
A QOS-AWARE RESOURCE REQUEST MECHANISM FOR DELAY
SENSITIVE SERVICES OVER TDMA/TDD WIRELESS NETWORKS
∗
Francisco M. Delicado, Pedro Cuenca and Luis Orozco-Barbosa
Department of Computer Engineering
University of Castilla la Mancha
Campus Universitario s/n, 02071 Albacete, SPAIN
Keywords:
Resource Request, QoS, Wireless LAN, HIPERLAN/2, Delay Sensitive Traffic.
Abstract:
Recent advances on wireless technology are enabling the design and deployment of multiservice wireless
networks. In order to be able to meet the QoS requirements of various applications, it is essential to deploy QoS
provisioning mechanisms. In this paper, we propose a QoS provisioning mechanism for providing support to
time constrained applications over wireless networks. The proposed mechanism is developed using a signaling
procedure. Our simulation results show the effectiveness of the proposed mechanism when supporting time
constrained services, such as MPEG-4 video communications.
1 INTRODUCTION
Nowadays wireless local networks represent an alter-
native to wired LAN’s. Current wireless LAN’s oper-
ate at transmission rates able to support various types
of applications, such as, data, voice and video. How-
ever, one of the main open issues is the definition of
QoS mechanisms capable of meeting the QoS require-
ments of the various applications. Within a broadcast
environment, such as a wireless LAN, it is important
to properly allocate the bandwidth to the various ap-
plications. Even though, recent standards have the un-
derlying elements to carry this important task, they
fall short on the definition of all the mechanisms re-
quired to implement a whole structured set of mech-
anisms. In this paper, taken as a basis the HIPER-
LAN/2 standard (H/2, 2000), we define a resource re-
quest mechanism capable of meeting the QoS require-
ments of time-sensitive applications.
The article is organized as follows. Section 2 pro-
vides a short overview of the HIPERLAN/2 standard.
In Section 3, we review the related bibliography on
the area of MAC algorithms for TDMA/TDD wireless
networks. Our proposed resource allocation mecha-
nism is described in Section 4. The results of a per-
formance evaluation study via simulation are given in
∗
This work was supported by the Ministry of Science
and Technology of Spain under CICYT project TIC2003-
08154-C06-02 and the Council of Science and Technology
of Castilla-La Mancha under project PBC-03-001.
Section 5. Finally, Section 6 concludes the paper.
2 HIPERLAN/2 MAC PROTOCOL
The HIPERLAN/2 MAC protocol (H/2, 2000) is
based on a dynamic TDMA/TDD scheme with cen-
tralized control, using as logical transmission unit
frames of 2 ms. Given that the allocation of the frame
resources to each Mobile Terminal (MT) is made by
the Access Point (AP), the requirements of the appli-
cation resources have to be known of these entities,
which are responsible of allocating the available re-
sources according to the user needs. Towards this
end, each MT has to request to the AP the required re-
sources by issuing a Resource Request (RR) message,
while the AP informs the MT of the positive outcome
by using a Resource Grant (RG) message. The con-
nections are identified by two identifiers: MAC ID
and DLCC ID. A MAC ID is assigned to each MT
at association time, while a DLCC ID is assigned to
each connection when this latter is setup; both identi-
fiers are assigned by the AP.
