
Target Planning for UAV Merchant Ship Recognition Based on KNN
Nearest Neighbor Algorithm
Meili Zhang
*
, Yue Yang, Hongmei Pei and Weili Liu
Dalian Naval Academy, Dalian, China
Keywords: Merchant Ship Identification, UAV, KNN Nearest Neighbor Algorithm, Shortest Path Algorithm.
Abstract: The planning of the port closure and control force is an important issue related to the port defence in the
face of war. According to the given information and the given coordinate information, this paper makes an
initial classification of them, and uses KNN nearest neighbour algorithm to classify the location information
of the given coordinates and obtain the central point by using its clustering information. After classification
training, its accuracy is high, and it is most appropriate when k=5. After obtaining the best classification
central point, take the classification central point as the initial starting position of the UAV, and take five
points as the starting points to establish the shortest path problem based on the Dijkstra algorithm. Based on
the idea of the shortest path, build the path planning strategy, analyse, model, and solve from a new
perspective, and optimize the closure and control force planning.
1 INTRODUCTION
In recent years, with the increasingly fierce
competition for maritime rights and interests of
various countries and the increasingly severe anti-
terrorism situation, coastal ports and bases have
gradually become the targets of terrorists and
enemies. With the military's awareness of the threat
to the security of ports and important coastal bases,
security measures at these strategic locations have
been gradually strengthened in recent years, leaving
fewer and fewer opportunities for terrorists and
adversaries to carry out sabotage from the road.
Therefore, the sealing-control operation planning of
the port is an important issue concerning the port
protection in the state of battle. In order to complete
the combat task, it is necessary to identify and
classify the merchant ships entering the port, and
study how to use UAVs to plan and intercept the
target and find the optimal strategy in the case of
port sealing and control.
At present, the research on port containment and
control operation planning mainly focuses on the
safety identification of merchant ships and the target
planning of coast guard ships and frigates in
blockade and interception operations. Although most
of the literature gives calculation methods from
different perspectives, most of these calculation
formulas are recursive formulas, which is rather
complicated. This paper mainly solves the problem
of optimizing the use of UAVs in the class
identification of all merchant ships and the problem
of sealing, control and interception and force
adjustment strategy.
2 PERPROBLEM DESCRIPTION
It is assumed that the port's external route is located
in a fan-shaped area with the port as the centre of the
circle and the orientation between 20°and
70°clockwise with the direction of due north, and the
course of merchant ships heading to a certain port
points to the centre of the circle, and the interception
disposal area is shown as the figure ABCD, as
shown in Figure 1.
Figure 1: Port diagram.
Zhang, M., Yang, Y., Pei, H. and Liu, W.
Target Planning for UAV Merchant Ship Recognition Based on KNN Nearest Neighbor Algorithm.
DOI: 10.5220/0012272700003807
Paper published under CC license (CC BY-NC-ND 4.0)
In Proceedings of the 2nd International Seminar on Artificial Intelligence, Networking and Information Technology (ANIT 2023), pages 11-15
ISBN: 978-989-758-677-4
Proceedings Copyright © 2024 by SCITEPRESS – Science and Technology Publications, Lda.
11
There are currently two frigates and three coast
guard ships performing containment and control
tasks. According to the given data, it is generally
required that all Class III ships be intercepted, and
the task planning of containment forces with the
highest interception rate for Class II ships is given,
including the initial position of deployment,
interception objects, and movement trajectory.
3 RECOGNITION OF
MERCHANT SHIPS --
ESTABLISHMENT AND
SOLUTION OF KNN MODEL
OF NEAREST NODE
ALGORITHM
Target identification refers to the identification of
target attributes, including motion attributes
(tonnage, velocity, acceleration, etc.), friend or foe
attributes (our side, friend, enemy, unknown), inter-
class attributes (air, sea, underwater), type attributes
(ship type or model) and class. The important
significance of target recognition is that it is
combined with target state estimation to form the
basis of battlefield situation assessment and threat
estimation and is an important basis for tactical
decision-making.
In general, merchant ships are divided into three
categories: merchant ships carrying general
necessities (Class I), merchant ships carrying major
strategic materials such as oil or gas (Class II), and
merchant ships carrying contraband such as weapons
and equipment (Class III). The significance of
merchant ship identification is that it is combined
with target state estimation, which forms the basis of
battlefield situation assessment and threat estimation
and is an important basis for tactical decision-
making.
