
A FORMULA DRIVEN INCREMENTAL CONSTRUCTION OF WEB
SERVICE COMPOSITIONS
Antonella Santone
∗
, Gigliola Vaglini
+
and Maria Luisa Villani
∗
∗
Dipartimento di Ingegneria, University of Sannio, Benevento, Italy
+
Dipartimento di Ingegneria della Informazione, University of Pisa, Italy
Keywords:
Model checking, Temporal logic, Tableaux, Web services.
Abstract:
We present a modular approach to system specification to support the realization of web services. In particular,
we solve the following problem: given the formal specification of the (incomplete) system, say p, already built,
what is a characterization of the sub-systems that can collaborate with p, through a given communication
interface L , so that the complete system satisfies a given property ϕ? An automatic procedure is defined to
identify the formula ψ such that, for each process q satisfying ψ, the parallel composition of p and q through
L satisfies ϕ. For applicability of the method to web service compositions the formula ψ should specify, as
much as possible, only the communication actions that allow p to correctly fulfill ϕ.
1 INTRODUCTION
The Service Oriented Architecture (SOA) model has
led to rethinking the way software systems are de-
veloped: systems are conceived as collaborations of
simpler services, whose concrete realizations will be
selected or even discovered at run-time. Also, these
systems can reconfigure themselves to recover from
problems that may occur during execution. Thus,
proper mechanisms to specify the behaviors of the
required services are essential, to enable automatic
search and compatibility checks of the services that
can be bound to the composition. Most importantly,
validity of the composition with respect to global ob-
jectives must be ensured not only at design time, but
also at execution time, when a binding with some ser-
vice might be changed with another one.
We present a modular approach to system specifi-
cation to support the realization of such systems. In
particular we solve the following problem: given the
formal specification of the (incomplete) system, say
p, already built, what is a characterization of the sub-
systems that can collaborate with p, through the given
communication interface L , so that the complete sys-
tem satisfies the property ϕ?
In this paper, properties are described by tempo-
ral logic formulae expressed, for the purpose of sim-
plicity, through the Selective Hennessy-Milner logic
(Barbuti et al., 1999), and systems by CCS processes
(Milner, 1989). If ϕ is the formula to be satisfied by
the complete system, an automatic procedure is de-
fined to identify a formula ψ such that, for each pro-
cess q satisfying ψ, (p | q)\L satisfies ϕ. Moreover,
the description of the lacking component through a
logic formula guarantees correctness of the integra-
tion with p of any process that exhibits a behavior
compliant with the inferred formula. This behavior
consists in a skeleton of communications so that pro-
cesses having the same skeleton are all able to be suc-
cessfully integrated with p.
The synthesized formula could be generally ob-
tained with the partial model checking technique pre-
sented in (Andersen, 1995), aiming to reduce the
model checking problem of a complex process to that
of smaller size processes. Andersen’s method moves
the cause of the possible exponential complexity of
the model checking of the concurrent processes with
respect to ϕ from the number of states of the transi-
tion system of (p | x)\L to the number of operators of
a new formula ψ, which includes also the specifica-
tion of all possible behaviors of p. Thus, the resulting
formula does not highlight the missing behavior in p
with respect to ϕ, and the method does not scale when
evolving the system with new components.
Our aim is, even at the price of non-completeness
of the method, to define a formula for q, whose com-
13
Santone A., Luisa Villani M. and Vaglini G. (2009).
A FORMULA DRIVEN INCREMENTAL CONSTRUCTION OF WEB SERVICE COMPOSITIONS.
In Proceedings of the 4th International Conference on Software and Data Technologies, pages 13-22
DOI: 10.5220/0002246800130022
Copyright
c
SciTePress

plexity depends mainly on the complexity of the orig-
inal formula ϕ and of the chosen communication in-
terface; moreover, the result of the model checking of
p is taken into account so that ψ includes only the part
of ϕ that is not satisfied by p. Finally, the efficiency of
the method is tackled by exploiting the Selective mu-
calculus logic and the local model checking method-
ology; logic and methodology that allow us to con-
sider (and build) only the part of the transition system
of p needed for the verification.
