
A CASE STUDY OF AUTOMATED INVENTORY
MANAGEMENT
Abrar Haider
School of Computer and Information Science, University of South Australia
Mawson Lakes, South Australia 5095, Australia
Keywords: IT asset, Tracking, Integration.
Abstract: Maintaining a knowledgebase the location and condition of IT assets in large organisation is a problem.
Knowledge of exact number of these assets is important for a number of reasons, which include controlling
or eliminating procuring multiple assets for the same job or task; cost savings on maintenance contracts in
accordance with the exact number of assets to be maintained; reduction in man hours spent in locating these
assets; and checking theft. This paper presents a case study of a large sized Australian utility that is
grappling with the same problems. In addition to these issues the company is also looking for looking for
improved security of fixed/removable/mobile IT assets used by staff, integration of IT asset movement
information with the staff access card and associated systems currently in use. This paper, therefore,
presents a set of options available to the company to track the movement of their assets, and using the same
technical architecture to integrate asset information with the information of the staff moving the asset.
1 INTRODUCTION
With improvements in computer power and
miniaturisation of the components of microchip
technology, automated identification technologies
are now being used in various applications in
governments, business, supply-chain management,
logistics and retail. Since early days of the current
decade numerous applications have been developed
using automated identification technologies. Among
these are applications like luggage tracking, tracking
individual parts along the production line; tagging
and tracking of patients; smart shelves for
pharmaceutical products, and smart toolbox etc.
Even though these identification technologies have
been used in a variety of settings, however, the
fundamental feature of tracking and traceability of
these technologies continues to hold great promise.
IT assets that get lost or misplaced add to the
total cost of ownership of these IT assets and thus
contribute to the costs of managing business
operations. Organisations generally use passive
technologies such as barcodes, which makes it
extremely difficult to track the IT assets and almost
impossible to maintain a history of the movements
of these assets. It is expected that the
implementation of the Radio frequency
identification (RFID) technology for asset tracking
will help to keep this cost in check. Using RFID
technology, it will be possible to not only track
assets but also maintain a history for every asset
which will prove to be a useful aid if an asset turns
put to be lost or misplaced. With integration of the
identification/access cards, the history could also
contain the details of personnel last responsible for
moving the asset. It will be possible not only to
monitor assets using RFID technology but also keep
track of the status of the assets which could be
viewed by anyone across the organisation through
related computer systems who would want access to
that asset. The adoption of RFID technology in
Australia is only recently escalating due to the new
standards that have emerged which have worldwide
acceptance as opposed to the previous ones which
were highly region-specific. This paper presents a
case study where RFID technology is applied to
track movement of IT assets in a large sized public
sector organisation, and the same architecture
integrates information of the asset with that of the
staff that moves or is responsible for the asset.
141
Haider A. (2009).
A CASE STUDY OF AUTOMATED INVENTORY MANAGEMENT.
In Proceedings of the 11th International Conference on Enterprise Information Systems - Software Agents and Internet Computing, pages 141-148
DOI: 10.5220/0002019401410148
Copyright
c
SciTePress
2 CASE BACKGROUND
This case involves a major utility in one of the
largest state in Australia. This organisation has
major problem in tracking the location of all of its IT
and related assets as well as finding out the exact
number of working IT assets. As a result not only
that the organisation keeps on procuring redundant
assets, but it also uses a rounded figure in signing
support and software licensing agreements. With
exact information on the number of assets, it will be
easy to manage resources effectively and to develop
maintenance contacts in accordance with the exact
number of assets to be maintained. For example, if
the current IT asset inventory states 5000 assets then
the support and licensing agreements are signed for
the same number regardless of the condition of the
assets. Information of exact number of assets, their
condition, and their location will help in reduction of
costs of support and licensing agreements, as well as
the man hours spent in locating these assets. In
addition, it will also eliminate the chance of
redundant purchase of IT assets. The company is
now looking for improved security of
fixed/removable/mobile IT assets used by staff,
integration of IT asset movement information with
the staff access card and associated systems
currently in use. It should be noted that the IT assets
include laptops, desktop computers, printers, servers,
hubs, scanners, plotters, data loggers, UPS units,
switches, routers, projectors, and smart boards.
3 CHOOSING APPROPRIATE
TECHNICAL FOUNDATION
Barcodes have traditionally been used for the
purpose of item tracking and warehouse
management. However, barcodes only identify a
class of items and cannot identity particular items.
