
PRACTICAL AND UNIVERSAL INTERPRETATION FUNCTIONS
FOR SECRECY
Hanane Houmani and Mohamed Mejri
LSFM Research Group, Computer Science Department
Laval University, Quebec, Canada
Keywords:
Cryptographic protocols, Secrecy, Formal verification, Sufficient conditions.
Abstract:
Using the notion of interpretation functions, this paper gives some sufficient and practical conditions allowing
to guarantee the correctness of a security protocol with respect to the secrecy property. An interpretation
function is a safe means by which an agent can estimate the security level of message components that he
receives so that he can handle them correctly. An example of an universal interpretation function is given in
this paper together with how to use it to analyse a cryptographic protocol.
1 INTRODUCTION
The verification of security of cryptographic proto-
cols is paramount, since they are used to make se-
cure our communications and transactions. The prob-
lem of the security verification of cryptographic pro-
tocols is undecidable in general (see (Cervesato et al.,
1999; Even and Goldreich, 1983; Heintze and Tygar,
1996)). To deal with this problem, researchers pro-
posed a large variety of methods and tools. A general
survey could be found in (Boreale and Gorla, 2002;
Comon and Shmatikov, 2002; Meadows, 2003).
Theses approaches can be classified in two
classes. The first one contains decidable methods
where some of them could be find in (Comon-Lundh
and Cortier, 2003a; Gangon and Mejri, 2006; Lowe,
1998; Ramanujam and Suresh, 2003; Stoller, 1999).
Using these methods, one can decide whether some
protocols are correct or not. This is due to the fact
that these methods make strong restrictions on the an-
alyzed protocols in order to make the analysis decid-
able. The second class contains semi-decidable meth-
ods and some of them could be found in (Abadi, 1999;
Blanchet and Podelski, 2003; Burrows et al., 1990;
Comon-Lundh and Cortier, 2003b; Durgin et al.,
2001; Houmani and Mejri, 2003; Mao and Boyd,
1993; Paulson, 1997). Some of these approaches aim
to prove that a given protocol respects some secu-
rity properties and others try to detect flaws on them.
However, in both cases, if the goal isn’t reached, the
security of the analyzed protocol cannot be guaran-
teed.
The major drawback of decidable and semi-
decidable approaches allowing to guarantee the se-
crecy property of a protocol is their strong restrictive
assumptions and any new less restrictive approach is
more than welcome.
The main result of this paper is to propose some
conditions that are not very restrictive but sufficient
to guarantee the correctness of any protocol satisfy-
ing them with respect to the secrecy property. Be-
sides, the results presented in this paper are generic
enough to deal with the verification of a large variety
of protocols in different contexts (different intruder
capabilities or different syntax of messages).
Intuitively, to guarantee that a protocol is correct
with respect to the secrecy property using our ap-
proach, one need to find an interpretation function
and to prove that each role (agent) involved in the pro-
tocol does not decrease the security level of compo-
nent of messages when he sends them over the net-
work. Protocols that satisfy this condition will be
called increasing protocol.
An interpretation function could be seen as a
means that can be used by agents involved in a pro-
tocol to estimate, in a safe way, the security level
of unknown components that they receive during the
protocol. If the security level of components handled
157
Houmani H. and Mejri M. (2007).
PRACTICAL AND UNIVERSAL INTERPRETATION FUNCTIONS FOR SECRECY.
In Proceedings of the Second International Conference on Security and Cryptography, pages 157-164
DOI: 10.5220/0002129101570164
Copyright
c
SciTePress

by each agent are known or could be estimated in
a safe way, then the verification of the protocol will
be considerably simplified. In fact, it will be enough
to check whether the agents protect in an appropriate
way the messages that they send over the network to
guarantee the secrecy property of the protocol.
The remainder of this paper is organized as fol-
lows. Section 2 formalizes some parameters that af-
fect the verification of protocols are called the context
of verification and clarifies the protocol specification
and the notion of generalized roles. Section 3 gives
a formal definition of the secrecy property based on
valid traces. Section 5 introduces the proposed condi-
tions and provides a proof that are sufficient to ensure
the secrecy property of a protocol. Section 6 presents
a guideline to define a safe interpretation function.
Section 7 gives an example showing how to verify the
secrecy property of a given protocol by using an inter-
pretation function. Section 8 discusses the approach
and compares it with some existing ones. Finally, sec-
tion 9 provides a few concluding remarks and future
works.
2 MODELING PROTOCOL
This section introduces the notions verification con-
text and role-based specification of a protocol.
2.1 Context of Verification
Intuitively, a verification context is a structure that
contains all the parameters that affect the verification
of a protocol. Basically, we find in this structure the
intruder capabilities, the knowledge of each princi-
pal and the security level of each atomic component.
