
AN EFFICIENT MULTIPLICATION ALGORITHM USING
BINOMIAL RESIDUE REPRESENTATION
Yin Li
Institute of Information Security, Shanghai jiaotong University, Shanghai 200240, China
Christophe Negre
Team DALI/ELIAUS, University of Perpignan, France
Keywords:
Finite Field, Multiplication, Montgomery, Binomial residue representation.
Abstract: In this paper, we propose an extension of the algorithm proposed by Bajard, Imbert and Negre in (Bajar et al.,
2006), refered as BIN algorithm. We use binomial residue representation of field elements instead of the
Lagrange representation of (Bajar et al., 2006). Specifically, every elements in F
p
k
is represented by a set
of residue modulo fixed binomials. We propose two versions of our algorithm, one in general form with a
sub-quadratic complexity equal to O(k
1.5
) operations in F
p
. The second one is optimized with the use of FFT.
In this case the cost is O(klog(k)) operations in F
p
. For fields GF(p
k
) suitable for elliptic curve cryptography
our algorithm roughly improves the time delay of (Bajar et al., 2006) by 45%.
1 INTRODUCTION
Efficient implementation of finite field arithmetic is
an important pre-requisite for cryptography and cod-
ing theory (Lidl and Niederreiter, 1994). Specifically
this is the case for elliptic curve cryptography (ECC),
proposed independently by Koblitz (Koblitz, 1987)
and Miller (Miller, 1986). In ECC, the most used and
also the most costly field operations is the multiplica-
tion.
During the past few years, more and more people
believe that elliptic curve defined over F
p
k
is better
than F
2
k
and F
p
in efficiency point of view in software
environment. Many works (Bailey and Paar, 1998;
Lim and Hwang, 2000) have shown that F
p
k
is a suit-
able choice for computer software implementation.
In 2006, Bajard, Imbert and Negre (Bajar et al.,
2006) proposed an efficient multiplication algorithm
for F
p
k
using Lagrange representation (we will refer
to it as the BIN algorithm). The BIN algorithm only
needs O(k) multiplications in F
p
. This algorithm is
very efficient in hardware, but in software, it is not so
efficient. Indeed it also needs O(k
2
logk) additions in
F
p
. When p has size of 32 bits which is an interesting
case in software environment, multiplication in F
p
is
only twice slower than addition in software platform.
So O(k
2
logk) additions cause too much time delay in
software implementation.
In this paper, we will use an extended form of La-
grange representation used in (Bajar et al., 2006), the
binomial residue representation, for field representa-
tion.
Using a strategy similar to BIN algorithm through
our binomial residue representation, we can reduce
the number of addition balanced by the cost of in-
creasing a few number of multiplications in F
p
.
Specifically, in our algorithm multiplications and ad-
ditions are only in sub-quadratic number. This en-
sures that our algorithm is faster in software imple-
mentation.
The rest of this paper is organized as follows. In
Section 2, we briefly recall the Lagrange representa-
tion and then give the definition of binomial residue
representation. In Section 3, we present the binomial
residue multiplication algorithm in a general and opti-
mized form. In Section 4 we evaluate the complexity
of our approach and compare it with other methods
for field multiplication. We then briefly conclude and
give some further perspectives of this work.
319
Li Y. and Negre C. (2008).
AN EFFICIENT MULTIPLICATION ALGORITHM USING BINOMIAL RESIDUE REPRESENTATION.
In Proceedings of the International Conference on Security and Cryptography, pages 319-324
DOI: 10.5220/0001924503190324
Copyright
c
SciTePress

2 BINOMIAL RESIDUE
REPRESENTATION
A finite field F
p
k
can be seen as the set of polynomi-
als in F
p
[x] with degree less than k. Arithmetic opera-
tion in F
p
k
, i.e., addition, multiplication or inversion,
consists to perform it modulo an irreducible polyno-
mial P ∈ F
p
[x] of degree k. The most used operations
in cryptographic protocol are addition and multiplica-
tion. The addition is just a simple addition of poly-
nomial in F
p
[x]. To multiply two elements A(x) and
B(x) modulo P, it requires to first compute the prod-
uct C = A× B and then to reduce C modulo P. This
operation is in general more costly than an addition,
and thus it should be performed efficiently.