For example, a barcode identifies a 500 ml of a coke
bottle but it is insufficient to identify the exact
location of that bottle. Similarly, information on
origin and manufacturing of an item could be related
to its barcode, but barcodes cannot provide
information regarding its movement after
manufacturing or commissioning, and current
condition. Another of their drawback is that barcode
technology is only effective in line of sight with the
reader, such that each item has to be scanned
individually. Hence for the purpose of item location
and tracking, Radio Frequency Identification (RFID)
is a suitable alternative. This technology has been
successfully deployed in different parts of the world
for various applications using its tracking and
identification allowance. The significant level of
interest in RFID technology’s development and
uptake has made it cost-effective and scalable (Wyld
2006). RFID technology falls under the
classification of Automatic Identification and Data
Capture technologies (Wamba et al. 2006). It
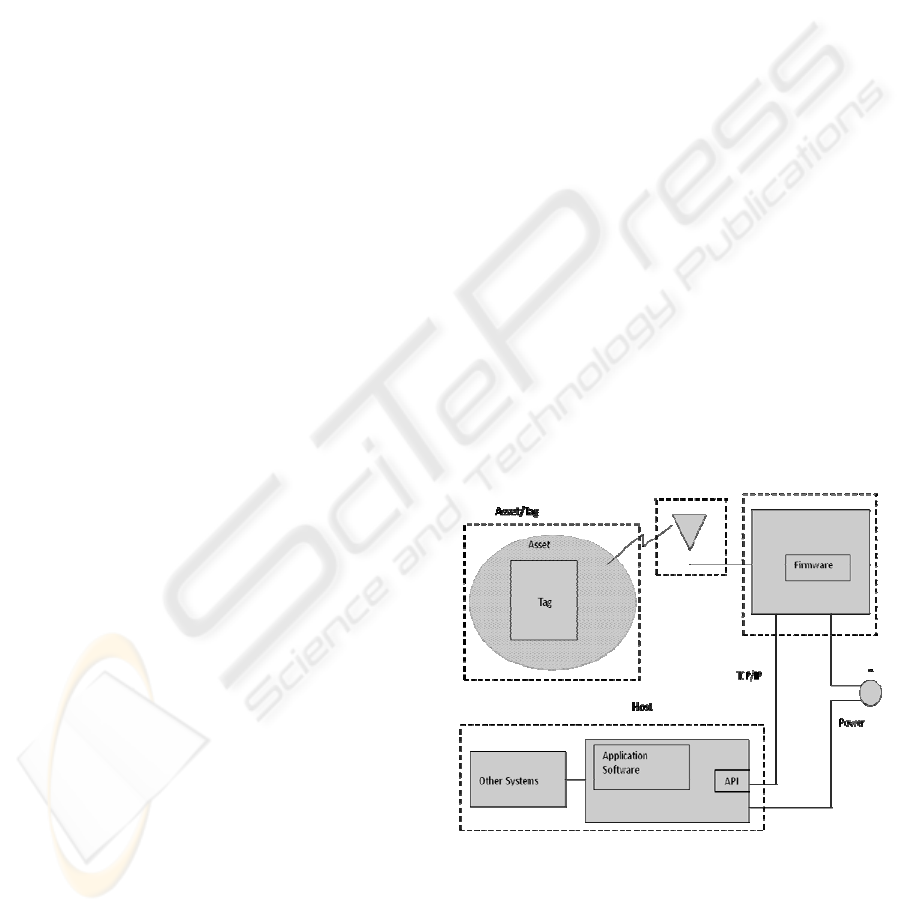
consists of three components, an RFID tag, a reader,
and a Tag/Reader management systems or a
middleware. RFID tags are made up of a small
microcontroller and antenna available in many
different packages. They provide a contact free form
of identification through the use of radio
frequencies. Each tag has an electronic product code
(EPC) or an identification number embedded into
the tag microcontroller that is used to uniquely
identify each tag, which can also be termed as the
RFID’s version of a bar code. When an RFID tag is
placed close enough to the reader it is powered up
through a magnetic field emitted by the reader thus
powering the microcontroller of the tag, such that it
transmits the EPC to the reader. RFID tags do not
require line of sight between tags and readers for
them to be detected and therefore make it possible
for tags attached to items to be identified from a
single point. Therefore it makes RFID a viable
option to address the issues at hand. The following
sections provide an analysis of how this technology
could be used to resolve the problems posed to the
case organisation.
Figure 1: RFID System Components.
ICEIS 2009 - International Conference on Enterprise Information Systems
142

4 AUSTRALIAN TECHNICAL
ENVIRONMENT
The International Telecommunication Union has
developed the ITU Radio Regulations. These
regulations form the basis of the Australian
Radiofrequency Spectrum Plan.
Figure 2: Automatic scanning using HF Tags.
The Radio Regulations divide the different radio
frequencies into bands and allocates services to each
band according to three geographic regions. These
regions are defined as Region 1, 2 and 3 (Australian
Communications Authority 2005). Region 1 is
composed of most of Europe, Africa and the Middle
East. Region 2 is composed of the Americas. Region
3 is made up of the Asia-Pacific region. Thus,
Australia is located in Region 3 (Australian
Communications Authority 2005). ISO/IEC 15693 is
a global standard for 13.56 MHz HF RFID tags
(Class 1) and reader electronics. The ISO/IE C
15693 protocol conforms to FCC (USA), ETSI
(Europe) and MPT (Japan) regulations worldwide.
