
Unobtrusive User Profiling: The Use of RFID to Create
a Smart Wardrobe
Maria Indrawan
1
, Seng Loke
2
, Sea Ling
1
and Frida Samara
1
1
Faculty of Information Technology, Monash University, Melbourne, Australia
2
Department of Computer Science, La Trobe University, Melbourne, Australia
Abstract. Many profiling systems rely on the user interactions directly with the
systems to gather their raw data. We present a profiling system based on
RFIDs. Unlike many profiling systems, the proposed profiling system is unob-
trusive because it does not interact directly with a mobile device or computer
systems. As proof of concept, we illustrate the idea by developing a Smart
Wardrobe system which creates the profile by observing the movement of
clothing items that have been tagged by RFID, in or out of the wardrobe. Based
on the observations, the fashion profile of the user is generated. The prototype
shows that meaningful profile can be created and can be used to feed other ap-
plications, such as shopping assistant or recommender systems.
1 Introduction
One major role that a computer plays in the modern society is providing convenience
to the users. The convenience is achieved by alienating mundane tasks from human
activities or by offering personalized services. The proliferations of smart devices and
information services together with the imposing ‘fast’ pace of modern society places
the need to provide users with the right information in a timely manner and be deliv-
ered in a way that conveniences the users. In the early development of computer sys-
tems, it is common that the systems dictate the way a user would use the systems.
This phenomenon has changed rapidly in the last decade. Many computer systems
provide personalized services to the user. Hence, it is the user who dictates how the
system should behave. One major area of interest of many researchers in providing
personalized and convenience services to human is in the area of pervasive comput-
ing, specifically in the investigation and development of smart home.
In a smart home environment, it is perceived that the electrical appliances can be
programmed to be aware of the user’s need and therefore are able to provide a per-
sonalized service to improve the user’s quality of life [7]. These appliances usually
refer to the traditional electrical appliances such as fridge, TV, washing machine,
dishwasher, music player and so on. In this paper, we present a system that allows
non-electrical item in the house to be equipped as a smart device. We propose the use
of RFID to create a smart wardrobe system. The RFID based system is used to build
the user’s fashion profile. The fashion profile, in turn, can be used to build recom-
Indrawan M., Loke S., Ling S. and Samara F. (2007).
Unobtrusive User Profiling: The Use of RFID to Create a Smart Wardrobe.
In Proceedings of the 1st International Workshop on RFID Technology - Concepts, Applications, Challenges, pages 3-13
DOI: 10.5220/0002433400030013
Copyright
c
SciTePress

mender system. In this paper, we present how the user’s dressing behaviour and fash-
ion sense can be observed and learned to create a fashion profile.
The paper is organised as followed. Section 2 presents the overview of other re-
searches that are related to our work. In Section 3, the architecture of the smart ward-
robe, the algorithms designed for creating the fashion profiles and the underlying data
model used are presented. Sample scenario of the proposed system is discussed in
section 5. We conclude our discussion in Section 6.
2 Related Work
Radio Frequency Identification (RFID) has been around since World War II. It was
used to help soldiers identify fighter planes as friend or foe [2]. Its usage in modern
era is also for identification purpose. As stated by Vogt [10], “Identification is a cen-
tral concept in user-oriented and ubiquitous computing”. RFID is used to identify real
objects such as humans, books, as well as movement of these objects. There has been
research on ubiquitous (“being or seeming to be everywhere at the same time” [12],
computing, which utilises RFID system architecture to pursue the seamless integra-
tion of technology and human environment [11]. The same research objective was
also undertaken [4], which presented the idea of having services provided by virtual
worlds such as computers to assist users in their daily tasks.
Want, et al. [11] states that the RFID technology has been used for sometime.
However, only simple prototypes were developed in many cases. This is due to the
relatively high cost of implementation in the past. Recent development allows the
reduction of the implementation cost of RFID systems which results in the emergence
of many smart and useful applications. These applications include:
• Tagged Business card: The application involves automatic detection of a person
through the embedded RFID in the business card. When a reader senses the busi-
ness card, it will trigger the user’s computer to open the home page of the person
represented in the business card [11].
