
MOBILE AGENT SECURITY WITH EFFICIENT OBLIVIOUS
TRANSFER
Wataru Hasegawa, Masakazu Soshi and Atsuko Miyaji
School of Information Science, Japan Advanced Institute of Science and Technology
Keywords:
Mobile Agent, Security, Oblivious Transfer, Encrypted Circuit, Secure Function Evaluation.
Abstract:
Cachin et al. and Algesheimer et al. proposed schemes using secure function evaluation for protecting mobile
agents in untrusted environments. One of essential ingredients of their protocols is oblivious transfer (although
not all of them require it). Unfortunately, naive application of oblivious transfer is inefficient because it must
be performed for each bit of encrypted circuit inputs. Therefore, in this paper we propose secure mobile agent
protocols with emphasis on efficient oblivious transfer suitable for secure function evaluation.
1 INTRODUCTION
Mobile agents are migratable autonomous software
program and mobile agent technology has drawn
much attention as a fundamental technology in
next generation computing (Rothermel and Popescu-
Zeletin, 1997). However, realization of mobile
agents is confronted by a serious security problem:
an attack on mobile agents by malicious execution
hosts such as tampering or eavesdropping agents’
secret during their execution. So the way of ex-
ecuting an ‘encrypted’ agent without decrypting it
has been studied so far. Among such approaches,
Cachin et al. (Cachin et al., 2000) and Algesheimer
et al. (Algesheimer et al., 2001) proposed promising
methods based on secure function evaluation. In par-
ticular, Algesheimer et al. introduced Trusted Third
Party (TTP) to their protocols and succeeded in en-
hancing security of them.
One of essential ingredients of their protocols is
oblivious transfer (although not all of them require
it
1
). Unfortunately, from a viewpoint of communi-
cation cost, naive application of oblivious transfer is
inefficient because it must be performed for each bit
of encrypted circuit inputs. Hence Mori et al. (Mori
1
For example, oblivious transfer is not needed in the ba-
sic scheme by Algesheimer et al. The scheme is discussed
in Section 4.2.
et al., 2005) proposed a mobile agent security scheme
using a new efficient oblivious transfer. However it
turns out that their oblivious transfer protocol is inse-
cure in a special situation (Hasegawa et al., 2007).
In this paper we propose two secure mobile agent
protocols with emphasis on efficient oblivious trans-
fer suitable for secure function evaluation. We show
that one is secure in honest-but-curios model and the
other is secure even in the malicious model. Fur-
thermore, we shall show that our proposed oblivious
transfer protocols are more efficient than a naive ap-
plication of 1-out-of-2 oblivious transfer in mobile
agent security schemes. Besides, our proposed obliv-
ious transfer protocols are interesting in their own
right and they are also important because they can
be building blocks for other security protocols, espe-
cially, more sophisticated type of oblivious transfer,
i.e., Naor’s k-out-of-n oblivious transfer (Naor and
Pinkas, 1999).
2 PRELIMINARY
2.1 Assumptions and Definitions
In this section, we present some preliminaries for our
work. Let G
1
be an additive group of a large prime
order p and G
2
be a multiplicative group of the same
299
Hasegawa W., Soshi M. and Miyaji A. (2007).
MOBILE AGENT SECURITY WITH EFFICIENT OBLIVIOUS TRANSFER.
In Proceedings of the Second International Conference on Security and Cryptography, pages 299-304
DOI: 10.5220/0002129002990304
Copyright
c
SciTePress

order. Let e : G
1
× G
1
→ G
2
be a function that satis-
fies the following properties: (1) Bilinearity: for any
P, Q ∈ G
1
and a, b ∈ Z, e(aP,bQ) = e(P,Q)
ab
; (2)
Non-degeneration: e(P,P) 6= 1 where P is a generator
of G
1
.
Now we give the definition of NT-CDH problem
below.
