourcing. Some MPC protocols have the data own-
ers secret-share their data with independent servers
who perform the MPC to obtain the result (Mohas-
sel and Zhang, 2017). However, they assume that the
servers do not collude. Bootstrapping and key switch-
ing are also possible in MKHE schemes without inter-
action (Chen et al., 2019b; Chen et al., 2019a).
Relinearization. (Chen et al., 2019b) introduces
two different relinearization techniques for MKHE-
CKKS and MKHE-BFV. The first technique (Chen
et al., 2019b, Alg. 1) has higher noise levels but has a
faster scheme compared to the second variant (Chen
et al., 2019b, Alg. 2). The second variant has lower
noise levels and requires less storage. The relineariza-
tion techniques introduced in (Chen et al., 2019a)
for MKHE-TFHE are very similar. We focus on the
second variant since that variant offers higher accu-
racy and has been used for benchmarks in the litera-
ture (Chen et al., 2019b; Chen et al., 2019a).
Let a
a
a ←R
d
q
be the CRS for modulus q and decom-
position degree d. k refers to the number of parties.
The key generation of the public key is slightly mod-
ified. Instead of outputting a single zero encryption,
we output d zero encryptions as the public key. Only
a single zero encryption is needed for normal encryp-
tion. However, the other encryptions are needed for
the relinearization.
KeyGen(p,s) := b
b
b = −s ·a
a
a + e
e
e (mod q) ∈ R
d
q
,
where e
e
e ← ϕ
d
for some error distribution ϕ and a
a
a ←
R
d
q
. The key s is drawn from the key distribution χ as
in the normal single key schemes (Cheon et al., 2017;
Fan and Vercauteren, 2012). This, in turn, allows to
define a new encryption method that will be used to
generate the new relinearization key:
UniEnc(µ;s) := d
d
d = [d
d
d
0
0
0
|d
d
d
1
1
1
|d
d
d
2
2
2
] ∈ R
d×3
q
1. r ← χ, e
e
e
1
1
1
,e
e
e
2
2
2
← ϕ
d
and d
d
d
1
1
1
← R
d
q
2. d
d
d
0
0
0
= −s ·d
d
d
1
1
1
+ e
e
e
1
1
1
+ r ·g
g
g (mod q)
3. d
d
d
2
2
2
= r ·a
a
a + e
e
e
2
2
2
+ µ ·g
g
g (mod q)
where s is the secret key, q is the modulus and
g
g
g is the decomposition vector. The decomposi-
tion vector represents a basis analogously to decom-
position in BFV (Fan and Vercauteren, 2012) and
TFHE (Chillotti et al., 2020). The relinearization key
is then defined as D
D
D ← UniEnc(s;s).
Arithmetic Operations. Generally, MKHE cipher-
texts store a tuple of the ids of the parties whose secret
key is required to decrypt the current ciphertext (Chen
et al., 2019b). If a binary operation combines two ci-
phertexts whose id tuples are distinct, then the cipher-
texts are expanded prior to the operation. Ciphertexts
will be of the form ct ∈ R
k+1
q
. Every id is associated
with an index i such that 1 ≤ i ≤ k and ct[i] is mul-
tiplied with the private key of the party with id
i
dur-
ing decryption. The expansion consists of padding a
ciphertext with zero polynomials at the indices cor-
responding to ids that are only present in the other
ciphertext. This results in a change of the id to index
mapping. An id might be associated with a new in-
dex afterward since both ciphertexts need to have the
same mapping. The addition does not require any spe-
cial treatment aside from a possible expansion. Multi-
plication also shares the first phase with the single key
Fully Homomorphic Encryption (FHE) variant. How-
ever, the particular MKHE relinearization method is
applied afterward.
Permutations and Rotations. Permutations use Ga-
lois Automorphisms, just like the single key variant
of the schemes (Chen et al., 2019b, §5.1). However,
since applying a Galois element to a ciphertext also
changes the key of that ciphertext, a key switch to the
original key is performed. Let τ
j
: a(X ) 7→ (aX
j
) be a
Galois element. Then we define:
MKHE.GKGen( j; s) := gk = [h
h
h
0
|h
h
h
1
] ∈ R
d×2
q
,
where h
h
h
1
← R
d
q
and h
h
h
0
= −s · h
h
h
1
+ e
e
e
′
′
′
+ τ
j
(s) · g
g
g
(mod q). To apply a Galois element, we then per-
form:
MKHE.EvalGal(ct; {gk
i
}
1≤i≤k
) := (c
′
0
,...,c
′
k
) , where
c
′
0
= τ
j
(c
0
) +
k
∑
i=1
⟨g
g
g
−1
(τ
j
(c
i
)),h
h
h
i,0
⟩ (mod q),
SECRYPT 2023 - 20th International Conference on Security and Cryptography
150

c
′
i
= ⟨g
g
g
−1
(τ
j
(c
i
)),h
h
h
i,1
⟩ (mod q) for 1 ≤i ≤k.
Distributed Decryption. For decryption, each party
multiplies the index of the ciphertext associated with
their id with their private key and adds noise from a
distribution φ which has a larger variance than ϕ, re-
ducing it mod q and publishes the result (Chen et al.,
2019b). The result can then be obtained by adding all
these shares and by removing the scaling in the case
of BFV (Fan and Vercauteren, 2012).
3.2 Pegasus (Lu et al., 2021)
Different FHE schemes have different strengths and
advantages (Boura et al., 2020; Lu et al., 2021):
on the one hand, CKKS (Cheon et al., 2017) and
BFV (Fan and Vercauteren, 2012) excel at tasks
that involve addition or multiplication and can be
performed in a SIMD-like manner. On the other
hand,TFHE (Chillotti et al., 2020) and FHEW (Ducas
and Micciancio, 2015) might perform better when
parallelization is not possible, the functions involve
many non-linear operations, or when very deep cir-
cuits need to be evaluated. This motivated researchers
to create conversions between different FHE schemes
such as Pegasus (Lu et al., 2021) and Chimera (Boura
et al., 2020). Pegasus (Lu et al., 2021) outperforms
Chimera (Boura et al., 2020) with faster conversions
and smaller keys. Indeed, benchmarks in (Lu et al.,
2021) demonstrated a significant speedup compared
to Chimera (Boura et al., 2020). This is the main
reason why we provide a MKHE variant of Pegasus
instead of Chimera in Griffin. The full Pegasus proto-
col merely allows for evaluating a look-up table with
CKKS-ciphertexts. However, this is achieved by con-
verting from CKKS to FHEW, performing the look-
up, and then converting to CKKS. The functionality
of Pegasus can be summarised as follows:
1. Apply the slots to coefficients transformation.
2. Extract all the slots of the ciphertext to obtain
LWE ciphertexts.