• Tagged Printed Documents: In this system, printed documents are tagged such
that a document can be linked to its electronic copy for an up to date version so
that readers are always aware of the version of the document [11].
• Tagged Dictionary: Once reader senses the tag, the system will perform a lan-
guage translation of the document displayed [11].
• Smart Toolbox. There are laws in aircraft maintenance business that requires
continuous checking and monitoring of tools used in the maintenance process to
ensure quality and safety of aeroplanes. To date, these routines are done manu-
ally and thus time consuming and prone to human errors. Smart toolbox is pro-
posed to automatically detect missing tools [5].
• Smart Medicine Cabinet [3]: This system is designed to provide visual repre-
sentation of RFID tracked medicine in the cabinet. The visual representation can
be adjusted for visually impaired users.
• Smart Surgical Kit [3]. Often doctors forget to remove some swabs and ban-
dages that have been used in surgical operations. This prototype is proposed to
continuously track and monitor how many RFID-tagged swabs and bandages
4

have been used and whether all have been returned or disposed. Otherwise it will
send out an alarm signal to doctors.
• RFID Chef [6]. This prototype illustrates how an RFID mechanism can be in-
corporated into smart home. Apart from providing the users with easy access to
information on cooking recipes based on RFID-tagged grocery items, it also ex-
plores the idea of context awareness. An advancement of the RFID chef’s capa-
bility has been mentioned in Römer et al. [8]. In this system, a user preference is
added to the selection of recipes, eg vegetarian or Asian dishes. A similar idea is
also proposed by Schneider [9] where an application called Smart Shopping As-
sistant is designed to help the shopper by displaying information regarding prod-
ucts in a display unit. The shelves and the products are equipped with RFID
reader and tags respectively so that the application can identify which product in-
formation to display.
• Flytrap [1] is a smart system that will play appropriate songs based on the music
preferences of occupants in a room. It has the knowledge of the occupants’ musi-
cal tastes and will construct a play list of songs that will please everyone in the
room. The system will construct each of the user’s songs preferences by monitor-
ing what music each individual person plays on his/her own computer. This sys-
tem is a good example of how a system can be built for a truly ubiquitous envi-
ronment. The presence of the system is seamless in the room but it is useful for
everyone
From these examples of prototypes and applications of RFID, it is evident that RFID
technology is a simple, unobtrusive identification tool that can be used to track and
monitor real objects. One area that has not been addressed by the sample prototypes is
the utilisation of RFID to build personal profile. Personalisation of services is crucial
for pursuing ubiquitous computing. In many cases, the collection of data to build user
profile is done through WWW interactions. Example of such system is amazon.com.
In this type of profiling system, the data collected is owned by the organisation that
owns the server. It is not possible for individual to get the data for their personal use.
RFID provides an alternative to the way data can be collected. It shifts the data col-
lection process from the organisation to the individual, hence will shift the ownership
of the data to the individual and enhanced privacy. In this research, we illustrate how
and RFID system can be used to create individual-owned profile. We use the scenario
of fashion profile which is created based on observing the users daily clothing
choices.
3 Smart Wardrobe Architecture
We envisage that the user profile generated by observing the behaviour of the user
can be used to help user understand his/her fashion preferences and be familiar with
the content of his/her wardrobe. This information can be used to help user make deci-
sion when purchasing fashion items in the future. For example, knowing that one
hardly uses bright colour clothes to work, he/she may not want to buy bright colour
jacket during a shopping trip. There are several interesting fashion profiles that can be
collected. In this research, we consider the following profile items as interesting:
• Most and least frequently worn item.
•
Most and least frequently worn brand.
5

• Most and least frequently worn colour.
•
Most and least frequently worn pattern (eg. floral, plain).
•
Most frequently worn combination of items;
During the daytime.
During the evening.
During the weekend.
The profile items presented above are used as illustration of the types of profile
items that can be generated. The list is not considered exhaustive. New profile item
can be added to the system.
The smart wardrobe uses observation of events to build the above profile items.