At present, the methods that can be used for
security classification are decision tree (Kleinberg J
M, 1999), genetic algorithm (Gongde Guo, 2006),
neural network (Feng Guohe, 2012), naive Bayes
(Tang Huxin, 2016), vote-based method (Liu Tong,
2018), Rocchio classification (Zhang Zitong, 2019),
KNN classification (Shaozhong Cao, 2012),
maximum entropy (Shen Yuqing, 2004), etc. KNN
algorithm is one of the simplest methods in data
mining classification technology.
3.1 KNN Algorithm
KNN algorithm is mainly based on a limited number
of adjacent samples to determine the category, so it
can be classified by measuring the distance between
different eigenvalues. Based on the KNN algorithm,
the proximity of the distance between the initial
information samples of merchant ships and the
mathematical values of these points is generally
measured by Euclidean distance. Assuming there are
two points p and q in the position samples of
merchant ships, the Euclidean distance formula
between the two points is
In addition, its testing phase is slow and
expensive in terms of time and memory, requiring
large memory to store the entire training data set for
prediction. Because KNN uses the Euclidean metric
between two data points to find the nearest
neighbour, we need to scale the number. In other
words, KNN algorithm is not suitable for large-
dimensional data, so it needs to reduce the
dimension to improve performance, but it has a good
classification effect for small data sets in this paper.
Moreover, to get better results, we standardize data
on the same scale, choosing a standardized range
considered between 0 and 1.
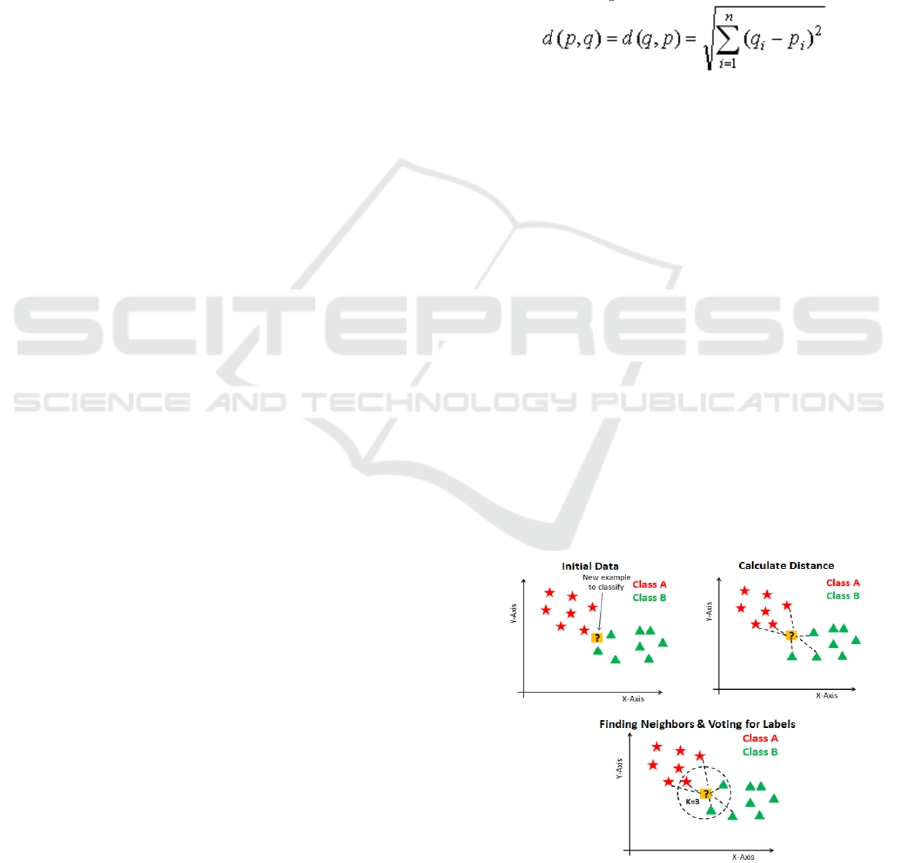
In the KNN algorithm, k is the number of nearest
neighbours, and this number of neighbours is the
decisive core factor. If the number of classes is 2,
then k is usually an odd number. When k = 1, the
algorithm is called the nearest neighbour algorithm.
Specific calculation steps are as follows, as shown in
Figure 2.
Figure 2: Specific calculation steps.
ANIT 2023 - The International Seminar on Artificial Intelligence, Networking and Information Technology
12
The KNN algorithm is more accurate at performing
a smaller number of features than a larger number of
features. As the number increases, the amount of
data required exceeds it. At the same time, the
increase in size will also lead to the problem of
overfitting. Its neighbourhood number k is a hyper
parameter that needs to be selected during modelling,
and k can be regarded as the control variable of the
prediction model, as shown in Figure 3.
