
REQUIREMENTS ENGINEERING FOR ORGANISATIONAL
MODELLING
Simon Tan, Kecheng Liu
Department of Computer Science, University of Reading, Whiteknight, Reading, RG6 6AY, UK
Keywords: Requirements Engineering, Semiotics, Organisation Modelling, Norms, Semantics, Agents
Abstract: This paper explores a semiotic perspective to information systems engineering, using organisational
modelling techniques rooted in organisational semiotics. The components and relationships of large
corporations are highly complex, volatile and unstructured. Semiotic modelling techniques are therefore
introduced to address these challenges posed by large enterprises. MEASUR, a suite of methods based on
organisational semiotics, are used to address the IT and organisational requirements, needed to encapsulate
behavioural patterns and to formalise the convoluted relationships. A case study illustrating the applicability
of MEASUR is presented, to evaluate a crime reporting system from the Police Information Technology
Organisation (PITO) in UK, and to examine its application and significance in the modelling of
organisations. We focus on two key fundamental issues. Firstly we investigate the agent behaviour within
the organisation. Secondly, we analyse the semantics of the relationships between these patterns of
behaviour in building a normative model of a large organisation.
1 INTRODUCTION
In the last decade great advances in technology and
the exponential growth of multinational corporations
have led business managers, practitioners and
academics to develop a growing interest in the field
of organisational modelling. Organisational
modelling is interdisciplinary, and as such
incorporates a variety of methods, techniques and
tools. It encompasses social, technical, business and
organisational domain. Modern enterprises are
highly complex, multifaceted and fluid. Traditional
systems, as such are overwhelmed, and unable to
address the social and technical roles of organisation
(Joaquim et al. 1999). Liu et al. (1999) observed that
due to this disparity, systems requirements and
organisational semantics have over the years
evolved separately.
This research employs semiotic methods for
organisational modelling, to improve the design of
business and IT systems. MEASUR (Stamper et al.
1988) proposes a set of methods comprising of
Problem Articulation Method (PAM), Semantic
Analysis Method (SAM), and Norm Analysis
Method (NAM), which we shall discuss and
illustrate using the Police Information Technology
Organisation (PITO) case study.
MEASUR offers a viable alternative, which until
now has not been fully exploited. This approach
contributes towards the overall usability and
coherence of organisational models. The need to
elicit business rules and norms are widely
recognised, it is however represented using
modelling languages that are ill-equipped to handle
organisational behaviours.
Key trait in representing an organisational model
lies in the representation and interpretation of
business rules and norms. These intricate
relationships have to be embedded during
organisational design phase. The weakness with
many information systems is largely attributed to the
inability of requirement engineering to determine
systems requirements based on complex
organisational behaviour. Most information systems
specifications are crudely mapped directly from
business requirements, without due consideration to
factors as norms, semantics and agents. There have
been numerous failed attempts to model
organisational semantics, which were based on
entity-relationships (Peckham & Mryanski 1988,
Wand et al. 1999).
PAM will enable us to identify the organisational
context and define the problem domain, while SAM
will help to study the agents and their behaviour.
NAM will analyse and extend this further by
identifying agent’s responsibility and norms that
control agents behaviour. This paper will offer an
alternative approach to business modelling to
383
Tan S. and Liu K. (2004).
REQUIREMENTS ENGINEERING FOR ORGANISATIONAL MODELLING.
In Proceedings of the Sixth International Conference on Enterprise Information Systems, pages 383-388
DOI: 10.5220/0002653003830388
Copyright
c
SciTePress

Unit System Stakeholders Roles Category Responsibility
Unit 1:
Crime reporting
system
SH 1:
Witness
Actor Contribution
interdependency
Providing statements,
assists investigation
SH 2:
Crime
Assessor
Principal Source
interdependency
Verify incident, refer
cases, issue case
code
Unit System Stakeholders Roles Category Responsibility
Unit 1:
Crime reporting
system
SH 1:
Witness
Actor Contribution
interdependency
Providing statements,
assists investigation
SH 2:
Crime
Assessor
Principal Source
interdependency
Verify incident, refer
cases, issue case
code
supplement modelling languages such as Role
Activity Diagram (Ould 1995), and Unified
Modelling Language (Martin & Ken 1999).
This paper is structured as follows: Section 2
illustrates with a case study of a crime reporting
system, using modelling techniques to derive a
conceptual model of PITO crime reporting process.
In section 3, we briefly describe the application of
the PAM method, and the significance of each
technique, to articulate complex organisational
issues, followed by Section 4 using Semantic
Analysis method to derive the semantics of crime
validation process. In Section 5 we highlight the
Norm Analysis method. Using a norm analysis
template we formulate norms from the crime
reporting process. Section 6 will draw conclusions
and discuss future work.