More precisely, a verification context, denoted by M,
is a quintuple h
M , |=, K , L ,
p
.
q
i , where :
•
M is the message algebra. It describes the class of
messages involved in the analyzed protocol. No-
tice that we use
A to denote the set of atomic mes-
sages in
M and A (M) to denote the set of atomic
messages in a given set of messages M.
• |= is the intruder capabilities. It is a set of infer-
ence rules showing how the intruder can infer new
messages.
•
K is the sets of messages (fresh and non-fresh
messages) that are initially known by each agent
including the intruder. More precisely,
K is a
set of triples (A, fr(A),
fr(A)), where A is the
name of the agent, f r(A) is a set of fresh mes-
sages known by A and fr(A) is the set of non-
fresh messages known by A. Notice that if M =
h
M , |=, K , L ,
p
.
q
i is a model, then we denote
by K
A
the set of messages ( fresh and non fresh)
known by A in M.
• (
L , ⊒) or simply L is a security lattice. It is used
to describe the security levels of components in-
volved in the protocol together with an ordering
relation between them.
•
p
.
q
is a function from
A to L . It specifies the secu-
rity level of components that are initially known
by principals including the intruder. If A is a set
of atomic messages and α is an atomic compo-
nent, we say
p
M
q
⊒
p
α
q
if it exists β in M such
that
p
β
q
⊒
p
α
q
Example 2.1 In the sequel, we denote by M
0
, the fol-
lowing verification model:
•
M
0
is the message algebra given by the the fol-
lowing BNF grammar.
m ::= A (Principal Identifier)
| N
a
(Nonce)
| k
ab
(Shared key)
| X (Variable)
| {m}
k
ab
(Encrypted Message)
| m, m
′
(Concatenated Message)
In the sequel, we denote by
I
M
the set of identi-
fiers in
M .
• |=
0
the following commun intruder rules:
(init)
M |= m
[m ∈ M]
(decrypt)
M |= k M |= {m}
k
M |= m
(encrypt)
M |= k M |= m
M |= {m}
k
(concat)
M |= m
1
M |= m
2
M |= m
1
.m
2
(deconcat)
M |= m
1
.m
2
M |= m
i
[i = 1, 2]
where M |= m means that the intruder can infer m
from M using the previous rules.
•
K
0
= {(A, fr(A),
fr(A)), (B, fr(B), fr(B)),
(S, fr(S),
fr(S)), (I, f r(I), fr(I))}, where :
fr(A) = {k
ab
}
fr(B) = {N
b
}
fr(S) =
/
0
fr(I) = {N
1
i
, N
2
i
, . . .}
fr(A) = {k
as
, A, B, S}
fr(B) = {k
bs
, A, B, S}
fr(S) = {k
bs
, k
as
, A, B, S}
fr(S) = {k
is
, A, B, S}
SECRYPT 2007 - International Conference on Security and Cryptography
158
• L
0
= (2
I
M
, ⊇).
•
p
·
q
0
. The security type of an atomic message in-
volved in the protocol is the set of principals that
are allowed to know this message.
p
·
q
0
= [N
b
, N
1
i
, N
2
i
, . . . 7→ ⊥, A, B, S 7→ ⊥,
k
ab
7→ {A, B, S}, k
is
7→ {I, S}
k
as
7→ {A, S}, k
bs
7→ {B, S}]
2.2 Protocol
Basically, a protocol P is specified by a sequence
of communication steps given in the standard nota-
tion. Hereafter, we give an example which is a vari-
ant extracted from the Woo and Lam (Woo and Lam,
1994) authentication protocol. As shown by Table 1,
this variant aims to distribute a fresh key that will be
shared between two agents A and B.
Table 1: Woo and Lam modified protocol.
P = h1, A → B : Ai.
h2, B → A : N
b
i.
h3, A → B : {N
b
, k
ab
}
k
as
i.
h4, B → S : {A, {N
b
, k
ab
}
k
as
}
k
bs
i.
h5, S → B : {N
b
, k
ab
}
K
bs
i
From a verification context M and a protocol P,
we extract a role-based specification (a set of gen-
eralized roles) that we denote by R
G
(P). A gener-
alized role is a protocol abstraction, where the em-
phasis is put on a particular principal and where all
the unknown messages are replaced by variables. An
exponent i (the session identifier) to each fresh mes-
sage to reflect the fact that these components change
their values from one run to another is added. Ba-
sically, a generalized role reflects how a particu-
lar agent perceives the exchanged messages. More
details about generalized roles and how they ex-
tracted from a protocol could be find in (Houmani and
Mejri, 2003). For instance, the role-based specifica-
tion of the protocol described in Table 1,
R
G
(P), is
{
A
1
G
,
A
2
G
,
B
1
G
,
B
2
G
,
B
3
G
,
S
1
G
} (see Table 2).
