
ADAPTIVE RISK MANAGEMENT IN DISTRIBUTED SENSOR
NETWORKS
Floriano Caprio
Siemens IT Solutions and Services spa, Centro direzionale Collina Liguorini, Avellino, Italy
Rossella Aiello, Giancarlo Nota
Dipartimento di Matematica e Informatica, University of Salerno, Fisciano (SA), Italy
Keywords:
Risk Management, Multiagent System.
Abstract:
The risk management in a distributed sensor network charged to put environmental variables under control is
receiving great attention in recent years. We propose a framework that considers an high level model together
with a distributed system based on adaptive agents able to handle the complete risk lifecycle at various levels
of responsibility.
The paper first describes the risk modeling problem in a distributed sensor network, then introduces three
fundamental agent types: the risk monitoring, the local monitoring and the global monitoring, used to build a
network that supports risk management in a distributed environment. Then, the adaptive management of risk
exposure is described in terms of a decision process based on a tight cooperation among Local Monitoring
Agents.
The framework is general enough to be applied in several appication domain.
1 INTRODUCTION
The problem of risk management is well understood
in many fields where a large body of knowledge has
been developed to cope with risk exposure. Examples
are enterprise risk management (Institute of Risk
Management, 2002; COSO, 2004), project risk
management (Project Management Institute, 2004;
Camara et al., 2006), software risk management
(Boehm, 1991; Williams et al., 1997; Han and
Huang, 2007) among others.
Even though risk management is a topic that is
assuming increasing relevance in many distributed
contexts, such as environmental control, health sys-
tems , etc. the topic of distributed risk management
has received little coverage in literature (Grabowski
et al., 2000; Schaller and Vaz, 1997) and there is a
need to investigate in such research field.
Due to the different application domain character-
istics there is no universally accepted definition of
risk, even if the concepts of uncertainty (an event
may or may not happen) and loss (an event has
unwanted consequences or losses) are common to
many definition of risk (Rosenberg et al., 1999). Risk
exposure, the fundamental definition of risk manage-
ment, is then obtained combining the probability of
an unwanted event and the amount of loss that arise
when the unwanted event happens:
Re = p(unwanted event)* loss(unwanted event)
Many models have been proposed in the litera-
ture in order to gain knowledge about the better
way to manage risks (Boehm, 1991; Williams et al.,
1997; Rosenberg et al., 1999). In this paper we
will refer to the model shown in fig. 1 known as
“The SEI Risk Management Paradigm” conceived
to represent continuous risk management activities
that can be applied to any development process.
It is a knowledge management model that can be
applied in other contexts as well; we borrow the
concept of the SEI model to propose a risk model in
a distributed sensor network where the survaillance
of given environmental variables is required to avoid
or mitigate risks.
The purpose of the activities represented in the
model is:
Identify: consider risks before they become prob-
lems
Analize: convert data into decision-making informa-
tion
315
Caprio F., Aiello R. and Nota G. (2008).
ADAPTIVE RISK MANAGEMENT IN DISTRIBUTED SENSOR NETWORKS.
