
A SECURE CREDITING PROTOCOL FOR HYBRID CELLULAR
AND AD-HOC NETWORKS
Bogdan C
˘
arbunar, Ioannis Ioannidis, Ananth Grama, Jan Vitek
Purdue University
West Lafayette, IN, USA
Keywords:
hybrid cellular ad-hoc networks, security, routing protocols
Abstract:
While wireless networking seems to be the way of the future, no definite architecture for large scale deploy-
ment of such networks has emerged. This can be attributed to financial reasons (a specialized infrastructure
is too expensive to build) as well as to the lack of solutions that could work with an existing infrastructure or,
in an ad hoc manner, without one. A viable alternative seems to be hybrid wireless networks. Such networks
use the existing cellular telephony infrastructure as basis and enhance it by building ad hoc networks of traffic
relayers around each cell, improving the overall throughtput and reliability of the network. These relayers are
users of the network that are willing to operate as such. In this setting, both efficiency and security are vital
properties. We propose SCP as an integrated solution for secure routing and crediting in hybrid networks.
We describe how a secure environment can be established efficiently by financially motivating users to avoid
attacks. Finally, we show that SCP imposes minimal load both in communication and computation, so that
even regular cellular phones can function as relayers, without demanding infrastructure upgrades.
1 INTRODUCTION
The past decade has witnessed rapid developments in
wireless communications, from wireless cellular tele-
phony to ad-hoc networks, wireless LANs and RF
networks. Wireless network cards have become af-
fordable and wireless connections are fast enough for
users to abandon more traditional networking possi-
bilities, as long as there is a nearby access point. The
only factor against an explosion of wireless computer
networking is the necessity for an expensive infras-
tructure that can provide extensive and reliable cover-
age with sufficient bandwidth.
Currently, the only infrastructure that addresses the
above problem is that of cellular telephony. When
a laptop equipped with a wireless network card con-
nects to a base station the same way as cell phones,
the bandwidth limitations are severe; the top rate
achievable in a cell is 2.4Mbps (1xEV-DO) and the
bandwidth drops fast as the device moves away from
the base station. Upgrading cellular base stations
can solve these problems, although it is doubtful that
providers will be willing to make such a massive in-
vestment.
A solution that grafts ideas from ad hoc networks
into cellular technology has started to attract atten-
tion. As in ad hoc networks, connections can in-
volve several intermediate relayers. Since wireless
LANs offer high throughput (IEEE 802.11b offers up
to 11Mbps), albeit in a range of just 115m, using a
web of multihop paths can considerably increase the
throughput from the base station to the devices in its
cell without requiring modifications in the infrastruc-
ture. An example of a hybrid network is shown in
Figure 1. Device DMH
1
is within the range of the base
station, but the expected downlink rate is very poor,
as it lies near the edge of the covered area. Since the
cellular throughput of MH
2
is larger than that of DMH
1
,
due to a shorter distance to the base station, DMH
1
can
use MH
1
and MH
2
as cellular traffic relayers, effectively
increasing its throughput.
In principle, this is a simple and powerful idea, but
multihop connections pose significant problems. The
major challenge is motivating users of the network to
act as relayers. A relayer not only has to sacrifice
some of its own bandwidth, but also battery power
to transmit and receive. Rewarding these users with
some form of credit to their account with the cellu-
lar provider is a reasonable incentive for participation.
However, imposing a crediting scheme over a multi-
142
Carbunar B., Ioannidis I., Grama A. and Vitek J. (2004).
A SECURE CREDITING PROTOCOL FOR HYBRID CELLULAR AND AD-HOC NETWORKS.
In Proceedings of the First International Conference on E-Business and Telecommunication Networks, pages 142-149
DOI: 10.5220/0001389901420149
Copyright
c
SciTePress

DMH
1
MH
1
MH
4
MH
3
MH
2
MH
6
MH
5
MH
7
MH
8
Figure 1: Example of a multihop cellular network. The gray
area represents the coverage cell of the base station. Dashed
lines represent cellular links, and full lines represent ad-hoc
wireless links.
hop cellular network fundamentally changes the in-
teractions between hosts. Malicious behavior will fo-
cus on gaining unwarranted financial rewards. Eaves-
dropping, impersonation, or denial of service attacks
can be profitable and will be performed if so.
We assume henceforth that users are selfish and fol-
low the principle that an action is to be performed
only if the credit gain brought by it is worth the ef-
fort spent to perform the action. Even though attacks
having personal satisfaction as the only gratification
may still persist, we claim that on the long run they
are not viable, since they necessitate credit, whose to-
tal amount is finite.
We propose a secure crediting protocol (SCP)
where attacks from malicious hosts are deflected by
making such attacks more expensive than honest
transactions. An interesting side-effect of this ap-
proach is that some forms of attack are now welcome.
As we will discuss in Section 5, nodes that want to
trim the relaying path, so that they will receive a larger
share of the credit for a route, act against congestion,
without diminishing the performance of the network.