Assumption 1. New Target Computational Diffie-
Hellman (NT-CDH) Problem
Let P be a generator of G
1
, s
0
,s
1
∈
R
Z
∗
p
,P
0
=
s
0
P,P
1
= s
1
P, b
i
∈ {0,1} for i = 1, 2, ·· ·, n. Fur-
thermore, let T
G
1
(·) be a target oracle that returns
Q
i
∈ G
1
, and
H
1
: {0, 1}
∗
→ G
1
be a cryptographic
hash function. The attacker A is given (p, P
0
, P
1
,
H
1
, s
b
1
Q
1
, ..., s
b
n
Q
n
) and the access to T
G
1
. Then
the advantage Adv
NT−CDH
G
(A) of A in attacking NT-
CDH problem is defined as the probability that A out-
puts s
b
Q
j
/∈ {s
b
1
Q
1
,. .., s
b
n
Q
n
}, where 1 ≤ j ≤ n, and
b ∈ {0,1}. There is no probabilistic polynomial-time
adversary A with non-negligible Adv
NT−CDH
G
(A).
Note that NT-CDH Problem is defined for the first
time in this paper and we believe that it is reasonable
to consider that the problem is computationally diffi-
cult to solve.
Finally, we define the attack model (Algesheimer
et al., 2001; Cachin et al., 2000; Chu and Tzeng,
2005) supposed in this paper.
Definition 1. Attack Model
Attack models for a mobile agent security proto-
col are classified into two types: honest-but-curious
(semi-honest) model and malicious model. Honest-
but-curious hosts follow the protocol, but seek to steal
some useful information about secrets of agents. On
the other hand, malicious hosts can do whatever they
want in order to obtain secret information.
2.2 Oblivious Transfer
One of key tools in security protocols is oblivious
transfer (Naor and Pinkas, 1999), which often means
1-out-of-2 oblivious transfer. A (1-out-of-2) oblivious
transfer is an interactive protocol between a sender
(Alice) with two secret messages m
0
and m
1
and a re-
ceiver (Bob) with a bit b. By oblivious transfer, Bob
gets m
b
, but learns nothing about m
b⊕1
. Furthermore,
Alice does not learn anything about b.
More general form of oblivious transfer, namely,
k-out-of-n oblivious transfer (Chu and Tzeng, 2005;
Naor and Pinkas, 1999) is also useful. As the name
implies, in k-out-of-n oblivious transfer, Alice has n
secrets m
1
,m
2
,. .., m
n
and Bob has k choices i
1
,. .., i
k
.
As we will see later, in mobile agent security
schemes, we basically need to repeat 1-out-of-2 obliv-
ious transfer n times for some n. That is, Alice has
n pairs of secret messages (m
1,0
, m
1,1
), (m
2,0
, m
2,1
),
.. ., (m
n,0
, m
n,1
) and Bob has n choices (1, b
1
), (2,b
2
),
·· ·, (n,b
n
), where b
i
∈ {0,1} (1 ≤ i ≤ n). After com-
pletion of n times 1-out-of-2 oblivious transfer, Bob
receives m
1,b
1
, m
2,b
2
, ··· , m
n,b
n
. Hence an oblivious
transfer scheme for mobile agent security must satisfy
the following three requirements
2
.
Definition 2. Correctness
An scheme is correct if the receiver R (Bob) ob-
tains the chosen messages when both of the sender
S (Alice) and R do not deviate from the steps of the
scheme.
Definition 3. The Receiver’s privacy - indistinguisha-
bility
For any two choice sets of R, say, C = {(1, b
1
),
(2,b
2
), ···, (n,b
n
)} and C
′
= {(1,b
′
1
), (2,b
′
2
), ···,
(n,b
′
n
)}, the transcripts of the protocol execution cor-
responding to C and C
′
, which S sees, are indistin-
guishable. Furthermore, if the received messages of
S for C and C
′
are identically distributed, then the
choices of R are said to be unconditionally secure.
Definition 4. The Sender’s privacy
This property is defined according to the type of
the attack model.
• The Sender’s privacy in the honest-but-curious
model - indistinguishability:
For any choices of R, the unchosen secret mes-
sages of S are indistinguishable from random
ones.
