
RFID AUTHENTICATION PROTOCOLS BASED ON ELLIPTIC
CURVES
A Top-Down Evaluation Survey
Michael Hutter
Institute for Applied Information Processing and Communications (IAIK)
Graz University of Technology, Inffeldgasse 16a, 8010 Graz, Austria
Keywords:
RFID, Elliptic curve cryptography, Authentication, Information security.
Abstract:
Authentication of RFID tags is a challenging task due to the resource-constrained environment they are oper-
ating in. In this article, we present a top-down evaluation survey for RFID-tag authentication based on elliptic
curves. First, we describe a general model to characterize different state-of-the-art public-key techniques that
provide entity and message authentication. Second, we present practical results of evaluations of elliptic-
curve based identification and signature schemes. We analyzed and compared the ECSchnorr, ECOkamoto,
and ECGPS protocol with respect to their computational complexity, storage requirement, and communica-
tion overhead. Furthermore, we examine different certificate-management solutions in RFID applications and
give size estimations from simulated scenarios. Our studies have led us to the result that elliptic-curve based
identification schemes and signature schemes have nearly the same complexity. ECOkamoto provides more
enhanced security features while ECGPS has been designed for efficient ”on-the-fly” authentication using of-
fline pre-computations. ECSchnorr might be preferred if primitive computation is performed online during tag
authentication.
1 INTRODUCTION
Radio Frequency Identification (RFID) is an emerg-
ing technology that has been already applied to ex-
isting applications such as supply-chain management
and inventory control. An RFID tag is composed of a
tiny microchip that is attached to an antenna. While
these tags are stuck onto objects, they can be identi-
fied and tracked by readers over an electromagnetic
field. RFID tags facilitate the process and the man-
agement of products during their life cycle. In the last
few years, many RFID devices have also been applied
to new applications where security plays a major role.
These applications are, for example, electronic pay-
ment, medical care, and access control. RFID tags are
very useful in this context by authenticating products
and also to thwart product counterfeiting.
RFID tags operate in a constraint environment and
are typically deployed in a large scale. It is evident
that such tags require appropriate protocols that are
extremely light-weight in terms of power, area, and
costs. Large effort has been made by the crypto-
graphic community to develop protocols that are suit-
able for RFID devices. One promising approach is to
use elliptic-curve cryptography (ECC). Elliptic curves
have proven to be applicable for resource-constrained
devices like RFID tags. For the same security level,
they need much smaller key sizes as opposed to other
asymmetric techniques like RSA. However, there ex-
ist many proposals for authentication protocols that
mainly differ in the used schemes and primitives. The
question of which kind of protocol becomes more ap-
propriate for a given application keeps therefore often
not straightforward to answer.
In this article, we focus on the evaluation of differ-
ent authentication protocols that are based on elliptic
curves. First, we define and describe a general model
for state-of-the-art public-key techniques which pro-
vide authentication as a cryptographic service. Sec-
ond, we present practical results of performance mea-
surements of authentication protocols that have been
especially designed for low-resource devices. We an-
alyze both identification and signature schemes of the
elliptic-curve variants of the Schnorr (Schnorr, 1990),
Okamoto (Okamoto, 1993), and GPS (Girault et al.,
2006) protocol. Furthermore, we analyze three dif-
ferent scenarios for efficient certificate management
in RFID applications. Our investigations show that
101
Hutter M. (2009).
RFID AUTHENTICATION PROTOCOLS BASED ON ELLIPTIC CURVES - A Top-Down Evaluation Survey.
In Proceedings of the International Conference on Security and Cryptography, pages 101-110
DOI: 10.5220/0002186201010110
Copyright
c
SciTePress

the described identification schemes and signature
schemes have nearly the same complexity in terms
of memory usage, computational effort, and commu-
nication. Point multiplication is the most complex
operation while additional hash computations have
a minor impact on the overall performance. The
right choice for a protocol depends on several is-
sues such as security (ECOkamoto), online computa-
tion of the scalar multiplication (ECSchnorr), or pre-
computed coupons offering ”on-the-fly” authentica-
tion (ECGPS).
The remainder of this article is structured as fol-
lows. Section 2 gives related works on that topic.
In Section 3, different public-key techniques are de-
scribed providing entity and message authentication.
Section 4 presents authentication protocols that have
been designed to be suitable for low-resource de-
vices. Section 5 discusses identification and signa-
ture schemes on RFID tags. In Section 6, we describe
our evaluation framework and discuss the used per-
formance metric. Results are given in Section 7. The
conclusion are drawn in Section 8.
2 RELATED WORK
There exist many articles that focus on elliptic-
curve cryptography and low-resource implementa-
tions on RFID devices. Large effort in that con-
text has been made by L. Batina et al. (Batina et al.,
2006). They have analyzed hardware implemena-
tions of the Schnorr and Okamoto protocol in the
case of elliptic curves over F
2
m
. Girault et al. (Girault
et al., 2007) presented hardware results of the GPS
authentication protocol based on an FPGA proto-
type implementation. Like the work of Girault,
M. McLoone et al. (McLoone and Robshaw, 2007)
assumed the use of so-called coupons, which repre-
sent (hashed) pre-computed commitments, and imple-
mented only the response calculation of the identifi-
cation scheme without performing the scalar multi-
plication. Low-resource implementations of elliptic-
curve processors in general have been investigated by
J. Wolkerstorfer (Wolkerstorfer, 2005), R. Schroeppel
et al. (Schroeppel et al., 2003), G. Gaubatz et
al. (Gaubatz et al., 2005), and Kumar et al. (Kumar
and Paar, 2006).
3 PUBLIC-KEY TECHNIQUES
There exist many applications nowadays that have to
provide security services such as authentication, con-
fidentiality, non-repudiation, or data integrity. Al-
Services
Protocols
Schemes
Primitives
Authentication
Signature
Schemes
Identification
Schemes
Encryption
Schemes
Key Agreement
Schemes
ECC RSA DH ElGamal NTRU ...
...
...
Entity
Authentication
Message
Authentication
Challenge-
Response
Witness-Challenge-
Response
Figure 1: Different public-key techniques lead to the cryp-
tographic service of authentication.
though, these services can be provided by using sym-
metric cryptography, public-key techniques have of-
ten been preferred in practice to tackle the prob-
lem of key distribution. However, cryptographic
services can not only be achieved by a specific
public-key technique. In contrast, there exist various
public-key techniques which lead to the same cryp-
tographic service. Authentication, for example, can
be achieved by various cryptographic protocols that
are based on different schemes and primitives. Both
digital-signature schemes and zero-knowledge proof-
of-knowledge schemes can be used in protocols to
follow the same security goal of entity authentica-
tion. Although many of these protocols have been
standardized in the last decade, less effort has been
made to uniformly classify these protocols according
to their underlying public-key technique. Hence, we
first describe a general model to characterize differ-
ent state-of-the-art public-key techniques. The model
separates all techniques into four levels: services, pro-
tocols, schemes, and primitives. Figure 1 shows the
natural structure of this model as an instance of au-
thentication.