2 CASE STUDY: POLICE CRIME-
REPORTING
This section introduces a case study which will be
used for further illustration of the MEASUR
methods. This case study was based on a project of
designing a crime management system for the police
force. An excerpt of this project, "crime-reporting"
was highlighted to reflect the actual research
conducted by our research team, which is still
ongoing. For the sake of brevity the detailed
workings and complexity of the model have not
been fully reproduced here.
The Crime Reporting Unit in the Police Force is
the contact point between members of the public and
the police departments. It is charged with the
responsibility of collecting, maintaining, analysing,
and reporting crime data for the nation-wide crime
management.
In the following sections, MEAUR methods will
be introduced. The application of the methods will
demonstrate how the problem domain,
organisational behaviour (in terms of agents and
affordance) and organisations dynamics (norms) are
dealt with in these methods.
3 MEASUR – REQUIREMENT
ENGINEERING METHODS
Organisational semiotics is a sub-discipline of
semiotics that studies the problems of how
information and human communication work in
organisational contexts (Liu et al. 2001).
MEASUR is a set of methods for organisational
modelling stemming from organisational semiotic.
This method aims to address business problems that
are ambiguous, and to define requirements of
organisational and IT systems domains. It seeks to
analyse the existing infrastructure in two aspects:
Organisational Infrastructure and IT Infrastructure.
Thereby it identifies relevant components and their
inter-relationship.
3.1 Problem Articulation Method
Problem Articulation Methodology (PAM) was first
conceived as one of the three methods of MEASUR
by Stamper (Stamper et al. 1988) and his researchers
(e.g. Kolkman 1993). PAM addresses infrastructural
analysis as an initial investigation for organisational
study and information systems design. This method
consists of a suite of five techniques. In the course of
our research, we have made extensions to the
various techniques. This paper will provide a brief
description and objectives of (1) Unit Definition, (2)
Stakeholders Identification, (3) Organisational
Containment, (4) Valuation Framing, and (5)
Collateral Structuring.
These techniques take the infrastructure and
social problem domain as input, and deliver
outcomes in the five categories. These outcomes can
be further seen as input for other semiotic methods
e.g. semantic analysis, norm analysis and the co-
design of business and IT systems.
Units Definition
Unit definition identifies courses of action and
lists interdependent sub-actions needed to
accomplish the lists of objectives. An organisation is
composed of the units systems, the problem situation
is then analysed as a constellation of different sets of
tasks, each providing a brief description. Each
activity can be taken to represent the focal system.
In the case of PITO, the activity of crime-reporting
represents the focal system.
Stakeholders Identification
Stakeholders identification, lists key stakeholders
and their roles within the domain, categorising and
defining stakeholders responsibilities (Table 1).
Table 1: Stakeholder Identification Template.
ICEIS 2004 - INFORMATION SYSTEMS ANALYSIS AND SPECIFICATION
384
Crim e Assessor
Start taking enquiry
R equest Identification
Request incident details
Victim / Reporter
Subm it identification
Describe incident
N o te r e p o rte r d e ta ils
F ill c rim e d e ta ils
Assign to
In v e s tig a tin g
Officer
Police
Allocate Case
Crim e Statem ent
W rite Statem ent
In v e s tig a tio n
Case solved?
yn
V a lid C rim e ?
V e rify n o
d u p lic a tio n
Refer to
R elevant
D ept
CRIME REPORTING
y n
Appraise Incident Validity
Assign C ase no.
