
A SURVEY OF SENSOR NETWORK AND RELATED ROUTING
PROTOCOLS
O. P. Vyas, M. K. Tiwari
S. O. S. in Computer Science, Pt. Ravishankar Shukla University, Raipur, India
Chandresh Pratap Singh
Department of Computer Science/IT, Dr. C. V. Raman University, Kargi Road – Kota, Bilaspur, India
Keywords: Routing Protocols.
Abstract: Recent advances in wireless sensor networks have led to many new protocols specifically designed for
sensor networks where energy awareness is an essential consideration. Most of the attention, however, has
been given to the routing protocols since they might differ depending on the application and network
architecture. Tiny sensor nodes create sensor network. These nodes are severely constrained by energy,
storage capacity and computing power. The prominent task of this network is to design proficient routing
protocols for to make the node’s life last longer. In this paper, we first analyze the requirements of sensor
networks and its architecture. Then, we enlighten the existing routing protocols for sensor networks and
present a critical analysis of these protocols. The paper concludes with open research issues. At the end of
this paper, we compare and contrast these protocols.
1 INTRODUCTION
Recent advances in micro-electro-mechanical
systems (MEMS) and low power and highly
integrated digital electronics have led to the
development of micro sensors. Such sensors are
generally equipped with data processing and
communication capabilities. The sensing circuitry
measures ambient conditions related to the
environment surrounding the sensor and transform
them into an electric signal. Processing such a signal
reveals some properties about objects located and/or
events happening in the vicinity of the sensor. The
sensor sends such collected data; usually via radio
transmitter (1), to a command center (sink) either
directly or through a data concentration center (a
gateway). A natural architecture for such
collaborative distributed sensors is a network with
wireless links that can be formed among the sensors
in an ad hoc manner.
Networking unattended sensor nodes are expected to
have significant impact on the efficiency of many
military and civil applications such as combat field
surveillance, security and disaster management.
These systems process data gathered from multiple
sensors to monitor events in an area of interest. For
example, in a disaster management setup, a large
number of sensors can be dropped by a helicopter.
Networking these sensors can assist rescue
operations by locating survivors, identifying risky
areas and making the rescue crew more aware of the
overall situation. Such application of sensor
networks not only can increase the efficiency of
rescue operations but also ensure the safety of the
rescue crew.
On the military side, applications of sensor networks
are numerous. For example, the use of networked set
of sensors can limit the need for personnel
involvement in the usually dangerous
reconnaissance missions. In addition, sensor
networks can enable a more civic use of landmines
by making them remotely controllable and target-
specific in order to prevent harming civilians and
animals. Security applications of sensor networks
include intrusion detection and criminal hunting.
However, sensor nodes are constrained in energy
supply and bandwidth. These challenges necessitate
energy-awareness at all layers of networking
protocol stack. The issues related to physical and
link layers are generally common for all kind of
215
P. Vyas O., K. Tiwari M. and Pratap Singh C. (2008).
A SURVEY OF SENSOR NETWORK AND RELATED ROUTING PROTOCOLS.
In Proceedings of the Third International Conference on Software and Data Technologies - PL/DPS/KE, pages 215-220
DOI: 10.5220/0001871802150220
Copyright
c
SciTePress
sensor applications. At the network layer, the main
aim is to find ways for energy efficient route setup
and reliable relaying of data from the sensor nodes
to the sink so that the lifetime of the network is
maximized. Routing in sensor networks is very
challenging due to several characteristics that
distinguish them from contemporary communication
and wireless ad-hoc networks. First of all, it is not
possible to build a global addressing scheme for the
deployment of sheer number of sensor nodes.
Second, in contrary to typical communication
networks almost all applications of sensor networks
require the flow of sensed data from multiple
regions (sources) to a particular sink. Third,
generated data traffic has significant redundancy in
it since multiple sensors may generate same data
within the vicinity of a phenomenon. Such
redundancy needs to be exploited by the routing
protocols to improve energy and bandwidth
utilization. Fourth, sensor nodes are tightly
constrained in terms of transmission power, on-
board energy, processing capacity and storage and
thus require careful resource management. Due to
such differences, many new algorithms have been
proposed for the problem of routing data in sensor
networks. These routing mechanisms have
considered the characteristics of sensor nodes along
with the application and architecture requirements.