The following events are being observed by the system:
• A clothing item is in or outside the wardrobe.
• A clothing item is being worn. It is possible that an item is taken out of the
wardrobe for a few minutes but not actually being worn.
• Two or more clothing items are being worn together.
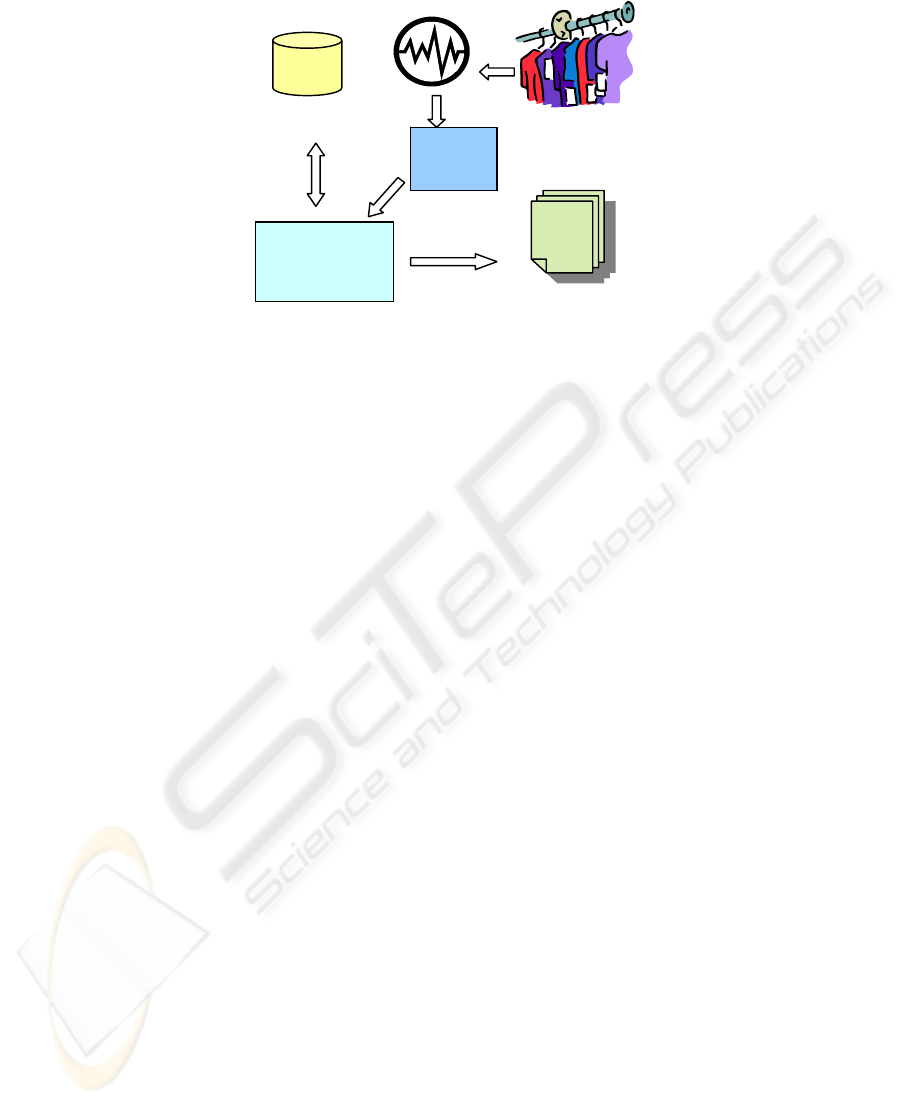
The architecture consists of three major components as shown in Figure 1. An
RFID reader is used to detect the presence or absence of clothing items inside the
wardrobe. Therefore, each clothing item that the user has must be tagged with an
RFID tag. Each of these tags has a unique id, so that the application is able to differ-
entiate one item from other items. In addition, the RFID reader is designed to periodi-
cally read all tags attached to clothing items inside the wardrobe. Then, signals can be
sent to the smart wardrobe application regarding which items are present, i.e., which
items are available inside the wardrobe.