• The Sender’s privacy in the malicious model -
compared with the Ideal Model:
In the Ideal model, first S sends all secret mes-
sages to TTP
3
. Next R sends his choices to TTP
and then TTP sends the chosen secret messages
of S to R. The Ideal model, as its name implies, is
the most secure scheme. We achieve the sender’s
privacy if for any R in the real world, there exists
another probabilistic polynomial-time Turing Ma-
chine (PPTM) R
∗
(called simulator) in the Ideal
model such that the outputs of R and R
∗
are indis-
tinguishable.
2.3 Mobile Agent Computation based
on Secure Function Evaluation
Secure function evaluation (Yao, 1986) is closely re-
lated to the model of mobile agent computation in this
2
The requirements are adopted from (Chu and Tzeng,
2005), but with slight modification.
3
TTP in the Ideal model is a different entity from TTP
involved in secure mobile agent protocols in the following
sections.
SECRYPT 2007 - International Conference on Security and Cryptography
300

paper. This section formalizes the basic idea. For
more details on secure function evaluation, refer to
(Yao, 1986).
In this paper, we suppose that agents travel only
one-hop away and back. That is, an agent which
works on behalf of a user is generated on the site
where the user resides. In particular the site is called
the originator O of the agent. Next the agent moves
to a host H to perform a task on behalf of the user.
Then the agent runs on H and returns to O along with
the result. This is the scenario for one-hop agents,
but it is straightforward to extend it into multi-hop
cases (Algesheimer et al., 2001; Cachin et al., 2000).
Therefore in the subsequent sections, for simplicity
we consider one-hop agents only.
Now we give a formalization of mobile agent
computations based on secure function evaluation.
Suppose that the task that the agent carries out on
behalf of the user is represented by function f :
X ×
Y → Z for some sets X and Y . Furthermore, let x ∈ X
and y ∈ Y be two inputs of O and H into f, respec-
tively. Let n
x
, n
y
, and n
z
be the lengths of x, y, and z,
respectively. Furthermore, (x
1
,. . .,x
n
x
), (y
1
,. . .,y
n
y
),
and (z
1
,. . .,z
n
z
) denote the binary representations of
x, y, and z, respectively. Let C be a polynomial-size
circuit to compute f.
Mobile agent computation proceeds as fol-
lows. First O executes
construct to obtain a tuple
(
C ,K ,L ,U ), where C is an encrypted circuit for C,
and
K , L , and U are “key pairs” for x, y, and z, re-
spectively:
K = ((K
1,0
, K
1,1
), ..., (K
n
x
,0
, K
n
x
,1
)), L =
((L
1,0
, L
1,1
), . . ., (L
n
y
,0
, L
n
y
,1
)), and
U = ((U
1,0
,U
1,1
),
.. ., (U
n
z
,0
,U
n
z
,1
)). Inputs x and y and output z of
C are
represented in an ‘encrypted’ form in terms of
K , L ,
and
U . Namely, x, y, and z are expressed as (K
1,x
1
, ...,
K
n
x
,x
n
x
), (L
1,y
1
, .. ., L
n
y
,y
n
y
), and (U
1,z
1
, .. .,U
n
z
,z
n
z
), re-
spectively.
Next O performs
transfer procedure. That is,
it repeats 1-out-of-2 oblivious transfer with H n
y
times to securely send the encrypted input for y, i.e.,
(L
1,y
1
,. . .,L
n
y
,y
n
y
), to H. Then O also transfers
C and
(K
1,x
1
,. . .,K
n
x
,x
n
x
) to H. Essentially speaking, it can
be considered that the mobile agent consists of
C ,
(K
1,x
1
,. . .,K
n
x
,x
n
x
), and (L
1,y
1
,. . .,L
n
y
,y
n
y
).
Finally the mobile agent runs on H. This
means that
evaluate(C , (K
1,x
1
, . .., K
n
x
,x
n
x
), (L
1,y
1
,
.. ., L
n
y
,y
n
y
)) is executed on H and the output
(U
1,z
1
,. . .,U
n
z
,z
n
z
) is obtained. Then the agent returns
to O along with the output. From this, O can recover
the final result z.
