
HOME NETWORK AND HUMAN INTERACTION SYSTEM
Rudolf Volner
Department of Air Transport, Faculty of Transportation Science
Czech Technical University in Prague, Horská 3, 128 03 Prague 2
Keywords: Network, human system, mobility system.
Abstract: The term security network intelligence is widely used in the field of communication security network. A
number of new and potentially concepts and products based on the concept of security network intelligence
have been introduced, including smart flows, intelligent routing, and intelligent web switching. Many
intelligent systems focus on a specific security service, function, or device, and do not provide true end-to-
end service network intelligence. True security network intelligence requires more than a set of
disconnected elements, it requires an interconnecting and functionally coupled architecture that enables the
various functional levels to interact and communicate with each other.
1 INTRODUCTION
The study of security network intelligence is an
extremely active area in the field of
communications. Thanks to the latest advances in
data communications – especially in the services
sector and in the communications software,
photonics, and programmable technologies areas –
service providers are spending millions of dollars a
year on an increasingly intelligent communication
infrastructure and applications. Research in the areas
of learning automata, intelligent agents technologies,
intelligent data-mining, knowledge discovery, data-
driven task sequencing, intelligent databases, wire-
speed real-time databases, virtual modelling, and
sophisticated communication network modelling has
provided insights into intelligent computing
processes. Significant progress has been made in
rule-based reasoning, planning, and problem
solving.
Future generation networking will be
characterized by the need to adapt to the demands of
agile networking, which include rapid response to
changing customer requirements, automated design
and engineering, lower-cost services, transparent
distributed networking, resource allocation on
demand, real-time planning and scheduling,
increased quality, reduced tolerance for error, and
in-process measurement and feedback. Future
networking systems will require automated
intelligent networking features that apply
intelligence to the domain of networking in such a
way as to make possible the realization of a full
range of agile and adaptable networks.
Cable operators will have to face the commercial
and operational strategy for:
• Building out or upgrading to bi-directional (two
way) networks,
• Offering voice telephony to residential and
business consumers,
• Offering multi-channel digital television,
• Video-on-demand,
• Home shopping,
• Home banking,
• Residential and business telephony,
• High-speed Internet,
• Home security.
The distributed interactive information system
can be structured in a hierarchical way for system
scalability and evolution – Figure 1, Figure 2. It can
start from an initial two level system with a central
information server and several local information
servers to a system with as many levels of the
hierarchy as needed. The number of levels needed
depends on the network size, network costs, and
network performance requirements.
323
Volner R. (2007).
HOME NETWORK AND HUMAN INTERACTION SYSTEM.
In Proceedings of the Ninth International Conference on Enterprise Information Systems - HCI, pages 323-327
DOI: 10.5220/0002400103230327
Copyright
c
SciTePress

2 INTELLIGENT SECURITY
AND COMMUNICATION
NETWORKS
Intelligent security and communication networks
must at least be able to understand the security and
communication environment, to make decisions, and
to use and manage network resources efficiently.
More sophisticated levels of security network
intelligence include the ability to recognize user,
application, service provider, and infrastructure
needs, as well as expected and unexpected events,
the ability to present knowledge in a world model,
and the ability to reason about and plan for the
future.
Network intelligence will evolve through growth
in computational power and through the
accumulation of knowledge about the types of input
data needed for making decisions concerning
expected response, and about the algorithmic
processing required in a complex and changing
communications environment. Increasingly
sophisticated network intelligence makes possible
look-ahead planning, management before
responding and reasoning about the probable results
of alternative actions. These intelligent network
capabilities can provide service providers with
competitive and operational advantages over
traditional networks.
3 THE HS/ATM ARCHITECTURE
For a network, the serving area is partitioned into a
number of basic service areas designated as cells.
Each cell is served by a base station – centre HS,
which exchanges radio signals with mobile terminals
– home control centers. Mobility is central to
networks. To provide mobility, tracking mobile
terminal locations becomes an important and
primary function of network and hence some
databases are introduced to support such a
capability. In HS/ATM networks, each HS network
covers a large geographical area and incorporates a
number of base stations. Meanwhile, the location
database of wireless cluster manager is broken into
two parts:
• one for the mobile terminals which are
permanently registered in the community, the
home community – home part,
• the other for the mobile terminals which are
visiting the community – visiting part.