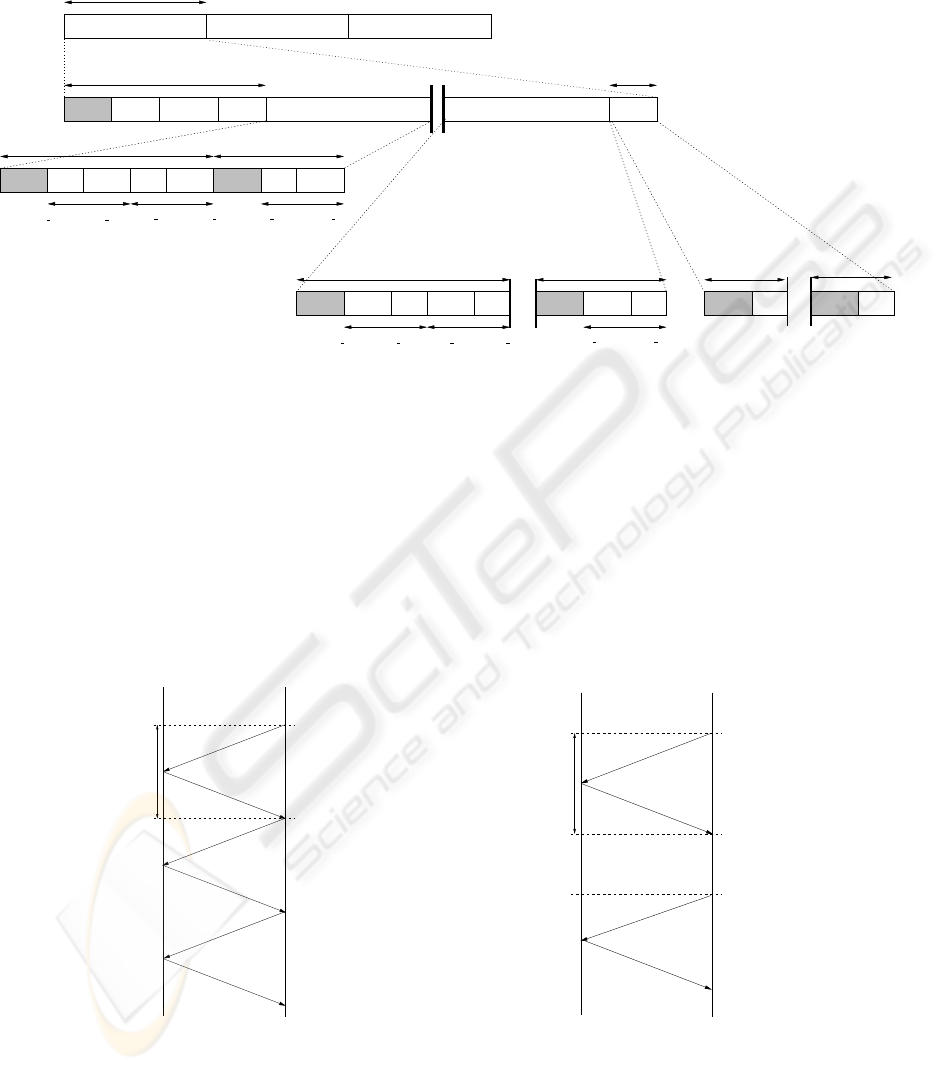
Figure 1 shows the format of the transmission
frame defined by the HIPERLAN/2 standard for a
system operating under the infrastructure mode. The
frame is divided into four phases, each phase being
composed by a group of transport channels. A trans-
port channel is a logical entity and its classification
depends on the type of data that it conveys.
402
M. Delicado F., Cuenca P. and Orozco-Barbosa L. (2004).
A QOS-AWARE RESOURCE REQUEST MECHANISM FOR DELAY SENSITIVE SERVICES OVER TDMA/TDD WIRELESS NETWORKS.
In Proceedings of the First International Conference on E-Business and Telecommunication Networks, pages 402-409
DOI: 10.5220/0001403604020409
Copyright
c
SciTePress

The phases of a frame are:
1. Broadcast phase: this phase is used for the commu-
nications taking place on the downlink. It is formed
by a preamble to determine the beginning of the
frame and three transport channels:
• BCH: contains the configuration parameters of
the frame, such as the number of RCH channels,
the size of the preambles of the uplink phase and
RA, among others.
• FCH: its size is variable and includes the re-
source grant (RG) messages for each connection.
These messages specify the number of granted
transport channels and their position within the
frame.
• ACH: contains the information regarding the
number of collisions having occurred in the RA
phase of the previous frame.
2. Downlink phase: this phase is formed by a group
of downlink PDU trains, which are formed by a
preamble and a variable number of SCH and LCH
channels dedicated to each one of those connec-
tions with resources granted in the FCH. The SCH
channels convey error control codes as well as in-
formation on any change on the connection param-
eters. The LCH channels transport user data, repre-
sented as PDU trains in Figure 1. Each PDU train
conveys the data pertaining to various connections
associated to a single MAC ID.