Finally, we demonstrate experimentally that the
SCP protocol also decreases the traffic inside the en-
tire network and the traffic to and from the base
station, compared with the similar, but insecure,
UCAN (Luo et al., 2003) protocol, without sacrific-
ing the achieved throughput.
2 RELATED WORK
There have been efforts to integrate infrastructure-
based network models with ad hoc components,
but most of them assume single-interface devices.
In (Aggelou and Tafazolli, 2001), GSM terminals are
used to relay information to other terminals to im-
prove coverage. In Opportunity Driven Multiple Ac-
cess (Rousse et al., 2002), transmission power is con-
served by relaying traffic from a CDMA host to the
base station through multiple, short hops. In (Wu
et al., 2000), some channels are reserved for for-
warding when the fixed channels become congested.
In (Akyildiz et al., 1997), a generic wireless network
is considered, where hosts contact a mobile base sta-
tion for access outside their cell, using only one inter-
face. In (Hsieh and Sivakumar, 2002), a hybrid net-
work using the IEEE 802.11 architecture with both
DCF and PCF modes is examined, using only one
wireless interface. In (Lin and Hsu, 2000), multihop
paths are used to decrease the number of base stations
by increasing their coverage.
Although double-interface architectures are con-
ceptually similar to their single-interface counter-
parts, they increase the overall capacity by using
short-range, high-bandwidth, ephemeral channels to
relay traffic and a long-range, low-bandwidth, perma-
nent channel to complete operations like routing and
data integrity confirmation or as a last resort in the
absence of neighbors. The low-bandwidth channels
are not necessarily cellular, but the already existing
infrastructure make them an attractive option. This
architecture has been examined in (Luo et al., 2003),
whose routing scheme is very similar to SCP, but it
generates considerably more network traffic. In (De
et al., 2002), traffic is diverted to neighboring cells to
increase throughput. The use of dedicated, stationary
relays increases the cost of their solution and limits
its utility. A study of local area hybrid networks is
in (Lee et al., 2004).
As we have mentioned, security plays a major role
in the hybrid environment. A protocol that solves
the crediting and security issues for multihop paths to
an infrastructure access point is presented in (Salem
et al., 2003). However, attacks to the routing part
of the protocol are not considered. There have been
works towards secure routing protocols, although they
do not consider attacks to the crediting scheme neces-
sary for the architecture involved in this paper. For
pure ad hoc networks, Ariadne (Hu et al., 2002) de-
scribes a secure protocol for Direct Source Routing,
and ARAN (Dahill et al., 2002) presents a secure ex-
tension for AODV. In (Paul and Westhoff, 2002), a
rate confirmation scheme is presented, a part of the
SCP protocol that is usually left unaddressed in the
literature.
3 NETWORK ASSUMPTIONS
The system that we consider is based on the
UCAN (Luo et al., 2003) architecture, and consists of
A SECURE CREDITING PROTOCOL FOR HYBRID CELLULAR AND AD-HOC NETWORKS
143

a base station (BS) and several mobile hosts (MHs).
The base station provides cellular coverage of a cer-
tain radius (up to 20km), and the mobile hosts located
inside this coverage area have a permanent, direct,
low bandwidth communication link to the base sta-
tion. In addition, each MH has an 802.11b wireless
interface that allows it to directly communicate with
other MHs situated inside the smaller, 802.11b, cov-
erage range(115m).
All the mobile hosts are registered with the base
station, that is, with the service provider that owns
the base station. The registration implies that each
mobile host MH has a unique identifier, Id
MH
given
by the base station, and each mobile host has an ac-
count with the base station. The base station provides
certain services, such as Internet access, to each reg-
istered host, for as long as the host has credit in its
account. Moreover, the base station and the mobile
hosts that it serves have synchronized clocks. This
can be easily done by the base station, either by peri-
odically beaconing its current time, or by piggyback-
ing the current time in the messages sent to the mobile
hosts.
We assume that the base station has a private/public
key pair, and each host knows the public key. The
base station also shares a one-way hash function H
with all the hosts, and a different secret key with each
host MH, denoted as K
MH
. We also assume that the
base station can provide a good estimate of the down-
link rate R
MH
for each MH.
4 THE PROPOSED PROTOCOL:
SCP
SCP has three parts, see Figure 2. In the first part, the
initiator A contacts potential relayers and in the sec-
ond a secure route is found from the base station to A.
The last part concerns the credit handling and the se-
cure forwarding of packets, sent from the base station
to A, through the relayers. The protocol is repeated
every time the initiator is not satisfied with the rate
at which it receives the information or if the route is
broken during the protocol.
Every time SCP is run, the initiator has to be
charged by the base station. The charges consist of
a fee for the service provider, a fee for initiating the
protocol and the credit to be given to the eventual re-
layers, if the resulting route is satisfactory to the ini-
tiator. The fees for the provider and for initiating the
protocol act as a safeguard against denial of service
attacks by hosts that simply request a route, without
intending to use it. Since the account of the attacker
has to be charged, it is easy to detect malicious pat-
terns and, anyway, the attacker has to pay for the at-
tack. Also, because most of the hosts participating in
a run of the protocol will never directly receive credit
for that run, a form of credit for all candidate relay-
ers must be provided. A suggestion could be that the
initiating fees be periodically split among the hosts,
according to their participation time.
