
SEC-SNMP: POLICY-BASED SECURITY MANAGEMENT FOR
SENSOR NETWORKS
Qinghua Wang and Tingting Zhang
Department of Information Technology and Media, Mid Sweden University, Sundsvall, Sweden
Keywords:
Security management, security policy, sensor network.
Abstract:
In this paper, we present a sensor network security management framework called Sec-SNMP, which orga-
nizes and manages security related behaviors in sensor networks based on security policies. There are three
main components in Sec-SNMP: Sec-SNMP manager, Sec-SNMP agent and a policy control and deployment
protocol. Sec-SNMP manager provides the interface between human administrator and the managed mesh
network. Sec-SNMP agent represents Sec-SNMP manager to enforce security policies within the managed
mesh network. The policy control and deployment protocol allows the communication between Sec-SNMP
manager and Sec-SNMP agents. The security management for sensor networks is still in its germinal stage,
and this paper provides a good guideline for future research.
1 INTRODUCTION
Sensor networks deployed in human-unattended en-
viroments for critical applications suffer from a mag-
nificent number of threats. Countermeasures includ-
ing key management, authentication, intrusion detec-
tion, intrusion/fault tolerance, privacyprotection, etc.,
have been proposed for conquering sensor network
threats. Unfortunately, these countermeasures are so
diversified and there is no easy in incorporating all
these countermeasures in one network. To provide the
possibility of coorporativelyexploiting the benefits of
different kinds of security measures, efficient security
management must be implemented. However, secu-
rity management as the mostly used way for security
situation to be awared and security operations to be
executed is left among those few untacted areas in
sensor network related research.
In this paper, we present a policy-based sensor
network security management framework called Sec-
SNMP. With this security management framework,
the administrator can monitor the dynamic security
situation of the sensor network, and then update the
security configuration according to the changed secu-
rity situation.
In the remainder of this paper, we firstly elab-
orate the proposed policy-based sensor network se-
curity management framework Sec-SNMP by seper-
ately introducing its architecture, three main compo-
nents (Sec-SNMP manager, Sec-SNMP agent, and
Policy Control and Deployment Protocol) and the
flow of security policy enforcement. After that, we
summarize some nice features of the proposed Sec-
SNMP framework in Section 3. A short introduction
of the related work is given in Section 4. The conclu-
sion is finally given in Section 5.
2 POLICY-BASED SENSOR
NETWORK SECURITY
MANAGEMENT FRAMEWORK
(SEC-SNMP)
In this section, we propose a security management
framework called Sec-SNMP, which organizes and
manages security related behaviors in WSNs based on
security policies. As for security policy, it is a high
level definition of what it means to be secure for a
system. In Sec-SNMP, the top security policy is that
the managed sensor network should fulfill security
requirements including Availability, Authentication,
Confidentiality, Integrity, Non-repudation, Freshness,
and Survivability. When it comes to implementation
in Sec-SNMP, this top security policy is divided into
many policy items which concretely specify security
operations when some pre-defined security situation
appears.
222
Wang Q. and Zhang T. (2008).
SEC-SNMP: POLICY-BASED SECURITY MANAGEMENT FOR SENSOR NETWORKS.
