
INCENTIVE-BASED AND PEER-ORIENTED DESIGN OF
UBIQUITOUS COMMERCE
Kyoung Jun Lee and Jeong-In Ju
School of Business, Kyung Hee University, Hoegi-dong, Dongdaemun-gu, Seoul, Korea
Keywords: Ubiquitous Commerce, Seamlessness, Privacy, Business Model, Peer-Oriented, PIB(Personal Information
Base).
Abstract: Seamlessness is the keyword of U-Commerce which may be defined as the commercial interaction among
providers, consumers, products, and services, enabled and supported especially by the real-world seamless
communication of each entity and object's digital information. However, the possibility of the seamless
transactions increases the privacy risk of the entities involved. Therefore, the core issue of U-Commerce is
how to promote seamless transactions while protecting the privacy. For the seamlessness, the role of
incentive-emphasized business model is important since the seamlessness makes clear which economic
entities contribute to a commercial transaction. Economic entities will reject the seamless transactions
unless the sufficient incentives are given to them. In order to consider the privacy issue, we suggest an
alternative U-Commerce architecture based on Hybrid P2P Model and Personal Information Base.
1 INTRODUCTION
U-Commerce research has been recently being done
by ubiquitous computing and e-commerce
researchers. According to Watson et al. (2002), U-
commerce is defined as the use of ubiquitous
networks to support personalized and uninterrupted
communications and transactions between a firm
and its various stakeholders to provide a level of
value over, above, and beyond traditional commerce.
Roussos & Moussouri (2004) defines U-commerce
as any transaction with a monetary value that is
conducted using ubiquitous computing technology.
We define U-Commerce as the commercial
interaction among providers, consumers, products,
and services, enabled and supported especially by
(the real-world) seamless communication of each
entity's (digital) information. The seamless
communication is supported by the combination of
automatic identification technologies (e.g. RFID),
(wireless) communication technologies (e.g.
bluetooth), positioning services (e.g. GPS), and
sensor network technologies (e.g. Smart Dust).
Seamlessness and the subsequent integration of
virtual digital space and physical space are the
fundamentally distinctive feature of U-Commerce in
comparison to the traditional commerce. The term
Seamlessness refers to the continuous and
uninterrupted information flow of products, services,
spaces and economic entities in commercial
transaction process. Seamlessness of U-Commerce
is made possible by embeddly digital information in
every object. Such embedded digital information
saves end users the cost to transfer analog
information into digital one (e.g. typing) allowing
the applicable information to flow seamlessly. In
turn such uninterrupted exchange of information
makes physical and virtual digital space integrated
meaning that all information in physical space
commerce activities is exchanged without any
interruption and pause as it is in virtual digital space
thereby eliminating the gap between the two
different spaces. To understand such integration,
Brock(2001) in MIT Auto-ID Center carried out
Physical Markup Language (PML) study.
This highly functional U-Commerce
environment reduces transaction costs, improves the
quality of exchanged information and heightens the
transparency of transaction to name a few. However,
the new environment has dark side and negative
potentials as well. Such an uninterrupted flow of
information has possibility to infringe on
individual’s privacy depending on how and where
the information is used and stored. It’s because the
continuity of information can be interpreted as
624
Jun Lee K. and Ju J. (2007).
INCENTIVE-BASED AND PEER-ORIENTED DESIGN OF UBIQUITOUS COMMERCE.
In Proceedings of the Ninth International Conference on Enterprise Information Systems - ISAS, pages 624-631
DOI: 10.5220/0002396806240631
Copyright
c
SciTePress
easiness in collecting information by certain entity.
Furthermore, the systematic storage of data enabled
by U-Commerce environment can worsen privacy
impairment if misused and/or abused. Considering
this, it’s safe to say that seamless storage of
information might be trade-off to privacy protection.
To figure out the secret of such relations, Acquisti
(2002) implemented a study that proved trade-off
between incentives to share information and the ones
to hide information.