The role-based specification is used to formalize
the notion of valid trace. A trace is considered as valid
if all honest participants act according to the protocol
specification and all the messages sent by the intruder
are derivable from his intercepted messages, his ini-
tial knowledge and his inference rules given within
the verification context. It is considered that an hon-
est agent acts according to the protocol specification
if any given run in which he participates is an instance
Table 2: Generalized roles of Woo and Lam protocol.
A
1
G
= hi.1, A → I(B) : Ai
A
2
G
= hi.1, A → I(B) : Ai.
hi.2, I(B) → A : Xi.
hi.3, A → I(B) : {X, k
i
ab
}
k
as
i
B
1
G
= hi.1, I(A) → B : Ai.
hi.2, B → I(A) : N
b
i
B
2
G
= hi.1, I(A) → B : Ai.
hi.2, B → I(A) : N
b
i.
hi.3, I(A) → B : Y
1
i.
hi.4, B → I(S) : {A, Y
1
}
k
bs
i
B
3
G
= hi.1, I(A) → B : Ai.
hi.2, B → I(A) : N
b
i.
hi.3, I(A) → B : Y
2
i.
hi.4, B → I(S) : {A, Y
2
}
k
bs
i.
hi.5, I(S) → B : {N
i
b
, Z}
k
bs
i
S
1
G
= hi.4, I(B) → S : {A, {U, V}
k
as
}
k
bs
i.
hi.5, S → I(B) : {U, V}
k
bs
i
(variables are replaced by constant messages) of one
of his generalized roles. The notation [[P ]] means
the set of the valid traces associated to the protocol P.
Also, [[ P ]] |=
K
I
α means that the protocol P exhibits
a trace allowing an intruder, having an initial knowl-
edge K
I
and using the inference rules defined by |= ,
modeled by |=
K
I
, to know the message α. To verify
the secrecy property, this paper proves that it is suf-
ficient to verify whether the generalized roles of the
analyzed protocol respect some conditions. This ver-
ification is decidable, because the set of generalized
roles of a protocol is finite.
3 SECRECY PROPERTY
Intuitively, a protocol keeps a component m secret, if
it has not a valid trace that decrease the security level
of m. More precisely, the formal definition of the se-
crecy property given hereafter states that the intruder
cannot learn from any valid trace more than what he
is eligible to know. We suppose that if an agent (in-
cluding the intruder) knows a message with a security
PRACTICAL AND UNIVERSAL INTERPRETATION FUNCTIONS FOR SECRECY
159

level τ, then he is also eligible to know all messages
having security level lower than τ
1
.
Definition 3.1 (Secrecy Property) Let P be a proto-
col and M = h
M , |=, K , L ,
p
.
q
i a verification con-
text. The protocol P is M-correct with respect the se-
crecy property, if:
∀α ∈
A (M ) · [[ p ]] |=
K
I
α ⇒
p
K
I
q
⊒
p
α
q
4 SAFE INTERPRETATION
FUNCTION
The aim of safe interpretation functions is to give a
correct means to the principals involved in the proto-
col by which they can estimate the security level of
the received components.
Definition 4.1 (Interpretation function) Let M =
h
M , |=, K , L ,
p
.
q
i be a verification context. An M-
Interpretation function F is function from
A (M )×M
to L .
Before introducing the notion of safe interpreta-
tion functions, we need to define the following order-
ing relation.
Definition 4.2 (⊒
F
) Let F be an M-Interpretation
function. We say that M
1
⊒
F
M
2
if:
∀α ∈
A (M
1
) · F(α, M
1
) ⊒ F(α, M
2
)
For the sake of simplicity, {m} ⊒
F
M is replaced by
m ⊒
F
M, and F(α, {m}) is replaced by F(α, m).
Now a safe interpretation function could be de-
fined as following:
Definition 4.3 (Safe Interpretation Function)
Let M = h
M , |=, K , L ,
p
.
q
i. An M-Interpretation
function is called M-Safe if the following conditions
are respected:
1. F is well formed, i.e:
F(α, {α}) = ⊥ and F(α, M
1
∪ M
2
) = F(α, M
1
) ⊓
F(α, M
2
) and F(α, M) = ⊤ where α 6∈
A (M)
2. F is full-invariant by substitution, i.e: for all
M
1
and M
2
two set of messages in M such that
Var(M
1
) ⊆ Var(M
2
) and M
1
⊒
F
M
2
we have:
∀σ ∈ Γ· M
1
σ ⊒
F
M
2
σ
where Γ is the set of possible substitution form X
to close messages in M .
3. F is full-invariant by intruder, i.e:
∀M ⊆ M , ∀α ∈ A (M) such that F(α, M) ⊒
p
α
q
and ∀m ∈
M such that M |=
K
I
m we have:
∀α ∈
A (m) · (F(α, m) ⊒ F(α, M) ∨ (
p
K
q
I
⊒
p
α
q
)
1
Notice that it is always possible to define a security lat-
tice that reflects our needs and which is coherent with this
hypothesis.
