
PRACTICAL TRACEABLE ANONYMOUS IDENTIFICATION
Daniel Slamanig
1
, Peter Schartner
2
and Christian Stingl
1
1
Department of Medical Information Technology, Healthcare IT & Information Security Group
Carinthia University of Applied Sciences, 9020 Klagenfurt, Austria
2
Institute of Applied Informatics, System Security Group, Klagenfurt University, 9020 Klagenfurt, Austria
Keywords:
Anonymity, Anonymous identification, Authentication, Privacy protection, Public key cryptography, Smart
cards.
Abstract:
Internet privacy is of increasing interest, since online services are getting more and more ubiquitous and cover
many aspects of one’s daily life. Hence users leave information tracks and disclose information during usage
of services which can be compiled by third parties to infer users behavior, preferences etc. and thus may violate
user’s privacy. In this paper we propose a practical method for traceable anonymous identification which can
be used for online services in order to protect user’s privacy. It enables users to authenticate themselves to a
service provider, whereas the service provider is not able to identify authenticating users. However, the service
provider can be sure that only authorized users are able to authenticate. Since absolute anonymity may open
the door for dishonest behavior, our protocol incorporates traceability, which enables a service provider to
identify authenticating users in cooperation with an offline trusted third party. The proposed method is fully
compatible with real world scenarios, i.e. public key infrastructures based on X.509 certificates, and can be
easily deployed using state of the art smart cards. Furthermore, the proposed method is very efficient and we
give a performance analysis as well as a security analysis of the introduced protocols.
1 INTRODUCTION
Internet based services are increasing in popularity
and cover many aspects of one’s daily life, e.g. bank-
ing, shopping, online subscriptions, social network-
ing, e-governmentand increasingly also health related
services. It is indisputable, that these services pro-
vide a convenient way for everyday’s activities, how-
ever, they also disclose a lot of information about
user’s preferences, behavior, etc. and thus may vio-
late their privacy. In this context we are faced with a
phenomenon denoted as privacy myopia (Froomkin,
2000), which means that people often are not aware
of dangers related to privacy and sell or give away
their data without reflecting on potential negativecon-
sequences. There is a vast body of research on anony-
mous communication techniques (Danezis and Diaz,
2008) which aims at providing anonymity for Internet
users by means of “hiding” their network addresses,
i.e. IP-addresses. However, many services require
user-identification at higher layers, i.e. the service
level. In addition to communication anonymity it
may also be desired to provide anonymity in context
of authentication, since adversaries which are often
less considered are insiders at providers which host
the aforementioned services, are able to access ser-
vice level information and build dossiers of service
users. However, in context of authentication, anony-
mous communication as the only measure to provide
anonymity is necessary, but not sufficient. If users
authenticate themselves to services, this allows insid-
ers to link all actions conducted within a service us-
age to this user. Thereby, it is desirable to achieve a
unique identification of a user by means of authenti-
cation, since the provider of a service wants to limit
access to authorized users, access rights may be given
individually to users and resources may be related to
specific users. But the unique identification of users
also eases to track user’s behavior and consequently
may violate their privacy. Hence, to protect user’s pri-
vacy it is necessary to give user’s the ability to anony-
mously authenticate to a service and at the same time
give the service provider the ability to restrict access
to authorized users.
1.1 Contribution of this Paper
In this paper we will introduce a practical scheme for
anonymous identification, denoted as traceable ring
authentication, which enables authorized users to au-
225
Slamanig D., Stingl C. and Schartner P. (2009).
PRACTICAL TRACEABLE ANONYMOUS IDENTIFICATION.
In Proceedings of the International Conference on Security and Cr yptography, pages 225-232
DOI: 10.5220/0002217502250232
Copyright
c
SciTePress

thenticate at a service provider, whereas this service
provider is not able to identify the user. However,
he can be sure that solely authorized users will pass
an authentication. Our approach is comparable to,
but more efficient than, deniable ring authentication
(Naor, 2002) and verifiably common secret encoding
(Schechter et al., 1999), which can be seamlessly inte-
grated into existing public key infrastructures (PKIs).
Furthermore, it can be seen as an improved version
of (Lindell, 2007) with reduced and optimal round
complexity. Additionally, it provides traceability us-
ing tamper resistant devices like smart cards, which
enables a service provider to identify authenticating
users in case of misuse or fraud.
One particular application that we have in mind for
the introduced protocol are personal health records
(PHRs), e.g. Google Health or Microsoft Health
Vault, which provide health institutions the possibil-
ity to integrate user’s health information, e.g. medi-
cal documents, and user’s the convenient possibility
to manage and access their health information online.
Especially in context of highly sensitive health data,
user behavior, e.g. the frequency of interaction with
the service, may reveal information that can affect the
user’s future life negatively. Think of a user who ap-
plies for a job and the recruiter knows that the fre-
quency of interactions of the user with his say Google
Health account is far above the average within the last
year. This clearly does not indicate a “perfect” state
of health.
1.2 Public Key Encryption Scheme
A public key encryption scheme is a triple of poly-
nomial time algorithms (G,E,D), whereas G(1
k
) is a
key generation algorithm which, given a security pa-
rameter k in unary, outputs a secret decryption key
SK and a corresponding public encryption key PK.
In order to encrypt a message m, the encryption al-
gorithm E is given m, the public encryption key PK
and some auxiliary random input ω. The algorithm
outputs a ciphertext c and the encryption is denoted
as c = E
PK
(m,ω). The random input ω indicates that
the encryption scheme is probabilistic and we assume
that, unless stated otherwise, it provides semantic se-
curity, i.e. indistinguishability under chosen plaintext
attacks (IND-CPA). The decryption algorithm is given
the ciphertext c and the secret decryption key and out-
puts the message m which is denoted as m = D
SK
(c).