3. Uplink phase: similar to the downlink phase, this
phase is also formed by Uplink PDU trains, sep-
arate one from another by a guard time, and com-
posed by a preamble and a variable number of SCH
and LCH channels dedicated to each one of the
connections. The SCH channels convey resource
request messages control codes or other control
messages. The LCH channels transport user data,
represented as PDU trains in Figure 1. Each PDU
train conveys the data pertaining to various connec-
tions associated to a single MAC ID.
4. Random Access (RA) phase: consists of the num-
ber of RCH channels determined in the BCH chan-
nel, the minimum number of RCH channels in each
frame should be one. Each RCH channel is inserted
in a RCH PDU which is formed by a preamble
and a RCH channel. It is used for the transmis-
sion of control information, provided that the MT
does not have granted resources in the UL phase,
or during the beginning of the association process.
Each RCH PDU is separated from the previous one
by a guard time. A contention process based on a
Slotted-ALOHA scheme is used to access the RCH
channels.
It is important to note that not all of the transport
channels have the same size and that this one depends
on the channel type. This is also true for the pream-
bles and guard times whose sizes are specified, at the
beginning of the frame, in the BCH channel (H/2,
2000).
3 RELATED WORK
Given the central role played by the MAC algorithms
on enabling the provisioning of the QoS requirements
to the various applications, there has been a large
number of studies focusing on the design and eval-
uation of QoS-aware MAC protocols. In (Karol et al.,
1995), the authors describe a resource reservation pro-
tocol. In this protocol, the MTs initially issue a re-
source request message by using a contention-based
protocol, similar to Slotted-ALOHA. Once having
been allocated a number of slots, the data packets
convey, via “piggybacking’, the following MT’s re-
source requests. As soon as the MT becomes idle, the
resources are freed. At a latter time, when the MT
becomes once again active, this one has to start the
reservation process by issuing a first request via the
contention process.
The MASCARA algorithm introduced in (Passas
et al., 1997) makes use of a resource request mech-
anism similar to the one described in (Karol et al.,
1995). The mechanism makes use of a “scheduler”
based on a “token bucket” scheme to distribute the re-
sources among the active connections.
More recent works focusing on the HIPERLAN/2
standards (Kadelka and Masella, 2001), (Politis and
Tafazolli, 2002), have proposed several algorithms to
distribute the bandwidth resources to different types
of connections. Within a given type of connection,
the bandwidth is allocated by taking into account the
status of the buffers or the connection parameters
provided at the time of establishing the connections.
However, the authors do not specify the resource re-
quest (signaling) protocol.
In (Lenzini and Mingozzi, 2001) the authors intro-
duce an allocation algorithm based on a FIFO pol-
icy and a signaling protocol. The proposed allocation
algorithm allocates a fixed number of control chan-
nels, whose associated connection can use to further
request more resources (bandwidth).
One of the main drawbacks of the request mecha-
nisms proposed by the authors in (Karol et al., 1995)
and (Passas et al., 1997) is that they have been built
around a contention-based MAC. It is well known that
the performance of these mechanisms severely de-
grades as the number of active connection increases.
This makes the allocation mechanism prone to delay
and losses; an undesirable condition when developing
QoS mechanisms. Furthermore, the “piggybacking”
mechanism can not be implemented in HIPERLAN/2.
A QOS-AWARE RESOURCE REQUEST MECHANISM FOR DELAY SENSITIVE SERVICES OVER TDMA/TDD
WIRELESS NETWORKS
403

One option is to replace it by a “polling” mechanism,
or by making use of a fixed number of control chan-
nels as proposed in (Lenzini and Mingozzi, 2001).
The drawback of the latter approach is the excessive
overhead introduced as the number of uplink connec-
tions increases.
4 A NOVEL RESOURCE
REQUEST MECHANISM
One of our main design objectives has been the defini-
tion of an effective signaling protocol. The effective-
ness of such mechanism will depend on the amount
of overhead: number of control packets and retrans-
missions required by the unsuccessful transmission
attempts due to the use of the contention-based mech-
anism.
The algorithm works in the following way. The AP
starts by polling the MT as soon as a connection is set
up. The MT replies to the AP’s polling by specifying
the amount of required resources. Based on the num-
ber of resource requests received, the AP will grant
the requested resources to the requesting MTs. De-
pending on the network operating conditions, it may
take several frames for the AP to completely grant all
the requested resources (LCHs). As soon as the AP
finishes granting the requested LCHs to a given MT,
the AP reserves a SCH for that MT. The MT can then
use this SCH channel to reply to the AP’s polling.