Therefore U-Commerce technology should find
the point where these two purposes can be
harmonized in between and help each economic
players not to leave away from U-Commerce by
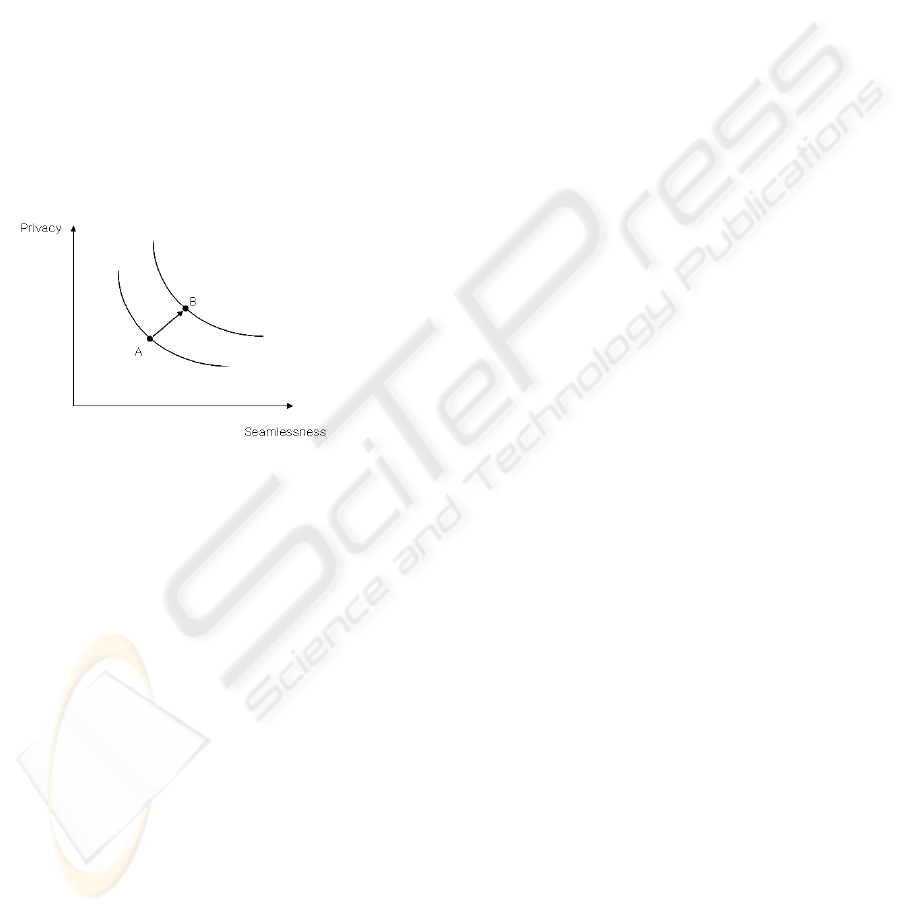
ensuring all incentives go to the right people. Figure
1 below shows the relationship between privacy and
seamlessness and the need to discover ways to shift
from point A to B where both privacy protection and
seamlessness can be improved together (Fig. 1).
Figure 1: The Relationship of privacy and Seamlessness in
U-Commerce environment.
1.1 Seamlessness
Scenario A and B below shows an example of
seamless commercial transaction in U-Commerce
environment. Scenario A describes an instance
where economic incentives flow to Displayer and
Scenario B depicts an example where providers and
users are encouraged to join U-Commerce via
incentive-emphasized business model despite some
privacy infringement. Both scenarios show the
possibility to provide economic incentives thanks to
the seamlessness.
A: Scenario 1
Tom visited nearby electronics shop to buy a digital
camera and finally found an attractive one. The clerk
kindly introduced the product that Tom chose. But
he wanted to know more detailed information such
as other users’ comments on it. So he took out his
terminal and scanned the product’s embedded RFID
Tag information. Related basic information was
displayed on the screen and links of supportive
information were provided as well. He opened some
of those linked pages to check unclear parts about
the camera and after some more checkups he
decided to buy the product in other shop located
nearby which according to the linked pages sold the
same product at lower price. The displayer in the
first shop also received economic incentives being
credited to display the product allowing the buyer to
check linked information. (Lee, K. and Seo, Y.,
2006)
B: Scenario 2
After work, Jane was on the subway to go to her
friend’s birthday party. She found the bag of the
woman sitting in the opposite side of the car pretty
cool. Doubtlessly it was difficult to talk to a total
stranger. So Jane took out her RFID Reader-
embedded terminal and read the tag attached to the
bag. Then many tags of other products located
within a 2 m radius were also scanned and Jane
touched filtering button and extracted the
information only about the bag. In addition to the
basic information, she also got more specific data by
logging on to web. And then she dropped by a shop
close to her friend’s house and bought the bag she
searched about. The owner of the bag which Jane
did scanning was provided some amount of
compensation from the bag’s manufacturer. (Lee, K.
and Lee, J., 2006)
Scenario A shows how an end user obtains and
utilizes the information of a certain product in a
physical shop under U-Commerce environment.