2 BASIC IDEA
We will now briefly sketch the idea of the proposed
approach. As mentioned in section 1.1 the main
goal is to provide users anonymous access to ser-
vices, whereas the access must be limited to autho-
rized users. One approach that is diametric to ours is
private information retrieval (PIR) (Chor et al., 1995).
In a PIR scheme a user queries data from a server,
whereas the server does not learn anything about the
queried data. Our approach targets at querying data
from a server, whereas the server learns which data
was queried, however has no clue who actually has
queried the data. Therefore we assume that the data
which is queried provides no identifying informa-
tion on the owner or authorized users respectively,
whereas we will not discuss the issue on how to re-
alize this. For simplicity, in context of a PHR we may
assume that user-centric encryption is used, whereas
every document is encrypted by a party prior to pro-
viding this data to the service.
Anonymous identification means that a user proves
to a service provider (SP) that he is a member of
the set of authorized users without revealing his iden-
tity. Thus, from the point of view of SP every user
is equally likely to be the one who is actually au-
thenticating to the service. A trivial solution to this
problem would be to give every authorized user the
same secret key k, which could be used in conjunc-
tion with a standard challenge-response authentica-
tion protocol. However, this approach suffers from
some serious drawbacks, i.e. a compromised key re-
quires the reissuing of a new secret key k
′
and so does
the revocation of a single user.
Our approach can be described as follows: The ser-
vice provider encrypts a random challenge using the
public keys of all authorized users and sends the re-
sulting vector to the anonymous user. The user de-
crypts the respective element of the vector and checks
whether the same challenge was encrypted for every
authorized user. If this check holds, the anonymous
user provides the challenge to the service provider.
If both challenges match, the user must be an autho-
rized user. This protocol also provides unlinkability,
i.e. different executions of the protocol of the same
user cannot be linked together. In order to be able to
identify users in case of misuse or fraud, we employ
a tamper resistant security token, e.g. a smart card,
which encrypts the user’s identity for an traceability
authority (TA) and appends it to the responded chal-
lenge. Consequently, the SP can give a transcript to
the TA, which is able to identify the corresponding
user, whereas the TA does not need to be online all
the time.
SECRYPT 2009 - International Conference on Security and Cryptography
226

3 RELATED WORK
Anonymous credential systems enable user’s to
anonymously obtain credentials for a pseudonym
from an identity provider, e.g. a signed token of the
age of the user, which can be anonymously shown to
other parties. These credentials can either be one-
show (Brands et al., 2007), which are essentially
based on blind signatures, or multi-show (Camenisch
and Lysyanskaya, 2001), which are based on group
signatures. The latter means that multiple showings of
the same credential cannot be linked. Clearly, anony-
mous identification can be implemented by means of
anonymous credential systems. However, we do not
require the variety of features of anonymous creden-
tial systems.
Thus, one may use the underlying concept of group
signatures (Ateniese et al., 2000; Chaum and van
Heyst, 1991) instead. Group signatures enable users
to anonymously sign messages on behalf of a group
and there exists a designated party, the so called group
manager, which is able to identify signers in case of
misuse or fraud. However, in contrast to group sig-
natures our approach is fully compatible with real-
world scenarios, i.e. public key infrastructures based
on X.509 certificates, and adding as well as removing
users can be easily achieved at a constant cost. Nev-
ertheless, (Canard and Girault, 2002) have proposed a
practical and efficient group signature approach based
on smart cards. But, their approach suffers form a
main drawback, i.e. compromising the smart card of
a single user requires a reinitialization of the entire
system. Another approach similar to group signatures
are ring signatures (Rivest et al., 2001). Ring sig-
natures enable users to anonymously sign messages
on behalf of a group, however, they provide fully
ad-hoc groups, there is no group manager involved
and their anonymity is unconditional. Consequently,
there is no possibility to revoke the anonymity of ma-
licious users. Ring signatures have also been used to
realize anonymous identification (Persiano and Vis-
conti, 2003) and there are also approaches to realize
ring signatures which provide anonymity revocation
(Xu and Yung, 2004). Nevertheless, in ring signature
schemes the user needs to perform a number of public
key operations that is linear in the size of the ad-hoc
group. In contrast to ring signatures, our approach re-
duces the computational cost by means of probabilis-
tic anonymity and thus provides more efficiency and
higher anonymity compared to ring signatures.
4 TRACEABLE RING
AUTHENTICATION
In context of traceable ring authentication (TRA) we
speak of the service provider (SP) who represents
the verifier and a group U of authorized users, the
so called ring, whereas every user u ∈ U may play
the role of a prover. The task for a prover is to
identify himself to the verifier, by proving member-
ship in the group U , such that the verifier solely
learns the membership, but not the exact identity of
the prover. Traceable ring authentication addition-
ally provides the possibility to identify a user who has
conducted the anonymous identification by means of
a third party, the so called traceability authority (TA).
Definition 1. A traceable ring authentication (TRA)
protocol is said to be secure if it satisfies the following
properties:
Anonymity. A TRA scheme is said to be anony-
mous, if a SP is not able to determine the identity
of an authenticating user with probability higher
than 1/|U |.
Correctness. A TRA scheme is said to be correct, if
the verifier always accepts a proof when he per-
forms the protocol with an honest prover in U .
Unforgeability. A TRA scheme is said to be un-
forgeable, if every non-member u /∈ U is unable
to run a protocol successfully with respect to any
U
′
⊆ U .
Unlinkability. A TRA scheme is said to provide un-
linkability, if different transcripts of the protocol
produced by the same prover can not be linked.
Traceability. A TRA scheme is said to be traceable,
if SP, given the protocol transcript, in cooperation
with the TA is able to identify the user who has
conducted the anonymous identification.
No-missatribution. A TRA scheme is said to pro-
vide no-missatribution, if the SP is not able to ma-
nipulate the identity escrow information in such
a way, that the TA would be able to attribute
an anonymous identification to a user who has
not conducted the anonymous identification. This
property also needs to hold for all users too.
