
A Traceability Service to Facilitate RFID Adoption in
the Retail Supply Chain
Gabriel Hermosillo, Julien Ellart, Lionel Seinturier and Laurence Duchien
INRIA Lille, Nord Europe, University Lille 1, Laboratoire LIFL, CNRS UMR 8022, France
Abstract. Nowadays, companies are suffering changes in the way they deal with
their inventories and their whole supply chain management. New technologies are
emerging to help them adapt to the changes and keep a competitive status, but the
adoption of such technologies is not always easy. Even though a lot of research
has been done for RFID, there are still some areas that are being left aside, like
the traceability aspect, which is one of the most important concerns in the retail
supply chain. We propose a service named TRASER (TRAceability SErvice for
the Retail supply chain) that will help the companies adopt the new technologies
into their existing environments, dealing with persistence and traceability, and
allowing the users to manage their operation according to their business rules,
workflows and historical data.
1 Introduction
Radio Frequency Identification (RFID) is a technology used to identify a tagged object
using radio frequency. It is mainly composed of an electronic tag attached to an ob-
ject, a reader that gathers the tag’s information and a computer system connected that
receives and processes the information provided by the readers [1]. RFID has come as
a relay to the bar code systems, bringing several advantages such as not to require a
line-of-sight between the tag and the reader, multiple tags read at once, possibility to
hide the tag or make it part of the design. The tags can be read from a short distance up
to considerably long distances (tens of meters with an active tag). Because of these ad-
vantages, RFID applications are growing widely in different domains, including health
care and medicine [2,3], warehouse management [4,5], aerospace and automobile in-
dustry [6, 7], construction and maintenance of oil facilities [8], retail and supply chain
management [9–11] and anti-counterfeit [12].
RFID has evolved during the last few years, from being an obscure technology,
almost unknown, used only by a small group of companies, to a fundamental technol-
ogy that is now adopted and used worldwide by many important companies, consumer
applications and governments. In commerce, RFID technology is mainly used for mon-
itoring inventory and identifying different assets (i.e. pallets, containers, etc.), while in
the industry, it is mainly used for monitoring production processes. In either environ-
ment, RFID can provide immediate and tangible benefits throughout the supply chain.
Rather than displacing bar codes, RFID will complement them, helping to facilitate all
the supply chain logistics in the companies that adopt it.
Hermosillo G., Ellart J., Seinturier L. and Duchien L. (2009).
A Traceability Service to Facilitate RFID Adoption in the Retail Supply Chain.
In Proceedings of the 3rd International Workshop on RFID Technology - Concepts, Applications, Challenges , pages 49-58
DOI: 10.5220/0002197200490058
Copyright
c
SciTePress
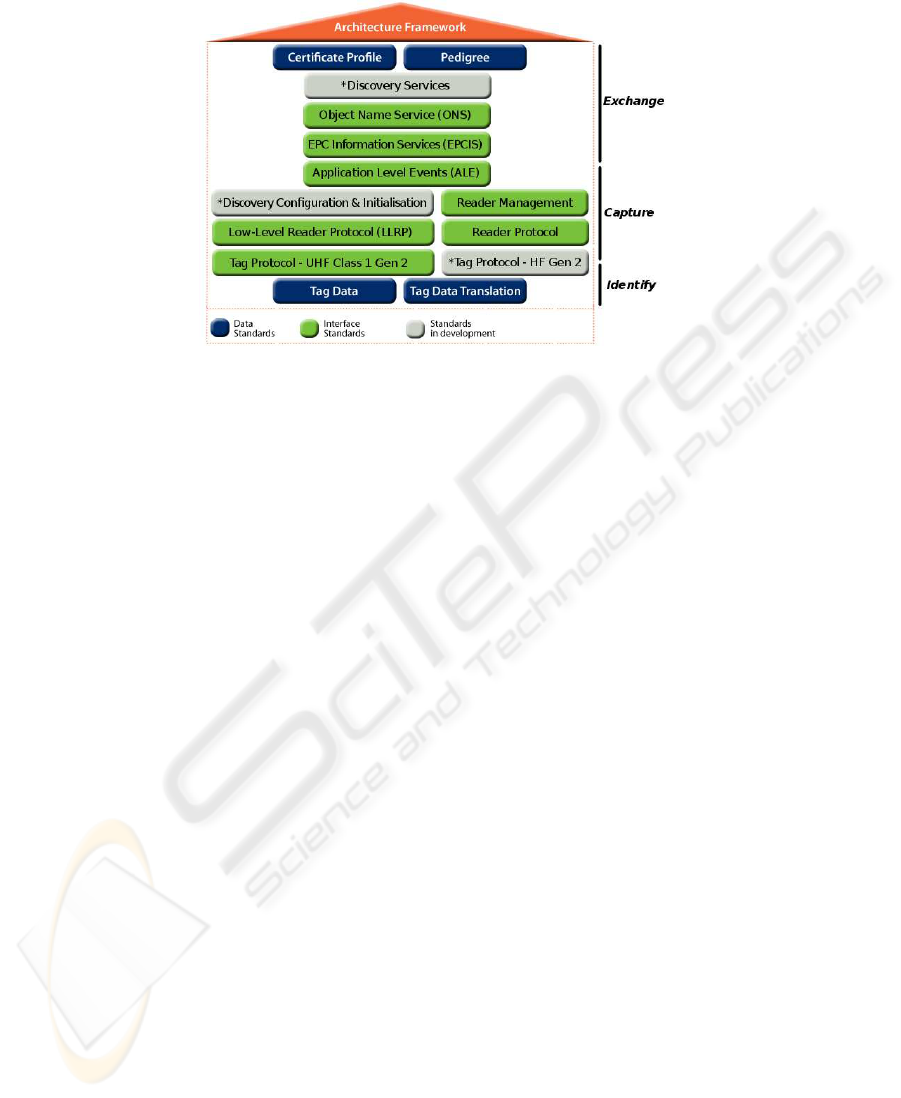
Fig.1. EPCglobal’s standards [1].
According to some authors, there are three main research streams in RFID applied
to the supply chain: conceptual analysis of opportunities (benefits and risks), case stud-
ies, and business values [13]. Others say that research publications are mainly focused
on technology, applications, and security [14]. The truth is that RFID is beginning to
become a key part of the industry, and its adoption is eminent for those who want to
keep a competitive status.
To correctly use and exploit the RFID technology, we need specific services that will
allow us to take advantage of the gathered information and to use it in a business model.