We consider crediting functions only of the follow-
ing form:
C
A
= C
BS
(S)+C
SCP
+ C
R
(S, r),
C
R
(S, r)=G(S) · F(r),
F(r)=c, if r ≤ 2,
F(r)=k
2
− k
1
· r, if r > 2
where C
A
is the total credit taken from the initiator,
S is the size of the information downloaded by the
initiator from the base station, C
BS
is the fee for the
provider, as a function of S, C
SCP
is the initiating fee,
and C
R
is the total credit given to the relayers, which
is a function of S and of r, the number of relayers.
The function G(S) denotes the participation of S to
C
R
. The only part that somewhat restricts the form of
C
A
is F(r). Its role in security and what the values of
c, k
1
and k
2
should be will be discussed in Section 5.
The role of C
BS
(S) and C
SCP
will be detailed in Sec-
tion 4.3. The amount of credit that each relayer gets
is C
R
(S, r)/r.
We believe that this crediting scheme can be ap-
plied in any realistic setting. The fees for the provider
and initiating the protocol can be of any form. The
impact of F(r) on the credit the relayers receive can
be scaled using G(S). As we will show, F provides
security, without resorting to expensive cryptography,
by maximizing the benefit of the hosts when they be-
have honestly.
4.1 Request Forwarding
The first part of SCP starts when A contacts the base
station, using its uplink connection, with the session
initialization message SINIT
[SINIT, Id
A
, R
A
, Seq
A
, H
K
A
(Id
A
, R
A
, Seq
A
)],
where Id
A
is the unique identifier of A, R
A
represents
A’s downlink rate, Seq
A
is a sequence number main-
tained by A, incremented by A each time the protocol
is run, and K
A
is the secret key shared by A and BS.
H
K
A
(M) represents the MAC (Message Authentication
Code) of message M, with the key K
A
. The base station
first checks the validity of the MAC, whose purpose
is to convince BS of the authenticity of the message,
since only A knows K
A
. The sequence number is used
to prevent a replay attack, if anyone captures a previ-
ous SINIT message.
As stated in Section 3, we assume that every host
has an account with the base station. The base sta-
tion first removes C
SCP
credit from A’s account. Then
ICETE 2004 - WIRELESS COMMUNICATION SYSTEMS AND NETWORKS
144

BS
A
0.75
0.8
0.85
B
C
D
II2. CC
II2. CC
II2. CC
I
1. SINIT / RCONF
II1. RREQ / RCON
F
I2. BREQ
I2. BREQ
I2. BREQ
BS
A
0.75
0.8
0.8
5
B
C
D
III2. MSG
III2. MSG
III2. MSG
III1. FREQ
III3.ACK
(a) (b)
Figure 2: Diagram of the SCP protocol. Mobile hosts are represented with small circles containing the names of the host in
the center. Arcs represent messages. Messages are prefixed with Roman numerals to represent the SCP phase. (a) (I) Request
forwarding and (II) path selection, see Section 4.1 and 4.2 (b) (III) Relaying of packets, see Section 4.3.
it replies with a downlink rate confirmation message
RCONF
[RCONF, T
BS
, Stamp
BS
A
],
where T
BS
is the current time of the base station and
Stamp
BS
A
= S
BS
(H(Id
A
, R
A
, Seq
A
, T
BS
)). S
BS
(M) repre-
sents the message M signed with the private key of the
base station. The purpose of this exchange of mes-
sages is to provide A with a receipt from the base sta-
tion that it has registered this run of the protocol and
has the necessary funds.
In the next step A sends to all the devices that are in-
side its ad-hoc wireless transmission range the broad-
cast request message BREQ
[BREQ, Id
A
, Seq
A
, TTL, R
A
, T
BS
, d
A
, Stamp
BS
A
],
where TTL is the time-to-live parameter of the mes-
sage, namely the number of hops the message is sup-
posed to travel, and d
A
is the distance in hops to the
initiator, which for A is 0.
Upon receiving such a BREQ message from a
neighbor P, a device N checks to see if for Id
A
it has
ever seen a sequence number larger than or equal to
Seq
A
, in which case it drops the packet. In order to
be able to do this, for every initiator that has sent a
packet through N, N has to store the host identifier and
the largest sequence number it has seen for that host,
along with the distance to the initiator, d
A
. Then N
checks the freshness of the message, by making sure
that T
N
≤ T
BS
+ TTL · T
proc
. T
N
is the current time at
host N, T
BS
is the timestamp carried in the BREQ mes-
sage and T
proc
is an upper bound on the time neces-
sary for each host to process and forward a BREQ
message. Finally, N checks the BREQ message valid-
ity condition H(Id
A
, R
A
, Seq
A
, T
BS
)=V
BS
(Stamp
BS
A
),
using the values received in the BREQ message. V
BS
means encrypting with BS’s public key, known to all
MHs, which in this context is equivalent with verify-
ing BS’s signature. If the condition does not hold N
drops the message.