The standard allows tags to travel around the world
under optimal conditions for operation with region
specific RFID readers (Attaran 2007). Hence the
standards for HF radiolocation are accepted all over
the world. However, for UHF radiolocation,
although, the frequency band assigned is from 860 to
960 MHz, not all the frequencies in this band are
usable. Both U.S. and Europe have different
frequencies in this band for radiolocation. In
Australia (Region 3), most of the frequencies in this
UHF band are used by mobile phone service
providers. Hence, the available frequency band that
may be used is from 915 to 928 MHz so that the
operation does not interfere with other applications
(Australian Communications Authority 2005). The
EPC has developed two standards, Class 0 and Class
1 for the UHF RFID tags. In December 2004, in
order to promote interoperability, they introduced
the Generation 2 standard to replace Class 0 and
Class 1. These Gen 2 tags are now being promoted
world-wide for their interoperability and their higher
memory capacity (Li et al. 2006).
The other regulation in Australia has to do with
the power output of the RFID readers. Current
Australian RFID services are governed by the
ACMA through the class of license for Low
Interference Potential Devices (LIPD). These
regulations limit the RFID services operating in the
915 to 928 MHz frequency band to a maximum
power of 1 watt EIRP (effective isotropic radiated
power). No licenses are required for applications up
to 1 Watt but anything between 1 and 4 Watts
requires a scientific license from GS1 Australia
(GS1 Australia 2008). Read range for RFID tags
depends on the power output of the RFID readers,
and the difference between 1 Watt and 4 Watt is
approximately a 300% improvement in read distance
and efficiency (i.e. improving the average read range
from 1 metre to 3 metres). Much of the World now
uses 4 Watt (GS1 Australia 2008). However, this
means that services operating at 4 Watts EIRP may