3.1 Services
Authentication has become one of the most important
services of cryptographic applications. It is the pro-
cess where someone or something is confirmed to be
authentic and that a verifier is assured of the identity
of a prover. The authentication service can be sepa-
rated into two main types: entity authentication and
message authentication. Entity authentication is re-
ferred to as a real-time service where both parties the
prover and the verifier actively participate in a com-
munication. Thus, the identity of the prover is guar-
SECRYPT 2009 - International Conference on Security and Cryptography
102

anteed in a timeliness fashion. In contrast, message
authentication refers to the service where a verifier
gets assurance of a dedicated message that was gen-
erated by the prover. The difference between entity
and message authentication is therefore as follows. In
the first case, an entity or person is authenticated ex-
actly during an actual communication protocol. The
proof of authentication is here not transferable. In the
second case, a prover digitally signs a message which
can be verified even after the actual communication
process. This is useful when one party is not active
in the communication, which may happen in Internet
applications, for instance. However, the latter case
implicitly provides two additional cryptographic ser-
vices that are data integrity and non-repudiation of the
signed message which makes the use of digital signa-
tures more attractive in practice.
3.2 Protocols
Protocols are typically used to provide one or more
cryptographic services. They define a sequence of
steps for two or more entities that would like to
achieve these services. Such protocols differ in sev-
eral properties. First, they can be built upon different
schemes. Entity authentication protocols, for exam-
ple, can be based upon encryption schemes, signature
schemes, or identification schemes. Protocols that
provide message authentication can be constructed by
encryption schemes or signature schemes. Second,
protocols may differ in the number of message passes
between the involved entities. The number of mes-
sage passes of a protocol actually depends on the re-
quired message passes of the underlying schemes and
also on the protocol specific passes that are needed to
achieve a certain service. Challenge-response proto-
cols usually need two message passes but there ex-
ist also other protocols that need more or even less
message passes than the sum of message passes of
the individual schemes they involve. Third, there are
protocols that provide services for all or a subset of
involved parties. In an unilateral authentication pro-
tocol, for instance, only one entity is authenticated,
whereas in a mutual authentication process both par-
ties get assured to be authentic (Menezes et al., 1997).
3.3 Schemes
Schemes are the basic building blocks of crypto-
graphic protocols. They provide a set of crypto-
graphic operations and methods that are typically
combined within a protocol in order to achieve a cer-
tain security service. One of the most commonly used
schemes are encryption schemes, signature schemes,
identification schemes, and key-agreement schemes.
Encryption schemes provide encryption and decryp-
tion routines and make use of encryption primitives
such as ElGamal or RSA. Signature schemes provide
a signature generation and signature verification op-
eration. These schemes use additional cryptographic
functionalities such as hash and redundancy func-
tions. They are based on signature primitives like
the (EC)DSA. Identification schemes, in contrast, of-
fer a prove and verify operation. They typically pro-
vide additional functionalities such as random num-
bers that are needed to compute the challenges, for
instance. Key-agreement schemes offer methods to
agree on a common session key and are based on
primitives such as DH (Diffie and Hellman, 1976) and
MQV (Law et al., 2003). In addition to the described
operations, schemes also offer methods for key man-
agement such as the generation and verification of
public keys.
3.4 Primitives
The lowest level of our model are cryptographic prim-
itives. Primitives are algorithms that rely on math-
ematical hard problems. The intractability of these
problems are typically exploited to provide the se-
curity of a cryptographic protocol. The problem of
factoring large integers (e.g. RSA), solving discrete
logarithms (e.g. ElGamal, DSA, DH), or solving el-
liptic curve discrete logarithms (e.g. ECDSA, ECDH)
are the most prominent mathematical problems nowa-
days. However, there are also other problems known
where protocols and schemes are based upon. Such
protocols are, for instance, the NTRU cryptosystem
which is based on the Shortest Vector Problem in a
Lattice or the Goldwasser-Micali cryptosystem that is
based on the Quadratic Residuosity Problem.
4 AUTHENTICATION
PROTOCOLS
The fundamental security goal of authentication pro-
tocols is the resistance against impersonation through
both passive and active attacks. Passive attacks ex-
tract information by passively monitoring (eavesdrop-
ping) multiple protocol executions. In active attacks,
an adversary plays the role of the verifier and extracts
information by actively interacting with the prover.
In the following, we focus on authentication proto-
cols that are at least provably secure against passive
attacks. They are constructed of different types of
schemes but they use the same cryptographic primi-
tive which is based on the intractability of the ellip-
RFID AUTHENTICATION PROTOCOLS BASED ON ELLIPTIC CURVES - A Top-Down Evaluation Survey
103
tic curve discrete logarithm problem (ECDLP). First,
we describe protocols providing entity authentication.
These protocols are composed of encryption schemes,
signature schemes, or (zero-knowledge) identification
schemes. Second, we describe message authentica-
tion protocols that are constructed using signature
schemes. All protocols involve two parties (a reader
and a tag) and provide unilateral authentication.
The following notation is used throughout the pa-
per. Common parameters to all entities are: the un-
derlying finite field F
q
, the elliptic curve parameters a
and b, the curve point P with order n, and the public
key Q. Finite elliptic-curve points are upper case such
as P and Q. x is the x-coordinate of P and x is the in-
teger representation of the binary representation of x.
The private key is denoted by s, the protocol challenge
is denoted by c, and the response is denoted by y. All
used random numbers (ephemeral keys) are referred
to r and the security parameter t defines the number
of bits for the challenge. The variable e represents the
output of the one-way hash function h.
