
Experiences with a Business Evaluation Model for
Mobile Commerce Services
Thomas Flor
1
, Walter Niess
1
, Gabriel Vögler
1
1
DaimlerChrysler AG, Research Information and Communication
Software Architectures (RIC/SA), P.O. Box 23 60
89013 Ulm, Germany
Abstract. If business processes (business cases) for mobile applications (perva-
sive computing) are to be evaluated, it is necessary to arrange a portfolio of
application scenarios. For this a methodical procedure is defined, which helps
to receive a prioritized overview over possible business cases as well as further
details regarding organizational and technical aspects. Due to certain criteria
application scenarios can be selected, which are used for the evaluation. For
these a detailed questionnaire is developed, which serves as decision basis for
the realization of the business cases.
1 Introduction to mobile services
Personal Digital Assistants (PDAs) find ever larger spreading. If they first were used
only as electronic alternative of a paper-based time schedule system for storing
personal data, like calendar, contacts and notes, thus so-called PIM (Personal
Information Management) data, today also more efficient applications such as word
processing and spreadsheet can be run on them.
Also in enterprises PDAs find increasingly wider fields of application. They are
not only applicable as single or off-line device, but are more and more integrated as
clients in the distributed enterprise network. It is possible and in individual cases also
advisable to execute larger applications on them and to access resources in the
enterprise network. So not only the classical PIM data on mobile devices is available,
but basically all information available in the enterprise network, e.g. files on file
servers, contents of database servers and also dynamically provided data from
application or portal servers.
In order to be able to make these information available for mobile devices, techni-
cal and organizational measures are necessary, e.g. the definition of appropriate
architectures and providing several services, e.g. dial-in for mobile devices or
synchronization services. In order to accomplish all these tasks, it is necessary to
compile a prioritized overview over relevant mobile applications and business
processes. The environment for pervasive computing must be evaluated before
startup. For that it is helpful to categorize the applications according to a defined
pattern in order to be able to judge the entire application field and the technical and
economical success of the individual business cases in detail.
Flor T., Niess W. and Vögler G. (2004).
Experiences with a Business Evaluation Model for Mobile Commerce Services.
In Proceedings of the 3rd International Workshop on Wireless Information Systems, pages 111-118
DOI: 10.5220/0002651701110118
Copyright
c
SciTePress
2 Architectural overview
All applications are to be rated by a certain schema with the same questions. Thus
they are comparable with each other.
For the evaluation of the infrastructure a portfolio with test cases can be arranged.
It should contain as many as possible different test cases, so that all functions of the
infrastructure to be tested are evaluated. The evaluation phase has not to cause much
expenditure. Therefore the evaluation portfolio should contain applications, which can
be implemented without much technical expenditure, for which however a high
economic success (business impact) is expected.
Thus it should be possible to identify business cases by a schematic procedure with
which all functions of pervasive computing can be evaluated, both the infrastructure