This application also utilises a database. The database consists of several tables;
one table that stores information about the inventory of the wardrobe, another table
records the data regarding the user dressing activities.
Based on the information on what the user has in the wardrobe as well as the usage
of these clothing items, the Smart Wardrobe application will then generate a user
fashion profile that reflects the user’s dressing preferences.
3.1 Data Model
The smart wardrobe keeps the information regarding the inventory of the wardrobe
and the events generated due to the wardrobe activities in a database. For the ward-
robe inventory, the system keeps the information on the type of clothing, colour,
brand, material, pattern and category. Examples of category instances are formal,
evening and casual. Formal refers to the clothes that are considered business-like, eg
suits.
A second table in the database is used to record the “in” and “out” of the clothing
item of the wardrobe. This table is updated periodically in a given read cycle. The
reading of the complete cycle is compared with the reading of the previous cycle to
identify any missing tag id. Any missing tag-id will be considered as item-out-of-
wardrobe. If a tag-id is still missing after a number of cycles, the item is considered a
worn-item. The data in the event tables is used by three different algorithms in the
system to determine three different events.
6
RFID
reader
Events Data
Smart
Wardrobe
application
profile
Fig. 1: System Architecture.
3.2 Event Detection Algorithms
There are three types of event that the system needs to detect as explained in section 3.1.
Algorithm 1. Detecting the IN and OUT of item.
At the start of the application, the application initialises the data storage that is
used to store the tag ids read by the reader. At each polling, every tag id that is read
by the reader will be added to a list. The list of tag ids that are read during current
polling are compared
with the list from previous polling. If the id is present during
reading, it will be concluded as being inside the wardrobe. However, when a tag is
not present during the current reading, but was available in a previous polling, the
application will conclude that the corresponding item has been taken out of the ward-
robe.
The application will continuously execute these steps for the duration of the appli-
cation runs. However, when an item is concluded as being taken out, it does not mean
the user is wearing it. Consider the scenario where the user takes an item out of the
wardrobe but decides not to wear it and puts it back into wardrobe within a certain
time frame; the application should be able to differentiate this event from other events
when the user actually decides to wear the item he/she takes out. In order to accom-
plish this, our proposed model has designed a second algorithm to detect whether an
item is being worn by the user.
Algorithm 2. Detecting whether item is being WORN.
The algorithm calculates the number of consecutive pollings allowed for an item to
be absent before it is concluded as being worn. If it first encounters that the tag status
is not present, it will check through the subsequent values from the following polling.
If the tag is still not present during these pollings, then it will be concluded as being
worn and then added to the list of worn items. This information is recorded as it is
important for the application to discover which of the items are worn together as a
pair in the next algorithm.
7

Algorithm 3. Detecting a pair of items worn together.
Using the result from the previous phase, this algorithm checks if at least two items
have been concluded as being worn, resulting from Algorithm 2. For the first item
that is concluded as worn, the application will try to find the partner for this item by
checking the polling period in which the partner is taken out. In this context, assump-
tion is made that at any one time, the user wears only two items, top and bottom
items. If the application can find another item that meets the criteria, i.e. also taken
out during the time allowed, then this pair will be added to a list as a pair of clothing
items that are worn together. Then, these items are removed from the list of single
items.
Following these steps, the application will then make database entries into a table
with information about items that are worn together as well as the time of usage, i.e.,
the day and the time of the day.
With respect to the time of usage, in the prototype, we have two time periods:
MORNING and EVENING. Every dressing event that occurs between 6am to 5pm
will be recorded as the MORNING event. If it occurs between 5pm and 6am, it is
categorized as an EVENING event. This categorization is important since most of the
time there is a distinct difference between a morning outfit and an evening outfit. For
example, a working professional can be assumed to be wearing business wear in the
morning and casual wear in the evening.
3.3 User Profile Generation
There are two main sources of data to be used in generating user fashion profiles. The
first is the inventory data and the second is the usage data.