interfere with other services like mobile
communications which also operate in the same area
and around the RFID UHF frequency band. Both 1
Watt and up to 4 Watt have been used by GS1
Australia in various RFID pilots; with 1 Watt
suitable for shorter range applications, such as hand
held devices, and up to 4 Watt more suited to RFID
gateways or other applications where accurate reads
at a distance are needed (GS1 Australia 2008).
5 AVAILABLE OPTIONS
There following section discusses the options
available to address the issues at hand in this paper.
5.1 First Option
High frequency tags can be used for asset tracking in
the company. The tags operating at the frequency of
13.56 MHz are very cost effective and flexible. They
are available in paper as well as filmic inlays which
makes embedding with the assets very convenient.
The ISO/IEC 15693 standard for 13.56 MHz is
accepted worldwide and the protocols conform to
FCC (USA), ETSI (Europe) and MPT (Japan)
regulations which constitute the three Regions
determined by the International Telecommunications
Union (ITU). The standard allows tags to travel
around the world under optimal conditions for
operation with region specific RFID readers (Attaran
A CASE STUDY OF AUTOMATED INVENTORY MANAGEMENT
143
2007). Australia being in Region 3, according to the
Australian Communications Authority, the HF
frequency band can be used for radiolocation
(Australian Communications Authority, 2005). The
tracking of assets using HF tags may be done in two
different ways:
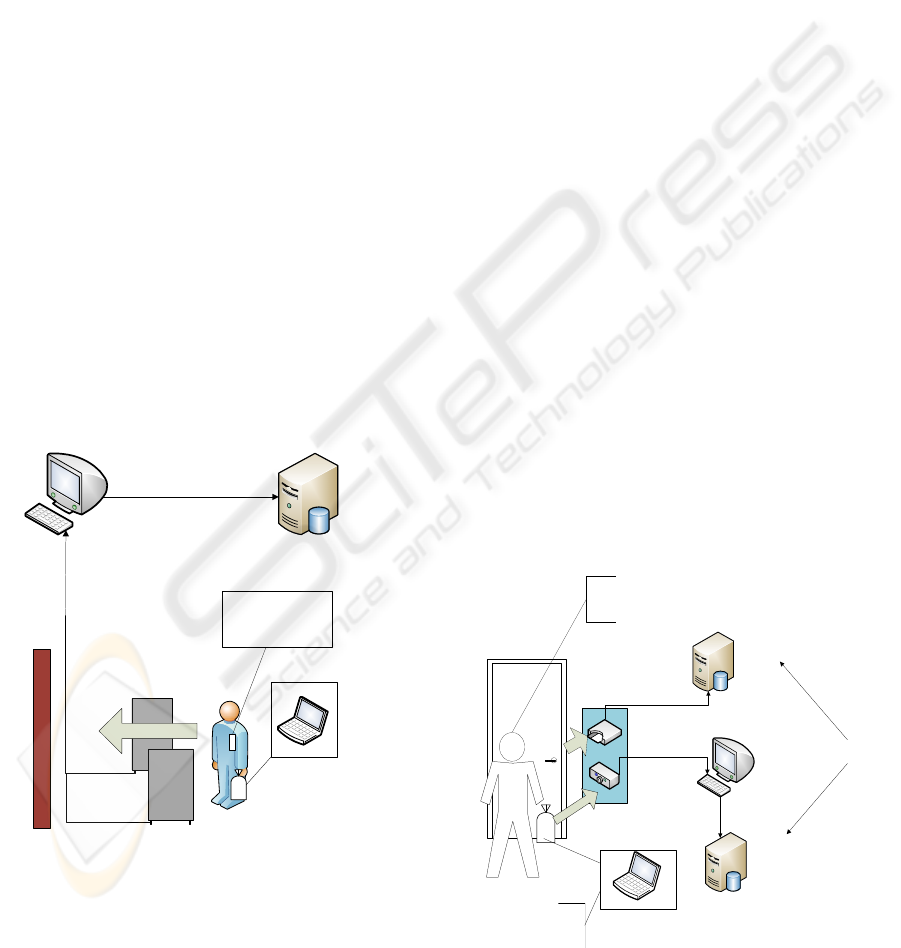
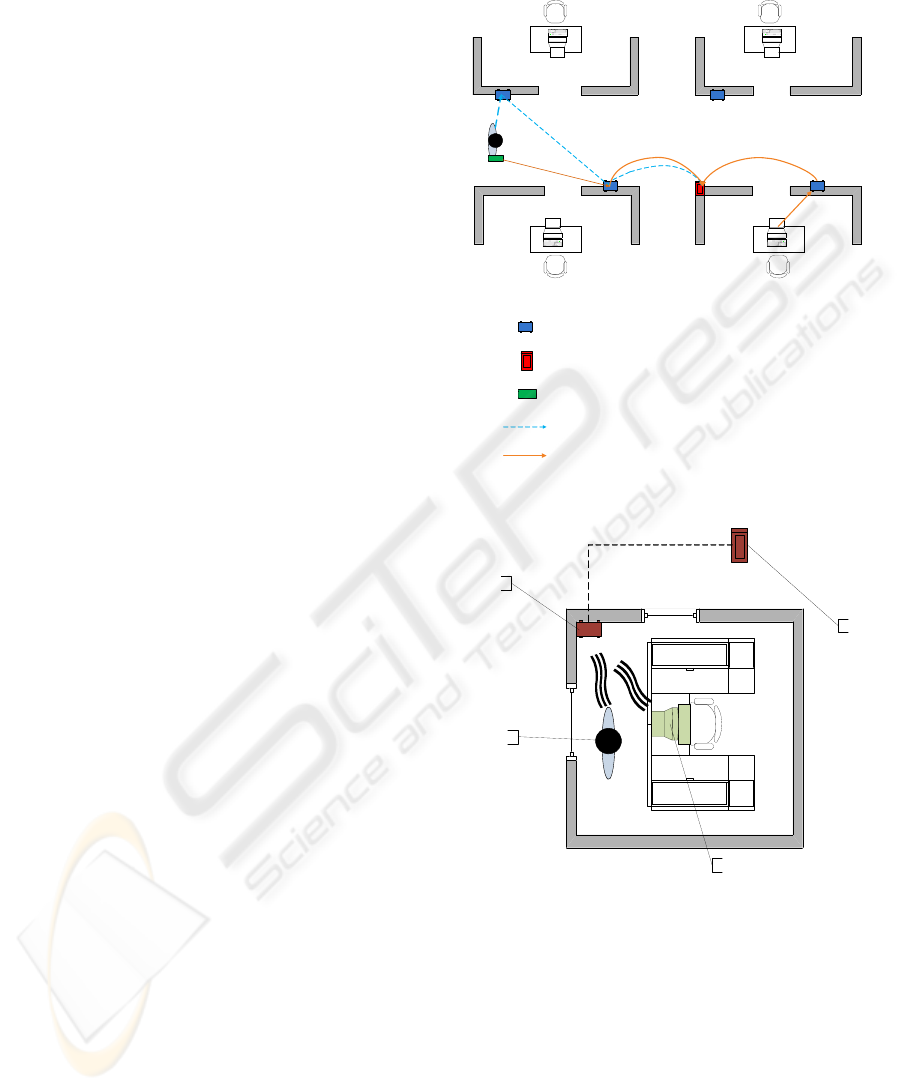
In this case, there are two RFID tags. One
attached to the IT asset and the other enabled on the
staff access/identity card. In this scenario, HF
readers are either mounted on the doorways or at
convenient locations similar to the ones present in
the anti-theft systems at supermarkets may be
installed before of after doorways (see figure 3).