on the mobile client side as well as the server side and the connecting network.
2.1 Applications and service blocks
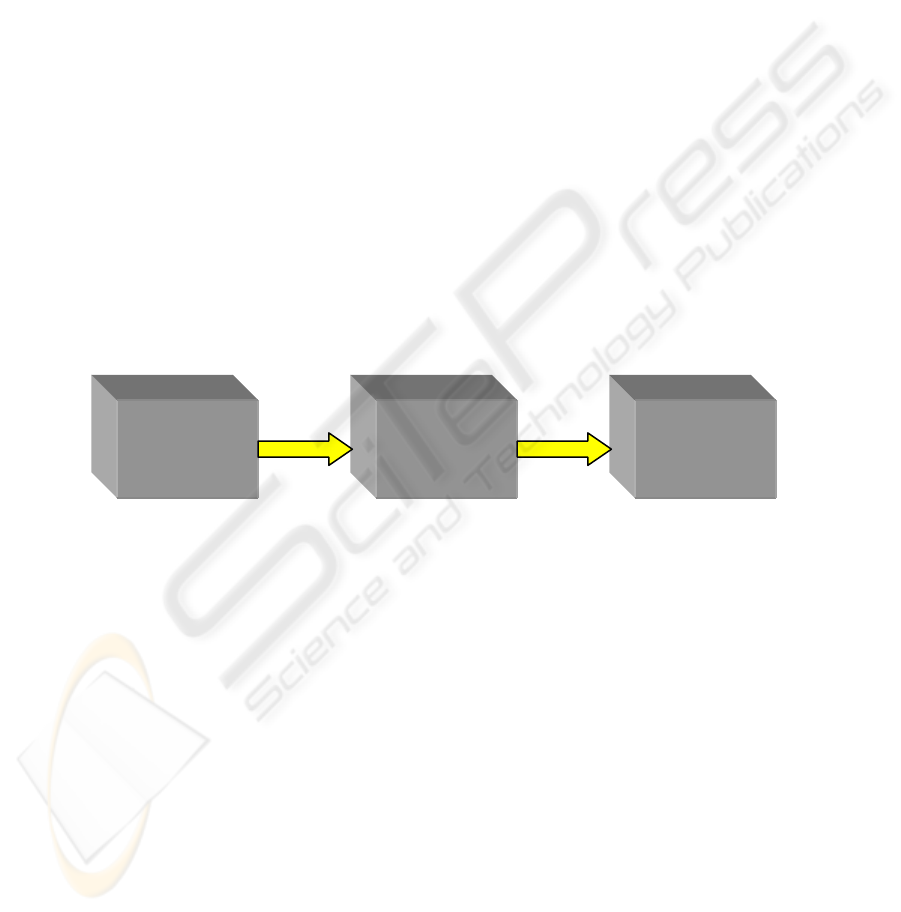
In order to determine the functionality needed by a business process, first of all the
professional requirements (business view) must be analyzed. Based onto that the
technical requirements at their implementation (technical view) are identified. Finally
the needed technical functionality can be combined into architecture components
(service blocks), in order to provide a uniform architecture for pervasive computing
for all business processes according to the requirements (see figure 1).
Fig. 1. Business view, technical view and derived service blocks
The identified architecture components make thus available all functions defined in
the technical view. With their assistance all professional requirements determined in
the business view can be realized.
This correlation is important for the evaluation: In order to evaluate service blocks,
business cases are used, that use the cross-section functions of these service blocks,
e.g. administration, synchronization, transcoding, etc. The business cases of a
portfolio have to be selected in such a way that functions described in the technical
views of the business cases cover all the functions of the service blocks which have to
be evaluated.
Business
View
Technical
View
Service
Blocks
112

3 Analysis of Pervasive Computing Business Cases
Mobile applications can be judged on the basis of questionnaires. Depending upon
which aspects of applications are to be judged, the list of questions can be more or
less extensive. So applications can be regarded e.g. only from the professional view or
also their technical implementation.
3.1 Professional Requirements
The professional requirements of a business case can be determined with the
following questions:
- Who? Which circle of users uses the application? Are further persons affected
through the operation of the application, e.g. administrators or data suppliers?
- What? Which data is the user supposed to work on with the mobile business case?
Which information must be accessed from mobile devices? Which data will be
modified or created and possibly must be synchronized with a central data server?
- When? When will the mobile application be used? At which time of day is
information with mobile devices processed? Is this limited to certain times or is it
necessary to make the data access possible all around the clock?
- Where? In which geographical range is the mobile application supposed to be
used? Does it have to be available only on the ground of the own enterprise or also
outside? Is an availability in areas with cellular phone network sufficient?
Through clarification of these questions the application is examined better. The
business view of the application is determined. On this basis the technical view can be
worked out.
3.2 Business case classification template
In order to be able to select business cases for a portfolio, it is beside the business
view also necessary to receive information about the possible technical realization. It
is recommended to collect all information, relevant for the selection task, in form of a
template. Such a template for the classification of individual business cases contains
therefore apart from the questions concerning the business view, in particular aspects
of a possible technical implementation (see figure 2).
A more detailed description of the implementation is not necessary in this stage of the
business case analysis. If necessary, the templates can be refined iteratively for
defining a suitable architecture.