New / Existing
Case
Update / Add
Case
Investigation
Social/Legislature
Policies/Regulations
Incident/Case
Roll-back
Retrieve files
reports ref
Close Case
Statement Taking /
Information gather
Assign Case
Criminal Justice System
D/Base, S/Ware, H/Ware,
Legal, Forensic, Police expert
Criminal psychologists
Crime Reporting
Process
New / Existing
Case
Update / Add
Case
Investigation
Social/Legislature
Policies/Regulations
Incident/Case
Network-backup
Storage Archive
Archive Case
Resolved/Pending
Close Case
Assign Case
Crime Database
Verify, Retrieve,
Search
Police National Mainframe,
Criminal files
New / Existing
Case
Update / Add
Case
Investigation
Social/Legislature
Policies/Regulations
Incident/Case
Roll-back
Retrieve files
recent backup
Close Case
Statement Taking /
Information gather
Assign Case
Criminal Justice System
D/Base, S/Ware, H/Ware,
Legal, Forensic, Police expert
Criminal psychologists
Crime Reporting
Process
New / Existing
Case
Update / Add
Case
Investigation
Social/Legislature
Policies/Regulations
Incident/Case
Network-backup
Storage Archive
Archive Case
Resolved/Pending
Close Case
Assign Case
Crime Database
Verify, Retrieve,
Search
Police National Mainframe,
Criminal files
New / Existing
Case
Update / Add
Case
Investigation
Social/Legislature
Policies/Regulations
Incident/Case
Roll-back
Retrieve files
reports ref
Close Case
Statement Taking /
Information gather
Assign Case
Criminal Justice System
D/Base, S/Ware, H/Ware,
Legal, Forensic, Police expert
Criminal psychologists
Crime Reporting
Process
New / Existing
Case
Update / Add
Case
Investigation
Social/Legislature
Policies/Regulations
Incident/Case
Network-backup
Storage Archive
Archive Case
Resolved/Pending
Close Case
Assign Case
Crime Database
Verify, Retrieve,
Search
Police National Mainframe,
Criminal files
New / Existing
Case
Update / Add
Case
Investigation
Social/Legislature
Policies/Regulations
Incident/Case
Roll-back
Retrieve files
recent backup
Close Case
Statement Taking /
Information gather
Assign Case
Criminal Justice System
D/Base, S/Ware, H/Ware,
Legal, Forensic, Police expert
Criminal psychologists
Crime Reporting
Process
New / Existing
Case
Update / Add
Case
Investigation
Social/Legislature
Policies/Regulations
Incident/Case
Network-backup
Storage Archive
Archive Case
Resolved/Pending
Close Case
Assign Case
Crime Database
Verify, Retrieve,
Search
Police National Mainframe,
Criminal files
This phase is concerned with identification of all
parties and actors involved or interested in the
business of the organisation.
Collateral Structuring
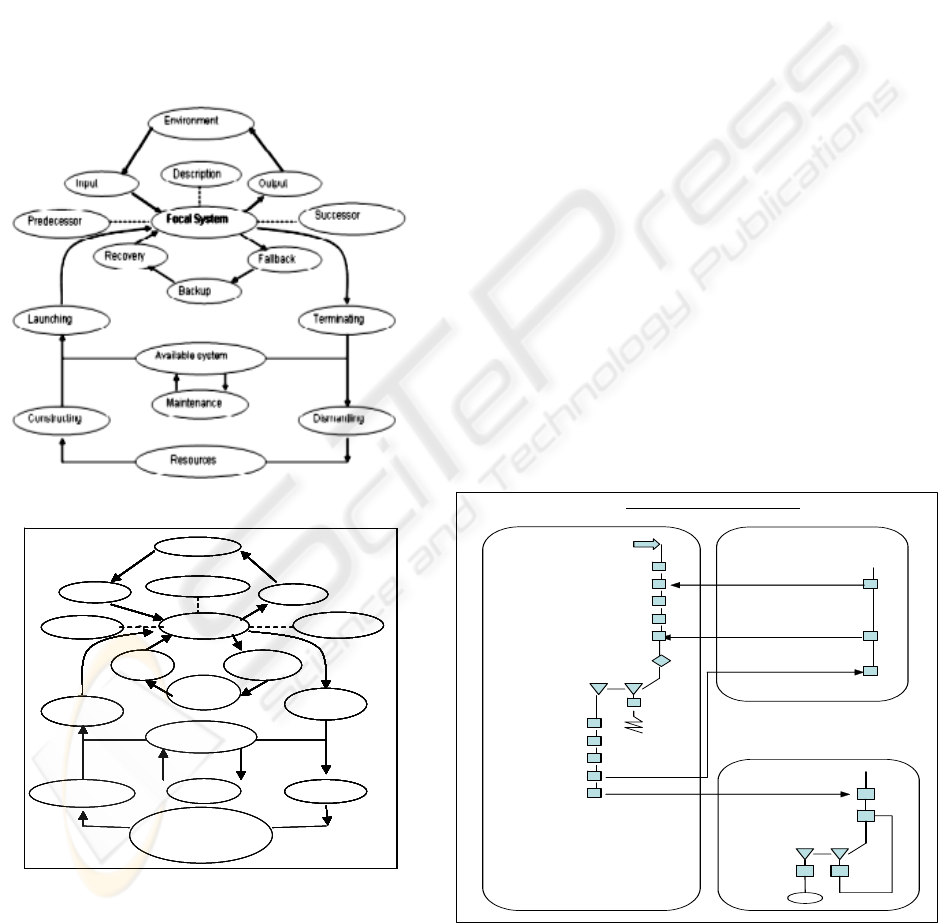
Collateral structuring (Fig. 1) assists in building a
given situation into a number of named unit systems
- a kernel course of action surrounded by activities
which stand beside it. This phase is concerned with
the definition of units that are interrelated and form
an infrastructure for the focal system. In the PITO
crime reporting case study, the crime reporting
system takes to represent the focal system.
Figure 1: Collateral System (Kolkman 1993)
Figure 2: Collateral Structuring – Crime Validation
A focal system addresses the need and solves
problems with a host of supporting processes, in a
given domain (Stamper & Kolkman 1991).