4.1 Ring Authentication
Anonymousidentification realized by ring authentica-
tion can be described by means of the following pro-
tocols.
• REGISTER. An interactive protocol between a
user u
i
and the SP. User u
i
provides identifying
information ID
u
i
together with a certified public
PRACTICAL TRACEABLE ANONYMOUS IDENTIFICATION
227
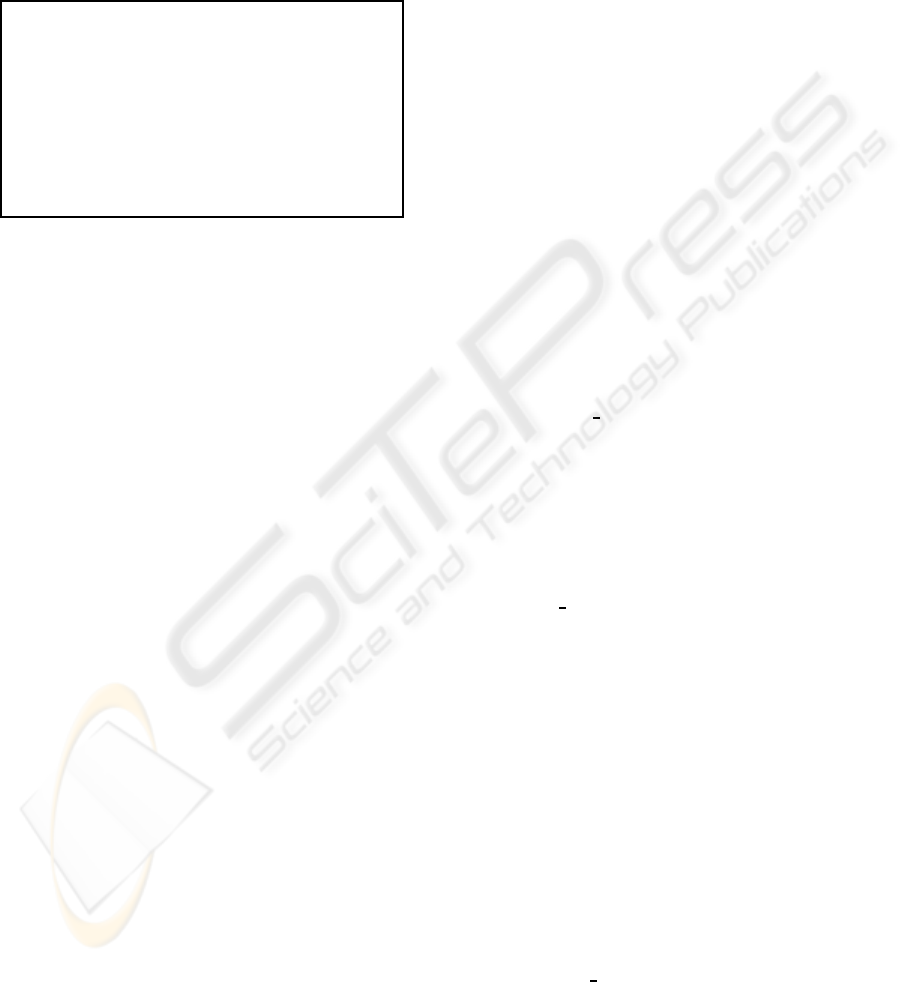
key PK
u
i
suitable for encryption, to SP, who adds
the tuple (ID
u
i
,PK
u
i
) to a public directory D .
• PROVE. An interactive protocol between a user
u
i
and the SP. SP sends an encrypted challenge
vector to u
i
who extracts the challenge and sends it
back to SP. If both challenges match, SP accepts,
otherwise he rejects the ring authentication.
Protocol 1. PROVE
1. SP → u
i
: Choose random r ∈
R
{0,1}
k
. Gen-
erate and send hC
1
= E
PK
u
1
(r,ω
1
),. . .,C
n
=
E
PK
u
n
(r,ω
n
)i, where ω
i
= f
R
(r,ID
u
i
).
2. u
i
→ SP : Decrypt C
i
to obtain r
′
. Check for
all j 6= i, 1 ≤ j ≤ n, whether C
j
= E
PK
u
j
(r
′
,ω
j
)
holds, where ω
j
= f
R
(r
′
,ID
u
j
). If this is true
send r
′
otherwise terminate the protocol.
3. SP : Check whether r
′
= r holds.
Subsequently we will provide a detailed description
of the PROVE protocol (see protocol 1). For simplic-
ity, let us assume that user u
i
proves membership in
the entire group U of n users, i.e. all users listed in D .
The idea behind PROVE is that SP encrypts a random
challenge r for every user u
i
∈ U and the auxiliary
random coins ω
i
for the probabilistic public key en-
cryption scheme, which are also called randomizers,
are not chosen uniformly at random, but computed
by means of a pseudorandom function f
R
which is
parametrized by the challenge r and the identity of the
respective user ID
u
i
. Note, that the output distribu-
tion of a pseudorandom function is indistinguishable
from uniformly distributed strings of equal length for
every computationally bound distinguisher. The user
decrypts the challenge r and, checks by means of the
pseudorandom function f
R
, whether SP behaves hon-
estly, i.e. has encrypted the same challenge for every
user. If this holds, the user returns the challenge to
the service provider, who on his part checks whether
the challenges match. It should be noted that for
efficiency purposes the checking on the user’s side
may also be probabilistic, i.e. the user only checks
whether κ < n randomly chosen elements of the vec-
tor were encrypted properly. However, this provides
only probabilistic anonymity, whereas the chances for
a cheating verifier heavily depend on the parameters
κ and n (see also section 4.4).
One efficient implementation of protocol 1 can be
achieved by using OAEP (Bellare and Rogaway,
1993) with low exponent RSA, which is also rea-
sonable for a practical implementation, since RSA is
among the most widespread cryptosystems in use to-
day. If we treat cryptographic hash functions, e.g.
