
ARGUMENT-BASED APPROACHES IN PRIORITIZED
CONFLICTING SECURITY POLICIES
Salem Benferhat and Rania El Baida
CRIL-Universit´e d’Artois
Rue Jean Souvraz, SP 18, 62307 Lens
Keywords: Organization-based access control, prioritized security policies, handling conflicts, argumentation reasoning.
Abstract: Information security system is an important problem in many domains. Therefore, it is very important to
define security policies to restrict access to pieces of information in order to guarantee security properties,
i.e. confidentiality, integrity and availability requirements. The joint handling of confidentiality, integrity and
availability properties raises the problem of potential conflicts. The objective of this paper is to propose tools,
based on the argumentation reasoning, for handling conflicts in prioritized security policies.
1 INTRODUCTION
Since information systems are more and more fre-
quently used to manage sensitive and critical data, in-
formation security has become a major challenge. In
this paper, we assume that a given information sys-
tem manages both sensitive or critical data and the
objective is to control access to these data in accor-
dance with a security policy. This security policy will
typically specify access control rules to protect data
from unauthorized reading (confidentiality require-
ment) and unauthorized modification (integrity re-
quirement). Another security requirement is to guar-
antee that data are accessible and usable upon demand
by an authorized user (availability requirement). En-
suring the security of an information system comes
down to check that these three requirements are satis-
fied.
Several access control systems have been proposed
(Georgiadiset al., 2001; Sandhu et al., 1996; Wilikens
et al., 2002). This paper deals with an access con-
trol model, called OrBAC (Organization-Based Ac-
cess Control) (Abou El Kalam et al., 2003).
In practice, knowledge bases, specifying security
rules, are sometimes conflicting. For instance, a con-
flict may happen when a security policy defines an
action that a user is permitted to perform and there
exist some exceptional situations where performing
such action is not acceptable.
There have been several proposals for handling con-
flicts in propositional knowledge bases (Dung, 1993;
Benferhat et al., 1995; Besnard and Hunter, 2001;
Brewka, 1989). Some of these approaches, called
”argument-based approaches”, accept inconsistency
and cope with it. They retain all available informa-
tion and suggest to select one or several consistent
subbases which support or reject a conclusion. We
show that contrary to the propositional case, some of
argument-based approaches are not appropriate when
dealing with conflicting first-order knowledge bases.
We illustrate this statement with the safely-supported
approach, and show that it suffers from the so-called
”drowning problem” (formulas outside of conflicts
are not recovered). We propose a solution to handling
conflicts in first order knowledge bases.
The rest of this paper is organized as follows. Section
2 presents basic concepts of OrBAC system. Section
3 gives a prioritized first-order logic framework for-
malization of the OrBAC system. In section 4, two
argumentation-based methods for handling conflicts
in the OrBAC system are investigated.
2 ORGANIZATION-BASED
ACCESS CONTROL (OrBAC)
The main features of OrBAC systems is that privi-
leges are not directly assigned to users, actions and
objects but to their respective abstractions called
roles, activities and views. Moreover, OrBAC allows
to represent security policies that depend on orga-
nizations and contexts. Following subsections give
main concepts of the OrBAC system illustrated by
Figure 1 (for more details see (Abou El Kalam et al.,
2003)).
349
Benferhat S. and El Baida R. (2006).
ARGUMENT-BASED APPROACHES IN PRIORITIZED CONFLICTING SECURITY POLICIES.
In Proceedings of the Eighth International Conference on Enterprise Information Systems - ISAS, pages 349-354
DOI: 10.5220/0002490603490354
Copyright
c
SciTePress

Basic Concepts We distinguish two types of basic
concepts: concrete basic concepts and abstract basic
concepts. The basic concrete concepts are organiza-
tions, subjects, objects and actions. An Organization
can be seen as an organized group of subjects playing
some roles. A Subject is basically a user. The entity
Object covers inactive entities. The entity Action
contains computer actions.
Basic abstract concepts are represented by the entities
Role, View and Activity. The entity Role is associated
with subjects that fulfill same functions. The entity
View corresponds to a set of objects that satisfy
common properties. The entity Activity corresponds
to actions that share same principles.