When he first acquired the product’s information,
Tom could avoid typing something but rather he just
read embedded digital information. For this reason
the information in the process of commercial
transaction could flow without any interruption.
Such a seamless information stream allowed the user
to locate the sources of relevant information such as
how, when and where the data was made and this
leads to the creation of incentive system. Under the
system, the displayer who provided information
could receive incentives.
Scenario B is focused on providing incentives to
business participants and thereby overcoming
potential weak points despite some infringement on
privacy. If people wear RFID-tagged clothes and a
person can scan the tags with their portable devices,
the end user’s cloth can be used as advertisement
sources as verbal marketing is. But here are hidden
risk potentials. Too much exposure of the
information about the clothes can have possibility to
make clothes’ owner feel “priced” just as his clothes.
This way the owner can get the impression his
INCENTIVE-BASED AND PEER-ORIENTED DESIGN OF UBIQUITOUS COMMERCE
625

privacy is infringed. For this reason, Scenario B
shows economic compensation is offered to
encourage economic players’ participation and
ensure that seamless transaction. In section2, let us
look more deeply into the incentive system and its
applicable business model under U-Commerce
environment.
1.2 Privacy Issue
U-commerce environment upgrades the quality of
commerce related information and in turn
contributes to the establishment of incentive system.
Looking at the other side of the coin, however, such
a systematic accumulation of information can trigger
individual’s privacy infringement. Scenario B tries
to overcome the privacy issue with a new business
model. However no matter how many profits and
benefits might be provided through a well-made
incentive system to each economic player, some end
users would not join U-Commerce activities if they
find there are too numerous privacy-threatening
factors to bear. The increase in “the dissatisfied”
becomes an obstacle to network effect, if, then the
two scenarios would have fewer chances to be
realized. This is why solutions to protect privacy
must be prepared without fail.
Many studies on ubiquitous computing have
suggested methods how to protect privacy. Usually
they’ve proposed principle or requirement for
privacy protection such as Bellotti & Sellen (1993),
Langheinrich (2001, 2002), Jiang (2002), Galanxhi-
Janaqi & Nah (2004) or user modeling such as Jiang
et al. (2002), Lederer et al. (2002).
It’s said privacy has been weakened very much
in e-commerce because the transaction between
providers and end users is a Client/Server structure
and most information gatherers are servers.
Regardless of the place, on-line shopping mall or
off-line shop, where you buy a product the provider
(e.g. credit card company) stores all information
about your commercial transaction in his own
server. Meanwhile end user does not have a good
way to store all the information about his
commercial activities in digital format. Under U-
Commerce environment, however, computing
capability is integrated to financial settlement
methods (e.g. uDA: Ubiquitous Digital Assistant’s
settlement application) and therefore there can be
many models which enable settlement without the
need to send relevant information to server (e.g. P2P
type electronic wallet). In addition information about
transaction can be systematically stored in end user’s
terminal. With this, privacy infringement problem
can be overcome as well.
As method for end user to become the biggest
information owner/collector, this paper suggests
Peer-oriented architecture and proposes
PIB(Personal Information Base) as supporting
system for Peer-oriented architecture. These two
issues will be covered in more detail in section 3.
2 THE ROLE OF BUSINESS
MODEL FOR SEAMLESS
U-COMMERCE
Unfortunately most of the existing U-Commerce
studies have been just focused on suggesting ideal
scenarios and implementing relevant technologies
without verifying feasibility in business perspective.
These types of researches have high possibility to
draw results that will be disregarded by end users
and/or providers in the real market. To be highly
valued in the real world, every solution must go
through business model development check-up
before technology development phase since more
thorough review including business entity
perspective is implemented in business model stage
than in scenario making a step. If scenario might be
just a good story from end-user perspective that
describes new exceptional utility to the end-user,
business model goes further and pictures 1) the roles
of participants in a business and the flow structure of
value among them, 2) potential profits of
participants, 3) profit sources of business providers
(Timmers 1998). This means U-Commerce should
be studied in the direction much more based on
Chesbrough & Rosenbloom (2002)’s angle who
finds business model located in-between technical
and economic domains than on Magretta (2002)’s
view who calls business model telling a good story
at scenario level. Let us think what roles business
model play in U-Commerce by reanalyzing scenario
A and B in section 1from the perspective of
Timmers (1998)’s business model.