5 MAIN RESULT
Now, it is time to give the sufficient conditions al-
lowing to guarantee the correctness of a protocol with
respect to the secrecy property. Informally, these con-
ditions state that (a) honest agents should never de-
crease the security level of any atomic message and
(b) they have to use a safe interpretation function to
estimate the security level of component that they
didn’t initially know. To formalize the condition (a),
we introduce the following definition.
Definition 5.1 (Increasing Protocol)
Let M be a verification context, F an M-interpretation
function and P a protocol. The protocol P is said to
be F-increasing if:
∀r ∈
R
G
(P), ∀α ∈
A (r
+
)· F(α, r
+
) ⊒
p
α
q
⊓F(α, r
−
)
where r
+
is a set containing the messages sent during
the last step of r and r
−
contains the set of messages
received by the honest agent in r.
Now the main theorem could be formalized as fol-
lowing:
Theorem 5.2 Let P be a protocol, M a verification
context and F a M-interpretation function . If F is M-
safe and P is F-increasing, then P is M-correct with
respect to the secrecy property.
Proof:
Due to the lake of space, proofs have been removed
and can be found in (Houmani and Mejri, 2007a).
6 GUIDELINES TO DEFINE SAFE
INTERPRETATION
FUNCTIONS
According to theorem 5.2, the first step of the ver-
ification of secrecy property is to find a safe inter-
pretation function and this is the delicate part of the
approach. In fact, an interpretation function needs to
be full-invariant by substitution and full-invariant by
intruder. For that reason, this section provides some
guidelines allowing to easily construct a safe interpre-
tation function.
Basically, we show hereafter that any interpreta-
tion function that has some given form is safe. In
particular, we focus on interpretation functions hav-
ing the following form:
F(α, M) = I ◦ S(α, M)
where S is a function that selects from M some
atomic components having some links with α and
SECRYPT 2007 - International Conference on Security and Cryptography
160
where I is a function that interprets what S returns as
a security type.
If we consider a message, which is a term in the
message algebra, as a tree and we attach to each arc
of this tree an integer value (reflecting costs or dis-
tance between nodes), then it will be easy to define S
that select some components that are at some distance
from a given component. To formalize the the notion
of distance, we introduce a function
T that takes a
message and attach a value to each arc in its corre-
sponding tree. An example of
T is as following:
T ((c, α)) = 0
T ((c, e)) = ∞
T ((e, c)) = 0
T ((e, α)) = 1
where e is the encryption operator, c is the con-
catenation operator and α is an atomic message. If we
apply this function to the message ”B, {N
b
, k
ab
}
k
as
”,
we obtain
T (”B, {N
b
, k
ab
}
k
as
”) given by Fig. 1.
@
@
@
@
@
@
@
@
@
B
c
0 ∞
e
0 1
00
N
b
k
ab
k
as
c
Figure 1: T (”B, {N
b
, k
ab
}
k
as
”).
In the rest of this paper, d
T (m)
(α, β) (or simply
d
m
(α, β) if
T (m) is clear from the context) denotes
the smallest distance between α and β in
T (m). This
notion can be easily extended to a set of messages M
as follows: d
M
(α, β) = Min
m∈M
(d
m
(α, β))
Now, we introduce the n-selection function S
n
T
as
following:
S
n
T
(α, M) =
A if α appears in clear in M
{β ∈
A (M) | d
T (M)
(α, β) = n} else
The definition of S
n
T
is extended to S
−→
n
T
, called the n-
vector selection function, as following:
S
−→
n
T
(α, M) = (S
0
T
(α, M), S
1
T
(α, M), . . . , S
n
T
(α, M))
This n-vector selection function will play a key role
in the definition of a safe interpretation function.
Any n-vector selection function S
−→
n
T
from
A × 2
M
to ((2
A
)
n
, ⊆) can be proved full-invariant by substi-
tution, where ⊆ is extended to deal with vectors as
follows:
(M
1
, M
2
, . . . , M
n
) ⊆ (M
′
1
, M
′
2
, . . . , M
′
n
) ⇔
∀i ∈ {1, . . . , n} · M
i
⊆
i
∪
j=1
M
′
j
This full-invariance of n-vector selection function is a
useful property to help us to construct an interpreta-
tion function that is full-invariant by substitution.
Now, some restrictions on
T are needed so that
S
−→
n
T
will be also full-invariant by intruder manipula-
tion. A simple and practical condition that T needs to
satisfy so that S
−→
n
T
becomes full-invariant by intruder
is given by definition 6.1.
Definition 6.1 (Safe Cost Attribution (SCA)) We
say that
T is an SCA if T (o, e) = ∞, where where e
is an encryption operator and o is any another node.
