
On Single-Server Delegation Without Precomputation
Matluba Khodjaeva
1
and Giovanni Di Crescenzo
2 a
1
CUNY John Jay College of Criminal Justice, NY, U.S.A.
2
Peraton Labs, Basking Ridge, NJ, U.S.A.
Keywords:
Cryptography, Secure Delegation, Pairings, Elliptic Curves.
Abstract:
Many public-key cryptosystems use pairings as important primitive operations. To expand the applicability
of these solutions to computationally weaker devices, it has been advocated that a computationally weaker
client delegates such primitive operations to a computationally stronger server. Important requirements for
such delegation protocols include privacy of the client’s pairing inputs and security of the client’s output,
in the sense of detecting, except for very small probability, any malicious server’s attempt to convince the
client of an incorrect pairing result. Except for less than a handful of results, all single-server delegation
protocols in the literature are structured into an offline phase, where precomputation can be performed, and an
online phase, where the client has resource constraints. Designing single-server delegation protocols without
precomputation is naturally harder. In this paper, we show that the computation of a pairing with non-private
inputs can be efficiently delegated to a single server, without need for precomputation. We also discuss the
failure of a previously published attempt, and note the inefficiency of natural extensions of our protocol to
more demanding input cases.
1 INTRODUCTION
The area of server-aided cryptography investigates the
problem of computationally weaker clients delegat-
ing the most expensive cryptographic computations
to computationally powerful servers. Interest in this
area is recently increasing because of computation
paradigms shifts, including cloud/fog/edge comput-
ing, large-scale computations over big data, and com-
putations with resource-constrained devices, as in the
Internet of Things.
This problem of delegating (aka outsourcing)
computation in cryptography was first discussed in
(Feigenbaum, 1985; Abadi et al., 1989; Matsumoto et
al., 1988), first modeled in (Hohenberger and Lysyan-
skaya, 2005). Consistently with these and follow-up
papers in the area (see, e.g., (Gennaro et al., 2010;
Cavallo et al., 2015; Di Crescenzo et al., 2022)), we
consider a model where a client, denoted as C, with an
input x, delegates to a server, denoted as S, the com-
putation of a function F on the client’s input, and the
main desired requirements are:
1. result correctness: if C and S honestly run the pro-
tocol, at the end of the protocol C returns F(x);
a
https://orcid.org/0000-0002-5138-1144
2. input privacy: no new information about x should
be revealed to S;
3. result security: S should not be able, except pos-
sibly with very small probability, to convince C to
return a result different than F(x) at the end of the
protocol; and
4. efficiency: C’s runtime, denoted as t
C
, should be
much smaller than the runtime, denoted as t
F
,
of computing F(x) without delegation; moreover,
it is of interest to minimize S’s runtime t
S
, the
communication complexity cc, and the number of
messages mc.
In almost all previous work in single-server delega-
tion, protocols can be partitioned into (a) an offline
phase, where input x is not yet known, but somewhat
expensive pre-computation, performed by the client
or a client deployer, is stored on the client’s device,
and (b) an online phase, where client’s runtime is lim-
ited, and thus help by the server is needed to compute
F(x). This partition has proved very useful to obtain
delegation protocols for many operations often used
in cryptographic protocols (see, e.g., (Di Crescenzo
et al., 2022) for a survey in the area). The problem of
designing delegation protocols without offline phase
precomputation, which we consider in this paper (see
also Figure 1), is of interest for both theoretical and
540
Khodjaeva, M. and Di Crescenzo, G.
On Single-Server Delegation Without Precomputation.
DOI: 10.5220/0012140100003555
In Proceedings of the 20th International Conference on Security and Cr yptography (SECRYPT 2023), pages 540-547
ISBN: 978-989-758-666-8; ISSN: 2184-7711
Copyright
c
2023 by SCITEPRESS – Science and Technology Publications, Lda. Under CC license (CC BY-NC-ND 4.0)
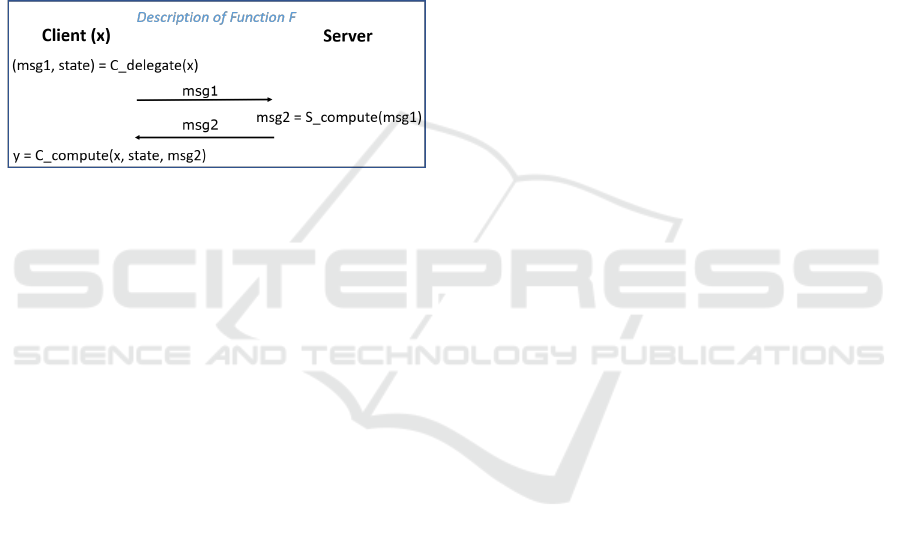
practical reasons. From a theoretical point of view,
a delegation protocol with precomputation typically
involves precomputation in the offline phase of the
same function that is being delegated on different in-
puts, while a delegation protocol without precompu-
tation would realize a more demanding type of del-
egated computation, giving different insights on the
problem that admit such solutions. From a practical
point of view, at the end of the offline phase, typi-
cally secret values are stored on the client’s resource-
constrained device, and the rest of the protocol has
to significantly rely on such values to remain secrets,
thus increasing the storage and trust requirements on
the system.
