
A CONTENT DRIVEN DATA PROPAGATION PROTOCOL FOR
MSN IN DISCONNECTED MANETS
Basit Qureshi, Geyong Min and Demetres Kouvatsos
School of Computing, Informatics and Media, University of Bradford, BD7 1DP, Bradford, U.K.
Keywords: Simulation, Mobile Social Networks, MANETs, Interest Profiles.
Abstract: Recently various architectures for Mobile Social Networks (MSNs) have been proposed. In MSNs users can
participate in communication with other users based on their respective interest profiles with the idea of
sharing documents that are of interest to a particular user. Typically users subscribe to a social networking
service and look for other users with similar interest profiles. However connectivity may not always be
available for sharing data. In this paper we propose a protocol for MSN implementation in a disconnected
Mobile Ad Hoc Network environment for sharing data. Message delivery in disconnected Mobile Ad Hoc
networks (MANETs) is difficult since the network graph is rarely connected. Our proposed protocol
exploits the store, carry and forward capability of a disconnected MANET. Results from simulations and
implementation show that this approach efficiently disseminates data while minimizing use of resources in
the network.
1 INTRODUCTION
Recently great interest is being shown in Mobile
Social Networks (MSN) (Ziv, 2006). In a social
network, users can communicate with each other
without prior personal knowledge. Cellular phones
have become a popular choice for social networking
with the help of Email, Short messaging or by
subscribing to a social networking service provider.
Typical user of a Social Network would have a
personal public profile advertised on the network
including information such as personal interests,
photos, videos etc. Any user with common interests
would subscribe to share in the social environment.
Traditional Social Networks have been implemented
in a client / server environment, however Mobile
Social Networks provide challenges in mobility,
range and security.
Recent implementations of MSNs from popular
Social network sites such as facebook and myspace
rely on Email and short messaging service on the
client’s device. To search for a friend in the social
network a user needs to subscribe to the service and
query the database for users with common interest.
This communication with the server causes
congestion in the network and may not provide
optimal search results. Instead a peer to peer
implementation would be effective in congestion
control and would provide additional functionality
of mobility to the users where the users would be
able to communicate while on the go. This would
provide users to directly communicate instead of
subscribing to the service provider or paying for
short text messages and hence may be able to share
rich media content. A very effective network
topology would be to use Mobile Ad Hoc Networks
(MANET) where the nodes have the freedom of
mobility. A node may store data and forward it when
it is required only, thus forming disconnected
clusters of participating nodes.
In this paper we present a protocol for providing
content based communication in a disconnected
MANET. In a MANET several devices can
communicate to each other using short range
wireless transmission (Masoudifar, 2009). A
wireless device can forward data for other devices
not in radio-range by creating multi-hop routes.
Further, devices can be mobile in any direction and
can stay connected as long as they are in range of a
neighboring node in the network. Mobility of nodes
allows the topology of the network to be dynamic
therefore creating a group of devices in range but
disconnected from another group. This leads to
challenges in routing for nodes that may get
disconnected, are in suspend mode or have moved
out of the range. Figure 1 illustrates an example of a
disconnected network. n
i
represent nodes in the
57
Qureshi B., Min G. and Kouvatsos D. (2009).
A CONTENT DRIVEN DATA PROPAGATION PROTOCOL FOR MSN IN DISCONNECTED MANETS.