Having a selection function that is full-invariant
by substitution and full-invariant by intruder is not
enough to construct a safe function F = I ◦ S that is
also full-invariant by substitution and full-invariant by
intruder. The function I needs also to be restricted so
that it can preserves the full-invariance properties of
S. For instance, the selection function S
n
T
returns a
vector of sets of atomic components that will be inter-
preted by I as a security type. These atomic compo-
nents could contain variables and therefore the func-
tion I needs to carefully handle them so that the ”full-
invariance” properties of S
n
T
are preserved.
Before giving how to choose I, we need to intro-
ducing the following notations: Given a security lat-
tice (
L , ⊒), we introduce the two following useful ex-
tensions.
• (
L
X
, ⊒
X
): where
X is a set of variables that range
over security types,
L
X
=
L ∪ X and the relation
⊒
X
is defined as follows:
τ
1
⊒
X
τ
2
⇔ ∀σ ∈
X × L : τ
1
σ ⊒ τ
2
σ
• (
L
n
X
, ⊒
n
X
) is an extension of (
L
X
, ⊒
X
) as follow-
ing:
–
L
n
X
=
L
X
× . . . ×
L
X
|
{z }
n
– ⊒
n
X
is defined as follows:
(τ
1
, . . . , τ
n
) ⊒
n
X
(τ
′
1
, . . . , τ
′
n
) ⇔
∀i ∈ {1, . . . , n} · τ
i
⊒
X
i
⊓
j=1
τ
′
j
The following theorem shows the condition that
need to be respected by I so that we get a safe inter-
pretation function.
Theorem 6.2 Let M be a context of verification and
S
−→
n
T
an n-vector selection function. If:
PRACTICAL AND UNIVERSAL INTERPRETATION FUNCTIONS FOR SECRECY
161

• T be a SCA, and
• I is a morphism from ((2
A
)
n
, ⊆) to (
L
n
X
, ⊒
n
X
)
Then, F = I ◦ S
−→
n
T
is M-safe.
Proof:
Due to the lake of space, proofs have been removed
and can be found in (Houmani and Mejri, 2007b).
Practical steps to construct F: To define a safe in-
terpretation function F, one can follow these steps:
1. Define a n-vector selection function S
−→
n
T
. To do
this, we should define the following elements:
• Choose a positive integer value for n.
• Choose
T such that it is an SCA.
2. Define a morphism I from ((2
A
)
n
, ⊆) to (
L
n
X
, ⊒
n
X
). Given a security lattice (
L , ⊒), a morphism can
be built simply by following these steps:
• Define mapping I from A to L .
• Extend the mapping I to deal with variable as
following:
I(x) = x if x is a variable
where x is a variable that ranges over secu-
rity types. This extension is done to appropri-
ately deal with variables that could be returned
by S
n
T
.
• Extend I to be able to handle sets a another as
following:
I(A
1
∪ A
2
) = I(A
1
) ⊓ I(A
2
)
• Extend the function I to be able to deal with
vectors as following:
I((A
1
, . . . , A
n
)) = (I(A
1
), . . . , I(A
n
))
3. Define an M-safe function F as:
F = I ◦ S
−→
n
T
6.1 Example
In this example, we define an M
0
-safe function, de-
noted by F
0
, where M
0
is the verification context de-
scribed in section 2.1. To that end we proceed accord-
ing to the previous steps:
1. Define a n-vector selection function S
−→
n
T
:
• Choose a value for n: In this example, we
choose n = 0.
@
@
@
@
@
@
@
@
@
@
@
@
c
e
0
0 0
c a
c a
0
0
a e
0 ∞
c
e
a e
∞
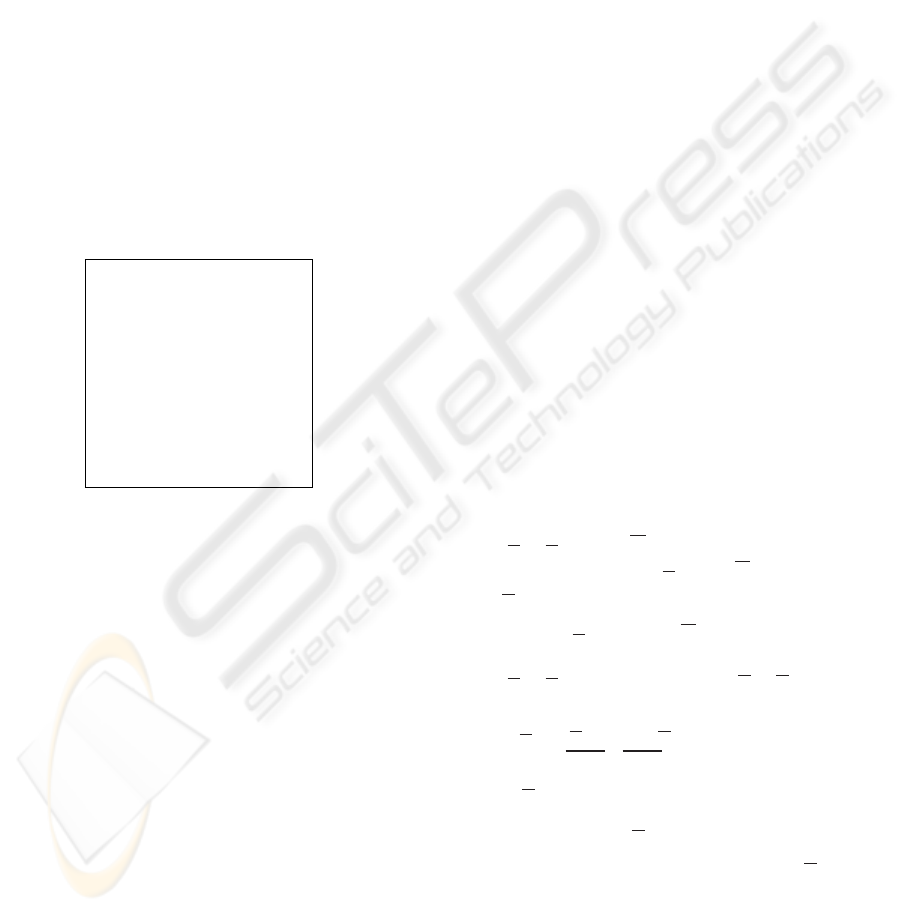
Figure 2: Example of costs.