Optimal extension field. A strategy to simplify the
reduction process consists to choose P as sparse as
possible. For example in OEF (Bailey and Paar, 1998)
they take P with binomial form. In this case the reduc-
tion modulo P consists simply to add the upper part to
the lower part of C.
Lagrange representation approach (Bajar
et al., 2006). Another interesting approach for
modular multiplication is the Montgomery algo-
rithm (cf. (Montgomery, 1985) for the integer
version). Given two polynomials A and B of
degree less than k, Montgomery algorithm com-
putes A × B × Φ
−1
mod P where Φ is a constant
polynomial often chosen as Φ = x
k
.
Algorithm 1: Montgomery Multiplication (Mont-
gomery, 1985)
Require: Two polynomials A(x),B(x) such that
degA,degB < k
Other data : an irreducible degree k polynomial
P, and Φ(x),Φ
′
(x) such that degΦ,degΦ
′
≥ k and
P,Φ,Φ
′
are pairwise prime.
Ensure: R = A × B× Φ
−1
mod P.
Step 1. Q ← A× B× P
−1
mod Φ
Step 2. R ← (A× B− Q× P) × Φ
−1
mod Φ
′
In their paper, Bajard et al. proposed a version
of Montgomery algorithm which use a Lagrange rep-
resentation of the elements. Specifically they repre-
sent a polynomial A(x) by its evaluation at 2k values
α
i
,α
′
i
∈ F
p
for i = 1,. ..,k
A
Lag
= (A(α
1
),... ,A(α
k
),A(α
′
1
),... ,A(α
′
k
))
As shown in (Bajar et al., 2006), the use of
such representation is interesting to implement Mont-
gomery algorithm when Φ =
∏
k
i=1
(x− α
i
) and Φ
′
=
∏
k
i=1
(x− α
′
i
). Indeed, due to Chinese remainder theo-
rem, the multiplication modulo Φ (or Φ
′
) in Lagrange
representation is a simple coefficient by coefficient
multiplication. In other words it requires k indepen-
dent multiplications in F
p
.
2.1 Binomial Residue Representation
In this subsection we present an extension of La-
grange representation of (Bajar et al., 2006). We
use this representation to perform Montgomery mul-
tiplication using the same strategy as in (Bajar et al.,
2006).
Let Φ(x) =
∏
n
i=1
φ
i
(x) where φ
i
are pairwise
prime. Recall that Chinese remainder theorem (Ba-
jar et al., 2006; Halbutoˇgullari and C¸ . K. Koc¸, 2000)
asserts that the following application is a ring isomor-
phism.
F
p
[x]/(Φ)
∼
→ F
p
[x]/(φ
1
) × ··· × F
p
[x]/(φ
n
)
U 7→ (U mod φ
1
,··· ,U mod φ
n
).
(1)
The CRT asserts also that if we know the residueU
i
=
U mod φ
i
we can get back to U by computing
U =
∏
n
i=1
|U
i
Φ
−1
i
|
φ
i
Φ
i
mod Φ
where
Φ
i
=
∏
n
j=1, j6=i
φ
i
|Φ
−1
i
|
φ
i
= Φ
−1
i
mod φ
i
(2)
The operator | ·|
φ
i
represents the reduction modulo φ
i
.
If we consider φ
i
with binomial form of fixed de-
gree d, then we know that they are pairwise prime.
Lemma 1. Two binomials φ(x) = x
d
+α,φ
′
(x) = x
d
+
α
′
with α,α
′
∈ F
p
are relatively prime if and only if
α 6= α
′
.
Proof. It is well known that for any φ(x),φ
′
(x)
gcd(φ(x),φ
′
(x)) = gcd(φ(x),φ
′
(x) − φ(x)).
But in the situation of the Lemma, we have φ
′
(x) −
φ(x) = α
′
− α. This implies
gcd(φ(x),φ
′
(x)) = gcd(φ(x),φ
′
(x) − φ(x)) = 1
if and only if α
′
6= α.
So if we take Φ =
∏
n
i=1
φ
i
(x) where φ
i
are distinct
binomials of degree d, then equation (1) holds. This
means that we can represent a polynomialU of degree
less than nd by its n residues modulo φ
i
.