Figure 1: Delegated computation of y = F(x).
Our Contributions. In this paper we show that a
pairing (aka bilinear map) with publicly known inputs
can be efficiently and securely delegated to a single,
possibly malicious, server, without need for offline
phase precomputations. We show that our protocol
is efficient with respect to a number of metrics; most
notably, the client performs strictly less computation
than in non-delegated computation, for all 4 classes of
practical elliptic curve families underlying the pairing
definition. We also discuss the failure of a very recent
attempt (Kalkar et al., 2022), and observe the ineffi-
ciency of natural extensions of our protocol to more
demanding input scenario, where one of the two in-
puts or both have to remain private. Previously, del-
egation protocols without precomputation were given
for group inverses (Cavallo et al., 2015), for a batch
of group exponentiations with a single public base and
multiple public exponents (Di Crescenzo et al., 2017),
and for a batch of pairings with one public fixed in-
put and one public variable input from (Tsang et al.,
2007).
Related Work. Pairing-based cryptography, start-
ing with (Joux, 2000; Sakai et al., 2000; Boneh and
Franklin, 2001), has attracted much research in the
past 2-3 decades (see, e.g., (Moody et al., 2015)).
Single-server delegation protocols with precompu-
tation for pairings have been proposed in (Girault
and Lefranc, 2005; Guillevic and Vergnaud, 2014;
Chevallier-Mames et al., 2010; Kang et al., 2005; Ca-
nard et al., 2014; Kachisa et al., 2008; Guillevic and
Vergnaud, 2014; Canard et al., 2014; Di Crescenzo
et al., 2020a; Di Crescenzo et al., 2020b). A sur-
vey on delegated computation of specific operations
beyond cryptography can be found in (Shan et al.,
2018). A survey on delegated computation of ar-
bitrary functions, with clients more computationally
powerful than considered here, can be found in (Ah-
mad et al., 2018).
2 DEFINITIONS
Let G
1
, G
2
be additive cyclic groups of order l and
G
T
be a multiplicative cyclic group of the same order
l, for some large prime l. A pairing is an efficiently
computable map e : G
1
× G
2
→ G
T
, with description
denoted as desc(e), with the following properties:
1. Bilinearity: for all A ∈ G
1
and B ∈ G
2
, and for
any r,s ∈ Z
l
, it holds that e(rA, sB) = e(A,B)
rs
2. Non-triviality: if U is a generator for G
1
and V
is a generator for G
2
then e(U,V ) is a generator
for G
T
(this property rules out the trivial scenario
where e maps all of its inputs to 1).
The currently most practical pairing realizations use
an ordinary elliptic curve E defined over a field F
p
,
for some large prime p, as follows. Group G
1
is the l-
order additive subgroup of E(F
p
); group G
2
is a spe-
cific l-order additive subgroup of E(F
p
k
) contained
in E(F
p
k
) \ E(F
p
); and group G
T
is the l-order mul-
tiplicative subgroup of F
∗
p
k
. Here, k is the embed-
ding degree; i.e., the smallest positive integer such
that l|(p
k
− 1); F
p
k
is the extension field of F
p
of
degree k; and F
∗
p
k
is the field composed of non-zero
elements of F
p
k
. After the Weil pairing was consid-
ered in (Boneh and Franklin, 2001), more efficient
constructions were proposed as variants of the Tate
pairing, including the more recent ate pairing variants
(see, e.g., (Vercauteren, 2010; Scott, 2013; Barreto et
al., 2015) for details on the currently most practical
constructions).
For our results, we further assume that G
T
is a
subgroup of a group G
T
, also contained in F
∗
p
k
, with
the following two properties:
1. testing membership in G
T
is more efficient than
testing membership in G
T
;
2. all elements of G
T
have order ≥ l.
This assumption is satisfied by a recently proposed
security strengthening of the most practical pairing
realizations. Motivated by reducing the chances of
low-order attacks in cryptographic protocols, in (Bar-
reto et al., 2015) the authors proposed the notion of
On Single-Server Delegation Without Precomputation
541

subgroup-secure elliptic curves underlying a pairing,
in turn extending the notion of G
T
-strong curves from
(Scott, 2013). As a critical step in achieving these no-
tions, both of these papers set G
T
= G
Φ
k
(p)
, where
G
Φ
k
(p)
is the cyclotomic subgroups of order Φ
k
(p)
in F
∗
p
k
, and where Φ
k
(p) denotes the k-th cyclotomic
polynomial. Satisfaction of above property (2) is di-
rectly implied by the definitions of both G
T
-strong
and subgroup-secure curves. Satisfaction of above
property (1) when G
T
= G
Φ
k
(p)
is detailed in Sec-
tion 5.2 of (Barreto et al., 2015) for the curve families
BN-12, BLS-12, KSS-18, and BLS-24, in turn elabo-
rating on Section 8.2 of (Scott, 2013). There, testing
membership in G
T
is shown to only require one mul-
tiplication in G
T
and a few lower-order Frobenius-
based simplifications. As a comparison, currently the
best methods for testing membership in G
T
involve
a large-exponent exponentiation in G
T
(see, e.g., dis-
cussions in (Scott, 2021)). Thus, in our protocols, in-
stead of an expensive membership test for G
T
, we use
a much cheaper membership test for G
T
, and prove
that it suffices for our purposes, when used in con-
junction with our probabilistic correctness tests.