Roles are organized in hierarchies. For instance,
physicians are staffs, which means that if an organi-
zation employs a user u in a role of physician, then u
is also employed in the role of staff.
Hierarchies between roles can be represented by the
relationship Subrole(org, r
1
, r
2
), which means that
within the organization org, role r
1
is a subrole of
role r
2
. In a similar way, we suppose that views and
activities are organized in form of hierarchies.
Concrete concepts are related to abstract concepts by
using the relationships Employ, Use and Consider.
The relationship Employ(org,s,r) means that the
organization org employs a subject s in a role r.
Similarly, the relationship Use(org,o,v) means that
the organization org uses the object o in a view v,
and the relationship Consider(org, α, a) means that
the organization org considers that action α falls
within the activity a.
Representing Abstracts Privileges and Contexts A
security policy is a set of permissions and prohibitions
rules which are not directly defined on users, objects
and actions but on their abstraction roles, views and
activities. In OrBAC model, they are defined using
the relationships Permission and Prohibition. The re-
lationship P ermission(org, r, a, v, c) means that the
organization org grants to a role r a permission to
perform an activity a on a view v within the context
c. The relationship P rohibition(org, r, a, v, c) is de-
fined similarly.
Contexts are used to specify the circumstances
where organizations grant roles privileges to per-
form activities on views. Contexts are defined
using the relationship ”Define”. The relationship
Define(org, s, α, o, c) means that within the organi-
zation org, context c is true between subject s, object
o and action α.
Concrete Privileges Last concepts in OrBAC con-
cern concrete actions that may be performed by sub-
jects on concrete objects. For this purpose, the
relationships Is-permitted and Is-prohibited are in-
troduced. The relationship Is
−
permitted(s, α, o)
means that the subject s is permitted to perform the
action α on the object o. Is-prohibited is defined in a
similar way. As we will see in the next section, these
relationships are generally logically derived from ab-
stract permissions and prohibitions granted to roles,
views and activities.
3 PRIORITIZED
LOGICAL-BASED ENCODING
OF OrBAC SYSTEM
In this section, we propose a prioritized first-order
logic encoding of OrBAC system. Prioritized first-
order logic are simple extensions of first-order logic,
by associating with each classical first-order formula
a level of priority. More precisely, a set of priori-
tized formulas is a set of weighted formulas having
the form {(φ
i
,a
i
),i=1,n}, where φ
i
is a first-order
formula and, a
i
belongs to ]0, 1]. The degrees a
i
’s
can simply express a preference relation between dif-
ferent formulas of the knowledge base. In this case,
prioritized formulas can be put in a stratified form
represented by Σ=S
1
∪ ···∪S
n
, where each S
i
contains classical first-order logic formulas. S
1
con-
tains the most priority formulas and, S
n
contains the
least ones. And more generally, formulas in S
i
have a
same priority level and are more preferred than those
of S
i+1
.
Prioritized first-order logic is enough for encoding
OrBAC system, since deontic modalities (Permis-
sion and Prohibition) only bear on elementary ac-
tions (there is no disjunction of deontic modalities,
no nested modalities ...).
Given an OrBAC model, given in entity-
relationship format, we can construct its associated
first-order knowledge base as usual. Namely, OrBAC
knowledge bases are built over a language where
the constant symbols correspond to the instances of
the entities of the OrBAC diagram. The constant
symbols and the individual variables (x,y,z...)
can be of types: Organization, Subject, Object,
Action, Role, View, Activity and Context, which
represent the domains of the OrBAC entities. The
function symbols (f(x, y),g(x, y, z),...) are used
for describing the entities attributes. The terms of the
language consist of variables, constants and functions
applied to these variables or constants. The relation
symbols (predicates) correspond to the relationships
of the OrBAC diagram (Figure 1).
We use binary relations to compare the values of the
entities attributes (e.g. =, >, <, etc.).
The following gives more precision on the structure
and stratification of OrBAC knowledge bases.