Figure 3: Category distance diagram.
To sum up, the nearest node algorithm is used to
classify the location information of a given
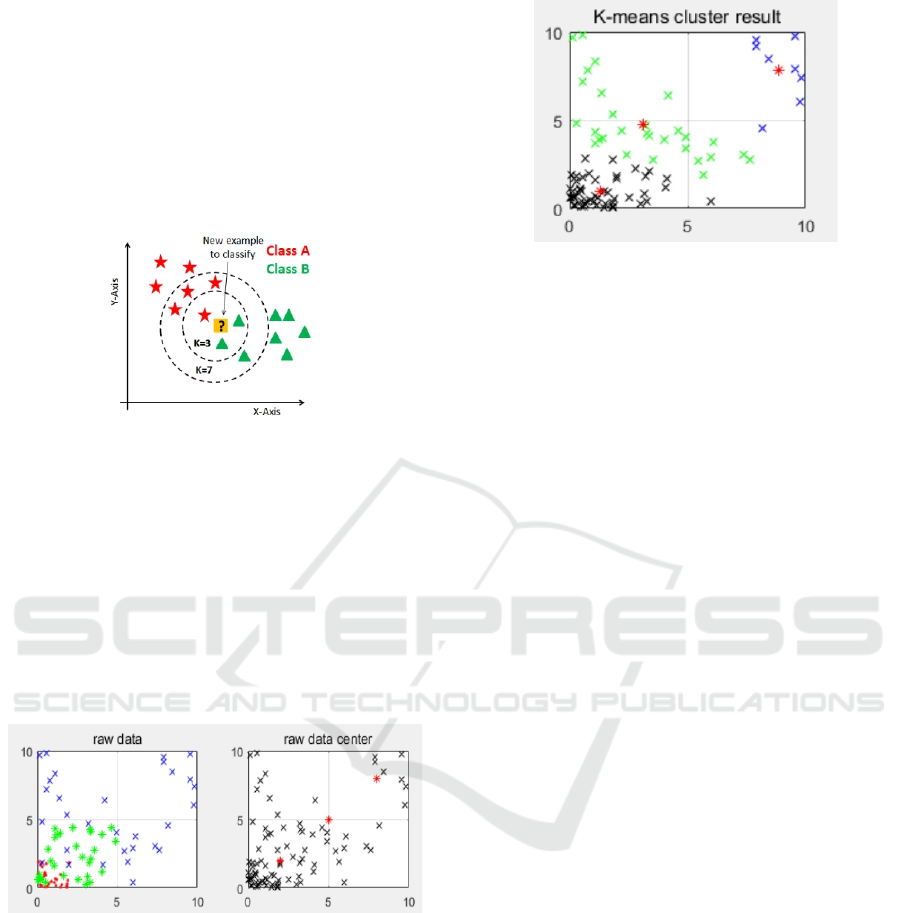
coordinate and obtain the central point. The position
of each merchant ship is displayed through KNN
model clustering by MATLAB software program, so
that the merchant ship is recognized and detected by
UAV. Figure 4 shows the positions of the three
classes of merchant ships on the left, and the red dot
on the right of Figure 4 shows the central points of
the three classes of merchant ships.
Figure 4: Classification and central points of merchant
ships.
The above results are summarized in Figure 5,
which shows the positions of class I, II, and III
merchant ships and their central points respectively.
Figure 5: Merchant vessel category classification and
central point.
The problem of identification and safety
classification of merchant ships uses the thought
information of clustering
to classify the location
information of a given coordinate and obtain the
central point. After classification training, its
accuracy is high, that is, the most appropriate K=5.
3.2 Dijkstra Algorithm
The existing means can find out the geographical
location, course speed and other information of the
commercial ship to enter the port at a long distance,
but the nature of the cargo carried by it needs to use
the UAV close-in reconnaissance.
The unmanned reconnaissance aircraft is
equipped with TV cameras, forward-looking
infrared instrument, synthetic aperture radar and
other loads, with an endurance time of more than 30
hours, a cruise speed of 120km/h, and strong
mobility (turning radius is not considered) and can
be independently deployed in important sea areas to
implement long-term and continuous reconnaissance
and surveillance tasks on maritime targets. The
UAV approaches the target at sea according to the
location information provided by the intelligence.