The inventory data contains information regarding the user’s current clothing col-
lections in the wardrobe. As mentioned earlier, the application database stores infor-
mation regarding each item’s attributes, such as the colour, brand, pattern and mate-
rial. From this information, the application is able to analyse and generate this part of
the user’s “potential” favourite attributes in his/her fashion profile simply using SQL
queries.
The second part of the user fashion profile is generated based on the usage of the
clothing. The information used to generate this profile is those that are recorded by
the application based on the events data collected by RFID reader discussed previ-
ously. It is important to analyse this record because at times what user has in the
wardrobe does not necessarily illustrate what he/she likes to wear. Thus, it is worth-
while to design this application to generate the profile from two different perspec-
tives: the favourites based on usage statistics as well as the favourites based on ward-
robe content.
Finally, usage patterns are derived. This information is useful as patterns can be
found from the way the user dresses such as the colour combination, pattern combina-
tion, and type combination. These combinations suggest the way the user matches
his/her top item with his/her bottom item. An example is shown below in Figure 2.
8
Colour:
1. white and black
2. blue and black
3. pink and blue
Pattern:
1. plain and plain
2. stripes and plain
3. stripes and stripes
Types:
1. shirt and pants
2. t-shirt and jeans
3. shirt and skirt
Fig. 2. User Dressing Combinations.
This example above shows the three most often combinations from each category.
The most often colour combination is white top and black bottom; the most often
pattern combination is plain top and bottom; and the most often type combination is
to wear shirt and pants.
This information is derived by applying the standard data mining algorithm to us-
age data. In this instance, we use association rules to capture patterns. The result is
useful as the application can use the knowledge to make recommendations to the user.
For example, when a user has selected a shirt, it will recommend wearing pants with
it since from the pattern found from the usage data, the user is very often wearing
shirt with pants (rather than jeans, for example).
4 Physical Design Considerations
In our proposed model, as described in previous sections, all clothing items must be
uniquely tagged. The RFID can be installed on each clothing item or attached to the
clothes hanger. The second option is less reliable because it requires user to ensure
that the clothes are placed with the correct clothes hangers. Having each clothing item
tagged with an RFID may not be far from reality as retailers have started demanding
manufactures to tag all their products with RFID [2].
Besides installing the RFID on the item, an RFID reader is also required to be in-
stalled inside the wardrobe. The reader may be installed near the wardrobe door or in
a place where the reader will be able to detect the tags inside the wardrobe. An ideal