Almost all of the routing protocols can be classified
as data-centric, hierarchical or location-based. Data-
centric protocols are query-based and depend on the
naming of desired data, which helps in eliminating
many redundant transmissions. Hierarchical
protocols aim at clustering the nodes so that cluster
heads can do some aggregation and reduction of data
in order to save energy. Location-based protocols
utilize the position information to relay the data to
the desired regions rather than the whole network. In
this paper, we will explore the routing protocols for
sensor networks developed in recent years. Each
routing protocol is discussed under the proper
category. Our aim is to help better understanding of
the current routing protocols for wireless sensor
networks and point out open issues that can be
subject to further research. The paper is organized as
follows. In the section 2, we will briefly summarize
the system architecture design issues for sensor
networks and their implications on data routing. We
then set our work apart from prior surveys on sensor
networks. In the section 3, explores some prominent
routing protocols of sensor network. In the Section
4, comparison of the routing protocols with a
comparative summary of the surveyed approaches
and points out open research problems. Finally
section 5, concludes this paper.
2 SENSOR NETWORK
ARCHITECTURE AND
REQUIREMENTS
Before we discuss the routing protocols, we present
sensor network architecture (10) and requirements.
A sensor network can, in practice, be composed of
tens to thousands of sensor nodes, which are
distributed in a wide area. These nodes form a
network by communicating with each other either
directly or through other nodes. One or more nodes
among them will serve as sink(s) that are capable of
communicating with the user either directly or
through the existing wired networks.
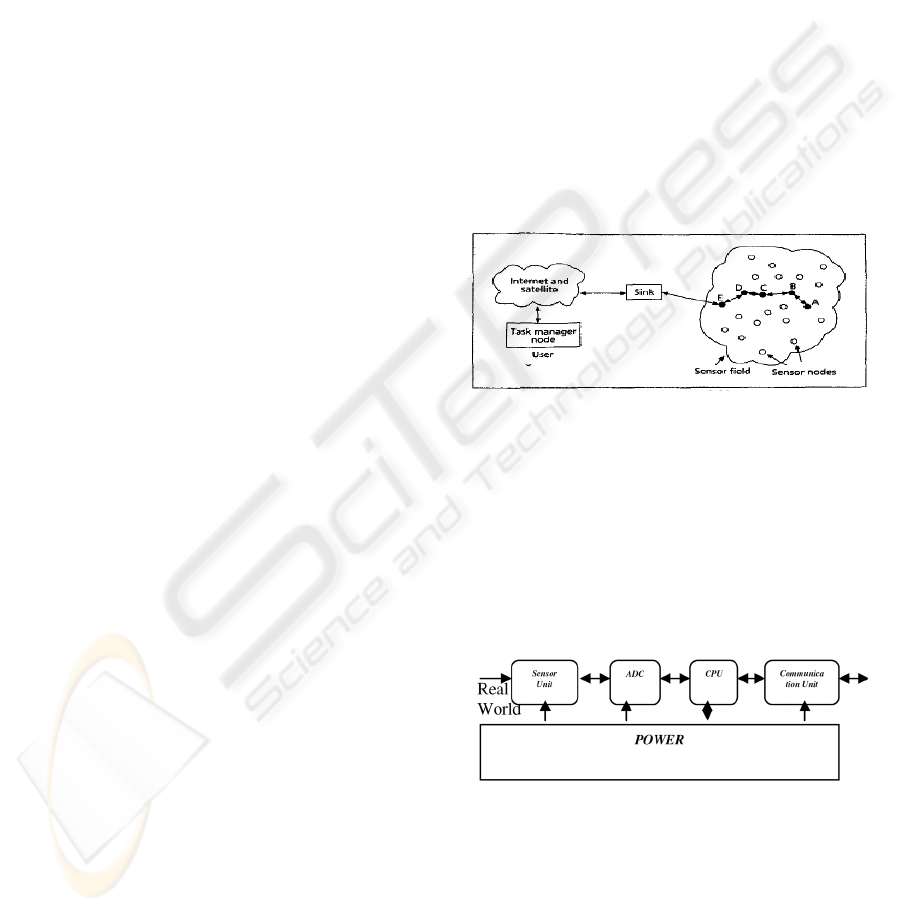
Figure 1: Sensor nodes scanered in a sensor field.