If the condition holds, N marks P as its parent in the
breadth-first tree initiated by A and confirms to P the
choice made. All the confirmation messages that P re-
ceives make P aware of all its direct successors in the
breadth-first tree of A, information that will be useful
in the convergence part of the protocol, described in
the following. If TTL = d
A
, N drops the message. Oth-
erwise, N compares its downlink rate, R
N
, with R
A
− δ,
where δ ≥ 0 is a small constant chosen by the proto-
col. If R
N
< R
A
− δ, then N drops the message. This
is because most probably the neighbors of N whose
downlink rate is larger than R
A
− δ have already been
reached by this BREQ message. However, if R
N
is
larger than R
A
− δ, it means that there is a high chance
that N’s neighbors, not yet reached by A’s BREQ mes-
sage, can provide a still better downlink rate. In this
case, N increments d
A
, decrements the TTLfield, and
broadcasts this message to all the devices inside its
transmission range.
4.2 Path Selection
A mobile host L that receives the BREQ message ini-
tiated by A, with TTL = d
A
, or with R
L
< R
A
− δ,or
that does not have any successors, becomes a leaf in
the breadth-first tree of A. Such a device initiates a
converge-cast operation meant to reach A. The pur-
pose of the converge-cast operation is to convey to
the initiator host A the best path to the base station.
If mobile host L is a leaf in A’s broadcast tree be-
cause R
L
< R
A
− δ, then L, which we will refer to as
a dead-end leaf, sends to its parent host the converge-
cast message
[CC, Id
A
, Seq
A
, Id
L
, R
L
],
containing the leaf’s downlink rate. However, if L is
a leaf because the TTL of the BREQ message was 0
or because it has no successors, but L has a downlink
rate larger than that of A, L may become a relayer.
A SECURE CREDITING PROTOCOL FOR HYBRID CELLULAR AND AD-HOC NETWORKS
145

Whether L is willing to become one is a decision that
L can make on locally available information. An im-
portant factor is the distance from A, because it deter-
mines the credit that L can expect to receive, which is
C
R
(S, d
A
)/d
A
. Other factors, such as the battery power
or congestion concerns can contribute to the final de-
cision.
If L decides to participate, it first contacts the
base station, through its uplink connection, with a
rate request message [RREQ, Id
L
, H
K
L
(Id
L
)] When BS
receives a RREQ message, it first checks the va-
lidity of the MAC, in order to authenticate the re-
quest. The base station then looks up the down-
link rate for L, and replies with a rate confirma-
tion message [RCONF, Id
L
, R
L
, T
BS
, Stamp
BS
L
], where
Stamp
BS
L
= S
BS
(H(Id
L
, R
L
, T
BS
)). L then sends to its
parent host the converge-cast message
[CC, Id
A
, Seq
A
, Id
L
, R
L
, T
BS
, d
A
(L), Stamp
BS
L
],
where d
A
(L) represents the number of hosts from L to
A. Each intermediate node N in the broadcast tree of A
waits to receive a CC message from all its direct suc-
cessors in this tree. For each such message, N checks
to see that the advertised number of hops to the initia-
tor, d
A
, is strictly larger than its own. This is because
N only receives CC messages from devices that are
its successors. This is a simple check that prevents
hosts from advertising shorter distances to the initia-
tor. After receiving the CC messages from all its suc-
cessors, N first discards those from dead-end leaves.
Then, it compares its downlink rate with the rates re-
ceived in the CC messages from each successor S.If
its rate is no smaller than the largest rate reported from
its sub-tree and strictly larger than the downlink rate
of the initiator, and N decides it wants to participate,
N can drop its subtree. In this case, it first contacts
the base station with a RREQ message and obtains
Stamp
BS
N
= S
BS
(H(Id
N
, R
N
, T
BS
)), as described in the
previous paragraph. Then it sends to its parent a CC
message [CC, Id
A
, Seq
A
, Id
N
, R
N
, T
BS
, d
A
(N), Stamp
BS
N
]
However, if there is a host with a better rate in the
subtree, N receives from a successor S
j
a CC message:
[CC, Id
A
, Seq
A
, L
i
, R
j
, T
BS
, d
A
(S
j
), Stamp
BS
S
j
],
L
i
= Id
S
j
, ..., Id
S
1
. The chain has originated at host
S
1
, and extended by all the hosts in the list L
i
. The
downlink rate R
1
of S
j
is the maximum among those
received by N from its subtree and R
1
is also strictly
larger than R
N
. In this case, N decides if it wants to par-
ticipate in the protocol based on the credit that it will
receive, which is C
R
(S, d
A
(S
1
))/d
A
(S
1
). N can calcu-
late the value d
A
(S
1
), the distance from S
j
to A, since
it should be equal to the distance from N to A plus the
number of intermediate hosts in the CC message. If N
is satisfied with the credit, it only appends its identi-
fier to the beginning of the list L
i
of identifiers in the
above CC message and forwards it to its parent
[CC, Id
A
, Seq
A
, Id
N
, L
i
, R
j
, T
BS
, Stamp
BS
S
j
]
When the process converges to A, the retrieved
paths will consist of hosts aware of the credit that they
may receive and willing to participate. A can choose
the optimal path. At this point, A will start the last
phase of the protocol, which will notify the relayers of
their status and the base station to start the file transfer
and credit the relayers.