In Proceedings of the Tenth International Conference on Enterprise Information Systems, pages 315-320
DOI: 10.5220/0001738703150320
Copyright
c
SciTePress
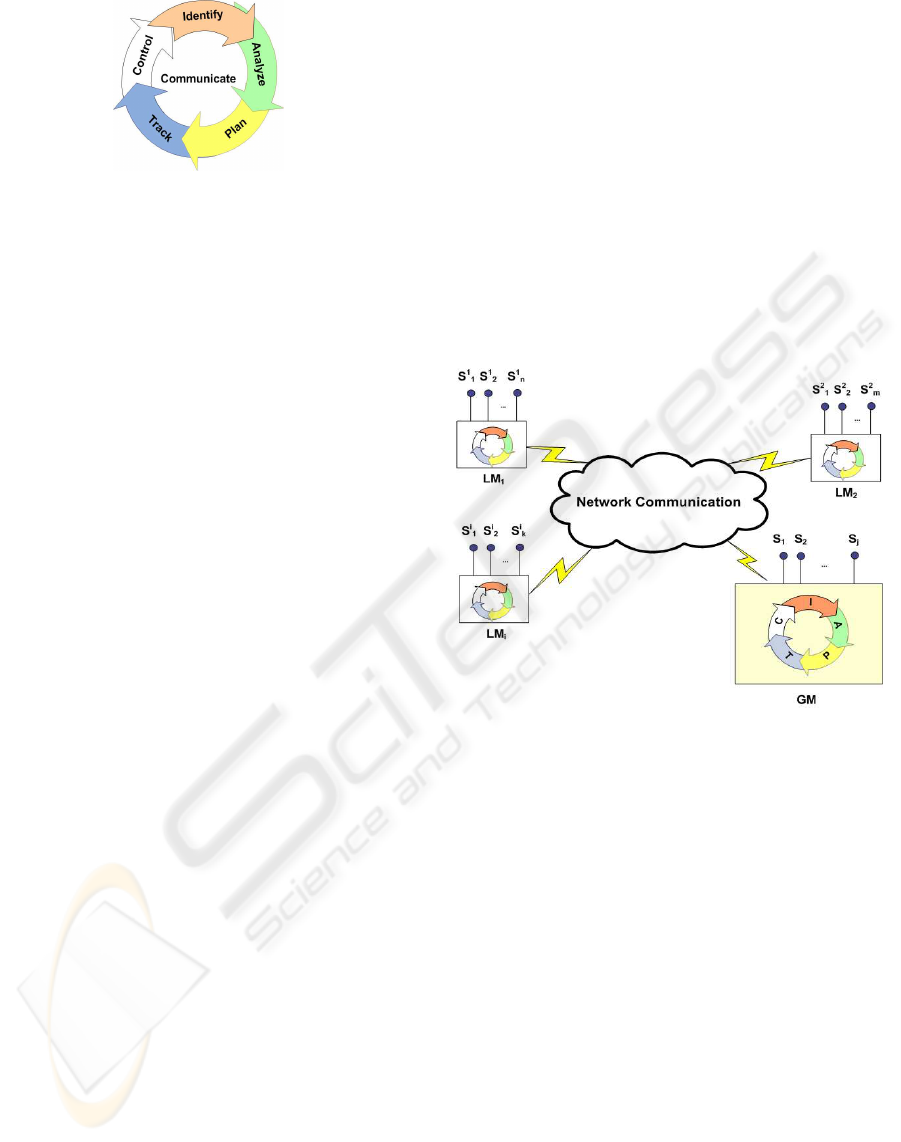
Figure 1: The SEI Risk Management Paradigm.
Plan: decide what should be done about a risk or a
set of related risks
Track: acquire risk status and record it
Control: decide for the best reaction when the risks
probability increases or when unwanted events
happens,
where the communication is a cross-activity in the
sense that data or information handled by a certain
activity can be communicated to the involved stake-
holders with the purpose of maintaining risk and risk
loss under control.
Our concern in this paper is to investigate on models
and technologies that can provide support to risk man-
agement systems in a geographically distributed envi-
ronment. The purpose is to provide a general setting
built on common principles and mechanisms so that
dynamic and adaptive risk management can be pur-
sued. The paper discusses an agent-based approach to
risk management in a distributed sensor network and
is structured as follows: in section 2 we model the
risk management in a distributed sensor network. The
framework described in section 3 maps this model
with a multiagent system while section 4 introduces
the description of the autonomous agent architecture.
2 RISK MODELING IN
DISTRIBUTED SENSOR
NETWORKS
A sensor network can be used in a wide scenario
of applications ranging from environmental monitor-
ing, climate control, structural monitoring, medical
diagnostics, disaster management or emergency re-
sponse (Culler et al., 2004). For their own nature,
these monitoring applications have to deal with intrin-
sic risk components that must be continuously con-
trolled. Therefore, an effective and efficient risk mod-
eling phase assumes great relevance for the preven-
tion and the mitigation of undesiderable and/or dan-
gerous events.
Note that, in order to keep the model as general as
possible, the concept of sensor is here used in a broad
sense, and indicates an individual unit that inputs data
(Wiener, 2000). Then, a sensor could be an electronic
device if we model environmental risk management
as well as an human being that collects data for an en-
terprise risk management system.