4 MODELS OF MOBILITY
Mobility models describe a mobile unit’s movement
through a geographical area. A number of systematic
and ad hoc models have appeared in the literature,
but they do net reflect realistic actual movement
patterns in many respects. Nor, being idealizations
for specific purposes, are they intended to describe
adequately the range of subscriber behaviours that
will appear in a mobile multimedia network
covering a large geographical area.
The mobile VCE (The Virtual centre of Excellence
in Mobile and Personal Communications) model
consists of a series of poles - places where mobile
users gather, such as a city centre, a shopping mall
or a road (hence the need to include direction).
Movement between poles is defined by four
properties, which between them determine the
spatial and temporal behaviours of the users:
• gravity, reflecting the attraction to a pole,
• elasticity, reflecting the reaction of restoring
equilibrium after changes of attraction,
• entropy, modeling the disorder at poles and in
the flows between them,
• viscosity, representing the spatial spreading
variations of the flow populations.
The model is a network of poles through which
circulates a population of mobiles, whose velocity is
determined by the configuration of the above four
elements. A mobile can be seen either as an
individual or as a mass. Every mobile belongs to a
specified mobility class, of which there are four:
• business,
• leisure,
• shopping,
• residential.
As shown in Figure 4, the model can be decomposed
into three distinct sub-models:
• the physical sub-model defines the topology
and the quantitative spatial distribution of the
mobiles,
• the gravity sub-model controls the temporal
evolution of the attraction of all the poes,
• the fluid sub-model fixes the laws of circulation
of each mobile between the poles.
ICEIS 2007 - International Conference on Enterprise Information Systems
324

5 CHARACTERIZATION OF
SERVICES, TRAFFIC
SOURCES AND SYSTEM
TELETRAFFIC
Traditional traffic modeling of data sources assumed
that the inter-arrival times of traffic packets were
basically exponential in distribution and independent
of one another, which means that the process is
memory-less. However, recent studies of the
behaviour of individual multimedia sources and
system-level activity show that traffic traces are
distributed in ways more complex than this.
Our analysis has aimed at improving the best-
fitting model for a given traffic scenario when the
underlying flow keeps changing over time and
space. To be confident that the results are useful a
model was sought that:
• was as simple as possible in a computational
sense without compromising accuracy,
• had a physical explanation in the network
context,
• can be related to real measurements for
verification purposes by the operators.
The investigation focused on extensions that could
retain tractability, in two steps as described below:
• statistical multiplexing,
• parameterization.
Traffic generation – if the traffic is memory-less,
generation of traffic to support the simulations can
be achieved simply by a negative exponentially
distributed process to specify packet inter-arrival
time. However, modeling self-similar traffic is much
more complex (Volner, 2003), (Volner, 1995),
(ATM, 1996).
6 CONCLUSION
In this paper, we have proposed a HS/ATM network
for supporting multimedia communication to mobile
terminals. Here the network is partitioned into core
and edge networks. The advantage of this portioning
has been discussed. The network bandwidth is
allocated in such a way that each VP is semi-
permanently allocated a certain amount of using
existing optimization techniques. Cell scheduling
and queuing implementations were discussed. We
conclude, that based on the proposed bandwidth
management framework, all ATM service classes
can be served with reasonable QoS guarantees, the
CAC procedures easily implemented, and potential
rate-based ABR congestion control easily
incorporated.
REFERENCES
Volner, R.: CATV – Interactive Security and
Communication System, proceedings the institute of
electrical and electronics engineers, 34th Annual
2000 International Carnahan Conference on Security
Technology, October 2000 Ottawa, Canada, pp. 124-
136, IEEE Catalog Number 00CH37083, ISBN 0-
7803-5965-8
Volner, R.: Home security system and CATV, 35th
Annual 2001 International Carnahan Conference on
Security Technology, October 2001 London, England,
pp. 293 – 306, IEEE Catalog Number 01CH37186,
ISBN 0-7803-6636-0
Volner, R.: CATV Architecture for Security, 36th Annual
2002 International Carnahan Conference on Security
Technology, October 2002, Atlantic City, New Jersey,
USA, pp. 209 – 215, IEEE Catalog Number
02CH37348, ISBN 0-7803-7436-3
Volner, R., Poušek, L.: Intelligence Security Home
Network, 37th Annual 2003 International Carnahan
Conference on Security Technology, October 2003
Taipei, Taiwan, pp. 30 – 37, IEEE Catalog Number
03CH37458, ISBN 0-7803-7882-2,
Volner, R.: Intelligence CATV – Traffic models, Design
and Analysis, International Conference on Computer,
Communication and Control Technologies CCCT’03
and The 9
th
International Conference on Information
Systems Analysis and Synthesis ISAS 03, Proceeding
volume IV, July 2003, Orlando, Florida, USA, pp. 340
-345, ISBN980-6560-05-1, CD - ISBN 980-6560-10-8
Volner, R. et al.: CATV In Multimedia Transmission
Systems, Electronic Horizont, Vol.55, Nov./ Dec.
