
PROCESS MODELLING – BURDEN OR RELIEF?
Living Process Modelling within a Public Organisation
Silke Palkovits
BOC Information Technologies Consulting GmbH, Baeckerstrasse 5/3, 1010 Vienna, Austria
Thomas Rössler
Secure Information Technology Center Austria – A-SIT, Inffeldgasse 16a, 8020 Graz, Austria
Maria Wimmer
University of Linz, Insitute of Applied Computer Science, Altenbergerstr. 69, 4040 Linz, Austria
Keywords: Integrated process modelling, Business Process Modelling
(BPM), e-business, e-government, security
aspects
Abstract: Process modelling and process reorganisation ar
e key criteria in regards to successful implementation of e-
government. Yet up to recently, e-government had a rather technical dimension. Nowadays, it is being
recognised that e-government is multi-faceted and that it requires a holistic approach. However, the
questions of ‘how can the concept of Business Process Modelling (BPM) be applied successfully’ and ‘what
is the added-value of managing an authority’s processes’ often cannot be answered immediately and directly
due to the complexity of this topic. So, many public authorities shy at thinking in a comprehensive way and,
instead, continue to focus on single issues because these are simpler to understand and easier to manage.
The aims of this paper are to create awareness about the added-value of integrated business process
modelling, to introduce a holistic concept for the analysis, re-organisation and modelling of government’s
processes and to propose a tailor-made methodology for describing the processes. The authors will go
deeply into the topic of process management with specific requirements of public authorities including legal
as well as security aspects. Reading through this contribution, the reader should easily recognise the added
value of BPM for public administrations and that the management of processes within public administration
is a relief and not a burden.
1 INTRODUCTION
In the last few years the term e-government became
a synonym for modernisation of the public sector,
better services to the citizens, integration of the
citizens into the political decision making process
(e-participation) and increase of efficiency within
government. This keyword was determined by a
number of political strategies all over Europe like
UK-online and the e-government interoperability
framework e-GIF
1
in Great Britain,
1
Office of the e-envoy, http://www.e-envoy.gov.uk, and
e-GIF
BundOnline2005
2
in Germany, eAustria
3
in Austria
or the regulation of the European Union
4
to create
prerequisites for an efficient administration until
2005.
http://www.govtalk.gov.uk/schemasstandards/egif_doc
ument.asp?docnum=731
2
BundOnline 2005 in Germany,
http://www.bund.de/BundOnline-2005-.6164.htm
3
e-Government initiatives and strategies of Austria’s chief
information office and ICT-Board, www.cio.gv.at
4
Initiatives eEurope 2002 and eEurope2005,
europa.eu.int/information_society/
eeuropenews_library/eeurope2005/index_en.htm
94
Palkovits S., Rössler T. and Wimmer M. (2004).
PROCESS MODELLING – BURDEN OR RELIEF? - Living Process Modelling within a Public Organisation.
In Proceedings of the Sixth International Conference on Enterprise Information Systems, pages 94-102
DOI: 10.5220/0002631900940102
Copyright
c
SciTePress

Since e-government is not any more understood
only as introducing ICT into the governmental work,
but is being perceived as a multi-faceted paradigm
for modernising public administration and
governments (c.f. the communication of the EC on
the role of e-government in 0), a brief determination
of the expression for our scope is required. In
accordance with 0 0 0 0 and 0, we refer to the part of
e-government that addresses the usage of ICT in
order to efficiently serve customers of public
administration (citizens, companies, NGOs, NPOs,
intermediaries) and governments themselves.
As a request of above mentioned national and
international strategies and policies towards
successful implementation of e-government, process
modelling and process reorganisation are becoming
key criteria and a major part within such projects.
This may be due to the high complexity of
governmental processes and organisational
structures. Another reason may be that, up to now,
focus of BPM tool developments was put on the
industry sector, where BPM has been accepted as an
important step in modernisation and optimisation of
business processes. Appropriate modelling
methodologies and tools for the public sector are not
really available yet.
In this contribution, we demonstrate that process
modelling is not a burden to public organisations but
a turnkey solution to support public administrations
in the efficient and effective reorganisation and re-
engineering of administrative processes towards
customer-oriented online service provision.
Section 2 of this paper investigates BPM in
general and in specific within the context of public
administrations. Based on that, tool and
methodology requirements are discussed in section
3. Since security and privacy are key criteria in
governmental service provision, section 4
investigates such requirements and describes a
concept to model security aspects with the support
of a comprehensive BPM tool. Section 5 concludes
with a discussion of the added value of such a
holistic BPM-tool for the public sector. I.e. the
benefits of introducing process management into
public organisations and of describing security
requirements for internal processes as well as for
processes related to the citizen are highlighted.