113
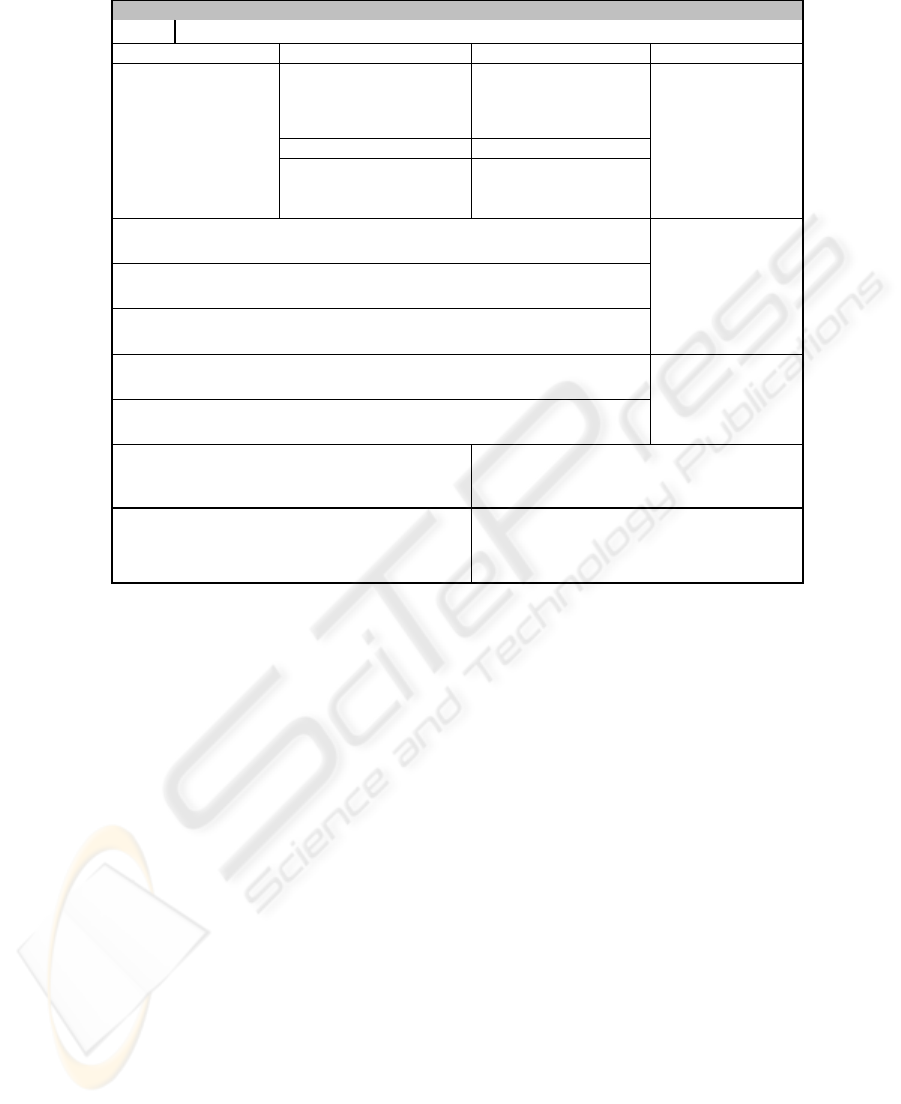
No.
Synchronous Data Flow Asynchronous Data Flow Annotations
always-on connections
offering immediate access to
information, may increase
actual costs
connections built on
demand, are removed if all
information has been
transmitted successfully
Push Data Flow Pull Data Flow
information (or part of it) are
delivered directly to the user
(e.g. SMS)
user checks for new
information
general description of the
specific business case
including the advantages
of a pervasive solution
Performance Requirements
To what extend will the network and infrastructure be
loaded?
When
(time + availability requirements):
When and how often may the system be used?
Where
(location):
Where can the technology be used? Are there any constraints?
Who
(people):
Who could make use of the business case?
Feasibility Requirements
How much effort has to be put into the realization of
the business case?
Business Impact
(when mobile devices are used
additionally):
What kind of advantages can be expected from the
realization of the business case?
Type of the Business Case
Name of Business Case
Description
Distinctive Features:
e.g.: minimizes delay, increases mobility, simplifies process
Device Support
supported mobile
devices
Data Security Requirements
Will security relevant data be transmitted? If so, to what
extend and how can the data be protected?
What
(information + average amount of data per transaction):
What amount of data will presumably be transmitted? (estimated values)
annotations specific for
the particular business
case
Bandwith Required
e.g. GSM, GPRS, UMTS,
WL AN
Fig. 2. Classification template for pervasive computing business cases
3.3 Business case portfolio
The portfolio for evaluation and prioritization of the most important business cases is
constructed according to criteria specified before. The selection process is not trivial,
since several assessment aspects are relevant usually. In order to simplify the
selection of business cases, graphical representations can be used.