Figure 2 depicts the process used by this type of
connection. Figure 2.(a) shows the operation of the
polling mechanism implemented by the AP. The AP
starts by issuing a RG message, RG:#SCH=1, con-
veyed via an SCH channel to poll the MT. The MT
replies by a RR message requesting n LCH channels,
RR:#LCH=n. It is then assumed that the AP grants
i slots in a first reply (RG) and the remaining n-i re-
quested resources in a second reply (RG:#SCH = 1,
#LCH = n-i). In this second RG, the AP also allocates
an SCH to the MT, the MT can use this SCH to place
its next resource request (RR) message.
Figure 2.(b) shows the case when the AP hav-
ing polled the MT issues a second polling message,
RG:#SCH = 1, after its timer has expired out. Fur-
thermore, in the case depicted, it is assumed that the
MT has been unable to grant the resources requested
in the first request issued by the MT. This condition
may arise when due to a long backlog, the AP is un-
able to serve the request due to the lack of available
resources. In this case, after a timeout period, the AP
polls once again the MT.
By basing the mode of operation of the request
mechanism on a “polling” scheme we look to address
two main issues: 1) to minimize the number of con-
trol packets (overhead) required to convey the MT’s
requests to the AP; 2) to avoid the use of a contention
procedure, which under heavy load conditions may
result on excessive delays or even on an unstable op-
eration of the allocation scheme. It is evident that the
effectiveness of the overall control structure to meet
the QoS requirements will depend very much on how
the different elements cooperate. Under the proposed
architecture, it is required that the entity responsible
of allocating the resources counts with the most up-
to-date information on the status of the all the active
MTs. The use of a proper tuned-up polling mecha-
nism should prove more effective on distributing the
bandwidth among the active MTs by taking into ac-
count their level of activity. In fact, the polling mech-
anism can be further enhanced to fairly distribute the
bandwidth according to the policies on place in a
given setup.
Under the proposed scenario, we assume that the
AP will serve the MTs requests on a strictly first-in
first-out (FIFO) discipline. This will allow us to carry
out a comparative study of our proposed scheme with
some other schemes proposed in the literature. Our
future plans include the study of different scheduling
disciplines to supplement the signalling mechanism.
5 PERFORMANCE EVALUATION
The main objective of this performance evaluation is
to assess the behavior of the proposed resource re-
quest mechanism with variable bit rate traffic and de-
lay sensitive applications. In our study we use one
HIPERLAN/2 cell operating in centralized mode. We
suppose that the connections have already been estab-
lished, i.e., it is assumed that all MTs and associated
connections are already engaged in the transmission
of video data. The only control messages are those
required to request and grant resources, RR and RG
messages, respectively. Furthermore, we assume the
use of use short preambles, times of guard of 2 ms,
and that the physical modes for the SCH and LCH
channels are QPSK3/4 and 16QAM3/4, respectively.
Regarding the applications each MT supports two
applications of MPEG-4 video ((MPEG4, 1999)) one
in the downlink and another in the uplink. Each video
application begins to transmit within a random pe-
riod given by the expression t = unif orm(0,
12
f
)
being f the frame rate. In this way, the peak peri-
ods of the source rates are randomly distributed along
a GOP period. The transmission of a video frame is
uniformly distributed along the interval of duration of
a frame (
1
f
). We use a sequence in QCIF format at
25 frames/sec of the movie Mr. BEAN (Fitzek and
Reisslein, 2001). Figure 3 shows a snapshot of the
traffic generated by the MPEG-4 video sources. It is
clear from this figure that these sources exhibit a high
ICETE 2004 - WIRELESS COMMUNICATION SYSTEMS AND NETWORKS
404

degree of burstiness characterized by a periodic traffic
pattern and a high variance on the rates at which the
data is generated.