When the weather conditions are good, the target
can be found at 20-30km, and the altitude can be
lowered after approaching 10km. The UAV will
circle the target for several weeks at a distance of no
more than 2km and take pictures from multiple
perspectives. Shore-based operators can identify the
ship name (side number), ship type (such as
container ship, oil tanker, natural gas tanker, cruise
ship), material type (such as oil, natural gas, coal,
iron ore, container material), flag (nationality), etc.,
and compare with the information and ship database
obtained by the red side to determine whether the
ship name and appearance are consistent. Whether
the ship name is altered or forged, whether the bad
records are in the case, whether the weapons and
Target Planning for UAV Merchant Ship Recognition Based on KNN Nearest Neighbor Algorithm
13
equipment are smuggled, etc., climb and fly away
after the completion of the identification, the entire
identification process takes 10 minutes, and the
identification results can be shared to any demand
party in real time.
The most commonly used routing algorithms
include Dijkstra algorithm (Liu Xuhong, 2005),
SPFA algorithm (Nannicini, 2008), Bellman-Ford
algorithm (Bang-Jensen, 2000), Floyd algorithm
/Floyd-Warshall algorithm (Shi Ren, 2009) to adjust
and intercept strategy schemes. In order to solve the
UAV reconnaissance route after the classification
results in the model, the shortest path can be solved
for the UAV starting from the fixed point. It is
solved by Dijkstra algorithm. The position
information is turned into a graph to facilitate its
subsequent calculation of the shortest flight path.
The Dijkstra algorithm is effective to solve this
problem. The interception problem and the merchant
ship entering the port need to be calculated and
analysed immediately, and the computational
complexity of this algorithm is low.
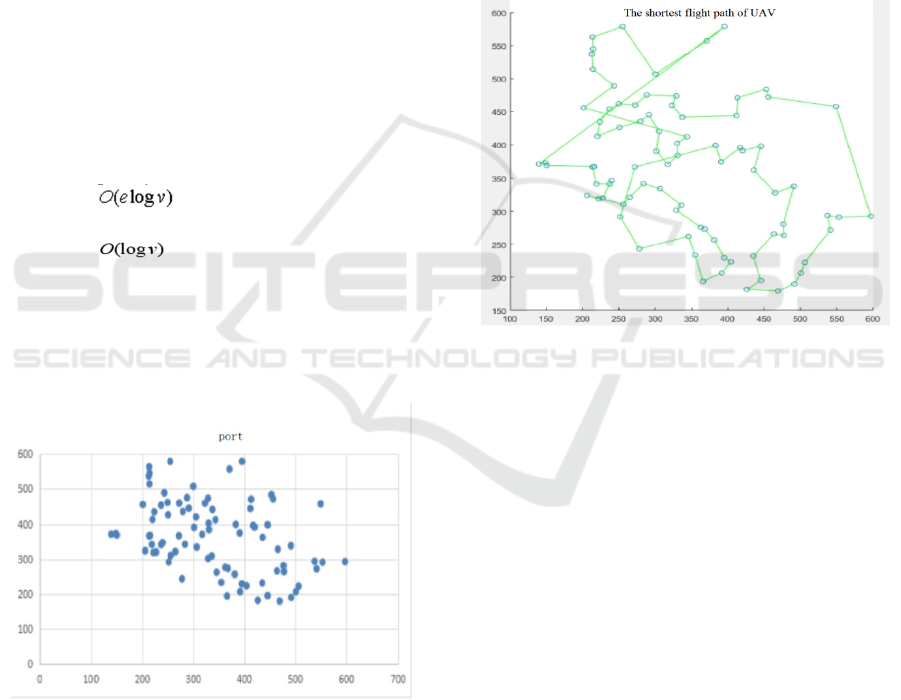
The complexity of Dijkstra's algorithm: (1) Time
complexity , where e is the number of
edges and v is the number of vertices. (2) Space
complexity .
The Dijkstra algorithm is effective to solve this
problem. The interception problem and the merchant
ship entering the port need to be calculated and
analysed immediately, and the computational
complexity of this algorithm is low, as shown in
Figure 6.
Figure 6: Dijkstra solution.
The model takes points 18, 23, 49, 53, and 60 as
the starting points, and follows 18, 15, 7, 6, 48, 57,
17, 67, 45, 79, 84, 66, and 23, 55, 64, 46, 73, 56, 63,
71, and 39, respectively. Python was used to analyse
and solve the model, and the results were obtained
after 100 iterations. Iterating the python solution 100
times. By substituting the model for calculation, it is
obtained that its initial position is (113.6410,
353.4564), and its intercepting objects include all of
the ship marks of the three types and can intercept
83% of the part of the second type. Its motion
trajectory starts from point (15) and intercepts along
the shortest path of the three types, and most of the
ships of the second type can be intercepted.