3. Evaluate the LUT T (x) on the LWE ciphertexts.
4. Repack the LWE ciphertexts into a RLWE cipher-
text and apply the proper encoding.
Removing the two last steps results in a conversion
from CKKS to FHEW, taking a tuple of LWE ci-
phertexts, and only applying the last step results in
a conversion from FHEW to CKKS. Repacking in-
volves homomorphically performing the partial LWE
decryption, represented as a linear transformation,
and then applying a modular reduction. The following
procedures play an important role for Pegasus and we
later translate them to the MKHE setting in Griffin:
LWE Key Switching. The key switching procedure
allows changing the key of a given ciphertext. It is
possible to change the lattice dimensionality of the
LWE instance. Note that LWE ciphertexts are of the
form (b,a
a
a). Where b = m + e −⟨a
a
a,s
s
s⟩. To obtain a
new encryption, we use encryption of the old key s
s
s
under the new key s
s
s
′
′
′
and homomorphically multiply
it with a
a
a (Lu et al., 2021). This ciphertext can then be
added to b to obtain encryption of m under s
s
s
′
′
′
.
LUT Evaluation. The lookup table (LUT) func-
tion evenly samples a real function at n points in
a bounded interval given by [−q/4∆,q/4∆]. These
sampling points are used as the coefficients of a poly-
nomial. The idea is to rotate the polynomial so that
the constant part of the polynomial corresponds to the
image of the function being evaluated under the given
input. This image is then recovered by performing a
slot extraction (Lu et al., 2021). This is achieved by
first performing a modulus switch from q to 2n. Then
we perform an arithmetic operation such that AC
k,n
is
an encryption of
ˆ
f ·X
˜
b+
∑
i∈[k]
s
i
˜a
i
=
ˆ
f ·X
∆m
. This re-
sults in the desired value being in the constant part of
the polynomial.
Linear Transformation (LT) Evaluation. Tiling
transforms a rectangular matrix into a square matrix
by repeating the matrix itself (Lu et al., 2021). The LT
evaluation algorithm combines tiling with baby step
and giant step to perform matrix multiplication and
then adds the vector t to the result (Lu et al., 2021;
Halevi and Shoup, 2014).
Eval Sine. EvalSine is used to approximate the mod-
ular reduction by q
0
as part of the repacking process.
There is no need for a special MKHE variant. The
algorithm is taken from (Bossuat et al., 2021).
Slots to Coefficients (S2C). The algorithm S2C takes
a ciphertext in the slot encoding and converts it to a ci-
phertext in the coefficient encoding (Lu et al., 2021).
While doing so, it consumes 1 or 2 slots. No spe-
cial adjustment is needed to move this routine to the
MKHE setting.
Slot Extraction. Given a RLWE ciphertext in the co-
efficient encoding, we can use this procedure to ex-
tract a given coefficient into a LWE ciphertext (Lu
et al., 2021).
4 Griffin
Griffin is capable of switching between different
MKHE schemes and also performing MPC. In Grif-
fin, the dimensions of the ciphertexts increase due to
the MKHE conversion and we require a switching,
evaluation, repacking and rotation key of every party.
We assume the CRS model and require the public
Griffin: Towards Mixed Multi-Key Homomorphic Encryption
151

keys of every party. Additionally, correctness for the
prior multiplication method of the Pegasus LUT pro-
cedure does not hold with MKHE ciphertexts. As a
result, Griffin uses a new multiplication method based
on (Chen et al., 2019a). Most of the Pegasus (Lu et al.,
2021) subroutines do not require any significant mod-
ifications to work with MKHE ciphertexts.
Griffin, Full Protocol. Alg. 1 shows the full protocol
of Griffin. It is an extension of the full Pegasus proto-
col (Lu et al., 2021, Fig. 6). The main modifications
are highlighted in gray.
Griffin LWE Key Switching. Adjusting the Key
Switching (KS) routine from the single-key (Lu et al.,
2021, Fig. 9) to the MKHE setting is fairly straightfor-
ward as shown in Alg. 2. We can simply perform parts
of the routine for every party and sum the result. The
operator ⋄in Alg. 2 refers to a product between an ex-
tended RLWE ciphertext (the key switching key) and
an arbitrary ring element. The ring element is decom-
posed along the same basis as the RLWE ciphertext,
the two decomposed elements are then multiplied
component wise, and all components of the result are
then summed together: r ⋄ct :=
∑
d−1
i=0
g
g
g
−1
(r)[i] ·ct[i].
Griffin LUT Evaluation. Our algorithm for LUT eval-
uation is shown in Alg. 3. This algorithm is an ex-
tension of the LUT evaluation in Pegasus (Lu et al.,
2021, Fig. 2), however it has a wider loop range in
line 5 and line 6 to obtain the correct evaluation key
in Griffin.
Griffin Slot Extraction. Moving the slot extraction
from the single key setting to the MKHE setting is
shown in Alg. 4. It consists of applying the routine
that is performed on a to all the a
i
.
Griffin LT Evaluation. The LT algorithm of Griffin
is given in Alg. 5 which is derived from the LT algo-
rithm in Pegasus (Lu et al., 2021, Fig. 5).
Correctness of Griffin. In this section, we show
the correctness of Griffin. Pegasus can be under-
stood as a transformation between the single-key
CKKS (Cheon et al., 2017) and FHEW (Ducas and
Micciancio, 2015) encryption methods. Griffin al-
lows for evaluating a look-up table with MKHE-
FHEW. This is achieved by converting from MKHE-
CKKS to MKHE-FHEW, performing the look-up,
and then converting back to MKHE-CKKS. The func-
tionality of Griffin is analogous to that of Pegasus (Lu
et al., 2021) and can be described as follows: (a)
Apply the slots to coefficients transformation, (b) ex-
tract all slots of the ciphertext to obtain LWE cipher-
texts, (c) perform LUT evaluations on the LWE ci-
phertexts, and (d) repackage the LWE ciphertexts into
an RLWE ciphertext and apply encoding. Omitting
steps (c) and (d) results in a conversion from MKHE-
CKKS to MKHE-FHEW, whereas performing only
step (d) results in a conversion from MKHE-FHEW
to MKHE-CKKS. Repacking involves homomorphi-
cally decrypting the LWE ciphertext, applying a linear
transformation, and performing a modular reduction.
