
RESISTING IMPERSONATION ATTACKS IN CHAINING-BASED
PUBLIC-KEY MANAGEMENT ON MANETS
The Virtual Public-key Management
Renan Fischer e Silva, Eduardo da Silva and Luiz Carlos Pessoa Albini
NR2/LARSIS − Department of Informatics, Federal University of Paran´a, Curitiba, Brazil
Keywords:
MANET, Public-key management, Virtualization, Virtual structure.
Abstract:
Chaining-based key management schemes seem to be the ones that best fit MANETs. The main chaining-based
scheme is the Self-Organized Public Key Management System (PGP-Like). However, it is fully vulnerable
to impersonation attacks. In order to reduce such vulnerability, this article introduces a new public-key man-
agement system for MANETs, the Virtual Key Management System (VKM). VKM uses a virtual structure
to indicate the trust between nodes and the certificate chains formation. VKM can behave in a restrict way,
being able to tolerate impersonation attacks to a certain level, or it can behave similarly to the PGP-Like, just
by changing a simple parameter. Thus, VKM can suit any user needs switching between these two models
dynamically, without any network reinitialization or reconfiguration.
1 INTRODUCTION
It is possible to classify the key management schemes
for MANETs in (Djenouri et al., 2005): identity-
based, chaining-based, cluster-based, predeployment-
based and mobility-based. Among them, the
chaining-based schemes appears to be the most suit-
able scheme to the MANETs environment. The
main chaining-based key management scheme for
MANETs is the Self-Organized Public Key Manage-
ment System (Hubaux et al., 2001;
ˇ
Capkun et al.,
2003), called PGP-Like from now on.
PGP-Like is a self-organized public-key manage-
ment scheme based on the PGP concepts, in which
all pair-wised keys are created by the nodes them-
selves. Nodes also issue certificates to the other ones
in which they trust. Each node has a local certifi-
cate repository that is periodically exchanged with its
neighbors. Keys are authenticated through certificate
chains which are built using the local certificate repos-
itories.
As presented in (Silva et al., 2008), PGP-Like is
highly vulnerable to the impersonation attack. Im-
personation attacks consist on an attacker using false
identities to deceive network protocols. The func-
tionality of PGP-Like is compromised even with only
5% of Misbehaviour nodes in the network. In order
to reduce such vulnerability, this article introduces a
new chaining-based public-key management system
for MANETs, the Virtual Key Management System
(VKM). VKM uses a virtual structure to indicate the
trust between nodes and the certificate chains forma-
tion. Virtual structures have already been used in rout-
ing protocols such as VRP (Albini et al., 2006) and
VDV (Robba and Maestrini, 2007).
VKM is a flexible key management scheme. It
can behave in a very restrict way, being able to toler-
ate impersonation attacks to a certain level, or it can
behave similarly to the PGP-Like, just by changing
a simple parameter. When VKM is set to a restric-
tive behavior, it is still able to correctly complete al-
most 80% of all key authentication requests with 5%
of compromised nodes. Thus, VKM can suit any user
needs with its ability to switch between the two mod-
els dynamically, without any network reinitialization
or reconfiguration.
The rest of this paper is organized as follows:
section 2 briefly describes the PGP-Like characteris-
tics; section 3 details the Virtual Key Management
Scheme; section 4 presents the Evaluation of the
VKM, and a comparison with the PGP-Like; finally,
section 5 draws the conclusions and future work.
155
Fischer e Silva R., da Silva E. and Carlos Pessoa Albini L. (2009).
RESISTING IMPERSONATION ATTACKS IN CHAINING-BASED PUBLIC-KEY MANAGEMENT ON MANETS - The Virtual Public-Key Management.
In Proceedings of the International Conference on Security and Cryptography, pages 155-158
DOI: 10.5220/0002236501550158
Copyright
c
SciTePress
2 SELF-ORGANIZED PUBLIC
KEY MANAGEMENT SYSTEM
The Self-OrganizedPublic Key Management System,
called PGP-Like, is a public key management scheme
which uses certificate chains (
ˇ
Capkun et al., 2003;
Hubaux et al., 2001). Private and public keys of
nodes are created by the nodes themselves following
the PGP concepts (Zimmermann, 1995). In addition,
each node issues public key certificates to other nodes
in which it trusts. In PGP-Like, if a node u believes
that a public key K
v
belongs to node v, it issues a cer-
tificate binding K
v
to the node v, (v, K
v
)
prK
u
, in which
prK
u
is the private key of node u. This certificate is
stored in both nodes local certificate repositories. Fur-
thermore, each node periodically exchanges its own
repository with its neighbors.