The sensor nodes are usually scattered in a sensor
field as shown in above figure 1. Each of these
sensor nodes has the capabilities to collect the data
and route data back to the sink. Data are routed back
to the sink by a multihop infrastructureless
architecture through the sink as shown in above
figure. The sink may communicate with the task
manger node via Internet or satellite.
Figure 2: Components of Sensor Node.
Figure. 2 shows components of sensor node in which
each node typically consist of the five components:
sensor unit, analog unit, analog digital convector
(ADC), central processing unit (CPU), power unit
and communication unit. They are assigned with
different tasks. The sensor unit is responsible for
collecting information as the ADC requests, and
returning the analog data it sensed. ADC is a
ICSOFT 2008 - International Conference on Software and Data Technologies
216

translator that tells the CPU what the sensor unit has
sensed, and also informs the sensor unit what to do.
Communication unit is tasked to receive command
or query from, and transmit the data from CPU to
the outside world. CPU is the most complex unit. IT
interprets the command or query to ADC, monitors
and controls power if necessary, processes received
data, computes the next hop to the sink, etc. Many
other units may be added for special usage, but the
above five are the most important ones and are
included in every sensor node.
Following are some of the features and requirements
of a sensor network -
• Varying network size – The size of a sensor
network can vary from one to thousands of
nodes.
• Long lifetime network – An important
characteristic of a sensor network is to design
and implement efficient protocols so that the
network can last as long as possible.
• Self – Organization – Sensor nodes should be
able to form a network automatically without
any external configuration.
• Query and re – tasking – The user should be
able to query for special events in a specific
area, or remove obsolete tasks from specific
sensors and assign them with new tasks. This
saves a lot of energy when the tasks change
frequently.
• Cooperation/ Data aggregation – Sensor nodes
should be able to work together and aggregate
their data in a meaningful way. This could
improve the network efficiency.
• Node Capabilities – In a sensor network,
different functionalities can be associated with
the sensor nodes. These special sensors either
deployed independently or the functionality
can be included on the normal sensors to be
used on demand. Reading generated from
these sensors can be at different rates, subject
to diverse quality of service constraints and
following multiple data delivery models, as
explained earlier. Therefore, such a
heterogeneous environment makes data
routing more challenging.
3 ROUTING PROTOCOLS
In this section, we classify the routing protocols (9)
for sensor networks first and then analyze the
existing routing protocols.
A. Classification of the Routing Protocols
Depending on how the sender of a message gains a
route to the receiver, routing protocol can be
classified into three categories, namely, proactive,
reactive and hybrid protocols. In proactive protocols,
all routes are computed before they are really
needed, while in reactive protocols routes are
computed on demand. Hybrid protocols use a
combination of these two ideas. Since sensor nodes
are resource poor, and number of nodes in the
network could be very large, sensor nodes cannot
afford the storage space for “huge” routing tables.
Therefore reactive and hybrid routing protocols are
attractive in sensor networks. According to the
participating style routing protocols can be classified
into three categories, namely, direct communication,
flat and clustering protocols.