Since the access/identity cards assigned to staff are
also equipped with HF tags, details like IT assets
assigned to them, asset configuration, maintenance
history, special operating requirements, and other
details can also be stored on the tags. In this
scenario, when staff enter or leave the room
equipped with RFID readers, the readers will
automatically read staff as well as IT asset tag. The
information captured will be compared against the
existing record to see if the IT asset being carried by
the staff members actually belongs to them or has
been issued to them. Upon confirmation, it will be
considered a valid ‘check-out’ event and relevant
information will be entered in the ‘asset movement
database’.
Figure 3: Automatic scanning.
This database will obviously be related to
employee/staff database and IT asset inventory
database. In case, the asset does not belong to the
staff member who is trying to take it out of the
room. They will need to make appropriate changes
to IT inventory database before leaving the room. In
case these changes are not made, the system will
generate an alarm and inform the security system.
When the employee returns with the asset to the
room, the same reader will be read the staff as well
as the asset tag, and the relevant ‘check-in’ event
will be recorded in the ‘asset movement database’.
The other option available is that of manual
scanning. This option is similar to the self-service
counters available at supermarket check-out or the
check-out systems available in many libraries. In
this case, the access/identity cards may not be
equipped with RFID tags, however, the assets are to
be tagged with HF tags. However, an RFID station
consisting of a reader and an access card scanner
needs to be present next to the door on the way out
of the room. When a staff member wishes to leave
the room with an asset, he/she will need to swipe his
card through the card scanner so as to invoke an
instance of the check-out event. Once his card has
been read, he will present the asset to the reader
which will read the HF tag and transmit this
information to the computer system. The system will
tie the employee data to the asset tag data and create
a ‘check-out’ entry in the ‘asset movement
database’. At the same time, the HF asset tag will be
deactivated and the employee can then leave the
room after the asset is ‘issued’ to him. If the
employee decides to leave without deactivating the
tag at the RFID station, an alarm will be raised and
the security system will be notified. The employee
can leave the room at anytime without going through
any scanning procedure if he is not carrying any
asset.
Figure 4: Manual scanning.
Tagged
Asset
RFID
Antenna
and Reader
RFID Host Database
Doorway
Tagged
Employee
Employee
Access card
Reader
RFID
Reader
RFID Host
Asset
Database
Doorway
First, employee has to scan his
access card through the card
reader
Next, the asset to be
checked out has to be
scanned at the scanner
Tagged Asset
Employee
Database
Tied at the
backend
ICEIS 2009 - International Conference on Enterprise Information Systems
144
When the employee wishes to return the asset, he
will have to scan his card which will bring up the
existing record and when the asset is presented to the
reader, the ‘check-out’ entry will be cleared as part
of the ‘check-in’ process. Also the tag will be
reactivated and ready for its next check-out event. It
should be noted that the HF tags and readers have
low read ranges and hence the automatic scanning
method might not be feasible unless the placement
of the antennas and readers is tested and the
optimum position is determined.
5.2 Second Option
Due to the read ranges provided by UHF (EPC Gen
2) tags, the automatic scanning method is feasible
when these tags are used for asset tracking. The tags
operate between the frequencies of 918 and 926
MHz in Australia and are available in many different
formats like paper, film, hard tags, discs and even
tamper-proof tags. Although these tags are designed
to operate in the frequency band of 860-960 MHz,
the Australian frequency spectrum plan only allows
operation in the 918 to 926 MHz range as the
remaining frequencies on either side of this band are
utilised by mobile service operators (Australian
Communications Authority, 2005). Various pilots
have been carried out in Australia to test the Gen 2
tags by GS1 Australia. One such pilot entailed the
implementation of EPC Gen 2 tags in the supply
chain of Patties Foods in Victoria along with their
logistics partners, Montague Cold Storage (GS1
Australia, 2008).
These tags only have provision for storing the
EPC which can be used as an identifier for the asset
to which the tag is attached. The EPC has been
designed to enumerate all objects and accommodate
all current naming methods. The EPC serves as a
reference to information on the computer network.