The model of HIPERLAN/2 network has been im-
plemented in OPNET 9.0 (OPNET, 1987-2002). We
have measured the jitter among video frames, i.e.,
the time between the last packets of two consecutive
frames and the end-to-end delay for each packet. In
order to limit the delay experienced by the video ap-
plication, an essential condition to guarantee the QoS
required by the video application, the maximum time
that a piece of video data (referred form now on as
packet) can remain in the transmission buffer has been
set to 100 ms. This time limit is on-line with the val-
ues specified in (Karam and Tobagi, 2000).
In order to evaluate the proposed mechanism, re-
ferred from now on as PROP, we carry out a compar-
ative study of our proposed scheme with two schemes
proposed in (Lenzini and Mingozzi, 2001). The first
method therein, referred from now on as MING1 re-
serves a given number of LCH channels and one SCH
channel every given number of frames. In this way,
the MT counts at regular intervals with a given num-
ber of LCH channels for data transmission. The MT
uses the SCH channel to request for more resources
on a timely basis. The second method in (Lenzini and
Mingozzi, 2001), namely MING2, only reserves one
SCH channel every given number of frames. It is clear
that the performance of all three mechanism heavily
relies on parameters, such as the number of reserved
LCH and SCH channels, the frequency at which the
MT´s can place the resource request (RR) messages
and the timer used by the polling mechanism. We start
then by studying the performance of the MING1 and
MING2 schemes by tuning their system parameters
when supporting the video services under consider-
ation. This will set the basis for a fair comparative
study.
Figure 4.(a) shows the end-to-end delay as a func-
tion of the number for the MING1 scheme. We have
varied the number of reserved LCHs per frame as well
as the reservation period of the SCH channel. This
last parameter has been expressed as
#SCH
#frames
. From
the figure, it is clear that the system performance is
severely affected as the number of reserved LCHs is
increased. This is due to the fact that this scheme is
unable to statistically multiplex the traffic. This is par-
ticular important in a system supporting video traffic.
This traffic is characterized by a high variability. This
is clearly shown by the fact that when LCH=4, the
maximum number of MTs is six while for LCH=2,
the maximum number MTs reaches 12. From the fig-
ures, it is also clear that by varying the reservation
period of the SCH does not help when the system op-
erates under heavy load. On the contrary, under low
loads, the periodicity of the SCH has a clear impact on
the system performance. From the figure, a clear ex-
ample is provided for the system consisting of 6 MTs
and making use of 2 LCHs.
Figures 4.(a) and (b) show that the best results are
obtained for the system with the least number of re-
served LCHs and lowest ratio of SCH per frame. It is
important to note that the number of LCHs (LCHs=2)
is given by the average bitrate required by the video
sequence.
In the case of the MING2, no reservation of LCHs
whatsoever is made. However, the AP changes the
rate at which the SCH is assigned to the MTs. Fig-
ure 5.(a) shows the end-to-end delay. This scheme
exhibits similar performance to the one obtained for
the MING1 scheme. At low loads, the performance
on the system improves as the frequency at which the
SCH´s are provided to the MT´s is increased. This is
due to the fact that the MTs can more frequently place
their requests. It is clear that under these load condi-
tions, there are plenty of available resources to fulfill
the MT’s requirements. However at high load condi-
tions, (#MT ≥ 15), the system shows better results as
the SCHs are granted at a lower rate. Once again, this
can be explained to the decrease in the multiplexing
gain due to the resources granted to the connections.
As more resources are reserved, the frequency of the
control slots (to convey the MT’s requests) should be
made less frequent to free resources that can be effec-
tively used for data transmission.
Regarding the jitter, the MING2 exhibits the best
results for the cases when the SCHs are granted at the
lowest rate (longest period), see Figure 5.(b).
In the case of the PROP mechanism, Figure 6.(a)
shows the end-to-end delay. From the figure, it is clear
that the best results are obtained when the timer is set
to 0.04 s. This can be explained by the fact that for
a shorter timer period, more capacity is used to the
SCHs resulting in a reduction of available capacity
dedicated to data transmission (LCHs). In the case
of low loads, the performance is independent of the
value of the timer; since the system is able to promptly
fulfill the MT´s needs. In other words, the system
is able to promptly poll the stations, i.e., before the
expiration of the timer.
Figure 6.(b) shows the jitter for the PROP mecha-
nism. From the figure, it is clear that the best results
are obtained for the case when the timer has been set
to 0.04 s.