B. Existing Routing Protocols
I. Low Energy Adaptive Clustering Hierarchy
(LEACH)
LEACH is a clustering – based protocol that utilizes
randomized rotation of the cluster – heads to evenly
distribute the energy load among the sensor nodes in
the sensor network. It assumes that the base station
is fixed and located far from the sensors and all
nodes in the network are homogenous and energy –
constrained. The main energy saving of LEACH
protocols comes from the combination of data
compression and routing. It (i) employs localized
coordination to improve the scalability and
robustness, (ii) uses data fusion to reduce the amount
of information transmitted between the sensor nodes
and a given sink, and (iii) uses dynamic cluster –
heads mechanism to avoid the energy depletion of
selected cluster – heads.
LEACH provides sensor networks with many good
features, such as clustering architecture, localized
coordination and randomized rotation of cluster –
heads; however, it suffers from the following
problems:
• The nodes on the route from a hot spot to the
base station might drain their battery soon,
which is known as “hot spot” problem.
A SURVEY OF SENSOR NETWORK AND RELATED ROUTING PROTOCOLS
217

• It cannot be deployed in time critical
applications.
• The assumption about the sink may
not be practical.
II. Power – Efficient Gathering in Sensor
Information Systems (PEGASIS)
PEGASIS (4) is a chain – based power efficient
protocol based on LEACH. It is near optimal
protocol under the following assumption about the
network.
All nodes have location information about
all other nodes and each of them has the
capability of transmitting data to the base
station directly.
Sensor nodes are immobile.
Figure 3: Token passing approach in PEGASIS.
Because each node has global knowledge of the
network, the chain can be constructed easily by
using a greedy algorithm. To balance the overhead
involved in communication between the leaders (s3
is the leader in above figure) and sink, each node in
the chain takes turn to be the leader. Nodes fuse the
received data with their own data when data are
transmitted in the chain.
PEGASIS outperforms LEACH by eliminating the
overhead of dynamic cluster formation, minimizing
the sum of distances that non – leader nodes must
transmit and limiting the number of transmissions.
However, PEGASIS has the same problem as
LEACH does, (about the sink) because of their
common assumptions. Furthermore, it requires
global information of the network known by each
sensor node. This does not scale well and is not
suitable for sensor networks where such global
knowledge is nit easy to obtain.
III. Threshold Sensitive Energy Efficient Sensor
Network Protocol (TEEN)
TEEN (8) is a cluster- based routing protocol based
on LEACH. Before we go into details of TEEN, let’s
have a look at the definition and assumptions used in
TEEN –
Definition
Hard Threshold (HT) – The absolute value
of the attribute beyond which, the node
sensing this value must switch on its
transmitter and report it.
Soft Threshold (ST) – A change in the
value of the sensed attribute, which
triggers the node, to switch on its
transmitter and report sensed data.
Assumptions
The network is composed of a base station
and sensor nodes with the same initial
energy.
The base station has a constant power
supply and can transmit with high power
to all the nodes directly.
TEEN employs LEACH’s strategy to form clusters,
so all the issues that are un – addressed by LEACH
are left un – addressed by TEEN as well. In addition
to LEACH’s drawbacks TEEN suffers from the
following disadvantages:
Cluster heads have to leave their
transmitter on all the time and wait for data
sent from other nodes.
A node’s time slot is wasted if it does not
have data to send, while other nodes have
to wait for their time slots.
There is no mechanism to distinguish a
node, which does not sense a “big” change
from a dead or failed node.
IV. Sensor Protocols for Information Via
Negotiation (SPIN)
SPIN (6) is family of protocols that efficiently
disseminate information among sensor nodes in
energy – constrained sensor network, assuming all
of them are potential sink. Every node uses meta –
data, i. e. high – level data descriptors, to name their
data and uses negotiations to eliminate the redundant
data transmissions throughout the network.
Conventional data dissemination approaches, e. g.
classic flooding and gossiping, have three problems,
namely, implosion, overlap, and resource blindness.
SPIN solves these problems by using data
negotiation and resource – adaptive algorithms.