In order to describe the physical objects that the tags
are connected to, a language called the Product Data
Markup Language (PDML) is used. PDML is based
on XML and it uses a schema describing the
common aspects of physical objects. Using PDML,
data about the assets like configuration details,
service or maintenance history, physical attributes,
special operating requirements and so on can be
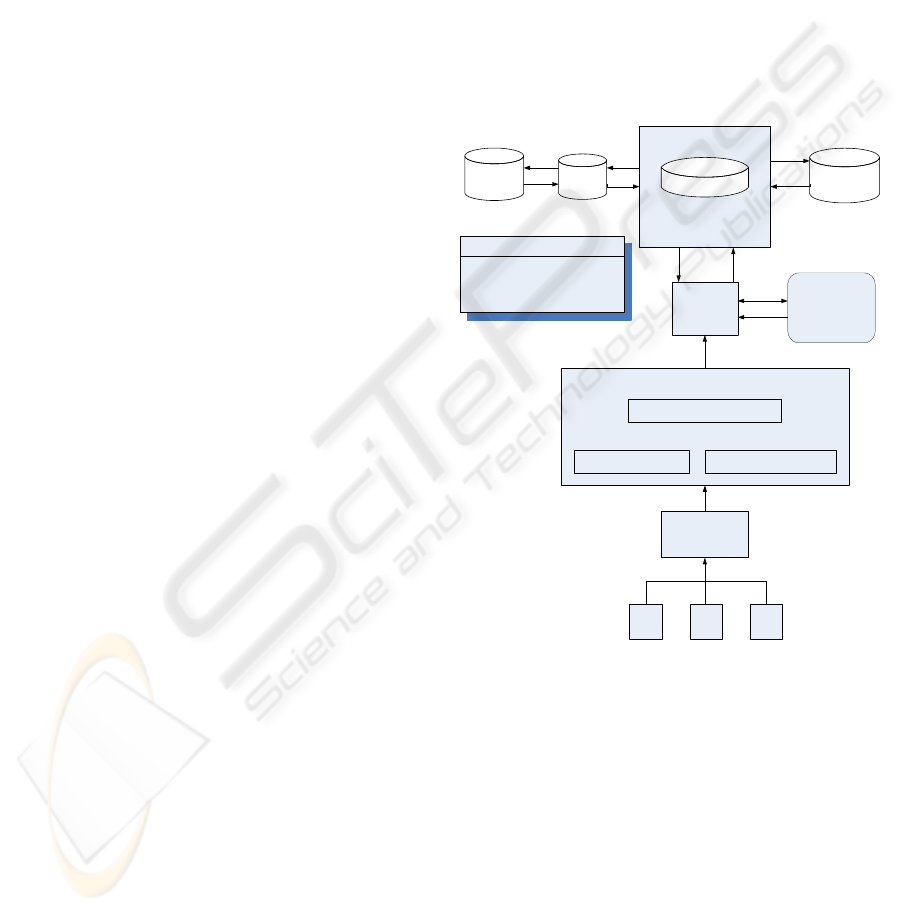
stored in a database. In this scenario (Figure 5), tags
attached to each IT asset are read by a reader fixed at
the convenient location, which passes the EPC
information to the middleware or savant. A savant
acts as buffer between the reader and other
organisational information systems, and consists of
various modules or sub programs with each module
performing specific functions. The savant remains
connected to the readers and act as a router of the
RFID network with the primary functions of EPC
related data smoothing, data forwarding and data
storage; along with reader coordination, and task and
event management. Savant need to be based on open
standards so as to provide for easy information
interoperability. Since the EPC is the only
information stored on the tag, it has to be used in
such a way that it provides additional information
about the IT asset that EPC is attached to. Data
exclusive to IT asset could be stored on a server
located on a connected local area network or the
Internet, by an application of the concept of domain
name service (DNS).
Figure 5: EPC framework (Adopted from Brock 2001).
The EPC stored in the savant is interpreted into a
unique address of an object naming service (ONS),
which is basically an automated network service
which when given an EPC number, returns a server
address where the corresponding PDML file is
located. The ONS service thus behaves similarly to
the DNS used in IP networks, in the way that DNS
converts the IP address of a computer connected to a
network into a domain name for communication
with other computers on the network (Brock, 2001).
The PDML file corresponding to the EPC can
Object
Name
Service
ONS
Cache
EPC Database
EPC Information Service
Serial number tracking,
Transaction tracking
PML Server
ERP or other
applications
Information
Exchange
RFID Middleware
Data filtering, smoothing, forwarding &
storage
Reader Manager
Event Filter & Log
RFID Reader
Tag Tag Tag
EPC
01 0000A37 00063C 000213BF7
Converts to an ONS and works like a
DNS
A CASE STUDY OF AUTOMATED INVENTORY MANAGEMENT
145
contain any type and length of information about IT
asset.
For automatic scanning, the staff access card
needs to be equipped with RFID tags as well as the
IT asset. In this scenario (figure 6), when an
employee leaves a room with an asset, the UHF
reader will scan the staff as well as the asset tag.