In Proceedings of the International Conference on Security and Cryptography, pages 222-226
DOI: 10.5220/0001928602220226
Copyright
c
SciTePress
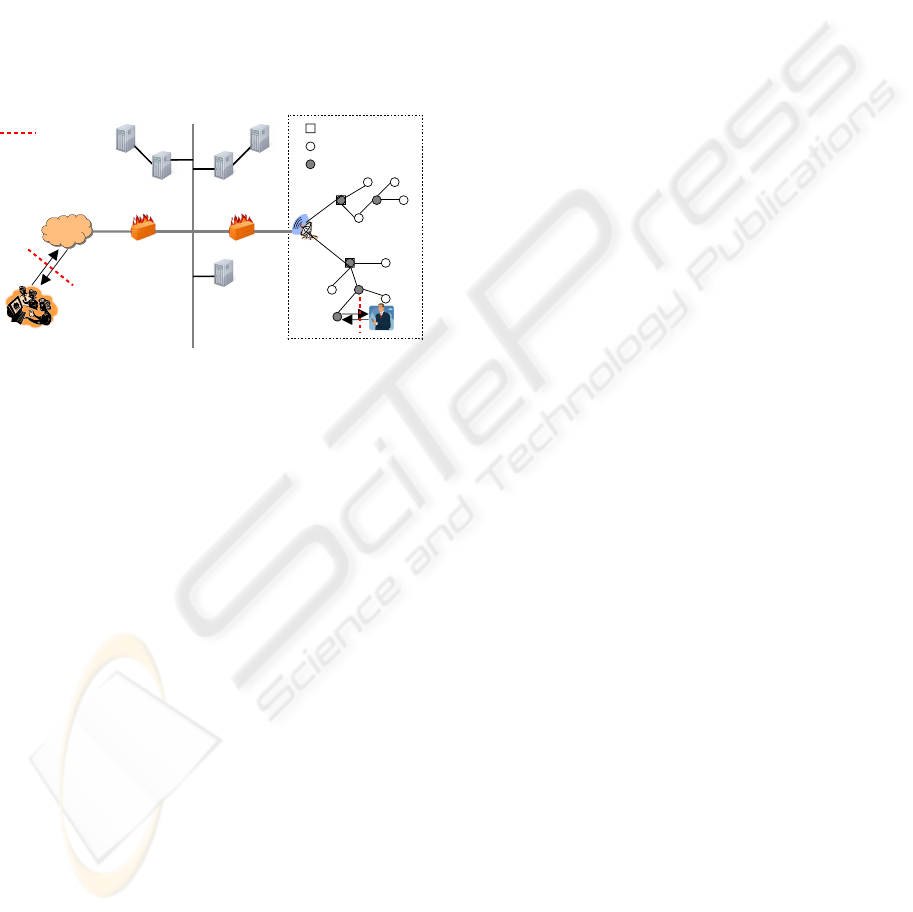
2.1 Architecture
Figure 1 shows the Sec-SNMP architecture. The con-
sidered sensor network system consists of two parts:
infrastructure servers and mesh network. Infrastruc-
ture servers provide remote data acquisition and query
service, strong authentication service, and network
management service. Mesh network provides data
collection, event detection, and authenticated in-field
query service. In Sec-SNMP, the security manage-
ment service is collaboratedly provided by the Sec-
SNMP manager standing on the infrastructure server
side and the Sec-SNMP agents distributedly installed
on the sensor side.
!
"!
!
!!#
$!%
#
Figure 1: Sec-SNMP architecture.
2.2 Sec-SNMP Manager
The Sec-SNMP manager provides the interface be-
tween the human network administrator and the man-
aged sensor network system. It consists of a Secu-
rity Policy Base, a Security Management Information
Base (Security MIB), a Security State Base, and a Se-
curity Event Processing Module.
• Security Policy Base stores all available security
policy rules configured by the network adminis-
trator.
• Security MIB provides static security manage-
ment information, including both network and
network component security configuration. In
a policy-based security management, a security
MIB tells what object (an object can be a node
component, a group of node components, a node,
or a group of nodes) is imposed with what kind of
security policy.
• Security State Base keeps the up-to-date network
and component dynamic states and the states are
stored according to sensor network security mod-
els. Examples of sensor network security mod-
els include network topology map, network con-
nectivity map, network routing path map, and
network behavioral history, etc. The Security
State Base is dynamically updated according to
the alerts and query results coming from Sec-
SNMP agents, and it provides necessary informa-
tion when the administrator decides to update net-
work security configuration.
• Security Event Processing Module consists of key
managemnet engine, authentication engine, intru-
sion detection engine, fault detection engine, etc.
It is responsible for security event detecting, iden-
tification, and processing. It also provides the in-
put for security policy matching and enforcement.
The Sec-SNMP manager runs an application that
provides an interface for the administrator to edit the
Security MIB and the Security Policy Base. It also
runs a Policy Control and Deployment Protocol for
its communication with Sec-SNMP agents.