If for example in an evaluation phase the business cases relevant for the enterprise
are to be realized with little expenditure, then a portfolio can be arranged after the
following criteria:
- It must be possible to evaluate all functions which must be tested with the business
cases, i.e. the business cases are supposed to use a possibly high portion of cross-
section functions (service blocks).
- The business cases have to be implemented without much expenditure.
- The business cases must have a business impact as high as possible.
The criteria can vary depending upon the evaluation to be practiced and must be
specified on an individual basis.
114
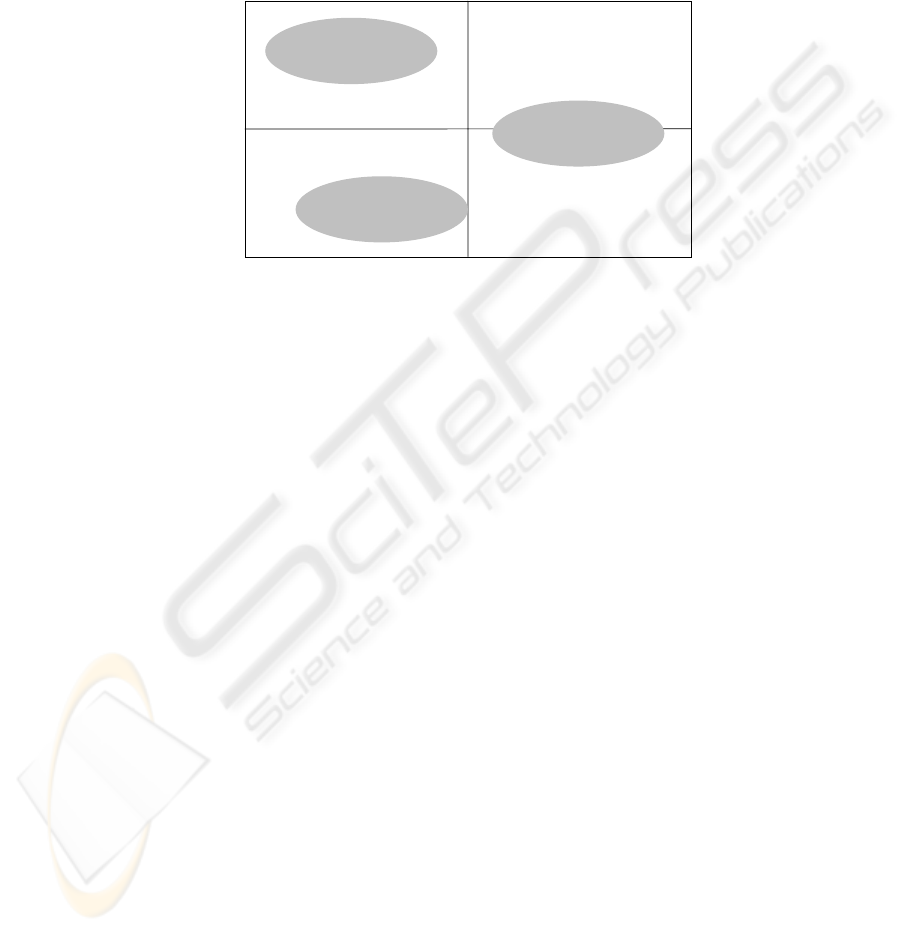
With a two-dimensional portfolio (representation of essential evaluation parame-
ters of a business process in relation to each other, see figure 3) the selection of the
business cases can be simplified. In order to determine e.g. business cases at high
business impact and small implementation expenditure, these two parameters should
be represented.
Implementation Expenditure
Low High
Business Impact
HighLow
Portfolio Business Cases
Business Case
2
Business Case
3
Business Case
1
Fig. 3. Portfolio with implementation expenditure and business impact
Since usually not only two parameters are relevant for the selection, such a two-
dimensional representation can only be an assistance for the selection task. Alter-
natively to multidimensional portfolios several portfolios can be provided in rela-
tionship to each other.
4 Analysis of technical requirements
For implementing the selected business cases of the portfolio additional information is
needed. In order to determine these, a detailed and uniform questionnaire is compiled
for each business case that has to be implemented. On basis of the templates it forms a
strongly refined decision basis for the selection of architecture components and
technologies to be used for realization.
