
IMAGE AUTHENTICATION USING HIERARCHICAL
SEMI-FRAGILE WATERMARKS
Yuan-Liang Tang* and Chun-Hung Chen
Department of Information Management
Chaoyang University of Technology
168, Jifong E. Rd., Wufong Township, Taichung County 41349, Taiwan (R.O.C.)
Keywords: Image authentication, Digital watermarking, Semi-fragile watermarks, Wavelet transformation.
Abstract: In this paper, a semi-fragile watermarking technique operating in the wavelet domain is proposed. A
hierarchy of the image blocks is constructed and the image features are extracted such that relationships
among image blocks are established in order to enhance the security and robustness of the system. With
such a hierarchy, the image can be authenticated at different levels of resolution, hence providing a good
property of tamper localization. In addition, by varying certain parameters, the system is able to control the
degree of robustness against non-malicious attacks. The proposed algorithm thus provides a fine trade-off
between security and localization, and is also robust to common image processing operations.
1 INTRODUCTION
1
With the advance of network technologies and the
popularity of digital multimedia, it is very easy to
create, duplicate, transmit, and modify digital
products. However, serious problems also arise
along with such convenience, that is, unauthorized
modification on digital products becomes very easy,
too, and detection of such tampering is extremely
difficult. If the digital products are images, we face
the problem of image authentication, namely, to
identify if an image has experienced malicious
tampering. One of the solutions referred to as exact
authentication embeds fragile watermarks (Lin,
1999) in the image and they break easily even if the
image experiences only tiny modification. The
applications of exact authentication are very limited
because manipulations which preserve the semantics
of the image should be acceptable. Such a
requirement leads to another solution known as
inexact authentication, in which semi-fragile
watermarks (
Bartolini, 2001) are embedded in stead
of fragile ones. Semi-fragile watermarks are
relatively robust to content-preserving manipulations,
while fragile to malicious modification.
1
This research is supported by a grant from National
Science Council, Taiwan, R.O.C.
(NSC92-2213-E-324-024).
There are a number of works related to
semi-fragile watermarks. For example, Queluz (
1999)
generated digital signatures, based on moments and
edges, to protect the image. An image may be
corrupted without affecting their moments, but their
edges will certainly be changed. This property is
used to authenticate the image content. Yu et al.
(2000) used the Gaussian distribution to model the
amount of modification on wavelet coefficients
which is introduced by incidental distortions or
malicious attacks. The number of coefficients
necessary for watermark embedding is optimized as
well. Lin et al. (2000) embedded a pseudorandom
m-sequence into the median frequency DCT
coefficients for image authentication. They used
correlation values to determine the authenticity of an
image.
284
Tang Y. and Chen C. (2004).
IMAGE AUTHENTICATION USING HIERARCHICAL SEMI-FRAGILE WATERMARKS.
In Proceedings of the First International Conference on E-Business and Telecommunication Networks, pages 284-289
DOI: 10.5220/0001380902840289
Copyright
c
SciTePress
In addition to authenticating an image as a whole,
it is also desirable to pinpoint the locations of
tampering. Most localized authentication methods
rely on some form of block-wise authentication
(Wong, 1999), in which the image is divided into
disjoint spatial regions and each of them is
authenticated independently. The spatial acuity with
which a block-based authentication system localizes
tampering depends on the block size, thus it might
be desirable to reduce the block. However, as
indicated by Holliman and Memon (2000), there are
potential security risks associated with smaller block
sizesthe system is vulnerable to the collage attack
(Wong, 1999; Yeung, 1997). Therefore, there exists a
trade-off between security and localization. In this
paper we describe a semi-fragile watermarking
technique operating in the wavelet domain. A
hierarchy of the image blocks is constructed and the
image features are extracted such that the
relationships among image blocks are established in
order to resist the collage attack. The hierarchy is
based on the work done by Celik et al. (2002), and
with such a hierarchy the image can be authenticated
at different levels of resolution, hence providing a
good localization property. In addition, the proposed
system is designed in such a way that by varying
certain parameters, it is possible to control the
degree of robustness against non-malicious attacks.
Therefore our algorithm provides a fine trade-off
between security and localization and is also robust
to common image processing operations.