Some of these services are already defined by the EPCglobal’s standards, like the use of
ONS, EPCIS and ALE, as shown in Figure 1, but others are not so deeply considered,
such as traceability and event storing. The lack of research and implementation of these
services has made it harder for the industry to adopt RFID and integrate them to their
existing applications, specially for the retail supply chain, where these approaches are
some of the most important.
Our project intends to cover those needs. In the following sections we propose an
RFID service named TRASER that will deal with persistence and traceability, allowing
the users to manage their operations according to business rules, workflows and histori-
cal data. This service will be part of a whole platform, which has for objective to create
a shared technical infrastructure, generic and parametrized, capable of managing the
communication of heterogeneous systems (RFID, bar codes, NFC, etc.) among them
and with existing IT services, to help the companies exploit and benefit from the cur-
rent technologies. This research takes place within the ICOM project, funded by “Ple
de comptitivit” PICOM and the Rgion Nord-Pas-de-Calais in France.
This paper is organized as follows: Section 2 explains the motivation of the project.
Section 3 describes our proposal. Section 4 presents some of the related work. Finally,
section 5 concludes and discusses some future work.
50
2 Motivation for a Traceability Service
In the retail supply chain, it is important to know the amount of inventory held, where
the products are located, in what condition they are and sometimes even to what envi-
ronment they have been exposed. This information is usually gathered manually, and
occasionally registered and then fed into a business application to be considered. The
use of bar codes has been used to keep track of products and to relate them with the rest
of the information, but unfortunately it is not very accurate. Bar codes are generic, so
a reading of a bar code does not provide information about an individual product, but
rather of a particular kind of products. That means that if we have 10 identical products,
we can scan each one or just scan the same one 10 times and get the same result. This
often leads to human errors during the stock receiving and inventory processes, where
the employees just scan one product and multiply it by the number of identical prod-
ucts that they think they have, instead of scanning each product individually. Another
problem is that if during the process one of the products is lost, we would not know for
sure in which step of the process we lost it, because there is no individual tracking and
normally the employee will not scan all the products again on each step of the process.
A solution for these problems is to use an RFID infrastructure, which will allow
each tag to be considered individually, and then add a traceability service to get the
information about the product’s location and environment and complement the package
with persistence, so that not only the present status of the product is considered, but
also the historical data that has been gathered about it can be used. The process has
to be relatively easy for the industry to adopt the RFID services, and it needs to have
useful results and be quite simple to manage. In this context, the data contained in a tag
is not interesting when it is isolated, but when it is used within a business application
it becomes very important. Every information sent by the RFID or bar code readers
creates an event, which can be used to go from one state of the process to another, but
not all the events cause a state change, sometimes it is a group of events, or even the
order in which they happen, what is needed to create such a transition.