1995
ATM Forum Technical Committee: Traffic management
specification version 4.0, AFTM 0056.000, Apr. 1996
ATM Forum technical committee: Flow controlled
connections proposal for ATM traffic management,
September 1994
HOME NETWORK AND HUMAN INTERACTION SYSTEM
325
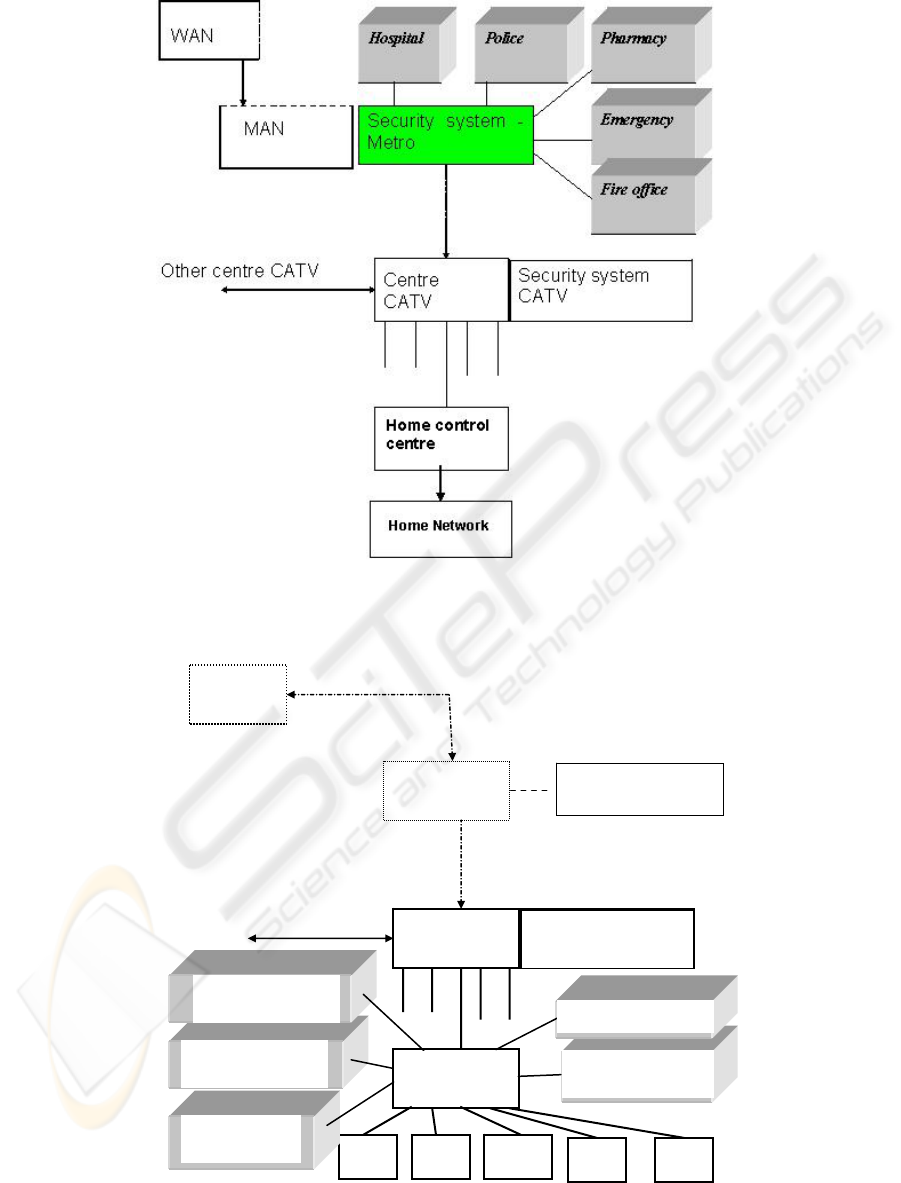
Figure 1: Basic home network – human interactive Subsystem.