Definition 1 (Binomial Residue Representation). Let
φ
1
(x) = x
d
− α
1
,··· ,φ
n
(x) = x
d
− α
n
be n relatively
prime binomials of degree d. Let U ∈ F
p
[x] with
degU < n· d. The residue representation U
BRΦ
of U
relatively to Φ =
∏
n
i=1
φ
i
is defined as the n remain-
ders modulo φ
1
,φ
2
,... and φ
n
U
BRΦ
= (U
1
,··· ,U
n
) where U
i
(x) = U(x) mod φ
i
(x)
SECRYPT 2008 - International Conference on Security and Cryptography
320
The arithmetic modulo Φ is advantageous in BR
representation since the arithmetic split into n inde-
pendent arithmetic units which perform arithmetic
operations (addition and multiplication) in F
p
[x]/(φ
i
).
Based on this feature, we construct an efficient Mont-
gomery Multiplication in the following section.
3 MONTGOMERY
MULTIPLICATION USING
BINOMIAL RESIDUE
REPRESENTATION
Let φ
1
(x),··· ,φ
n
(x) and φ
′
1
(x),... ,φ
′
n
(x) be 2n dis-
tinct binomials of degree d > 0 and let
Φ(x) =
∏
n
i=1
φ
i
(x), Φ
′
(x) =
∏
n
i=1
φ
′
i
(x).
Using this type of polynomial for Φ and Φ
′
in
Montgomery Algorithm 1 we can perform Step 1 and
Step 2 in BR representation. The major drawback of
this approach is that it requires two BR representa-
tion systems : one relatively to Φ and the other to Φ
′
.
Consequently we must include two conversion opera-
tion to convert Q from BRΦ to BRΦ
′
and the other to
convert R from BRΦ
′
to BRΦ. We will explained in
subsection 3.1 how to perform these conversions.
In the sequel we note Γ the BRΦ
′
representation of
Φ
−1
mod Φ
′
, and we note P
′
the inverse of P mod-
ulo Φ (such polynomials exists since Φ,Φ
′
and P are
pairwise prime ).
Algorithm 2: BR multiplication
Require: A
BRΦ
,A
BRΦ
′
and B
BRΦ
,B
BRΦ
′
the BR rep-
resentation of A(x) and B(x). of degree < k.
Other data : an irreducible degree k polynomial
P, and Φ(x),Φ
′
(x) such that degΦ,degΦ
′
≥ k and
P,Φ,Φ
′
are pairwise prime.
Ensure: Q
BRΦ
,Q
BRΦ
′
where Q = A × B × P
−1
mod Φ
Step 1. Q
BRΦ
← A
BRΦ
× B
BRΦ
× P
′
BRΦ
Step 2. Q
BRΦ
′
← Convert
BRΦ→BRΦ
′
(Q
BRΦ
)
Step 3. R
BRΦ
′
← (A
BRΦ
′
× B
BRΦ
′
− Q
BRΦ
′
×
P
BRΦ
′
) × Γ
Step 4. R
BRΦ
′
← Convert
BRΦ
′
→BRΦ
(R
BRΦ
′
)
Remark 1. We notice that Algorithm 2 requires 2n
binomials with degree d. But, due to Lemma 1 there
are at most p distinct binomials of degree d in F
p
[x].
So we must have p ≥ 2n.
3.1 Conversion Operation
In this subsection, we focus on the conversion opera-
tion in Step 2 and Step 4 in Algorithm 2. There are
several methods for completing the transformation.
The first method is mentioned in (Bajar et al.,
2006), it consists to apply Newton interpolation. It
first computes Q(x)and then compute the remainders
of Q(x) modulo φ
′
i
for i = 1,... ,n. This method re-
quires roughly O(
3
2
n
2
d) operations in F
p
.
This second method consists to apply an interpo-
lation similar to the original Lagrange interpolation.
This method is also mentioned in (Bajar et al., 2006)
but they showed that it is more complicated than New-
ton interpolation. Here we will show that this method
is well suited to our Binomial Residue representation.
Let Q be a polynomial of degree less than k where
k is the degree of P the polynomial which defines the
field F
p
k
. Let Q
BRΦ
= (Q
1
,... ,Q
n
) be its binomial
representation relatively to Φ. Using equation (2) we
can get back to the polynomial form of Q
Q =
n
∑
i=1
Q
i
|Φ
−1
i
|
φ
i
Φ
i
!
m
od Φ,
where
Φ
i
=
n
∏
j=1, j6=i
φ
j
.