In Proceedings of the International Conference on Wireless Information Networks and Systems, pages 57-62
DOI: 10.5220/0002183400570062
Copyright
c
SciTePress
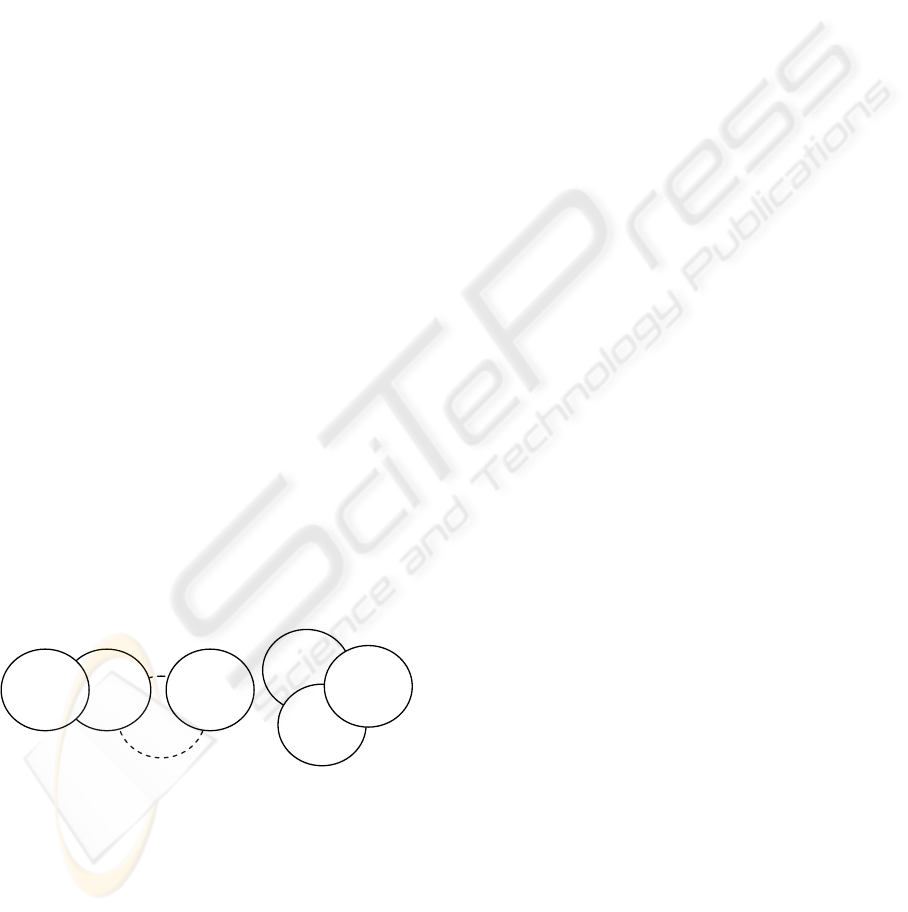
MANET where two groups have been formed. The
nodes n5, n6 and n7 are adjacent and in range of
each other (overlapping circles) therefore a
connection is ensured. Neighboring nodes create a
group as long as they are in range and end to end
connectivity is guaranteed. Nodes n1, n2, n3 and n4
were connected as long as the multi hop path (from
n1 to n4) was available until n3 was disconnected /
suspended (dotted circle). Whenever any node in the
multi hop route is made unavailable end to end
connectivity may not be guaranteed resulting in
disconnected groups. In the figure 1, n4 is shown to
be isolated from the rest of the group following n3’s
unavailability; for n4 to join the group a new one
hop route needs to be established. Both of these
groups may join and form one group if nodes would
physically move closer and come within the
transmission range.
In our design we assume that the MSN users
posses devices that are capable of data storage and
transmission over a Bluetooth or Wi-Fi medium (ad
hoc mode). Any such device with the ability to store
data and forward when needed can form a delay
tolerant network (Jain, 2004). In a delay tolerant
network it is possible for a message to reach the
destination if circumstances permit after a prolonged
period of time. For instance in figure 1, if n1 needs
to send a message to n4 while n4 is isolated, it
cannot be done while n3 is unavailable and no
routing information from n1 to n4 is present. In this
case n1 would transmit the message to n2 that would
be stored for later forwarding. If n3 becomes
available and a route is established, n2 would take
the opportunity to send this message to n4, while n3
would serve as intermediate routing node. A delay
tolerant network provides a means of
communication even if no existing end to end
connectivity is possible.
Figure 1: Illustration of a disconnected MANET.
The rest of the paper is presented as follows,
Section 2 details design for content sharing in the
proposed system, section 3 details proposed
protocol, section 4 presents simulation, results and
evaluation followed by conclusions in section 5.
2 CONTENT SHARING IN MSN
In a typical social network, users subscribe to the
service by making a public profile. A profile is
designed to introduce a person to other members of
the network announcing personal information,
interests, location and a list of documents to share. If
a user makes a search, his personal interests are
matched in a database and query results are returned.