4.1 Entity Authentication based on
ECC Encryption Schemes
One way to reach entity authentication is to demon-
strate the knowledge of a private key through the de-
cryption of a ciphertext. In view of ECC, this can
be achieved by applying the ECC-based variant of
the ElGamal encryption scheme (ElGamal, 1984), for
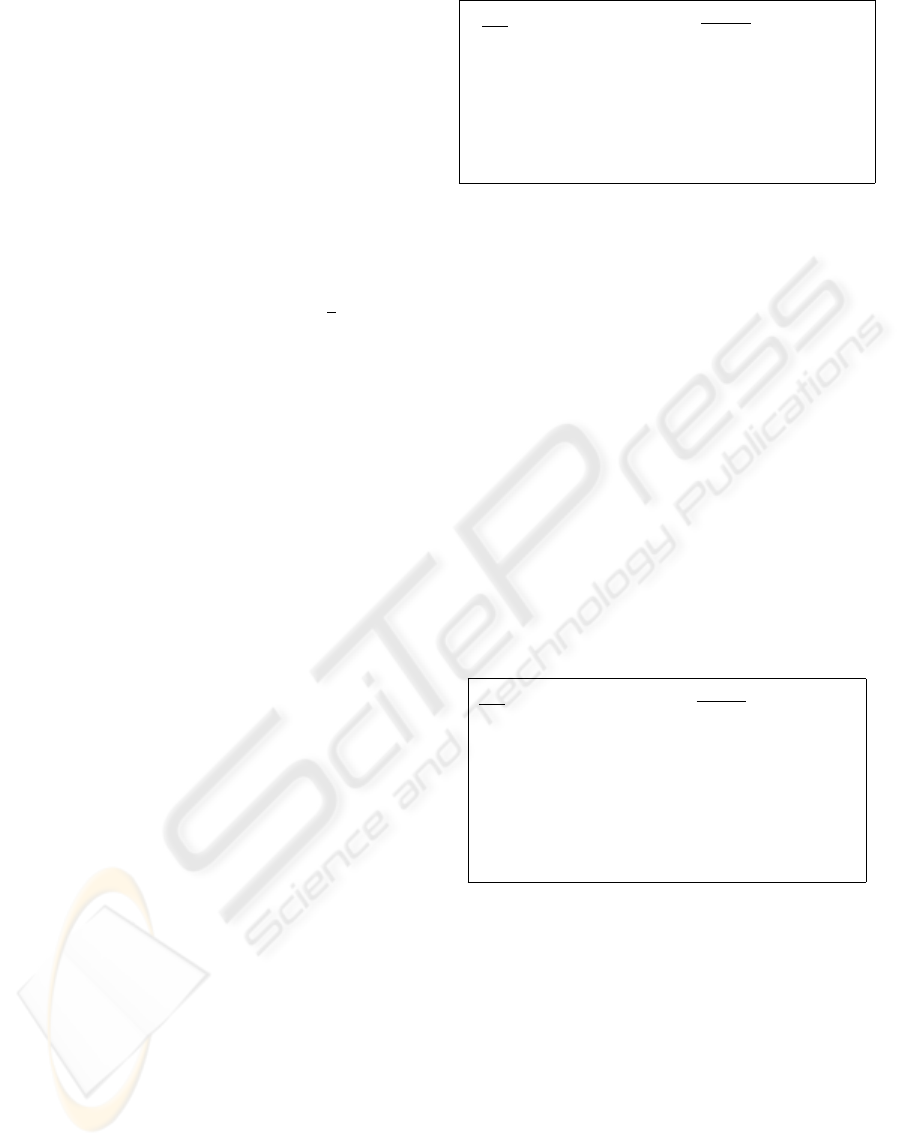
instance. In Figure 2, the principle of an entity-
authentication protocol is shown that is based on an
encryption scheme. First, the reader generates a ran-
dom number r and encrypts r together with the identi-
fier of the tag. Then it sends the result c, the identifier
ID and the witness e of the random number r to the
tag. The tag decrypts the message and verifies the ob-
tained values. It sends the decrypted value y to the
reader which accepts if it is equal to the previous gen-
erated random number r. Note that the random num-
ber is necessary to prevent replay attacks, the identi-
fier avoids reflection attacks, and the witness e = h(r)
is used to preclude chosen-text attacks.
Although encryption-based entity-authentication
protocols are semantically secure and provide se-
curity against passive and active attacks, they lack
several basic needs which limit the use in practi-
cal applications. First, they rely on encryption al-
gorithms which would not be licensed for an export
to external countries. Second, they often make use
of additional functionalities such as hash functions
and timestamps. These building blocks are usually
considered to be difficult to construct especially on
resource-constrained devices like RFID tags.
Tag Reader
r ∈
R
Z
n
e = h(r)
c,ID,e
←−−−−−−
c = Encrypt(r,ID)
(y,ID) = Decrypt(c)
verify h(y) = e
verify ID y
−−−−−−→
If y = r
then accept, else reject
Figure 2: Entity authentication based on an encryption
scheme.
4.2 Entity Authentication based on
ECC Signature Schemes
Another way to obtain entity authentication is
to demonstrate the knowledge of the private key
through the signing of a challenge. Figure 3
shows an authentication protocol according to
ISO/IEC 9798-3 (International Organisation for Stan-
dardization (ISO), 1993). The protocol is structured
as follows. First, the reader generates a random chal-
lenge c
1
and sends it to the tag. The tag now digitally
signs the challenge and sends the signature y together
with the identifier of the reader and the public-key cer-
tificate of the tag to the reader. The reader verifies
both the certificate of the tag and the signature and it
accepts the tag if the verification succeeded.
Tag Reader
r ∈
R
Z
n
, c
2
∈
R
Z
2
t
c
1
←−−−
c
1
∈
R
Z
2
t
y = Sign(c
1
,c
2
,ID)
c
2
,ID,y,cert
tag
−−−−−−−−−−−→
Verify cert
tag
Verify y
If verification succeed
then accept, else reject
Figure 3: Entity authentication based on a signature
scheme.
Entity-authentication protocols that are based on
signature schemes typically rely on a one-way hash
function to prevent existential-forgery attacks, i.e. to
find another challenge that results in the same signa-
ture.
In the following, we describe entity-authentication
protocols that are based on identification schemes.
These schemes have been especially adapted to work
also without encryption and hash functions. They
provide an interactive proof-of-knowledge and have
become more and more important for RFID applica-
tions because of their small footprint and ability to
pre-compute values to perform ”on-the-fly” authenti-
SECRYPT 2009 - International Conference on Security and Cryptography
104
cation (Girault et al., 2006).
4.3 Entity Authentication based on
ECC Identification Schemes
We describe three entity-authentication protocols that
are based on identification schemes. As opposed to
the previous described challenge-response protocols,
the given proofs are probabilistic rather than absolute.
A verifier (reader) is convinced by a prover (tag) to
be in possession of the private key. The described
schemes consist of three communication passes that
may be executed several times (sequential version) or
only in a single round (parallel version).