2.3 Sec-SNMP Agent
The Sec-SNMP agent is a piece of software located
in the managed device and provides the interface be-
tween the Sec-SNMP manager and the physical de-
vices or software applications being managed. Each
Sec-SNMP agent is a mini Sec-SNMP manager, and
is responsible for accepting the security policy config-
uration from the Sec-SNMP manager, for enforcing
configured local security policies, and for reporting
local security states to the Sec-SNMP manager. To
fulfill these functions, it needs to keep a local Secu-
rity MIB, a local Security Policy Base, a local Secu-
rity State Base, and a local Security Event Processing
Module.
As for the implementation of Sec-SNMP agent,
we use the way that Almajali and Elrad proposed
in their Remote Dynamic Policy Deployment Frame-
work (RDPD) (Almajali and Elrad, 2006). Simply
speaking, Sec-SNMP agent is run as an agent service
application on the host sensor node, and the agent
application relies on a underlying filter driver called
Network Driver Component to control the traffic that
flows in and out through sensors. Sec-SNMP agent
stays in contact with Sec-SNMP manager using the
Policy Control and Deployment Protocol. Sec-SNMP
agent communicates with the Network Driver Com-
ponent in order to enforce the policies configured by
Sec-SNMP manager.
2.4 Policy Control and Deployment
Protocol
The Policy Control and Deployment Protocol (PCDP)
allows the different components (Sec-SNMP manager
SEC-SNMP: POLICY-BASED SECURITY MANAGEMENT FOR SENSOR NETWORKS
223
and Sec-SNMP agents) to communicate with each
other and perform their various functions. The PCDP
protocol used in Sec-SNMP framework is a revised
version of a cognominal protocol proposed in ref.
(Almajali and Elrad, 2006), where Almajali and Elrad
define the following message types that can be imple-
mented in the PCDP protocol:
• New network policy deployment request
• Check for new policies deployment/ un-
deployment request
• Check for new policies deployment/ un-
deployment reply
• Policy request
• Policy reply
• Network policy deactivation request
We enlarge this message group to make it fit for
security management by adding the following mes-
sage types:
• MIB update. In Sec-SNMP, the security configu-
ration is organized by MIB. Sec-SNMP manager
needs to update the local MIB information on the
place of each Sec-SNMP agent when there is up-
dated security strategy.
• Security state query. Global security state at the
place of Sec-SNMP manager is regularly updated
by sending a security state query message to ev-
ery Sec-SNMP agents distributed in the mesh net-
work.
• Security state reply. Sec-SNMP agents check
the local security state and reply this message to
Sec-SNMP manager on receiving a security state
query message.
• Security state alert. This message is sent from
Sec-SNMP agents to Sec-SNMP manager when
there is some emergent security state change.
2.5 Security Policy Enforcement
In Sec-SNMP, an individual security policy item
tells what kind of operation needs to be executed
when a corresponding security event happens. Ex-
amples of defined security events include: authenti-
cation failed/succeeded, node failure detected, mali-
cious node detected, etc. Examples of adoptable op-
erations include: sending alert to manager, accouting,
re-establishing routing, going to sleep, droping pack-
ets, etc.