4.3 Crediting and Relaying
In the last part of the protocol, A contacts the base sta-
tion and sends the entire route, L
A
= Id
N
r
,...,Id
N
1
,
where N
r
is the first relayer from the base station and
N
1
is the direct relayer to A. More precisely, A sends
to BS a file request message
[FREQ, Id
A
, Seq
A
, f, L
A
, H
K
A
(Id
A
, Seq
A
, f, L
A
)]
where f is the name of the file requested by A. The
purpose of the MAC is to authenticate the originator
of the message as A, since A and BS are the only ones
that know K
A
. It also prevents other MHs from trying
to impersonate A and acquire information concerning
A from the base station.
The base station first removes C
BS
(S) credit from
A’s account, which is due by A to the base station for
sending it the information requested. Then it retrieves
the actual information requested by A, INFO
f
, of size
S and breaks it into packets of size s, to allow the
crediting to be done at a smaller, packet level granu-
larity. That is, each of the relayers receives credit for
each packet sent by BS that reaches A. More precisely,
for each packet P
i
, i = 1,...,S/s, the base station
first removes C
R
(s, r) credit from A’s account. The
base station then generates a source routing message
of type MSG destined to A, containing the identifiers
of the relayers along with the packet P
i
:
[MSG, T
BS
, Seq
A
, Tr
BS
r
,...,Tr
BS
i
, Packet
BS
A
],
where Tr
BS
i
=(Id
N
i
, H
K
N
i
(Id
N
i
, T
BS
)) and
Packet
BS
A
= Id
A
, P
i
, H
K
A
(P
i
, T
BS
). Each interme-
diate relayer N looks at the first Tr field searching for
its identifier Id
N
and checks the field’s validity. If the
check is passed, N peels off the first Tr field from the
message and forwards it to the next host specified in
the message.
A acknowledges the reception of a packet by send-
ing to BS, through the direct uplink cellular connec-
tion, an ACK message containing H
K
A
(P
i
). Only after
confirmation, will BS provide the credit C
R
(s, r)/r to
the relayers, and send A the next packet P
i+1
.
If A receives an invalid MAC, it contacts the base
station with a NACK message for packet P
i
. Then
ICETE 2004 - WIRELESS COMMUNICATION SYSTEMS AND NETWORKS
146

BS
B
D
0
.7
0.9
0.75
0.8
0.8
5
0.65
0.8
M
1
M
2
M
3
M
4
M
5
A
Figure 3: Example of potential attacks. A is the initiator
and BS is the base station. Hosts M
1
,...,M
5
are potentially
malicious. The numbers around the hosts represent their
downlink rate, in Kbps. For δ ≥ 0.05, B will propagate A’s
request.
the base station removes ∆
BS
more credit from A’s ac-
count and subtracts ∆
R
from the credit that each re-
layer should get for the packet, C
R
(s, r)/r. It then re-
sends the packet P
i
with a new MSG packet, with an
incremented Seq
A
value, via the same path. Each re-
layer, upon seeing a retransmission, knows that it will
receive less credit from the base station, and therefore
it can opt out by dropping the packet. The initiator
A waits for a given timeout interval to receive the re-
transmission, after which it initiates a new SCP proto-
col, to find an alternate path of relayers. The purpose
of ∆
BS
and ∆
R
is to prevent an attacker, acting either as
initiator or relayer, from denying service or draining
the battery of other users.
5 SECURITY ANALYSIS OF SCP
In this section we analyze SCP’s security.
Security against inflated downlink rates SCP re-
lies on the downlink rates advertised by the MHs
reached by the BREQ message in order to choose
the best path. Malicious hosts can try to falsify their
downlink rates so as to become the first relayers from
the base station and receive undue credit. This is
a critical attack because A may pay for undesirable
service. However, SCP requires each host N that
wants to become a relayer to contact the base station
and obtain a signed certificate of its downlink rate,
S
BS
(H(Id
N
, R
N
, T
BS
)). Since the certificate contains the
timestamp of the base station, a host is prevented from
using older, stale downlink rates.
Moreover, another host M cannot eavesdrop on the
RREQ/RCONF protocol of the host N, in an attempt
to impersonate N and its larger rate R
N
. This attack
would not work for two reasons. First, the account
that would receive credit would be that of N. Second,
the MSG packets will have to go through N instead
of M, and since N’s neighbors are different from M’s,
M cannot provide a valid path that includes N as a re-
layer.