Public keys and certificates are represented by a
directed graph G(V, A), in which V represents the
public keys and A represents the certificates. A di-
rected edge between two vertexes K
u
and K
v
, (K
u
→
K
v
), denotes a certificate, signed by node u, binding
K
v
to node v. Each node u maintains an updated local
certificate repository,G
u
, and a non-updated local cer-
tificate repository, G
N
u
, which contains the certificates
that have expired.
When node u wants to authenticate the public key
K
v
of node v, it must find a path connecting K
u
and K
v
,
represented by (K
u
K
v
). It firstly tries to find (K
u
K
v
) ∈ G
u
. If ¬∃(K
u
K
v
) ∈ G
u
, node u merges G
u
with G
v
, G
′
= G
u
∪G
v
, and it tries to find (K
u
K
v
) ∈
G
′
. If a path exists, the authentication succeeds.
The use of certificate chains makes PGP-Like
highly vulnerable to impersonation attacks, as shown
in (Silva et al., 2008). An attacker, node x, can create
a false identity m and issues a certificate binding k
m
to
m. Thus, if node x maintains a correct behavior dur-
ing a considerable time, several units will, probably,
trust it and the false identity will be spread over the
network due to the certificate exchange mechanism.
3 VIRTUAL KEY MANAGEMENT
SYSTEM
The Virtual Key Management System (VKM) uses a
virtual structure to indicate the trust between nodes
and the certificate chains formation. The virtual struc-
ture is represented by a directed graph L(N, E), which
is unrelated to the actual network topology. Set N
represents the nodes and set E represents the virtual
links. A virtual link (i, j) ∈ E indicates that node i is-
sues a certificate binding K
j
to node j. Note that node
i must do this for each node to which it has a direct
connection in the virtual structure. For example, the
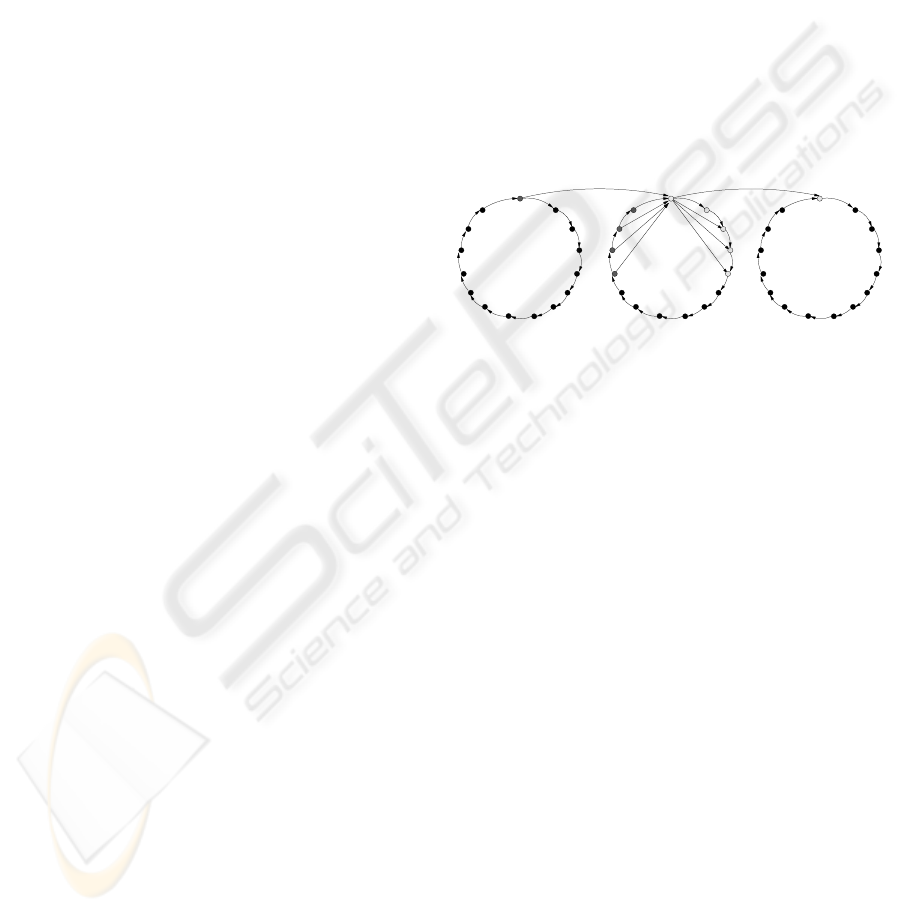
virtual structure can be a RoR, a hypercube, a CCC
or a torus, though results reported in this paper were
obtained using the Rings of Rings (RoR) structure.