In the following section, the basics of the specifi-
cation language we refer to are recalled, together with
the temporal logic through which the system proper-
ties are defined. Section 3 shows the core of the ap-
proach, while Section 4 presents an application of the
methodology through a known example in the field
of Web Services. Finally, considerations and compar-
isons with some related work are given in Section 5.
2 PRELIMINARIES
In a web service composition, the implementation de-
tails are hidden, as web services are black box compo-
nents running on the provider servers, but their inter-
face specifications, described by standard languages
like WSDL (W3C Working Group, 2007) and ”ab-
stract” WS-BPEL (Andrews et al., 2003), could be
public and they are automatically accessible. These
descriptions include the incoming/outcoming mes-
sages for each service operation and the interaction
protocol for their usage. This work considers a set
of WS-BPEL processes, which can be translated into
CCS processes, and a global formula to be satisfied
by the integrated system: the presented approach can
be used to deduce the behavioural specification of the
missing partner, i.e., a partner providing the opera-
tions required by the existing part of the system to cor-
rectly satisfy the global formula. Mappings of WS-
BPEL constructs to CCS are discussed in (Breugel
and Koshkina, 2006) and (Martinelli and Matteucci,
2007), while arguments sustaining CCS modelling of
web services compared to, for example, pi-calculus
are given in (Bao et al., 2006).
2.1 The Calculus of Communicating
Systems
The Calculus of Communicating Systems (CCS)
(Milner, 1989) is an algebra suitable for modelling
and analyzing processes. The syntax of processes is
the following:
p ::= nil | α.p | p + p | p|p | p\L | p[ f] | x
where α ranges over a finite set of visible actions
V = {a,a,b,b,...}. Input actions are labelled with
“non-barred” names, e.g. a, while output actions are
“barred”, e.g. a. The set L, in processes with the form
p\L ranges over sets of visible actions, f ranges over
functions from actions to actions, while x ranges over
a set of constant names: each constant x is defined by
a constant definition x
def
= p.
The operational semantics is given in Appendix.
In the following, given a process p, the sort of p is
the subset of V containing the actions that p can per-
form. The reader can refer to (Milner, 1989) for the
precise definition of the syntactically based version of
the sort of p.
Let δ ∈ A
∗
: if δ = α
1
.. . α
n
,n ≥ 1, p
δ
−→q means
p
α
1
−→·· ·
α
n
−→q; if δ = λ, where λ is the empty se-
quence, p
δ
−→q iff p = q. A process q such that there
is a computation p
δ
−→q is a δ-derivative of p with
−→ (or simply a derivative of p).
2.2 Model Checking and Selective
mu-calculus Logic
In the model checking framework (Clarke et al.,
2000), systems are modelled as automata (often called
transition systems) and requirements are expressed as
formulae of some temporal logic. The selective mu-
calculus is a branching temporal logic to express be-
havioral properties of systems (Barbuti et al., 1999).
It is equi-expressive to mu-calculus (Stirling, 1991),
but they differ in the definition of the modal opera-
tors. Given a set A of actions and a set Var of vari-
ables, selective mu-calculus formulae are defined as
follows:
ϕ ::= tt | ff | Z | ϕ ∨ ϕ | ϕ∧ ϕ | [K]
R
ϕ |
hKi
R
ϕ | νZ.ϕ | µZ.ϕ
where Z ∈ Var and K,R ⊆ A . The operators µZ.ϕ and
νZ.ϕ are fixed point operators: µZ.ϕ is the least fixed
point of the recursive equation Z = ϕ, while νZ.ϕ is
the greatest one. In the formula µZ.ϕ (νZ.ϕ) µZ (νZ)
binds the occurrences of Z in ϕ. A variable that is not
bounded by any fixed point operators is called free. A
formula without free variables is called closed. From
now on only closed formulae are considered. The pre-
cise definition of the satisfaction of the closed formula
ϕ by the process p is given in the Appendix.