With this questionnaire the functional requirements are regarded apart from more
detailed business aspects, as well as technical boundary conditions and organizational
aspects:
Business aspects: Through analysis of further business aspects the economic
background can be better understood. Thus it is guaranteed that during the design of
the technical solution the economical aspects are always the center of attention.
- First of all, the mission is described, which is pursued with realization of the
business case. To reasons belong why the targeted mobile solution is needed and
what is to be aimed with it.
115

- Furthermore the desired goals are discussed. For controlling the achievement of
objectives measurable criteria must be defined, e.g. specific financial changes or
measurable improvements of the satisfaction of users or customers in relation to
possibly an already existing stationary solution.
- In addition all involved persons should be determined, thus beside users also
administrators, data supplier, etc. Since possibly not only advantages are expected
with a mobile solution, it should be determined whether the persons profit from the
solution or whether disadvantages result. Such disadvantages can be e.g. a higher
administration or data maintenance expenditure.
- It is important to clarify which changes are expected in defined process flows, if
the business processes are mobilized.
Functional requirements: The functional requirements are refined with the
background of the determined business aspects. They serve as basis for the draft of
the technical solution and determine the architecture components relevant for
implementation. Furthermore a first overview of the information processed in the
system and necessary data flows results.
- The tasks to be done with the application are determined. For each task the user
group is recorded that has to do the task. Beside the end-users also system users
etc. are regarded.
- For each work routine the single steps are represented.
- Also an overview of the necessary data results from that. It is shown, who or which
technical component processes which data and where the data comes from.
Interfaces to external systems with which data is exchanged, result from that.
- Further the importance of certain system properties can be estimated, e.g.
performance, security or service availability.
Technical boundary conditions: All boundary conditions to be kept according to
possibly already existing technical infrastructures (concerns both server side and
mobile client side and existing network) or architecture specifications are
documented. Appertaining to that:
- the existing infrastructure, like system environments, operating system platforms,
middleware systems and test environments
- enterprise standards, e.g. system management and operational concepts of
applications
- network access and dial-in knots
- security standards
Organizational aspects: Certain organizational aspects are associated with the
introduction of mobile business processes, like e.g..
- planning, operation and process of rollouts.
The above list shows only an overview with the most important aspects of the
compiled questionnaire. It analyzes the business view and the technical view very
detailed. With these informations the evaluation and prioritization of the business
cases in the portfolio can be revised in an iterative process on the one hand and on the
other hand the planned realization of the business cases can be executed more
purposefully.
116
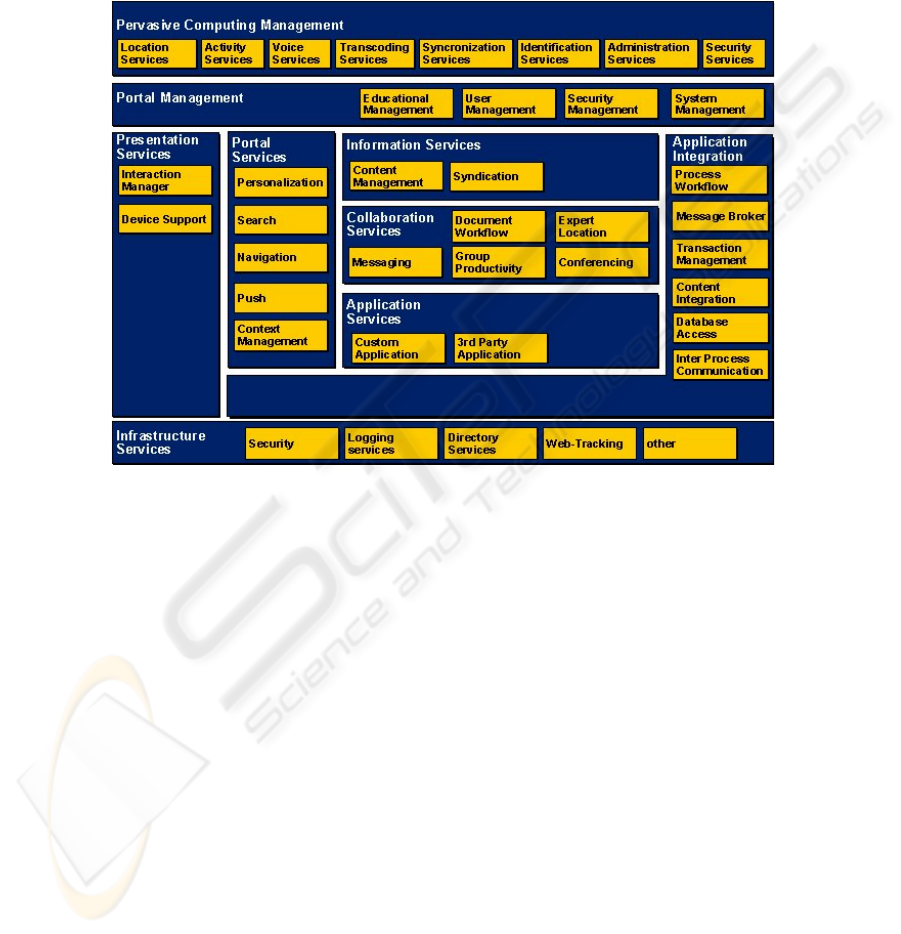
5 Pervasive Computing Service Blocks