The Rings of Rings (RoR) structure is based on the
following: assume that there are two integers, x and
y, such that, x ∗ y = n, and let s be an integer such
that 1 < s ≤ y. Set N is partitioned into x rings, called
N
0
, N
1
, ..., N
x−1
, in which, for each a ∈ [0, x), N
a
=
{i : a∗y ≤ i < (a+ 1)∗y}. Link (i, j) belongs to E iff
either j mod y = (i+ d) mod y for some 1 ≤ d < s or
j = (i+ y) mod n. A notable feature of RoR structure
is the redundancy of virtual paths, whose degree is
determined by parameters x, y, and s. In VKM s is
the number of certificates that a node issues. Figure 1
exemplifies the Ring of Rings (RoR) structure.
5
a
V
a+1
V
a−1
1
2
3
4
5
w’
w’
w’
w’
1
2
3
4
V
s−1 s−1
w
w
w
w
w’
w
w
Figure 1: RoR Virtual Structure.
In VKM each node i creates its own pair of public
and private keys, K
i
and prK
i
. Afterwards, it must
issue certificates following the virtual structure. A
pair of nodes in the virtual structure must exchange
its keys through a secure channel. When a certificate
is issued, its issuer stores it in a local repository and
sends it to the correspondent node. All certificates are
issued with a limited lifetime T
v
.
VKM can behave in a restrict way, being able to
tolerate impersonation attacks to a certain level, or it
can behave similarly to the PGP-Like, just by chang-
ing a simple parameter. The main difference between
these behaviors is the way nodes authenticate public-
keys. Both forms will be presented next.
In VKM with reactive authentication (VKM-RA),
each node maintains only its initial certificates, the
certificates issued by it and the ones issued to it, thus
reducing the memory needed by the local certificate
repositories. When node i wants to authenticate the
public-key of node j, it must find a virtual path from i
to j, a certificate chain, in the virtual structure. After
choosing a virtual path, thesource must gather all cer-
tificates to validate the entire virtual path as follows:
(i) the first certificate is directly verified by node i us-
ing its own public key, as it is the issuer; (ii) each
remaining certificate can be verified using the public
key contained in the previous certificate; (iii) the last
certificate contains the public key of node j.
SECRYPT 2009 - International Conference on Security and Cryptography
156
VKM with proactive authentication (VKM-PA)
behaves similarly to PGP-Like. Though certificates
are issued following the virtual structure, nodes peri-
odically exchanges their certificate repositories with
their physical neighbors. . When a node i wants to
authenticate the public key K
j
of node j, it tries to
find a certificate chain in its local repository, (K
i
K
j
) ∈ G
i
. If ∃(K
i
K
j
) ∈ G
i
, it performs the authen-
tication using VKM-PA. If ¬∃(K
i
K
j
) ∈ G
i
, node
i, node i invokes VKM-RA. This characteristic makes
the authentication more effective than PGP-Like, as it
is possible to reach all nodes using the VKM-RA.