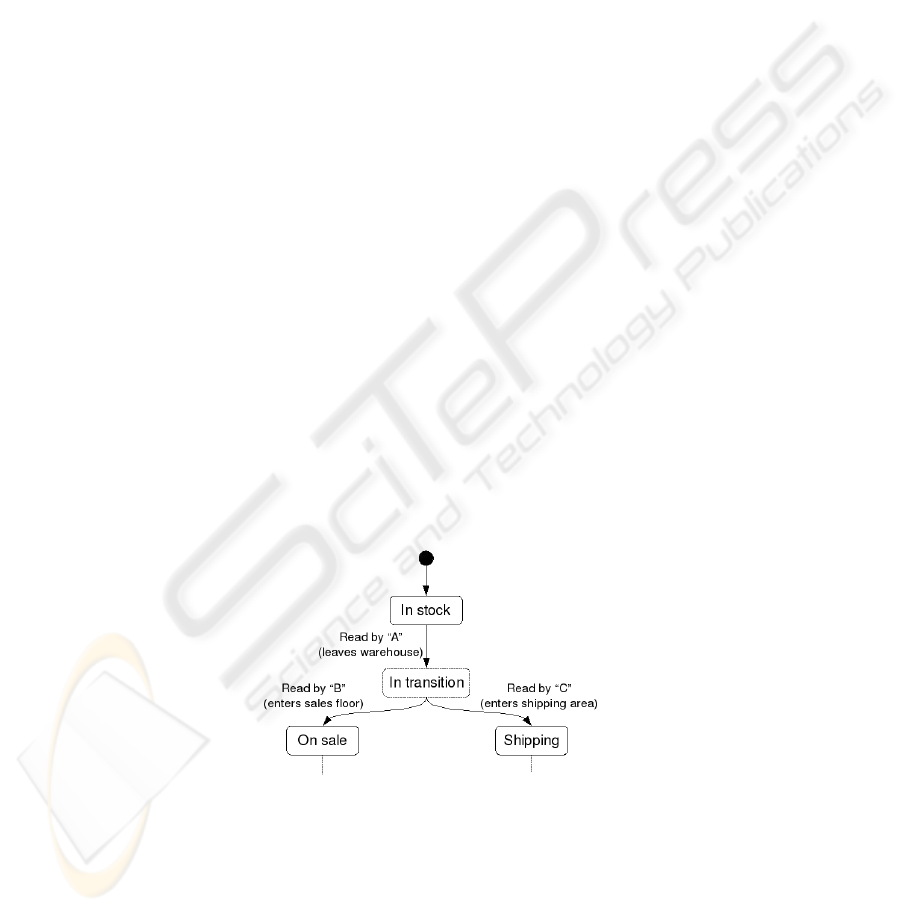
An example of such transitions can be seen in Figure 2. If we have a product X in
Fig.2. Transition example.
a warehouse, when the tag of X is read by reader A in the exit of the warehouse, and a
few minutes later it is read by reader B in the sales floor, it will create a transition of
product X to be on sale, but if instead it is read by reader C on the shipping area, the
51

transition of product X will go to shipping. So depending on the business process,
the status of the product will change according to its location.
Gathering all the possible information from the created event, like cause, time and
place, will help the final user to create a workflow that will fit better to their business
process by adding Complex Event Processing (CEP) to the system [15]. This can even
be used to create on-the-fly reports that are updated with each event and create alerts
when an anomaly is found, which help the user to keep a live monitoring of the process.
It is in this context that we propose TRASER, a traceability service for the retail supply
chain, that will allow the companies to know the status of their products and incorporate
that information into their business management.
3 TRASER: A TRAceability SErvice for the Retail Supply Chain
3.1 An Overview of TRASER
The objective of TRASER is not to create a completely new approach to solve the
problems, but to bring together the existing standards and research projects to create
a complete and useful service that can be easily adopted in the retail supply chain.