In order to make a fair comparison, we have taken
the system configurations exhibiting the best results
for all three schemes. For the case of MING1,
LCH=2, and a SCH every 15 frames. Similarly to
MING1, for MING2, one SCH channel every 15
frames. In the case of PROP, the timer has been set
to 0.04 s.
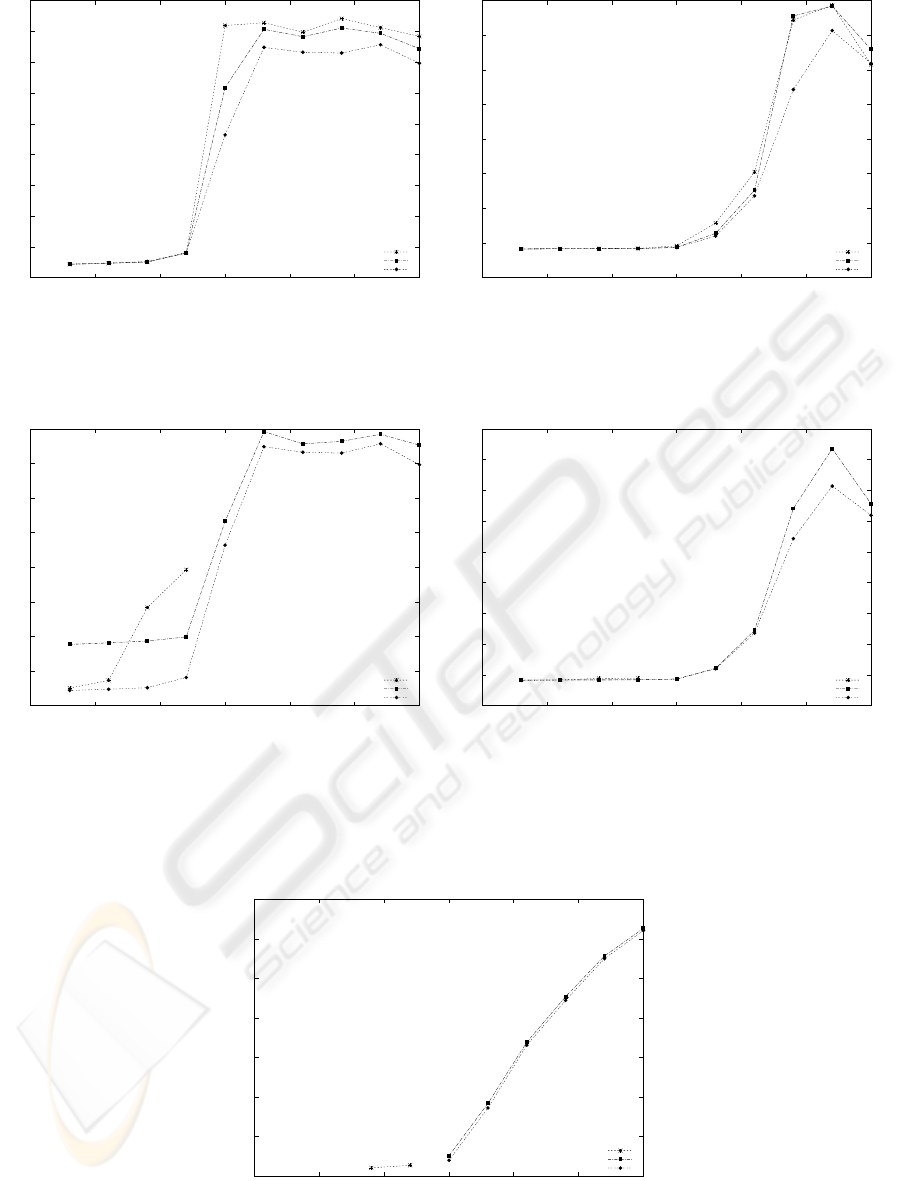
Figures 7.(a) and 7.(b) show the end-to-end delay
and jitter for all three schemes, respectively. From
A QOS-AWARE RESOURCE REQUEST MECHANISM FOR DELAY SENSITIVE SERVICES OVER TDMA/TDD
WIRELESS NETWORKS
405

the figures, it is clear that our proposed mechanism
exhibits the best results. As shown in the figures, the
MING1 schemes is unable to provide support to more
than twelve stations due to the fact that this scheme
is unable to statistically assign LCH to the active con-
nections. In particular, it is important to note that un-
der low loads, our mechanism ensures a shorter delay
on the transmissions taking place over the downlink.