Algorithm 1: Griffin, Full Protocol (modified from (Lu
et al., 2021, Fig. 6)).
Input: • Ciphertext moduli q
0
,q
1
,...,q
L−1
, special mod-
ulus q
′
. Define Q
i
= Π
l∈[i]
q
l
for 1 ≤i ≤ L.
• CRS: a
a
a.
• Public keys: {b
i
}
i∈[k]
.
• Digit decomposition gadget vector g
g
g
digit
=
[1,B
ks
,...,B
d
ks
ks
] for some B
ks
,d
ks
> 0 and B
d
ks
ks
≥ q
0
.
• RNS decomposition gadget vector g
g
g
rns
= [q
′
mod q
0
].
• Rescaling factors 0 < ∆, ∆
r
,∆
′
r
< q
0
.
• Switching keys SwK
s
i
→s
i
,
• LWE evaluation keys EK
i
:
EK
i, j,0
∈ UniEnc
n,q
′
q
0
s
i
(I
+
(s
i
[ j])),
EK
i, j,1
∈ UniEnc
n,q
′
q
0
s
i
(I
−
(s
i
[ j]))
for j ∈ [n], where I
+
(x) = 1{x ≥ 0} and I
−
(x) =
1{x ≤0} for i ∈ [k].
• Repacking keys RK
i
∈ RLWE
n,Q
L
s
i
(Ecd(s
i
,∆
r
)) for
i ∈[k].
• Rotation keys of the CKKS scheme RotK
i
for i ∈[k].
• A level-l RLWE ciphertext (l > 1) of an encoded
vector v
v
v ∈ R
ℓ
, i.e., ct
in
∈ RLWE
n,Q
l
s
i∈[k]
(Ecd(v
v
v,∆)) for
i ∈[k].
• A look-up table function T (x) : R 7→ R .
Output: A RLWE ciphertext ct
out
∈
RLWE
n,Q
L
′
{s
i
}
i∈[k]
(Ecd(T (v
v
v),∆)), i.e., the evaluation
of T (x) on the elements of v
v
v.
1: Slots to coefficients and drop moduli: ct
′
= S2C(ct
in
)
2: Extract Coefficients: ct
l
= Extract
l
(ct
′
) for each l ∈ [ℓ]
3: for l ∈ [ℓ] do
4: Switch from n to the smaller dimension
n.
˙
ct
l
= GRIFFIN.KS(ct
l
,{SwK
s
i
→s
i
}
i∈[k]
)
5: Evaluate the look-up table.
¨
ct
l
= GRIFFIN.LUT(
˙
ct
l
,{EK
i
}
i∈[k]
,{b
i
}
i∈[k]
,T (x))
6: Switch from n to n.
...
ct
l
= (b
l
,a
a
a
l,0
,...,a
a
a
l,k−1
) =
GRIFFIN.KS(
¨
ct
l
,{SwK
s
i
→s
i
}
i∈[k]
)
7: end for
8: Define b
b
b = b
0
,...,b
ℓ−1
and A
A
A
i
∈ Z
ℓ×n
q
0
, s.t. the l-th row
of A
A
A
i
is a
a
a
l,i
.
9: for i ∈[k] do
10: Evaluate the linear transform
˜
ct
i
=
GRIFFIN.LT(RK
i
,RotK
i
,∆
′
r
,A
A
A
i
,0
0
0)
11: end for
12:
˜
ct = GRIFFIN.LT(RK
k
,RotK
k
,∆
′
r
,A
A
A
k
,b
b
b) +
∑
k−1
i=0
˜
ct
i
13: Evaluate the modulo q
0
on
˜
ct via F
mod
and output the
result as ct
out
.
SECRYPT 2023 - 20th International Conference on Security and Cryptography
152

Algorithm 2: Griffin LWE KS (modified from (Lu et al.,
2021, Fig. 9)).
Input: A LWE ciphertext (b,{a
a
a
i
}
i∈[k]
) ∈ LWE
n
n
n,q
{s
s
s
i
i
i
}
i∈[k]
(m).
The LWE switching key of every party:
SwK
i, j
∈
^
RLWE
n,q
{s
i
}
i∈[k]
∑
l∈[n]
s
s
s
i
i
i
[ jn +l]X
l
;g
g
g
!
for j ∈ [n/n].
Output: A LWE ciphertext ct
out
∈ LWE
n
,q
{s
s
s
i
i
i
}
i∈[k]
(m).
1: Define a set of polynomials {ˆa
i, j
} where ˆa
i, j
= a
a
a
i
i
i
[ jn]−
∑
n−1
l=1
a
a
a
i
i
i
[ jn +l]X
n−l
for j ∈ [n/n].
2: Compute
˜
ct
i
=
∑
j∈[n/n]
ˆa
i, j
⋄SwK
i, j
∈ R
2
n,q
.
3: Output (b,0
0
0) +
∑
k−1
i=0
Extract
0
(
˜
ct
i
) as ct
out
.
Algorithm 3: Griffin LUT evaluation (modified from (Lu
et al., 2021, Fig. 2)).
Input: (b,a
a
a) ∈ LWE
n,q
{s
i
}
i∈[k]
(⌊∆m⌉) of a message m ∈ R
with a scaling factor ∆ such that |⌊∆m⌉| < q/4. Look-
up table function T (x) : R 7→ R . The evaluation keys
{EK
i
}
i∈[k]
are a set of Uni-encryptions of the respective
keys s
s
s
i
∈ {0, ±1}
n
. Public keys of the involved parties
{b
i
}
i∈[k]
.
Output: A LWE ciphertext ct
out
∈ LWE
n,q
{s
i
}
i∈[k]
(·).
1: Let η
k
= kq/(2n∆) ∈R for 1 ≤k ≤n/2. Define a poly-
nomial
ˆ
f ∈ R
n,q
whose coefficients are:
f
j
=
⌊∆T (0)⌉ if j = 0
⌊∆T (−η
j
)⌉ if 1 ≤ j ≤ n/2
⌊−∆T (η
n−j
)⌉ if n/2 < j < n
2:
˜
b = ⌊
2n
q
b⌉ and
˜
a
a
a = ⌊
2n
q
a
a
a⌉.
3: Initialize AC
0
= (
ˆ
f ·X
˜
b mod n
,0) ∈ R
2
n,q
.