For parameterized efficiency evaluation of our
protocols, we will use the following definitions:
• a
i
: runtime for addition in G
i
, for i = 1,2;
• m
i
(`): runtime for scalar multiplication of a group
value in G
i
with an `-bit scalar value, for i = 1,2;
• m
T
: runtime for multiplication of group values in
G
T
;
• e
T
(`): runtime for an exponentiation in G
T
to an
`-bit exponent;
• p
T
: runtime for the bilinear pairing e;
• i
l
denotes the runtime for multiplicative inversion
in Z
l
;
• t
M
: runtime for testing membership of a value to
G
T
= G
Φ
k
(p)
.
We recall some well-known facts about these quan-
tities, of interest when evaluating the efficiency of
our protocols. First, for large enough `, a
1
<<
m
1
(`), a
2
<< m
2
(`), m
T
(`) << e
T
(`), and e
T
(`) <
p
T
. Also, using a double-and-add (resp., square-and-
multiply) algorithm, one can realize scalar multipli-
cation (resp., exponentiation) in additive (resp., mul-
tiplicative) groups using, for random scalars (resp.,
random exponents), about 1.5` additions (resp., mul-
tiplications). Membership of a value w in G
T
can be
computed using one exponentiation in G
T
to the l-th
power (i.e., checking that w
l
= 1), but we avoid this
or any other expensive group membership tests in our
protocols.
For numeric efficiency evaluation of our proto-
cols, we will use benchmark results from (Bos et al.,
2013) on runtime of an optimal ate pairing and of
other most expensive operations (i.e., scalar multipli-
cation in groups G
1
, G
2
and exponentiation in G
T
) for
some of the best curve families, also recalled in Ta-
ble 2. For both parameterized and numeric evaluation
of our protocols, we will neglect lower-order opera-
tions such as equality testing, assignments, Frobenius
calculations, etc.
3 A FLAWED PROTOCOL
In this section we review a protocol underlying the
first 3 delegation schemes in (Kalkar et al., 2022),
and study its properties. We show that this proto-
col satisfies result correctness without need for pre-
computation but does not satisfy result security, by
describing an adversary who, while acting as S, can
force C to return an incorrect output with probability
1. We also discuss the flaw in the proof for the result
security property which was described in (Kalkar et
al., 2022).
Informal Description: We consider the task of dele-
gating, without pre-computation, the computation of
a pairing e on input A ∈ G
1
and B ∈ G
2
, for the in-
put scenario where both A and B are publicly known
(thus, no input privacy is required). A very natural ap-
proach consists of C asking S to produce both the de-
sired pairing e(A,B) and a pairing for a related input
pair e(A
0
,B
0
), and use the relationship between (A,B)
and (A
0
,B
0
) to probabilistically check the correctness
of the first pairing value. We formally describe one
instance of this approach from (Kalkar et al., 2022).
Formal Description: A formal description of Algo-
rithm 1 (PVPV) in (Kalkar et al., 2022) for i = 1.
Input scenario: A and B are public online.
Online phase instructions:
1. C randomly chooses a, b ∈ Z
l
C computes A
0
:= aA and B
0
= bB
C sends A
0
,B
0
to S
2. S computes α := e(A,B) and α
0
:= e(A
0
,B
0
)
S sends α,α
0
to C
3. C checks that α, α
0
∈ G
T
C checks that α
0
= α
ab
If any of these tests fails,
C returns ⊥ and the protocol halts
C returns y := α
Remarks. In (Kalkar et al., 2022), the authors use a
particular case of this protocol as part of their delega-
tion protocol for a batch of pairing computations. We
SECRYPT 2023 - 20th International Conference on Security and Cryptography
542

note that their batch delegation protocol is a direct n-
fold repetition of the same subprotocol for each input
pair (A
i
,B
i
) in the batch. This subprotocol, in turn,
can be seen as a particular case of the protocol above
described; specifically the pair of values (a,b) is cho-
sen in a small set (i.e., [0, 2
t
] × {1}) in their protocol,
for some small value t, and in a much larger set (i.e.,
Z
l
× Z
l
) here, where l is the (large) order of pairing
groups G
1
,G
2
,G
T
. This generalization increases the
entropy of C’s message and thus even strengthens our
observation below that this approach is not successful.
Result Correctness Is Satisfied. To see that the result
correctness property is satisfied with probability 1, we
observe that if C and S follow the protocol, then C’s
output y satisfies y = e(A,B) by step 2 of the protocol,
and C does not output ⊥ since the verification check
in step 3 is satisfied, as:
α
0
= e(aA,bB) = e(A, B)
ab
= α
ab
.
Result Security Is Not Satisfied. To see that the re-
sult security property is not satisfied with probability
1, we now show an attacker algorithm S
0
which, when
playing as S, makes C return y 6= e(A, B) with proba-
bility very close to 1.
S’s instructions: On input C’s message (A
0
,B
0
), S
0
does the following:
1. randomly choose u,v ∈ Z
l
2. S
0
sets β := e(uA,vB) and β
0
:= e(uA
0
,vB
0
)
3. S
0
sends β,β
0
to C.
We now show that both of C’s verifications are sat-
isfied. About the first verification, we observe that
A
0
,uA, uA
0
∈ G
1
since so does A, B
0
,vB, vB
0
∈ G
2
since so does B, and thus β, β
0
∈ G
T
by definition of
pairing. About the second verification, we observe
that
β
0
= e(uA
0
,vB
0
) = e(u(aA), v(bB))
= e(a(uA),b(vB)) = e(uA,vB)
ab
= β
ab
.