SHA-1, as random oracles, then we can instantiate
our pseudorandom function f
R
by means of a col-
lision resistant cryptographic hash function H, i.e.
ω
i
= H(r||ID
u
i
).
4.2 Achieving Traceability
In order to achieve traceability we employ a tamper
resistant device, e.g. a smart card, for every user. This
device performs, among others, identity escrow on
behalf of the user in such a way, that a cheating user is
not able to manipulate the escrowed identity informa-
tion. Therefore we additionally introduce a new entity
called the traceability authority (TA) which is in pos-
session of a key pair (SK
TA
,PK
TA
) of a public key en-
cryption scheme that provides non-malleability under
chosen plaintext attacks (NM-CPA). The public key
PK
TA
will be integrated into the user’s smart card. It
must be mentioned, that this party will not be involved
online in the protocols, but may be contacted by the
SP in case of misuse or fraud. Furthermore, in order
to firstly achieve improved reliability and secondly to
reduce the required trust, the secret decryption key
corresponding to PK
TA
may also be shared among n
TAs, e.g. by means of a (t,n)-threshold scheme. Sub-
sequently, we will describe the protocols, whereas the
REGISTER protocol stays unchanged and will not
be explicitly treated here.
• REGISTER ESCROW. An interactive protocol
between the user u
i
, his smart card SC
u
i
and the
traceability authority (TA). The user chooses a
second identifier, i.e. a pseudonym, γ
u
i
at ran-
dom and sends it together with ID
u
i
to the TA.
The TA stores the tuple (γ
u
i
,ID
u
i
) and keeps γ
u
i
secret, such that it is only known to u
i
and TA,
and gives γ
u
i
and PK
TA
to SC
u
i
.
• PROVE T. An interactive protocol between a
user u
i
, his smart card SC
u
i
and SP. u
i
chooses
D
′
⊂ D and sends a suitable encoding of the iden-
tities in D
′
to SP. SP sends an encrypted challenge
vector to u
i
, who gives the challenge vector, a vec-
tor of all public keys in D
′
and a security param-
eter κ to SC
u
i
. SC
u
i
decrypts the challenge and
checks for κ public keys whether the challenge
was encrypted properly. If the check fails SC
u
i
returns ⊥, otherwise it encrypts the challenge to-
gether with the identity of u
i
for TA, the result-
ing ciphertext and the challenge for SP and returns
the result to u
i
. Subsequently, u
i
sends the result
back to SP. If the decrypted challenge and the send
challenge match, SP accepts, otherwise he rejects
the anonymous identification.
• IDENTIFY TRA. An interactive protocol be-
tween SP and TA, whereas SP sends a transcript
of the traceable ring authentication protocol to TA
and TA returns the identity ID
u
i
of the correspond-
ing user.
SECRYPT 2009 - International Conference on Security and Cryptography
228
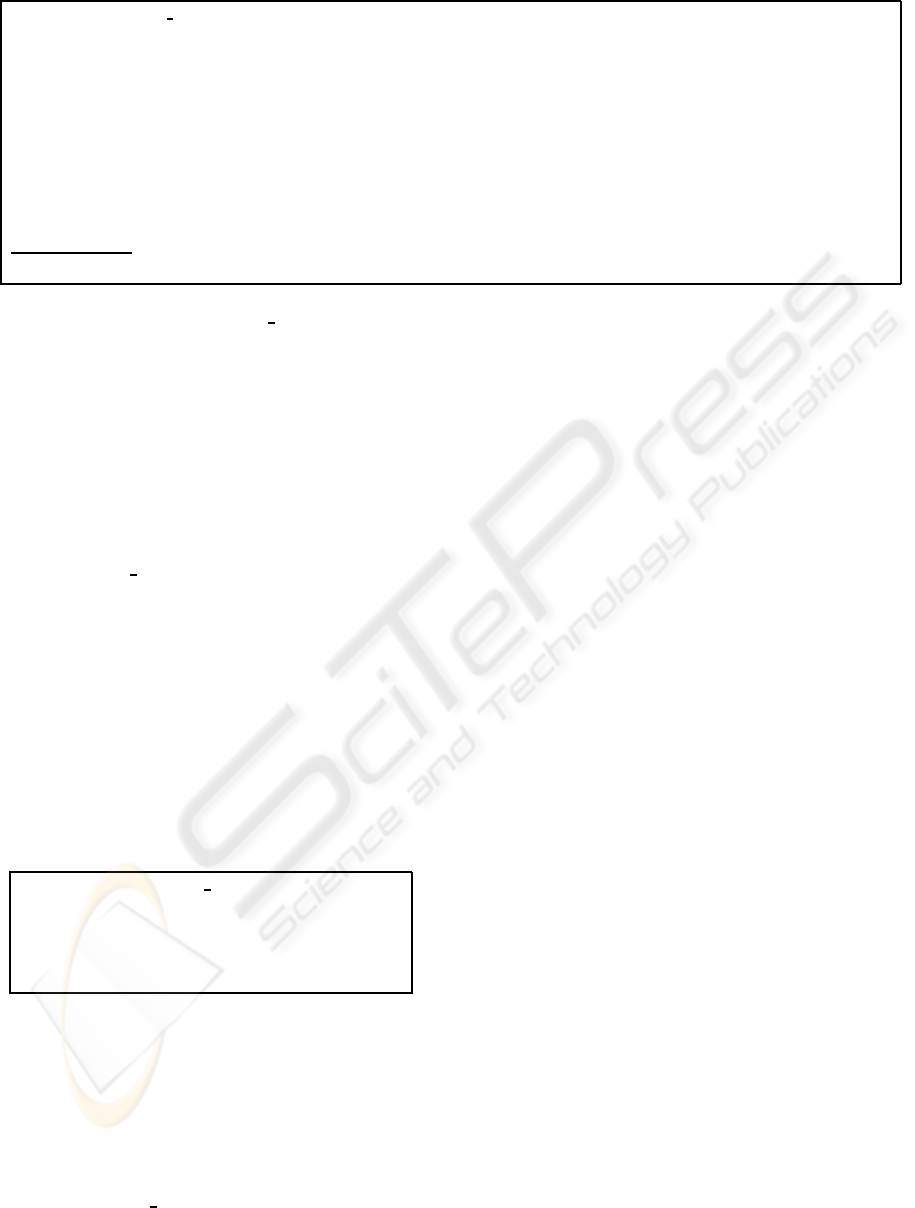
Protocol 2. PROVE T
1. u
i
→ SP : u
i
randomly chooses D
′
⊂ D , whereas u
i
∈ D
′
, and sends ENC(D
′
) to SP.