4: for j ∈ [kn] do
5: t
j
= ((X
˜
a
a
a[ j] mod n
− 1) · AC
j
) ◦
(EK
⌊j/n⌋, j mod n,0
,{b
i
}
i∈[k]
) + AC
j
6: AC
j+1
= ((X
−
˜
a
a
a
i
i
i
[ j] mod n
− 1) · t
j
) ◦
(EK
⌊j/n⌋, j mod n,1
,{b
i
}
i∈[k]
) + t
j
7: end for
8: Extract
0
(AC
kn
) as ct
out
.
To show the correctness of Griffin, we show the
correctness of each of its subprocedures. Addition-
ally, we present a lemma that applies to linear trans-
formations generally, rather than the algorithm used
in Pegasus only (Lu et al., 2021).
Lemma 1. Let c be a MKHE-CKKS ciphertext en-
crypting the polynomial m with noise level e and f be
a linear transformation. There exists an efficient algo-
rithm, using only public information, that calculates
c
′
, a MKHE-CKKS ciphertext encrypting the polyno-
mial f (m) with noise level f (e) + e
lt
, where e
lt
is the
noise added by the evaluation of the linear transform.
Algorithm 4: Griffin Slot Extraction.
Input: A MKHE-RLWE ciphertext that uses the coeffi-
cient encoding: ct ∈ RLWE
n,Q
i
s
(m). The coefficient to
extract j.
Output: A MKHE-LWE ciphertext ct
′
∈ LWE
n,Q
i
s
(m
j
).
1: Let ct = (
∑
n−1
l=0
b
l
X
l
,
∑
n−1
l=0
a
0,l
X
l
,...,
∑
n−1
l=0
a
k−1,l
X
l
).
2: return
ct
′
= (b
j
,a
0, j
,a
0, j−1
,...,a
0,0
,−a
0,n−1
,...,−a
0, j+1
,
a
1, j
,a
1, j−1
,...,a
1,0
,−a
1,n−1
,...,−a
1, j+1
,...
a
k−1, j
,a
k−1, j−1
,...,a
k−1,0
,−a
k−1,n−1
,...,−a
k−1, j+1
).
Algorithm 5: Griffin LT evaluation (modified from (Lu
et al., 2021, Fig. 5)).
Input: ct
in
∈ RLWE
n,q
{s
s
s
i
i
i
}
i∈[k]
(Ecd(z
z
z,∆
r
)). Rotation keys
RotK
i
. A scaling factor ∆
′
r
> 0. A plain matrix M
M
M ∈
R
ℓ×n
such that ℓ,n < n. A vector t
t
t ∈ R
ℓ
.
Output: A RLWE ciphertext ct
out
∈ RLWE
n,q/∆
r
{s
s
s
i
i
i
}
i∈[k]
(m).
1: Tiling and Diagonals. Let ¨n = max(ℓ,n) and ˜n =
min(ℓ,n). Define ˜n vectors { ˜m
j
}
˜n−1
j=0
by going through
the rows and columns of M
M
M
˜
m
m
m
j
[r] = M
M
M[r mod ℓ,r + j mod n] for r ∈ [ ¨n].
2: Baby-Step. Let ˜g =
√
˜n
. For g ∈ [ ˜g], compute c
g
=
RotL
g
(ct
in
).
3: Giant-Step. Let
˜
b =
⌈
˜n/ ˜g
⌉
. Compute
˜
ct =
∑
b∈[
˜
b]
RotL
b ˜g
∑
g∈[ ˜g]
Ecd(
˜
m
m
m
b ˜g+g
≫ b ˜g,∆
′
r
) ·c
g
.
4: if ℓ ≥ n then
5: Output Rescale(
˜
ct,∆
r
) + Ecd(t
t
t,∆
′
r
) as ct
out
.
6: else
7: Let γ = log(n/ℓ) and ct
0
=
˜
ct.
8: Update iteratively for 1 ≤ j ≤ γ
ct
j
= RotL
ℓ2
j
(ct
j−1
) + ct
j−1
.
9: Output Rescale(ct
γ
,∆
r
) + Ecd(t
t
t,∆
′
r
) as ct
out
.
10: end if
Proof. It has been established in previous research
that rotations can be homomorphically evaluated on
MKHE ciphertexts (Chen et al., 2019b). Additionally,
it has been shown that linear transformations can be
efficiently represented as a combination of rotations,
constant products, and additions, as outlined in (Han
et al., ). Given that all the basic operations required
to evaluate a linear transformation can also be applied
to an MKHE-ciphertext, it can be inferred that an al-
gorithm for homomorphically evaluating linear trans-
formations on MKHE-ciphertexts must exist.
Corollary 1. The single key variant of the Slot-
sToCoefficients (S2C) transformation can be adapted
Griffin: Towards Mixed Multi-Key Homomorphic Encryption
153

to a MKHE variant by replacing all the basic op-
erations with their MKHE equivalents. In other
words, the S2C transformation can be transformed
into a MKHE-variant by applying the corresponding
MKHE counterparts of the primitive operations used
in the single key variant.
From Lemma 1, we can deduce Corollary 1,
which states that the SlotsToCoefficients (S2C) trans-
formation corresponds to a linear transformation, as
previously established in (Han et al., ). This is also
the approach used for the implementation of MKHE
variant of S2C. The single key variant of S2C was
modified by replacing each primitive operation with
its corresponding MKHE equivalent. As the effect of
these operations on the encrypted message is identi-
cal, it follows that the resulting ciphertext utilizes a
coefficient encoding rather than a slots encoding.
Lemma 2. Let c be a MKHE-CKKS ciphertext en-
crypting N coefficients, v
0
,...v
N−1
under the keys
(s
1
,...s
k
). There exists an efficient algorithm that
given an integer p ∈ [N − 1], produces a MKHE-
FHEW ciphertext that encrypts v
p
under the keys
(s
s
s
′
1
,...,s
s
s
′
k
), where s
s
s
′
i
is the coefficient vector corre-
sponding to the polynomial s
i
.
Proof. Alg. 4 is an example of such an algorithm.
Let c = ({a
i
}
i∈[k]
,b) be the input ciphertext and c
′
=
({a
a
a
′
i
}
i∈[k]
,b
′
). First, we use the p-th coefficient of the
polynomial b to obtain b
′
. Just as in (Chillotti et al.,
2020) we use antiperiodic indexes. Let N be the de-
gree of the polynomial. a
′
i, j
shall refer to the j-th co-
efficient of a
a
a
′
i
. a
′
i, j
is set to the (p − j)-th coefficient
of a
i
. Since we are using antiperiodic indexes, a neg-
ative index corresponds to the additive inverse of the
respective coefficient. For example, −2 would corre-
spond to the additive inverse of the (N −2)-th coeffi-
cient. This is a consequence of the assumption that we
are using cyclotomic polynomials of the form X
N
+1.