3 OUR SCHEMES
In this section we propose two secure mobile agent
protocols with emphasis on efficient oblivious trans-
fer suitable for secure function evaluation. Actually
in the two protocols, two novel oblivious transfer pro-
tocols, each of which is based on its own security as-
sumption, are devised.
Our model of mobile agent computation is basi-
cally the same as presented in Section 2.3, but with
one additional participant involved, i.e., a trusted third
party (TTP). The reason for the introduction of TTP
in our mobile agent computation is that no secure mo-
bile computing schemes exist without TTP as shown
in (Algesheimer et al., 2001). We call TTP T. In
this paper we suppose that T utilizes a secure pub-
lic key cryptosystem. E
T
and D
T
denote the corre-
sponding encryption and decryption operations, re-
spectively. The symbols in the subsequent sections
follow the definitions given in Section 2.
3.1 Our Scheme 1
In this section we propose a secure mobile agent
scheme in the honest-but-curious model.
Protocol 1
Step 1. 1. O chooses a unique string id for the mobile
computation.
2. O executes
construct(C) and has the output
(
C ,L ,K ,U ).
3. Using encryption with T’s public key, O gen-
erates
¯
L = E
T
(idk1k(L
1,0
,L
1,1
)k2k ... kn
y
k
(L
n
y
,0
,L
n
y
,1
)), where ‘k’ means concatenation
operation.
4. Let K
′
i
be K
i,x
i
for i = 1, 2, .. . , n
x
and x = (x
1
,
x
2
, .. ., x
n
x
).
5. O sends id,
C , K
′
1
, K
′
2
, ..., K
′
n
x
,
¯
L to the host H.
Step 2. H forwards id and
¯
L to T.
Step 3. 1. T decrypts
¯
L with its own private key and
checks whether or not the decrypted message
includes id. If it does not, T quits the proto-
col. Otherwise, if id is used in some previous
computation, then T also aborts.
2. T chooses s
0
,s
1
∈
R
Z
∗
p
and computes s
0
P, s
1
P.
Then it sends s
0
P,s
1
P to H.
3. H chooses a
i
∈
R
Z
∗
p
and compute A
i
=
H
1
(i)
+s
y
i
P +a
i
P (i = 1, 2, ..., n
y
).
4. H sends A
i
to T (i = 1, 2,... , n
y
).
5. For i = 1, 2, ... , n
y
, T calculates D
i,0
= s
0
(A
i
−
s
0
P), D
i,1
= s
1
(A
i
− s
1
P). Next it also chooses
r
i,0
, r
i,1
∈
R
Z
∗
p
and computes C
i,0
= (r
i,0
P,
MOBILE AGENT SECURITY WITH EFFICIENT OBLIVIOUS TRANSFER
301

L
i,0
× e(H
1
(i), s
0
P)
r
i,0
), C
i,1
= (r
i,1
P, L
i,1
×
e(
H
1
(i), s
1
P)
r
i,1
).
6. T sends D
i,0
, D
i,1
, C
i,0
, C
i,1
to H (1 ≤ i ≤ n
y
).
7. H computes D
′
i,y
i
= D
i,y
i
− a
i
s
y
i
P and ob-
tains L
i,y
i
= C
i,y
i
[2]/e(D
′
i,y
i
, C
i,y
i
[1]) = e(
H
1
(i),
s
y
i
P)
r
i,y
i
/ e(D
′
i,y
i
, r
i,y
i
P) (i = 1, 2, ... , n
y
). Here
C
i,y
i
[1] and C
i,y
i
[2] denote the first and the sec-
ond part of the tuple C
i,y
i
respectively.
Step 4. Let L
′
i
be L
i,y
i
(i = 1, 2, . . ., n
y
). H executes
evaluate(C , K
′
1
, K
′
2
, ..., K
′
n
x
, L
′
1
, L
′
2
, ..., L
′
n
y
),
which yields the output U
′
1
, U
′
2
, . .., U
′
n
z
. H sends
them to O.
Step 5. O obtains the final result z = (z
1
, z
2
, ... , z
n
z
)
by comparing U
′
1
, U
′
2
, .. ., U
′
n
z
with
U .