2 BUSINESS PROCESS
MANAGEMENT
Business Process Management (BPM) comprises a
number of different tasks concerning organisational
processes. BPM is often used as a generic term for
Business Process Reengineering (BPR), Quality
Management or Implementation of Workflow
Management Systems 0. Important parts of Business
Process Management are the acquisition of relevant
data and the illustration of models of the
organisation, the products and processes as well as
the usage of resources like for example information
technology. The analysis and simulation of the
models deliver advice for the strategic optimisation
and quality assurance.
The state-of-the-art in the area of modelling of
organisations is based on fixed meta models. A
meta-model is the formalism the modelling bases on
(or more detailed information read 0 ).
Requirements for a modelling platform like
flexibility, adaptability and openness should be
fulfilled by environments providing flexible meta
modelling capabilities 0. The main characteristic of
such environments is that the formalism of
modelling – the meta model – can be freely defined.
Such a meta modelling tool was developed by BOC
in the mid 90s
5
. The idea of being flexible, adaptable
and open for all business branches turned out to be
successful.
Talking about all branches also includes public
administrations. Being successful in this area means
to find out what public authorities want and need
from process management. The lack of an already
existing modelling tool leaded to the initiation of a
research and development project in Austria to
implement and customise a BPM methodology and
tool specifically targeted for the public sector. This
project result is called ADOamt
® 6
. The approach is
to develop a modelling tool, which realises the most
important requirements to support the
implementation of e-government solution from a
business process management (BPM) and integrated
service modelling perspective. Some of these
requirements are the identification of actors and their
roles, the definition of possible communication
channels, the transparency of the flows, the
standardisation of terminologies for an efficient and
transparent communication, the integrated modelling
from the portal to the back office and the integration
5
ADONIS
®
, www.boc-eu.com
6
www.adoamt.com
PROCESS MODELLING - BURDEN OR RELIEF? LIVING PROCESS MODELLING WITHIN A PUBLIC
ORGANISATION
95

of the citizen as customer and company clerk as
service provider.
2.1 BPM within Public
Administrations
Government's internal and external traditional
business processes need to be adapted to electronic
businesses processes. For the external perspective,
this means to provide public services in a well-
structured and well understandable way meeting the
needs of the specific users (i.e. citizens, businesses,
other organizations). Here, re-engineering of
business processes for better serving the needs of
citizens or enterprises in specific situations (“life-
events, business situations”) is an important option 0
0.
Implementing integrated e-Government means to
adequately map external service structures to
internal process structures of public authorities as
well. Integrated service and process models are of
utmost importance for achieving a seamless
government. A great help in this respect is a logical
and organizational separation of front offices, which
bundle citizens’ demands and pass them on, and
back offices, which satisfy these demands through
adequate business processes and products.
Apart from the process perspective, a
comprehensive approach towards BPM requires the
integration of different resources and perspectives,
like (cf. 0)
− Users: as already mentioned, government
activity is strongly impacted by the variety and
diversity of stakeholders involved in a certain
business case.
− Laws: government activity is heavily based on
legal regulations and norms.
− Security: government activity requires high
security and trustworthiness as well as
implementation of privacy decrees. Customers call
for the same quality of security in e-government as
in the traditional way of service consumption.
− ICT resources: to implement e-government
one needs to know, which applications, data
resources and network protocols are used.
− Organisation: as already mentioned, BPM is
strongly related with the organizational structure of
an institution and its relation to other institutional
bodies.
− Data, info and knowledge: official proceedings
require data and document input and outputs. One
has to integrate these resources adequately in the
process workflow.
To realize the need of developing such integrated
process models, an appropriate BPM methodology
and tool is key. Section 3 of this paper is introducing
the project approach, the practical implementation of
the BPM tool as well as a critical discussion of the
topic.
3 TOOL AND MODELLING
REQUIREMENTS
As pointed out above, e-government requires a
holistic concept and integration of technological,
organisational, user-specific and process-specific
dimensions. An integrated approach of BPM is an
instrument to harmonise the issues of these
dimensions and to realise a comprehensive business
process re-organisation motivated by innovative IT
potentials (see also 0 ).
The project idea was born after the authors
experienced the lack of an appropriate modelling
methodology for the use within e-government
project on national and international levels
7
. Basic
requirements from the administration point of view
were the comprehensive insight into inter-
organisational and front- and back-office processes,
an integration of the organisational and technical
perspectives, a horizontal integration in respect to
service bundling or an integration of decisions in the
limelight of political strategies of governments.
As stated in the introduction of this paper,
Austria is in the middle of the transformation from
government to e-government. Huge projects
launched by the federal government, clear directives
for federal, regional and local administrations and
the new e-government law
8
are pushing authorities
into the information technology age. A big issue is
the transformation of processes as they are executed
now to processes automatically executable.
ADOamt
®
, the modelling methodology covering
the requirements of public administrations to
identify, describe, analyse and document their
processes, was developed within a nationally funded
project, approved in some practical projects and is
now in its second development phase. The following
sections will describe the procedure model within
ADOamt
®
, some project insights as well as a critical
discussion about introducing BPM with ADOamt
®
at public administrations.