In order to understand how our system works, Figure 3 shows a basic architecture,
based on the EPCglobal’s standards [1]. The system receives the events created from
the readers (after being filtered), containing the reader ID, the time of read and the
Electronic Product Code (EPC) (step 1), among other fields that can be added according
to the user’s needs. These events will be translated to a business event (step 2), to have
a more significant meaning. To increase the usefulness of the events, there is a need
to store them so they can be available at any time and be considered for the decision
making process or be consulted by any system interested in them, and to cover this
need, we use the EPC Information System (EPCIS) repository (step 3), following the
EPCglobal’s standards [16]. For the external entities, it is not so easy to know where the
information about a tag is being stored, so there must be a service which can provide
the relation between a tag and the EPCIS repository containing it’s information. Here is
where the EPCglobal’s architecture requires the Object Name Service (ONS) (step 3’), a
service based on the Domain Name System (DNS) [16]. Finally, an application interface
will allow the existing applications to exploit the generated information (step 4) or even
send new business events through it (step 4’). This last step allows the generation of
events that are not related to the readers (i.e. a manual intervention in a certain step of
the process).
3.2 Traceability Service
To simplify and improve the traceability service, we divided the whole process in
two main parts: Event Translation, which will transform the ALE events into business
events, using Complex Event processing (CEP) and a rule engine, and the Process Man-
ager, which will receive the business event and create the transitions accordingly in the
Business Process Manager (BPM), as shown in Figure 4. Both parts are explained in
more detail in the following sections.
52
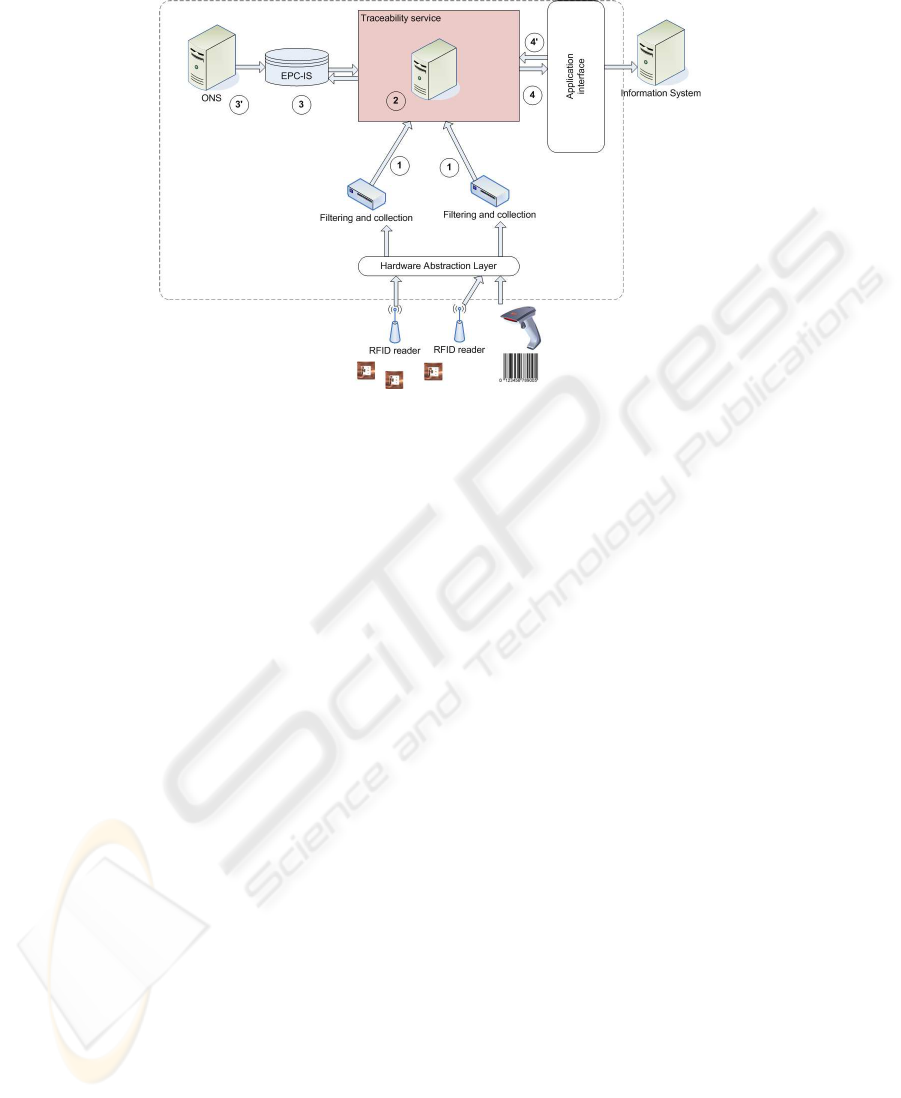
Fig.3. System architecture.