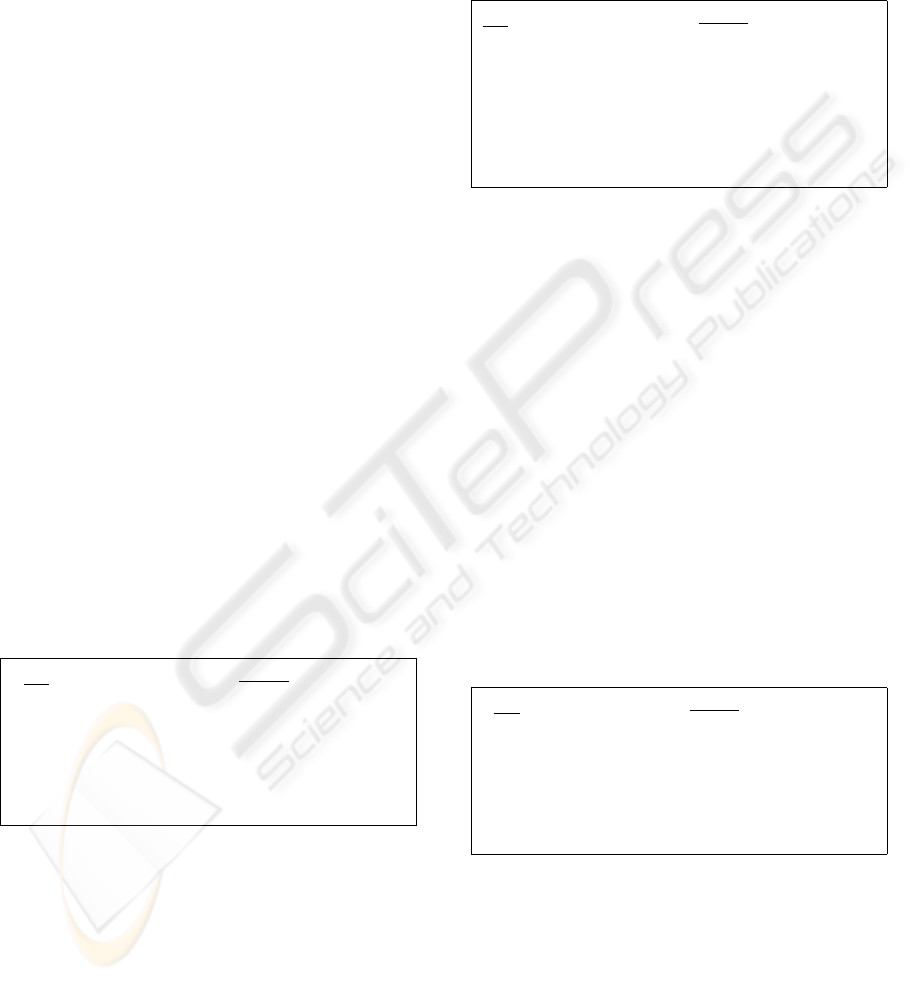
The first protocol is given in Figure 4. It is an
ECC-variant of the authentication protocol published
by C. Schnorr (Schnorr, 1990). First, the tag gener-
ates a random number r and calculates the elliptic-
curve point X as a witness. The tag sends the wit-
ness together with its certificate to the reader. Sec-
ond, the reader verifies the certificate and generates a
challenge c which it sends to the tag. The tag now
calculates y and send it as a response back to the
reader which accepts or rejects the tag. The proto-
col of Schnorr is an interactive identification scheme
that provides completeness, soundness, and honest-
verifier zero-knowledge. That means that it provides
the perfectly zero-knowledge property only when the
tag interacts with a honest reader. For cheated read-
ers, which may choose the challenge to be too large
(super-polynomial), it loses the zero-knowledge prop-
erty. The protocol is thus secure against passive ad-
versaries under the elliptic-curve discrete logarithm
assumption but it is not secure against active attacks.
Tag Reader
r ∈
R
Z
n
X ← rP X, cert
tag
−−−−−−−→
verify cert
tag
c
←−−−−−−
c ∈
R
Z
2
t
y = r + (s × c) mod n y
−−−−−−→
If yP + cQ = X
then accept, else reject
Figure 4: ECSchnorr authentication protocol.
The second authentication protocol is due to
T. Okamoto (Okamoto, 1993) shown in Figure 5. It is
a variant of the prior described Schnorr protocol but
provides additional security against active and con-
current attacks. First, the tag generates two random
numbers r
1
and r
2
. Using these two random num-
bers, it calculates the elliptic-curve point X and sends
it together with the certificate to the reader. As a sec-
ond step, the reader picks a challenge c and sends it
to the tag. Then, the tag calculates two responses y
1
and y
2
and sends it back to the reader which verifies
the authenticity of the tag. As opposed to the proto-
col of Schnorr, Okamoto is an interactive identifica-
tion scheme that provides a witness-indistinguishable
proof-of-knowledge.
Tag Reader
r
1
,r
2
∈
R
Z
n
X ← r
1
P
1
+ r
2
P
2
X, cert
tag
−−−−−→
verify cert
tag
c
←−−−−
c ∈
R
Z
2
t
y
1
= r
1
+ (s
1
× c) mod n
y
2
= r
2
+ (s
2
× c) mod n y
1
,y
2
−−−−−→
If y
1
P
2
+ y
2
P
2
+ cQ = X
then accept, else reject
Figure 5: ECOkamoto authentication protocol.
The third authentication protocol is an ECC-
variant of an interactive identification protocol pro-
posed by M. Girault, G. Poupard, and J. Stern in 2001.
It is part of the European project NESSIE (Preneel
et al., 2003) and has been standardized in the
ISO/IEC 9798-5 standard (International Organisation
for Standardization (ISO), 2004). The protocol is sim-
ilar to Schnorr but eliminates the modular reduction
during the response calculation by performing the op-
erations in Z. Like the Schnorr protocol, GPS is
proven to have the (statistical) zero-knowledge prop-
erty if the challenge c is chosen not too large. It
provides the honest-verifier zero-knowledge property
and is thus only secure against active attacks under a
given honest-reader assumption. In order to guarantee
the statistical zero-knowledge property, we followed
the equation r = c × s × 2
80
in our experiments as it
has been advised by the authors (Girault et al., 2006).
Tag Reader
r ∈
R
Z
2
ρ
X ← rP X, cert
tag
−−−−−−−→
verify cert
tag
c
←−−−−−−
c ∈
R
Z
2
t
y = r + (s × c) y
−−−−−−→
If yP + cQ = X
then accept, else reject
Figure 6: ECGPS authentication protocol.