7
see http://www.egov-project.org and [11]
8
E-Government-Gesetz; January 2004
ICEIS 2004 - INFORMATION SYSTEMS ANALYSIS AND SPECIFICATION
96
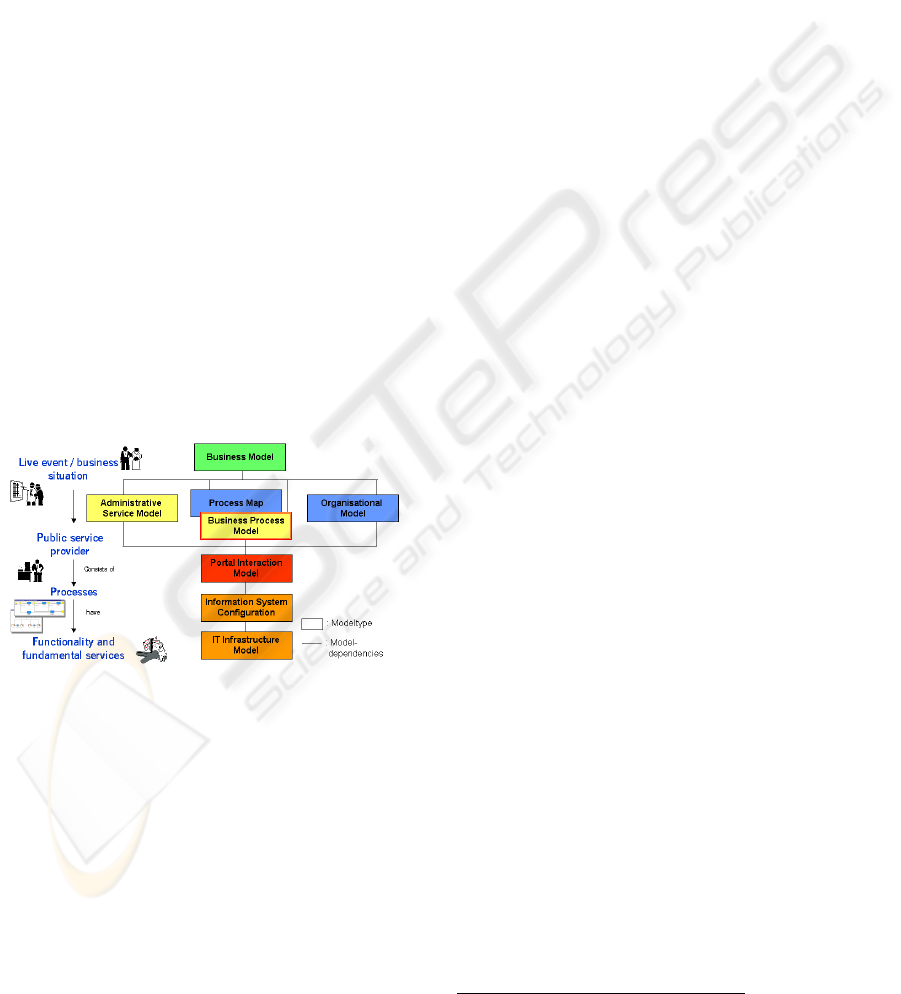
3.1 Procedure Model
Through the provision of a number of different
model types within ADOamt
®
, diverse management
approaches can be followed within the BPM tool.
Process models are seen as the core element as the
process flow, upcoming decision paths, activity
descriptions, documents links, executing roles and
performers and other resources are identified and
described. The strategy-/planning model supports
the life-event approach described in [11] [12]. The
products and services offered by public authorities
can be depicted and linked to the process models
executing such services. Security aspects, described
in more detail in section 4, are an important issue
within e-government and are therefore handled in a
separate model type.
Use case diagrams, activity diagrams and class
diagrams from the UML notation are provided to
follow a model-based application development.
Another management approach supported by
ADOamt
®
is the IT infrastructure management to
administer the underlying IT within public
authorities.
All the model types are interacting with each
other to form an integrated, multi-level business
process management tool.
Figure 1: Holistic Process Modelling Framework
In order to scoop out the whole spectrum of the
tool the following modelling procedure is suggested.
Starting from the description of products and
services in the strategy-/planning model, either
following the life-event approach or in form of a
business model, the products and services are
assigned to organisational units providing them.
Business processes are describing the procedure,
how products and services are provided to the
citizen and how internal processes are executed. The
processes are modelled on swim lanes to structure
the activities according to the involved roles. The
working environment, depicting the organisational
units with their performers and roles, is process-
oriented and is directly assigned to the process
models. The business process with security aspects
is automatically generated out of the business
process and provides security attributes to be
documented according the description given in
section 4 of this paper.
If the technical part of the realisation of e-
government projects should also be model-based,
several model types are provided within ADOamt
®
.