• Define an SCA
T : In this example, T attaches
values to arcs as shown by Fig. 2, where a is an
atomic message. Intuitively, T allow S
−→
n
T
(α, M)
to select the innermost keys that encrypt α in M
together with the atomic components that are
concatenated to α in M (called direct neigh-
bors).
2. Define a morphism I
X
from (2
A
, ⊆) to (2
I
X
, ⊆
X
).
In this example, let I be the mapping defined as
follows I
(
A) = A and I(α
ab
) = {A, B}. After that
we can extend this mapping with following steps
described previously to the mapping I that is from
(2
A
, ⊆) to (2
I
X
, ⊆
X
).
3. The interpretation function is now as following:
F
0
= I ◦ S
−→
0
T
For instance:
F
0
(α, {{α, B, X}
k
as
}
k
bs
) = I({B, X, k
as
})
= {A, S, B, } ∪
X
This function is called
DEKAN (Direct Encrypting
Keys and Neighbors). We believe that such a
DEKAN function is powerful enough to allow us
to appropriately analyze a large class of protocols
with respect to the secrecy property.
7 CASES STUDY
By using the DEKAN safe interpretation function F
0
and the theorem 5.2, one can prove that P (the version
of Woo and Lam protocol given by Table 1) is M
0
-
correct with respect to the secrecy property. To this
end, we need only to prove that the protocol is F
0
-
increasing, i.e., for each generalized role r in Table 2,
we have:
∀α ∈
A (r
+
) · F
0
(α, r
+
) ⊆
X
p
α
q
∪ F
0
(α, r
−
)
SECRYPT 2007 - International Conference on Security and Cryptography
162

For the role A
1
G
, since
p
A
q
= ⊥ and F is well-defined
(F(A, A) = ⊥), then the role
A
1
G
is F-increasing:
F
0
(A, A) ⊆
X
p
A
q
∪ F
0
(A, A)
For the role
A
2
G
, since F
0
(k
i
ab
, {{X, k
i
ab
}
k
as
}) =
{A, S} ∪
X, F
0
(X, {{X, k
i
ab
}
k
as
}) = {A, B, S} ,
p
k
i
ab
q
=
{A, B, S},
p
X
q
= ⊤ and F is well-defined (F
0
(X, X) =
⊥, F
0
(k
i
ab
, X) = ⊤), then the role A
2
G
is not F-
increasing. Indeed, we have:
F
0
(k
i
ab
, {{X, k
i
ab
}
k
as
}) 6⊆
X
p
k
i
ab
q
∪ F
0
(k
i
ab
, X)
F
0
(X, {{X, k
i
ab
}
k
as
}) ⊆
X
p
X
q
∪ F
0
(X, X)
For the role
B
1
G
, since
p
N
i
b
q
= ⊥ and F is well-
defined (F
0
(N
i
b
, N
i
b
) = ⊥, F
0
(N
i
b
, A) = ⊤), then the
role
B
1
G
is F-increasing. Indeed, we have:
F
0
(N
i
b
, N
i
b
) ⊆
X
p
N
i
b
q
∪ F
0
(N
i
b
, A)
For the role
B
2
G
, since F
0
(Y
1
, {{A, Y
1
}
k
bs
}) =
{A, B, S}, F
0
(A, {{A, Y
1
}
k
bs
}) = {B, S} ∪
Y
1
,
p
A
q
= ⊥,
p
Y
1
q
= ⊤ and F is well-defined (F
0
(Y
1
, {Y
1
, A}) =
⊥, F
0
(A, {Y
1
, A}) = ⊥), then the role
B
2
G
is F-
increasing. Indeed, we have:
F
0
(Y
1
, {{A, Y
1
}
k
bs
}) ⊆
X
p
Y
1
q
∪ F
0
(Y
1
, {Y
1
, A})
F
0
(A, {{A, Y
1
}
k
bs
}) ⊆
X
p
A
q
∪ F
0
(A, {Y
1
, A})
For the role
S
1
G
, since F
0
(U, {U, V}
k
bs
) =
{B, S} ∪
V, F
0
(V, {U, V}
k
bs
) = {B, S} ∪ U,
F
0
(U, {A, {U, V}
k
as
}
k
bs
) = {A, S} ∪ V,
F
0
(V, {A, {U, V}
k
as
}
k
bs
) = {A, S} ∪ U and
p
U
q
=
p
V
q
= ⊤, then the role
S
1
G
is not F-increasing.