2 THE PROPOSED SYSTEM
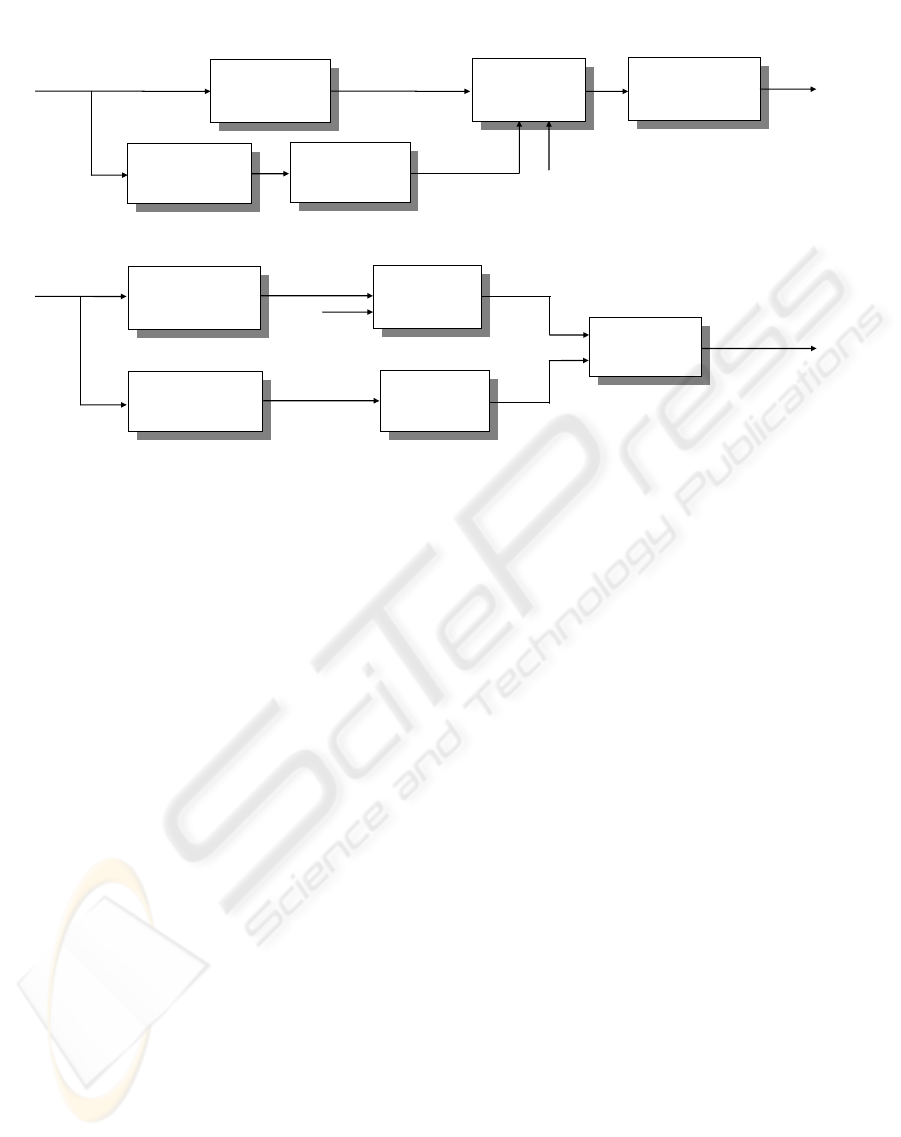
Figure 1 delineates the embedding and
authentication processes of our system. In the
embedding process, a hierarchical structure is first
constructed for the original image, X, and then the
features are extracted from such a hierarchy. The
features represent the image content and are
embedded as a watermark into the
wavelet-transformed image, X
t
, resulting in X
tw
.
Finally, X
tw
is inversely transformed back to the
original format, producing the watermarked image
X
w
. The embedding process also requires a private
key to ensure the security of the system. During
authentication, both the image features and the
watermark are extracted using the same methods as
in the embedding process. These two pieces of data
are then compared against each other to determine if
the image blocks are authentic. The locations of
tampering, if any, will be reported as well.