The user may choose to select from a number of
interested users and send an “invite”. The invited
user receives the invitation message, if interested he
responds and the two users become friends. Friends
can show their documents publicly and may even
share them. A user announces his documents to a
friend, if the friend is interested he can request a
document. Papers (Eagle, 2006), (Lugano, 2007) and
(Raento, 2005) discuss implementation of various
forms of a social network.
Typically three factors are essential to successful
data sharing in a social network, Interest Profiles,
Document Lists and Document Repository.
Interest Profiles. Each user maintains a list of
keywords describing his interests. These keywords
are used for searching and indexing purposes. An
interest profile can be detailed and may even contain
both text as well as graphics data and therefore it can
take increasing amount of storage allocation.
However for the proposed protocol we assume that
an interest profile would be a collection of keywords
only and therefore would take minimal amount of
storage.
Document List. Is a list of documents stored at a
host. A document list consists of certain attributes of
documents stored in the repository. These attributes
include but are not limited to a Unique Identifier for
the document, Document size, Document type,
ownership and a Timestamp. Each document stored
in the document repository has this information.
A Unique identifier uniquely identifies a
document, we assume the standard file name format
suffice i.e. (filename.extension). Document size is
mentioned in bytes. Document type could be
categories of documents such as image, video, text
or object etc. Ownership is the MAC address of a
device. A Timestamp is the date and time for the
document creation and indicates when the document
was last updated. A list of documents is announced
whenever two users with similar interests decide to
share. We therefore intend to decrease the size of the
document list since it would be broadcast to other
users of the network; we assume that it must not
increase by 200 bytes.
•n
3
•n
4
•n
2
•n
1
•n
5
•n
7
•n
6
WINSYS 2009 - International Conference on Wireless Information Networks and Systems
58
Document Repository. Each node maintains a
document repository for documents to be shared.
Since there is no limit to the number of documents
stored in a host we therefore set no limits on the size
of the repository.
3 PROTOCOL DESIGN
We propose a content driven protocol where nodes
in an Ad Hoc network share data only if they are
interested, i.e. a node would send or receive
messages, store data and forward the message only if
it is interested and hence routes would be established
in opportunistic manner with nodes having similar
interests. Routes can be established to distant nodes
if they also show interest, provided that a relaying
node is able to forward message in a multi-hop
manner. This however requires the essential storage
capability at each node for storing messages as
transient messages for later transmission to the
intended destination. The proposed protocol relies
on broadcast transmission for announcement and
point to point unicast transmission for destination
oriented messages. Broadcast transmissions are also
used for single hop transmission sending messages
to neighboring nodes depending on the number of
requests received for a particular message.
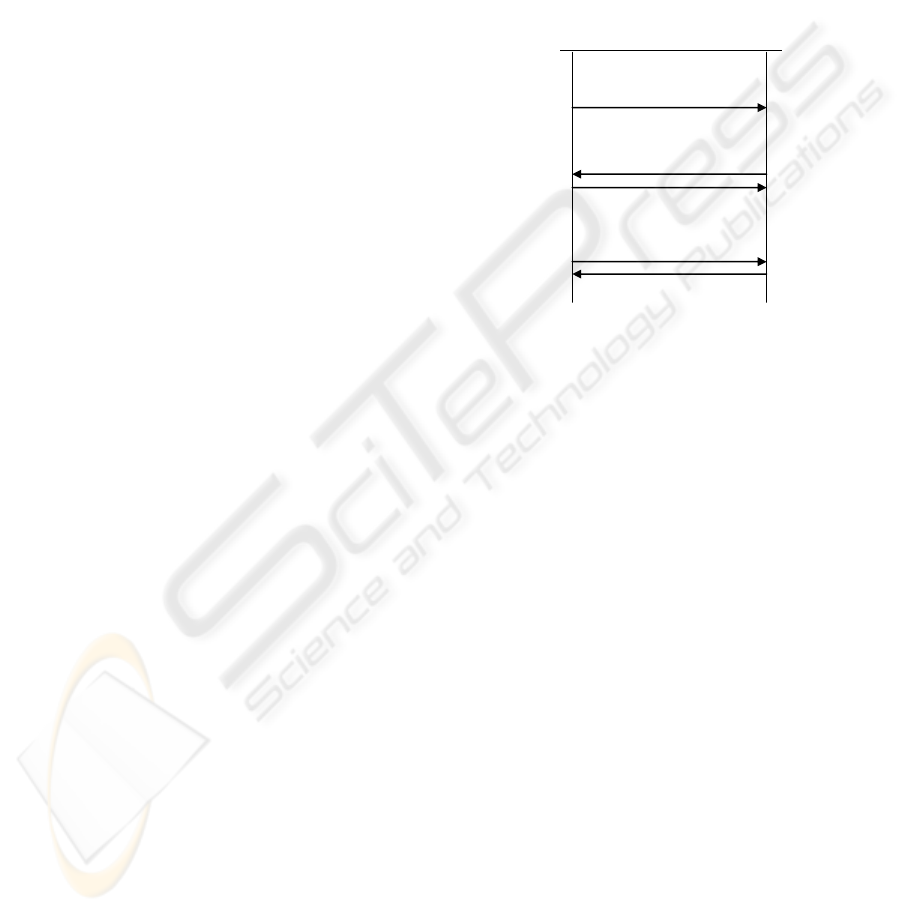