To get the BRΦ
′
representation of Q we have to com-
pute the remainder modulo φ
′
j
, for j = 1,...,n, of the
previous expression of Q. In the following lemma we
give the resulting expression of these residues.
Lemma 2. Let Φ and Φ
′
be as follow
Φ =
n
∏
i=0
(x
d
− α
i
) a
nd Φ
′
=
n
∏
i=0
(x
d
− α
′
i
),
with α
i
,α
′
i
∈ F
p
all distinct. Let Q
BRΦ
= (Q
1
,... ,Q
n
)
the BR representation relatively to Φ, then the BR rep-
resentation of Q relatively to Φ
′
can be computed as
Q
BRΦ
′
=
ω
1,1
ω
1,2
··· ω
1,n
ω
2,1
ω
2,2
··· ω
2,n
.
.
.
.
.
.
.
.
.
.
.
.
ω
n,1
ω
n,2
··· ω
n,n
Q
1
Q
2
.
.
.
Q
n
(3)
where
ω
i, j
=
n
∏
ℓ=1,ℓ6=i
α
′
j
− α
ℓ
α
i
− α
ℓ
Proof. Let us go back the the following equation
Q =
n
∑
i=0
Q
i
|Φ
−1
i
|
φ
i
Φ
i
| {z }
(⋆)
mod Φ.
AN EFFICIENT MULTIPLICATION ALGORITHM USING BINOMIAL RESIDUE REPRESENTATION
321

Ω =
1
2
r
·
1 1 ·· · 1
1 β
2
··· β
2n−2
1 β
4
··· β
4n−4
.
.
.
.
.
.
.
.
.
.
.
.
1 β
2n−2
··· β
(2n−2)(2n−2)
| {z }
(⋆)
·
1 0 · ·· 0
0 β ·· · 0
.
.
.
.
.
.
.
.
.
.
.
.
0 0 · ·· β
n−1
·
1 1 ·· · 1
1 β
2
··· β
2n−2
1 β
4
··· β
4n−4
.
.
.
.
.
.
.
.
.
.
.
.
1 β
2n−2
··· β
(2n−2)(2n−2)
| {z }
(⋆)
Figure 1: DFT form of equation (3).
We first show that in our context, no final reduction
modulo Φ is needed in this previous expression of Q.
Indeed, we show that the polynomials |Φ
−1
i
|
φ
i
for i =
1,... ,n are constant polynomials, and this will prove
that the polynomial (⋆) has a degree at most nd − 1.
Let us prove that |Φ
−1
i
|
φ
i
is a constant. We have
|Φ
i
|
φ
i
=
n
∏
j=1, j6=i
(x
d
− α
j
)
!
mod (x
d
− α
i
)
Bur, since x
d
= α
i
mod (x
d
− α
i
), we can replace x
d
by α
i
we get |Φ
i
|
φ
i
=
∏
n
j=1, j6=i
(α
i
− α
j
) and also
|Φ
−1
i
|
φ
i
=
1
∏
n
j=1, j6=i
(α
i
− α
j
)
.
This proves that |Φ
−1
i
|
φ
i
is a constant polynomial and
that the following equation holds
Q =
n
∑
i=0
Q
i
|Φ
−1
i
|
φ
i
Φ
i
.
Now we compute the BRΦ
′
representation of Q by
computing the remainder of the later expression of Q
modulo φ
′
j
for j = 1,.. .,n. We have
Q
′
j
=
n
∑
i=0
Q
i
|Φ
−1
i
|
φ
i
Φ
i
φ
′
j
. (4)
where Q
′
j
is the j-th polynomial in Q
BRΦ
′
. To simplify
this expression (4) we use the binomial form of the
polynomials φ
i
and φ
′
j
.
We first remark that
Q
i
|Φ
−1
i
|
φ
i
Φ
i
φ
′
j
=
Q
i
|Φ
−1
i
|
φ
i
|Φ
i
|
φ
′
j
φ
′
j
(5)
But we know that
|Φ
−1
i
|
φ
i
=
1
∏
n
j=1, j6=i
(α
i
− α
j
)
.
and we can obtain using a similar method that
|Φ
i
|
φ
′
j
=
n
∏
ℓ=1,ℓ6=i
(α
′
j
− α
ℓ
).