2.1 Comparison Shopping: RFID-
based Comparison Shopping
Business participants of Scenario A are displayer,
shopping network, retailer and customer. Value
flows seamlessly and uniquely in comparison to the
traditional commercial transaction as follows: the
information embedded in a product’s RFID tag is
ICEIS 2007 - International Conference on Enterprise Information Systems
626

read by user’s terminal, purchase price is searched
for via shopping network, finally a product is
purchased. Thanks to this, displayer and retailer are
guaranteed fair profits, Customer easy access to
desired information and business providers
commission made from their provision of shopping
network.
RFID-based Comparison Shopping model is
designed to channel incentives to displayer who
provided product information in the off-line shop. In
traditional commerce environment, an end user may
first check price information of a product in web
sites, visits shops to evaluate the product physically,
bargains over product price and went to another
shop if the first shop sells the product at far higher
prices than he saw on the web site. This kind of
sequence can explain one recent shopping trend.
When young-aged students visit a big shopping
mall, the clerk doesn’t pay great attention to them
because he assumes that those students might
already have full knowledge about product price and
expects the visitors will not buy a product if the shop
sells products more expensively than on the internet.
Under RFID-based comparison shopping, however,
displayer receives certain incentives for offering
product information and this encourages him not to
give up his role as displayer, benefiting both visitors
and displayer himself as win-win model. The
displayer would do his best for visitors because he
gets economic compensation in proportion to
visitors’ purchase frequency regardless of where
they actually buy a product. RFID-based
Comparison shopping model offer values to each
displayer and end user and especially the value to
displayer should be attractive enough so that the
display doesn’t have to feel the desire to become
seller. Furthermore when this model is made public
for the first time, potential rejection that participants
might feel over the division of one role into two
should be minimized so that more participation can
be taken. Technical requirement to implement this
model includes the installation of RFID reader
module in end user’s terminal and efficient display
of diverse shopping information into small display
screen that end users see.
2.2 U-Referral Marketing
In scenario B, business participants are referrer,
business provider and buyer who scans information
and purchases a product. Pertaining to value flow,
buyer reads information embedded in product’s tag
via his terminal and searches products based on DB
provided by business providers and finally buys the
product. Referrer also gets incentives. Potential
benefits of participants include easy access to
information for buyer, economic compensation for
referrer and promotion effect for business provider.
U-Referral marketing model ensures economic
incentives to information providers when an end
user obtains product information by scanning
another end user’s product and finally purchases a
product. U-Referral marketing is quite an interesting
model in that product-consuming end users function
as advertisement model, promotes products and
receives economic compensation instead of
advertiser employs a model to promote his product
via TV, magazines, the Internet, etc. Verbal
marketing or Amway model can be seen as the most
similar model to this new marketing model in the pre
U-Commerce times. But verbal marketing doesn’t
have incentive system to use and Amway model
albeit having incentive system has potentials to
bother buyers. In this regard U-Referral marketing
model is more reasonable because under the model
incentive system is available since a person who
scans a product can identify the information sources
and it is more acceptable since all participants can
enjoy certain level of freedom in scanning and/or
being scanned and therefore stay free from unwanted
bothering. Incentives provided to U-Referral
marketing’s participants include cyber money,
premiums and gift certificate to name a few.
As RFID-based comparison shopping model does,
U-Referral marketing model also requires some
technical feasibility such as the installation of RFID
reader module in end user’s terminal. Considering
great numbers of participants and broad service
range, however, the technical feasibility related to
security and accurate information control here is
seen to be higher than the former model. As social
requirement protecting privacy is a critical issue.
End users, referrer, should be offered authority to
decide on information provision easily and
anonymity should be guaranteed so that end users
who do scanning can not identify referrers who give
product information. To make U-Referral marketing
model successful, it’s important to create an
environment where end users accept and enjoy the
process of information collecting via product
scanning and incentive offering to information
providers as part of cultural phenomenon.
Both U-Referral marketing and RFID-based
comparison shopping business models are designed
to give economic compensation to information
providers. These two models show incentive
provision is attributed to seamlessness and such un-
stopped information flow is credited to the incentive
INCENTIVE-BASED AND PEER-ORIENTED DESIGN OF UBIQUITOUS COMMERCE
627

system in turn. Also they show how an institutional
system of business model can attract “runaways”
concerned about seamlessness related privacy risk
back into the new commerce environment.