Thus, C returns y = β = e(uA, vB), which is 6= e(A,B)
whenever u 6= 1 and v 6= 1, and thus with probability
1 − 1/l
2
.
Flaws in the Proof from (Kalkar et al., 2022). The
proof for the result security property, as written in
(Kalkar et al., 2022), is based on the following 3
claims:
1. A
0
leaks no information about a
2. A
0
is uniformly distributed since a is chosen uni-
formly random
3. Claim 2 implies Claim 1.
We now analyze these 3 claims.
As written, Claim 2 is unspecified because there
are no domains for the uniform distribution or set
from which a is chosen. Given that the protocol uni-
formly chooses a from [1,2
t
], and sets A
0
= a · A, a
correct revision of this statement would say that A
0
is
uniformly distributed in a 2
t
-size subset of G
1
since a
is chosen uniformly from [1,2
t
].
To meaningful analyze Claim 3, we observe that
the above updated variant of Claim 2 does not imply
Claim 1. This is because there are only 2
t
possible
values for a, if not conditioning on A,A
0
, and there is
only 1 value of a, when conditioning on A,A
0
.
Indeed Claim 1 is also false because given A,A
0
,
and a, it is possible to test whether A
0
= aA. In other
words, A
0
always leaks the output of a predicate of
equality to a given value a.
4 A NEW PROTOCOL
In this section we investigate client-server protocols
for pairing delegation, in the scenario where the two
pairing inputs are known to both parties, and there is
no offline phase or precomputation prior to the online
phase. In other words, all calculation will be done
only during the online phase. Our main result is a new
protocol with desirable security and efficiency prop-
erties. In what follows, we give a formal statement
of our result, an asymptotic and concrete efficiency
comparison with the previous most efficient protocols
in the same input scenario, an informal description of
the ideas behind the protocol, a formal description of
the protocol and a proof of the protocol’s correctness
and security properties.
Theorem 4.1. Let e be a pairing, as defined in Sec-
tion 2, let σ be its computational security param-
eter, and let λ be a statistical security parameter.
There exists (constructively) a client-server protocol
(C, S) for delegating the computation of e without pre-
computation, when inputs A and B are both publicly
known in the online phase, which satisfies 1-result
correctness, 2
−λ
-result security, and efficiency with
parameters (t
S
,t
C
,cc, mc), where
– t
S
= 3 p
T
– t
C
≤ a
1
+ i
l
+ m
1
(σ) + m
T
+ e
T
(λ) + e
T
(r) + 2t
M
– cc = 2 values in G
1
+ 3 values in G
T
– mc = 2.
The main takeaway from this theorem is that C can
securely and efficiently delegate to S the computation
of a bilinear pairing whose both inputs A and B are
publicly known in the online phase and where there
is no offline phase for C to precomputes anything. In
On Single-Server Delegation Without Precomputation
543

particular, in the online phase C performs one group
exponentiation and 1 exponentiation to a λ-bit expo-
nent in G
T
, and 1 group multiplication and 1 multipli-
cation to a λ-bit scalar in G
1
, as well as other lower-
order operations; see also Table 3 for a more detailed
analysis of the asymptotic performance of our proto-
col, even compared with previous work. The numeric
efficiency improvement over non-delegated computa-
tion was estimated to range between 1.353 and 2.832
depending on the curve used; see also Table 3. Addi-
tionally, C does not precalculate any operations dur-
ing offline phase, S only computes 3 pairings, and C
and S only exchange 2 messages containing a small
number of group values.
Protocol Description. The main idea in this pro-
tocol is that since both inputs A and B are publicly
known, S can compute w
0
= e(A,B) and send w
0
to C, along with some efficiently verifiable ‘proof’
that w
0
was correctly computed. This proof is re-
alized by the following 3 steps: first, C sends to S
a randomized version Z
0
and Z
1
of a randomly cho-
sen value U and the input value A (masked using
U); then S computes and sends to C pairing values
w
1
= e(Z
0
,B) and w
2
= e(Z
1
,B); and finally C ver-
ifies that w
0
,w
1
∈ G
T
and uses w
0
,w
1
and w
2
in an
efficient probabilistic verification for the correctness
of S’s message (w
0
,w
1
,w
2
). We stress that instead
of performing offline calculations, C performs 1 ex-
ponentiation with a full-domain exponent and 1 ex-
ponentiation with a 1 short, λ-bit exponent, in group
G
T
. A formal description follows.
Formal Description of Protocol P
1
(C,S).
Online Input to C and S: 1
σ
,1
λ
, desc(e), A ∈ G
1
, and
B ∈ G
2
Online phase instructions:
1. C randomly chooses b ∈ {1, ...,2
λ
}, and U ∈ G
1
;
C sets u
0
:= u
−1
mod l, Z
0
:= u
0
· U, and Z
1
:=
b · A +U
C sends Z
0
,Z
1
to S
2. S computes w
0
:= e(A, B), w
1
:= e(Z
0
,B) and
w
2
:= e(Z
1
,B)
S sends w
0
,w
1
,w
2
to C
3. Membership Test: C checks that w
0
,w
1
∈ G
T
Probabilistic Test: C checks that w
2
= w
b
0
· w
u
1
If any of these tests fails,
C returns ⊥ and the protocol halts
C returns y = w
0
Properties of Protocol P
1
(C, S): The efficiency prop-
erties are verified by protocol inspection. In particu-
lar:
- Round complexity: the online phase of the proto-
col only requires two messages: one from C to S,
followed by one from S to C.
- Communication complexity: during the online
phase, C sends 2 values in G
1
and S sends 3 values
in G
T
.