option is to install an RFID reader that can read multiple tags so the polling can be
done almost instantaneously.
9
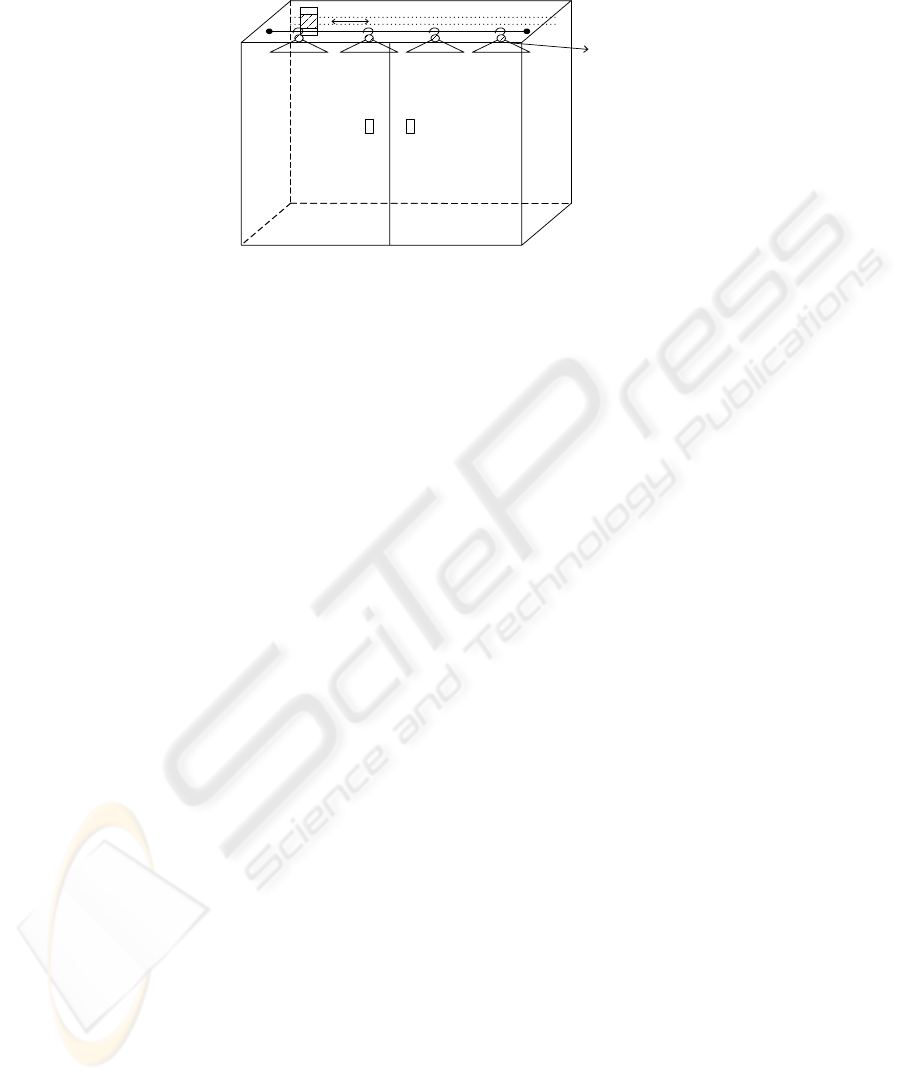
Fig. 3. RFID technology installation in wardrobe.
For the case of an RFID reader that is able to read only one tag at a time, the ward-
robe needs to be equipped with a motor and reel installed along the length of the
wardrobe; the RFID reader, then, should be positioned on top
of the motor such that the reader is able to move along the reel to read the tags inside-
the wardrobe one by one.
Figure 3 illustrates the wardrobe set up of the RFID reader that is only able to read
one single tag at a time. This setting does not show the installation of the motor.
However, the RFID reader should move along the wardrobe track to read the tag one
at time. In this example, we assume the RFID tags are embedded in cloth hangers. In
the future, clothing labels will be made of RFID labels so that we do not need to em-
bed the RFID tags in cloth hangers.
Once the reader is installed, it needs to be started such that the reader will start to
travel along the reel to read tags inside the wardrobe, i.e. polling for data, one tag at a
time. This polling can be scheduled to happen periodically. For example, every 2
minutes, the reader will be activated to start polling i.e. reading radio frequency signal
that is reflected back from the tag within the range. This reader signals and notifies
the application with information of which tags have been successfully read. This
information consists of the unique id numbers of the RFID tags. From this unique id
number, the application is able to cross match the read id with the corresponding
clothing item. Therefore, it is able to identify which items are currently in the ward-
robe. This process of reading tags will be done periodically within the time periods
set by the user.
5 Prototype Evaluation
As proof of concept, a prototype of the Smart Wardrobe Application has been built.
Random generated data were populated into the events data storage. We created
simulation data from two different types of user, a working professional and a stu-
dent. These two categories are chosen because these types of users may be considered
to be different in the way they dress. Therefore, we like to test whether the applica-
tion can appropriately generate the profile.
track
RFID
reader
RFID tags
embedded in
cloth hangers
10

Fig. 4. Clothes items being worn.
When creating this simulation data, some assumptions are made. They are:
• The inventory generator creates woman’s clothing items. We choose to generate
woman data because there is a broader range of woman clothing items compared
to menswear.
• All clothing items inside a single wardrobe belong to a single user.
• All clothing items inside the wardrobe are tagged with RFID tags.
• When one decides not to wear the item, one will always put the item back into
the wardrobe. Therefore, application can be certain that the user wears clothing
items that have been taken out of the wardrobe for a long time period.