Indeed, we have:
F
0
(U, {U, V}
k
bs
) 6⊆
X
p
U
q
∪ F
0
(U, {A, {U, V}
k
as
}
k
bs
)
F
0
(V, {U, V}
k
bs
) 6⊆
X
p
V
q
∪ F
0
(V, {A, {U, V}
k
as
}
k
bs
)
Therefore, this protocol is not an F
0
-increasing
and we can not ensure its correctness with respect
to the secrecy property. Moreover, it is not difficult
to see that this protocol contains a flaw and therefore
we will never be able to construct a a safe interpreta-
tion function that makes it an increasing one. What is
interesting however, is that the previous verifications
help as to localize the origin of the problem which
are in steps 3 and 5. For instance in step 3, the mes-
sage k
i
ab
is sent with security level equal to {A, S} ∪
X
which is not in its security level specified in the proto-
col {A, B, S} for all the possible values of X (a similar
problem appears in step 5). To resolve this problem
and prove the correctness by using F
0
as interpreta-
tion function, we need to modify the protocol. One
possible way of modifying this protocol is as shown
by Table 3).
We can now prove that this new version is F
0
-
increasing.
Table 3: Woo and Lam modified protocol: Second version.
P = h1, A → B : Ai.
h2, B → A : N
b
i.
h3, A → B : {{N
b
}
A
, B, k
ab
}
k
as
i.
h4, B → S : {A, {{N
b
}
A
, B, k
ab
}
k
as
}
k
bs
i.
h5, S → B : {{N
b
}
A
, A, k
ab
}
k
bs
}
k
bs
i
8 DISCUSSION
The approach proposed in this paper shares some
characteristics with others existing works like the se-
crecy by typing technique proposed in (Abadi, 1999)
and rank functions proposed in (Schneider, 1998;
Delicata and Schneider, 2005).
With the secrecy by typing technique, we share
the idea of having some secure way allowing to prop-
agate the security level of exchanged information dur-
ing a protocol so that they can be correctly han-
dled by the receivers. To this end, the secrecy by
typing approach uses standard forms of messages
({secret, any, public, confounder}
k
) so that it will
be easy to deduce its ”secret”, ”public” and ”any”
(component with unknown security level) parts. This
involves that this approach can only ensure the secu-
rity of protocols that exchange messages having the
standard format. With our approach, however, the se-
curity level of any component can be inferred in a safe
way by using what we called interpretation function.
It is possible for us to define an interpretation func-
tion, when the message have the standard form giv-
ing a safe way to know the security level of its com-
ponents (like the one used in the secrecy by typing
approach), but also it still possible to define an inter-
pretation function even such kind of standard are not
respected by the protocol. This gives to our approach
the ability of certifying the security of a larger class
of protocols.
With the rank functions techniques, we share the
idea of using inductive proofs and the use of a func-
tion that allows to know whether a message is ap-
propriately protected or not. However, interpretation
functions are more precise than rank functions. This
is due to fact that rank functions are global functions
that ensure if a message is globally constructed in a
secure way. However, interpretation functions are lo-
cal functions than allows to know whether each com-
ponent of messages are convenably protected or not.
Therefore, the interpretation functions give more help
to detect problems in a protocol, and how to modify it
so that its security could be guaranteed. In fact, when
PRACTICAL AND UNIVERSAL INTERPRETATION FUNCTIONS FOR SECRECY
163

they fail to ensure the security of a protocol they give
the exact components that could be inappropriately
protected. We believe also that interpretation func-
tions are more helping during the conception of new
protocols and could give some guidelines.
9 CONCLUSION
By using the notion of safe interpretation functions,
this paper gives sufficient conditions to guarantee the
correctness of a cryptographic protocol with respect
to the the secrecy property. These conditions could be
verified in a linear time on the protocol. It gives also a
practical way to construct these kind of interpretation
functions.