- Runtime complexity: the runtime property directly
follows by protocol inspection. In particular, C’s
calculation of Z
0
,Z
1
only requires 1 group multi-
plication, 1 multiplication to a short, λ-bit, scalar,
and 1 scalar addition in a group G
1
. In C’s G
T
-
membership test only requires 1 multiplication in
G
T
for each membership test, as discussed in Sec-
tion 2, total 1 multiplications in G
T
, and C’s prob-
abilistic test requires 1 multiplication, 1 group
multiplication and 1 exponentiation in G
T
to a
short, λ-bit, exponent.
The correctness property follows by showing that
if C and S follow the protocol, C always output y =
e(A,B). We show that the 2 tests performed by C are
always passed. The membership test is always passed
by pairing definition; the probabilistic test is always
passed since
w
2
= e(Z
1
,B) = e(b · A +U,B)
= e(A,B)
b
· e(U, B) = e(A,B)
b
· e(u
−1
·U,B)
u
= e(A,B)
b
· e(Z
0
,B)
u
= w
b
0
· w
u
1
.
This implies that C never returns ⊥, and thus returns
y = w
0
= e(A,B).
To prove the security property against any mali-
cious S we need to compute an upper bound ε
s
on the
security probability that S convinces C to output a y
such that y 6= e(A,B). We obtain that ε
s
≤ 2
−λ
as a
consequence of the following 3 facts, which we later
prove:
1. (Z
0
,Z
1
) leaks no information about b to S;
2. for any S’s message (w
0
,w
1
,w
2
) different than
what would be returned according to the proto-
col instructions, there is only one b for which the
tuple (w
0
,w
1
,w
2
) satisfies both membership and
probabilistic tests in step 2;
3. for any S’s message (w
0
,w
1
,w
2
) different than
what would be returned according to the proto-
col instructions, the probability that (w
0
,w
1
,w
2
)
satisfies the probabilistic test is ≤ 2
−λ
.
Towards proving Fact 1, we observe that: (a) Z
0
=
u
−1
·U is uniformly and indigently distributed in G
1
since so is the u in Z
l
and it does not leak any in-
formation about U in G
1
; (b) Z
1
= b · A + U is also
uniformly distributed in G
1
since so is U by (a) and
Z
1
does not leak any information about b to S.
SECRYPT 2023 - 20th International Conference on Security and Cryptography
544
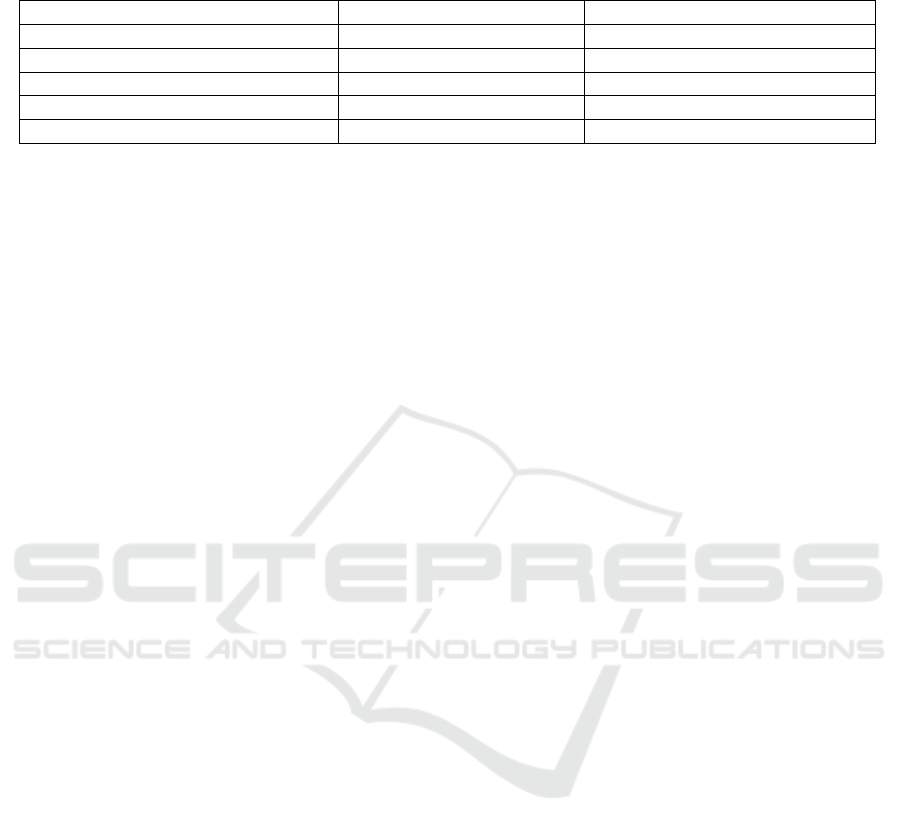
Table 1: Protocols comparison in the input scenario (A and B public online). The expressions for t
C
only include higher-order
functions p
T
,e
T
,m
1
,m
2
.