Our protocol 1 is almost the same as (Algesheimer
et al., 2001; Cachin et al., 2000; Mori et al., 2005) ex-
cept for Step 3, which is the large difference between
ours and the previous work.
3.2 Our Scheme 2
In our scheme 1, if H is malicious and sends some
queries A
i
in some special form in Step 3.4, it would
be able to get extra information. Therefore we im-
prove our scheme 1 and propose scheme 2 which is
secure even in the malicious model.
Protocol 2 The difference between Protocol 1 and 2
lies in Step 3. Other steps of Protocol 2 are the same
as those of Protocol 1. Below
H
2
is a cryptographic
hash function over G
1
× {0, 1}
∗
× {0, 1}.
Step 3. 1. T decrypts
¯
L with its own private key and
checks whether or not the decrypted message
includes id. If it does not, T quits the proto-
col. Otherwise, if id is used in some previous
computation, then T also aborts.
2. T chooses s
0
,s
1
∈
R
Z
∗
p
and computes s
0
P, s
1
P.
It then sends s
0
P, s
1
P to H.
3. H chooses a
i
∈
R
Z
∗
p
and computes A
i
=
H
1
(i)
+ s
y
i
P + a
i
P (i = 1, 2, ..., n
y
).
4. H sends A
i
to T (i = 1, 2, . . ., n
y
).
5. For i = 1, 2, . .., n
y
, T computes D
i,0
= s
0
(A
i
− s
0
P), D
i,1
= s
1
(A
i
− s
1
P) and computes
C
i,0
= L
i,0
⊕
H
2
(s
0
H
1
(i), i, 0), C
i,1
= L
i,1
⊕
H
2
(s
1
H
1
(i), i, 1).
6. T sends D
i,0
,D
i,1
,C
i,0
,C
i,1
to H (i = 1, 2, ... ,
n
y
).
7. H obtains L
i,y
i
= C
i,y
i
⊕
H
2
(D
i,y
i
− a
i
(s
y
i
P), i,
y
i
) (i = 1, 2, .. . , n
y
).
The property, security, and efficiency of our pro-
tocol 2 are extensively discussed in Section 4.
4 EVALUATION
4.1 General Discussion on Our
Protocols
Our scheme 1 and 2 are almost the same as
(Algesheimer et al., 2001; Cachin et al., 2000; Mori
et al., 2005). However, each Step 3. of them deviates
far from the previous work. As stated in Section 2, in
the previous mobile agent security schemes we need
to repeat 1-out-of-2 oblivious transfer n
y
times be-
tween Alice and Bob. On the other hand, in this paper
in each Step 3. of our protocol 1 and 2 we have pro-
posed two novel oblivious transfer protocol suitable
for mobile agent security. This is one of the reasons
why our protocols are efficient compared with the pre-
vious work. More detailed analysis on performance is
given in Section 4.4.
Our oblivious transfer protocols modify k-out-of-
n oblivious transfer proposed in (Chu and Tzeng,
2005). Note that we cannot use k-out-of-n oblivious
transfer in mobile agent security schemes in a naive
manner because in k-out-of-n oblivious transfer, it is
possible to choose k indices arbitrarily.
Another important point to note is that in our pro-
tocols T can be less trusted. For example, in the basic
scheme in (Algesheimer et al., 2001), if T and O col-
lude, then the secret y of H is revealed. However, even
in such a case, our two protocols are secure.
4.2 Security Analysis of Scheme 1
In this section we conduct security analysis of our
protocol 1. It is obvious that our protocol 1 is as se-
cure as the original secure function evaluation except
for Step 3. Therefore in order to prove the security
of our protocol 1, what we have to do is only to show
that Step 3. actually satisfies the requirements given
in Section 2.2.
1. Correctness
The proof is omitted because the readers should
easily verify the correctness of the protocol.
2. The Receiver’s privacy
For privacy of the receiver, H, we can prove The-
orem 1:
Theorem 1. For our scheme1, the choices made by
H are unconditionally secure.