2. SP → u
i
: Choose random r ∈
R
{0,1}
k
. Parse ENC(D
′
), generate and send hC
1
= E
PK
u
1
(r,ω
1
),. . .,C
n
= E
PK
u
n
(r,ω
n
)i,
where ω
i
= f
R
(r,ID
u
i
).
3. u
i
↔ SC
u
i
: Send hhC
1
,. . .,C
n
i,hPK
u
1
,. . .PK
u
n
i,κi to SC
u
i
. SC
u
i
decrypts C
i
to obtain r
′
. For 1,. . .,κ it chooses
j ∈
R
{1,. .. ,i−1,i+1,.. . ,n} without duplicates and checks whetherC
j
= E
PK
u
j
(r
′
,ω
j
) holds, where ω
j
= f
R
(r
′
,ID
u
j
).
If this holds for all κ checks, it chooses ρ
1
,ρ
2
at random, computes c
1
= E
PK
TA
(r
′
||γ
u
i
,ρ
1
) and c
2
= E
PK
SP
(r
′
||c
1
,ρ
2
)
and returns c
2
to u
i
. Otherwise it returns ⊥.
4. u
i
→ SP : If c
2
6= ⊥ send c
2
to SP.
5. SP : Compute r
′
||c
1
= D
SK
SP
(c
2
) and check whether MSB
k
(r
′
||c
1
) = r. Store the tuple (r,c
1
, TIME).
a
a
MSB
i
(s) denotes the most significant i bits of the bitstring s and TIME represents a timestamp.
A detailed description of PROVE T is given in proto-
col 2. Note, that user u
i
does not authenticate against
the entire directory D , but a subset D
′
of appropriate
size, such that the protocol can be used efficiently but
provides enough anonymity, e.g. |D
′
| = 100. Fur-
thermore we assume that ENC provides a compact
encoding of the indices of all ID
u
i
in D . For sim-
plicity, we assume in protocol 2, that D
′
is of cardi-
nality n and the authenticating user u
i
holds position
i in D . Furthermore, for simplicity we assume that
there is a single traceability authority (TA). The idea
behind PROVE T is, that protocol 1 is extended by
means of a tamper resistant smart card, which per-
forms all cryptographic operations on behalf of the
user in a way such that the user is not able to manipu-
late the escrowed identity information. Therefore, the
decrypted challenge r
′
must not be visible to the user
in plain at any time. Clearly, if the smart card would
provide (r
′
,c
1
) to the user, the user may easily substi-
tute c
1
with any bit string, without the SP being able
to detect it. Hence, in case of misuse or fraud the TA
would not be able to recover the identity of the user.
Therefore the smart card additionally encrypts (r
′
,c
1
)
for the SP and provides c
2
to the user.
Protocol 3. IDENTIFY TRA
1. SP → TA : Send (r,c
1
, TIME) to TA.
2. TA → SP : Compute r
′
||γ
u
i
= D
SK
TA
(c
1
) and ver-
ify whether MSB
k
(r
′
||γ
u
i
) = r. If this holds find
ID
u
i
corresponding to γ
u
i
and send ID
u
i
to SP.
Since we require the public key encryption scheme
for the latter operation to provide NM-CPA security
and the escrow identities γ for all other users are not
known to the user and furthermore are chosen at ran-
dom, the user will not be able to misattribute the pro-
tocol to another user. The same holds for the SP,
which is also not in possession of the escrow iden-
tities γ of all users.
In the IDENTIFY TRA protocol (see protocol3) the
SP, who wants to identify a user who conducted an
anonymous identification at time TIME for some rea-
son, provides the stored tuple (r, c
1
, TIME) to the TA,
which decrypts c
1
by means of its secret decryption
key SK
TA
and verifies whether the provided and the
encrypted challenge matches. If this holds it looks
up the identity ID
u
i
corresponding to γ
u
i
and sends
ID
u
i
to SP. The SP may subsequently remove the en-
try (ID
u
i
,PK
u
i
) from D such that user u
i
will not be
able to anonymously identify himself to SP in the fu-
ture anymore.
4.3 Separability & IBE Setting
As we have mentioned earlier, one efficient realiza-
tion of (traceable) ring authentication can be achieved
by means of RSA-OAEP. However, we are not limited
to a specific public key encryption scheme. Moreover,
users may register to a service provider using public
keys of different schemes. But it should be noted, that
firstly the pseudorandom function f
R
needs to be cho-
sen according to the respective scheme and secondly
the user’s smart card must be capable of computing
all cryptographic operations for these schemes. Alter-
natively, an elegant way of realizing (traceable) ring
authentication is the use of identity-based encryp-
tion (IBE) schemes, e.g. the FULLIDENT scheme of
(Boneh and Franklin, 2001). In contrast to traditional
public key cryptography, in IBE the public key of a
user can be computed by means of an identity string.
Obviously, this reduces the size of entries in D . Tra-
ditional public keys integrated in X.509 certificates
consume about 1 KByte of storage space and conse-
quently transmission bandwidth, whereas the repre-
sentation of the public key of a user is reduced to a
few bytes, e.g. an email address, in case of IBE.