Protocols C’s pre-calculation (t
P
) C’s online calculation (t
C
)
(Chevallier-Mames et al., 2010) §5.2 p
T
+ e
T
(r) + m
1
(r) + m
2
(r) 3e
T
(r) + m
1
(r) + m
2
(r)
(Canard et al., 2014) §4.1 p
T
+ e
T
(r) + m
1
(r) + m
2
(r) e
T
(r) + m
1
(r) + m
2
(r)
(Di Crescenzo et al., 2020a) §4.1 2 p
T
+ m
2
(r) + 2 m
1
(r) 2e
T
(λ) + m
2
(λ) + m
1
(r) + m
1
(λ)
(Di Crescenzo et al., 2020b) §3 p
T
+ m
2
(r) e
T
(λ) + m
2
(λ) + m
1
(r)
Ours [§ 4] 0 e
T
(r) + e
T
(λ) + m
1
(r)
Towards proving Fact 2, let (w
0
,w
1
,w
2
) be
the values that would be returned by S accord-
ing to the protocol, and assume a malicious algo-
rithm Adv, corrupting S returns a different triple
(w
0
0
,w
0
1
,w
0
2
). Note that if w
0
0
6∈ G
T
or w
0
1
6∈ G
T
, the
triple (w
0
0
,w
0
1
,w
0
2
) does not satisfy the group G
T
-
membership test. Thus, we assume that both w
0
0
∈ G
T
and w
0
1
∈ G
T
and observe that if triple (w
0
0
,w
0
1
,w
0
2
)
satisfies the probabilistic correctness test, then w
0
2
∈
G
T
. Because G
T
is a multiplicative group, we can
write w
0
i
= d
i
· w
i
for i = 0,1, 2 and some d
0
,d
1
,d
2
∈
G
T
such that d
0
6= 1 or d
1
6= 1 or d
2
6= 1. Now, as-
sume wlog that d
0
6= 1 and consider the following
equivalent rewritings of the probabilistic test, ob-
tained by variable substitutions and simplifications:
w
0
2
= (w
0
0
)
b
· (w
0
1
)
u
d
2
· w
2
= (d
0
· w
0
)
b
· (d
1
· w
1
)
u
d
2
· w
2
= (d
b
0
· d
u
1
) · w
b
0
· w
u
1
d
2
= d
b
0
· d
u
1
d
2
(d
1
)
−u
= d
b
0
,
where the 4th equality follows from the correctness
property implying that w
2
= w
b
0
· w
u
1
.
Now, if there exist two distinct b
1
and b
2
, assumed
wlog to satisfy b
1
> b
2
, and such that
d
2
(d
1
)
−u
= d
b
1
0
and d
2
(d
1
)
−u
= d
b
2
0
,
then d
b
1
−b
2
0
= 1. By our assumption that every el-
ement in G
T
has order > l, which is > 2
λ
, and by
observing that b
1
− b
2
< 2
λ
, we derive that d
0
cannot
have order ≤ b
1
− b
2
. Thus the equality d
b
1
−b
2
0
= 1
can only hold when b
1
= b
2
.
This proves Fact 2.
Towards proving Fact 3, note that, by Fact 1, C’s
message Z
0
,Z
1
does not leak any information about
b. This implies that all values in {1,..., 2
λ
} are still
equally likely for c even when conditioning over mes-
sages Z
0
,Z
1
. Then, by using Fact 2, the probability
that S’s message (w
0
,w
1
,w
2
) satisfies the probabilis-
tic test, is 1 divided by the number 2
λ
of values of
b that are still equally likely when conditioning over
message Z
0
,Z
1
. This proves Fact 3.
4.1 Extension to Other Input Cases
A Private and B Public. In this input scenario, we
can define protocol P
2
by some natural modifications
to protocol P
1
, where C further apply a random mask
to A before asking S to compute and return pairings,
and later C performs one more exponentiation in G
T
to undo the mask, and recover the desired pairing
value.
A and B Private. In this input scenario, we can de-
fine protocol P
3
by some natural modifications to pro-
tocols P
1
and P
2
, where C further applies a random
mask to both A and B before asking S to compute and
return pairings, and later C performs one more expo-
nentiation in G
T
to undo the masks, check the cor-
rectness of the received values and recover the desired
pairing value.
Performance Analysis. In our performance analy-
sis for protocols P
2
and P
3
, C’s runtime is only lower
than non-delegated computation for one of the 4 con-
sidered curve families.
5 NUMERICAL PERFORMANCE
ANALYSIS
We show a numerical performance analysis of our
protocols from Section 4, as well as previous proto-
cols from the literature in each of the considered in-
put scenarios. Our numerical performance analysis
consists of using benchmark results from (Bos et al.,
2013) for the runtime of an optimal ate pairing and of
the other most expensive operations (i.e., scalar multi-
plication in groups G
1
, G
2
and exponentiation in G
T
)
for relative to an optimal ate pairing based on some
of the currently most practical elliptic curve families
(i.e., BN-12, BLS-12, KSS-18, BLS-24), also recalled
in Table 2. In Table 3 we compare the performance of
our protocols in Section 4 with past work for the same
input scenario.