Simple arithmetic shows that this method results in an
a
a
a
′
i
= (a
′
i,0
,...,a
′
i,n−1
) such that ⟨a
a
a
′
i
,s
s
s
′
i
⟩ = (a
i
s
i
)
p
. That
is, the inner product corresponds to the p-th coeffi-
cient of the product of the two polynomials. It follows
that we obtain a correct MKHE-LWE encryption of v
p
without any additional noise.
Lemma 3. The MKHE variant of the LWE KS
(Alg. 2) is a correct key switching procedure. That
is, given a FHEW-MKHE ciphertext of dimension n,
c encrypted by the keys s
i
and a tuple of key switch
keys (SwK)
i
, the procedure outputs a FHEW-MKHE
ciphertext c
′
of dimension n
′
encrypted by the keys s
′
i
for i ∈ [k]. We assume
n
n
′
> 1 .
Proof. First, we observe that the key switch key of
party i is an extended RLWE encryption of the LWE
secret key s
i
. This RLWE instantiation uses a cy-
clotomic polynomial of degree n
′
. The elements of
the LWE secret key vector are interpreted as coeffi-
cients of a polynomial. A single polynomial will not
be able to contain all of the key elements, therefore
there are ⌈n/n
′
⌉-many. The LWE KS algorithm intro-
duced in (Lu et al., 2021) homomorphically computes
the inner product of a
i
and s
i
and adds the result to
b of the input. This corresponds to a homomorphic
partial decryption. A full decryption (i.e., bootstrap-
ping) would be followed by a modular reduction. Our
MKHE variant homomorphically computes this inner
product for every party and then adds the sum of these
ciphertexts to the b of the input. This again is a par-
tial decryption, which follows from the definition of
MKHE decryption.
A crucial algorithm in Griffin is the LUT evalu-
ation. In the single key case, this algorithm utilizes
RGSW ciphertexts, which cannot be easily combined
with MKHE ciphertexts. A possible solution is to
replace the RGSW encryption of the evaluation key
with the Uni-encryption method outlined in (Chen
et al., 2019b). This allows for the use of one of
the multiplication algorithms previously introduced,
to evaluate the LUT table.
Lemma 4. Alg. 3 evaluates a LUT on a MKHE-LWE
ciphertext.
Proof. First, we observe that the idea behind the sin-
gle key LUT evaluation is to encode each possible
image of the LUT as a coefficient in the polynomial
ˆ
f . We then calculate X
ˆ
b+ ˆas
≈ X
2nm/q
. The polyno-
mial coefficients of
ˆ
f are chosen such that the follow-
ing slot extraction extracts the correct coefficient with
the correct value. The reasoning behind the MKHE
variant is similar. We calculate X
ˆ
b+
∑
k
i=1
ˆa
i
s
i
≈ X
2nm/q
.
This multiplication of a MKHE ciphertext with a uni-
encryption by a single party is identical to the usage
of the algorithm in (Chen et al., 2019a).
The correctness of the LT evaluation follows
straightforwardly from Lemma 1. The final part is
the modular reduction.
Lemma 5. MKHE-F-Mod correctly evaluates the
modular reduction on a RLWE-MKHE ciphertext.
Proof. We obtain MKHE-F-Mod by replacing the
primitive operations of F-Mod in (Bossuat et al.,
2021) with their MKHE counterparts. Since the mod-
ifications of the encoded message are identical it fol-
lows that the reduction is applied properly.
Theorem 4.1. Griffin is a correct MKHE instantia-
tion of the Pegasus (Lu et al., 2021).
SECRYPT 2023 - 20th International Conference on Security and Cryptography
154

Proof. This follows from Corol-
lary 1, Lemma 1, Lemma 2, Lemma 3, Lemma 4 and
Lemma 5.
Security of Griffin. The security of the Griffin
scheme can be analyzed with relative ease due to the
fact that the evaluator does not have access to any pri-
vate information. The evaluator is only able to access
public information, which simplifies the task of prov-
ing the security of the scheme to demonstrating that
this public information does not reveal any sensitive
information. To achieve this, we will demonstrate that
all public information is indistinguishable from ran-
domly generated data. Our scheme relies on the LWE,
RLWE, CRS and circular security assumptions.
We will divide the analysis into two distinct
phases:
• The setup phase, during which all keys and en-
crypted inputs are published.
• The decryption phase, during which ciphertexts
are decrypted.
The setup phase in particular, involves public mate-
rial from the MKHE-CKKS and the MKHE-FHEW
schemes, as well as new material from the Griffin
keys. We will only prove the security of the new ma-
terial, as the security of the other material has already
been established in (Chen et al., 2019b) and (Chen
et al., 2019a). The decryption phase is equivalent
to the decryption phase of the MKHE schemes and
as such, does not require any special treatment. We
only focus on the RKWE swtiching keys, needed
for MKHE-LWE key switching, and repacking key,
needed for the MKHE-repacking operation, as the
rest are either present in MKHE-CKSS (Chen et al.,
2019b) or are variants of (Chen et al., 2019a) present
in MKHE-FHEW.
Lemma 6. The RLWE switching key is indistin-
guishable from a randomly generated ciphertext of the
same size under the RLWE assumption and the circu-
larity assumption.
Proof. We observe that the MKHE-RLWE switching
key of one party is identical to the switching key in
the single key instantiation. This in turn is a tuple of
RLWE encryptions of the LWE key. This is secure if
we combine the RLWE and circularity assumptions.
Lemma 7. The repacking key is indistinguishable
from a randomly generated ciphertext of the same size
under the RLWE assumption and the circularity as-
sumption.
Proof. The argument follows the same line of reason-
ing as in the previous Lemma 6. The repacking key
is the collection of the party’s single-key repacking
key, which is a RLWE encryption of the LWE key.
Combining the RLWE and the circularity assumption
again results in the proof.
Theorem 4.2. Griffin is secure against semi-honest
adversaries under the LWE assumption.
Proof. This follows from combining the results of
(Chen et al., 2019b), (Chen et al., 2019a) with
Lemma 6 and Lemma 7.
5 EVALUATION
In this section, we present several applications of
Griffin. We primarily compare the runtime of the ap-
plications with single-key Pegasus (Lu et al., 2021) to
show the overhead of our modifications.
Optimizations. Our implementation uses various op-
timisations, including the Residue Number System
(RNS) representation (Chen et al., 2019b), the special
modulus technique (Gentry et al., 2012), and seeded
ciphertexts (Joye, 2022).