4.4 Efficiency Considerations
The proposed protocol for TRA is very efficient in
terms of round complexity and in particular solely
needs one round of communication. However, a large
number of authorized users (D ) may represent a bot-
PRACTICAL TRACEABLE ANONYMOUS IDENTIFICATION
229
tleneck for the efficiency of the scheme. As already
implicitly applied in protocol 2, one, however, may
choose a subset D
′
⊂ D of cardinality n of all au-
thorized users for a traceable ring authentication. For
instance, the choice of |D
′
| = 100 would require the
user’s smart card to perform 99 public key opera-
tions and a single private key operation considering
the challenge vector. This can be realized at the addi-
tional cost of one message (send D
′
to SP), i.e. three
messages overall.
As already noted in section 4.1, the user may only
perform κ < n public key operation which results in
probabilisticanonymity,i.e. SP may cheat without the
user being able to detect it. Clearly, SP may encrypt
distinct challenges r
1
,... , r
n
in order to uniquely iden-
tify the authenticating user. But this will only work if
the user chooses κ = 0. Instead, SP may only encrypt
some distinct r in order to reduce the anonymity of
users. However, if the user chooses κ appropriately,
i.e. n− 1 ≫ κ ≥ 10, the probability that a cheating SP
succeeds will be 2
−κ
. Hence, the chances to cheat un-
noticeable decrease exponentially in κ as κ increases.
Thus, the choice of κ mentioned before seems reason-
able for practical purposes. Consequently, the number
of public key operations which need to be performed
can be reduced to a small value of κ.
It must be noted, that in our scheme SP solely re-
quires to manipulate D to add new or remove users.
Hence, users need to update their local copy of D
from time to time in order to use the actual set of au-
thorized users. Nevertheless, sate of the art security
tokens provide enough storage to manage D . More-
over, users may only update and maintain ID’s of
authorized users and load corresponding public keys
from time to time.
In order to obtain an understanding of the perfor-
mance of the proposed protocol, we will provide an
estimation of the user’s computation cost based on
state of the art cryptographichardware for security to-
kens (see table 2) subsequently. Due to the fact, that
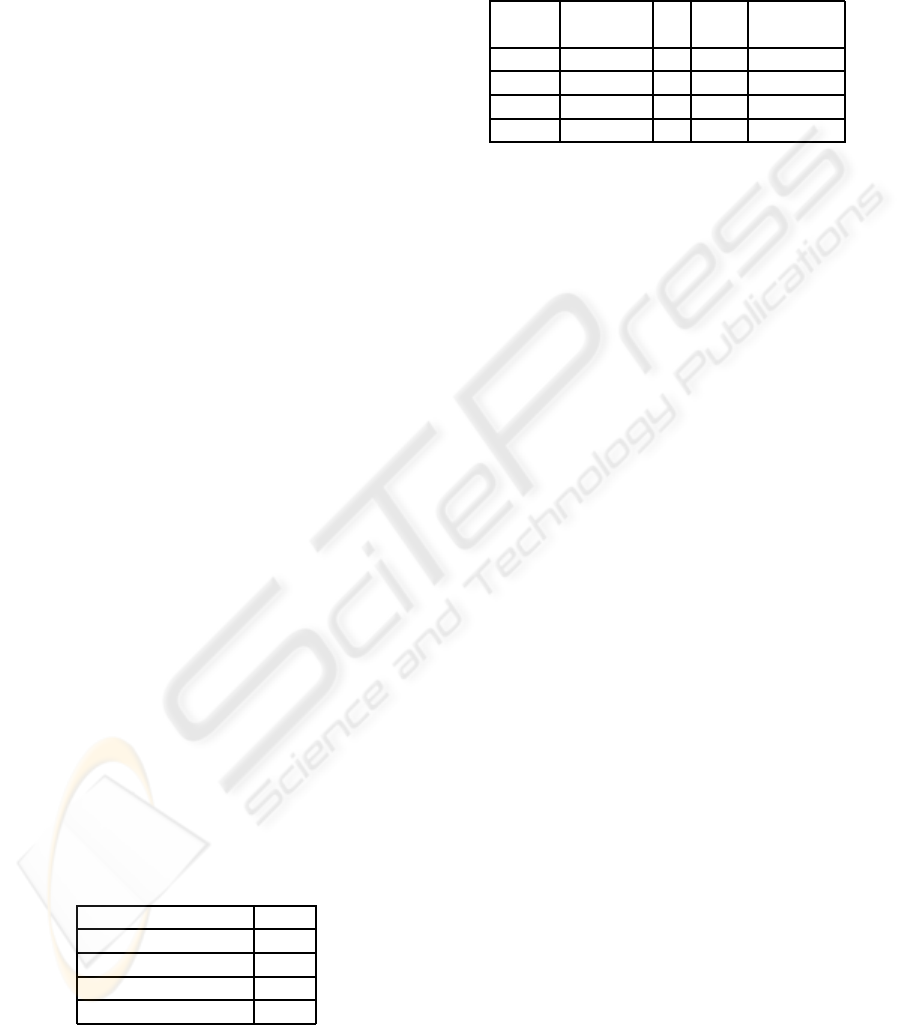
Table 1: Cryptographic performance of a state of the
art cryptographic controller for security tokens (SLE
88CFX4002P from Infineon) for private key (SK) and pub-
lic key (PK) operations.
Scheme [ms]
RSA 1024 bit (PK) 0.5
RSA 1024 bit (SK) 4
RSA 2048 bit (PK) 35
RSA 2048 bit (SK) 11
RSA is actually the most common public key cryp-
tosystem used for encryption in context of security
tokens we will base our analysis on the RSA scheme.
More precisely, we will use RSA-OAEP with a mod-
Table 2: Performance evaluation for |D
′
| = 100 and κ = 10
and modul size of m
1
= 1024 and m
2
= 2048. The table pro-
vides computation cost for the user (C-U), estimated dura-
tion of the computation for the user (T-U), computation cost
for the service provider (C-SP) and communication costs
(Comm).