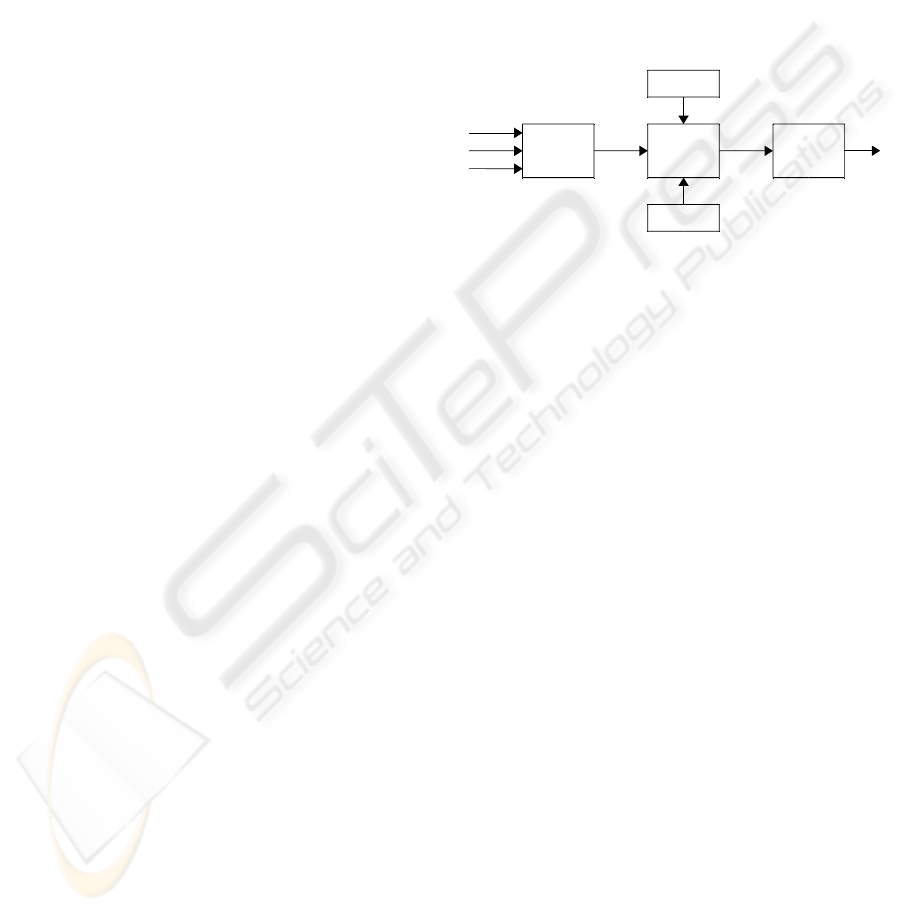
Security policies must be enforced after their con-
figuration. Figure 2 shows the flow of policy enforce-
ment. When a general event (e.g. sensing event, ra-
dio event, time event, etc.) is captured by the system,
it is firstly forwarded to the Security Event Process-
ing Module for security analysis. The Security Event
Processing Module consists of key management en-
gine, authentication engine, intrusion detection en-
gine, fault detection engine, etc. Thus, it has the abil-
ity to translate a general input event into a predefined
security event. The identified security event is fur-
ther forwarded to the policy matching engine for the
extracting of the applicable policy on the applicable
object. Finally, the extracted applicable policy is en-
forced by the system according to the operation de-
fined in this policy.
Figure 2: Security policy enforcement.
3 DESIGN FEATURES OF
SEC-SNMP
Sec-SNMP is designed to provide convenient security
management service for resource-constrained sensor
networks. It possesses the following nice features:
• Energy efficiency The main computation, commu-
nication and storage tasks related to security man-
agement are put on the infrastructure server side.
The concept of agent allows most of security re-
lated events to be processed locally. The main
communication overheads in Sec-SNMP are se-
curity configuration updates and the on-demand
local security state reports, which shouldn’t hap-
pen too often.
• Compatibility The three main components (Sec-
SNMP manager, Sec-SNMP agent, Policy Con-
trol and Deployment Protocol) in Sec-SNMP
framework can also be used in other network
management services, such as fault management,
power management, etc. Besides, the concepts of
Security MIB, Security Policy Base and Security
State Base can also be generalized for the use in
a general purpose policy-based network manage-
ment structure.
• Seamless Integration Independently implement-
ing different available security mechanisms in
sensor networks can cause unnecessary over-
heads, and possibly even a mess. Sec-SNMP or-
ganizes available security mechanisms according
SECRYPT 2008 - International Conference on Security and Cryptography
224

to their mutual dependency relations, and makes
them act under the common defined security poli-
cies. Thus, the security related information can be
presented to the security administrator by a single
interface.
• Local Response & Global Awareness Sec-SNMP
agents respond to security events locally and
in time, while collaborations among these dis-
tributed agents are still possible through Sec-
SNMP manager, which can be accessed by all
agents and is globally situation aware.