Collateral structuring studies the focal activity; in
this instance the crime validation process and other
related activities (Fig. 2). The collateral units are
systems that surround and support the focal system
needed to establish its logical structure. This
technique is equipped to elicit organisational
semantics and identify inter-relationship between
processes. The semantic analysis to be conducted in
the next phase associates interprets and validates
these ontological dependency relationships.
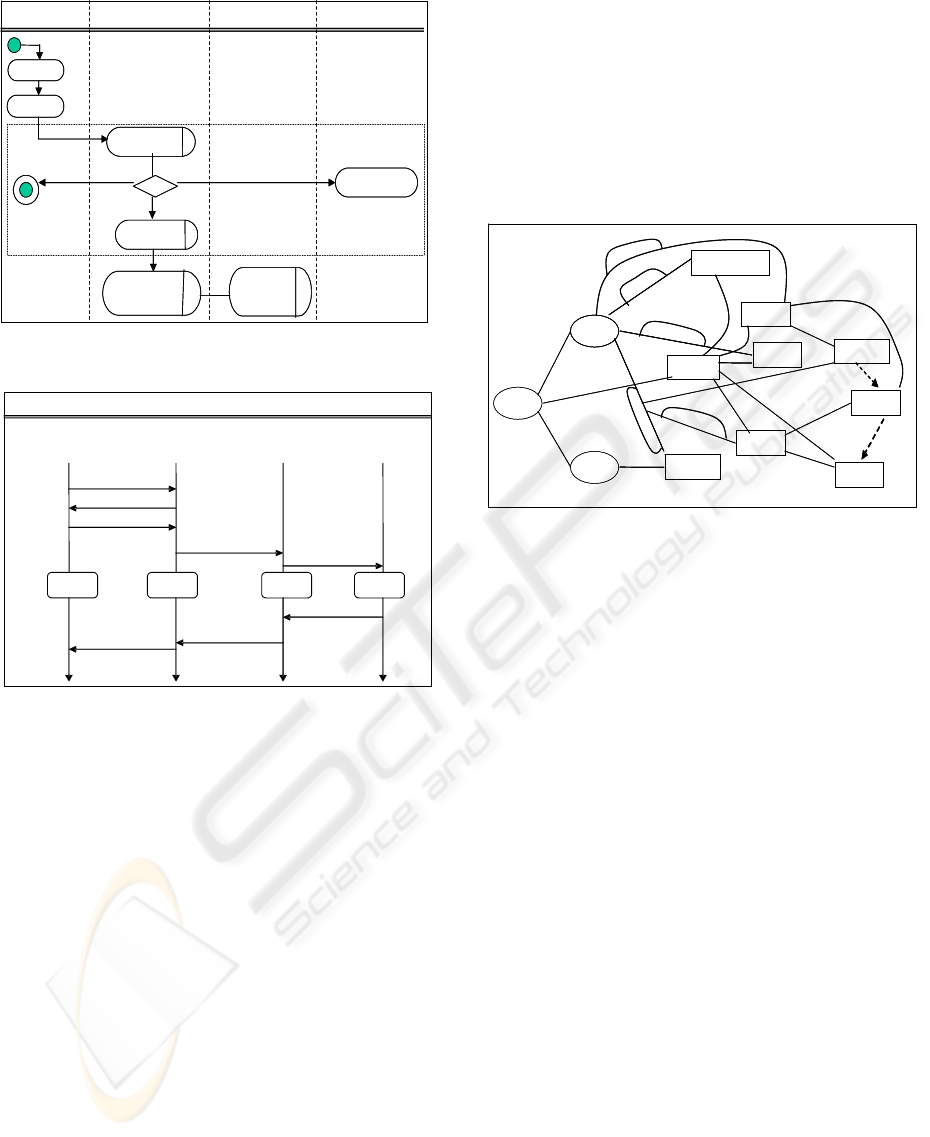
Modelling the Processes
In the crime reporting case study, Role Activity
Diagram (Ould 1995) was used to capture the
overview of the systems outline of crime reporting
department (Fig. 3) Roles have been seen as
effective for modelling the authority, responsibility,
functions, and interactions, associated with agents
within an organisation. However, these are ideal for
an initial mapping, but insufficient to establish
detailed relationships between agents and the targets
they manage. Crime validation activity diagram
(Fig. 4) and scenario diagram (Fig. 5) provide
simplified workflow diagrams; however it is not
equipped to fully reflect the norms, dependency
relations and the agents behaviour which have been
omitted. This has, nevertheless, provided a schema
mapping of inter-processes within the crime
validation process, supported by collateral
structuring. Collateral structuring assists in
identifying the infrastructural and organisational
entities and requirements to initiate systems
intervention and analyse the business processes.