C-U T-U C-SP Comm
[ms] [bit]
RA
1024
10PK + SK 9 100PK 100m
1
+ k
TRA
1024
12PK + SK 11 101PK100m
1
+ m
2
RA
2048
10PK + SK 361 100PK 100m
2
+ k
TRA
2048
12PK + SK 466 101PK 101m
2
ulus size of m
1
= 1024 and m
2
= 2048 bit for en-
cryption keys of users respectively. The security of
1024 and 2048 bit RSA is assumed to be sufficient till
2010 and 2030 respectively, assuming that there will
be no breakthrough in quantum computation. Further-
more, it must be mentioned that values encrypted un-
der user’s public keys only have a very short life time.
More care should be taken with the choice of the es-
crow key of the TA. For the time being, however, we
assume that 2048 bit will be sufficient. In our perfor-
mance estimation hash function evaluations and other
operations will be neglected, and we will only con-
sider public and private key operations as well as the
protocol versions providing probabilistic anonymity.
5 SECURITY ANALYSIS
5.1 Some Aspects
One problem that is inherent to the anonymity of the
two protocols is the following: If a user chooses a
strict subset D
′
of users in D for efficiency purposes,
say of cardinality 100, the SP may have inserted fake
identities and fake certified public keys into the di-
rectory D . Assume, that a user u
i
, who conducts
an anonymous identification using some D
′
of cardi-
nality 100, may unluckily chose 50 fake certificates.
Consequently, the anonymity will be reduced to 1/50,
since SP is able to sort out the faked certificates. How-
ever, it must be mentioned that if public keys are cer-
tified by some commonly trusted certification author-
ity, which also checks the identity of the respective
user before issuing certificates, this threat does no
longer exist. It is desirable that the communication
channel between the user and the SP provides con-
fidentiality and integrity. Clearly, all message from
the user to SP can be encrypted by means of the pub-
lic encryption key PK
SP
of SP. However, securing the
communication from SP to the user cannot be real-
ized by means of public keys since this would con-
tradict the anonymity. However, a user can randomly
SECRYPT 2009 - International Conference on Security and Cryptography
230

choose a secret key of a block cipher, e.g. AES, for
every anonymous identification and send this key en-
crypted under SP’s public key to SP. The communi-
cation from the SP to the user can consequently be
encrypted using a mode of operation that provides au-
thenticated encryption, e.g. the Galois/Counter Mode
(GCM) (Dworkin, 2007) using this single secret key.
5.2 Traceable Ring Authentication
Theorem 1. The traceable ring authentication pre-
sented in section 4.2 is secure with respect to defini-
tion 1.
Subsequently, we sketch the proof of theorem 1 by
inspecting all properties.
Anonymity. Firstly, we will look at a honest but cu-
rious service provider, represented as adversary A .
Let c
1
,... , c
n
be the challenge vector which is sent
by A to some user. Hence it must hold that there ex-
ist ω
i
,... , ω
n
such that c
i
= E
PK
u
i
(r,ω
i
) holds for all
i. By correctness of the used encryption scheme this
implies that r = D
SK
u
i
(c
i
) for all i. Consequently, A s
view of this attack is identical to the view for any j
chosen in experiment Expt
anon
TRA,A
SP
,n
(k) and the prob-
ability of j = i is at most 1/n.Secondly, we need to
investigate the aspect of pseudorandomly chosen ran-
domizers. Since the pseudorandom function f
R
is
treated as a random oracle, i.e. the cryptographic hash
function H, and furthermore the random challenge r is
of appropriate size and fully unknown to to any party
except the service provider, the semantic security of
the encryption scheme holds.
Correctness. The correctness of the TRA protocol
holds by construction.
Unforgeability. If we assume there exists an
adversary A which is able to win the unforgeability
experiment Expt
unf
TRA,A
NA
,n(k)
with non-negligible
probability, then adversary A could be used by
an adversary A
E
that attacks the used encryption
scheme, i.e. the IND-CPA security. Therefore A
E
is given public keys PK
1
,... , PK
n
and chooses two
messages m
0
and m
1
. A bit b is chosen at random
(unknown to A
E
) and c
1
,... , c
n
is given to A
E
, where
the c
i
’s encrypt m
b
. A
E
gives c
1
,... , c
n
as challenge
vector to A . Consequently A
E
receives back m from
the user part of A . A
E
checks whether m = m
0
or
m = m
1
holds and outputs b
′
. Thus, A
E
is able to
win the IND-CPA experiment with non-negligible
probability and this contradicts the assumption that
the encryption scheme provides IND-CPA security.
Unlinkability. The unlinkability property of the
TRA follows from the anonymity property. What we
need to look at is the identity escrow information c
1
of every TRA protocol. Since the used encryption
scheme is NM-CPA secure, all possible plaintext are
equally probable to result in the escrowed identity in-
formation c
1
. Since SP will not have access to a de-
cryption oracle (TA solely provides a result for valid
escrowed identities and otherwise will accuse SP to
be dishonest) he will not be able to link transcripts
of the TRA protocol by means of escrowed identity
information.
Traceability. Since the smart card is tamper resis-
tant and trusted, we can be sure that γ
u
i
is escrowed
if SC
u
i
runs a TRA protocol with user u
i
. Conse-
quently, TA will be able to extract γ
u
i
from any tuple
(r,c1,TIME) and will be able to provide ID
u
i
to SP.
No-missatribution. By construction of the TRA
protocol, user u
i
registers a pseudonym γ
u
i
with the
traceability authority (TA). Hence, γ
u
i
is not known
to the service provider (SP) for all users 1 ≤ i ≤
n. Recall, SP stores the tuple (r,c1,TIME) for ev-
ery instance of the TRA protocol, whereas c
1
=
E
PK
TA
(r
′
||γ
u
i
,ρ
1
). The tuple is sent to TA in case of
anonymity revocation. Hence, in order to miss at-
tribute an instance of the TRA to some user, SP would
need to construct c
′
1
which decrypts to r
′
and some
valid γ
u
j
for some user 1 ≤ j ≤ n, j 6= i. Clearly,
SP knows r
′
, but none of the pseudonyms γ
u
i
. Since
we require the public key encryption scheme to pro-
vide NM-CPA security, which implies IND-CPA se-
curity and SP has no access to a decryption oracle,
SP can only guess γ
u
j
. Since we assume that the bit
length of γ is chosen appropriately, the success prob-
ability of SP is negligible.