ICEIS 2006 - INFORMATION SYSTEMS ANALYSIS AND SPECIFICATION
350
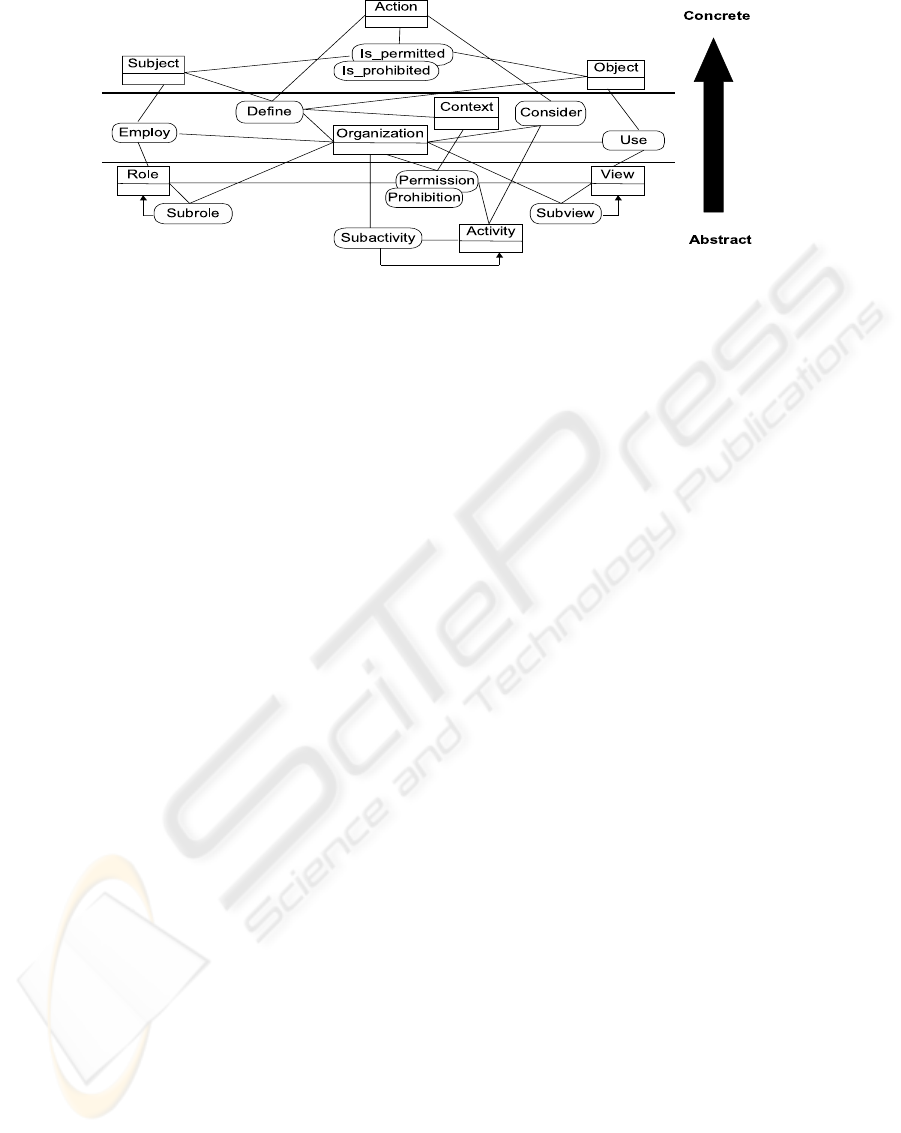
Figure 1: The OrBAC model.
Different Components Of OrBAC
Knowledge Base
OrBAC knowledge base has three components (see
Figure 2). The first one is the set of constraints that
should be absolutely satisfied. The second part is
composed of three parts: set of facts and formulas
associated with the OrBAC relationships, set of facts
and formulas associated with the OrBAC entities
attributes and, set of inheritance rules. The last part
of the knowledge base is the set of rules that allow to
jump from abstract privileges to concrete privileges.
Formulas encoding constraints: We distinguish
two kinds of constraints: constraints relating to the
mutual exclusion and deontic modalities constraints.