Figure 3: Crime Reporting Process
REQUIREMENTS ENGINEERING FOR ORGANISATIONAL MODELLING
385
Public Domain Crime Reporter Other Departments
Crime
Committed
Contact
Police
Crime Reporter
appraise incident
Department (referral)
Forward
Reject
Take written
statement
Accept
1) Assign to Crime
Recorder
2) Record Crime
Crime Recorder
Accept & record
Crime
[Norm 3]
2
3A
3B
[Norm 2][Norm 1]
1
Select
Public Domain Crime Reporter Other Departments
Crime
Committed
Contact
Police
Crime Reporter
appraise incident
Department (referral)
Forward
Reject
Take written
statement
Accept
1) Assign to Crime
Recorder
2) Record Crime
Crime Recorder
Accept & record
Crime
[Norm 3]
2
3A
3B
[Norm 2][Norm 1]
1
Select
Victim/
Witness
Crime
Reporter
Police
Force Info
Crime
Reporter
Crime - Validation Process
Report Incident
Describe Incident
Waiting Verifying Searching
Statement Report
Furnish incident
Apprise incident
Verifying
policies
Verify no duplication
Assign Reporter
Taking Statement
databse
society
person
police
employs
e
m
p
l
o
y
e
e
record
assign
verify
Subjected to
report
w
i
t
n
e
s
s
cause
V
i
c
t
i
m
@
appraise
@
incident
r
e
c
o
r
d
e
r
s
u
s
p
e
c
t
society
person
police
employs
e
m
p
l
o
y
e
e
record
assign
verify
Subjected to
report
w
i
t
n
e
s
s
cause
V
i
c
t
i
m
@
appraise
@
incident
r
e
c
o
r
d
e
r
s
u
s
p
e
c
t
Figure 4: Activity Diagram – Crime Validation
Figure 5: Scenario Diagram – Crime validation
4 SEMANTIC ANALYSIS
Semantic analysis involves interpreting the meaning
of agents, affordances and its relationships within
the focal system in the organisation, thereby offering
a much richer interpretation than lexical or syntactic
analysis.
Wand (1999) uses entity relations to establish
logical dependencies. This approach was however,
not designed to capture complex organisational
relationships. A technically, logically or
syntactically sound representation, will not
guarantee a correct semantic relationship. Semantic
analysis thus plays a crucial role to identify and
address these problems to establish a semantically
valid system, to determine what they explicitly
mean. This relationship is termed as ontological
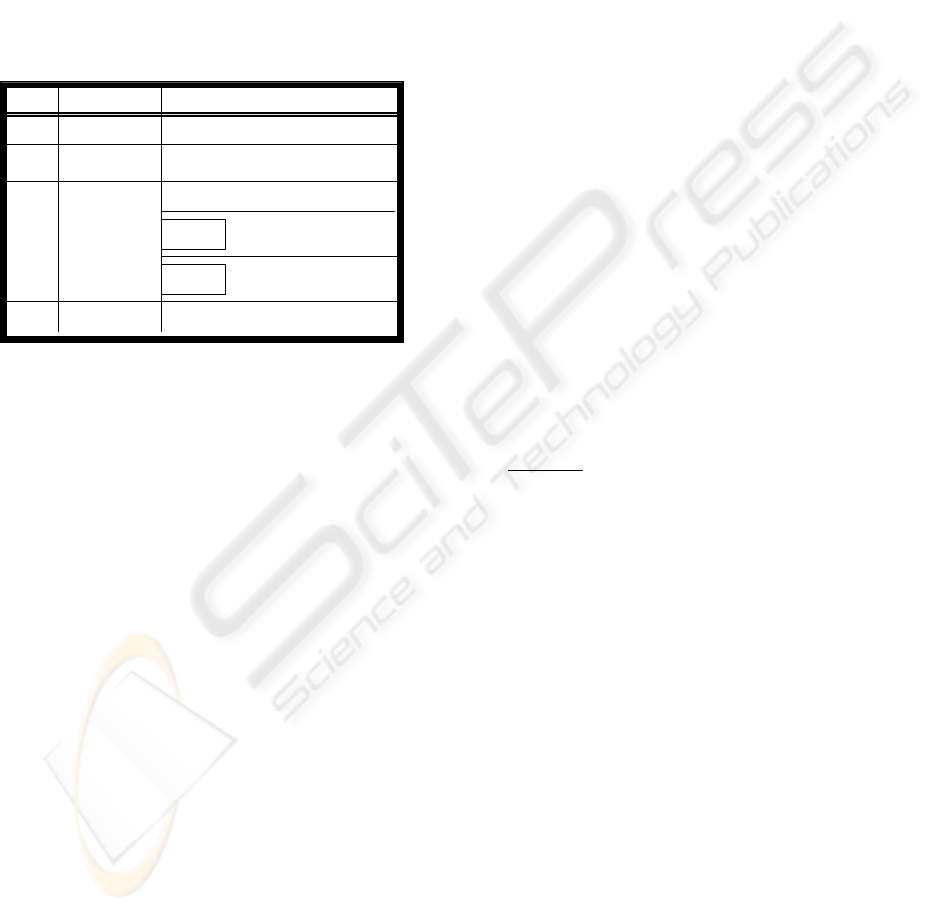
dependency, with the antecedents on the left and the
dependencies on the right. Three key components
need to be present in the ontology-chart (Fig. 6)
namely:
1) An agent is the responsible person or
organisation involved in the focal systems. An agent
is represented with an oval.