2.1 Construction of the Hierarchy
and Feature Extraction
Celik et al. (2002) proposed a hierarchical structure
in which the original image is first divided into
disjoint blocks which constitute the bottom level of
the hierarchy. And then successive levels are formed
by combining distinct groups of blocks at a
preceding level. Without loss of generality, we
assume that 8-bit grayscale square images are dealt
Figure 1: The embedding and authentication processes.
w
X
~
Watermark
Extraction
Feature
Extraction
Comparison
Watermark
Non-authentic
blocks
Wavelet
Transform
Features
tw
X
~
Authentication:
Wavelet
Transform
Original
Image, X
Feature
Extraction
Watermark
Embedding
key
X
t
X
w
Features
(watermark)
Inverse Wavelet
Transform
X
tw
Embedding:
key
Hierarchy
Construction
Hierarchy
Construction
IMAGE AUTHENTICATION USING HIERARCHICAL SEMI-FRAGILE WATERMARKS
285

with. Given an N×N image X, if X is divided into
M×M blocks at the bottom level, we have a
hierarchy of L = log
2
M + 1 levels. Let X
ij
l
denote a
block at level l, l = 0..L–1, where indices ij represent
the spatial position. Assuming that 2×2 blocks at a
given level of the hierarchy are combined to create a
block at the next level, we have
=
−
++
−
+
−
+
−
1
12,12
1
2,12
1
12,2
1
2,2
||
||
l
ji
l
ji
l
ji
l
ji
l
ij
XX
XX
X
,
for l = 1..L–1. The top level thus consists of only one
block X
00
L–1
= X. Based on Celik’s hierarchy, for
each block, X
ij
l
, we first compute the mean, m
ij
l
, of
pixel intensities of the block. Due to the limitation of
capacity, the bottom-level mean, m
ij
0
, is quantized
into 64 levels, i.e., a 6-bit intensity instead of the
ordinary 8-bit intensity. In addition, since tampering
with a block may not affect the mean when the block
size is large, we introduce the polarity to improve
the sensitivity as well as the reliability of detection.
The four-bit polarity, p
ij
l
, of X
ij
l
is obtained by
comparing the parent block’s mean with those of its
4 children:
≥
=
−
++
otherwise 0,
if ,1
),(
1
2,2
l
yjxi
l
ij
l
ij
mm
yxp
,
for l = 1..L–1 and x, y = 0..1. Denoting | ⋅ | as the
length in bits, we have |m
ij
0
| = 6, |m
ij
l
| = 8, and |p
ij
l
| =
4 (l = 1..L–1), respectively. These intensity means
and polarities, denoted by A
ij
l
(A
ij
0
= m
ij
0
and A
ij
l
=
m
ij
l
|| p
ij
l
, l = 1..L–1), are regarded as the image
features (i.e., the authentication data or watermark)
and are embedded back into the image for content
protection.
2.2 Watermark Embedding
The coefficients in frequency band LL
2
of the
wavelet-transformed image are selected for
embedding. These coefficients are good candidates
in that they represent the perceptually significant
part of the image and it is impossible for an attacker
to tamper with the image without gross
modifications to its appearance. The high level
authentication data is spread over a number of lower
level blocks and the accumulated payload is inserted
at the lowest level of the hierarchy by wavelet
coefficient modification. This is done by partitioning
A
ij
l
into a number of smaller strings:
{} {} { }
,1)( ,1)(||...||1 ,0||0 ,0 −Λ−Λ= llAAAA
l
ij
l
ij
l
ij
l
ij
where Λ(l) = 2
l
. The payload of a block on the
lowest level is formed by concatenating the units
inherited from higher level blocks:
{
}
{}
,)(),(||...
||)(),(||
11)(),(
11)(),(
0
11
11
jCjiCiA
jCjiCiAAD
LLjCiC
jCiCijij
LL
−−
−−
−−=
−−
where C
b
(x) =
x/2
b
. After the above preparation,
wavelet coefficients corresponding to each block on
the lowest level of the hierarchy are embedded with
payload bits. To increase the security level of the
system, we use the pseudo-random number
generator (PRNG), initialized by a private key, to
establish the correspondence between an image
block and the wavelet coefficients. This is illustrated
in Figure 2, in which the watermark is embedded in
the corresponding 4×4 coefficients in subband LL
2
.