4 EVALUATION
The Network Simulator 2 (NS-2) (NS-2, 2007), ver-
sion 30, was used to evaluate VKM. The parame-
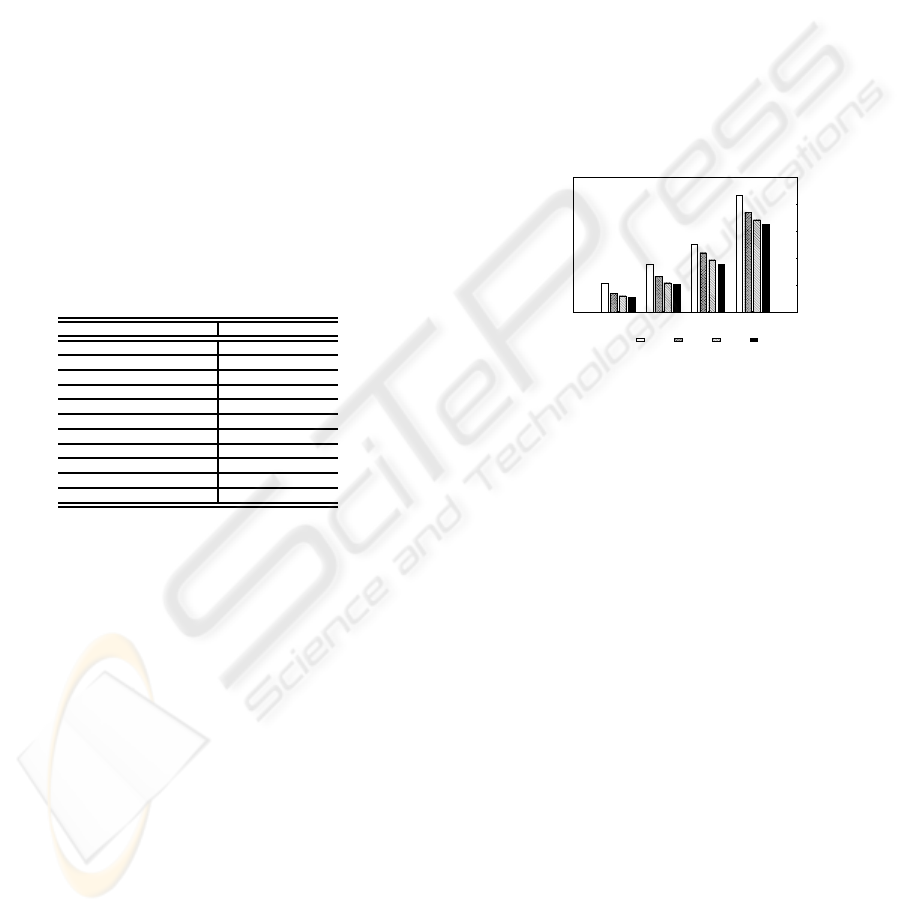
ters used in the simulations are presented in table 1.
All simulations results are averages of 35 simulations
with 95% of confidence interval.
Table 1: Simulation scenarios.
Parameter Value
Network dimension 1000 x 1000 meters
Transmission range 120 meters
Nodes 100
Mobility model random waypoint
Max. speed 20 m/s
Max. pause time 20 seconds
Exchange certificate interval 60 seconds
Simulation time 1500 seconds
Propagation Model two-ray ground
MAC 802.11
RoR x=4, y=25, s=5
VKM was evaluated under two different network
behaviors: (i) under the impersonation attack and (ii)
under the lack of cooperation attack. The evalua-
tion under the impersonation attack demonstrates that
VKM-RA can tolerate several misbehavior nodes in
the network, while PGP-Like is completely vulnera-
ble even with only 5% of misbehavior nodes (Silva
et al., 2008). The evaluation under the lack of cooper-
ation attack was made to demonstrate that the behav-
ior of VKM-PA is similar to PGP-Like. The results
shown here for PGP-Like are from (Silva et al., 2008).
4.1 Impersonation Attack
As VKM-RA must use the virtual structure in all au-
thentications, a valid impersonation attack must be an
impersonation of a node within the virtual structure.
Otherwise, the attack is useless, as no authentication
would use such a node.
Simulations scenarios consider 5%, 10%, 20%
and 40% of misbehaviour nodes. They also consider
s = 5, s = 10, s = 15 and s = 20 certificates issued
to and by each node. As shown in figure 2, even with
20% of misbehaviournodes in the network, VKM-RA
is still able to authenticate several certificate chains.
In the presence of 5% of misbehaviour nodes, VKM-
RA is able to correctly authenticate almost 80% of the
certificate chains, while PGP-Like is completely com-
promised even with only 5% of attackers (Silva et al.,
2008).
VKM-RA can tolerate impersonation attacks bet-
ter than PGP-Like due to the virtual structure, as the
virtual structure is highly redundant and it establishes
several “fixed” chains for authentication. If the num-
ber of compromised nodes is small, it is possible to
avoid compromisednodes simply by randomly choos-
ing the certificate chain. It is also possible to imple-
ment a misbehavior detection mechanism, thus nodes
might explicitly avoid compromised nodes.
0
20
40
60
80
100
0 5 10 20 40
Authentications Through Compromised Units (%)
Sybil Nodes (%)
S = 5 S = 10 S = 15 S = 20
Figure 2: Authentications Through Compromised Nodes.