The mutual exclusion constraints concern the sep-
aration of roles, views, activities and contexts. An
example of constraints of separation of roles can be:
Within the organization A, a same user should not be
assigned to role “physician” and role “nurse”, which
is modeled by: ∀s, ¬Employ(A, s, physician) ∨
¬Employ(A, s, nurse).
The second kind of constraints relates to the
link between concrete modalities. The following
axiom links concrete permissions Is-permitted
to concrete prohibitions Is-prohibited: ∀s∀α∀o,
¬Is
−
permitted(s, α, o) ∨¬Is
−
prohibited(s, α, o),
which means that a user cannot be permitted and
prohibited to execute the same action on the same
object.
Formulas of OrBAC relationships, entities, inheri-
tance rules: OrBAC relationships are encoded by
first-order predicates. They can be given as facts. For
instance, we can have:
- Employ(A, Mary, secretary).
- Permission(A, staff, write, adm-rec, default).
- Subrole(A, physician, staff).
They can also be provided and completed by first-
order formulas. For instance, a rule of the form
“if one is permitted to write JO’s administration
record then he is permitted to read this object” can be
written as: ∀s, Is
−
permitted(s, write, rec
−
JO) →
Is
−
permitted(s, read, rec
−
JO).
Roles’ hierarchies are described by formulas which
relate on Employ’s relationship: ∀s, r
1
,r
2
,
Employ(org, s, r
1
) ∧ Subrole(org, r
1
,r
2
) →
Employ(org, s, r
2
), means that if a subject s is
employed in the role r
1
, and if r
1
is a subrole of r
2
,
then s is also employed in role r
2
.
Hierarchies between activities and views are defined
in a similar way.
Set of jumping rules: The last part of the OrBAC
knowledge base is a set of rules which allow to jump
from abstract privileges into concrete privileges. This
transformation is given by the following axiom (for
each organization, role, view, activity and context ex-
plicitly stated in the knowledge base):
∀s∀α∀o, P ermission(org, r, a, v, c)∧
Employ(org, s, r) ∧ Use(org, o, v)∧
Consider(org, α, a) ∧ Define(org, s, α, o, c)
→ Is
−
permitted(s, α, o):
If the organization org, within the context c, grants
role r permission to perform activity a on view v, and
if org employs subject s in role r, and if org uses ob-
ject o in the view v, and if org considers that action
α falls within the activity a and if, within the organi-
zation org, the context c is true then s is permitted to
perform α on o.
The transformation from abstract prohibition to con-
crete prohibition is defined in a similar way.
These jumping rules have not the same level of pri-
orities and are stratified, since there are situations in
which they should not be applied.
The stratification of these rules can be given by an
expert or automatically computed. It also depends on
ARGUMENT-BASED APPROACHES IN PRIORITIZED CONFLICTING SECURITY POLICIES
351

Figure 2: The OrBAC Knowledge base component.
conflicts resolution strategies. A strategy of resolu-
tion of conflicts can be for example that rules encod-
ing ”prohibitions” are always preferred to rules en-
coding ”permissions”. However, this is not satisfac-
tory since it can occur that certain specific rules are ig-
nored and never be used. In the OrBAC system, con-
flicts are generally due to exceptions of the privileges
inheritance induced by the hierarchy between roles,
views and activities. In this paper, we propose to
use the algorithm of ”Minimum Specificity Principle”
(MSP) detailed in (Benferhat et al., 1997). The idea
in this algorithm is first to consider that rules with-
out exceptions and facts are always preferred to rules
with exceptions. Then, a rule encoding an exceptional
situation is preferred to a rule encoding a general sit-
uation. A rule is considered as ”exceptional” if letting
its antecedent to be true leads to an inconsistency.
4 ARGUMENT-BASED
APPROACHES FOR HANDLING
CONFLICTS IN OrBAC
SYSTEM
Several approaches have been proposed for handling
conflicts in propositional knowledge bases (Benfer-
hat et al., 1995; Besnard and Hunter, 2001; Brewka,
1989; Dung, 1993). Some of these approaches, called
”argument-based approaches”, accept inconsistency
and cope with it. They retain all available informa-
tion and suggest to select one or several consistent
subbases which support or reject a conclusion.