3.2 Project Experience and Critical
Discussion
The first project period was finalized in November
2002. From this time on the project members were
eager to practically use the modeling methodology
in practical projects to get some feedback and results
from public administrations.
ADOamt
®
is used in projects with reference
cities by a local team of ministerial delegates and an
internationally operating consulting company
9
as
well as in several Austrian ministries.
Experience showed that most e-government
projects with the aim to provide services to the
citizen via an online platform do not take business
processes into consideration. The general attitude
about business process management in federal
governments is rather negative as it is often seen as
additional not necessary work. Federal governments
are workflow-oriented to tighten their internal
organizational processes and their service processes.
But from the authors point of view the identification
of the as is processes is of utmost importance in
order to identify the automation potential of the
should be processes. Several applications show the
results of that attitude and are not really timesaving
and satisfactory for the citizen (e.g. mobile parking
or annual adjustment of income tax).
The situation for local authorities is a bit
different. Business process modeling is seen as a
burden rather than a relief. But especially for small
organizations, business process management can
offer numerous advantages like the efficient usage of
limited resources or cost saving online services for
the citizen.
Critics of the business process management
approach may have the argument that BPM is time
consuming, costly or even more confusing to not
experienced project responsibles. Maybe in some
point they are right, but with the right concept, the
9
CIO Office, www.cio.gv.at, and Unisys
PROCESS MODELLING - BURDEN OR RELIEF? LIVING PROCESS MODELLING WITHIN A PUBLIC
ORGANISATION
97

appropriate support and a flexible management
integrated business process management can be seen
as strategic assistance in executing successful
projects.
The next section is concentrating on the security
aspects within e-government applications and the
need of documentation of such aspects within
process models.
4 SECURITY ASPECTS
Mapping conventional business process models of
public administrations to e-governmental
applications requires keeping an eye on security
aspects. Ideally, during the modelling phase the
process owner should be already faced with security
requirements and their impacts. However, in a
business process modelling tool there is a need to
express security requirements in an abstract way. As
a result, close to the business process model some
kind of security model should arise.
4.1 Security Requirements for e-
Governmental Applications
Talking about e-government means to talk about IT
security. The aim is to build a system guaranteeing
at least the same security standards than
conventional governmental applications provide
nowadays. Moreover, within such new applications
users and providers are facing even higher security
risks. Thus, there is a need to take a lot of additional
efforts for reducing these rising threats.
Giving a brief overview, we have to ensure at
least the following principles 0:
− Identification
− Authentication
− Non-Repudiation
− Confidentiality
− Data Integrity
− Availability
Identification means to identify some entity,
namely the user, in context with the application. In
order to ensure that a person is really the one it
claims to be, there is a need for some kind of
authentication. There are a lot of possibilities to
realize authentication. Especially in context with e-
government, citizens may use their smart cards for
this purpose. In some circumstances, there is no
need to authenticate a person by the use of such a
strong mechanism. Very often it would be sufficient
to do this by asking for some ordinary credentials
such as a password or a PIN.
Non-Repudiation is of paramount importance, in
e-governmental applications respectively. Not only
the user has to be forced to do not repudiate his
actions, but also public authorities have to do so
either. Confidentiality and data integrity seems to be
naturally, however, they are one of the most
important requirements.
At last, depending on the application availability
may become very important. It is obvious, that very
critical processes have to be realized redundantly in
order to guarantee that the process keeps on running
anyway.
Beside these major requirements, local
legislative administrations may add some additional
requirements defined by law. Depending on the local
situation, data protection laws
10
or e-governmental
laws
11
have to be considered.
4.2 Modelling Security
Conventional business processes contain a lot of
security measurements and security requirements
without knowing them explicitly. For example,
client authentication at some public administrative
offices takes place without any additional effort by
simply adding the client’s signature onto the form.
In some cases, there is also a need for strong
authentication in the sense of presenting some
personal ID-card or some kind of birth certificate.
Many of these security measurements and security
tasks happen without being noticed. In e-
governmental applications, these security tasks have
to be rebuilt by some adequate IT security
measurements.
10
E.g. in Austria: Datenschutzgesetz (DSG 2000). StF:
BGBl. I Nr. 165/1999 idgF.
11
E.g. in Austria: Bundesgesetz über elektronische
Signaturen (Signaturgesetz – SigG), BGBl. I Nr.