Using MATLAB software, we get the best route
for the UAV to travel through all merchant ships,
and the UAV can travel according to this route,
which can make the UAV spend the shortest time
and experience the shortest path, as shown in Figure
7.
Figure 7: The shortest flight path of UAV.
4 CONCLUSION
Through the research and demonstration in this
paper, we first use KNN algorithm to classify and
identify merchant ships. This method has strong
robustness to noise training data. Starting from the
geographical coordinate position of merchant ships,
this algorithm solves the problem of merchant ships
category well. Through the research and
demonstration in this paper, we know that it is easy
to implement KNN algorithm, and this method has
strong robustness to noise training data. From the
perspective of algorithm performance comparison,
take Floyd algorithm and Dijkstra algorithm as an
example. On the one hand, if Floyd algorithm is
applied to a certain vertex successively, then
compared with Dijkstra algorithm, many path and
result calculations are repeated. Although the
complexity is the same, the calculation amount is
much different. At the same time, more importantly,
Floyd's algorithm requires no loops with a sum less
ANIT 2023 - The International Seminar on Artificial Intelligence, Networking and Information Technology
14

than 0, while Dijkstra's algorithm uses the
prerequisite that as long as the length of the path in
the graph is greater than or equal to 0. Therefore, we
use Dijkstra algorithm to calculate the shortest path
of UAV classification of merchant ships and
optimize Floyd algorithm.
ACKNOWLEDGMENTS
This paper is one of the stage achievements of the
Research Fund project of Dalian Naval Academy of
the People's Liberation Army Navy (DJYKKT2023)
and the research project of Dalian Naval Academy
students (DJYKKT2022-007, DJYKKT2022-003).
REFERENCES
Kleinberg J M. Authoritative sources in a hyperlinked
environment[J].Journal of the ACM, 1999, 46 (5): 604
-632.
Gongde Guo, Hui Wang, David Bell, Yaxin Bi & Kieran
Greer. Using KNN model for automatic text
categorization[J]. Soft Computing, 2006, 10(5): 423-
430. https://doi.org/10.1007/s00500-005-0503-y
Feng Guo he, Wu Jingxue. Advances in the improvement
of KNN classification algorithm [J]. Library and
Information Work, 2012, 56(21):97-100.
Tang Huxin, Website Operation and Data Analysis two-
colour edition, Aviation Industry Press, 2016, (12):81-
82.
Liu Tong, Gao Shichen. Optimization of KNN method
based on data spatial structure [J]. Mathematics in
Practice and Understanding, 2018, 048(014):197-206.
Zhang Zitong, Zhang Chun lei, Zhang Yan, et al. Data
space structure and its application in KNN algorithm
[J]. Mathematics in Practice and Understanding, 2019,
49(1):8.
Shaozhong Cao, Ji Tu. Double Motor Coordinated Control
Based on Hybrid Genetic Algorithm and CMAC [J].
Physics Procedia, 2012 Vol. 33, pp. 975-982
https://doi.org/10.1016/j.phpro.2012.05.163
Shen Yuqing, Xu Lihong. A Genetic algorithm based on
pattern clustering [J]. Microcomputer Applications,
2004(04):9-11.
LI Ping. Improvement and Implementation of Dijkstra
Algorithm [J]. Information Construction,
2020(02):345.
Gao Wu, Zhou Gongjian, Wang Yang. Application of
Dijkstra Algorithm in Temporary speed limiting
operation [J]. Electronic World, 2020(08):31-32+35.
Li Min qiang. Basic Theory and Application of Genetic
Algorithm [M]. Science Press, 2002.
Liu Xuhong, Zhang Guoying, Liu Yushu, et al. Path
planning based on multi-objective genetic algorithm
[J]. Journal of Beijing Institute of Technology, 2005,
25(7):4.
Nannicini, G., Delling, D., Liberti, L., Schultes, D.:
Bidirectional A* Search for Time-Dependent Fast
Paths. In: McGeoch, C.C. (ed.) WEA 2008. LNCS, vol.
5038, pp. 334–346. Springer, Heidelberg, 2008.
Bang-Jensen, Jørgen; Gutin, Gregory. Section2.3.4: The
Bellman-Ford-Moore algorithm. Digraphs: Theory,
Algorithms and Applications[M], ISBN: 978-1-84800-
997-4, 2000.
Shi Ren, Wang Kai. Research on Shortest path Planning
of Mobile Robot based on Floyd Algorithm [J].
Chinese Journal of Scientific Instrument, 2009,
30(10):2088-2092.
Target Planning for UAV Merchant Ship Recognition Based on KNN Nearest Neighbor Algorithm
15