This data will be sent to the middleware and
onwards to the PDML files and ‘asset movement
database’. The data from staff will then be related to
the data from the asset and a ‘check-out’ entry will
be created in a database that can be interfaced with
other existing systems so that this information is
available to all the related systems. As mentioned in
the earlier scenario, the identity of the staff will be
matched with the IT asset and if they don’t match
then alarms will be raised and relevant procedures
invoked. When the employee enters the room with
the asset, the staff and asset tags will be scanned
again and a ‘check-in’ entry will be made. The UHF
paper and filmic inlays are very thin and their
compact nature makes their application very
flexible. These tags have been used successfully for
baggage identification in the airline industry. As
mentioned earlier, due to their compact nature, it is
possible to enclose the tags in the barcode labels
such the tags are concealed and the barcode is
visible. This will prevent possible tampering of tags.
Figure 6: Automatic Scanning with UHF Tags.
If manual scanning option is south then as
explained in the manual scanning option for HF tags,
there need to be a RFID reader and an access card
scanner available at the exit door. When a staff
member exist the room with an IT asset, he/she will
have to manually scan the access card and the RFID
reader will automatically read the card. The data
thus captured will be matched to see if the person
carrying the IT assets is the one whom the asset has
been assigned. If not, an alarm will be raised.
Therefore, anybody who wants to take the asset out
of the room will have to ensure that the asset is
‘issued’ to them.
Apart form these options there is a third option
available under this category, which uses microwave
tags. The UHF range microwave tags operating at
the frequency of 2.45 GHz can also be used for asset
tracking. They have longer read ranges than the
UHF 860-960 MHz range tags. The use of the 2.45
GHz frequency for the purpose of radiolocation is
permitted in Australia according to the Australian
Communications Authority. Due to the long range
nature of tags, the tags may be read in multiple
positions. Using this feature of the long-range tags
and with multiple antennas connected to readers at
appropriate positions, tracking of assets on the entire
floor is possible. This will result in real-time
tracking of assets and staff who take those assets.
These tags also employ the EPC standard and so, all
the information about the personnel and assets has to
be stored in a database separately and identified
using the EPC. Hyper-X and Balogh RFID solutions
offered by Electro-com in Australia use these long
range tags.
5.3 Third Option
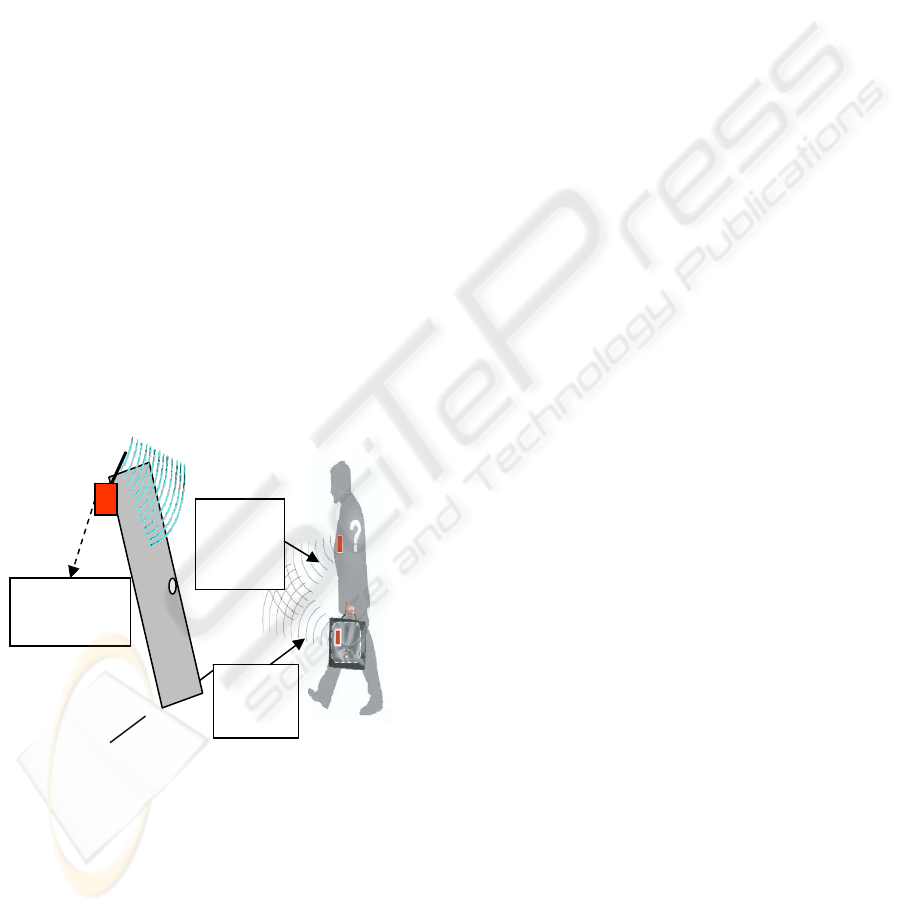
The third option includes active tags. These tags are
powered by batteries and can be automatically
activated at control points in a building. They can
broadcast non line-of-sight to small receivers
networked on the existing corporate LAN/WAN,
VPN or Internet over IP. They operate on dual
frequencies, one to activate the tag and the other for
transmission of data. They can be used for real-time
tracking of assets in the building. The read points
can also be grouped into zones to locate an asset or
person within a specific zone, as well as monitor
movement between zones. The memory on these
tags allows storage of a unique code and other
information like location, status information, etc. In
this scenario (figure 7a&b) a tagged personnel enter
the premises, access may be granted without swiping
a card or entering a code using active tags embedded
on their access/identity cards. The active tags, using
their battery power, transmit data at every control
point like a beacon, which is forwarded to the
reader. So when an employee enters a room, the
tracking system will detect him based on the data
transmitted by his access card.