Different scholars express different opinions over
business model and among them this paper analyzes
two business models based on Timmers (1998)’s
view who interprets business model from the
perspective of an entire flow. The analysis clearly
shows the flow of value which was not identified at
scenario level, potential benefits that participants can
get and the role of business model in U-Commerce.
The next section suggests how to resolve privacy
infringement issue via technical methods.
3 SUGGESTIONS FOR
PRIVACY-ENHANCED
U-COMMERCE
Seamlessness facilitates information linkage and in
turn it improves the quality of exchanged
information. It also enables systematic incentive
system. But ironically the same feature which allows
accurate location of information sources and
systematic storage of such information threatens
individuals’ privacy. In order to decrease these
privacy-intimidating factors, this paper proposes
Peer-Oriented service architecture as a solution.
3.1 Peer-Oriented Architecture
In U-Commerce environment, seamless flow of
information helps economic players gather needed
information easily and this can also mean business
providers do not have difficulties in collecting and
storing end users’ information. To protect privacy
intact in these circumstances, decentralization of
information storage among participants should be
accomplished so that business providers might not
monopolize information. In other words, a specific
architecture should be designed under which
information-generating end user can be the biggest
owner of such information and other participants can
store only part of the entire information.
Such a Peer-Oriented architecture shares the
essence of ubiquitous environment since ubiquitous
environment itself is based on P2P (Takemoto
2002). Considering that WWW was created based
on Client/Server architecture where web server and
client’s web browser interacts it was quite natural
that Web-based commerce was designed to make all
relevant information was stored and many work was
done in business provider’s servers. However, P2P is
a natural format for U-Commerce environment.
Service structure in this P2P form which does not
burden business provider’s servers is also expected
to enhance the efficiency and expansibility of
information processing and computing power
(Morikawa & Aoyama 2004). Section 3.2 introduces
two scenarios related to Peer-Oriented Architecture
and explains why such architecture is required in U-
Commerce environment.
3.2 U-Recommendation & U-Payment
through Peer-Oriented
Architecture
Until now concerning recommendation, most
information ranging from private information
including customer ID to commercial transaction
information has been stored in the server of business
providers and pertaining to e-commerce payment. In
U-Commerce, the possibility and need of
recommendation has increased but privacy-
protecting model has not been proposed. In these
circumstances we need to study how to safeguard
privacy while utilizing conveniences of U-
Commerce by constructing Peer-Oriented
architecture.
First, the recommendation can be made via
temporary peer network rather than by merchant’s
servers which analyze the ID and tastes of buyers.
Some incentives are provided to players who
participate in the recommendation. When end users
holding UDA (Ubiquitous Digital Assistant) which
is similar to PDA enter Uzone (Ubiquitous
Recommendation Zone) the UDAs start P2P
communication. If one end user’s UDA agent
detects relevant content, event-driven agent pushes
the content and in turn Top-k filtering agent
recommends it and neighbor reformation agent
monitors end user’s decision. If the end user actually
chooses the product following the recommendation
of the neighbor, all neighbors involved in the
recommendation receive 1/n amount of incentives.
For sure the amount of such incentives is different
on how much a neighbor contributes to the process.
Figure below is the Architecture for P2P
recommendation.