Figure 2 shows the model of a distributed sensor net-
work for risk management. Each local monitoring
node LM
1
, LM
2
,...LM
j
of the network is responsible
for the risk monitoring of a specific locations and is
connected to others by a communication infrastruc-
ture. Considerating the generic local monitoring node
LM
i
, sensors S
i
1
,...S
i
n
captures data from the environ-
ment and send them to the associated node for the data
analysis and risk evaluation. At a given time instant, a
Figure 2: A distributed sensor network.
node LM
i
manages one or more risk lifecycles that are
associated to specific risks to be monitored. A higher
level node, Global Monitoring GM, is responsible for
the global monitoring of the network; apart from the
typical functions assigned to local monitoring nodes,
it executes further functions:
• identifies risk types;
• analyzes risks;
• plans and configures LM
i
• assigns responsibilities to LM
i
• capture alarms that involve two or more local
monitoring nodes.
For example, an instance of the nodes shown in fig. 2
could be a sensor network part of a system that is
charged of supervising environmental risks of fire, air
pollution, etc. in a forest, and the nodes LM
1
, LM
2
and LM
n
are local monitors placed in particular areas
of the territory to put under surveillance various types
of risk. Each node is connected to sensors S
1
,...,S
k
measuring, for example, Temperature, Humidity,
ICEIS 2008 - International Conference on Enterprise Information Systems
316

CO
2
level and so on. A preliminary risk analysis
phase could establish that the risk of fire increases
when the temperature gets over a certain threshold
(e.g. 45 C
◦
) while humidity decreases. In this way,
local monitors evaluate at distinct time instants
the information retrieved from the sensor network,
estimating in real time the risk level and making
a mitigation action when a fire risk probability
increases (for example, sending an alarm to local
authorities).
3 A FRAMEWORK FOR RISK
MANAGEMENT
The framework proposed in this paper considers the
model presented in the previous section together with
a distributed network of smart autonomousagents that
provides automatic support to the model implemen-
tation. According to Wooldridge and Jennings def-
inition (Wooldridge and Jennings, 1995; Jennings,
2001), agents are computer-based systems having the
following characteristics:
• can operate autonomously, because theyhavecon-
trol both over their internal state and over their be-
haviour;
• have the capability to communicate and interact
with other agents;
• receive inputs from the environment and react to
them in order to satisfy the design goals;
• exhibit goal-directed behaviour by taking the ini-
tiative.
The distributed agent architecture fits well the general
model described in the previous section. Each local
monitoring node is now realized by a Local Moni-
toring Agent that aims to manage one or more risk
tipologies associated to the encompassing environ-
ment.
Because the number of possible risks for each consid-
ered domain can be very high, a single agent, able to
manage a great number of risks, could become very
complex. Furthermore, as the knowledge acquisition
for a single type of risk may involves a substantial
amount of communication with many others agents, it
is convenient introduce a simplified light agent, spe-
cialized to handle a single risk type: the Risk Monitor
Agent. Therefore, while an autonomous agent must
coordinate the global behaviour of all its Risk Mon-
itor Agents and decide the correct and more efficient
action to perform when risks arise, each Risk Monitor
Agent restricts its work to the monitoring of a single
risk tipology.
In the following, the generic Local Monitoring and
Risk Monitoring Agents will be denoted with A and
R respectively. Risk Monitor Agents are created by
the agent who own them on the basis of assigned
risk types, chosen among those registered during the
identification phase managed by the Global Monitor
Agent (G). For example, in the case of surveillance of
some environmental variables in a forest described in
the previous section, there are n agent A
1
, A
2
,...A
n
that
perform local monitoring. Each A
i
creates an agent R
devoted to evaluation of fire risk, another for air pol-
lution risk, and so on.
When R signals a critical situation, A must evaluate
the current state and take a decision in order to resolve
the problem or mitigate the risk. If not enough infor-
mation are available to decide autonomously, A could
require other information from neighbouring agents.
The identification and analysis of risk types is man-
aged by the agent G that, having the complete knowl-
edge of the initial planned agent distribution, instanti-
ates the network configuration. Then, the risk lifecy-
cle of a local agent A performs the following activi-
ties:
Identify: A receives by G the risk types under its re-
sponsibility and creates an agent R dedicated for
each risk type to monitor;
Analyse: an agent R evaluates the inputs from the
sensors and historical data exploiting the fuzzy
rules to eventually suggest a mitigation action;
Plan: the agent A uses data analyis received from R
to decide the better strategy to follow (e.g. plan a
mitigation action or start a cooperation with other
agents to “learn” more about );
Track: risk status data are collected by R and regis-
tered in the Historical Data Repository;
Control: A decides to handle the risk locally or to
perform an escalation action. It has a global
overview of all its identified risk types and estab-
lishes if there exists risk correlation between two
or more of them;
Communicate: the communication (internal
with/between Rs and external with other As) is
guaranteed through the sending and receiving of
messages.