As future works, we want to show the efficiency of
this approach by verifying real life protocols such as
SSL, SET, Kerberos, etc. We would like also to define
other safe and universal interpretation functions. Fi-
nally, it will be interesting to see wether this approach
could help in order analyze others security proper-
ties.
REFERENCES
Abadi, M. (1999). Secrecy by typing in security protocols.
Journal of the ACM, 46(5):749–786.
Blanchet, B. and Podelski, A. (2003). Verification of cryp-
tographic protocols: Tagging enforces termination. In
Foundations of Software Science and Computational
Structures, volume 2620 / 2003, pages 136–152, War-
saw, Poland. Springer-Verlag Heidelberg.
Boreale, M. and Gorla, D. (2002). Process calculi
and the verification of security properties. Journal
of Telecommunication and Information Technology—
Special Issue on Cryptographic Protocol Verification,
(4/02):28–40.
Burrows, M., Abadi, M., and Needham, R. (1990). Re-
joinder to Nessett. ACM Operating Systems Review,
24(2):39–40.
Cervesato, I., Durgin, N. A., Lincoln, P., Mitchell, J. C.,
and Scedrov, A. (1999). A meta-notation for protocol
analysis. In CSFW, pages 55–69.
Comon, H. and Shmatikov, V. (2002). Is it possible to de-
cide whether a cryptographic protocol is secure or not.
Journal of Telecommunications and Information Tech-
nolog,.
Comon-Lundh, H. and Cortier, V. (2003a). New decidabil-
ity results for fragments of first-order logic and ap-
plication to cryptographic protocols. In RTA, pages
148–164.
Comon-Lundh, H. and Cortier, V. (2003b). Security prop-
erties: Two agents are sufficient. In ESOP, pages 99–
113.
Delicata, R. and Schneider, S. (2005). Temporal rank func-
tions for forward secrecy. In CSFW ’05: Proceed-
ings of the 18th IEEE Computer Security Foundations
Workshop (CSFW’05), pages 126–139, Washington,
DC, USA. IEEE Computer Society.
Durgin, N., Mitchell, J., and Pavlovic, D. (2001). A com-
positional logic for protocol correctness.
Even, S. and Goldreich, O. (1983). On the security of multi-
party ping-pong protocols. In IEEE Symposium on
Foundations of Computer Science, pages 34–39.
Gangon, F. and Mejri, M. (2006). A decision procedure for
structured cryptographic protocols. In New Trends in
Software Methodologies, Tools and Techniques, pages
272–286. IOS Press.
Heintze, N. and Tygar, J. D. (1996). A model for secure pro-
tocols and their compositions. Software Engineering,
22(1):16–30.
Houmani, H. and Mejri, M. (2003). Secure protocols for se-
crecy. In Foundations of Computer Security Afiliated
with LICS’03, pages 85–96, Ottawa, Canada.
Houmani, H. and Mejri, M. (2007a). Secrecy by in-
terpretation functions. Knowledge-Based Systems,
doi:10.1016/j.knosys.2007.05.003.
Houmani, H. and Mejri, M. (2007b). Secrecy by interpreta-
tion functions: Extended version. Thechnical Report,
www.ift.ulaval.ca\
˜
hahou\techReport1.pdf
.
Lowe, G. (1998). Towards a Completeness Result for
Model Checking of Security Protocols. In Proceed-
ings of 11th IEEE Computer Security Foundations
Workshop, pages 96–108.
Mao, W. and Boyd, C. (1993). Towards the Formal Analy-
sis of Security Protocols. In Proceedings of the Com-
puter Security Foundations Workshop VI, pages 147–
158. IEEE Computer Society Press.
Meadows, C. (2003). What makes a cryptographic protocol
secure? the evolution of requirements specification in
formal cryptographic protocol analysis. In Proceed-
ings of ESOP 03. Springer-Verlag.
Paulson, L. C. (1997). Proving properties of security pro-
tocols by induction. In 10th Computer Security Foun-
dations Workshop, pages 70–83. IEEE Computer So-
ciety Press.
Ramanujam, R. and Suresh, S. (2003). Tagging makes
secrecy decidable with unbounded nonces as well.
In Lecture Notes in Computer Science, volume
2914/2003. FST TCS 2003: Foundations of Software
Technology and Theoretical Computer Science, Pub-
lisher Springer Berlin / Heidelberg.
Schneider, S. (1998). Verifying authentication protocols in
csp. IEEE Trans. Softw. Eng., 24(9):741–758.
Stoller, S. D. (1999). Lower and upper bounds for attacks on
authentication protocols. In Symposium on Principles
of Distributed Computing, page 283.
Woo, T. Y. C. and Lam, S. S. (1994). A Lesson on Authen-
tication Protocol Design. Operating Systems Review,
pages 24–37.
SECRYPT 2007 - International Conference on Security and Cryptography
164