After having analyzed the business cases, the functions needed to implement them,
can be determined. The functions can be grouped to service blocks by the field of
application. For applications of a pervasive computing environment, the service
blocks could be (see figure 4):
Fig. 4. Pervasive computing layer on top of other architecture layers
- location services: They are used to locate a mobile device, e.g. to offer location
based services
- activity services: They are used to get information if a mobile device is active and
connected
- voice services: They are used to access applications by voice
- transcoding services: They are used to transcode contents for the specific demands
of different devices
- synchronization services: They are used to synchronize contents, e.g. for mail
synchronization
- identification services: The are used to identify the user and the mobile device
- administration services: They are used to administrate the other services
- security services: They are used to transport data in a secure way to and from the
mobile devices
The mobile services use the existing services of the applications to offer their contents
to mobile devices. So they build an additional layer on top of the other architecture
layers
117

6 Summary
If a portfolio must be defined for the evaluation and prioritization of pervasive
computing business cases, then first the evaluation criteria relevant for the selection
has to be determined systematically. Apart from essential aspects, like small
implementation expenditure or high business impact, the coverage of the functions
which have to be evaluated by the individual business case, belongs to this criteria. A
systematic procedure is guaranteed by deriving the technical view from the business
view and by the following alignment with the functions of the necessary service
blocks. All evaluation criteria, relevant for the composition of the portfolio, is
registered in template.
For the execution of the evaluation further details of the business processes are
necessary, which are answered in a refined question catalog.
Through this iterative top-down procedure the information needed for the
respective step of implementation of a pervasive computing business case is
purposefully developed and analyzed also under economical points of view.
References
1. Coen, M.A.: "A Prototype Intelligent Environment," Cooperative Buildings--
Integrating Information, Organization, and Architecture, N. Streitz, S. Konomi,
and H.-J. Burkhardt, Editors, Lecture Notes in Computer Science, Springer-
Verlag, Heidelberg (1998)
2. Coen, M.A.: "Design Principles for Intelligent Environments," Proceedings of
AAAI 1998 Spring Symposium on Intelligent Environments, Palo Alto, CA
(1998)
3. Czarnecki, K., Eisenecker, U.: Generative Programming: Methods, Techniques,
and Applications, Addison-Wesley, (2000)
4. Hausmann, J.H., Heckel: Use Cases as views: A formal approach to Requirements
engineering in the Unified Process. Informatik 2001: Tagungsbang der GI/OCG-
Jahrestagung, 25.-28. September, Universität Wien, Band 1, S. 595-599, (2001)
5. Johnson, D.B., Maltz, D.A.: Protocols for Adaptive Wireless and Mobile Networking.
IEEE Personal Communications Magazine 3 No. 1, S. 34-41, (1996)
6. Kulak, D., Guiney, E.: Use Cases: Requirements in Context. Addison Wesley
Professional: Boston, MA, (2000)
7. Sommerville, I.: Software Engineering, 6. Auflage. Addison Wesley Professional: Boston,
MA, (2001)
8. Zöller-Greer, P.: Softwareengineering für Ingenieure und Informatiker. Vieweg Verlag:
Wiesbaden, (2002)
118