Figures 8 show the packet losses as a function of
active MTs. The losses reported in this figure cor-
responds to those PDU having resided in the MT’s
transmission buffers for more than 100 ms. As seen
from the figures, our proposed scheme exhibits good
results. The figures also show that the inability of the
MING1 scheme to provide lossless transmission even
to a system consisting of as few as eight MTs.
6 CONCLUSIONS AND FUTURE
WORK
In this paper a novel resource request algorithm for
HIPERLAN/2 has been developed and evaluated. We
have evaluated the proposed scheme and conducted
a comparative study with two other schemes previ-
ously proposed in the literature. We have been partic-
ularly interested in examining the ability of the pro-
posed scheme in supporting MPEG-4-based services.
Our results have shown that the proposed scheme is
able to support a larger number of connections than
a scheme based on the static reservation of a mini-
mum number of slots. Furthermore, we have shown
that proposed scheme exhibits a shorter end-to-end
delay under all network loads. We plan to conduct
further studies under a multi-service scenario, i.e.,
when various services, such as video, voice and data
are multiplexed together over the same wireless chan-
nel. As already mentioned, we will also consider to
supplement the proposed signalling mechanism with
a scheduling policy.
REFERENCES
Fitzek, F. H. and Reisslein, M. (2001). MPEG-4 and
H.263 video traces for network performance evalua-
tion. IEEE Network, 15(6):40–54.
ETSI TS 100 761-1. Broadband radio access networks
(BRAN); HIPERLAN type 2; data link control (DLC)
layer; part1: Basic data transport functions.
Kadelka, A. and Masella, A. (2001). Serving IP quality
of service with HiperLAN/2. Computer Networks,
37(1):17–24.
Karam, M. and Tobagi, F. (2000). On the Traffic and Ser-
vice Classes in the Internet. In Proc. of IEEE GLOBE-
COM’00, San Francisco,CA, US.
Karol, M., Liu, Z., and Eng, K. (1995). An efficient
demand-assignment multiple access protocol for wire-
les packet (ATM) networks. Wireless Networks,
1:267–279.
Lenzini, L. and Mingozzi, E. (2001). Performance evalu-
ation of capacity request and allocation mechanisms
for HiperLAN2 wireless LANs. Computer Networks,
37:5–15.
ISO/IEC 14496-2. Information technolo- gy –Generic cod-
ing of audio-visual objects– Part 2: Visual.
OPNET Technogies, Inc. OPNET Modeler 9.0. http:
//www.opnet.com
Passas, N., Paskalis, S., Vali, D., and Merakos, L. (1997).
Quality-of-service-oriented medium access control
for wireless ATM networs. IEEE Communications
Magazine, 35(11):42–50.
Politis, C. and Tafazolli, R. (2002). MAC protocol for sup-
porting QoS in All-IP HiperLAN2. In Pro. 4th Euro-
pean Wireless Conference (EW’02), Florence, Italy.
ICETE 2004 - WIRELESS COMMUNICATION SYSTEMS AND NETWORKS
406
PSfrag replacements
2 ms
MAC frameMAC frameMAC frame
Broadcast phase
RA PHASE
PreamblePreamblePreamblePreamble
PreamblePreamble
Preamble
BCH FCH
ACH
Downlink phase
Uplink phase
DOWNLINK PDU TRAINDOWNLINK PDU TRAIN
UPLINK PDU TRAINUPLINK PDU TRAIN
RCH PDU TRAIN
RCH PDU TRAIN
SCHsSCHsSCHs
SCHs SCHsSCHs
LCHsLCHsLCHs
LCHsLCHsLCHs
RCHRCH
MAC
ID k, DLCC ID j
MAC
ID k, DLCC ID k MAC ID m, DLCC ID i
MAC
ID l, DLCC ID qMAC ID l, DLCC ID p
MAC
ID m, DLCC ID r
Guard Time
Guard Time
Figure 1: HIPERLAN/2 MAC frame format
PSfrag replacements
MT
AP
2 ms
RG: #SCH = 1 (polling)
RR: #LCH = n
RG: #LCH = i, i ≤ n
send #LCH = i
RG: #SCH = 1, #LCH = n-i
send #LCH = n-i; RR: #LCH = k
(a)
PSfrag replacements
MT
AP
2 ms
RG: #SCH = 1 (polling)
RR: #LCH = n
RG: #LCH = i, i ≤ n
send #LCH = i
RG: #SCH = 1, #LCH = n-i
send #LCH = n-i; RR: #LCH = k
expire temp.