In this section, we investigate two notions of conse-
quence based on the argument-based reasoning. The
first one provides, for each access control request, a
best argument that supports a permission or a prohibi-
tion of access. The second one distinguishes between
safe and unsafe arguments.
4.1 Argued Consequence
A conclusion can be inferred from an inconsistent
knowledge base if the latter contains an argument that
supports this conclusion with some priority level, but
there is no argument that supports its negation with
a higher or equal level of priority. More formally, the
arguedconsequenceis summarizedby the two follow-
ing definitions:
Definition 1 A subbase A of Σ is said to be an ar-
gument of rank i for a formula φ , if it satisfies the
following conditions:
1. A ⊥ (consistency),
2. A φ (relevance), and
3. ∀ψ ∈ A, A −{ψ} φ (economy).
4. R(A)=max{j : A ∩ S
j
= ∅} = i.
Namely, an argument in favour of a conclusion φ is a
smallest consistent subbase of Σ that infer φ. R(A)
represents the degree of support of φ by A; it corre-
sponds to the rank of the least priority formula in A.
Definition 2 A formula φ is said to be an argued con-
sequence of Σ, denoted by Σ
A
φ if and only if:
1. there exists an argument of rank i for φ in Σ , and
2. all arguments for ¬φ (if any) are of rank j>i.
Example 1 Let us consider an organization ”Hos-
pital A”, where we have one patient (”JO”) and
two staffs: one physician (”Bob”) and one secretary
(”Mary”). Assume that we have one object: JO’s ad-
ministration record. We assume that the security pol-
icy of this organizationis represented by the following
rules:
1. A staff member has a permission to write patients’
administration records.
2. A physician has a prohibition to write patients’ ad-
ministration records.
3. A physician is a staff member.
4. A secretary is a staff member.
ICEIS 2006 - INFORMATION SYSTEMS ANALYSIS AND SPECIFICATION
352

5. Regarding JO’s administration record, if one is
permitted to write this record then he is permitted
to read this record.
Let us suppose that security policy rules lead
to the following prioritized knowledge base
Σ=S
1
∪ S
2
∪ S
3
∪ S
4
, with
S
1
= {R
1
. ∀s, α, o, ¬Is
−
permitted(s, α, o) ∨
¬Is
−
prohibited(s, α, o)};
S
2
= {R
2
.Subrole(A, physician, staff );
R
3
.Subrole(A, secretary, staf f);
R
4
.Employ(A, Bob, physician);
R
5
.Employ(A, Mary, secretary);
R
6
.Consider(A, read, consult);
R
7
.Consider(A, write, write);
R
8
.Use(A, rec
−
JO,adm
−
rec);
R
9
. P ermission(A, staf f, write, adm
−
rec, defa
−
ult);
R
10
.Prohibition(A, physician, write, adm
−
rec,
def ault);
R
11
. ∀s, Is
−
permitted(s, write, rec
−
JO) →
Is
−
permitted(s, read, rec
−
JO);
R
12
. ∀s, Employ(A, s, physician) ∧
Subrole(A, physician, staf f ) →
Employ(A, s, staf f);
R
13
. ∀s, Employ(A, s, secretary) ∧
Subrole(A, secretary, staf f) →
Employ(A, s, staf f);
R
14
. ∀org, s, α, o, Def ine(org, s, α, o, def ault) ↔
};
S
3
= {R
15
. ∀s∀α∀o,
P rohibition(A, physician, write, adm
−
rec, defa
−
ult)∧ Employ(A, s, physician) ∧
Use(A, o, adm
−
rec) ∧ Consider(A, α, write)∧
Define(A, s, α, o, def ault) →
Is
−
prohibited(s, α, o)}.
S
4
= {R
16
. ∀s∀α∀o,
P ermission(A, staf f, write, adm
−
rec, default)∧
Employ(A, s, staf f ) ∧ Use(A, o, adm
−
rec) ∧
Consider(A, α, write) ∧
Define(A, s, α, o, def ault) →
Is
−
permitted(s, α, o)}.