Security against adding invalid relayers Figure 3
shows an example where hosts M
1
and M
2
collude
to include host M
3
to the list of relayers, during the
converge-cast towards the initiator A. M
3
is not neces-
sarily a direct neighbor of M
1
or M
2
, but it may have a
path to them. M
3
could also be another host taken over
by the owners of M
1
and M
2
. Note that a single host
cannot add false relayers. A way to prevent such at-
tacks is to make sure that the sum of credit the collud-
ing hosts receive is not greater than what they would
receive if they behaved honestly. We show how the
structure of the crediting function C
A
of Section 4 and
more specifically, the structure of F(r), which cap-
tures the dependence of C
A
on the number of relayers,
guarantees this property.
In the following, we will assume that there are
r honest relayers, m true, but colluding, relayers
and l false relayers, added by the colluding ones.
We also assume that the sum of the credit that
goes to the m + l malicious hosts is divided equally
among the m colluding relayers. This is the worst
case scenario, as the l false relayers are assumed
to be hosts taken over and the credit they receive
can be funneled to the m colluding hosts. The
credit each host receives without adding false relay-
ers is F(r + m)/(r + m), while the credit each col-
luding host receives when adding l false relayers
is (l + m) · F(r + m + l)/[m · (r + m + l)]. We can
prove that there are values of c and k
1
and k
2
such
that the credit each colluding host receives decreases
for l > 0.
Theorem 5.1 There are k
1
, k
2
and c such that, when
TTL ≤ 18,
F(r + m)
r + m
≥
l + m
m
·
F(r + m + l)
r + m + l
.
Proof A possible solution is k
1
= 1, k
2
= 9 and
c = 7. In fact, there is an infinite number of solu-
tions, which can be derived by varying the value of c
and solving the inequalities system for k
1
and k
2
.
Security against removing legitimate relayers
Another attack involves M
4
and M
5
colluding to re-
move D from the set of hosts receiving credit (Fig-
ure 3). This is impossible, since D has to be notified
by BS that it will receive credit before it forwards a
packet and at that point the colluding hosts cannot re-
move D from the credited path.
A SECURE CREDITING PROTOCOL FOR HYBRID CELLULAR AND AD-HOC NETWORKS
147
0
10
20
30
40
50
60
70
80
90
100
50 100 150 200 250 300 350 4
00
number of contacts
total number of nodes
SCP vs UCAN, TTL=3
# nodes visited UCAN
# nodes visited SCP
# BS contacts UCAN
# BS contacts SCP
0
10
20
30
40
50
60
70
80
90
1 1.5 2 2.5 3 3.5 4 4.5
5
number of contacts
TTL
SCP vs UCAN, #nodes=200
# nodes visited UCAN
# nodes visited SCP
# BS contacts UCAN
# BS contacts SCP
(a) (b)
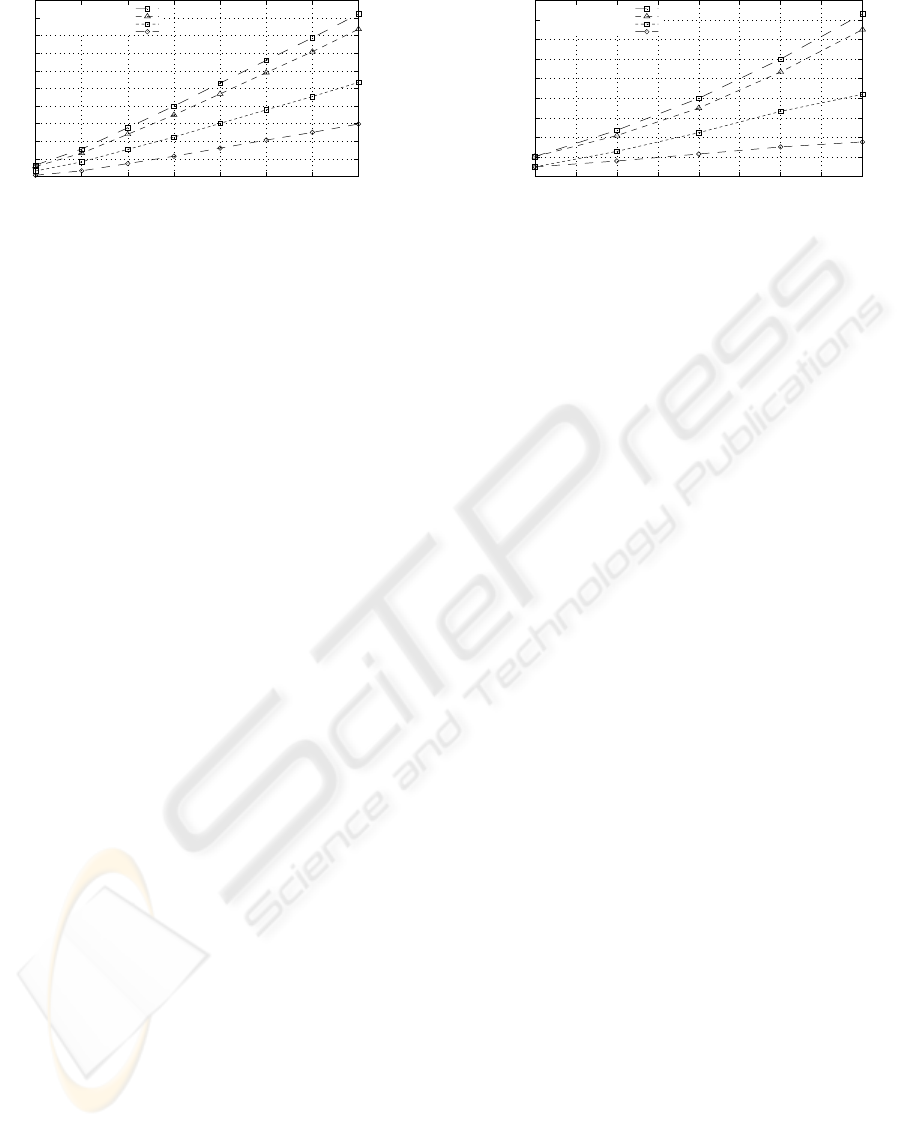
Figure 4: Experimental results comparing SCP and UCAN. (a) Evolution of the average number of devices contacted and of
average number of base station contacts during SCP and UCAN, when the total number of hosts served by the base station
grows from 50 to 400. TTL was set to 3 for both SCP and UCAN. (b) Evolution of the same two metrics with a TTL increasing
from 1 to 5, when the total number of hosts is 200.
Pruning the relayer path In Figure 3, host B, dur-
ing the converge-cast part of the protocol presented in
Section 4.2 can decide to ignore the CC message orig-
inated at M
2
, conveying a larger downlink rate than
that of B. The purpose of B, as in the previous attack,
is to present to A a shorter relayer path and therefore
obtain more credit from the base station. In this par-
ticular example, B would not have to split the credit
with anyone.
There are two observations we can make in favor of
this attack. The first is that the characterization of this