4.4 Message Authentication based on
ECC Signature Schemes
Any of the previous described (interactive) iden-
tification schemes can be transformed into a
(non-interactive) signature scheme using the trans-
formation technique proposed by A. Fiat and
RFID AUTHENTICATION PROTOCOLS BASED ON ELLIPTIC CURVES - A Top-Down Evaluation Survey
105

A. Shamir (Fiat and Shamir, 1987). The non-
interactive signature schemes can be constructed
by replacing the challenge c by the outcome of a
cryptographic hash-function h. The input of the
hash function is the witness x concatenated with the
message m that has to be signed c = h(x,m). For the
security of the signature scheme it is necessary to
apply a hash function that is collision resistant, i.e.
that two messages do not lead to the same hash value.
Furthermore, the size of the hash function must be
chosen not too small to prevent existentially un-
forgeable signatures under adaptive chosen-message
attacks. Therefore, we applied a 160-bit SHA-1 hash
function to all described protocols and transformed
them into signature schemes.
5 IDENTIFICATION VS.
SIGNATURE SCHEMES
There are two major authentication services which
are entity authentication and message authentication.
The kind of service that an RFID tag has to provide
basically depends on the application. A typical sce-
nario where authentication plays an important role, is
protection against counterfeiting goods. There, RFID
tags proof the origin of objects to which they are at-
tached to. These tags are typically powered passively
and are implicitly involved in an active communica-
tion to the reader. Such tags actually have to pro-
vide at least entity authentication. There is no need
for RFID tags to provide additional cryptographic ser-
vices such as data integrity or non-repudiation. This
actually discourages the use of signature schemes in
that scenario.
However, there exist also other scenarios where
it becomes important for a tag to provide message-
authentication capabilities. Suppose the case where
the reader has to transfer the proof of the tag’s origin
or has to prove the authenticity of a tag even at some
later instant of time. Digital signatures provide these
services which can not be realized using identification
schemes.
In the following, we focus on the evaluation
of different identification and signature schemes.
Each scheme provides specific services and tradeoffs
among costs, security, and performance.
6 PROTOCOL EVALUATION
In order to evaluate the performance and efficiency
of the described authentication protocols, we have
Certificate
Version: 1
Serial Number: 4660
Signature Algorithm: ecdsaWithSHA1 (1.2.840.10045.4.1)
Issuer: CN=TestCA
Valid not before: Thu Feb 12 18:08:14 CET 2009
not after: Tue Feb 12 18:08:14 CET 2019
Subject: CN=14443A00,EMAIL=test@test.com
SubjectPublicKeyInfo:
Algorithm: ecPublicKey, NISTp192 (1.2.840.10045.2.1)
SubjectPublicKey:
03:32:00:04:62:B1:2D:60:69:0C:DC:F3:30:BA:BA:B6:
E6:97:63:B4:71:F9:94:DD:70:2D:16:A5:63:BF:5E:C0:
80:69:70:5F:FF:F6:5E:5C:A5:C0:D6:97:16:DF:CB:34:
74:37:39:02
SignatureAlgorithm: ecdsa-with-SHA1 (1.2.840.10045.4.1)
Signature:
30:35:02:18:1F:91:F5:89:8B:4F:C5:D3:47:D8:7C:F2:5D:8F:
AE:53:6F:F7:39:3E:B2:D3:18:92:02:19:00:B4:F5:9A:F7:3B:
13:80:48:B3:86:82:42:62:C8:23:57:7A:C5:A9:A6:B5:96:C2:
D9
Figure 7: Structure of a generated standard X.509 certifi-
cate.
developed a framework in Java. The framework is
able to model an RFID system involving several com-
ponents such as a tag, reader, air-interface, RFID-
communication protocol, cryptographic protocol, and
public-key management capability. Using this model,
we have been able to simulate different RFID sce-
narios that apply different settings, protocols, and
schemes. As a common cryptographic primitive,
we have used a standardized 192-bit NIST elliptic
curve (National Institute of Standards and Technol-
ogy (NIST), 2000) defined over the finite field GF(p).
The main operation of the primitive is a scalar mul-
tiplication that adds k copies of a certain elliptic-
curve point P together. For achieving this operation,
we applied the Montgomery method using standard-
projective coordinates. For the evaluation of different
interactive identification schemes, we considered only
the one round l = 1 (parallel) version. The size of the
challenge is defined by the security parameter t. It has
been chosen to be 48 bits. The probability of cheating
the verifier is therefore l/2
t
= 1/2
48
.
For the signature schemes, we applied the SHA-
1 hash function and used the same security parame-
ter as used for the identification schemes. Further-
more, we simulated a simple public-key infrastruc-
ture where the public-key of an RFID tag is signed
by a trusted third party. This certificate is stored in
the memory of the tag and is transmitted during the
tag authentication process.
6.1 Certificate Management
We considered three different scenarios for certifi-
cate management in an RFID application. All scenar-
ios are based on the International Telecommunication
Union (ITU-T) standard X.509 for Public-Key Infras-
tructure (PKI). Only version 1 certificates have been
SECRYPT 2009 - International Conference on Security and Cryptography
106

created to restrict the size of the certificates that will
be stored in the non-volatile memory of RFID tags. In
the first scenario, a standard X.509 certificate is gener-
ated. The structure of this certificate is shown in Fig-
ure 7. It contains attributes such as the version num-
ber, serial number of the certificate, issuer and subject
identifier, validity, public-key data, and the signature
of the certificate. The certificate is encoded using the
Distinguished Encoding Rules (DER) which results in
a binary representation of the given Abstract Syntax
Notation One (ASN.1).
The second scenario takes compressed certifi-
cates, which only store the x coordinate of the pub-
lic key since the y coordinate can be easily recon-
structed by solving the curve equation. This technique
is known under point compression and is claimed by
U.S. patent 6141420.
In the third scenario, we only stored the variable
part of the certificate, which are the public key, the se-
rial number of the certificate, and the signature. The
rest of the certificate can be reconstructed by a reader
which adds the remaining constant part of the certifi-
cate to obtain a valid X.509 certificate. The last sce-
nario might be preferably used in RFID applications
where less memory is an urgent requirement.
7 RESULTS
In the following, we describe a protocol-performance
metric of all described authentication protocols of
Section 4. The protocols have been evaluated based
on different criterias such as their security assump-
tions, storage requirements, computational effort, and
communication overhead. First, we present results of
analyzed authentication protocols that are based on
identification schemes. Second, we focus on results
obtained from the evaluation of authentication proto-
cols which are based on signature schemes.