Before any data is really transmitted, a node
performs meta – data negotiations. Exchanging
ADV and REQ messages between the sender and
receiver does the negotiations. In addition, SPIN
checks the current energy level of nodes and adapts
the protocol it is running based on how much energy
remains. Simulation results show that SPIN is more
ICSOFT 2008 - International Conference on Software and Data Technologies
218

energy – efficient than flooding or gossiping while
distributing data.
SPIN disadvantages are clear. First of all, it is not
scalable. Secondly, the nodes around a sink could
deplete their battery quickly if the sink is interested
in too many events. Finally, events are always sent
throughout the network.
V. Directed Diffusion
Directed Diffusion (5) is a data – centric routing
algorithm in which all communication is for named
data.. It consists of four elements – interests, data
messages, gradients and reinforcements. An interest
is a task description, which is named by, for instance
a list of attribute – value pairs that describe a task. A
gradient specifies both data rate and the direction
along which events should be sent. Reinforcement is
used to select a single path from multiple paths.
Although this protocol achieves some energy saving,
it also has problems. For instance, to implement data
aggregation, it employs time synchronization
technique, which is not easy to realize in a sensor
network. One other problem in data aggregation is
the overhead involved in recording information.
VI. Flooding and Gossiping
Flooding and gossiping (15) are two classical
mechanisms to relay data in sensor networks without
the need for any routing algorithms and topology
maintenance. In flooding, each sensor receiving a
data packet broadcasts it to all of its neighbors and
this process continues until the packet arrives at the
destination or the maximum number of hops for the
packet is reached. On the other hand, gossiping is a
slightly enhanced version of flooding where the
receiving node sends the packet to a randomly
selected neighbor, which picks another random
neighbor to forward the packet to and so on.
Flooding has several drawbacks. Such drawbacks
include implosion caused by duplicated messages
sent to same node, overlap when two nodes sensing
the same region send similar packets to the same
neighbor and resource blindness by consuming large
amount of energy without consideration for the
energy constraints. Gossiping avoids the problem of
implosion by just selecting a random node to send
the packet rather than broadcasting. However, this
cause delays in propagation of data through the
nodes.
VII. Maximum Lifetime Energy Routing
Chang et al. (16) presents an interesting solution to
the problem of routing in sensor networks based on a
network flow approach. The main objective of the
approach is to maximize the network lifetime by
carefully defining link cost as a function of node
remaining energy and the required transmission
energy using that link. Finding traffic distribution is
a possible solution to the routing problem in sensor
networks and based on that, comes the name
“maximum lifetime energy routing”. The solution to
this problem maximizes the feasible time the
network lasts. In order to find out the best link
metric for the stated maximization problem, two
maximum residual energy path algorithms are
presented and simulated. The two algorithms differ
in their definition of link costs and the incorporation
of nodes’ residual energy.
By using Bellman-Ford shortest path algorithm for
the above link costs, the least cost paths to the
destination (gateway) are found. The least cost path
obtained is the path whose residual energy is largest
among all the paths. The algorithms utilizing these
link costs are compared to Minimum transmitted
energy (MTE) algorithm, which considers ij e as the
link cost. Simulation results show that the proposed
maximum residual energy path approach has better
average lifetime than MTE for both link cost
models. This is due to the absolute residual energy
metric that MTE uses. The newly proposed metrics
are concerned with relative residual energy that
reflects the forecasted energy consumption rate.
4 COMPARISON
In this section, we compare and contrast the routing
protocols for sensor networks, discussed above, with
respect to a few metrics we identified.
As we observe LEACH, PEGASIS and TEEN are
protocols with similar features designed with the
similar idea. It is hard to say one protocol is better
than another one because sensor network are
application specific. For example, SPIN should be
one of the best protocols for application deployed in
a small
sensor network in which no mobility is
required and each node can serve as a sink.
Based on the analysis of the above protocols, we
believe that some of the desirable features of a good
routing algorithm for sensor networks are:
Dynamic clustering architecture – It
prevents cluster heads from depleting their
power soon and hence extends the
network’s lifetime.