190/1999 idF: BGBl. I Nr. 152/2001
ICEIS 2004 - INFORMATION SYSTEMS ANALYSIS AND SPECIFICATION
98
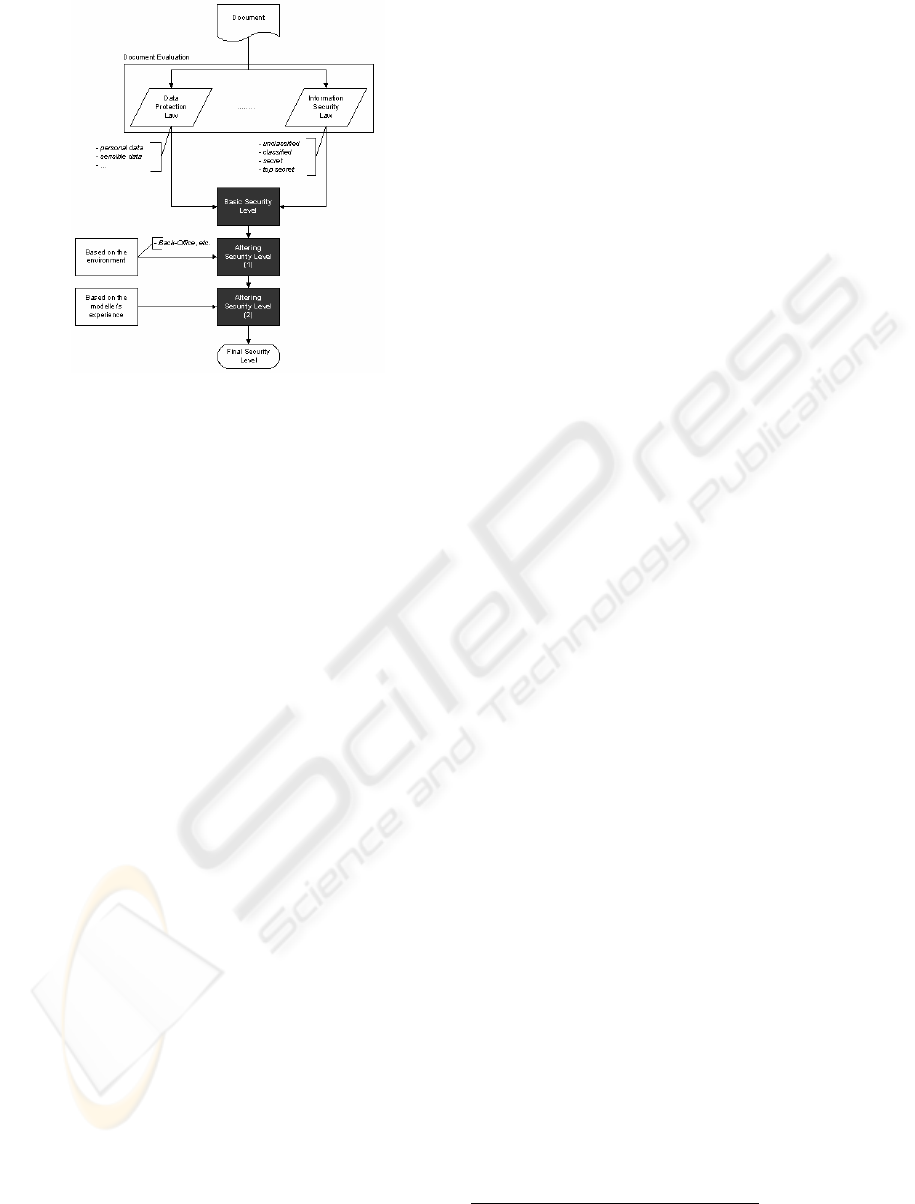
Figure 2: Approach for modelling security
Therefore, in order to be able to create a business
model, which should contain all the information for
transforming it into e-enabled processes, these
hidden security requirements have to be discovered
and they have to be inserted into the business
process model as well.
Since business process modellers are normally
not familiar with IT security and since IT security
can become quite complex especially with regard to
the high security requirements given within e-
governmental environments, there is a need to
describe security on a quite high abstraction level.
Providing an easy approach for modelling
security related aspects within business process
modelling the following workflow is applicable (Fig.
1), which consists of the following steps:
− Evaluation of the document
− Altering the security level based on the environment
− Altering the security level based on the modeller’s
experience
Document Evaluation: Modelling security, as
described in this paper, is based on the thesis, that
the level of security of an activity, or of the process
as such, is demanded mainly by the data contained
in the documents used. In other words, the data
contained in the forms and records involved in an
activity define the basic security requirements.
Based on the evaluation of the data contained in
a document it can be categorized with different
security levels. Such a security level is a quite good
abstraction describing the strength of security
measurements that have to be implemented.
Consideration of the Environment: The basic
security level retrieved from the document
evaluation step may be altered depending on the
environment of the process. Therefore, activities
working in the back office area may require a lower
level of security although the data and documents
require a higher level of security. In such a situation,
the environment provides some security itself
resulting in a lower overall security level.
Altering the resulting security level by using
the modeller’s experience: The modeller’s
experience should be used to vary the resulting level
of security as well. Thus, for any good reason the
modeller is able to correct the resulting level of
security according to the situation. Of course, any
alteration has to be explained by the modeller. Such
an explanation is important for an optional
evaluation process asserting that the security
requirements claimed by the model are sufficient.