7.1 Authentication Protocols based on
Identification Schemes
The performance metric of the described authentica-
tion protocols is given in Table 7.1. All protocols
provide an interactive proof-of-knowledge and are
secure against impersonation under passive attacks.
ECOkamoto also provides provably security against
active and concurrent attacks. The protocols are not
secure against reset attacks as shown by Cannetti et
al. (Canetti et al., 2000) but can be protected as shown
by Bellare et al. (Bellare et al., 2001).
The memory requirement of the protocols has
been characterized by considering the storage of the
Table 1: Authentication Protocols based on Identification
Schemes.
Schnorr Okamoto GPS
Zero knowledge
honest- witness- honest-
verifier indist. verifier
Crypt. Service
Entity auth. Yes Yes Yes
Message auth. No No No
Security against
Passive attacks Yes Yes Yes
Active attacks No Yes No
Concurrent attacks No Yes No
Reset attacks No No No
Memory [byte]
Private key 24 48 24
(Certificate 1 268 292 268)
(Certificate 2 243 267 243)
Certificate 3 76 100 76
Total 100 148 100
Computation
Size of scalar 24 48 40
#Additions 771 1,544 1,283
#Subtractions 769 1,536 1,281
#Multiplications 3,271 6,542 5,447
#Squarings 962 1,924 1,602
#Inversions 2 4 2
#Hash comp. 0 0 0
Total Operations 5,775 11,550 9,615
Estim. Cycle Count 993,432 1,986,864 1,630,872
private key and the certificate of the public key. The
private key needs 24 bytes for all protocols except for
ECOkamoto, which needs 48 bytes for one additional
private key. The size of the certificate depends on the
scenario described in the previous section. For a stan-
dard X.509 certificate, as given in Scenario 1, we ob-
tained a size of 268 bytes for ECSchnorr and ECGPS,
and 292 bytes for ECOkamoto due to the storing of an
additional public key. (see Figure 7 for the structure
and content of the certificate). For the second sce-
nario, we applied a point compression technique and
yielded a certificate size of 243 bytes and 267 bytes,
respectively. In the third scenario, only the variable
part of the certificate is stored that is the public-key
(24 bytes for the x-coordinate of one public key), the
signature (48 bytes), and the serial number (4 bytes).
Thus, we obtained a certificate size of 76 bytes and
100 bytes, respectively. By taking the third scenario
as a reference, we got a total memory usage of 100
bytes for both ECSchnorr and ECGPS and 148 bytes
for the ECOkamoto protocol.
The computational complexity of the protocols
has been evaluated as follows. First, we have de-
termined the elemental number of finite-field opera-
tions by counting the appropriate simulation-method
invocations. ECSchnorr needs 5,775 operations,
RFID AUTHENTICATION PROTOCOLS BASED ON ELLIPTIC CURVES - A Top-Down Evaluation Survey
107
76
24
6
24
100
48
6
24
76
40
6
24
0
20
40
60
80
100
120
140
160
180
Communication [bytes]
ECSchnorr ECOkamoto ECGPS
Certificate Response Challenge Witness
Figure 8: Communication overhead of evaluated identifica-
tion schemes.
ECOkamoto needs 11,550 operations, and ECGPS
needs 9,615 operations. Second, we empirically
weighted the operations due to their computational
complexity. We estimated the cycle counts for the
finite-field operations by assuming 45 cycle counts for
modular addition and subtraction, 220 cycle counts
for modular multiplication, 176 (=220*0.8) cycle
counts for squaring, and 17,600 (=220*80) for mod-
ular inversion. By summing up the weighted values,
we obtained a rough estimation for the overall compu-
tational efficiency of the analyzed protocols. The re-
sults are presented in the bottom of Table 7.1. It shows
that in our experiment ECSchnorr is the most efficient
protocol resulting in a total cycle count of 993,432
followed by ECGPS with 1,630,872 and ECOkamoto
with 1,986,864.
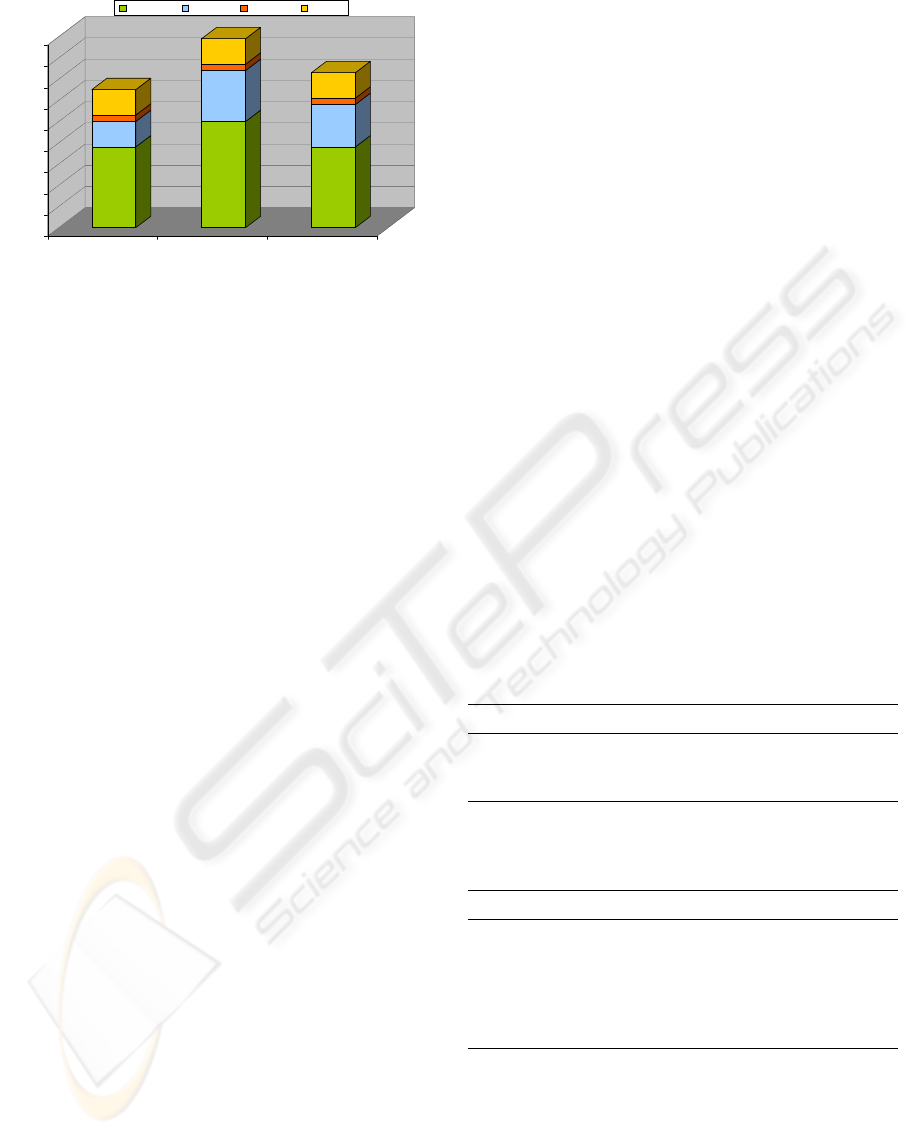
The evaluation result of the protocol-
communication overhead is shown in Figure 8.