To make our model simple we follow a three
step process for all transmissions. Each node n
i
periodically broadcasts a announce(n
i
) message
containing interest profile of the user. Neighboring
nodes n
j
and n
k
receive this announcement and
process the interest profile. If willing n
j
sends an
invite(n
i
) message to n
i
including document list of n
j
.
n
i
responds with its own invite(n
j
) including list of
documents for n
i
. Both nodes would parse document
list and may tag documents to be shared. For a
document with a unique identifier to be requested by
n
i
a request(n
j
, doc-id1, …) is made upon which n
j
would send(doc-id1, …) the required document as
shown in figure 2. These three transmissions are
detailed as follows.
Announcing Interest Profile. In a neighborhood of
nodes announcements for personal interests are
made. A host n
i
periodically broadcasts announce(n
i
)
including its interest profile. Adjacent nodes
receiving this announcement match their own
interest profile keywords, if the receiving host is
interested, it sends an invite() invitation to the
announcer. Consequently, if the receiving host is not
interested in the interest profile, it simply ignores the
announcement.
Inviting Interested Host. When an announcement
from n
i
reaches a node n
j
, it compares the interests in
the users interest profile. If any of the keywords
match, the receiving host n
j
may be interested in
starting a conversation. It therefore creates a
invite(n
i
) message to be unicast to the originating
node n
i
. This invite() contains a documents list
including document attributes such as a Unique
Identifier for the document, Document size,
Document type, ownership and a Timestamp. We
assume the size of the invite() may not exceed 300
bytes thus keeping the payload of transmission to
minimal.
Figure 2: Transmission between hosts n
i
and n
j.
When the originating node n
i
receives the invite
message from n
j
, it may send its own invite to n
j
describing a list of n
i
’s documents. When both nodes
receive each other’s invite messages they can
process the documents list to search for an
interesting document to share. If there exists such a
document, it can be tagged for sharing among these
two nodes. Any tagged document may be sent if
requested.
Requesting, Sending and Storing Documents.
Nodes that had a chance to look at the document
lists of each other can request or send documents. As
described earlier a document-list contains attributes
for each document stored in a node’s repository.
These attributes include a Unique Identifier for the
document, document size, document type,
ownership and a Timestamp.
If the node n
i
requires a document doc-1 that is
available in repository of node n
j
it would send a
request(n
j
, doc-1) message to n
j
. To process the
request n
j
would proceed by forwarding the
document doc-1 to the requesting node by
embedding the document in the send(doc-1)
message. This send message is forwarded in a
unicast mode intended only for the requesting node
n
i
. When a document is received, it has to be stored
in the nodes repository and the documents list is
updated. It is possible that many adjacent nodes
User(n
i
) User(n
j
)
announce
(
n
i
)
invite
(
n
j
)
invite (n
i
)
re
q
ues
t
(
n
j
,do
c
id
)
s
end
(
docid
)
A CONTENT DRIVEN DATA PROPAGATION PROTOCOL FOR MSN IN DISCONNECTED MANETS
59

would request same documents. In this case a
unicast message needs to be sent to all requesters.