An interesting property, which will be used in the
successive sections, is expressed by the formula be-
low, where S ⊆ A , γ = α
1
.. . α
n
and α
i
∈ A for all
1 ≤ i ≤ n:
ICSOFT 2009 - 4th International Conference on Software and Data Technologies
14

event seq(γ,S, ψ) = eventually(α
1
,S) ∧ [α
1
]
A
(eventually(α
2
,S) ∧ [α
2
]
A
(·· · ∧
[α
n−1
]
A
(eventually(α
n
,S)∧
[α
n
]
A
ψ)· · · ))
The property says: ”the actions of the sequence γ
eventually happen (each action is not interleaved with
actions in S) and then ψ holds”. The property uses the
formula eventually(α,S), i.e. ”α eventually happens,
not preceded by actions in S”, whose formal definition
is:
eventually(α,S) = µZ.h−i
S
tt∧
[S− {α}]
/
0
ff ∧ [−{{α} ∪ S}]
S
Z.
To the purpose of explaining the methodology with-
out too much technicality, system properties will be
defined through the Selective Hennessy-Milner Logic
(SHML) instead of the full selective mu-calculus
(Barbuti et al., 1999). SHML is more expressive than
the Hennessy-Milner logic (Stirling, 1991) because of
the intrinsic recursion of the selective operators. The
syntax of such logic is:
ϕ ::=
tt
|
ff
| ϕ ∧ ϕ | ϕ ∨ ϕ | [K]
R
ϕ | hKi
R
ϕ.
3 THE METHOD
Given a process p and a formula ϕ, a formula ψ is
looked for such that the parallel composition of p and
q satisfies ϕ, for each process q satisfying ψ. In fact,
the aim of the present work is the integration of the
functionality of an existing process p with new ones:
such integration has to maintain certain guarantees,
expressed by the formula ϕ, together with the require-
ments of the new functionalities. Thus, the logic for-
mula ψ supplies the formal specification of the pro-
cess q and it is thought to force q to support p to meet
ϕ; obviously, the behavior of p might be such that no
formula ψ can be deduced to guarantee a solution to
the satisfiability problem of ϕ . Such a case is detected
as unsuccessful by the tableau-based algorithm. In
particular, we consider a process p offering a commu-
nication interface to cooperate with another process q:
if such interface is not sufficient to guarantee, for the
part involving p, the satisfaction of the formula (i.e. a
required communication is not in the interface of p or
it exists, but is not correctly performed) then the algo-
rithm stops with failure. Thus the method hypotheses
can be recalled: given a CCS process p,
• all actions of p are either communication ac-
tions, τ
l
, performed inside p or visible actions
that are proposed for communicating with q; only
the communication actions with q, together with
the corresponding dual actions, constitute the set
L ⊆ sort(p);
• in the global formulae, only actions τ
α
will occur,
both performed inside p or between p and q.
We need also the definition of the following set con-
taining the corresponding actions through which a
communication occurs, beyond the internal commu-
nication actions performed by p.
Definition 3.1. Given the set of communication ac-
tions L and R ⊆ {τ
l
| τ
l
∈ A },
R
L
τ
= {l,l | (τ
l
∈ R)∧(l, l ∈ L )}∪{τ
l
| (τ
l
∈ R)∧(l, l 6∈ L )}.
When clear from the context we use R
τ
instead of R
L
τ
.
We propose a tableau-based method since such
method permits the exploration (and then requires the
construction) of only the part of the transition sys-
tem of the process involved in the verification of a
given formula. In our tableau two parts are distin-
guished: the goal and the environment. Intuitively, at
each intermediate stage while producing the solution,
the goal says what remains to be done and the envi-
ronment records the solution produced so far along a
branch of the tableau itself. The tableau works on se-
quents on which a set of rules can be applied; sequents
are defined as follows.