In the Event Translation part, the service has an Application Level Event (ALE) in-
terface that receives the events from the readers after being filtered, or any other source
that can generate an ALE event (like intelligent readers). The input of this interface
shall be an XML file containing the fields and information specified in the EPCglobal’s
ALE standard 1.1 [16]. After that, the events are transformed into EPCIS events (or
business events), using the business rules defined by the user. The EPCIS events are de-
fined in the EPCglobal’s EPCIS standard 1.0.1 [16], and are introduced into the system
using the Core Business Vocabulary created by EPCglobal for a better, and
yet standard, use and understanding of the events. Once the translation is done, the EP-
CIS events are then sent to the process manager, where they will be analyzed and will
allow the process to move from one state to another, according to the provided work-
flow of the business. This will be done using a state-transition diagram, that will show
the different states in which a tag (or the object containing the tag) will be followed. At
the end, the process engine will trigger a new event for the business applications or an
alert, in case some conditions are not met.
3.3 Complex Event Processing
In Complex Event Processing (CEP), the main goal is to figure out a meaningful and
complex event by analyzing multiple streams of simple events. These complex events
can be either the occurrence of a group of simple events in any order or the sequence
of them [15]. An example of this could be when a delivery is received and a sample of
the items is taken for quality purposes, if the sample is not sent back to the warehouse
within 2 hours, then an alert of missing stock will be generated. These kind of event
analysis can also be used to prevent merchandise theft from stores [17], which is also
one of the goals of this project. For example, if a product’s tag is read in the exit reader,
53
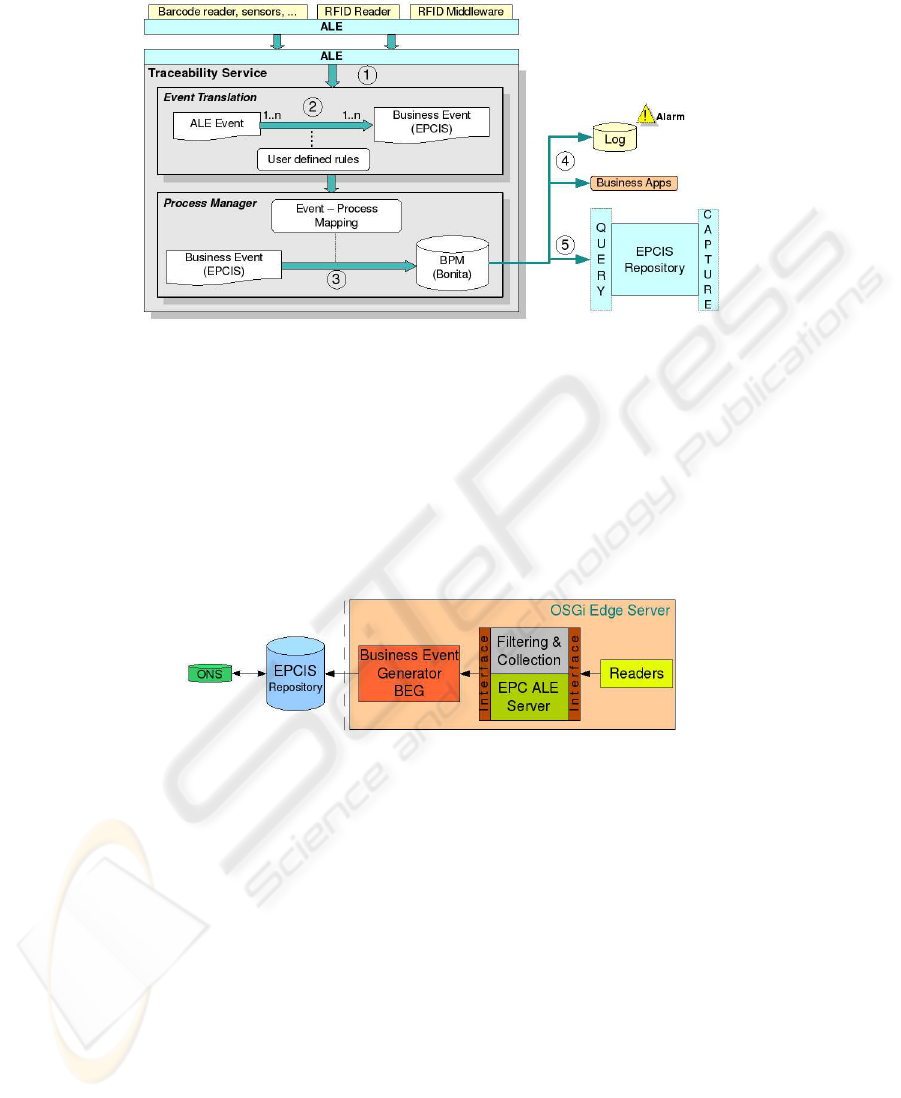
Fig.4. Traceability service.
without being read before at the register machine, the system can assume that a possible
theft is in progress and alert the security guards.