Figure 2 also shows that with 40% of misbe-
haviour nodes and 5 issued certificates, the possibil-
ity of choosing a compromised chain reaches more
than 80%. However, this percentage is reduced to al-
most 60% if the number of issued certificates is in-
creased to 20, thus demonstrating that increasing the
node connectivity in the virtual structure, it is possi-
ble to reduce the effects of the impersonation attack.
However, it is still possible to have efficient attacks
on VKM-RA: attackers could organize a cooperative
attack to a node of the virtual structure and separate it
from the rest of the network.
4.2 Lack of Cooperation Attacks
To demonstrate that VKM-PA behaves similarly to
PGP-Like, VKM-PA was evaluated under the Lack
of Cooperation Attack and its results are compared
with the ones provided by (Silva et al., 2008). These
simulations consider 5%, 20%, 40% and 60% of self-
ish nodes. Following the results presented in (
ˇ
Capkun
et al., 2003) and (Silva et al., 2008) to evaluate the
PGP-Like, two metrics are used in this evaluation: CE
(Certificate Exchange Convergence) and UR (User
Reachability).
Figures 3 and 4 illustrate the VKM-PA behavior
under lack of cooperation attacks. In both, VKM-
RESISTING IMPERSONATION ATTACKS IN CHAINING-BASED PUBLIC-KEY MANAGEMENT ON MANETS -
The Virtual Public-Key Management
157
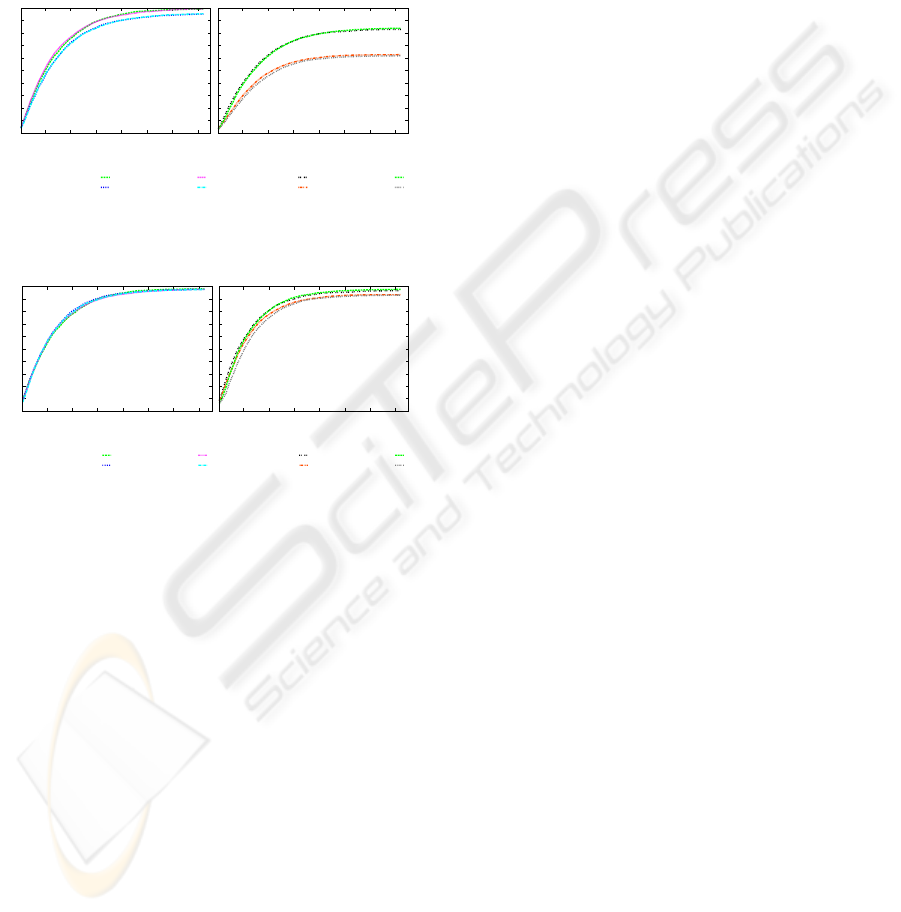
PA results are compared with PGP-Like ones. As ex-
pected, increasing the number of attackers, CE value
decreases (Figure 3). In scenarios without attackers
or with 5% up to 60% of attackers, VKM-PA presents
the same behavior of PGP-Like. UR results for VKM-
PA with up to 60% of selfish nodes are also similar
to those of PGP-Like (Figure 4). UR is almost 100%
even in the presence of 60% of selfish nodes, the same
behavior found on PGP-Like.