The capabilities of an agent A are:
• generate a newlocal R, replicate or migrate a local
R to another A, split a local R in two or more parts,
merge two or more local Rs in a new one;
• accept or deny a remote replication or migration
of an agent R;
ADAPTIVE RISK MANAGEMENT IN DISTRIBUTED SENSOR NETWORKS
317
• maintain explicit belief models of itself and other
agents and be able to reason with incomplete, in-
consistent and uncertain information;
• have a set of capabilities (which can change dy-
namically) that permit to “learn from environ-
ment”;
The main features of the of the operator “replication”,
“migration”, “split” and “merge” together with the
motivation for their introduction are discussed below.
3.1 Replication
Replication allows multiple instances of the same R to
be created in order to share the new risk types with an-
other A. If A
i
, having a risk type R, asks for a support
to a remote A
j
, it can replicate its agent R to A
j
, shar-
ing its local knowledge. For example, if A
i
is evaluat-
ing the risk of a certain type of bacteric infection by
means of R
k
, A
i
can ask to the neighbour agent A
j
, that
monitors only cancer risks, to host a replication of R
k
in its own environment in order to collect information
about the same infection in a given surrounding area.
3.2 Migration
Agent “Migration” allows to move the complete R
environment from an agent A to another in order to
undertake a distribute decision. When an agent re-
ceives a new event and it has no possibility to evalu-
ate the correct action to perform the risk mitigation,
then it starts a speculative action ((Kitamura and Mu-
rao, 2004)) that evaluates if a cooperative action be-
comes necessary. In the cooperative action the agent
uses the Migration function to move its whole envi-
ronment (DB, Fuzzy Logic, Program Code, etc.) to a
neighbour agent.
Migration of Risk Monitor Agent is triggered when a
migration message is processed (sent by another agent
in the computation) or when a decision agent deter-
mines that the R should be migrated. When the A
lifecycle is expiring, it can also decide to migrate all
its Rs to the near A to avoid that the local knowledge
be lost.
3.3 Split and Merge
If the risk is too complicate to resolve or there is
a need to do analysis at a finer level, then A can
split R in two or more parts respectively with a sub-
risk to evaluate. Consider, for example, a scenario
where R receives the responsibility of collecting data
about Meningitis occurrences in a system that moni-
tors the risk of epidemies in a specific territory; the
analysis could reveal that the risk associated to a
pneumococcus meningitis epidemy is faster increas-
ing compared with those induced by meningococcus
or Haemophilus B. In this case, A can decide to split
R, isolating the cases of pneumococcus meningitis to
better evaluate this specific risk in the area.
On the contrary, if starting from the analysis of two
risks managed, for example, by R
1
and R
2
can be in-
ferred a new risk, A can merge R
1
and R
2
in R
3
. More-
over, after a migration or replication to a new envi-
ronment, same versions of the same risk type might
already exist; in this case, a merge can be performed
to save resources.