On Single-Server Delegation Without Precomputation
545
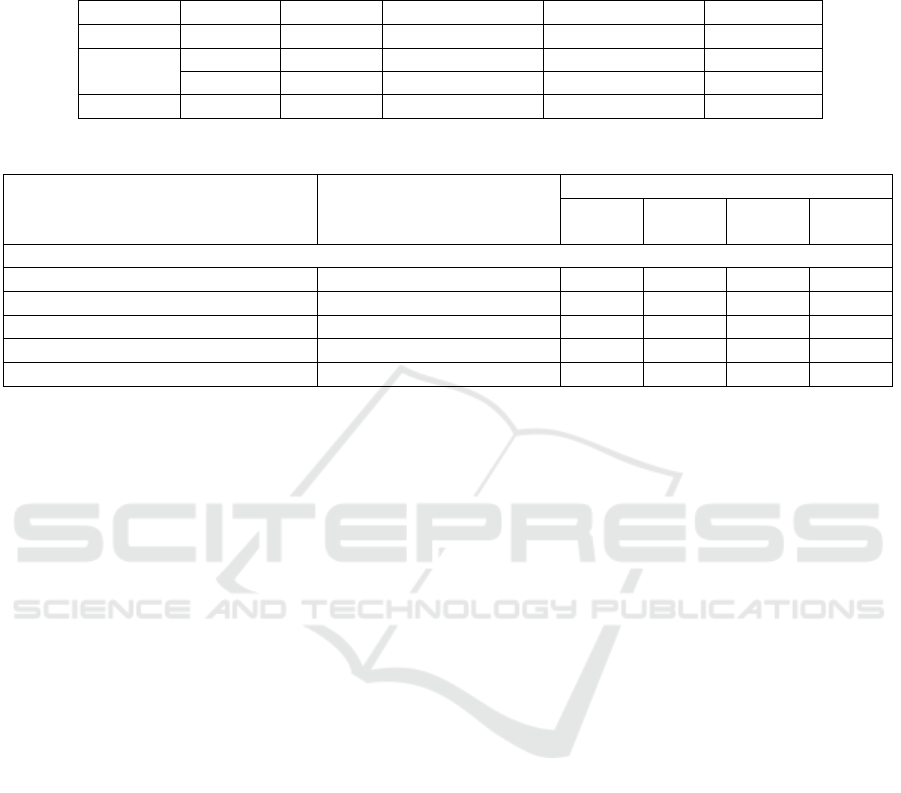
Table 2: Benchmark results (obtained by (Bos et al., 2013) on an Intel Core i7-3520M CPU averaged over thousands of
random instances) for scalar multiplications in G
1
,G
2
and exponentiations in G
T
relative to an optimal ate pairing based on
some of the best known curve families, measured in millions (M) of clock cycles. The security levels are from (Bos et al.,
2013), except for BN-12, whose level was reduced because of recent attacks (Kim and Barbulescu, 2016).
Sec. level Family-k Pairing e Scal. mul. in G
1
Scal. mul. in G
2
Exp. in G
T
105-bits BN-12 7.0 0.9 1.8 3.1
192-bits
BLS-12 47.2 4.4 10.9 17.5
KSS-18 63.3 3.5 9.8 15.7
256-bits BLS-24 115.0 5.2 27.6 47.1
Table 3: Protocols comparison in scenarios where both A and B are publicly known.
Protocols C’s pre-calculation (t
P
)
Ratio: p
T
/t
C
BN12
r = 210
BLS12
r = 424
KSS18
r = 376
BLS24
r = 504
Input Scenario: (A and B are publicly known and thus no input privacy is required)
(Chevallier-Mames et al., 2010) §5.2 p
T
+ e
T
(r) 0.580 0.694 1.045 0.659
(Canard et al., 2014) §4.1 p
T
+ e
T
(r) + m
1
(r) + m
2
(r) 1.197 1.433 2.173 1.434
(Di Crescenzo et al., 2020a) §4 2 p
T
+ m
2
(r) + 2 m
1
(r) 2.001 4.045 6.869 5.571
(Di Crescenzo et al., 2020b) §3 p
T
+ m
2
(r) 2.981 5.519 8.216 7.994
This paper §4 0 1.353 1.881 2.832 1.958
6 CONCLUSIONS
In this paper we studied the problem of techniques
for a computationally weaker client to efficiently, pri-
vately and securely delegate bilinear pairings to a sin-
gle, possibly malicious, server, without precompu-
tation. Previously to this paper, we only knew of
two examples of operation commonly used in cryp-
tographic protocols having such delegation protocols
without precomputation: group inverses, and multiple
group exponentiations with a public base and mul-
tiple public exponents. It remains of interest to ex-
tend our protocol to more elaborated input scenarios
(i.e., keeping input privacy) while achieving client ef-
ficiency for many curve families of interest in practi-
cal applications of pairings. It also remains of interest
to find more operations often used in cryptography
constructions for which such delegation protocols ex-
ist.
ACKNOWLEDGEMENTS
Work by Matluba Khodjaeva was supported by a
Faculty Scholarship grant from the Office for the
Advancement of Research at John Jay College and
PSC CUNY Cycles 53 and 54. Work by Giovanni
Di Crescenzo was supported by the Defense Ad-
vanced Research Projects Agency (DARPA), contract
n. HR001120C0156. Approved for Public Release,
Distribution Unlimited. The U.S. Government is au-
thorized to reproduce and distribute reprints for Gov-
ernmental purposes notwithstanding any copyright
annotation hereon. Disclaimer: The views and con-
clusions contained herein are those of the authors and
should not be interpreted as necessarily representing
the official policies or endorsements, either expressed
or implied, of DARPA, or the U.S. Government.
REFERENCES
M. Abadi, J. Feigenbaum, J. Kilian, On Hiding Information
from an Oracle In: J. Comput. Syst. Sci. 39(1): 21-50
(1989).
H. Ahmad, L. Wang, H. Hong, J. Li, H. Dawoo, M. Ahmed,
Y. Yang, Primitives towards verifiable computation: a
survey. In Front. Comput. Sci. 2018, Vol. 12, Issue (3)
: 451-478.
P.S.L.M. Barreto, C. Costello, R. Misoczki, M. Naehrig,
G.C.C.F. Pereira, G. Zanon, Subgroup security in
pairing-based cryptography. In Lauter K., Rodr
´
ıguez-
Henr
´
ıquez F. (eds) LATINCRYPT 2015. LCNS vol.
9230. Springer.
D. Boneh, M. Franklin, Identity-based encryption from the
weil pairing. In Kilian J. (eds) Advances in Cryptol-
ogy — CRYPTO 2001. LNCS vol 2139. Springer.
J.W. Bos, C. Costello, M. Naehrig, Exponentiating in pair-
ing groups. In Lange T., Lauter K., Lison
ˇ
ek P. (eds)
SAC 2013. LNCS vol 8282. Springer.
S. Canard, J. Devigne, O. Sanders: Delegating a pairing
can be both secure and efficient. In Boureanu I., Owe-
sarski P., Vaudenay S. (eds) Applied Cryptography
SECRYPT 2023 - 20th International Conference on Security and Cryptography
546

and Network Security. ACNS 2014. LNCS vol 8479.