If we replace these expressions of |Φ
−1
i
|
φ
i
and
|Φ
i
|
φ
′
j
in (5) we finaly get
Q
′
j
=
n
∑
i=0
Q
i
ω
i, j
where ω
i, j
=
n
∏
ℓ=1,ℓ6=i
α
′
j
− α
ℓ
α
i
− α
ℓ
The main advantage of the conversion expression
of equation (3), is that the matrix Ω has its coeffi-
cients in F
p
. Consequently, if we perform the change
of representation using (3) with a direct computation
of the matrix vector product, the conversion has a cost
of n
2
d multiplications and n(n− 1)d additions in F
p
.
3.2 Optimization
In some special cases, we can perform the conversions
more efficiently. This is possible with the strategy
used by Negre (Negre, 2006) to improve Bajard et al.
approach. Negre showed that under some conditions
on α
i
and α
′
j
and p the matrix vector product in equa-
tion (3) can be done through two FFT evaluation.
Specifically, assume that n = 2
r
and that 2
r+1
|(p−
1) then there exists a primitive 2
r+1
-th root of unity
β ∈ F
p
. The 2
r+1
elements β
i
for i = 0, ...,2
r+1
− 1
are distinct elements. We take Φ and Φ
′
as
Φ =
n−1
∏
i=0
(x
d
− β
2i
) and Φ
′
=
n
∏
i=0
(x
d
− β
2i+1
)
In this situation the matrix Ω = [ω
i, j
]
i, j=1,...,n
ex-
pressed in Lemma 2 can be written as in Figure 1 (cf.
Negre (Negre, 2006) for detailed explanation).
The matrix (⋆) is 2
r
× 2
r
matrix of Discrete
Fourier Transform , so we can compute the corre-
sponding matrix vector product with FFT algorithm.
Consequently a conversion between two BR rep-
resentations require two FFT computation and the
same is true for the reverse transformation. We de-
duce that a conversion as a cost of 2nlog
2
(n)d addi-
tions and nlog
2
(n)d + nd multiplications in F
p
.
SECRYPT 2008 - International Conference on Security and Cryptography
322
4 COMPLEXITY AND
COMPARISON
In this section we evaluate the complexity of Algo-
rithm 2. The complexity is given by the number of
addition, multiplication and multiplication by a con-
stant of F
p
elements. We denote by M the cost of one
multiplication, by A the cost of an addition and CM
the cost of one multiplication by a constant in F
p
.
4.1 Classical Approach
This approach consists to perform Algorithm 2 using
no optimization given by FFT approach. This is the
case for example when no 2
r+1
root of unity lie in
F
p
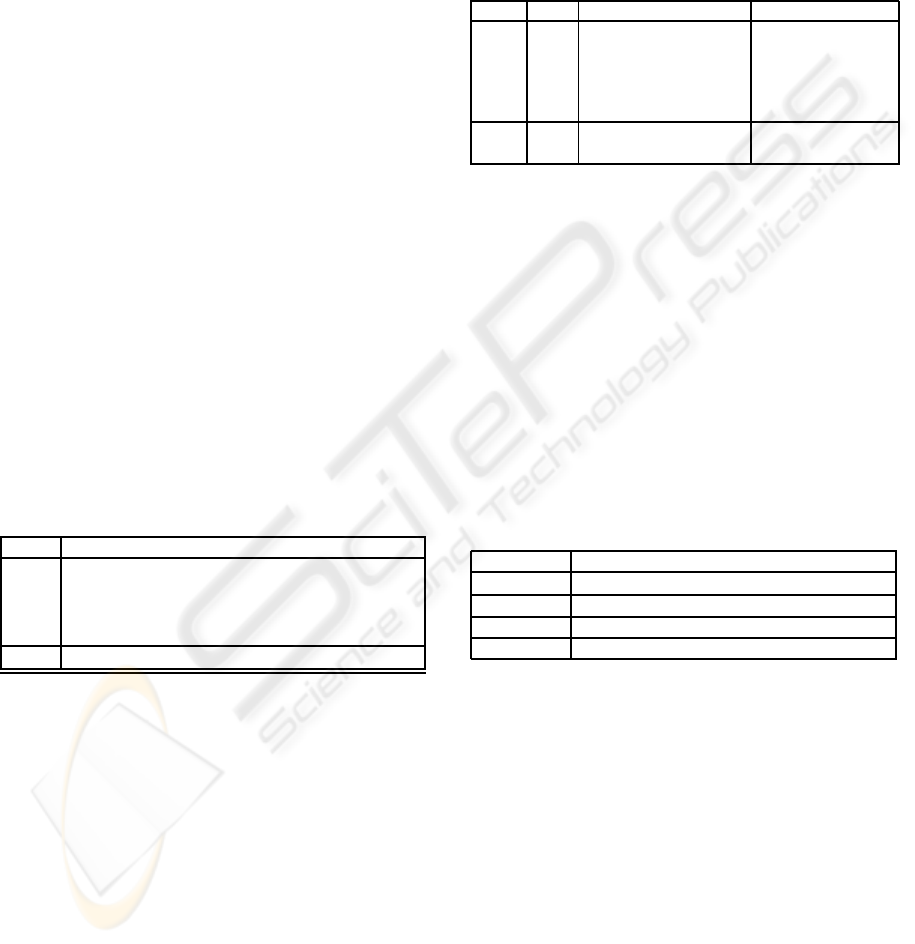
. We evaluate in Table 1 the cost of each step of
Algorithm 2 separately.