0
0.1
0.2
0.3
0.4
0.5
0.6
0.7
0.8
0.9
1
200 400 600 800 1000 1200 1400
CE(t)
Time (s)
(A)
PGP-Like 5%
PGP-Like 20%
VKM-PA 5%
VKM-PA 20%
200 400 600 800 1000 1200 1400
Time (s)
(B)
PGP-Like 40%
PGP-Like 60%
VKM-PA 40%
VKM-PA 60%
Figure 3: Convergence of Certificate Exchanges.
0
0.1
0.2
0.3
0.4
0.5
0.6
0.7
0.8
0.9
1
200 400 600 800 1000 1200 1400
UR(t)
Time (s)
(A)
PGP-Like 5%
PGP-Like 20%
VKM-PA 5%
VKM-PA 20%
200 400 600 800 1000 1200 1400
Time (s)
(B)
PGP-Like 40%
PGP-Like 60%
VKM-PA 40%
VKM-PA 60%
Figure 4: User Reachability.
5 CONCLUSIONS AND FUTURE
WORK
Chaining-based key management schemes seem to be
the ones that best fit the MANET paradigms. The
main chaining-based scheme is the Self-Organized
Public Key Management System (PGP-Like). How-
ever, as presented in (Silva et al., 2008), PGP-Like
is highly vulnerable to the impersonation attack. The
functionality of PGP-Like is compromised even with
only 5% of misbehaviour nodes in the network.
This article introduces a new chaining-based
public-key management system for MANETs, the
Virtual Key Management System (VKM). VKM is
a flexible key management scheme. It can be con-
figured to work in two different ways, VKM-RA and
VKM-PA. VKM-RA has a restrictive behavior. Using
VKM-RA, nodes follow the rules of the virtual struc-
ture to issue certificates and authenticate keys. As
showed in simulations, only few misbehaviour nodes
in a disorganized way cannot effectively compromise
the network behavior. VKM-RA is still able to cor-
rectly complete almost 80% of all key authentication
requests with 5% of compromised nodes. Further-
more, VKM can behave similarly to PGP-Like just
by changing a simple parameter, VKM-PA.
Future work includes the test of VKM under dif-
ferent kinds of attacks. It also includes the develop-
ment of a secure version of the VRP routing protocol
using VKM as the key management scheme.
REFERENCES
Albini, L., Caruso, A., Chessa, S., and Maestrini, P.
(2006). Reliable routing in wireless ad hoc net-
works: The virtual routing protocol. Journal of
Network and Systems Management, 14(3):335–
358.
ˇ
Capkun, S., Butty´an, L., and Hubaux, J.-P. (2003).
Self-organized public-key management for mo-
bile ad hoc networks. IEEE Transactions on Mo-
bile Computing, 2(1):52–64.
Djenouri, D., Khelladi, L., and Badache, N. (2005).
A survey of security issues in mobile ad hoc and
sensor networks. IEEE Surveys and Tutorials,
7(4):2–28.
Hubaux, J.-P., Butty´an, L., and
ˇ
Capkun, S. (2001).
The quest for security in mobile ad hoc net-
works. In Proceedings of the 2nd ACM Interna-
tional Symposium on Mobile Ad Hoc Networking
& computing (MobiHoc 2001), pages 146–155.
NS-2 (2007). The network simulator - ns-2.
Robba, A. and Maestrini, P. (2007). Routing in mo-
bile ad-hoc networks: The virtual distance vector
protocol. In Proceedings of the IEEE Interna-
tional Conference on Mobile Ad-hoc and Sensor
Systems (MASS 2007), pages 1–9.
Silva, E., dos Santos, A. L., Albini, L. C. P., and
Lima, M. N. (2008). Quantify misbehavior at-
tacks against the self-organized public key man-
agement on manets. In Proceedings of the Inter-
national Conference on Security and Cryptogra-
phy (SECRYPT 2008), pages 128–135.
Zimmermann, P. R. (1995). The official PGP user’s
guide. MIT Press, Cambridge, MA, USA.
SECRYPT 2009 - International Conference on Security and Cryptography
158