CEP is an essential tool for the retail supply chain, since it allows the relation of tags
to a specific business scenario. It can be used for simple things, like relating the reads
of a product tag and a container tag at the same time by the same reader and assume
that the product is being shipped inside the container, to the most complicated business
rules that a user can introduce, by relating time, cause and place, and trigger an action
accordingly [18].
Fig.5. BEG interaction.
We will be using the ASPIRE project as the base of our work [19,20], since it’s
design is very close to our needs and especially because it is an Open Source solution,
which will allow us to adapt it exactly as we need to, and finally it also has an active
community, eager to contribute with the adoption and correct use of RFID technologies.
The ASPIRE project’s specifications include a middleware component that deals with
CEP,called Business Event Generator (BEG), a configurablecomponentwhich captures
the raw events sent by the readers and generates new business events [21]. As shown in
Figure 5, the BEG receives the filtered events captured by the readers and then queries
the EPCIS to get the context information needed for interpreting the incoming data.
With all the gathered information, it finds the rules that can be applied to it and then
creates the corresponding business event, which in our case will allow the process to
move from one state to the other in the process manager.
54
3.4 Process Manager
The process manager is the service in charge of relating the business events, created by
the BEG, to the business processes. The products follow steps during their life cycle:
they are moved, packaged, shipped, received, etc. Those steps are part of a business
process. The RFID events are part of the transition between steps in the process. The
process manager aims to process the RFID events in order to follow the provided busi-
ness processes. To implement this part we will use Bonita, a workflow and BPM open
source solution [22].
The formal definition of a process allows to specify the expected steps that it will
follow and the expected triggers (i.e. RFID events) to go from one step to the other.
If an unexpected business event is received at a step where there is no corresponding
transition, that means there is an error in the process, either in the design or in the
execution of it. All the information obtained from the process (transitions, errors, etc.)
can be used by existing software applications, once the information is translated to the
format expected by them, which allows an easy adoption of RFID by the companies.
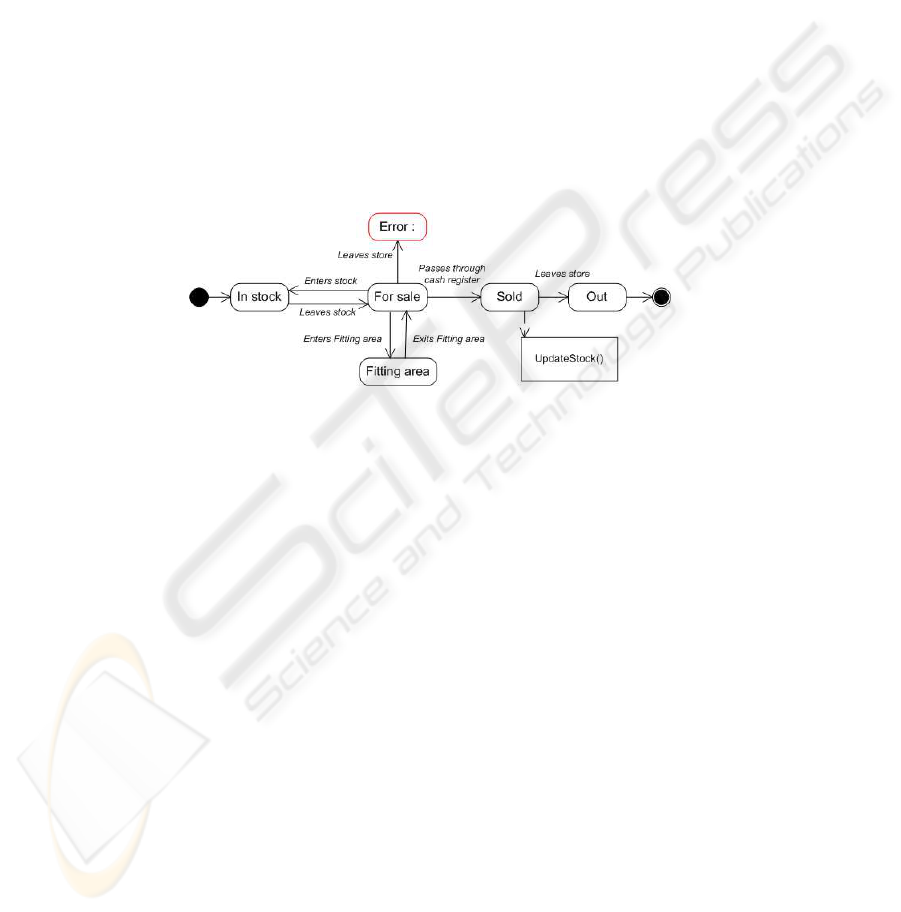
Fig.6. Store process.