Based on the simulated data, the system generates profile of the inventory statis-
tics, usage statistics and usage pattern. To generate the usage pattern, the system em-
ploys association rules algorithm. Figure 4 shows the interfaces of the system. Figure
5 depicts the content of a simulated wardrobe of a working professional.
From the generated inventory data, the events of wearing any of these items as
pairs in a given time of the day are generated. And the user profile is generated. An
example of the profile is the information about the combination of items worn. The
information is generated using the association rules algorithm. An example of this
type of profile is shown in Figure 6.
Fig. 5. A working person’s wardrobe.
11
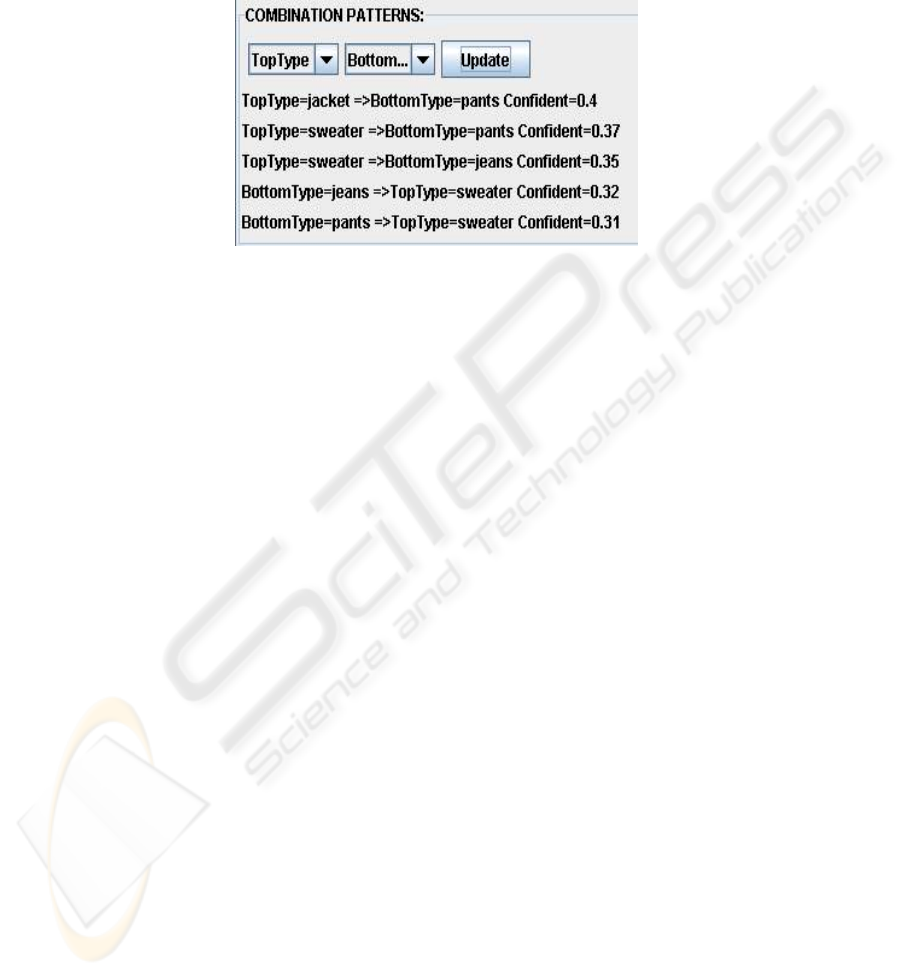
The discovered pattern shows that a working professional is likely to match
his/her jacket with pants. Using this information, when the user picks a top item, the
application will then able to make appropriate suggestions of which item to match
with the selected top.
Fig. 6. Association of clothing items generated.