This however would greatly decrease the
performance due to overhead of repeatedly sending
the same message. As a solution to this problem we
suggest maintaining a list of adjacent nodes at all
times. If a simple majority of hosts request same
documents we send a broadcast message to all
instead of individual unicast messages.
As with the case of ad Hoc networks a new or
returning node can enter the range of n1 and start
communication. If a node n
k
enters the moment n
1
sent the broadcast, n
k
would receive a copy of the
document, which can be saved in the repository of
n
k
. Our experimentation shows an interesting effect
on performance of this phenomenon, nonetheless we
show that broadcasting a document requested by
multiple hosts is in fact better than sending multiple
unicast messages to each requesting host.
4 SIMULATION AND ANALYSIS
The proposed protocol in section 3 has been
implemented in Java and interfaced with MADHOC
(Hogie) simulation tool. We run a number of 15,000
iteration / seconds, simulations to study the various
conditions of the protocol based on many
parameters. These parameters are discussed as
follows.
We assume that each user is equipped with a
laptop device or a Wi-Fi enabled PDA device. Each
device has a Omni directional transmission range of
100m. There are 100 users in a 1000m x 1000m
environment. This environment consists of various
spots with a random size no larger than 100m x
100m. These spots can be considered as shops or
other buildings. The transmission range is reduced to
40 m when inside a spot due to various factors. The
users move between spots using a random waypoint
model, where a user may pause for a random time,
decide a target destination spot then start moving
towards that spot. For the mobility model, we
assume the user moves with a speed of 3 m/s when
not in a spot and 2 m/s when inside the spot area;
amount of mobility within the spot is set to 60% and
outside is 40%. User may pause for up to 2 minutes
to look for a destination.
In our experiments we define 32 different
interest profiles. Each user in the MSN would have
to select four distinct interests. We match user’s
interests for a possibility of communication. Each
user has various documents of different types
including images, videos and audios. We assume
that no document is larger than 512Kb. Each user
can also create a document every 10 seconds in the
simulation. Since we assumed that the Users
Repository is limited therefore we place a bound on
the size of the repository and leave it to 10MB
maximum in the host. Each host broadcasts an
announce message every 15 seconds, we assume this
delay because at pedestrian speeds 15 seconds is
generally considered as an adequate time for
MANETs (Haillot, 2008). Each node announces four
interests in its profile, any neighbor with at least one
of the similar interests, sends invite to share
documents. At a certain time if the repository is
filled and no further documents can be stored, the
node in question would remove the least recently
used document to make space for a newer document.
To evaluate the proposed protocol in section 3
we compare its performance with a modified version
of the same protocol. In the modified version of the
protocol, every host requests for every possible
document from a neighbor with no limits to numbers
of documents being shared, thus being a greedy host.
The consequence of the greedy host protocol would
be that each host requests and stores documents it
may not be interested in, but these documents can be
forwarded later to other interested hosts.
In Figure 3, a comparison is shown between the
numbers of documents received by both protocols.
On average it can be seen that the proposed protocol
has received more documents as compared to the
greedy version. The number of documents created is
clearly more than the documents received by either
protocol. It can be seen that our protocol receives
documents at a rate almost similar to the rate of
document creation. However the greedy protocol is
less efficient in this regard. In the beginning of the
simulation the rate for documents received by either
protocol is much lower, the reason could be that it
takes time for documents to disseminate in the
network.
Another aspect to be noted is that the number of
documents received by the greedy protocol is higher
than the proposed protocol in the beginning of the
simulation, i.e upto 3000 sec in this scenario; Since
greedy protocol enthusiastically searches and stores
more documents regardless of relativity to the
interests, for that reason it is able to obtain more
documents. However since there is a limited space
available in each repository the space quickly fills
up in the beginning of the simulation. When there is
no space to store a newer document, the node looks
for the least recently used document and removes it
from the repository. This technique for making more
space obviously has a disadvantage of removing
some documents before these are even shared on the
network.