Figure 2: The HS interactive system can be structured in a hierarchical way for system scalability and evolution.
Fibre Optic System
BMHS network
Centre
BMHS
Other centre BMHS
Security system -
Metro police
PC
Audio
Text Data
WAN
MAN
Home control
centre
TV
Security system
BMHS
Telemetrically
security system
Telemetric
systems
Security cameras
Video and audio
identification
Biometric
identification
ICEIS 2007 - International Conference on Enterprise Information Systems
326
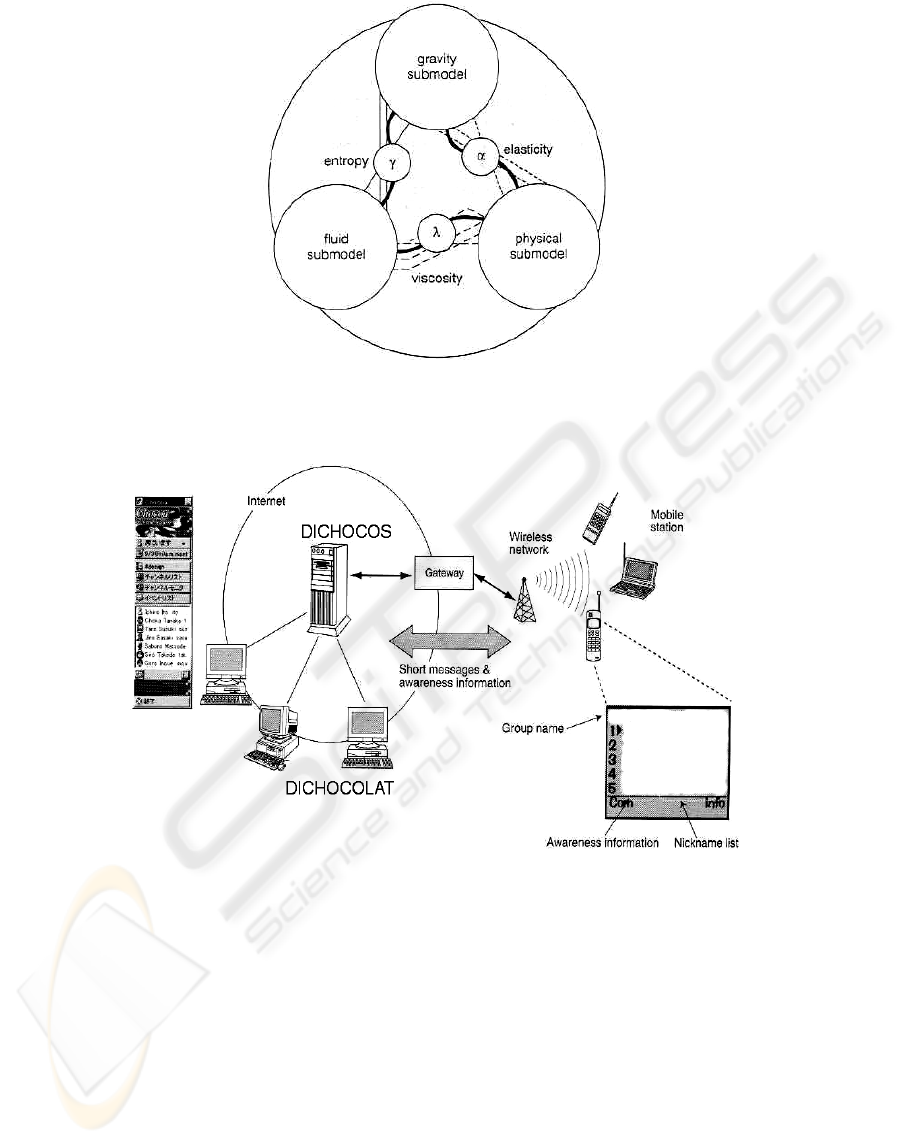
Figure 3: Mobility model into three sub-models.
Figure 4: Mobile awareness service.
HOME NETWORK AND HUMAN INTERACTION SYSTEM
327