Springer
B. Cavallo, G. Di Crescenzo, D. Kahrobaei, V. Shpilrain,
Efficient and secure delegation of group exponentia-
tion to a single server. In Proc. of RFIDSec 2015: pp.
156–173, LNCS, Springer.
X. Chen, W. Susilo, J. Li, D.S. Wong, J. Ma, S. Tang, and
Q. Tang, Efficient algorithms for secure outsourcing
of bilinear pairings. In Theor. Comput. Sci., vol. 562,
no. 9, pp. 112–121, 2015.
B. Chevallier-Mames, J.S. Coron, N. McCullagh, D.
Naccache, M. Scott: Secure delegation of elliptic-
curve pairing. Cryptology ePrint Archive. In Proc.
of Smart Card Research and Advanced Application.
CARDIS 2010. LNCS vol 6035. Springer. Also in
http://eprint.iacr.org/2005/150.
G. Di Crescenzo, M. Khodjaeva, D. Kahrobaei, V. Shpil-
rain, Secure and Efficient Delegation of Elliptic-Curve
Pairing. In: Proc. of ACNS 2020. LNCS, vol 12146.
Springer, Cham.
G. Di Crescenzo, M. Khodjaeva, D. Kahrobaei, V. Shpil-
rain, Secure and Efficient Delegation of Pairings with
Online Inputs. In: Proc. of CARDIS 2020. LNCS, vol.
12609. Springer.
G. Di Crescenzo, M. Khodjaeva, D. Kahrobaei, and V. Sh-
pilrain, Computing Multiple Exponentiations in Dis-
crete Log and RSA Groups: From Batch Verification
to Batch Delegation. In Proc. of 3rd IEEE Workshop
on Security and Privacy in the Cloud, IEEE, 2017.
G. Di Crescenzo, M. Khodjaeva, D. Kahrobaei, and V. Sh-
pilrain: A Survey on Delegated Computation. In Proc.
of DLT 2022: 33-53.
J. Feigenbaum, Encrypting Problem Instances: Or ..., Can
You Take Advantage of Someone Without Having to
Trust Him? In Proc. of CRYPTO 1985: 477-488.
R. Gennaro, C. Gentry, B. Parno, Non-interactive veri-
fiable computing: Outsourcing computation to un-
trusted workers. In Proc. of CRYPTO 2010, LNCS
6223, pp. 465–482.
M. Girault, D. Lefranc, Server-aided verification: Theory
and practice. In Roy, B.K. (ed.) ASIACRYPT 2005.
LNCS, vol. 3788, pp. 605–623.
A. Guillevic, D. Vergnaud, Algorithms for outsourcing pair-
ing computation. In Joye M., Moradi A. (eds) Smart
Card Research and Advanced Applications. CARDIS
2014. LNCS vol 8968. Springer.
S. Hohenberger, A. Lysyanskaya, How to securely out-
source cryptographic computations. In Proc. of TCC
2005, pp. 264–282, Springer.
A. Joux, A one round protocol for tripartite Diffie-Hellman,
in Proc. of ANTS IV, LNCS, vol. 1838, Springer,
2000, pp. 385–393.
E.J. Kachisa, E.F. Schaefer, M. Scott, Constructing Brezing-
Weng pairing friendly elliptic curves using elements in
the cyclotomic field. In Galbraith S.D., Paterson K.G.
(eds) Pairing-Based Cryptography – Pairing 2008.
LNCS vol. 5209. Springer.
B.G. Kang, M.S. Lee, J.H. Park, Efficient delegation of pair-
ing computation. In IACR Cryptology ePrint Archive,
n. 259, 2005.
O. Kalkar, I. Sertkaya, and S. Tutdere, On The Batch Out-
sourcing Of Pairing Computations, in: The Computer
Journal, 2022.
T. Kim, R. Barbulescu, Extended Tower Number Field
Sieve: A New Complexity for the Medium Prime Case.
In Proc. of CRYPTO (1) 2016, pp. 543–571, Springer.
T. Matsumoto, K. Kato, H. Imai, An improved algorithm
for secure outsourcing of modular exponentiations.
In Proc. of CRYPTO 1988, pp. 497–506, LNCS,
Springer.
D. Moody, R. Peralta, R. Perlner, A. Regenscheid, A. Ro-
ginsky, and L. Chen, Report on Pairing-based Cryp-
tography, in J. Res. Natl. Inst. Stand. Technol. 120:
11–27, 2015.
M. Scott, Unbalancing pairing-based key exchange pro-
tocols. In IACR Cryptology ePrint Archive, n. 688,
2013.
M. Scott, A note on group membership tests for G
1
, G
2
and
G
T
on BLS pairing-friendly curves. In IACR Cryptol-
ogy ePrint Archive, n. 1130, 2021.
R. Sakai, K. Ohgishi, andM. Kasahara, Cryptosystems
based on pairing, in Symposium on Cryptography and
Information Security (SCIS), 2000.
Z. Shan, K. Ren, M. Blanton, C. Wang, Practical Secure
Computation Outsourcing: A Survey. In ACM Com-
put. Surv. 51(2): 31:1-31:40, 2018.
P. Tsang, S. Chow, and S. Smith Batch pairing del-
egation. In: Proceedings of International Work-
shop on Security Nara, Japan, 29-31 October, 2007,
pp.74–90.Springer,Berlin.
F. Vercauteren, Optimal Pairings. In IEEE Transactions on
Information Theory, vol. 56, no. 1, pp. 455–461, Jan.
2010.
On Single-Server Delegation Without Precomputation
547