Selecting Parameters. For the benchmarks we use
the same parameters as Pegasus (Lu et al., 2021). We
use binary keys rather than trinary keys because the
implementation only supports binary keys. Tab. 2
shows the parameters that are used in Pegasus (Lu
et al., 2021). We use these parametes for the mi-
crobenchmarking in Griffin.
Table 2: Parameters used in Pegasus (Lu et al., 2021). n is
the lattice dimensions, q
′
the special modulus, q
∗
a modulus
prime used for the Residue Number System (RNS), σ
∗
the
standard deviation of the noise distribution, B
ks
and d
ks
are
parameters for the digit decomposition, Q is the modulus.
Encryption Parameters
^
RLWE
n,q
0
s
(·), level 0 n = 2
10
,q
0
≈ 2
45
,σ
ks
= 2
10
,B
ks
= 2
7
,d
ks
= 7
RGSW
n,q
′
q
0
s
s
s
(·), level 1 n = 2
12
,q
′
≈ 2
60
,σ
lut
= 2
10
RLWE
n,∗
s
(·), level 2 n = 2
16
,q
i
≈ 2
45
,σ
ckks
= 3.19,log Q = 795
Communication Cost. Griffin requires communica-
tion only during the setup and the decryption phase.
Setup Phase: The per party communication for the
setup phase is independent of the number of parties.
It also merely depends on the number of levels of the
CKKS scheme and not on the depth of the circuit.
The repacking procedure resets the number of levels
and can thus be used to evaluate circuits whose multi-
plicative depth exceeds the number of levels. Gener-
ally, lower levels offer a better runtime for primitive
operations, but this might come at the cost of more
frequent repacking. Repacking itself also introduces
Griffin: Towards Mixed Multi-Key Homomorphic Encryption
155

a minimum number of levels, since it consumes lev-
els. Our Griffin implementation requires 9 levels for
repacking.
Decryption Phase: For decryption, each party re-
ceives part of the ciphertext from the evaluator. This
part has a size of n log
2
(q
0
) bits per party. Note that
we are assuming that the ciphertext is at its lowest
level. Even if the computation did not consume all
levels, the evaluator can reduce the levels in order to
reduce communication. This part is also unaffected
by the seeded optimization. Afterwards, the party per-
forms its computation and sends a polynomial with
the same size back. The total communication per
party for the decryption phase is thus 2n log
2
(q
0
) bits
per ciphertext.
Since the communication costs only depend on the
number of ciphertexts and the parameters, we can cal-
culate them without a specific application in mind.
Tab. 3 shows per party communication costs for Grif-
fin and Pegasus considering Pegasus parameters (cf.
Tab. 2). As Tab. 3 shows, communication per party for
an application that requires each party to contribute a
ciphertext is 3.86 GB and 2.08 GB with the seeded ci-
phertexts optimization (Joye, 2022). If the evaluator
has downloaded the public material of the involved
parties in the past, then this communication can be
reduced to 12.42 MB or 6.21 MB with the seeded ci-
phertexts optimization. A single ciphertext can con-
tain 2
15
slots and thus the amortized ciphertext size
(i.e., ciphertext size divided by number of slots) with
the seeded ciphertexts optimization is 199 bytes. This
corresponds to 35 ciphertext bits per plaintext bit with
this optimization.
Microbenchmarks. Tab. 4 shows the comparison of
different operations of our MKHE framework Griffin
with single-key Pegasus framework (Lu et al., 2021).
Note that Pegasus only supports a single party.
Sorting with Griffin. Similar to Pegasus (Lu et al.,
2021), we use bitonic sorting (Batcher, 1968) which
is data independent and can be parallelized easily. In
order to implement this sorting, we approximate the
min and max functions with LUTs.
min(a,b) := 0.5(a + b) −0.5|a −b|,
max(a,b) := 0.5(a + b) + 0.5|a −b|.
Tab. 5 shows the performance results of Griffin in
comparison with Pegasus (Lu et al., 2021).
Maximum of Two Numbers with Griffin. A pure
MKHE-CKKS circuit that obtains the maximum of
two numbers has 27 levels to reach an accuracy com-
parable to the MKHE-FHEW implementation (Cheon
et al., 2019). The MKHE-CKKS approach to cal-
culating the maximum is similar to the approach
Table 3: Communication Costs for Pegasus Parameters
in Griffin. SCO denotes seeded ciphertexts optimiza-
tion (Joye, 2022). PK
i
is the public key of level i, SwK
is a switching key, EK is the LUT evaluation key, RepackK
is the repacking key, RotK is the rotation key, RelinK is
the relinearization key of level 2, Input CT is the size of a
fresh ciphertext, and output CT is the communication for
decrypting one ciphertext. The column of seeded optimiza-
tion is marked with ✗ if the optimisation cannot be applied.
Key Size Size with SCO
PK
2
105 MB ✗
PK
1
105 KB ✗
SwK
s
s
s→s
s
s
4.92 MB 2.46 MB
SwK
s
s
s→s
s
s
315 KB 157.5 KB
EK 315 MB 210 MB
RepackK 12.42 MB 6.21 MB
RotK 3.11 GB 1.55 GB
RelinK 298.13 MB 198.75 MB
Input CT 12.42 MB 6.21 MB
Output CT 11.5 KB ✗
Total 3.86 GB 2.08 GB
Table 4: Runtime comparison of Griffin with Pegasus (Lu
et al., 2021). LUT refers to a LUT evaluation and KS to a
keyswitch. S2C is the slots to coefficients transformation,
LT the linear transformation routine, and Mod the modular
reduction.
Pegasus (Lu et al., 2021) Griffin (Ours)
Operation 1 Party 1 Party 2 Parties 4 Parties
1 slot
KS(s →s) 20ms 18ms 37ms 76ms
KS(s →s) 1.5ms 1.3ms 2.5ms 4.9ms
LUT 0.93s 1.2s 2.96s 8.51s
256 slots
S2C 0.78s 0.41s 0.76s 1.48s
LT 16.76s 15.4s 30.94s 62.55s
Mod 7.06s 13.6s 35.41s 108.26s
1024 slots
S2C 1.28s 0.65s 1.21s 2.39s
LT 44.50s 42.9s 86.14s 174.00s
Mod 7.06s 13.35s 35.06s 107.72s
4096 slots
S2C 2.02s 0.97s 1.88s 3.67s
LT 44.65s 43.32s 87.09s 175.84s
Mod 7.06s 13.43s 35.03s 107.57s
outlined above, except that the LUT for calculating
0.5|x| is replaced by sqrt(x
2
). Most of the layers are
consumed by approximating the sqrt function. Griffin
replaces the LUT for 0.5|x| with a plaintext multipli-
cation in CKKS. The algorithm halves the CKKS ci-
phertext, converts it to two FHEW ciphertext and then
proceeds to use a single LUT for |x|. The parameters
for the benchmark are slightly adjusted from Tab. 2.