2) Affordances are the things involved and the
behaviours afforded by the agent. Affordance is
indicated by a rectangle.
3) Ontological dependencies, represents how
these agents and their behaviours are interrelated
in existence. Role name are represented between
agent and affordance with an arch.
Figure 6. Crime validation ontology-chart
A person (agent) may be classified as a victim
(role name) when he is subjected to an incident
(affordance). A report is generated when an incident
occurs, with information provided by a witness. The
incident in this case is the antecedent, it thus should
be positioned to the left of the report, a dependency,
else the report would cease to exist. The report must
be available before the crime reporter can appraise
the incident. The verification of an incident cannot
take place before appraisal which is indicated by a
dotted-line attached with a “@” standing for
“authority” – a permission for starting the activity of
verifying the crime record. Likewise to assign an
incident to an investigator; it first needs to be
verified before it can acquire the authority to
delegate, the investigation to an investigator. Having
established an ontology chart it will greatly facilitate
the modelling of organisational norms using norm
analysis methods describe in the next section.
5 NORM ANALYSIS
Norms are a set of rules and regulations, an
underlying protocol governing the agent
communications network. Norms revolves around
agents, which influences the agents to execute a
series of concerted actions to achieve a particular
goal. In this respect, it can specify to a limited extent
how an agent should or should not behave, under a
prescribe sets of triggers. They represent procedures,
ICEIS 2004 - INFORMATION SYSTEMS ANALYSIS AND SPECIFICATION
386
Identify responsible agents for the
Start/finish of “an instance”
Select type of key information required
by “an instance”
Pre- The conditions for
conditions acting and invoking norm
post- The resultant after the
conditions successful execution of norm
tasks outcome
Responsibilities
Analysis
Information
Identification
Triggers
Analysis
Norm
Specification
Activities/actions effecting the
Start/finish of “an instance”
Norms specified in the standard construct.
stages
1
2
3
4
constraints and policies on the way an organisation
should conduct its business (Liu & Ong 1999).
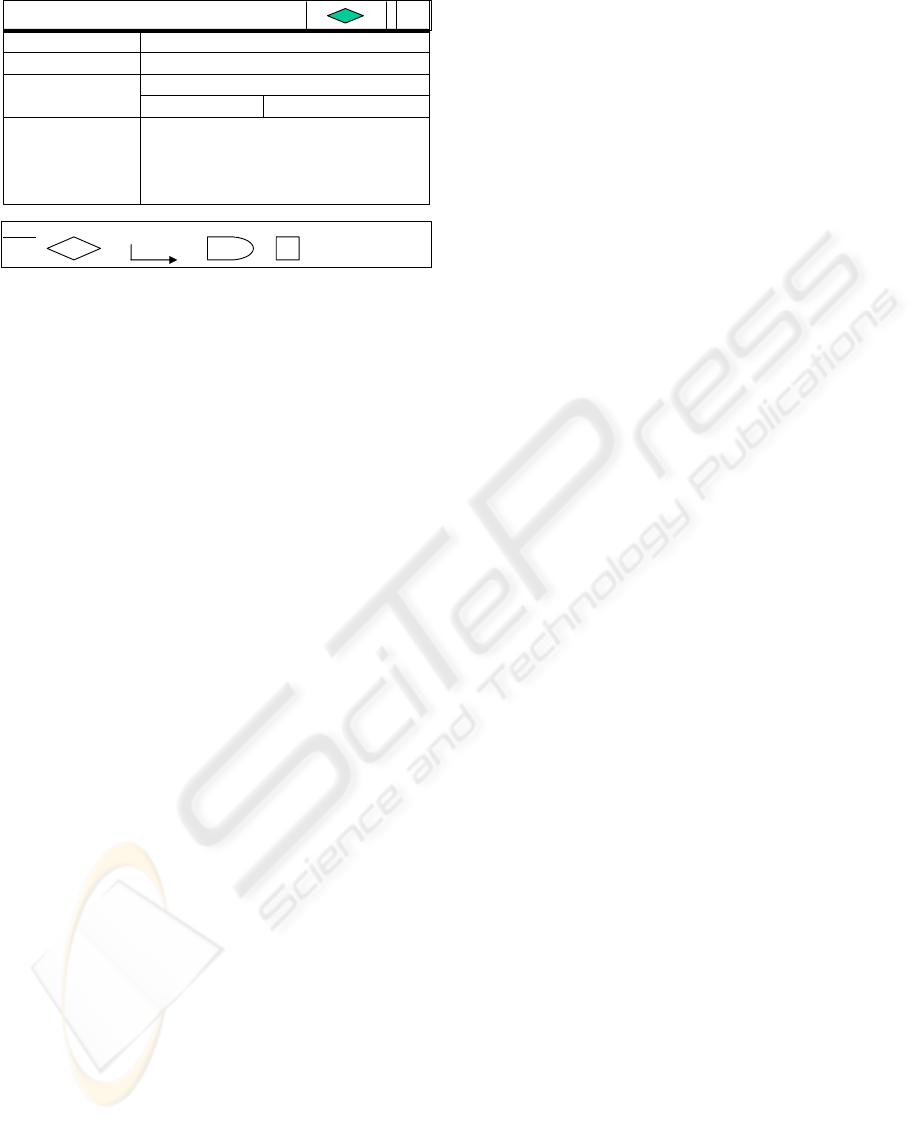
Norm Analysis formulates a systematic approach to
elicited norms, agents behaviour and defines
pre/post conditions of event triggers. The analysis is
carried out in 4 stages to provide each process with a
tabular normative unit of information. The NA table
(Table 2.) is designed to capture a series of norm
“instance”. This modular design enables a clear and
well-defined norm structure, representative of each
characteristics pertaining to a specific norm.
Table 2: The Method of Norm Analysis (Adapted from
Liu 2000 and Liu & Salter 2002)
Norm Analysis formulates an approach to elicit
organisational knowledge. A norm subscribes to the
following construct (Stamper et al. 2000):