Definition 3.2. A sequent is an expression of the
form: hp, L ,x
ψ
,B i ⊢
E
ϕ, s.t.:
• ϕ is a SHML formula;
• p is a CCS process (the existing process or one of
its derivatives);
• L is the communication interface offered by p;
• E is the environment (i.e. a set of incomplete se-
lective mu-calculus formulae representing the un-
til now performed path on the tree);
• x
ψ
represents the unknown formula that will be
possibly built through the tableau branches as the
search will go onward;
• B is a boolean value yes or no: B is yes when
the last selective operator, being examined when
producing ψ, is a box operator; otherwise B is
no.
Each rule is of the form:
hp, L ,x
ψ
,B i ⊢
E
ϕ
hp
1
,L ,x
ψ
1
,B i ⊢
E
′
ϕ
1
·· · hp
n
,L ,x
ψ
n
,B i ⊢
E
′
ϕ
n
where n > 0 and side conditions may exist. The
premise sequent is the goal to be achieved, the conse-
quents are the sub-goals which are determined by the
structure of the formula and by the possible deriva-
tives of p.
A FORMULA DRIVEN INCREMENTAL CONSTRUCTION OF WEB SERVICE COMPOSITIONS
15

Table 1: The Rules.
dia
1
hp, L ,x
ψ
j
,noi ⊢
E
i
hτ
l
i
R
ϕ
hp
′
,L ,x
ψ
j+1
,noi ⊢
E
i+1
ϕ
p
γα
=⇒
R
τ
∪L
p
′
, α ∈ {l, l}, α ∈ L , γ ∈ (L − R
τ
)
∗
E
i+1
= E
i
∪ {ψ
j
= hγi
R
τ
∪L
hαi
R
τ
∪L
ψ
j+1
}
dia
2
hp, L ,x
ψ
j
,noi ⊢
E
i
hτ
l
i
R
ϕ
hp
′
,L ,x
ψ
j+1
,noi ⊢
E
i+1
ϕ
p
γα
=⇒
{τ
l
}∪R
τ
∪L
p
′
, α = τ
l
, l 6∈ L , γ ∈ (L − R
τ
)
∗
E
i+1
= E
i
∪ {ψ
j
= hγi
R
τ
∪L
ψ
j+1
}
dia
3
hp, L ,x
ψ
j
,yesi ⊢
E
i
hτ
l
i
R
ϕ
hp
′
,L ,x
ψ
j+1
,noi ⊢
E
i+1
ϕ
p
γα
=⇒
R
τ
∪L
p
′
, α ∈ {l,l}, α ∈ L , γ ∈ (L − R
τ
)
∗
E
i+1
= E
i
∪ {ψ
j
= event seq(γ,R
τ
∪ L ,hαi
R
τ
∪L
ψ
j+1
)}
dia
4
hp, L ,x
ψ
j
,yesi ⊢
E
i
hτ
l
i
R
ϕ
hp
′
,L ,x
ψ
j+1
,noi ⊢
E
i+1
ϕ
p
γα
=⇒
{τ
l
}∪R
τ
∪L
p
′
, α = τ
l
, l 6∈ L , γ ∈ (L − R
τ
)
∗
E
i+1
= E
i
∪ {ψ
j
= event seq(γ,R
τ
∪ L ,ψ
j+1
)}
box
1
hp, L ,x
ψ
j
,B i ⊢
E
i
[τ
l
]
R
ϕ
hp
1
,L ,x
ψ
j
1
,yesi ⊢
E
i+1
ϕ· · · hp
n
,L ,x
ψ
j
n
,yesi ⊢
E
i+1
ϕ
condition
condition =
{p
i
| p
α
=⇒
R
τ
∪L
p
i
, 1 ≤ i ≤ n, α ∈ {l,l} , α ∈ L }
E
i+1
= E
i
∪ {ψ
j
= [α]
R
τ
(
^
k=1...n
ψ
j
k
)}
box
2
hp, L ,x
ψ
j
,B i ⊢
E
i
[τ
l
]
R
ϕ
hp
1
,L ,x
ψ
j
1
,yesi ⊢
E
i+1
ϕ· · · hp
n
,L ,x
ψ
j
n
,yesi ⊢
E
i+1
ϕ
condition
condition =
{p
i