WINSYS 2009 - International Conference on Wireless Information Networks and Systems
60
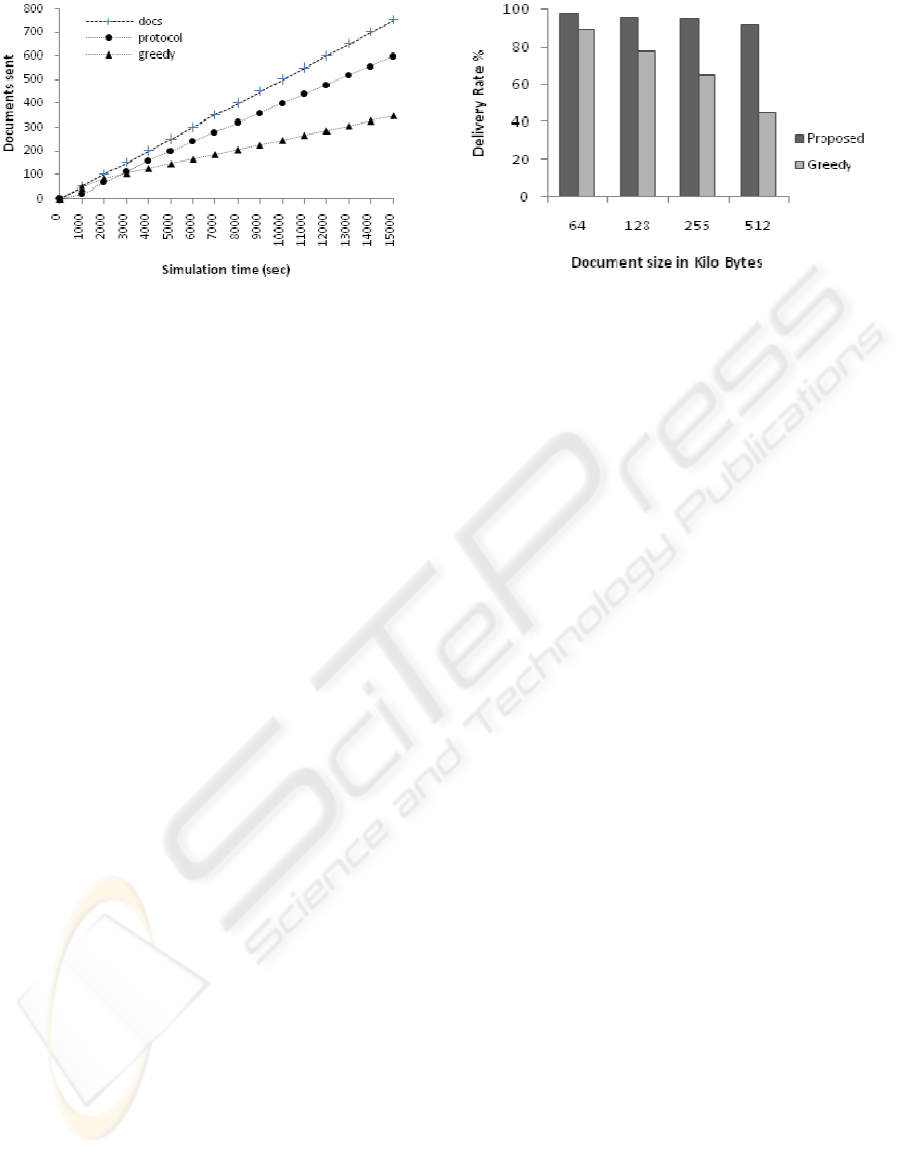
Figure 3: Number of documents received against sent for
both protocols.
Figure 4: Comparison of Delivery Rate for both protocols.
The proposed protocol is more efficient in
receiving documents compared to the greedy
approach. In the above simulation each host created
a document every 10 seconds on the average. From
simulation time 3000 sec onwards the rate of
documents sent by a host was 6.1 documents per
second on the average. However the greedy
approach had a much higher rate at 159.2 documents
per second. The huge difference in the rates of
documents sent reflects the huge amount of traffic in
the network created by the greedy approach. On the
other hand the rate for documents received for the
proposed protocol was 6.0 documents per second
compared to only 2.2 documents per second for the
greedy approach. Therefore the document delivery
ratio for the proposed protocol is 98.2% compared to
only 46.6% in the greedy approach.