4 RELATED WORK
Louis Lee et al. (Lee et al., 2006) propose an
adaptive policy-based management system for sen-
sor networks, called Wireless Sensor Network Man-
agement System (WinMS). The end user predefines
management parameter thresholds on sensor nodes
that are used as event triggers, and specifies man-
agement tasks to be executed when the events oc-
cur. WinMS uses its underlying MAC and routing
protocol FlexiMAC, which is a TDMA-based pro-
tocol that provides synchronized communication, to
support resource (time slots) transfer from the rest of
the network to areas where important sensing events
are detected. MANNA (a Management Architecture
for Wireless Sensor Networks) (Ruiz et al., 2003),
is another policy-based management system that col-
lects dynamic management information, maps this
into WSN models, and executes management func-
tions and services based on WSN models. WSN mod-
els maintain the information about the state of the net-
work. MANNA defines the relationship among WSN
models in a Management Information Base (MIB). It
has been shown (Ruiz et al., 2004) that fault manage-
ment aiming to detect failures in WSNs can be easily
performed by analyzing WSN models within the ar-
chitecture of MANNA. Unfortunately, both WinMS
and MANNA are proposed for general network man-
agement, and the solution of security management
cannot be provided by WinMS and MANNA in a
straight-forward way. However, we found that Sec-
SNMP has a good compatibility with them, thus
Sec-SNMP can be integrated into the existing net-
work mangement frameworks for security manage-
ment purpose.
Coming to the research attempts in the special area
of security management, ref. (Misic et al., 2007) ad-
dresses the networking and security architecture of a
healthcare information system which includes a wire-
less hop. This hop includes wireless sensor networks
and, possibly, wireless local area or mesh networks
to connect to the main wired hospital network. The
authors discuss confidentiality and integrity policies
for clinical information systems and propose the fea-
sible enforcement mechanisms over the wireless hop.
They also compare two candidate MAC technologies,
IEEE 802.15.4 and IEEE 802.15.1, from the aspect of
resilience to jamming and denial-of-service attacks.
Compared to Sec-SNMP proposed in this paper, the
solution proposed in (Misic et al., 2007) is too spe-
cialized and not appropriate for the security manage-
ment of a general purpose wireless sensor network.
5 CONCLUSIONS AND FUTURE
WORK
Security management is the process of managing,
monitoring, and controlling the security related be-
haviors of a network, and it plays a vital important
role in network management. Currently, a few at-
tentions have been paid on general network manage-
ment for sensor networks, with fewer papers specif-
ically discussing security management. This paper
presents a policy-based sensor network security man-
agement framework called Sec-SNMP, which spec-
ifies the necessary important components and func-
tionalities in a sensor network security management
system. To the best knowledge of the authors, this pa-
per is within the earliest works in the important sensor
network security management area.
Although the framework of sensor network se-
curity management has been presented in this pa-
per, there exist open problems to implement it. One
challenge is to make clear the dependency relations
among different proposed security technologies and
design appropriate interfaces among them. Another
challenge could be the development of expressive
languages or metadata for representing management
policies and for representing the MIBs that can be un-
derstood by the security agent application, the secu-
rity manager application, and the security administra-
tor.
REFERENCES
Almajali, S., Elrad, T., 2006. Remote dynamic policy de-
ployment for sensor networks using application trans-
parent approach. In OOPSLA ’06, Workshop on Build-
ing Software for Sensor Networks.
Lee, W.L., Datta, A., Cardell-Oliver, R., 2006. WinMS:
wireless sensor network-management system, an
adaptive policy-based management for wireless sen-
SEC-SNMP: POLICY-BASED SECURITY MANAGEMENT FOR SENSOR NETWORKS
225

sor networks. In Technical Report UWA-CSSE-06-
001. The University of Western Australia.
Misic, J., Misic, V.B., 2007. Implementation of security
policy for clinical information systems over wireless
sensor networks. In Ad Hoc Networks. Elsevier, 5(1),
pp. 134-144.
Ruiz, L.B., Nogueira, J.M. and Loureiro, A.A.F., 2003.
MANNA: a management architecture for wireless
sensor networks. In IEEE Communications Magazine.
41(2), pp. 116-125.
Ruiz, L.B., Siqueira, I.G., etc., 2004. Fault manage-
ment in event-driven wireless sensor networks. In
MSWiM’04, 7th ACM International Symposium on
Modeling, Analysis and Simulation of Wireless and
Mobile Systems. ACM Press.
SECRYPT 2008 - International Conference on Security and Cryptography
226