Summing up, a document or its data respectively
require a basic level of security. Based on this basic
level, the modeller can modify it and he is asked for
adding his experiences and to consider the
environment either.
4.3 Influences on the Tool
Within the tool, the conceptual workflow
presented in the last section is the basic idea for
modelling security. Therefore, for creating a
business process model containing security
requirements as well, the modeller has to obey this
workflow.
This means that in a so-called document model
all existing documents have to be evaluated based on
their contents as described in the workflow. Thus,
the tool provides the possibility to compare the
content with applicable criteria allowing
categorising them easily. For example, in an
Austrian version of the tool, these criteria are
partially taken from the local legislation such as the
data protection law or the so-called information
security law
12
. Both of them allow to evaluate
documents and to categorise them in security levels.
An activity using these categorised documents
inherits initially the level of security given by them.
If several documents are used, the highest level
required by at least one document is the one the
activity gets assigned.
To depict the security level required by an
activity, a special security view is helpful.
Fig. 1 Workflow for security level
determination
12
E.g. in Austria: Informationssicherheitsgesetz (InfoSiG),
StF: BGBl. I Nr. 23/2002 idgF.
PROCESS MODELLING - BURDEN OR RELIEF? LIVING PROCESS MODELLING WITHIN A PUBLIC
ORGANISATION
99
Security Level
I
III
0
Secured
Connection
>100
?
Security Level at
the output
Security Level at
the input
Security Level of
the main part
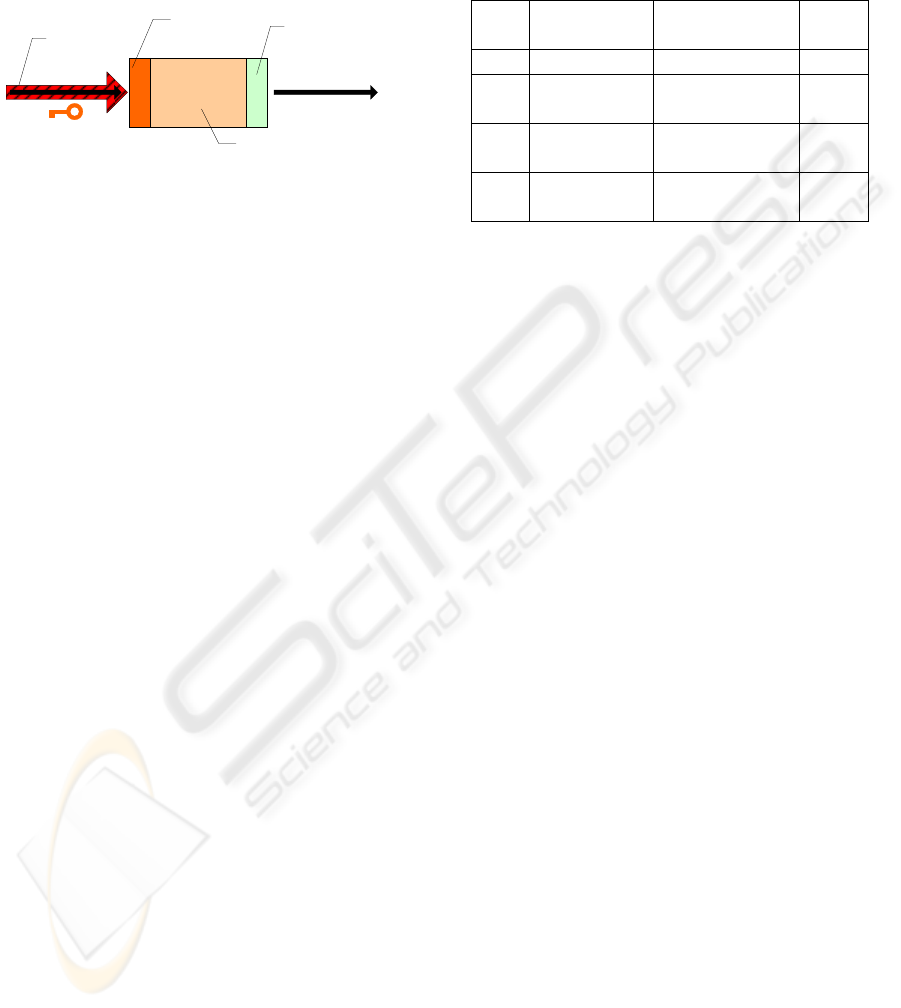
Therefore, the models illustrating activities from the
security perspective can be divided into three parts:
the input, the output and the process itself. Figure 3
depicts a symbol for a business activity (in the
security view) showing the three parts and their
security levels.