The proof is omitted. Theorem 1 can be proved in
a similar way as in (Chu and Tzeng, 2005).
3. The Sender’s privacy
Theorem 2. Our scheme1 meets the Sender’s privacy
requirement. That is, by the DBDH assumption, if
SECRYPT 2007 - International Conference on Security and Cryptography
302

H has honest-but-curious behavior (semi-honest), he
gets no information about unchosen messages.
The proof is also omitted due to space limitation.
It would be straightforward to prove Theorem 2 by
consulting (Chu and Tzeng, 2005).
4.3 Security Analysis of Scheme 2
In this section we consider the security of our protocol
2. As stated in Section 4.2, here we consider the Step
3. of our protocol 2.
1. Correctness
It is easily proved and the proof is omitted.
2. The Receiver’s privacy
We introduce Theorem 3 without proof. It can be
proved almost in the same way as in (Chu and Tzeng,
2005).
Theorem 3. For our scheme2, the choices made by
H are unconditionally secure.
3. The Sender’s privacy
Theorem 4. In the malicious model our scheme2 sat-
isfies The Sender’s privacy under the assumption of
NT-CDH and the random oracle model.
Proof. First remember that
H
2
is considered as a ran-
dom oracle. So in order to query the oracle to ob-
tain
H
2
(s
y
i
H
1
(i), i, y
i
), the malicious H must have
s
y
i
H
1
(i) beforehand. Now given any malicious H, we
construct a simulator H
∗
in the Ideal model, whose
output is indistinguishable from that of H. H
∗
works
in the following way:
Step 1. H
∗
simulates H to obtain its output A
∗
i
(i = 1,
2, .. . , n
y
). If H submits query with index i to
H
1
,
then H
∗
feeds into H a random Q
∗
i
, which should
be consistent with the previous queries.
Step 2. H
∗
simulates T. First it generates s
∗
0
and s
∗
1
.
Then for i = 1, 2, .. ., n
y
, with input A
∗
i
, H
∗
obtains
D
∗
i,0
= s
∗
0
(A
∗
i
− s
∗
0
P) and D
∗
i,1
= s
∗
1
(A
∗
i
− s
∗
1
P).
Step 3. H
∗
outputs (C
∗
i,0
, C
∗
i,1
) at random (i = 1, 2,
.. ., n
y
).
Step 4. H
∗
simulates H with inputs s
∗
0
P, s
∗
1
P, {D
∗
i,0
,
D
∗
i,1
, C
∗
i,0
, C
∗
i,1
} (i = 1, 2, . .., n
y
). If H issues a
query with (x, i, b) to
H
2
(b ∈ {0, 1}), then H
∗
verifies x
?
= s
∗
b
Q
∗
i
. If it holds, then H
∗
obtains L
i,b
from the TTP in the Ideal model and returns C
∗
i,b
⊕ L
i,b
to H as the hash value (consistent with the
previous queries).
Step 5. Outputs s
∗
0
P, s
∗
1
P, {A
∗
i
, D
∗
i,0
, D
∗
i,1
, C
∗
i,0
, C
∗
i,1
}
(i = 1, 2, ..., n
y
).
First note that if for some i, H can obtain both
of decryption keys for the i-th key pair L
i,0
and L
i,1
,
then H
∗
cannot exactly know the indices chosen by H
and the simulation would not succeed. This situation
could arise if H sends to
H
2
two queries (x
0
, i, 0) and
(x
1
, i, 1) such that x
0
= s
∗
0
Q
∗
i
and x
1
= s
∗
1
Q
∗
i
. How-
ever, it contradicts to the assumption of the hardness
of NT-CDH problem and hence the situation above
cannot occur.
For i = 1, 2, . .., n
y
, if (x, i, y
i
) is queried and
legal at the same time, thenC
i,0
andC
i,1
are consistent
with the returned hash values. Since no other (s
∗
b
Q
∗
j
,
j, b) where s
∗
b
Q
∗
j
6∈ {s
∗
y
1
Q
∗
1
, s
∗
y
2
Q
∗
2
, ···, s
∗
y
n
y
Q
∗
n
y
} can
be queried to the
H
2
hash oracle, C
j,0
and C
j,1
have
the right distribution due to the random oracle model.