6 CONCLUSIONS
In this paper we haveproposed a practical protocol for
traceable anonymous identification which can easily
deployed using state of the art smart cards. More-
over, the protocol is highly efficient since it has opti-
mal round complexity and furthermore it is fully com-
patible with real world scenarios, i.e. public key in-
frastructures based on X.509 certificates.
REFERENCES
Ateniese, G., Camenisch, J., Joye, M., and Tsudik, G.
(2000). A Practical and Provably Secure Coalition-
PRACTICAL TRACEABLE ANONYMOUS IDENTIFICATION
231

Resistant Group Signature Scheme. In CRYPTO ’00,
volume 1880 of LNCS, pages 255–270. Springer.
Bellare, M. and Rogaway, P. (1993). Random Oracles are
Practical: A Paradigm for Designing Efficient Proto-
cols. In CCS ’93, pages 62–73, New York, NY, USA.
ACM.
Boneh, D. and Franklin, M. K. (2001). Identity-Based En-
cryption from the Weil Pairing. In CRYPTO ’01, vol-
ume 2139 of LNCS, pages 213–229, London, UK.
Springer.
Brands, S., Demuynck, L., and Decker, B. D. (2007). A
Practical System for Globally Revoking the Unlink-
able Pseudonyms of Unknown Users. In ACISP 2007,
volume 4586 of LNCS, pages 400–415. Springer.
Camenisch, J. and Lysyanskaya, A. (2001). An Efficient
System for Non-transferable Anonymous Credentials
with Optional Anonymity Revocation. In EURO-
CRYPT ’01, volume 2045 of LNCS, pages 93–118,
London, UK. Springer.
Canard, S. and Girault, M. (2002). Implementing Group
Signature Schemes with Smart Cards. In CARDIS ’02,
pages 1–10. USENIX.
Chaum, D. and van Heyst, E. (1991). Group Signatures. In
EUROCRYPT ’91, volume 547 of LNCS, pages 257–
265. Springer.
Chor, B., Goldreich, O., Kushilevitz, E., and Sudan, M.
(1995). Private Information Retrieval. In FOCS ’95,
pages 41–50. IEEE Computer Society.
Danezis, G. and Diaz, C. (2008). A Survey of Anonymous
Communication Channels. Technical Report MSR-
TR-2008-35, Microsoft Research.
Dworkin, M. (2007). Recommendation for Block Cipher
Modes of Operation: Galois/Counter Mode (GCM)
and GMAC. In National Institute of Standards and
Technology SP 800-38D.
Froomkin, M. (2000). The Death of Privacy? Stanford Law
Review, 52(5):1461–1543.
Lindell, Y. (2007). Anonymous Authentication - Preserving
Your Privacy Online. Black Hat 2007.
Naor, M. (2002). Deniable Ring Authentication. In
CRYPTO ’02, volume 2442 of LNCS, pages 481–498.
Springer.
Persiano, P. and Visconti, I. (2003). A Secure and Pri-
vate System for Subscription-Based Remote Services.
ACM Trans. Inf. Syst. Secur., 6(4):472–500.
Rivest, R. L., Shamir, A., and Tauman, Y. (2001). How to
Leak a Secret. In ASIACRYPT ’01, volume 2248 of
LNCS, pages 552–565. Springer.
Schechter, S., Parnell, T., and Hartemink, A. (1999).
Anonymous Authentication of Membership in Dy-
namic Groups. In Proc. International Conference on
Financial Cryptography 1999, volume 1648 of LNCS,
pages 184–195. Springer.
Xu, S. and Yung, M. (2004). Accountable Ring Signatures:
A Smart Card Approach. In CARDIS’04, pages 271–
286. Kluwer.
APPENDIX
Below we define two experiments for the anonymity
and unforgeability property respectively where n rep-
resents the number of authorized users and k is a se-
curity parameter for the key generation algorithm G.
The Anonymity Experiment Expt
anon
TRA,A
SP
,n
(k) :
1: G generates PK
1
,... , PK
n
.
2: Index i is secretly chosen uniformly at random
from 1,. . . ,n.
3: The malicious SP A
SP
is given all public keys
PK
1
,... , PK
n
and user u
i
is given SK
i
.
4: The TRA protocol is executed between A
SP
and
u
i
, whereas A
SP
has access to an encryption oracle
O
E
(m, j), which encrypts a message m with the
public key PK
j
, 1 ≤ j ≤ n.
5: At the end of the experiment, A
SP
outputs an in-
dex i
′
, 1 ≤ i
′
≤ n. A
SP
has succeeded in the ex-
periment, if and only if i
′
= i, which is denoted as
Expt
anon
TRA,A
SP
,n
(k) = 1.
The Unforgeability Experiment Expt
unf
TRA,A
NA
,n
(k) :
1: G generates PK
1
,... , PK
n
.
2: The SP and the malicious non authorized user A
NA
are both given all public keys PK
1
,... , PK
n
.
3: The TRA protocol is executed between SP and
A
NA
, whereas A
NA
has access to an encryption or-
acle O
E
(m, j), which encrypts a message m with
the public key PK
j
, 1 ≤ j ≤ n.
4: At the end of the experiment, A
NA
has suc-
ceeded in the experiment, if and only if SP ac-
cepts the TRA protocol, which is denoted as
Expt
unf
TRA,A
NA
,n
(k) = 1.
SECRYPT 2009 - International Conference on Security and Cryptography
232