Figure 3: Activity with security levels
ach of them requires different levels of security
depending on the docume s used and depending on
the given environment as well. Thus, on one hand it
is possible to have some critical documents requiring
some hig t of an
act ity. On the other hand, the documents used at
the
If the
mo
uld
del
ity measurements
E
nt
her level of security at the inpu
iv
output may be not the same. Thus the output
requires a lower level of security. This is why the
input and the output are considered separately from
the point of view of security. The main part
describing the security level, and security
requirements respectively, of the process itself can
vary not only depending on the documents used but
also with regard to the activity’s environment.
As mentioned before, the workflow used to
determine the resulting level of security is
influenced by the environment of the process and by
the experiences of the modeller. Thus, the tool
provides a lot of possibilities for altering the basic
security level given by the documents used.
deller decides to vary the security level inherited
from a set of documents, he is forced to give some
arguments for reasoning. As mentioned above, these
arguments are very important in the case of
verification of the security requirements. Especially
within e-governmental applications, processes and
their security requirements should be verifiable.
Throughout the whole work on modelling the
business process and considering the security
requirements, the user is never touched with
technical details concerning the realisation of the
required security measurements so far. However, the
tool and the resulting business process model sho
iver requirements for the IT specialists realising
the process and its activities as well. Therefore,
since the user assigns abstract security levels only,
though, these security levels can be mapped to hard
requirements for the IT specialists.
Table 1 gives an example of the assignment
between security levels and their corresponding
security requirements and their security
measurements respectively.
Table 1 Mapping security levels to secur
Sec.
Level
Ident./
Auth.
Additional
Requirements
Comm
.
0 - - -
I - standard system SSL/
TLS
II chall. resp. ID-card SSL/
dig.signature TLS
III cert ty L/
S
ificate no manipulabili SS
TL
Nevertheless, the process modelling to ould
pro de so s, w dva user
the possibility to add con y requ nts.
For exam ring a t e of
certificates or by the use of some challenge onse
mechanisms may be specified during modelling.
ide
var
scussed
advantages and added values of using business
ons.
ded
val t levels: local,
regional and federal.
standard interfaces to operative systems. These goals
ol sh
vi me setting hich give an a nced
iremecrete securit
ple, requi uthentication by he us
-resp
Modelling security requirements by the use of a
process modelling tool enables to simulate and
calculate additional efforts caused by the security
measurements. Therefore, a set of data describing
the additional efforts raised by using security
technologies must be available. Due to the w
iation of security mechanisms and their
implementations respectively, it is necessary to
collect these data in an environment similar to the
target environment given in a public administration
for instance.
However, by the use of such sets of data in
context with the security model, the process
modelling tool might simulate additional efforts
needed, e.g. time delay, additional costs, etc.
5 ADDED-VALUE FOR PUBLIC
ADMINISTRATIONS
In previous sections we already di
process management within public administrati
These paragraphs should now stress the ad
ues for authorities at differen
Three objectives of utmost importance within
public organisations could be named efficiency
increase, quality increase of public services and
standardisation in the sense of reference processes or
ICEIS 2004 - INFORMATION SYSTEMS ANALYSIS AND SPECIFICATION
100

can be achieved with the help of management
approaches like bu
siness process management,
qua
line. Business
pro
able to
all
proach including the description and
doc
d be realised with
the
mo
velopment of a tailor-
made modelling methodology the authors come to
lic authorities need an
veloping innovative and
new public services in order to become more citizen-
Commission to the Council, the European
Parliament, The European Economic and Social
Committee and the Committee of the Regions,
final, Brussels, 26.9.2003,
ation_society/eeurope/2005/
Gis
Grö
pplications
lity management or IT Management. The
integrated approach described in this paper supports
such management approaches and can be the basis
for an integration platform.
Local authorities have different priorities and
objectives than regional or federal. Cities or villages
heavily emphasise on the development of a catching
Internet presentation of their organisation. Offering
public services via the Internet needs the
transformation of processes to e-processes, that is
the possibility to execute processes on
cess management optimally supports this
intention by finding, describing, optimising and
documenting governmental processes. An example
of such an e-process could be the online application
for a new passport or the online registration.
Another big issue in local governments are
reference processes and the communication and
cooperation with other local authorities. By
providing reference processes to cities a lot of effort
can be avoided. The process for an application for
holidays for example could be standardised and
published in the intranet/internet to be avail
employees.
The regional level itself pursues different
objects. It is quite important for these authorities to
be well coordinated in their daily treatment with
local and federal organisations. Therefore
standardised processes should be the major goal.
These processes can be developed by an integrated
management ap
umentation of the processes, the implementation
of interfaces to standard software or legacy systems
and the transformation of the business processes to
workflow management systems for online execution.
The measurement of indicators and goals combined
with the business processes is becoming a major
issue for public administrations.
Last but not least federal governments define
their objectives on a higher level. Comprehensive e-
government projects surface the IT landscape of
federal authorities, portals for online public services
are developed and standardisation efforts became of
utmost importance. These goals demand a well-
structured organisation that coul
help the integrated business process management
toolkit developed in the project described above.