We are interested to know if Bob is permitted to write
JO’s administration record.
We have an argument
B = {R
4
,R
7
,R
8
,R
10
,R
14
,R
15
}, of rank 3 for Is-
prohibited(Bob, write, rec-JO).
There is only one argument
C = {R
2
,R
4
,R
7
,R
8
,R
9
,R
12
,R
14
,R
16
} for
Is-permitted(Bob, write, rec-JO) which is of rank 4.
Therefore, Is-prohibited(Bob, write, rec-JO) is an ar-
gued consequence of Σ.
The following proposition shows that applying
argued-consequence relation on a first-order knowl-
edge base or on its instantiated base is equivalent. We
are restricted to a finite domain, namely to the case
when the instantiated base is finite.
Proposition 1 Let Σ=S
1
∪ ...∪ S
n
be an incon-
sistent first-order knowledge base, and let ψ be an in-
stantiated formula. Let Instantiate(Σ) be the base
obtained by instantiating all first order formulas in Σ
with only constant symbols appearing in Σ (we as-
sume that there exist at least one constant symbol be-
fore instantiating). If Instantiate(Σ) is finite, then
Σ
A
ψ iff Instantiate(Σ)
A
ψ.
4.2 Safely Supported Consequence
The second approach that we investigate, called
”safely supported inference”, can be summarized by
the two following definitions.
Definition 3 A formula (φ, i) is said attacked if there
exists an argument of rank j for ¬φ such that j<i.
A subbase A is a safe argument if φ ∈ A such that φ
is attacked.
Definition 4 A formula ψ is said to be a safely sup-
ported consequence of Σ, denoted by Σ
SS
ψ,iff
there exists in Σ a safe argument for ψ.
The safely supported relation is satisfactory in pro-
postional bases. However, it fails in first-order knowl-
edge bases, since it suffers from the drowning prob-
lem (formulas outside of conflicts are not recovered)
as it is illustrated by the following example.
Example 2 Let us take again example 1.
There exists an argument of rank 4 for
Is-permitted(Mary, read, rec-JO): B =
{R
3
,R
5
,R
7
,R
8
,R
9
,R
11
,R
13
,R
14
,R
16
}. How-
ever, B is not a safe argument. Indeed, the
formula (R
16
, 4) is attacked by the argument
C = {R
4
,R
7
,R
8
,R
10
,R
14
,R
15
} of rank 3.
Hence, Is-permitted(Mary, read, rec-JO) is not a
consequence of Σ.
This limitation is explained by the fact that the for-
mula ”R
16
” is attacked (for instance Bob) and thus,
will be drawn aside by the safely supported relation.
By drawing aside this formula, it cannot be applied
for Mary which leads to the drowning problem.
4.3 Adaptation of Safely Supported
Consequence
The limitation of the safely supported consequence
are explained by the fact that drawing aside a first-
order formulas comes back to drawing aside a set
of propositional formulas (which are not necessarily
tackled). This is not satisfactory because if a formula
ARGUMENT-BASED APPROACHES IN PRIORITIZED CONFLICTING SECURITY POLICIES
353

is responsible for a conflict, then it is not the case that
all its instances are also responsible for the conflict.
We distinguish two ways in which a formula can be
attacked:
• Weakly attacked: if only some instances of this for-
mula are attacked.
• Strongly attacked: if all instances are attacked.
We propose to redefine the safely supported relation
for first-order knowledge bases. The idea is that
a conclusion can be inferred from an inconsistent
knowledge base if the latter contains an argument that
supports this conclusion such that there is no strongly
attacked formula in this argument.
The counterpart of the safely supported inference is
as follows:
Definition 5 A formula (φ(x),i) is weakly attacked
if, there exists an instance x
k
such that, there exists
an argument of rank j for ¬φ(x
k
) such that j<i.
A formula (φ(x),i) is strongly attacked if, ∀x, there
exists an argument of rank j for ¬φ(x) such that j<
i.