behavior as malicious is rather tenuous. It is no differ-
ent from a host refusing to relay packets because the
credit it will receive is inadequate. The relaying path
is a valid one and the credit given to the relayers is
correct. The only adverse effect is that A might have a
better and longer path to the base station. However, if
the pruned path is chosen, it means that the download
rate it provides is at least satisfactory to A.
The second observation is that pruning can be ben-
eficial to the network. Longer paths may have better
rates, but they consume bandwidth and create conges-
tion. Also, from A’s point of view, a longer path is
less robust, as even a single host can break it by mov-
ing. A longer path incurs larger delays, as well. If
hosts decide to optimize their chances of being relay-
ers against the credit they will receive, the operation
of the whole network will benefit from a reduced load,
without compromising connectivity.
6 EXPERIMENTAL RESULTS
In this section we experimentally analyze the per-
formance of SCP. Our goal is to measure the over-
head introduced by the secure crediting protocol and
compare it with UCAN. We will show that even
though more secure than UCAN, SCP significantly
decreases the network traffic, while maintaining sim-
ilar throughput performance. We modeled the ad-
hoc wireless network using the unit disk graph model,
where all hosts have the same transmission range, 115
units, and two hosts are neighbors iff they are inside
each other’s transmission ranges. The positions of
the hosts were randomly chosen, inside a square of
size 886 units. We modeled the cellular access of the
hosts using the HDR downlink rate vs. distance de-
pendency graph presented in (Luo et al., 2003). We
chose the position of the base station to be in the cen-
ter of the 886×886 square, and the cellular transmis-
sion range of the base station to be 500 units. Accord-
ing to this model, each mobile host inside the square is
covered by the cellular transmission range of the base
station. For the mobility scenario, we used the ran-
dom waypoint model. Each host chooses a target des-
tination and moves towards it with a random speed be-
tween 1 and the maximum speed. After reaching the
destination, the host chooses a new destination and a
new random speed.
6.1 Network Load
For the first set of experiments we consider that all the
hosts are static and we choose one host at distance 400
units from the base station to be the initiator of the
protocol. Each point on the plots is computed as an
average over 500 different ad-hoc network configura-
tions. Our goal is to measure the number of messages
produced by a protocol run and the number of times
the base station will be contacted. Figure 4 compares
SCP with UCAN’s proxy discovery algorithm. Fig-
ure 4(a) shows the evolution of the two metrics when
the total number of hosts in the square increases from
50 to 500 and for TTL 3. Figure 4(b) plots the evo-
lution of the two metrics when TTL ranges from 1 to
5, but the total number of hosts is 200. Both plots
show that SCP constantly requires fewer hosts to be
contacted and fewer hosts to contact the base station
ICETE 2004 - WIRELESS COMMUNICATION SYSTEMS AND NETWORKS
148

0
0.2
0.4
0.6
0.8
1
1.2
1.4
1.6
0 5 10 15 20 25 3
0
throughput improvement (Mb/s)
speed (unit/s)
SCP vs. UCAN, #nodes=200
UCAN TTL=3
SCP TTL=3
UCAN TTL=4
SCP TTL=4
UCAN TTL=5
SCP TTL=5
Figure 5: Throughput measurements for SCP and UCAN
when 200 hosts move at maximum speeds ranging between
1 and 30units/s.
than UCAN. The reason is that UCAN will forward a
request to a TTL range, while SCP stops if the down-
link rate falls below a threshold. This way, nodes at
the fringes of the coverage area are not contacted.