Kundur and Hatzinakos (1999) embed the
watermark by first defining the quantization
function:
±±±=+<≤
±±=+<≤
=
... 5 ,3 ,1for )1( if ,0
... 4 ,2 ,0for )1( if ,1
),(
kqkfkq
kqkfkq
qfQ
where f is the wavelet coefficient and q denotes the
size of the quantization interval. They update f by
≤≠−∆
>≠+∆
=+∆
=
qrbqfQqf
qrbqfQqf
bqfQqf
f
5.0 and ),( if ,5.0
5.0 and ),( if ,5.1
),( if ,5.0
'
where ∆f =
f/q
⋅ q, r = f−∆f (quantization noise),
and b is the watermark bit. Obviously, the result of
such update will locate at exactly the middle of the
quantization step, which makes it very easy to
identify the watermarked coefficients. To overcome
this security risk, we modify the coefficient update
function as follows:
≤≠+−∆
>≠−+∆
−<=−+∆
+>=++∆
+≤≤−=
=
qrbqfQsqf
qrbqfQsqf
zqrbqfQsqf
zqrbqfQsqf
zqrzqbqfQf
f
5.0 and ),( if ,5.0
5.0 and ),( if ,5.1
)5.0( and ),( if ,5.0
)5.0( and ),( if ,5.0
)5.0()5.0( and ),( if ,
'
where s is a random number in the range [1..z] and z
is the randomness tuner (z =
q/6
in our
experiments). The result of such new update will
look random and therefore is more secure. Normally,
a larger q gives a more robust watermark and it
should vary according to the host image. However, a
larger q also creates more visual impact. In order to
search for an appropriate value, dozens of
well-known images were tested to obtain the
ICETE 2004 - WIRELESS COMMUNICATION SYSTEMS AND NETWORKS
286
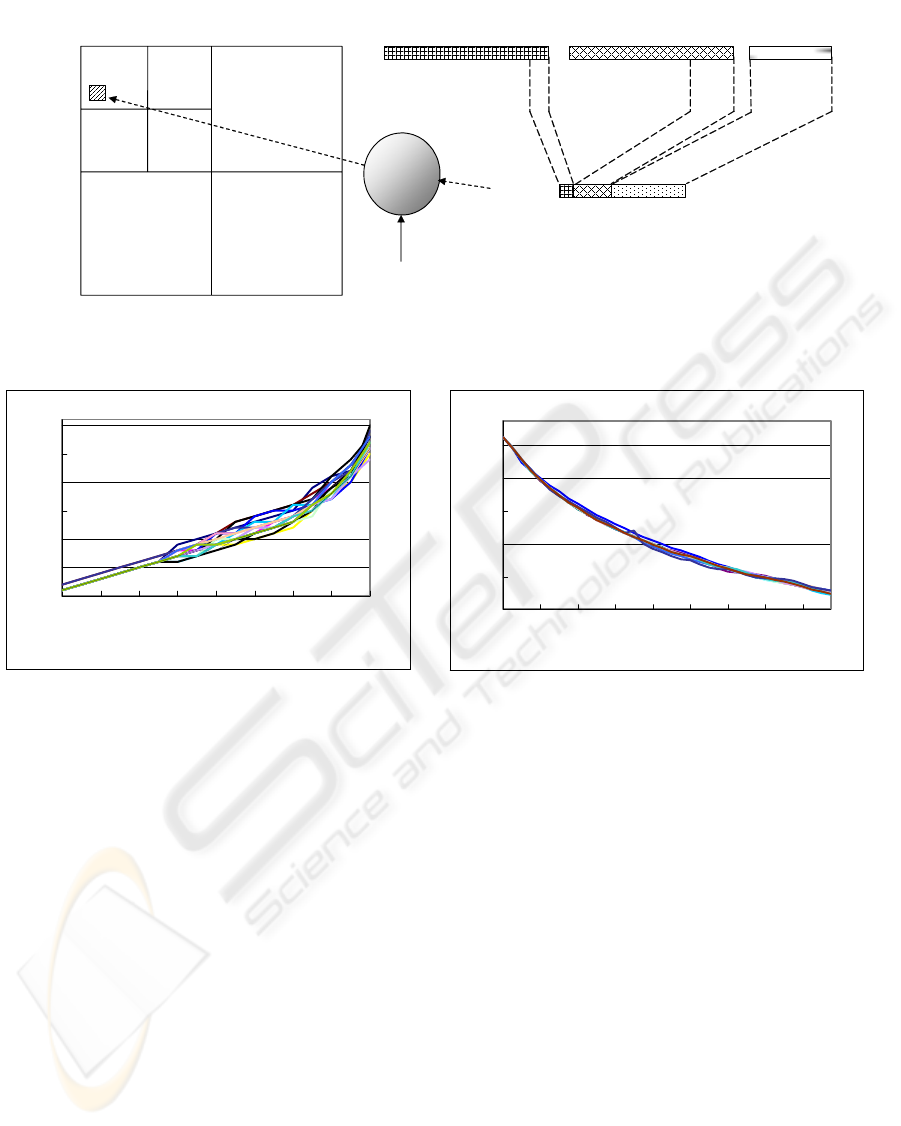
40
90
140
190
240
290
340
100 90 80 70 60 50 40 30 20
JPEG Quality Factor (%)
q
Figure 3: Watermark robustness as a relationship between
quantization intervals and compression quality factors.