ICEIS 2007 - International Conference on Enterprise Information Systems
628
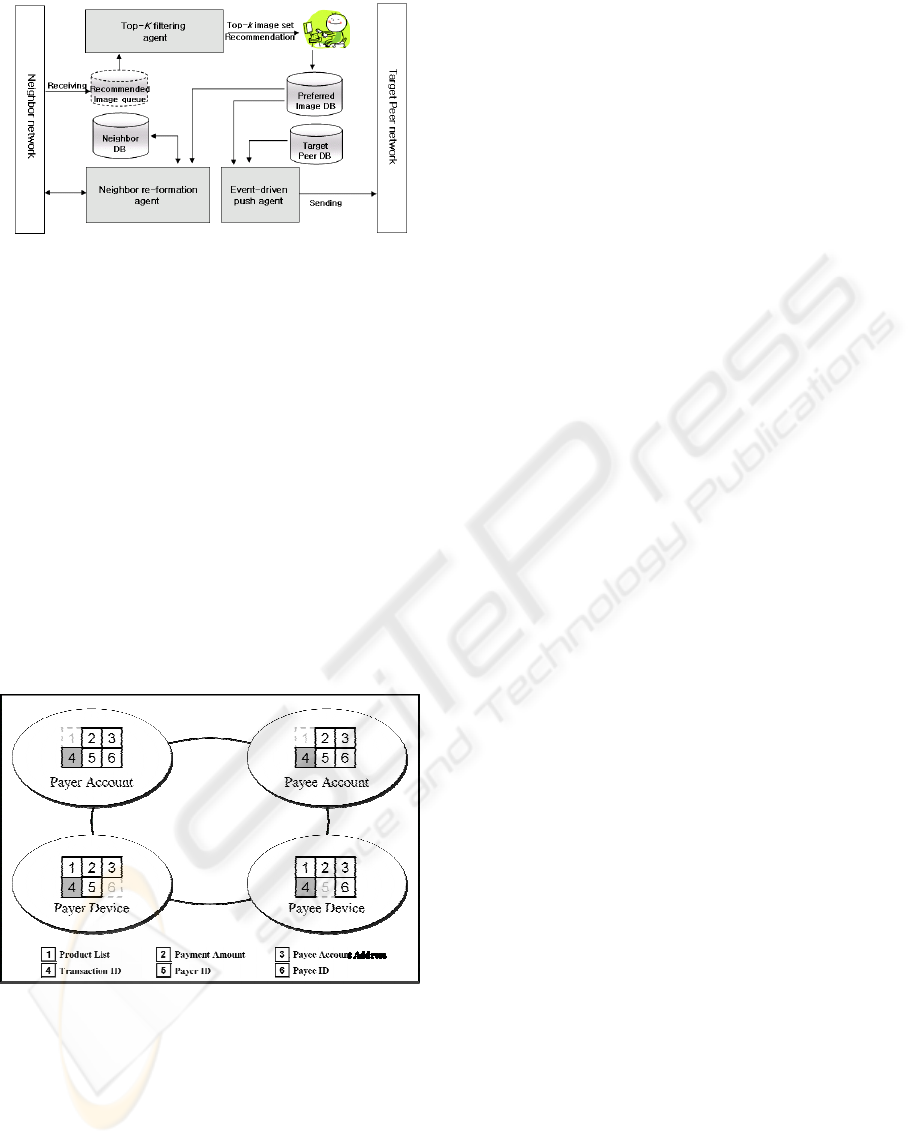
Figure 2: Peer Oriented Architecture for ubiquitous
recommendation (Kim, H., Lee, K., Kim, J., 2006).
In commercial transaction process payment is the
weakest spot to privacy infringement. At least before
payment stage each end user can make efforts not to
expose his personal information. However once the
payment is made, other people also come to be able
to know who bought the product. We can consider a
scenario in which seamlessness is preserved and end
user’s privacy is safeguarded at the same time. The
scenario goes: end user James tries to pay for a one-
piece dress; shop clerk reads the product’s tag
information; settlement information application is
executed on James’s terminal; James gives
authentication and orders payment; an amount of
money is deposited into the shop’s bank account on
the screen; James gets electronic receipt to his
terminal.
Figure 3: The Structure of Payment-Related Information
Possession in Each Entity (Lee, K., Jeong, M., Ju, J.,
2006).
This scenario is distinctive from the traditional C/S
system in three perspectives: first, the payment
system starts from the end user’s terminal; second,
the scenario involves only necessary participants in
the payment process such as payer, payee and main
banks while in the pre-U Commerce setting, one’s
credit card and payment information has to go
through intermediate vendors on its way to a credit
card company; and third, newly created transaction
ID allows fund settlement through financial
institutions without exposing the IDs of payer and
payee. In every deal one unique transaction ID is
generated out of payer and payee’s transaction IDs
and participants in payment process possess only
essential information.
Picture above shows what information payment
process participants have. Payer’s device does not
have payee’s ID and payee’s device does not contain
payer’s ID. Since they do not share each other’s IDs,
those two economic players do not know each other.
But still they can enjoy product/service provision,
payment, and even after services including refund
without any problem. Payer account and payee
account do not possess product lists and thereby
protect the privacy of end user, payer. Furthermore
designed to resemble the cash payment structure in
off-line commercial transaction as much as possible,
this model tries to ensure smooth P2P
communications between economic entities involved
in payment process. In the past only big–scale
business providers which could afford C/S
architecture had digitalized and systematically-
stored information. Meanwhile U-Commerce is
expected to enable Payer, i.e. end user, and even
small product/service providers to systematically
store and manage their information by upgraded
computing power.