6.2 Throughput
This section describes the throughput improvement
measurements for SCP and UCAN. The experiments
were run in the following way. For each of the maxi-
mum speeds of 2, 5, 10, 15, 20, 25 and 30 units/s, 10
random initial network configurations with 200 hosts
were chosen. The experiment was performed for 400
seconds for each such configuration. During the ex-
periment, each host moved continuously according
to the random waypoint model. We have addressed
the problem of the random waypoint mobility model
identified in (Yoon et al., 2003) by choosing the speed
of each device to be uniformly distributed in the inter-
val [1, MS − 1], where MS is the maximum speed, and
by discarding the first 200 movements for each exper-
iment, so that the initial configurations do not bias the
results. We have performed the experiment for TTL
values of 3, 4, and 5.
Figure 5 shows the results of the experiments. For
the same TTL, the curves of SCP and UCAN are al-
most identical, with UCAN having only a nominal
advantage, negated by a higher network load. The
improvement was measured against the throughput of
the link to the base station.
7 CONCLUSIONS
We have presented a routing and crediting protocol
that establishes a cooperative environment for hybrid
networks. SCP is secure against attacks to the cred-
iting scheme. This was achieved by using a special
crediting function that does not reward longer paths.
The advantage of our approach is that it minimizes the
number of expensive cryptographic operations needed
and relies on the users being rational. We showed ex-
perimentally that the elevated security of SCP does
not come at the expense of the network load or the
efficiency of the routes.
REFERENCES
Aggelou, G. and Tafazolli, R. (February 2001). On the re-
laying capacity of next-generation gsm cellular net-
works. In IEEE Personal Communications Magazine,
8(1):40-47.
Akyildiz, I., Yen, W., and B.Yener (1997). A new hierar-
chical routing protocol for dynamic multihop wireless
networks. In Proceedings of IEEE INFOCOM.
Dahill, B., Levine, B. N., Royer, E., and Shields, C. (2002).
A secure routing protocol for ad hoc networks. In Pro-
ceedings of ICNP.
De, S., Tonguz, O., Wu, H., and Qiao, C. (2002). Integrated
cellular and ad hoc relay (icar) systems: Pushing the
performance limits of conventional wireless networks.
In Proceedings of HICSS-37.
Hsieh, H.-Y. and Sivakumar, R. (2002). On using the ad-
hoc network model in wireless packet data networks.
In Proceedings of ACM MOBIHOC.
Hu, Y.-C., Perrig, A., and Johnson, D. (2002). Ariadne:
A secure on-demand routing protocol for ad hoc net-
works. In Proceedings of ACM MOBICOM.
Lee, S., Banerjee, S., and Bhattacharjee, B. (2004). The
case for a multi-hop wireless local area network. In
Proceedings of IEEE INFOCOM.
Lin, Y.-D. and Hsu, Y.-C. (2000). Mulithop cellular: A new
architecture for wireless communications. In Proceed-
ings of IEEE INFOCOM.
Luo, H., Ramjee, R., Sinha, P., Li, L., and Lu, S. (2003).
Ucan: A unified cellular and ad-hoc network architec-
ture. In Proceedings of ACM MOBICOM.
Paul, K. and Westhoff, D. (2002). Context aware inferenc-
ing to rate a selfish node in dsr based ad-hoc networks.
In Proceedings of IEEE GLOBECOM.
Rousse, T., Band, I., and McLaughlin, S. (2002). Capacity
and power investigation of opportunity driven multi-
ple access (odma) networks in tdd-cdma based sys-
tems. In Proceedings of IEEE ICC.
Salem, N., Buttyan, L., Hubaux, J.-P., and Jakobsson, M.
(2003). A charging and rewarding scheme for packet
forwarding in multi-hop cellular networks. In Pro-
ceedings of ACM MOBIHOC.
Wu, X., Chan, S.-H., and Mukherjee, B. (2000). Madf:
A novel approach to add an ad-hoc overlay on a
fixed cellular infrastructure. In Proceedings of IEEE
WCWN.
Yoon, J., Liu, M., and Noble, B. (2003). Random waypoint
considered harmful. In Proceedings of IEEE INFO-
COM.
A SECURE CREDITING PROTOCOL FOR HYBRID CELLULAR AND AD-HOC NETWORKS
149