6 Conclusion
We have illustrated the use of RFID for creating individual profile. The profile is
generated based on the observation of the user’s daily activities. In this particular
system, we observe the fashion activities of the user. The SmartWardrobe system
shows that creating individual and private profile is possible without having the user
interact directly with a computer panel, which many of the current profiling systems
rely upon. The prototype has shown that some useful profile can be generated regard-
ing the user’s fashion profile, such as inventory statistics, commonly used brand,
commonly used fabric and commonly used combination of clothing items. This in-
formation can be consumed by other applications, such as shopping assistant or re-
commender systems. The profile can be loaded into a PDA or mobile phone and as-
sist the user in chooosing appropriate clothing item during a shopping trip. For ex-
ample, the user may not buy a clothing item with the colour that does not match with
any item in the wardrobe. Additional functionality to generate the profile can also be
added to the system in order to enrich the profile. For example, associating the cloth-
ing items with the season and the time of the day.
The idea can certainly be extended to other containers (not just wardrobes) such as
a laundry basket, a bin, a shopping trolley etc. They can contain similar kind of in-
strumentation and tagged items for the same purpose. Certainly, such a system needs
to be tested in longer term scenarios – an avenue for future work on our anecdotal
experiments and prototype demonstration. Long term learning is conceivable as we
envisage our techniques can be easily extended to such learning.
12

References
1. Crossen, A., Budzik, J. and Hammond, K.J. (2002), “Flytrap: intelligent group music rec-
ommendation”, In: Proceedings of the 7th international conference on Intelligent user in-
terfaces, Jan 13-16, 2002, ACM Press, New York, pp. 184-185.
2. Evans, N. (2004), “Why Wal-Mart Had To Deploy RFID”, RFID Journal [Online],
Available: www.rfidjournal.com/article/articleprint/1257/-1/82/ (Accessed: 8 Sept 2005)
3. Floerkemeier, C., Lampe, M. and Schoch, T. (2003), “The Smart Box Concept for Ubiqui-
tous Computing Environments”, In: Smart Objects Conference, 2003, Grenoble.
4. Floerkemeier,C. and Lampe, M. (2004), “Issues with RFID usage in ubiquitous computing
applications”, In: Ferscha, A., Mattern, F., (eds) Pervasive Computing: Second Interna-
tional Conference, April 18-23, 2004, Springer-Verlag, Vienna, pp. 188-193.
5. Lampe, M. and Strassner,M. (2003), “The potential of RFID for moveable asset manage-
ment”, In: Workshop on Ubiquitous Commerce, Ubicomp'03, Oct 2003, Seattle, USA.
6. Langheinrich, M., Mattern, F., Romer,K. and Vogt, H. (2000), “First Steps Towards an
Event-based Infrastructure for Smart Things”, In: Ubiquitous Computing Workshop, PACT
2000, Oct. 2000, Philadelphia.
7. Park, S.H., Won, S.H., Lee, J.B., and Kim, S.W. (2003), “Smart Home: digitally engi-
neered domestic life”, Personal and Ubiquitous Computing, vol. 7 (July 2003), pp. 189-196.
8. Römer, K., Schoch, T., Mattern, F., and Dübendorfer, T. (2003), “Smart Identification
Frameworks for Ubiquitous Computing Applications”, In: Proceedings of the First IEEE
International Conference on Pervasive Computing and Communications, March 2003,
IEEE Press, Washington D.C, pp. 253-273.
9. Schneider, M.(2003), "A Smart Shopping Assistant utilizing Adaptive Plan Recognition",
In: ABIS Workshop on adaptivity and user modelling in interactive software systems, pp.331-
334.
10. Vogt, H. (2002), “Efficient Object Identification with Passive RFID Tags”, In: Mattern, F.,
Naghshineh, M. (eds), Proceedings of the International Conference on Pervasive Comput-
ing, 2002, Pervasive2002, vol.2414, Springer-Verlag, pp.98-113, Zurich, Switzerland.
11. Want,R., Fishkin,K.P., Gujar,A., and Harrison,B.L. (1999), “Bridging physical and virtual
worlds with electronic tags”, In: Proceedings of the 1999 Conference on Human Factors in
Computing Systems (CHI'99), May 15-20 1999, ACM Press, New York, pp. 370–377.
12. WordNet (2003), “Free On-line Dictionary of Computing”, (Dictionary.com), Available:
http://dictionary.reference.com/search?q=ubiquitous (Accessed: 25 April 2005).
13