Norms Constructs:
whenever <condition>
if <state>
then <agent>
is <deontic operator>
to do<action>
Responsibility Analysis (Stage 1 - Analyse)
Responsibility analysis identifies state association
of entities and agents that are responsible for the
start and finish of “an instance”. The incident starts
immediately from the instance a case number is
issued but not prior to it being classified as a crime.
It is therefore more evocative to link processes,
which are time-bounded and responsibility linked, as
compared to establishing links based exclusively on
process that trigger a subsequent or concurrent
process.
Information Identification (Stage 2 - Identify)
“An instance” needs key source information for
the preceding action. The investigating officer would
need to know information such as, details of the
victims, location/time of crime committed and
description of incident to proceed with the
investigation. These affordance and agents define in
the NA tables, are elicited after semantic analysis,
based on the ontology chart drafted.
Trigger Analysis (Stage 3 - Associate)
Triggers act as a mechanism to activate
associated processes based on the pre-post
conditions of existing social norm define in Stage 1;
it could either take the form of Temporal,
Substantive or Semiological to control or delay the
trigger procedure.
Norm Specification (Stage 4 – Course of Action)
Norm specification is the final stage, where the
earlier 3 stages of information are collated,
decimated, formalised and structured to facilitate
prudent behaviour decisions based on conditional
norm presented. The complexity here is to deal with
formalise norm when instances of violation or
contention occurs.
Norm Analysis information table clearly helps to
state and structure responsible agents, key data, pre-
post triggers and detailed behaviour norms.
An example of possible norms is given below,
after the validation of an incident (Table 3.)
Norm Analysis – Algorithm
[Norm 1] Reject : (Sub-Norm 1.1, 1.2, 1.3..)
[Norm 2] Accept : (Sub-Norm 2.1, 2.2, 2.3..)
[Norm 3] Forward : (Sub-Norm 3.1, 3.2, 3.3..)
[Norm 1]
Sub-Norm - 1.2:
IF the (incident does not constitute to a crime);
a case of customer/consumer disagreement.
THEN Crime Reporter
Is Obliged
To forward it to the consumer
association organisation
Sub-Norm3:…..
Norm Analysis, present an unambiguous detailed
description of the interrelated entities and its
possible behaviour, which is structured on
information modelled from collateral structuring,
high level RAD and Activity diagram.
Norms are used in organisational systems
modelling e.g. by Sergot (2001) and Ivan (2000),
with varying degrees of systems complexities. The
roles and norms are identified to further capture
high-level normative elements. An activity diagram
(Fig. 4) is only sufficed to model at a surface level.
A scenario diagram shows the existence of objects,
their relationships in a logical view, and how they
execute a particular scenario or use case. Norm
analysis offers an extension to capture norms, which
may appear obscure but present.