Under e-Commerce environment end users had
to disclose all of their private information to
provider’s servers for recommendation and/or
payment. Unlike this, Peer-Oriented networking
service prevents diverse information from being
concentrated on one side and therefore protects
privacy.
While P2P type service architecture preserves
privacy, dispersed information storage in the process
can be an obstacle to the best service. Section 3.3
proposes to tackle this problem via the so-called PIB
(Personal Information Base).
3.3 PIB (Personal Information Base)
for Peer-Oriented Architecture
Information storage supporting system is inevitable
to execute Peer-Oriented architecture successfully.
In P2P architecture information is stored in a
decentralized manner and this can interfere with
seamless accumulation and storage of information.
To overcome this shortcoming, PIB (Personal
Information Base), i.e. individual’s information
collection space, is made. Although PIB is used to
INCENTIVE-BASED AND PEER-ORIENTED DESIGN OF UBIQUITOUS COMMERCE
629

support Peer-Oriented architecture designed to
protect privacy, the fact that all information about
commercial transactions remain in end user’s device
plays as environment that leads to the establishment
of PIB as well.
PIB can be summed up as critical module to be
stored in end user’s terminal. Such information
includes individual’s ID and profile which explain
who an end user is, all kinds of Personal Information
made by end users, digital certificate settlement
related information, etc. Information which goes to
PIB covers age, gender, nationality, income, activity,
interest, schedule, wish list and so on.
Besides tackling P2P architecture’s problem of
dispersed information accumulation, PIB also has
many other merits such as improvement of use’s
privacy and service quality. For example, in a
restaurant a clerk asks a customer, “Do you like
something hot and spicy?” and the customer says,
“Yes.” In this situation, the clerk can do the
recommendation of appropriate meal without
knowing the end user’s ID. If PIB shows the
preference of the end user without revealing his ID,
it means that the clerk can do recommendation
successfully while the customer can keep his privacy
safe. This structure of PIB makes a stark contrast to
C/S structure e-commerce in which one person
makes his identification proved by inputting his
unique ID and has all of his relevant information
stored in server to get services. To be short, under
the new structure end users can enjoy proper product
recommendation and services fit to each different
situation as PIB allots specific places for keeping the
preference and/or commercial dealing information of
individual user. Furthermore PIB has other features
related to commercial transaction information such
as wish list or purchase list. It can also provide
similar concepts to ‘To Do List’ suggested in Carolis
et al. (2004). Gemmell et al. (2003) in studies on
My Life Bits System aimed at recording all relevant
information of one person.
The existence of PIB emphasizes the need of agent
that will utilize it instead of human user. In e-
commerce environment, the performance and usage
of agent was not active since the place to store
individual’s information did not exist. With affluent
PIBs in place, it would be easier for agents to carry
out services on behalf of their owners by referring to
various preferences and/or decision records of
former specific cases. Search, comparison,
negotiation and recommendation functions are
expected to strengthen for agents to ease Users’
burden in decision making.
4 CONCLUSION
Seamlessness is the core concept of U-Commerce.
This seamless flow results in positive effect such as
the improvement of exchanged information. But it
also has risk factors such as privacy infringement.
So to make the best use of Seamlessness it is critical
to develop business model constructed to prevent
economic players from leaving away from the new
type of commerce and to come up with a
fundamental solution to minimize privacy
threatening elements in the first place. This paper
attempts to resolve this privacy related problem by
introducing U-Referral marketing and RFID-based
Comparison Shopping as examples of incentive-
emphasized business models and suggesting Peer-
Oriented architecture and PIB as supportive tool.
PIB not only helps the protection of privacy by
providing product recommendation and other
services without disclosing user’s ID but also helps
end users store and collect information
systematically. In addition, Peer-Oriented
architecture contributes much to privacy protection
by preventing excessive concentration of
information on one place.
ACKNOWLEDGEMENTS
This research is supported by the Ubiquitous
Autonomic Computing and Network Project, the
Ministry of Information and Communication (MIC)
21st Century Frontier R&D Program in Korea.
REFERENCES
Acquisti, A., 2002. Protecting Privacy with Economics.
Economic Incentives for Preventive Technologies in
Ubiquitous Computing Environments. Workshop on
Socially-informed Design of Privacy-enhancing
Solutions, 4th International Conference on Ubiquitous
Computing (UBICOMP 02)
Bellotti, V., Sellen, A., 1993. Design for Privacy in
Ubiquitous Computing Environments. Proc. Euro.