It shows that the ECSchnorr protocol needs the
smallest amount of communication bytes which
is 130 bytes. ECGPS needs 146 bytes because of
the increased size of the response. As opposed to
ECSchnorr, no modulo reduction of the response
value is performed in ECGPS. However, this allows
faster response calculations but needs more bytes
to be transferred over the air interface. The highest
obtained value is due to ECOkamoto which needs
an extra amount for the response and also for the
certificate. The total number of bytes for ECOkamoto
is 178 bytes.
Although a comparison of the described protocols
becomes largely fair at some level, it has to be noted
that there exist many variants and improvements for
their implementations in practice. One technique that
we have used in our evaluation is to reduce the mem-
ory usage by only storing the x-coordinate of the pub-
lic keys (point compression). Another common tech-
nique is to hash the witness to reduce the communi-
cation overhead which becomes rather interesting in
scenarios where the commitments are pre-computed
to be used as coupons. The challenge can also be
chosen with a low-hamming weight so that the final
multiplication in the response calculation can be omit-
ted. This offers speed advantages for scenarios that al-
low ”on-the-fly” authentication. However, in order to
compare different protocols, it is necessary to provide
common parameters and setting for all protocols to
become a fair evaluation in general. Thus, it is conve-
nient to deal with relative values rather than absolute
ones.
7.2 Authentication Protocols based on
Signature Schemes
Next, we analyze authentication protocols which
are based on different signature schemes. There-
fore, we transformed the ECSchnorr, ECOkamoto,
and ECGPS identification schemes into signature
schemes using the technique proposed by Fiat-
Shamir (Fiat and Shamir, 1987). All schemes are then
used in a challenge-response protocol according to
ISO/IEC 9798-3 (International Organisation for Stan-
dardization (ISO), 1993).
The performance metric of the resulting protocols
is shown in Table 7.2. All protocols provide security
against passive and active attacks and provide security
against existential-forgery attacks.
Table 2: Authentication Protocols based on Signature
Schemes.
Schnorr Okamoto GPS
Crypt. Service
Entity auth. Yes Yes Yes
Message auth. Yes Yes Yes
Security against
Passive attacks Yes Yes Yes
Active attacks Yes Yes Yes
existent. forgery Yes Yes Yes
Memory [byte] 100 148 100
Computation [byte]
Hash-input size 30 30 30
#FF Operations 5,775 11,550 9,615
#Hash comp. 1 1 1
Total Operations 5,793 11,568 9,633
Estim. Cycle Count 997,392 1,990,824 1,634,832
The memory usage of the signature schemes is the
same as for the identification schemes. We considered
the storing of the private key and the certificate hold-
ing the public key and the signature. Also the com-
putational costs are very similar to that of the eval-
uated identification schemes. The number of finite-
field operations keeps constant but an additional hash
calculation is needed to compute the signature. For
SECRYPT 2009 - International Conference on Security and Cryptography
108

all schemes, the input size of the hash functions is 30
bytes. We estimated the costs for that hash calcula-
tion by assuming 4,000 clock cycles for the computa-
tion. This corresponds to approximately 18 additional
finite-field multiplications. The overall complexity
of the evaluated signature schemes are therefore as
follows. ECSchnorr results in 5,793 finite-field op-
erations with a cycle count of 997,392 followed by
ECGPS with 9,633 operations and 1,634,832 cycles,
and ECOkamoto with 11,568 operations and a cycle
count of 1,990,824.
The communication of the described protocols is
composed of the challenge (message), which is sent
by the verifier, and the response (signature and cer-
tificate) that is sent by the prover. The results of our
investigations are shown in Figure 9. ECSchnorr pro-
vides the smallest amount of communication bytes
which is 126 bytes. ECGPS follows with 146 bytes
and ECOkamoto needs to transmit 222 bytes in our
experiment.
8 CONCLUSIONS
In this article, we presented a top-down evaluation
survey of different public-key techniques to achieve
RFID-tag authentication. First, we described a gen-
eral model to characterize different authentication
protocols and schemes. Second, we provided prac-
tical results of evaluations for elliptic-curve based
variants of schemes that have been especially de-
signed for low-resource devices. We analyzed both
identification schemes and signature schemes of EC-
Schnorr, ECOkamoto, and ECGPS. Our evaluation
has led us to the result that elliptic-curve based iden-
tification schemes and signature schemes have nearly
the same complexity in terms of memory usage,
computational complexity, and communication band-
width. For both types of schemes, the most resource-
consuming operation is the elliptic-curve point mul-
tiplication. The hash computation performed by the
signature schemes does not has a large impact on
the overall performance, even though that signature
schemes provide additional cryptographic services
such as non-repudiation, data integrity, and a transfer-
able proof-of-origin. In addition to that, our experi-
ments have shown that ECSchnorr is more efficient in
both computational effort and communication band-
width than ECOkamoto and ECGPS. This is the case
when the scalar multiplication is performed online
by the tag during the authentication process. If the
scalar multiplication is performed in an offline way
and the tag uses pre-computed coupons, for example,
ECGPS provides enhanced performance due to the
76
44
6
100
116
6
76
64
6
0
50
100
150
200
250
Communication [bytes]
ECSchnorr ECOkamoto ECGPS
Certificate Signature Message
Figure 9: Communication overhead of evaluated signature
schemes.
lack of the modulo reduction during response calcula-
tion. The performance of ECOkamoto, in contrast, is
higher than ECSchnorr and ECGPS due to the need of
storing, computation, and communication transfer of
an additional public-key pair. We conclude that each
protocol provides different tradeoffs among the cryp-
tographic service, storage, computational effort, and
communication bandwidth. ECOkamoto provides ad-
ditional security features while ECGPS has been de-
signed for efficient ”on-the-fly” authentication. EC-
Schnorr might be preferred if the primitive computa-
tion is done online by the tag itself.