Thus, the output distribution is indistinguishable from
that of H.
4.4 Performance Evaluation
In this section we compare our schemes with
Cachin’s scheme (Cachin et al., 2000) and Mori’s
scheme (Mori et al., 2005) in terms of communica-
tion cost and the computational complexity
4
. Table 1
and Table 2 depict the communication cost between
sender S and receiver R and the computational com-
plexity of S and R, respectively. Note that in Cachin’s
scheme, S and R correspond to O and H. On the other
hand, in our schemes S and R correspond to T and H.
The communication cost is estimated by the num-
ber of required messages, each of which is in G
1
. For
the computational complexity, first we interpret oper-
ations of the protocol in (Cachin et al., 2000) as those
in G
1
. Then we take into consideration the number
of the most expensive operations, that is, the scalar
multiplication in G
1
and bilinear map (pairing) e over
G
1
× G
1
. Note that for good legibility n
y
is written as
n in Table 1 and 2.
From Table 1 and 2, it should be clear that our
schemes are more efficient than Cachin’s scheme with
respect to the communication cost and the computa-
tional complexity. Furthermore, our schemes are al-
most as efficient as Mori’s scheme, but note that the
latter is insecure. On the other hand, as we showed,
our protocol 1 is secure in the semi-honest model and
our protocol 2 is secure in the malicious model.
4
From the viewpoint of the communication cost and
the computational complexity, (Cachin et al., 2000) and
(Algesheimer et al., 2001) are almost the same. Therefore
due to space constraints here we compare ours with the for-
mer only.
MOBILE AGENT SECURITY WITH EFFICIENT OBLIVIOUS TRANSFER
303
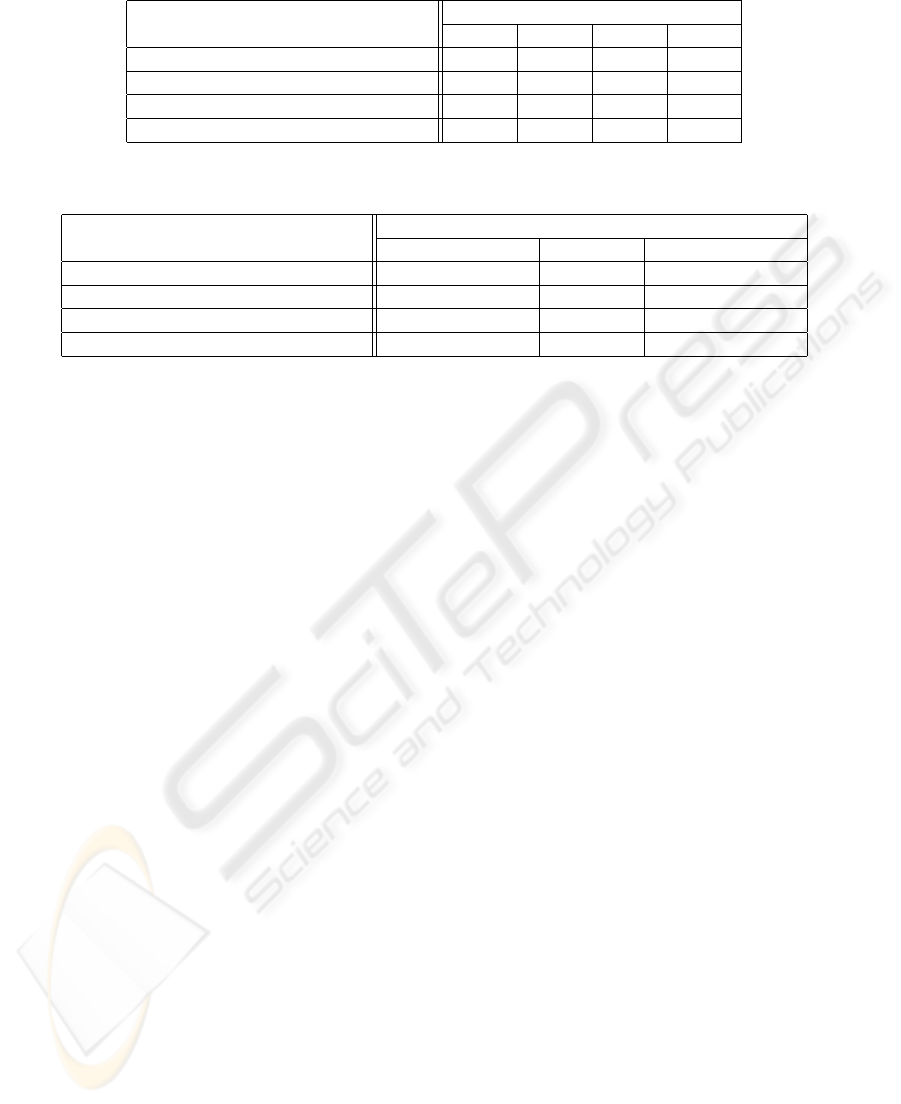
Table 1: Comparison on the communication cost.