Tab. 6 shows that Griffin has the lowest runtime
compared to pure MKHE-CKKS (Chen et al., 2019b)
and MKHE-FHEW. All benchmarks involved two
parties. MKHE-CKKS uses (Cheon et al., 2019) with
SECRYPT 2023 - 20th International Conference on Security and Cryptography
156

Table 5: Runtimes for sorting (Batcher, 1968) with two par-
ties in Griffin.
Elements Threads Pegasus (Lu et al., 2021) 1 party This work 2 parties
32 20 34s 187s
16 38s 186s
8 73s 293s
4 149s 476s
1 493s 1441s
64 20 84s 458s
16 104s 457s
8 200s 748s
4 409s 1277s
1 1381s 4062s
a total depth of 15. MKHE-FHEW uses Pegasus (Lu
et al., 2021) and Griffin combines MKHE-CKKS op-
erations with MKHE-FHEW operations.
Table 6: Runtimes for calculating the maximum of two
numbers among two parties.
Scheme Time Avg. Err. [%] Max. Err. [%]
MKHE-CKKS (Chen et al., 2019b) 17.54s 2.00 4.28
MKHE-FHEW 5.91s 0.11 0.32
Griffin (Ours) 3.21s 0.17 0.50
6 CONCLUSION AND FUTURE
WORK
We presented Griffin, a new MKHE scheme that can
convert between different MKHE schemes depending
on the function that needs to be evaluated. Griffin
satisfies the on-the-fly property, i.e., it requires no
interaction for converting from one MKHE scheme
to another. To the best of our knowledge, this is the
first time that a MKHE scheme with such properties
has been constructed. As future work, we intend to
expand the capabilities of Griffin by incorporating
other MPC protocols like FLUTE (Br
¨
uggemann
et al., 2023). Furthermore, we aim to explore the
potential benefits of hardware acceleration (M
¨
unch
et al., 2021) and synthesis tools (Patra et al., 2021b;
Heldmann et al., 2021) in the context of Griffin.
ACKNOWLEDGEMENTS
This project received funding from the ERC under the
European Union’s Horizon 2020 research and innova-
tion program (grant agreement No. 850990 PSOTI).
It was co-funded by the DFG within SFB 1119
CROSSING/236615297 and GRK 2050 Privacy &
Trust/251805230.
REFERENCES
Al Badawi, A., Bates, J., Bergamaschi, F., Cousins, D. B.,
Erabelli, S., Genise, N., Halevi, S., Hunt, H., Kim,
A., and Lee, Y. (2022). OpenFHE: Open-source fully
homomorphic encryption library. In WAHC.
Batcher, K. E. (1968). Sorting Networks and Their Appli-
cations. In American Federation of Information Pro-
cessing Societies.
Boemer, F., Cammarota, R., Demmler, D., Schneider, T.,
and Yalame, H. (2020). MP2ML: A Mixed-Protocol
Machine Learning Framework for Private Inference.
In ARES.
Boemer, F., Lao, Y., Cammarota, R., and Wierzynski, C.
(2019). nGraph-HE: A Graph Compiler for Deep
Learning on Homomorphically Encrypted Data. In
ACM International Conference on Computing Fron-
tiers.
Bossuat, J.-P., Mouchet, C., Troncoso-Pastoriza, J., and
Hubaux, J.-P. (2021). Efficient Bootstrapping for
Approximate Homomorphic Encryption with Non-
Sparse Keys. In EUROCRYPT.
Boura, C., Gama, N., Georgieva, M., and Jetchev, D.
(2020). Chimera: Combining Ring-LWE-based Fully
Homomorphic Encryption Schemes. Journal of Math-
ematical Cryptology.
Brakerski, Z., Gentry, C., and Vaikuntanathan, V. (2014).
(Leveled) Fully Homomorphic Encryption without
Bootstrapping. In ACM Transactions on Computation
Theory.
Br
¨
uggemann, A., Hundt, R., Schneider, T., Suresh, A., and
Yalame, H. (2023). FLUTE: Fast and Secure Lookup
Table Evaluations. In IEEE S&P.
Carpov, S., Dubrulle, P., and Sirdey, R. (2015). Armadillo:
A Compilation Chain for Privacy Preserving Applica-
tions. In International Workshop on Security in Cloud
Computing.
Chen, H., Chillotti, I., and Song, Y. (2019a). Multi-Key Ho-
momorphic Encryption from TFHE. In ASIACRYPT.
Chen, H., Dai, W., Kim, M., and Song, Y. (2019b). Efficient
Multi-Key Homomorphic Encryption with Packed Ci-
phertexts with Application to Oblivious Neural Net-
work Inference. In CCS.
Cheon, J. H., Kim, A., Kim, M., and Song, Y. (2017).
Homomorphic Encryption for Arithmetic of Approxi-
mate Numbers. In ASIACRYPT.
Cheon, J. H., Kim, D., Kim, D., Lee, H. H., and Lee, K.
(2019). Numerical Method for Comparison on Ho-
momorphically Encrypted Numbers. In ASIACRYPT.
Chielle, E., Mazonka, O., Gamil, H., Tsoutsos, N. G., and
Maniatakos, M. (2018). E3: A Framework for Com-
piling C++ Programs with Encrypted Operands. Cryp-
tology ePrint Archive.
Chillotti, I., Gama, N., Georgieva, M., and Izabach
`
ene, M.
(2020). TFHE: Fast Fully Homomorphic Encryption
over The Torus. JoC.
Chillotti, I., Joye, M., and Paillier, P. (2021). Programmable
Bootstrapping Enables Efficient Homomorphic Infer-
ence of Deep Neural Networks. In CSCML.
Griffin: Towards Mixed Multi-Key Homomorphic Encryption
157

Dathathri, R., Kostova, B., Saarikivi, O., Dai, W., Laine, K.,
and Musuvathi, M. (2020). EVA: An Encrypted Vec-
tor Arithmetic Language and Compiler for Efficient
Homomorphic Computation. In PLDI.
Dathathri, R., Saarikivi, O., Chen, H., Laine, K., Lauter,
K., Maleki, S., Musuvathi, M., and Mytkowicz, T.