REQUIREMENTS ENGINEERING FOR ORGANISATIONAL MODELLING
387
Crime Statement : Selection (Accepts)
Responsibility
Info. Identification
Trigger
Detailed Norm
Crime Reporter
Type of crime, category, urgency
Determine Incident
(Conditions Pre/Post)
WHEN a crime is confirmed
IF it is urgent that it will be assign immediately
THEN the officer in contact is to investigate
Valid Crime Statement report
N2
selection process process # N# <norm>
Legend:
Table 3: Norm Analysis (Crime Statement - Accepts)
The results attained are comprehensive in its
procedural logic, which considers entities behaviour,
norms and agents (Table 3). This allows the
flexibility to model the very essences of complex
organisation systems. Equipped with this
information the modeller will have an invaluable
glimpse of a significant insight in the
communication network of the organisation (Tan &
Liu 2003).
6 CONCLUSION
The above case study illustrated the significance of
ontological dependencies, affordances and
normative agents in a business domain. The next
phase of systems study is to define and model
norms, as well as to develop the interoperability of
agents. This approach would structure on
behavioural norms for systems optimisation and
reuse. It is with the aim of bringing requirement
engineering a step closer to realising the above
objective with the advent of tools such as semantic
analysis ‘SAM’ and norm analysis ‘NAM’; more
effort however, needs to be done in the following
areas, (1) Elicitation and abstraction of
organisational norms/patterns for reuses, (2)
Develop the interoperability of agents structured on
norms, (3) Develop a case tool to formulise
organisational norms and (4) Validation of
organisational norms
Equipped with these sets of semiotic tools, we
aim to improve future work and formulise the
current requirement system technique, unifying
systems design with MEASUR methods, with
further enhancement.
Acknowledgement
This research is partly supported by EPSRC –
SEDITA project GR/S04840/01.
REFERENCES
Chong, S. & K. Liu 2000 A Semiotic Approach for
Modelling and Designing Agent-Based Information
Systems Based on Roles and Norms. Proceedings of
AOIS-2000 at CAiSE*00. iCue Publishing, Berlin.
Liu, K, 2000, Semiotics in Information Systems
Engineering, Cambridge University Press, Cambridge
(UK).
Liu, K, A. Alderson, Z. Qureshi, 1999, Requirement
Recovery from Legacy Systems by Analysing and
Modelling Behaviour. International Conference on
Software Maintenance, IEEE Computer Society, Los
Alamitos, pp3-12.
Liu, K. Andy Salter, 2002, Using Semantic Analysis And
Norm Analysis To Model Organisations. Proceedings
of ICEIS 4th International Conference On Enterprise
Information Systems Ciudad Real - Spain. pp. 847-850
Liu, K., R.C. Clarke, P.B. Andersen, R.K. Stamper (2001)
(eds). Preface, Information, Organisation and
Technology: Studies in Organisational Semiotics,
Kluwer, Boston.
Liu, K, Ong Tina, 1999, A Modelling Approach For
Handling Business Rules And Exceptions. The
Computer Journal, Vol 42, No.3. 221-231.
Joaquim, F., K. Liu & B, Sharp, 1999, A Semiotic
Approach to Organisational Role Modelling for
Intelligent Agents, Kluwer Academic Publishers, The
Netherlands. Pp.187-211.
Kolkman, M, 1993, Problem Articulation Methodology,
Febo, Enschede, ISBN 90-9005972-5
Martin Fowler, Ken Scott, 1999, UML Distilled Second
Edition A Brief Guide to the Standard Object
Modelling Language, Addison-Wesley, Reading.
Ould, M.A., 1995, Business Processes, Modelling and
Analysis for Re-engineering and Improvement. John
Wiley & Sons, Chichester.
Peckham, J. & F. Mryanski, 1988, Semantic Data Models,
ACM Computing Surveys 20(3). Vol. 20, Issue 3, pp.
153-189.
Sergot Marek, 2001, A computational theory of normative
position. ACM transaction on computational logic.
Vol. 2, Issue 4, pp. 581-622.
Stamper, R., K. Liu, M. Hafkamp & Y. Ades, 2000,
Understanding the Roles of Signs and Norms in
Organizations, A Semiotic Approach to Information
Design. Journal of Behaviour and Information
Technology. Vol.19, No.1, pp. 15-27.
Stamper, R.K. and M. Kolkman, 1991, Problem
Articulation: A Sharper-edged Soft Systems
Approach, Journal of Applied Systems Analysis
(18)1991, pp.69-76.
Tan, S. Liu, K. 2003, Requirement Engineering for
Organisational modelling. Proceedings of UKAIS
ICEIS 2004 - INFORMATION SYSTEMS ANALYSIS AND SPECIFICATION
388