4 THE AUTONOMOUS AGENT
ARCHITECTURE
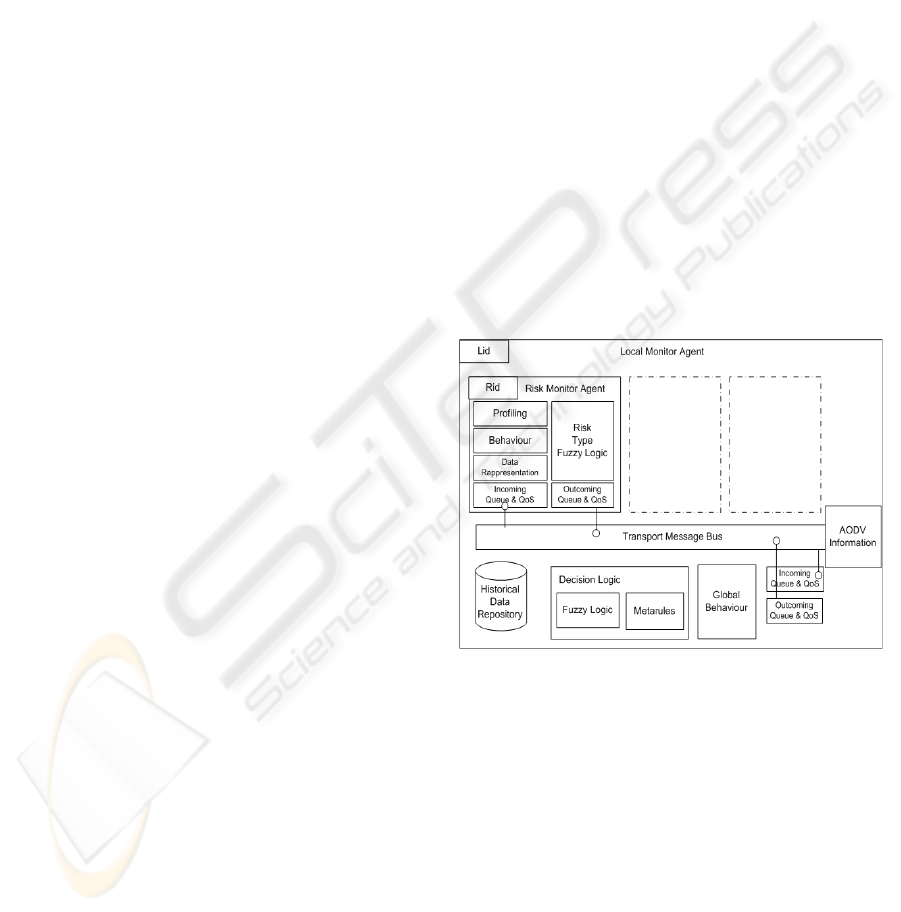
The architectural model of an Autonomous Agent is
shown in fig. 3. It includes a certain number of Rs
each one uniquely identified by its Rid, that combined
with Lid allows the retrieval of a Risk Monitor Agent
over the network.
Figure 3: The Architecture of a Local Monitoring Agent.
The role played by the components of an A is de-
scribed as follows. A Risk Monitor Agent, tracks risk
status and risk identification, uploading the content
of its captured data into the Historical Data Reposi-
tory. The Profiling of a Risk Monitor Agent specify
the characteristics of the risk type to handle. Local
Monitoring Agent can adopt different profiling strate-
gies for their R, based on the way profiles will be
used. Generally, they profile risk type but also pro-
cessing power, memory, storage, latency and band-
width, where messages are sent to and received from,
as well as the time spent to process or send a mes-
sage. On the basis of the profiled information, the
Decision Logic component decides how the risk mon-
ICEIS 2008 - International Conference on Enterprise Information Systems
318
itoring agents must be distributed. The Fuzzy Logic
component in the Local Monitor Agent is locally used
from each Risk Monitor Agent to evaluate the specific
risk type; R suggests a correct mitigation action that
in many cases can be more effective when the collab-
oration with other Rs is tight. The final mitigation ac-
tion is performed from the A that, on the basis of the
historical information and the R suggestion, starts the
Decision Process. The decision process is based on
the Fuzzy logic for the Risk Type evaluation and on
the Meta Rules for the infrastructure environment and
profiling evaluation. Fig. 4 illustrates the macro deci-
sion process in an Autonomous Agent. The Transport
Figure 4: The decision process of an Autonomous Agent.
Message Bus enables both the internal and external
communication. Message priorities based on the as-
sociated weighed risk are also considered to manage
the message queue allowing for urgent reconfigura-
tion messages and QoS.
From the consideration that risks can be very often
well evaluated by observing phenomena happened in
neighbouring areas, such as fires, inundations, epi-
demics and so on, AODV algorithm is selected to al-
low communication. This algorithm can be used in
dynamic and mobile network where the neighbour list
can change every time and it builds routes between
nodes only as desired by source nodes.
5 CONCLUSIONS
The paper proposes a framework for an adaptive risk
management in a distributed sensor network that con-
siders an abstract model together with an agent-based
distributed system that realizes it. The system is com-
posed of a certain number of agents able to proac-
tively monitor the risks and adapt their behaviour,
“learning” from the environment the more effective
mitigation action for each risk.