Figure 6 shows an example of a simple process representing the states of a product
inside a store. The store is equipped with RFID readers between the areas. A normal
process for a product that is In stock, will be to go from the warehouse to the sales
floor, after receiving the Leaves stock event. Then it can enter and leave the fitting
area, with its corresponding events. Finally, it can go to the cash machine to get sold,
which would generate an event to update the stock and then leave the store.
When the steps are followed as expected the process continues normally, but when
an unexpected event arrives, it means we have a problem. For example, if we receive a
Leaves store event, without being in the Sold step, it gets an error and generates
an alert. This kind of alerts are an excellent feedback, since they can make the users
realize some mistakes in their process design or show them that the process is not being
followed as expected, either by the employees or by the clients.
4 Related Work
A lot of research is being done in different areas, in order to facilitate the adoption of
RFID mainly for governments, hospitals and retail suppliers. Most of the recent works
propose the use of CEP for obtaining meaningful information from the gathered data
and there are different approximations for this topic.
55

An attempt to apply the principle of separation of concerns in CEP has lead a re-
search to create a layered middleware for it, which consists on a logic structure layer, a
temporal constraint layer and an event detection layer [23]. They support their approach
by standing that a layered design provides a better understanding for RFID events.
A tool called Cascadia, capable of extracting and managing meaningful high-level
events from raw RFID data is another work on this area [24]. Cascadia offers a complete
system for managing RFID events, but it doesn’t use any standards for this, so the
interaction with other systems depends on specific development for the tool.
A research similar to our project presents a middleware for RFID and Wireless Sen-
sor Networks (WSN), using CEP in a partial EPC architecture, including an EPCIS
[25]. They present a good work for monitoring products, considering the environment,
but they lack of interaction with an ONS and don’t consider traceability in their appli-
cation.
5 Conclusions and Future Work
Being able to get the present and historic information about a product is very important
in the supply chain management, since it helps to make the right decisions in the right
moment. That is why traceability is one of the most important aspects for it, and the lack
of research and solutions that successfully implement traceability and persistence has
caused the retail supply chain to take longer to adopt RFID. In this paper we presented
a service that covers those needs with an easy-to-use tool that will allow the users to
exploit the benefits of RFID by integrating it into their business processes, helping them
also to get feedback about certain processes that are not being followed as expected.
We propose a service that integrates several existing solutions (like Bonita [22] and
ASPIRE [20]) to offer the final users a complete, interesting and easy-to-use applica-
tion. We are still in the process of implementing the service, working with the ASPIRE
team and talking with different companies in the retail supply chain to gather their needs
and offer solutions.
Acknowledgements
This project is partially funded by the “Ple de comptitivit” PICOM and the Rgion Nord-
Pas-de-Calais in France.
References
1. EPCglobal’s website. http://www.epcglobalinc.org
2. Tu, Y.J., Zhou, W., Piramuthu, S.: Identifying RFID-embedded objects in pervasive health-
care applications. Decis. Support Syst. 46 (2009) 586–593
3. Lai, C.L., Chien, S.W., Chen, S.C., Fang, K.: Enhancing medication safety and reduce ad-
verse drug events on inpatient medication administration using RFID. WTOC 7 (2008)
1045–1054
56

4. Tan, H.: The Application of RFID Technology in the Warehouse Management Information
System. In: ISECS ’08: Proceedings of the 2008 International Symposium on Electronic
Commerce and Security, Washington, DC, USA, IEEE Computer Society (2008) 1063–1067
5. Yan, B., Chen, Y., Meng, X.: RFID Technology Applied in Warehouse Management System.
In: CCCM ’08: Proceedings of the 2008 ISECS International Colloquium on Computing,
Communication, Control, and Management, Washington, DC, USA, IEEE Computer Society