• In Step 1 and Step 3, we have to perform respec-
tively 2n multiplications of polynomial of degree
d modulo binomials (for Step 3, Γ lie in F
n
p
).
These multiplications are done using school book
method and direct reduction modulo the binomi-
als φ
i
and φ
′
j
. Each of these multiplications in
F[x]/(φ
i
) has a cost of d
2
M + d(d − 1)A+ (d −
1)CM.
• Step 2 and Step 4, is done through a matrix vector
product as expressed in Lemma 2.
We indicate the cost of each case in Table 1.
Table 1: Complexity of BR Montgomery Multiplication.
Step M A CM
1 2nd
2
2nd(d − 1) 2n(d − 1)
2 - n(n− 1)d n
2
d
3 2nd
2
2nd(d − 1)+ nd 2n(d −1) + nd
4 - n(n− 1)d n
2
d
Total 4nd
2
4nd
2
+ 2n
2
d − 5nd 2n
2
d +5nd − 4n
By adding the complexity of each step and obtain
the total complexity of Algorithm 2.
4.2 Optimized BR Multiplication
We suppose now that there exists an integer r such
that 2
r+1
|(p − 1) and we take n = 2
r
≥ d. Then, we
can use the FFT optimized version of Algorithm 2 .
• For Step 1 and Step 3, we have to perform op-
eration modulo φ
i
or φ
′
j
. Since 2
r+1
≥ 2d, we can
perform the multiplication modulo φ
i
and φ
′
j
using
FFT method (cf. (von zur Gathen and Gerhard,
1999)). Each of them require 2d multiplications,
(4d log(d) + d) additions and (2d log(d) + 2d)
constant multiplications in F
p
.
• Step 2 and Step 4 are computed as explained
in subsection 3.2. Their cost are thus equal to
2nlog
2
(n)d additions and nlog
2
(n)d + nd con-
stant multiplications in F
p
.
The resulting complexity is given in Table 2.
Table 2: Complexity of Optimized BR Multiplication.
Step M A CM
1 4nd 2nd(4log
2
(d) +1) 4nd(log
2
(d) +1)
2 - 2ndlog
2
(n) nd(log
2
(n) + 1)
3 4nd 2nd(4log
2
(d) +1) 4nd(log
2
(d) +1)
+nd +nd
4 - 2ndlog
2
(n) nd(log
2
(n) + 1)
Tot. 8nd 4ndlog
2
(d
4
n) + 5nd 2ndlog
2
(d
4
n)
+11nd
4.3 Comparison
For practical fields F
p
k
)
, care must be taken for the
selection of algorithm parameters n and d. The prod-
uct of n and d should be close to k (if nd ≫ k, our
algorithm have high complexity).
To simplify, let us assume that nd = k. The best
choice for n and k to get the best complexity is when
n = 2d. In this situation we get the Complexities of
Table 3. We gave also in this table the complexity of
the approaches presented in (Bajar et al., 2006) and
(Negre, 2006).
Table 3: Comparison.
M A CM
This paper 4k
1.5
6k
1.5
− 5k 2k
1.5
+ 5k
BIN 2k O(k
2
log(k)) (4k−1)
This paper 8k 10klog
2
(k) −k 5klog
2
(k) +8k
Negre 4k 4klog
2
(k) +k 2klog
2
(k) +2k
Comparison of general approaches. Compare to
the BIN algorithm, our algorithm requires more mul-
tiplications but less additions, both multiplications
and additions are in sub-quadratic number. For soft-
ware implementation with p of size less than a word
computer, BIN algorithm is less appropriate to this
case than BR multiplication.