The agent decisional process uses fuzzy rules and
fuzzy logic inference to map human concepts and
rules, simulating reasoning mechanisms as proposed
in (He et al., 2003; Chrysanthakopoulos et al., 2004).
The introduction of light agents devoted to risk moni-
toring allows the system to decompose the complexity
of risks handling. Moreover, the capability of a Local
Monitoring Agent to split and merge simpler agents
allows to focus the attention at the right granularity
level.
The presented framework is part of a project for the
supervising of environmental risks in specific areas
(called cluster) of “Regione Campania” in the South
of Italy. The project, funded by POR Campania 2000-
2006 Misura 6.2 “Societ`a dell’Informazione”, is al-
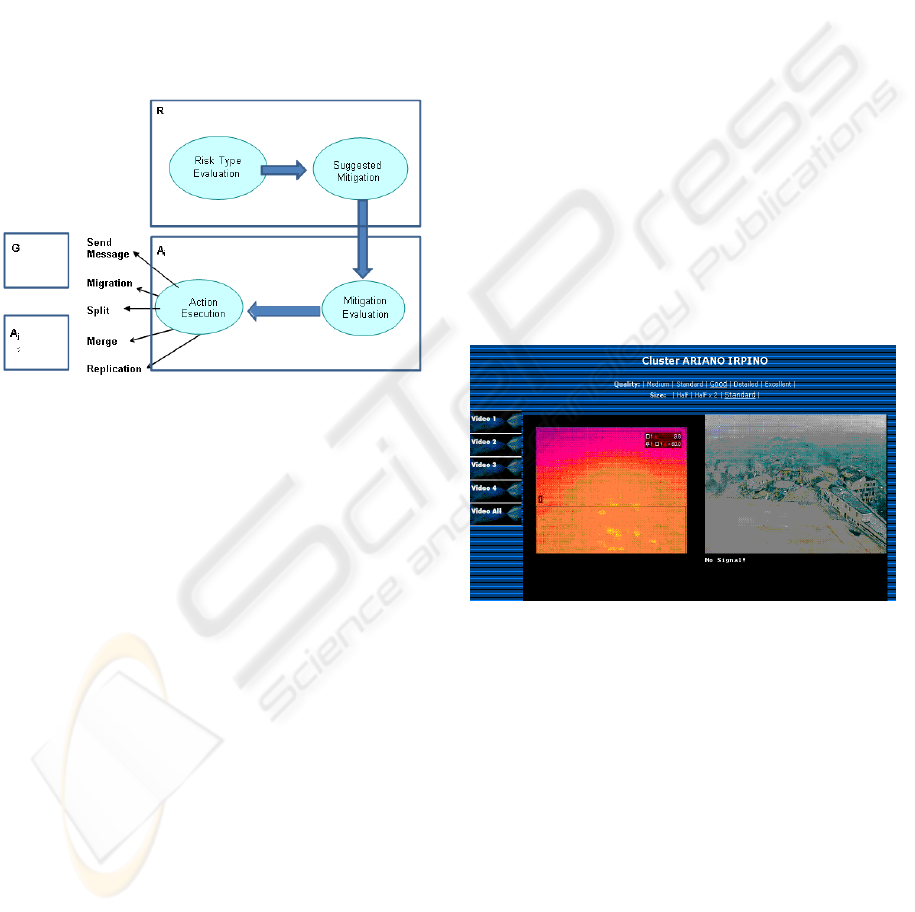
most completed. Some hw/sw devices concerning the
video sensor network have already been installed for
each cluster and include day&nigth and/or infrared
cameras (fig. 5) together with sensors for meteo sur-
vey, electromagnetism, earthquake, air pollution, etc.
responsible for the capture of data that local monitor-
ing agents will evaluate. The implementation of our
framework is in progress and an early prototype is ex-
pected in the next months.
While the proposed model provides some important
Figure 5: An infrared termocamera for the video surveil-
lance of a cluster.
benefits deriving especially from the automation of
several activities of the risk lifecycle, limitations ex-
ist. As the risk management strategy is defined by
humans, failures may be latent in the system and the
identification of errors or mistakes can be underevalu-
ated and hidden in the multiagent system. They must
be considered as further risk types difficult to identify
and resolve. Furthermore, the decisional behaviour
of agents contains itself a certain degree of risk that
must be considered in the implementation phase as
suggested in (Vytelingum et al., 2004; Lorenz et al.,
2005).