(2008) 363–367
6. Ahmad, R., Yuqing, F., Cheng, Z., Jihua, Z.: Closing information loops with extended PLM.
In: CSECS’06: Proceedings of the 5th WSEAS International Conference on Circuits, Sys-
tems, Electronics, Control & Signal Processing, Stevens Point, Wisconsin, USA, World Sci-
entific and Engineering Academy and Society (WSEAS) (2006) 344–349
7. Strassner, M., Fleisch, E.: The Promise of Auto-ID in the Automotive Industry. Technical
report, (Auto-ID Center, Massachusetts Institute of Technology)
8. Domdouzis, K., Kumar, B., Anumba, C.: Radio-Frequency Identification (RFID) applica-
tions: A brief introduction. Adv. Eng. Inform. 21 (2007) 350–355
9. Albrecht, K.: Supermarket Cards: The Tip of the Retail Surveillance Iceberg. Denver Uni-
versity Law Review 79 (2002) 534–565
10. Sabbaghi, A., Vaidyanathan, G.: Effectiveness and efficiency of RFID technology in supply
chain management: strategic values and challenges. J. Theor. Appl. Electron. Commer. Res.
3 (2008) 71–81
11. Tu, Y.J., Piramuthu, S.: Reducing false reads in RFID-embedded supply chains. J. Theor.
Appl. Electron. Commer. Res. 3 (2008) 60–70
12. Chen, C.L., Chen, Y.Y., Huang, Y.C., Liu, C.S., Lin, C.I., Shih, T.F.: Anti-counterfeit own-
ership transfer protocol for low cost RFID system. W. Trans. on Comp. 7 (2008) 1149–1158
13. Madlberger, M.: A Model of Antecedents of RFID Adoption Intention in the Supply Chain.
In: HICSS ’09: Proceedings of the 42nd Hawaii International Conference on System Sci-
ences, Washington, DC, USA, IEEE Computer Society (2009) 1–10
14. Ngai, E.W.T., Moon, K.K., Riggins, F.J., Yi, C.Y.: RFID research: An academic literature
review (1995-2005) and future research directions. International Journal of Production Eco-
nomics 112 (2008) 510–520
15. Wang, G., Jin, G.: Research and Design of RFID Data Processing Model Based on Complex
Event Processing. In: CSSE ’08: Proceedings of the 2008 International Conference on Com-
puter Science and Software Engineering, Washington, DC, USA, IEEE Computer Society
(2008) 1396–1399
16. EPCglobal’s Standards. http://www.epcglobalinc.org/standards/
17. Huber, N., Michael, K.: Minimizing Product Shrinkage across the Supply Chain using Ra-
dio Frequency Identification: a Case Study on a Major Australian Retailer. In: ICMB ’07:
Proceedings of the International Conference on the Management of Mobile Business, Wash-
ington, DC, USA, IEEE Computer Society (2007) 45
18. Ku, T., Zhu, Y., Hu, K.: A Novel Complex Event Mining Network for Monitoring RFID-
Enable Application. In: PACIIA ’08: Proceedings of the 2008 IEEE Pacific-Asia Work-
shop on Computational Intelligence and Industrial Application, Washington, DC, USA, IEEE
Computer Society (2008) 925–929
19. Kefalakis, N., Leontiadis, N., Soldatos, J., Gama, K., Donsez, D.: Supply chain management
and NFC picking demonstrations using the AspireRfid middleware platform. In: Companion
’08: Proceedings of the ACM/IFIP/USENIX Middleware ’08 Conference Companion, New
York, NY, USA, ACM (2008) 66–69
20. ASPIRE’s website. http://aspire.objectweb.org
21. ASPIRE Middleware and Programmability Specifications. http://fp7-aspire.eu/fileadmin/
aspire/docs/D24.pdf
57

22. Bonita’s website. http://bonita.objectweb.org
23. Hu, W., Ye, W., Huang, Y., Zhang, S.: Complex Event Processing in RFID Middleware:
A Three Layer Perspective. In: ICCIT ’08: Proceedings of the 2008 Third International
Conference on Convergence and Hybrid Information Technology, Washington, DC, USA,
IEEE Computer Society (2008) 1121–1125
24. Welbourne, E., Khoussainova, N., Letchner, J., Li, Y., Balazinska, M., Borriello, G., Suciu,
D.: Cascadia: A System for Specifying, Detecting, and Managing RFID Events. In: MobiSys
’08: Proceeding of the 6th international conference on Mobile systems, applications, and
services, New York, NY, USA, ACM (2008) 281–294
25. Wang, W., Sung, J., Kim, D.: Complex Event Processing in EPC Sensor Network Mid-
dleware for Both RFID and WSN. In: ISORC ’08: Proceedings of the 2008 11th IEEE
Symposium on Object Oriented Real-Time Distributed Computing (ISORC), Washington,
DC, USA, IEEE Computer Society (2008) 165–169
58