Definition 6 A formula ψ is said to be a strongly con-
sequence of Σ, denoted by Σ
S
ψ, iff there exists an
argument A for ψ such that φ ∈ A, φ is weakly at-
tacked.
A formula ψ is said to be a weakly consequence of Σ,
denoted by Σ
W
ψ, iff there exists an argument A
for ψ such that φ ∈ A, φ is strongly attacked.
Example 3 Let us consider example 2. The subbase
B is the only argument for Is-permitted(Mary, read,
rec-JO) of rank 4. However, B contains the formula
R
16
which is weakly attacked by the argument C of
rank 3, for instance (s = Bob, α = read and,
o = rec
−
JO). Hence, Is-permitted(Mary, read, rec-
JO) is not a strongly consequence of Σ, i.e.
Σ
S
Is
−
permitted(Mary, read, rec
−
JO).
B does not contain any strongly attacked formula,
thus Is-permitted(Mary, read, rec-JO) is a weakly
consequence of Σ, i.e.
Σ
W
Is
−
permitted(Mary, read, rec
−
JO).
5 CONCLUSION
This paper proposed to equip the flexible access con-
trol system OrBAC with a conflict resolution module.
Two approaches, based on the argumentation reason-
ing, have been proposed. The argued consequence is
very intuitive. Indeed, it retains all available informa-
tion and suggests to select one or several arguments
which support or reject a permission or a prohibition
of access. However, this method is not entirely sat-
isfactory. Indeed, it can lead to undesirable conclu-
sions. This limitation is explained by the fact that one
argument may for instance contain pieces of informa-
tion which are directly involved in the inconsistency
of the knowledge base. The safely supported conse-
quence only delivers safe conclusions. However, this
method is not appropriate when dealing with incon-
sistent first-order knowledge bases. We showed how
to rephrase the safely supported relation in the frame-
work of first-order logic.
ACKNOWLEDGMENTS
This work is supported by the national ACI project
DESIRS.
REFERENCES
Abou El Kalam, A., El Baida, R., Balbiani, P., Benfer-
hat, S., Cuppens, F., Deswarte, Y., Mi`ege, A., Saurel,
C., and Trouessin, G. (2003). Organization based ac-
cess control. In 4th IEEE International Workshop on
Policies for Distributed Systems and Networks (Pol-
icy’03), pages 120–131. IEEE Computer.
Benferhat, S., Dubois, D., and Prade, H. (1995). How to
infer from inconsistent beliefs without revising? In
IJCAI’95, pages 1449–1455, Montr´eal, Canada. Mor-
gan Kaufmann.
Benferhat, S., Dubois, D., and Prade, H. (1997). Non-
monotonic reasoning, conditional objects and possi-
bility theory. Artificial Intelligence Journal, 92:259–
276.
Besnard, P. and Hunter, A. (2001). A logic-based theory of
deductive arguments. Artificial Intelligence, 128:203–
235.
Brewka, G. (1989). Preferred Subtheories: an extended log-
ical framework for default reasoning. In International
Joint Conference on Artificial Intelligence (IJCAI’89),
pages 1043–1048. Morgan Kaufmann Publishers.
Dung, P. M. (1993). On the acceptability of arguments and
its fundamental role in non-monotonic reasoning and
logic programming. In 13th International Joint Con-
ference on Artificial Intelligence (IJCAI’93), pages
852–857. Morgan Kaufmann Publishers.
Georgiadis, C., Mavridis, I., Pangalos, G., and Thomas, R.
(2001). Flexible Team-Based Access Control Using
Contexts. In 6th ACM Symposium on Access Control
Models and Technologies (SACMAT’01), pages 21–
27. ACM Press.
Sandhu, R., Coyne, E., Feinstein, H., and Youman, C.
(1996). Role-Based Access Control Models. IEEE
Computer, 29(2):38–47.
Wilikens, W., Feriti, S., and Masera, M. (2002). A context-
related authorization access control method based on
RBAC : a case study from the healthcare domain. In
7th ACM Symposium on Access Control Models and
Technologies (SACMAT’02). ACM Press.
ICEIS 2006 - INFORMATION SYSTEMS ANALYSIS AND SPECIFICATION
354