(2019). CHET: An optimizing compiler for fully-
homomorphic neural-network inferencing. In PLDI.
Ducas, L. and Micciancio, D. (2015). FHEW: Bootstrap-
ping Homomorphic Encryption in Less than A Sec-
ond. In EUROCRYPT.
Fan, J. and Vercauteren, F. (2012). Somewhat Practical
Fully Homomorphic Encryption. Cryptology ePrint
Archive. https://eprint.iacr.org/2012/144.
Fereidooni, H., Marchal, S., Miettinen, M., Mirhoseini, A.,
M
¨
ollering, H., Nguyen, T. D., Rieger, P., Sadeghi, A.-
R., Schneider, T., Yalame, H., and Zeitouni, S. (2021).
SAFELearn: Secure Aggregation for Private FEder-
ated Learning. In DLS@S&P.
Gehlhar, T., Marx, F., Schneider, T., Suresh, A., Wehrle,
T., and Yalame, H. (2023). SAFEFL: MPC-friendly
Framework for Private and Robust Federated Learn-
ing. In DLSP@S&P.
Gentry, C., Halevi, S., and Smart, N. P. (2012). Homomor-
phic Evaluation of the AES Circuit. In CRYPTO.
Goldreich, O., Micali, S., and Wigderson, A. (1987). How
to Play ANY Mental Game. In STOC.
Gorantala, S., Springer, R., Purser-Haskell, S., Lam, W.,
Wilson, R., Ali, A., Astor, E. P., Zukerman, I., Ruth,
S., Dibak, C., Schoppmann, P., Kulankhina, S., and
Forget, A. (2021). A General Purpose Transpiler for
Fully Homomorphic Encryption. Cryptology ePrint
Archive. https://eprint.iacr.org/2021/811.
Halevi, S. and Shoup, V. (2014). Algorithms in HElib. In
CRYPTO.
Han, K., Hhan, M., and Cheon, J. H. Improved Homomor-
phic Discrete Fourier Transforms and FHE Bootstrap-
ping. IEEE Access.
Hegde, A., M
¨
ollering, H., Schneider, T., and Yalame, H.
SoK: Efficient Privacy-preserving Clustering. PETS,
2021.
Heldmann, T., Schneider, T., Tkachenko, O., Weinert, C.,
and Yalame, H. (2021). LLVM-based Circuit Compi-
lation for Practical Secure Computation. In ACNS.
Joye, M. (2022). Guide to Fully Homomorphic Encryption
over the [Discretized] Torus. In TCHES.
Juvekar, C., Vaikuntanathan, V., and Chandrakasan, A.
(2018). GAZELLE: A Low Latency Framework for
Secure Neural Network Inference. In USENIX Secu-
rity.
Keller, H., M
¨
ollering, H., Schneider, T., and Yalame, H.
(2021). Balancing Quality and Efficiency in Private
Clustering with Affinity Propagation. In SECRYPT.
L
´
opez-Alt, A., Tromer, E., and Vaikuntanathan, V. (2012).
On-the-fly Multiparty Computation on The Cloud via
Multi-Key Fully Homomorphic Encryption. In STOC.
Lou, Q., Feng, B., Fox, G. C., and Jiang, L. (2020). Glyph:
Fast and Accurately Training Deep Neural Networks
on Encrypted Data. In NeurIPS.
Lu, W.-j., Huang, Z., Hong, C., Ma, Y., and Qu, H. (2021).
Pegasus: Bridging Polynomial and Non-polynomial
Evaluations in Homomorphic Encryption. In IEEE
S&P.
Lyubashevsky, V., Peikert, C., and Regev, O. (2010). On
Ideal Lattices and Learning with Errors over Rings.
In EUROCRYPT.
McMahan, B., Moore, E., Ramage, D., Hampson, S., and
y Arcas, B. A. (2017). Communication-Efficient
Learning of Deep Networks from Decentralized Data.
In AISTATS.
Microsoft Research (2020). Microsoft SEAL. https:
//github.com/Microsoft/SEAL. Microsoft Research,
Redmond, WA.
Mishra, P., Lehmkuhl, R., Srinivasan, A., Zheng, W., and
Popa, R. A. (2020). Delphi: A Cryptographic Infer-
ence Service for Neural Networks. In USENIX Secu-
rity.
Mohassel, P. and Zhang, Y. (2017). SecureML: A System
for Scalable Privacy-Preserving Machine Learning. In
IEEE S&P.
Mouchet, C., Bossuat, J.-P., Troncoso-Pastoriza, J., and
Hubaux, J.-P. (2020). Lattigo: A Multiparty Homo-
morphic Encryption Library in Go. In WAHC.
M
¨
unch, J.-P., Schneider, T., and Yalame, H. (2021). VASA:
Vector AES Instructions for Security Applications. In
ACSAC.
Nguyen, T. D., Rieger, P., Chen, H., Yalame, H., M
¨
ollering,
H., Fereidooni, H., Marchal, S., Miettinen, M., Mirho-
seini, A., Zeitouni, S., Koushanfar, F., Sadeghi, A.-
R., and Schneider, T. (2022). FLAME: Taming Back-
doors in Federated Learning. In USENIX Security.
Patra, A., Schneider, T., Suresh, A., and Yalame, H.
(2021a). ABY2.0: Improved Mixed-Protocol Secure
Two-Party Computation. In USENIX Security.
Patra, A., Schneider, T., Suresh, A., and Yalame, H.
(2021b). SynCirc: Efficient Synthesis of Depth-
Optimized Circuits for Secure Computation. In IEEE
HOST.
Regev, O. (2005). On Lattices, Learning with Errors, Ran-
dom Linear Codes, and Cryptography. In STOC.
Riazi, M. S., Weinert, C., Tkachenko, O., Songhori, E. M.,
Schneider, T., and Koushanfar, F. (2018). Chameleon:
A Hybrid Secure Computation Framework for Ma-
chine Learning Applications. In AsiaCCS.
Schneider, T., Suresh, A., and Yalame, H. (2023). Com-
ments on “Privacy-Enhanced Federated Learning
Against Poisoning Adversaries. IEEE TIFS.
Stehl
´
e, D., Steinfeld, R., Tanaka, K., and Xagawa, K.
(2009). Efficient Public Key Encryption Based on
Ideal Lattices. In ASIACRYPT.
Yao, A. C.-C. (1986). How to generate and exchange se-
crets. In FOCS.
SECRYPT 2023 - 20th International Conference on Security and Cryptography
158