Data fusion – If nodes could classify and
aggregate data, it helps in efficient query
A SURVEY OF SENSOR NETWORK AND RELATED ROUTING PROTOCOLS
219

processing and decreases network overhead
dramatically. This saves energy.
Randomizing path choice – If a routing
algorithm can support multiple paths to a
destination with low overhead, it could
help balancing the network load and
tolerating the failure of nodes.
Thresholds for sensor nodes to transfer
sensed data – Given good threshold it may
solve “hot spot” problem.
Thresholds for sensor nodes to relay data –
Determining appropriate thresholds of
energy and time delay to relay data would
help in elongating nodes’ lifetime.
5 CONCLUSIONS
Sensor networks that are capable of sensing various
physical phenomena will become ubiquitous in the
near future. Hence, designing efficient routing
protocols for sensor networks that suits sensor
networks serving various applications is important.
In this paper, we identified some of the important
desired features of routing protocols for sensor
networks and also compared and contrast the
existing routing protocols.
REFERENCES
I. Akyildiz, W. Su, Y. Sankarasubramaniam, and E.
Cayirci, “A survey on Sensor Networks,” IEEE
Communication Magazine, August 2002.
B. Chen, K. Jamieson, H. Balakrishan, and R. Morris,
“Span: an Energy – Efficient Coordination Algorithm
for Topology Maintenance,” in Proc. of the 7th Annual
International Conf. On Mobile Computing and
Networking, July 2001.
W. Heinzelman, J. Kulik, and H. Balakrishnan,
“Negotiation – Based Protocols for Disseminating
Information in Wireless Sensor Network,” in Proc. of
the 5th Annual ACM/IEEE International Conf. on
Mobile Computing and Networking, 1999.
S. Lindsey and C. Raghavendra, “PEGASIS – Power
Efficient Gathering in Sensor Information Systems,”
in International Conf. on Communications, 2001.
C. Intanagonwiwat, R. Govindan, D. Estrin, J.
Heidermann, and F. Silva, “Directed Diffusion for
Wireless Sensor Networking,” IEEE/ACM
Transactions on Networking, Feb 2003.
A. Perrig, R. Szewczyk, V. Wen, D. Culler, and J. D.
Tygar, “SPINS: Security Protocols for Sensor
Networks,” in Proc. of the 7th Annual International
Conf. on Mobile Computing and Networking, July
2001.
K. Sohrabi, J. GAO, V. Ailawadhi, and G. Pottie,
“Protocols for Self – Organization of a Wireless
Sensor Network,” IEEE Personal Communications,
2000.
A. Manjeshwar and D. Agrawal, “TEEN: a routing
protocol for Enhanced Efficiency in Wireless Sensor
Network,” in International Proc. of the 15th Parallel
and Distributed Processing Symposium, 2001.
Qiangfeng Jiang, and D. Manivannan, “Routing Protocols
for Sensor Network,” IEEE Personal Communications,
2004.
C. Shen, C. Srisathapomphat and C. Jaikaeo, “Sensor
Information Networking Architecture and
Applications,” IEEE Personal Communications, Aug.
2001.
G. J. Pottie, and W. J. Kaiser, “Wireless Integrated
Network Sensors,” Communication ACM, May 2000.
J. M. Kahn, R. H. Katz, and K. S. J. Pister, “Next Century
Challenges: Mobile Networking for Smart Dust,”
Proceeding ACM Mobicom’99, 1999.
F. Ye, S. Lu. And L. Zhang, “Gradient broadcast: A
robust, long – lived large sensor network,” Tech. Rep.,
2001.
David Culler, Deborah Estrin and Mani Srivastava, “An
overview of Sensor Networks,” August 2004.
S. Hedetniemi and A. Liestman, “A survey of gossiping
and broadcasting in communication networks,”
Networks, 1988.
J. H. Chang and L. Tassiules, “Maximum Lifetime
Routing in Sensor Network,” in the proceedings of the
Advanced Telecommunications and information
distribution Research Program, March 2000.
ICSOFT 2008 - International Conference on Software and Data Technologies
220