ACKNOWLEDGEMENTS
The author would like to thank Manfred Aigner, Jo-
hannes Wolkerstorfer, and Martin Feldhofer for their
valuable inputs and helpful discussions. The research
described in this paper has been supported by the Eu-
ropean Commission funded project Collaboration at
Rural under grant number 034921 (Project C@R) and
the Austrian government funded project CRYPTA es-
tablished under the Trust in IT-Systems program FIT-
IT.
REFERENCES
Batina, L., Guajardo, J., Kerins, T., Mentens, N., Tuyls, P.,
and Verbauwhede, I. (2006). Public-Key Cryptogra-
phy for RFID-Tags. In Workshop on RFID Security
2006 (RFIDSec06), July 12-14, Graz, Austria.
Bellare, M., Fischlin, M., Goldwasser, S., and Micali, S.
(2001). Identification Protocols Secure Against Reset
Attacks. In Proceedings of the International Confer-
ence on the Theory and Application of Cryptographic
Techniques: Advances in Cryptology, pages 495–511,
London, UK. Springer-Verlag.
RFID AUTHENTICATION PROTOCOLS BASED ON ELLIPTIC CURVES - A Top-Down Evaluation Survey
109

Canetti, R., Goldreich, O., Goldwasser, S., and Micali, S.
(2000). Resettable zero-knowledge. In Proceedings of
the thirty-second annual ACM symposium on Theory
of computing, pages 235–244, New York, NY, USA.
ACM.
Diffie, W. and Hellman, M. (1976). New Directions in
Cryptography. IEEE Transactions on Information
Theory, 22(6):644–654.
ElGamal, T. (1984). A Public Key Cryptosystem and a Sig-
nature Scheme Based on Discrete Logarithms. In Ad-
vances in Cryptology - CRYPTO ’84, Santa Barbara,
California, USA, August 19-22, 1984, Proceedings,
volume 196 of Lecture Notes in Computer Science,
pages 10–18. Springer.
Fiat, A. and Shamir, A. (1987). How to prove your-
self: Practical solutions to identification and signature
problems. In In Advances in Cryptology - Crypto 86,
volume 263, pages 186–194. Lecture Notes in Com-
puter Science, Springer.
Gaubatz, G., Kaps, J.-P., Ozturk, E., and Sunar, B. (2005).
State of the art in ultra-low power public key cryp-
tography for wireless sensor networks. Proceedings
of the Third IEEE International Conference on Per-
vasive Computing and Communications Workshops,
pages 146–150.
Girault, M., Juniot, L., and Robshaw, M. (2007). The feasi-
bility of On-the-Tag Public Key Cryptography. In Mu-
nilla, J., Peinado, A., and Rijmen, V., editors, Work-
shop on RFID Security 2007 (RFIDSec07), July 11-
13, Malaga, Spain, pages 77–86.
Girault, M., Poupard, G., and Stern, J. (2006). On the fly
authentication and signature schemes based on groups
of unknown order. Journal of Cryptology, 19:463–
487.
International Organisation for Standardization (ISO)
(1993). Information Technology - Security Tech-
niques - Entity authentication mechanisms - Part 3:
Entity authentication using a public key algorithm.
International Organisation for Standardization (ISO)
(2004). ISO/IEC 9798 Part 5: Information technology
– Security techniques – Entity authentication –
Mechanisms using zero knowledge techniques.
Kumar, S. S. and Paar, C. (2006). Are standards compliant
Elliptic Curve Cryptosystems feasible on RFID? In
Workshop on RFID Security 2006 (RFIDSec06), July
12-14, Graz, Austria.
Law, L., Menezes, A., Qu, M., Solinas, J., and Vanstone,
S. (2003). An efficient protocol for authenticated
key agreement. volume 28, pages 119–134, Norwell,
MA, USA. Designs, Codes and Cryptography, Kluwer
Academic Publishers.
McLoone, M. and Robshaw, M. J. B. (2007). Public Key
Cryptography and RFID Tags. In Abe, M., editor,
Topics in Cryptology - CT-RSA 2007, The Cryptogra-
phers’ Track at the RSA Conference 2007, San Fran-
cisco, CA, USA, February 5-9, 2007, Proceedings,
volume 4377 of Lecture Notes in Computer Science,
pages 372–384. Springer.
Menezes, A. J., van Oorschot, P. C., and Vanstone, S. A.
(1997). Handbook of Applied Cryptography. Se-
ries on Discrete Mathematics and its Applications.
CRC Press. ISBN 0-8493-8523-7, Available online
at http://www.cacr.math.uwaterloo.ca/hac/.
National Institute of Standards and Technology (NIST)
(2000). FIPS-186-2: Digital Signature Standard
(DSS). Available online at http://www.itl.nist.
gov/fipspubs/.
Okamoto, T. (1993). Provably Secure and Practical
Identification Schemes and Corresponding Signature
Schemes. In Brickell, E. F., editor, Advances in
Cryptology - CRYPTO ’92, 12th Annual International
Cryptology Conference, Santa Barbara, California,
USA, August 16-20, 1992, Proceedings, volume 740
of Lecture Notes in Computer Science, pages 31–53.
Springer.
Preneel, B. et al. (2003). NESSIE Security Report, D20.
Available online at http://www.nessie.eu.org.
Schnorr, C.-P. (1990). Efficient Identification and Signa-
tures for Smart Cards. In Brassard, G., editor, Ad-
vances in Cryptology - CRYPTO ’89, 9th Annual In-
ternational Cryptology Conference, Santa Barbara,
California, USA, August 20-24, 1989, Proceeding,
volume 435 of Lecture Notes in Computer Science,
pages 239–252. Springer.
Schroeppel, R., Beaver, C., Gonzales, R., Miller, R., and
Draelos, T. (2003). A Low-Power Design for an El-
liptic Curve Digital Signature Chip. In Jr., B. S. K.,
C¸ etin Kaya Koc¸, and Paar, C., editors, Cryptographic
Hardware and Embedded Systems – CHES 2002, 4th
International Workshop, Redwood Shores, CA, USA,
August 13-15, 2002, Revised Papers, volume 2523 of
Lecture Notes in Computer Science, pages 366–380.
Springer.
Wolkerstorfer, J. (2005). Is Elliptic-Curve Cryptography
Suitable for Small Devices? In Workshop on RFID
and Lightweight Crypto, July 13-15, 2005, Graz, Aus-
tria, pages 78–91.
SECRYPT 2009 - International Conference on Security and Cryptography
110