Conf. on Computer Supported Cooperative Work . pp.
77-92.
Brock, D. L, 2001. The Electronic Product Code – A
Naming Scheme for Physical Objects. Technical
Report, AutoID center.
Carolis, B., Pizzutilo, S., Palmisano, I. and Cavalluzzi, A.,
2004. A Personal Agent Supporting Ubiquitous
Interaction. Workshop From Objects to Agents pp. 55-
61
ICEIS 2007 - International Conference on Enterprise Information Systems
630

Chesbrough, H., and Rosenbloom, R., 2002. The Role of
the Business Model in Capturing Value from
Innovation: Evidence from Xerox Corporation's
Technology Spin-off Companies. Industrial and
Corporate Change, Vol. 11. No. 3.
Galanxhi-Janaqi, H. and Nah, F., 2004. U-Commerce:
emerging trends and research issues. Industrial
Management & Data Systems, Vol. 104. No. 9. pp.
744-755
Gemmell, J., Lueder, R. and Bell, G., 2003. The
MyLifeBits Lifetime Store. Proceedings of the 2003
ACM SIGMM workshop on Experiential telepresence.
pp. 80–83
Jiang, X., 2002. Safeguard Privacy in Ubiquitous
Computing with Decentralized Information Spaces:
Bridging the Technical and the Social.
http://guir.berkeley.edu/pubs/ubicomp2002/
privacyworkshop/papers/jiang-privacyworkshop.pdf
Jiang, X., J. Hong, and Landay, J., 2002. Approximate
Information Flows: Sociallybased Modeling of
Privacy in Ubiquitous Computing. In Proceedings of
proceedings of the Fourth International Conference
on Ubiquitous Computing, GÖTEBORG, SWEDEN .
Kim, H., Lee, K., Kim, J., 2006. A Peer-to-Peer CF-
Recommendation for Ubiquitous Environment. Ninth
Pacific Rim International Workshop on Multi-Agents,
Guilin, China.
Langheinrich, M., 2001. Privacy by design - principles of
privacy-aware ubiquitous systems. In Proceedings of
Ubicomp, Springer LNCS pp. 273–291.
Langheinrich, M., 2002. A privacy awareness system for
ubiquitous computing environments. In Proceedings
of Ubicomp
Lederer, S., Dey, A. K., Mankoff, J., 2002. Everyday
Privacy in Ubiquitous Computing Environments.
Ubicomp.
Lee, K. and Lee, J., 2006. Design of Ubiquitous Referral
Marketing: A Business Model and Method. 7th
International Conference on Electronic Commerce
and Web Technologies (EC-Web 2006), Krakow,
Poland.
Lee, K. and Seo, Y., 2006. Design of a RFID-Based
Ubiquitous Comparison Shopping System. KES 2006,
10th International Conference on Knowledge-Based &
Intelligent Information & Engineering Systems,
Bournemouth, U.K.
Lee, K., Jeong, M., Ju, J., 2006. Seamlessness & Privacy
Enhanced Ubiquitous Payment. 7th International
Conference on Electronic Commerce and Web
Technologies(EC-Web 2006), Krakow, Poland.
Magretta, J., 2002. Why Business Models Matter. Harvard
Business Review.
Morikawa, H. and Aoyama, T., 2004. Realizing the
Ubiquitous Network: the Internet and Beyond.
Telecommunication Systems, Vol. 25. pp. 449–468
Roussos, G. and Moussouri, T., 2004. Consumer
perceptions of privacy, security and trust in ubiquitous
commerce. Pers Ubiquit Comput, Vol. 8. pp. 416–429
Takemoto, M., Sunage, H., Tanaka, K., Matsumura, H.,
and Shinohara E., 2002. The Ubiquitous Service-
Oriented Network (USON) An Approach for a
Ubiquitous World based on P2P Technology. In Proc.
2nd International Coference on Peer-to-Peer
Computing.
Timmers, P., 1998. Business Model for Electronic
Markets. Electronic Markets, Vol. 8. No. 2. pp. 3-8
Watson, R. T., Pitt , L. F., 2002. Berthon, P., and Zinkhan,
G. M.: U-Commerce: Expanding the Universe of
Marketing. Journal of the Academy of Marketing
Science, Vol. 30. pp. 333-347.
INCENTIVE-BASED AND PEER-ORIENTED DESIGN OF UBIQUITOUS COMMERCE
631