Communication cost
S → R R → S S → R Total
C. Cachin, etc. (Cachin et al., 2000) n 2n 4n 7n
Mori, etc. (Mori et al., 2005) n n 3n+ 2 5n+ 2
Our scheme 1 2 n 4n 5n+ 2
Our scheme 2 2 n 4n 5n+ 2
Table 2: Comparison on the computational complexity.
Computational complexity
S R Total
C. Cachin, etc. (Cachin et al., 2000) 5nM 2nM 7nM
Mori, etc. (Mori et al., 2005) 4n+ 2M 2nM (6n+ 2)M
Our scheme 1 (4n+ 2)M + 2nE 2nM + nE (6n+ 2)M + 3nE
Our scheme 2 (4n+ 2)M 2nM (6n+ 2)M
M: one scalar multiplication, E: one paring
5 CONCLUSION
In this paper we proposed two secure mobile agent
protocols with emphasis on efficient oblivious trans-
fer suitable for secure function evaluation in untrusted
environments. Actually in the two protocols, two
novel oblivious transfer protocols were devised. We
showed that one is secure in honest-but-curios model
and the other is secure even in the malicious model.
Furthermore, we showed that our proposed oblivious
transfer protocols are more efficient than the previous
work.
ACKNOWLEDGEMENTS
We would like to thank anonymous referees for their
valuable comments.
REFERENCES
Algesheimer, J., Cachin, C., Camenisch, J., and Karjoth, G.
(2001). Cryptographic security for mobile code. In
Proc. IEEE Symp. Security and Privacy, pages 2–11.
Cachin, C., Camenisch, J., Kilian, J., and M
¨
uller, J.
(2000). One-round secure computation and secure au-
tonomous mobile agents. In Proc. ICALP, vol. 1853
of LNCS, pages 512–523. Springer-Verlag.
Chu, C.-K. and Tzeng, W.-G. (2005). Efficient k-out-of-
n oblivious transfer schemes with adaptive and non-
adaptive queries. In PKC 2005, vol. 3386 of LNCS,
pages 172–183. Springer-Verlag.
Hasegawa, W., Soshi, M., and Miyaji, A. (2007). Effi-
cient communication on mobile agent security. In
Symposium on Cryptography and Information Secu-
rity (SCIS2007), 4F1-5.
Mori, M., Soshi, M., and Miyaji, A. (2005). Consideration
for mobile agent security. IPSJ SIG Technical Reports
2005-CSEC-28. pp. 123–128.
Naor, M. and Pinkas, B. (1999). Oblivious transfer and
polynomial evaluation. In Proc. STOC ’99, pages
245–254.
Rothermel, K. and Popescu-Zeletin, R., editors (1997). Mo-
bile Agents: First International Workshop (MA ’97),
vol. 1219 of LNCS. Springer-Verlag.
Yao, A. C. (1986). How to generate and exchange secrets.
In Proc. FOCS, pages 162–167.
SECRYPT 2007 - International Conference on Security and Cryptography
304