24
28
32
36
40
44
50 90 130 170 210 250 290 330 370
q
PSNR (dB)
Figure 4: PSNR versus quantization intervals.
relationship between q and the JPEG quality factors
(QFs). Figure 3 shows the results, in which, for a
specified value of QF, any quantization intervals set
below the curve will cause our system to produce
false positives. For instance, if we want to validate
the watermarked image that can withstand JPEG
compression of 80% QF, q should be greater than 85,
otherwise such an operation will be identified as a
malicious attack instead of common processing. In
order to obtain a more general form, those curves are
approximated by a second order non-linear equation
using the regression technique, and the following
equation is obtained:
q = 393 – 6.014QF + 0.027QF
2
.
The equation above actually defines the lower bound
of the quantization interval. On the other hand, to
determine upper bound, the PSNRs as a function of
q are computed for each watermarked image. Figure
4 shows the results and, because PSNR ≥ 30 is
generally acceptable, q should be less than 200,
namely, the upper bound. Since the lower bound
produces least visual impact on an image, it is a
good candidate when determining q. As a
consequence, our system allows determining the
quantization interval automatically, depending on
the visual quality requirement of JPEG compression.
2.3 Image Authentication
The authentication process is analogous to the
embedding process. Let
l
ij
X
ˆ
denote a block of the
image that may have been tampered with. The
watermark bit is extracted by
),
ˆ
(
ˆ
qfQb =
, where
f
ˆ
is the corresponding coefficient. The partitioning
algorithm used during embedding is reversed to
recover the authentication data
l
ij
A
ˆ
, which is further
partitioned to obtain
l
ij
m
ˆ
and
l
ij
p
ˆ
. The same feature
Figure 2: Concatenation of blocks to form a payload and placement of resulting payload in wavelet domain of the image.
2
ij
A
Payload
HH
1
HL
1
LH
1
Wavelet version:
LL
2
HL
2
LH
2
HH
2
PRNG
key
4×4
1
ij
A
0
ij
A
IMAGE AUTHENTICATION USING HIERARCHICAL SEMI-FRAGILE WATERMARKS
287

extraction is also applied to obtain
l
ij
m
~
and
l
ij
p
~
for
each block. And finally, the difference between the
extracted features and watermark is calculated. Let
;
ˆ
~
l
ij
l
ij
l
ij
mmT −=
l
ij
X
ˆ
is determined as non-authentic
if
ll
ij
TT >
, where T
l
is the threshold and it varies
according to the size of the block. At the bottom
level, since we have ignored the 2 least significant
bits when collecting the authentication data, we set
T
0
= 8 (3 bits) to increase the robustness.
Furthermore, because tampering with a small area
may have little influence on the intensity mean of a
large-sized block, the threshold should be smaller. In
our experiments, we set T
1
= 6, T
2
= 4, and T
l
= 2
for l = 3..L–1 to accommodate such a situation.
For polarity checks,
l
ij
p
ˆ
and
l
ij
p
~
are compared
against each other bit by bit. Any bit difference
signifies a non-authentic block. However, if the
intensity means of the two blocks are similar,
non-malicious modification may easily reverse their
polarity. Based on such reasoning, when the
intensity difference between the parent block and the
child block is small, say less than 4, that bit is
ignored during comparison. In summary, a block is
authentic only when it passes both intensity mean
and polarity tests.
3 EXPERIMENTAL RESULTS
In our experiments, the 512×512 grayscale Lena
image is used as the host image, as shown in Figure
5(a). We set the size of the lowest level block to be
16×16 pixels, which results in a 6-level hierarchy.
Figure 5(b) shows the watermarked image, whose
PSNR value is about 38 dB. The degradation of the
watermarked image depends on the amount of the
embedded data and the embedding strength. To
demonstrate the effectiveness of our technique, we
modify the image by placing a tattoo (apple) on
Lena’s arm (Figure 5(c)). As can be seen in Figure
5(d), the tampered blocks are correctly detected, in
which non-authentic blocks at lower levels are
shown in darker shades, while those at upper levels
are shown in lighter shades. Furthermore, we
perform several non-malicious manipulations to test
the robustness of our system, including 80%-QF
JPEG compression, blurring, sharpening, and
addition of Gaussian noise with zero mean and
variance of 20. As expected, our system didn’t make
any false positive errors and Table 1 shows the
results.