Process modelling is an essential aspect in e-
government projects in order to depict the
significance of the changes and necessary adoptions
of procedures and products within public
administrations (for example online public services).
The integration of organisational and IT
perspective as well as strategic and operative level
become a crucial success factor. The process
modelling tool ADOamt
®
faces the challenge and
supports public authorities in their whole process life
cycle – from the strategic decision over design of
processes to the execution and evaluation. The
dularity and openness of the process modelling
tool offers the possibility of the integration of
different software tools like workflow management
systems, standard software or groupware tools. The
integrated modelling from the portal to the back-
office including the underlying IT architecture as
well as the integration of the involved parties
(citizen, organisation, administrative clerk, etc.)
form the core of ADOamt
®
.
6 CONCLUSION
After more than one year of working intensively
with the topic process modelling within public
administrations and the de
the conclusion that pub
integrated platform for de
oriented and transparent in their day-to-day business.
The high level of interest in our work coming from
representatives of different administrative
organisations makes us confident that we are on the
right way helping e-government projects become
successful.
REFERENCES
Commission of the European Communities: The Role of
eGovernment for Europe's
Future, Communication
from the
COM(2003) 567
http://europa.eu.int/inform
doc/all_about/egov_communication_en.pdf
[2003/10/20] [1]
ler, Michael: Einführung in die Begriffswelt des e-
Government. In Gisler, Michael, Spahni, Dieter (Eds).
E-Government – eine Standortbestimmung, Paul
Haupt, Bern, 2001, pp. 13 – 30; [2]
nlund, Ake: Electronic Government – Efficiency,
Service Quality and Democracy. In Grönlund, Ake
(Ed): Electronic Government: Design, A
PROCESS MODELLING - BURDEN OR RELIEF? LIVING PROCESS MODELLING WITHIN A PUBLIC
ORGANISATION
101

and Management, Idea Group Publishing, Hershey et
al, 2002, pp. 23 – 50; [3]
nl, Stefan and Wimmer, Maria: Rahmenkonzept für e-
Government Entwicklungen. In Wim
Ha
mer, Maria (Ed.):
ISO rocessing systems - Open
Ka
ird
Poo
gang mit
Rei
ür
Sch Servicequalität
UN
Wi r, Maria A.: Integrated service modelling for
rch and Applications, 1
Wi
rnment: eine Zwischenbilanz. In Schweighofer,
2002, pp. 19 - 27; [13]
Impulse für e-Government: Internationale
Entwicklungen, Organisation, Recht, Technik, Best
Practices. Proceedings of the 1st e|Gov Day of the
Forum e|Gov.at. OCG, Wien, 2002, pp. 72-83; [4]
7498-2: Information p
Systems Interconnection - Basic Reference Model -
Part 2: Security Architecture, International
Standardization Organization, 1989; [5]
ragiannis, D., Kühn, H.: Metamodelling Platforms,
Invited Paper, appeared in: Bauknecht, K., Min Tjoa,
A., Quirchmayer, G. (Eds.): Proceedings of the Th
International Conference EC-Web 2002 – Dexa 2002,
Aix-en-Provence, France, September 2-6, 2002; [6]
k, K., Starkloff, P.: Geschäftsprozesse und
Wissensmanagement – vom Um
erfolgskritischem Fachwissen, in: Praxis
Wissensmanagement 4/01, page 2; [7]
nermann, Heinrich / von Lucke, Jörn (Eds.): Electronic
Government in Deutschland - Ziele, Stand, Barrieren,
Beispiele, Umsetzung. Forschungsinstitut f
öffentliche Verwaltung bei der Deutschen Hochschule
für Verwaltungswissenschaften Speyer, Speyer, 2002;
[8]
edler, Kuno: e-Government und neue
der Verwaltung?, in Schedler, Kuno (Ed.): Grundlagen
des e-Government, 200, pp. 33 – 51; [9]
PAN DPADM/UNDESA: e-government principles
and definitions, http://www.unpan.org/dpepa-kmb-
tools.asp [2003/10/20] ; [10]
mme
online one-stop government, EM - Electronic Markets,
Special issue on e-Government, 12 (3), 2002, pp. 1-8;
[11]
Wimmer, Maria A.: A European Perspective Towards
Online One-stop Government: The eGOV Project,
Electronic Commerce Resea
(1), 2002, p. 92-103; 12]
mmer, Maria, Traunmüller, Roland:
Geschäftsprozessmodellierung im Bereich E-
Gove
Erich, Menzel, Thomas, Kreuzbauer, Johann (Eds.): IT
in Recht und Staat. Aktuelle Fragen der
Rechtsinformatik 2002. SR Rechtsinformatik # 6,
Verlag Österreich, Wien,
ICEIS 2004 - INFORMATION SYSTEMS ANALYSIS AND SPECIFICATION
102