Figure 4 shows the comparison of delivery rates
for both protocols based on document size. We limit
the size of document to 64, 128, 256 and 512 Kilo
bytes. It can be seen, with all document size the
delivery rate is much higher, i.e more than 92% for
the proposed protocol, but is lower for the greedy
approach. The size of documents affects the delivery
rate for documents using the greedy version of the
protocol.
5 CONCLUSIONS
Users of Mobile Social Networks share data only if
they are interested, therefore there was a need to
create a content driven communication protocol for
MANETs. In this paper we proposed a simple
protocol for data sharing in disconnected MANETs.
Our protocol is light weight and does not rely on
costly methods for constructing and maintaining
complex routes, (Khelil, 2005), (Leguay, 2006). The
ability of a node in MANET to store, carry and
forward documents has been fully exploited. We use
this ability of nodes replicating users to announce
their interest profiles, documents and share them. A
Node therefore successfully announces its
documents stored in repository and shares them with
other users. Documents thus stored are carried to
other locations and are shared with other users
having similar interest profiles. Simulation shows
that our protocol is effective in propagating
documents between senders and interested receivers
thus successfully disseminating and forwarding
messages in multi-hop connections in the network.
In the current version of the protocol we fixed the
threshold for broadcasting documents to near
neighbors. In future we hope to show the effects of
individual nodes decisions for broadcasting
documents, limitless repository and document size.
REFERENCES
Ziv, N.D., Mulloth B., 2006. “An Exploration on Mobile
Social Networking: Dodgeball as a Case in Point,
Proceedings of the International Conference on
Mobile Business, ICMB '06. 26-27 June 2006
Page(s):21 – 21
Masoudifar M., 2009. “A review and performance
comparison of QoS multicast routing protocols for
MANETs”, Elsevier Ad Hoc Networks, Volume 7,
Issue 6, August 2009, Pages 1150-1155
Jain S., Fall K. and Patra R., 2004. “Routing in a Delay
Tolerant Network”, Proceedings of ACM SIGCOMM,
(Portlan, OR), Aug. 2004.
Eagle N. and Pentland A., 2006. “Reality mining: Sensing
complex social systems,” Personal and Ubiquitous
Computing, Vol. 10, No. 4, March 2006, pp. 255–268.
Lugano G. and Saariluoma P., 2007. “To Share or not to
share: Supporting the user decision in Mobile Social
Software applications,” Proceedings of the
International User Modelling conference (UM 2007;
Corfu, Greece, 25–29 July). Lecture Notes in
A CONTENT DRIVEN DATA PROPAGATION PROTOCOL FOR MSN IN DISCONNECTED MANETS
61

Computer Science, volume 4511. Berlin: Springer. pp.
440–444
Raento M. and Oulasvirta A., 2005. “Privacy management
for social awareness applications,” Proceedings of 1st
Workshop on Context Awareness for Proactive
Systems — CAPS 2005, Helsinki, Finland, pp. 105–
114.
Hogie L., Bouvry P. and Guinand F., “The MADHOC
simulator”, http://agamemnon.uni.lu/~lhogie/madhoc/
Haillot J. and Guidec F., 2008. “A Protocol for Content
Based Communication in Disconnected Mobile Ad
Hoc Networks”, Proceedings of 22
nd
International
Conference on Advanced Information Networking and
Applications, AINA 2008, pp 188- 195.
Khelil, A. Marron, P.J. Rothermel, K, 2005. “Contact-
Based Mobility Metrics for Delay-Tolerant Ad Hoc
Networking”, Proceedings of the 13th IEEE
International Symposium on Modeling, Analysis, and
Simulation of Computer and Telecommunication
Systems (MASCOTS 05), Pages 435- 444, 27-29 Sept.
2005
Leguay, J., Friedman, T. and Conan, V., 2006.
“Evaluating Mobility Pattern Space Routing for
DTNs”, Proceedings of the IEEE INFOCOM 2006,
April 2006, vol. 5, pp 2540-2549.
WINSYS 2009 - International Conference on Wireless Information Networks and Systems
62