4 CONCLUSION
We have presented in this paper an image
authentication technique using semi-fragile
watermarks. The authentication data is embedded in
the image and is arranged in a hierarchical structure
so that the whole contents of image are tightly
connected in order to overcome the security
weakness of block-based techniques. The system is
insensitive to common image processing techniques
in that robust image features are selected and a
variable quantization interval further controls the
degree of robustness. The system is also secure
because not only the block-dependence property
significantly discourages the collage attack, but also
the random correspondence between blocks and
coefficients prohibits brute-force attacks. The
experimental results demonstrated that our system is
very effective.
(a) (b)
(c) (d)
Figure 5: (a) Original image, (b) watermarked (q = 110),
(c) tampered, (d) detection result.
Table 1: Experimental results of various attacks.
Attack
Quantization
Interval
Authentic?
JPEG (QF = 20%~100%)
Blurring
Sharpening
Gaussian noise addition
By formula
160
190
120
Yes
Yes
Yes
Yes
ICETE 2004 - WIRELESS COMMUNICATION SYSTEMS AND NETWORKS
288

REFERENCES
Bartolini, F., Tefas, A., Barni, M., and Pitas, I. (2001)
“Image authentication techniques for surveillance
applications,” Proc. IEEE, vol. 89, no. 10, pp.
1403−1418.
Bhattacharjee, S. and Kutter, M. (1998) “Compression
tolerant image authentication,” Int. Conf. Image
Processing, vol. 1, pp. 435−439.
Celik, M.U., Sharma, G., Saber, E., and Tekalp, A.M.
(2002), “Hierarchical watermarking for secure
image authentication with localization,” IEEE Trans.
Image Processing, vol. 11, no. 6, pp. 585−595.
Chotikakamthorn, N. and Sangiamkun, W. (2001)
“Digital watermarking technique for image
authentication by neighbouring block similarity
measure,” Int. Conf. Electrical and Electronic
Technology, vol. 2, pp. 743−747.
El-Din, S.N. and Moniri, M. (2002) “Fragile and
semi-fragile image authentication based on image
self-similarity,” Int. Conf. Image Processing, vol. 2,
pp. 897−900.
Fridrich, J., Goljan, M., and Du, R. (2001) “Invertible
authentication watermark for JPEG images,” Int.
Conf. Coding and Computing, pp. 223−227.
Holliman, M. and Memon, N. (2000) “Counterfeiting
attacks on oblivious block-wise independent
invisible watermarking schemes,” IEEE Trans.
Image Processing, vol. 9, pp. 432−441.
Kundur, D. and Hatzinakos, D. (1999) “Digital
watermarking for telltale tamper proofing and
authentication,” Proceedings of the IEEE, vol. 87, pp.
1167−1180.
Lin, E.T. and Delp, E.J. (1999) “A review of fragile
image watermarks,” Multimedia and Security
Workshop (ACM Multimedia ’99) Multimedia
Contents, pp. 25−29.
Lin, E.T., Podilchuk, C.I., and Delp, E.J. (2000)
“Detection of image alteration using semi-fragile
watermarks. SPIE Conf. Security and Watermarking
of Multimedia Content II, vol. 3971, pp. 152−163.
Queluz, M.P. (1999) “Content-based integrity protection
of digital images,” SPIE Conf. Security and
Watermarking of Multimedia Contents, vol. 3657,
pp. 88−93.
Sun, Q. and Chang, S.-F. (2002) “Semi-fragile image
authentication using generic wavelet domain
features and ECC,” Int. Conf. Image Processing, vol.
2, pp. 901−904.
Wong, P.W. (1999) “A watermark for image integrity
and ownership verification,” IS&T Image
Processing, Image Quality, Image Capture, Systems
Conference, pp. 374−379.
Yeung, M. and Mintzer, F. (1997) “An invisible
watermarking technique for image verification,” Int.
Conf. Image Processing, vol. 2, pp.680−683.
Yu, G.J., Lu, C.S., Liao, H.Y. Mark, and Sheu, J.P. (2000)
“Mean quantization blind watermarking for image
authentication,” Int. Conf. Image Processing, vol. 3,
pp. 706−709.
IMAGE AUTHENTICATION USING HIERARCHICAL SEMI-FRAGILE WATERMARKS
289