RG: #SCH = 1 (polling)
RR: #LCH = q, q ≥ n
(b)
Figure 2: Resource request Mechanism
A QOS-AWARE RESOURCE REQUEST MECHANISM FOR DELAY SENSITIVE SERVICES OVER TDMA/TDD
WIRELESS NETWORKS
407

0
2000
4000
6000
8000
10000
12000
14000
16000
0 5000 10000 15000 20000 25000
bytes
#frame
Figure 3: MPEG-4 stream
0
0.005
0.01
0.015
0.02
0.025
0.03
0.035
0.04
0 5 10 15 20 25 30
seconds
#MTs
SCH per FRAME = 1/5
SCH per FRAME = 1/10
SCH per FRAME = 1/15
LCH = 2
LCH = 4
(a) Delay vs. #MTs
0.042
0.0425
0.043
0.0435
0.044
0.0445
0.045
0.0455
0 5 10 15 20 25 30
seconds
#MTs
SCH per FRAME = 1/5
SCH per FRAME = 1/10
SCH per FRAME = 1/15
LCH = 2
LCH = 4
(b) Jitter vs. #MTs
Figure 4: Delay and Jitter - MING1 mechanism
0
0.01
0.02
0.03
0.04
0.05
0.06
0.07
0.08
0.09
0 5 10 15 20 25 30
seconds
#MTs
SCH per FRAME = 5
SCH per FRAME = 10
SCH per FRAME = 15
(a) End-to-End delay vs. #MTs
0
0.05
0.1
0.15
0.2
0.25
0.3
0.35
0.4
0.45
0 5 10 15 20 25 30
seconds
#MTs
SCH per FRAME = 1/5
SCH per FRAME = 1/10
SCH per FRAME = 1/15
(b) Jitter vs. #MTs
Figure 5: Delay and Jitter - MING2 mechanism
ICETE 2004 - WIRELESS COMMUNICATION SYSTEMS AND NETWORKS
408
0
0.01
0.02
0.03
0.04
0.05
0.06
0.07
0.08
0.09
0 5 10 15 20 25 30
seconds
#MTs
Polling Thr. = 0.01
Polling Thr. = 0.02
Polling Thr. = 0.04
(a) End-to-End delay vs. #MTs
0
0.05
0.1
0.15
0.2
0.25
0.3
0.35
0.4
0 5 10 15 20 25 30
seconds
#MTs
Polling Thr. = 0.01
Polling Thr. = 0.02
Polling Thr. = 0.04
(b) Jitter vs. #MTs
Figure 6: Delay - PROP mechanism
0
0.01
0.02
0.03
0.04
0.05
0.06
0.07
0.08
0 5 10 15 20 25 30
seconds
#MTs
MING1 (2,1/15)
MING2 (1/15)
PROP (0.04)
(a) End-to-End delay vs. #MTs
0
0.05
0.1
0.15
0.2
0.25
0.3
0.35
0.4
0.45
0 5 10 15 20 25 30
seconds
#MTs
MING1 (2,1/15)
MING2 (1/15)
PROP (0.04)
(b) Jitter vs. #MTs
Figure 7: Delay and Jitter- all mechanisms
0
500
1000
1500
2000
2500
3000
3500
0 5 10 15 20 25 30
#LCH
#MTs
MING1 (2,1/15)
MING2 (1/15)
PROP (0.04)
Figure 8: Packets Losses - all mechanisms
A QOS-AWARE RESOURCE REQUEST MECHANISM FOR DELAY SENSITIVE SERVICES OVER TDMA/TDD
WIRELESS NETWORKS
409