ADAPTIVE RISK MANAGEMENT IN DISTRIBUTED SENSOR NETWORKS
319

REFERENCES
Boehm, B. W. (1991). Software risk management: Princi-
ples and practices. IEEE Software, 08(1):32–41.
Camara, M. S., Kermad, L., and Mhamedi, A. E. (2006).
Risk prediction in erp projects: Classification of
reengineered business processes. In CIMCA ’06: Pro-
ceedings of the International Conference on Compu-
tational Inteligence for Modelling Control and Au-
tomation and International Conference on Intelli-
gent Agents Web Technologies and International Com-
merce, page 213, Washington, DC, USA. IEEE Com-
puter Society.
Chrysanthakopoulos, G., Fox, W. L. J., Miyamoto, R. T., II,
R. J. M., El-Sharkawi, M. A., and Healy, M. (2004).
A fuzzy-logic autonomous agent applied as a supervi-
sory controller in a simulated environment. IEEE T.
Fuzzy Systems, 12(1):107–122.
COSO (2004). Enterprise risk management - integrated
framework.
Culler, D., Estrin, D., and Srivastava, M. (2004). Guest
editors’ introduction: Overview of sensor networks.
Computer, 37(8):41–49.
Grabowski, M., Merrick, J. R. W., Harrald, J. R., Mazzuchi,
T. A., and van Dorp, J. R. (2000). Risk modeling in
distributed, large-scale systems. IEEE Transactions
on Systems, Man, and Cybernetics, Part A, 30(6):651–
660.
Han, W.-M. and Huang, S.-J. (2007). An empirical analy-
sis of risk components and performance on software
projects. Journal of Systems and Software, 80(1):42–
50.
He, M., fung Leung, H., and Jennings, N. R. (2003). A
fuzzy-logic based bidding strategy for autonomous
agents in continuous double auctions. IEEE Trans.
on Knowl. and Data Eng., 15(6):1345–1363.
Institute of Risk Management (2002). A Risk Management
Standard.
Jennings, N. R. (2001). An agent-based approach for
building complex software systems. Commun. ACM,
44(4):35–41.
Kitamura, Y. and Murao, T. (2004). Risk management
methods for speculative actions. In AAMAS ’04: Pro-
ceedings of the Third International Joint Conference
on Autonomous Agents and Multiagent Systems, pages
1250–1251, Washington, DC, USA. IEEE Computer
Society.
Lorenz, M., Gehrke, J. D., Langer, H., Timm, I. J., and
Hammer, J. (2005). Situation-aware risk management
in autonomous agents. In CIKM ’05: Proceedings
of the 14th ACM international conference on Infor-
mation and knowledge management, pages 363–364,
New York, NY, USA. ACM.
Project Management Institute (2004). A Guide to the
Project Management Body of Knowledge (PMBOK
Guide) - Third Edition.
Rosenberg, L. H., Hammer, T., and Gallo, A. (1999). Con-
tinuous risk management at nasa. In Applied Soft-
ware Measurement / Software Management Confer-
ence, San Jose, California.
Schaller, M. and Vaz, A. (23-25 Mar 1997). Derma: a
distributed enterprise risk management architecture.
Computational Intelligence for Financial Engineering
(CIFEr), 1997., Proceedings of the IEEE/IAFE 1997,
pages 22–28.
Vytelingum, P., Dash, R. K., David, E., and Jennings, N. R.
(2004). A risk-based bidding strategy for continu-
ous double auctions. In de Mntaras, R. L. and Saitta,
L., editors, European Conference on Artificial Intelli-
gence, pages 79–83. IOS Press.
Wiener, N. (2000). Cybernetics: Or Control and Communi-
cation in Animal and the Machine. MIT Press, Cam-
bridge, MA, USA.
Williams, R., Walker, J., and Dorofee, A. (1997).
Putting risk management into practice. IEEE Softw.,
14(3):75–82.
Wooldridge, M. and Jennings, N. (1995). Intelligent
Agents: Theory and Practice. The Knowledge Engi-
neering Review, 10(2):15/152.
ICEIS 2008 - International Conference on Enterprise Information Systems
320