Using the asset tracking system, assets can be
assigned to authorised staff. A work-request system
RFID
Reader
RFIDHost&
Database
RFID
Enabled
AccessCard
RFID Asset
Tag
Asset
Employee
ICEIS 2009 - International Conference on Enterprise Information Systems
146
may be employed for this purpose. As that employee
moves with his asset in or out of the room, the
access card as well as the tag on the asset is read by
the control point and the data is sent to the system.
The system compares the data with the records
created by the work-request and when a match is
found, confirms that the employee is an authorised
user of the asset. Tamper-proof tags are available
which raise an alarm if removal of the tags is
attempted. If an employee other than the authorised
user attempts to take the asset, the system senses the
mismatch between the personnel tag data and asset
tag data and an alarm is raised. Also, if an employee
leaves his personnel tag behind (say in his cabin)
and attempts to take the asset, he has to go through
the coverage area of many different control points.
The control points relay the movement of the asset
to the system and the system senses that the asset is
being moved without its authorised user. So an
alarm is raised in this event as well.
The active tags can also be used for populating
automatic inventory. The tags broadcast their data
periodically at predetermined intervals to the control
points like beacons. This allows the system to
maintain an inventory of all the assets currently
available. In this way, employees can check on
availability of assets in real-time and if an asset has
been checked-out, the status can be displayed on the
system. Active tags however are the most expensive
and cost in the range of 30 Australian dollars to 75
Australian dollars each.
6 CONCLUSIONS
This paper has presented options for tracking IT
asset using RFID technology and using the same
architecture to integrate asset information with the
information of the staff moving the asset or
responsible for the asset. One of the biggest risks in
the project would be trying to manage all the
expectations from the technology. It is necessary to
understand the drawbacks of the technology and
challenges that other organisations have encountered
while implementing this technology. Most important
among these are the privacy concerns, since the
same technology could be used to track employees
as well. One of the major risks in the project is
system and application integration. Seamless
integration of the RFID system with existing
systems with few changes is vital. If such integration
proves to be infeasible, the fate of this project might
be uncertain as the costs and efforts involved to
bridge the gap would be enormous.
Figure 7a: Active tags for automatic access.
Figure 7b: Active tags for automatic access.
REFERENCES
Attaran, M, 2007, ‘RFID: An enabler of supply chain
operations’, Supply Chain Management: an
International Journal, Vol. 12, Issue 4, p249-257.
Australian Communications Authority, 2005, ‘Australian
Radiofrequency Spectrum Plan’, Australian
Communications and Media Authority, viewed 11
December 2008,
http://www.acma.gov.au/webwr/radcomm/frequency_
planning/spectrum_plan/arsp05.pdf
Employee
Asset
Control Point
Tagged Mobile Asset
RFID Reader
Response from personnel tag
Response from asset tag
Control Point
Tagged Employee
Tagged Asset
Reader
A CASE STUDY OF AUTOMATED INVENTORY MANAGEMENT
147

Brock, D. L, 2001, ‘The Electronic Product Code (EPC):
A Naming Scheme for Physical Objects’, Auto-ID
Center, Massachusetts, viewed 3 November 2008,
http://www.autoidlabs.org/uploads/media/MIT-
AUTOID-WH-002.pdf
GS1 Australia, 2008, 4 Watt License Program, viewed 12
November 2008,
http://www.gs1au.org/products/epcglobal/4watt/
Li, S, Visich, J, K, Khumawala, B, M, Chen, Z, 2006,
‘Radio frequency identification technology:
applications, technical challenges and strategies’,
Sensor Review, Vol. 26, Issue 3, p193-202.
Wyld, D. C, 2006, ‘RFID 101: The next big thing for
management’, Management Research News, Vol. 29,
Issue 4, p154-173.
Wamba, S. F., Lefebvre, L. A., Lefebvre, E, 2006,
‘Enabling intelligent B-to-B eCommerce supply chain
management using RFID and the EPC network: a case
study in the retail industry’, Proceedings of the 8th
international Conference on Electronic Commerce,
ACM, New York, Vol. 156, p281-288.
ICEIS 2009 - International Conference on Enterprise Information Systems
148