Indeed, we denote T
M
the time delay of one multi-
plication in F
p
and we denote T
A
the time delay of one
addition in F
p
. We will assume that T
M
is about two
times the value of T
A
, as this is the case in software
environment when p has the size of a computer word.
The total time delay of Algorithm 2 for software im-
plementation is (18k
1.5
+ 5k)T
A
. On the other hand
the multiplication algorithm of (Bajar et al., 2006) ac-
tually has a time delay (3k
2
logk+ 3k
2
+ 12k)T
A
.
AN EFFICIENT MULTIPLICATION ALGORITHM USING BINOMIAL RESIDUE REPRESENTATION
323

Table 4: Explicit comparison.
p k n× d algorithm 1 BIN(Bajar et al., 2006) accelerate
#T
A
#T
A
59 29 10× 3 2950 7292 59%
67 29 10× 3 2950 7292 59%
73 29 10× 3 2950 7292 59%
127 23 8× 3 2072 4024 48%
257 23 8× 3 2072 4024 48%
503 19 8× 2 1620 2692 39%
521 19 8× 2 1620 2692 39%
8191 13 7× 2 933 1227 23%
131071 11 6× 2 732 873 16%
In Table 4 we give several fields with crypto-
graphic size and the corresponding time delay re-
quired for BIN multiplier and BR multiplier.
Comparison of FFT approaches. For FFT ap-
proach we see that our algorithm is slower by a factor
between 2 and 4. In the case 2
r
> k, Negre’s Algo-
rithm should be preferred to BR-FFT multiplication.
But when there are not enough roots of unity, Negre’s
approach cannot be used, in this case we get benefit
of our algorithm.
5 CONCLUSIONS
In this paper, we have proposed a multiplication algo-
rithm for field F
p
k
. This algorithm extends the pre-
vious work done in (Bajar et al., 2006). We study
different strategies to implement our algorithm (gen-
eral approach with Lagrange conversion and opti-
mized approach with Fast Fourier Transform). We
get two multipliers : one with sub-quadratic complex-
ity O(k
1.5
) which works in general and the other with
complexity O(klog
2
(k)) which works only in special
situations.
In software platform our general method seems to
be better than original BIN (Bajar et al., 2006) al-
gorithm. Compared to the BIN algorithm for sev-
eral fields of cryptographic size our algorithm should
accelerated the multiplication by an average ratio of
30%.
REFERENCES
Bailey, D. V. and Paar, C. (1998). Optimal extension field
for fast arithmetic in public key algorithm. In Ad-
vances in Cryptology-CRYPTO’98, volume 1462 of
LNCS, pages 472–485. Springer-Verlag.
Bajar, J. C., Imbert, L., and Negre, C. (2006). Arithmetic
operation in finite fields of medium prime characteris-
tic using the Lagrange representation.
Halbutoˇgullari, A. and C¸. K. Koc¸ (2000). Parallel multi-
pliers using polynomial residue arithmetic. Designs,
Codes and Cryptography, pages 155–173.
Koblitz, N. (1987). Elliptic curve cryptosystems. Mathe-
matics of Computation, 48(177):203–209.
Lidl, R. and Niederreiter, H. (1994). Introduction to Fi-
nite Fields and Their Applications. Cambridge Univ.
Press.
Lim, C. H. and Hwang, H. S. (2000). Fast implementa-
tion of elliptic curve arithmetic in GF(p
n
). Public Key
Cryptography, 1751:405–421.
Miller, V. (1986). Uses of elliptic curve in cryptography.
In Advances in Cryptology, Proc. CRYPTO’8, pages
417–428.
Montgomery, P. L. (1985). Modular multiplication with-
out trial division. Mathematics of Computation, pages
519–521.
Negre, C. (2006). Finite field multiplication in lagrange
representation using fast fourier transform. In Inter-
national Conference on Security and Cryptography,
SECRYPT 2006.
von zur Gathen, J. and Gerhard, J. (1999). Modern com-
puter algebra. Cambridge University Press, New
York, NY, USA.
SECRYPT 2008 - International Conference on Security and Cryptography
324