| p
α
=⇒
{τ
l
}∪R
τ
∪L
p
i
, 1 ≤ i ≤ n, α = τ
l
, l 6∈ L }
E
i+1
= E
i
∪ {ψ
j
= (
^
k=1...n
ψ
j
k
)}
and
hp, L ,x
ψ
j
,B i ⊢
E
i
ϕ
1
∧ ϕ
2
hp, L ,x
ψ
j
1
,B i ⊢
E
i+1
ϕ
1
hp, L ,x
ψ
j
2
,B i ⊢
E
i+1
ϕ
2
E
i+1
= E
i
∪ {ψ
j
= ψ
j
1
∧ ψ
j
2
}
or
1
hp, L ,x
ψ
j
,B i ⊢
E
i
ϕ
1
∨ ϕ
2
hp, L ,x
ψ
j
,B i ⊢
E
i
ϕ
1
or
2
hp, L ,x
ψ
j
,B i ⊢
E
i
ϕ
1
∨ ϕ
2
hp, L ,x
ψ
j
,B i ⊢
E
i
ϕ
2
3.1 Tableau Rules
A tableau, i.e., a proof tree, is built starting from a
root labelled with the following initial goal
hp, L ,x
ψ
0
,B
0
i ⊢
E
0
ϕ.
where, for any tableau, B
0
= no, E
0
=
/
0 and ψ
0
is the
formula to be obtained through the tableau search.
Then, the construction proceeds by applying spe-
cific rules to successively simplify the goal and extend
the environment until terminal sequents are reached.
Namely, the sequents labelling the immediate succes-
sors of a node are determined by the rules in Table 1,
while terminal sequents (successful and unsuccessful)
are identified in Table 2.
The rules take into account the structure of the
formula present in the premise of each sequent (the
first modal operator), and some ”context” informa-
tion: specifically, context information regard the last
examined logical operator. The rules and and or
specify recursion on one or both the component for-
mulae.
In Table 1 the shorthand hγi
S
ϕ is used to repre-
sent the sequence hδ
1
i
S
·· · hδ
n
i
S
ϕ when γ = δ
1
·· · δ
n
and n ≥ 1. If γ = λ, then hγi
S
ϕ is equal to ϕ. The
rules dia and box have a case regarding the actions
in the interface L and one regarding communications
inside p; in the case in which p does not perform ei-
ther the required action in the interface or the internal
communication, instead of forcing q to substitute p,
ICSOFT 2009 - 4th International Conference on Software and Data Technologies
16

Table 2: Successful/unsuccessful terminal sequents.
success
1
hp, L ,x
ψ
j
,B i ⊢
E
i
tt
E
i+1
= E
i
∪ {ψ
j
= tt}
succes
2
hp, L ,x
ψ
j
,B i ⊢
E
i
[τ
l
]
R
ϕ
{p
′
| p
α
=⇒
{α}∪R
τ
∪L
p
′
, α ∈ {l,l,τ
l
}} =
/
0
E
i+1
= E
i
∪ {ψ
j
= tt}
unsucces
1
hp, L ,x
ψ
j
,B i ⊢
E
i
ff
unsucces
2
hp, L ,x
ψ
j
,B i ⊢
E
i
hτ
l
i
R
ϕ
p 6
γα
=⇒
{α}∪R
τ
∪L
p
′
, α ∈ {l,l,τ
l
},γ ∈ (L − R
τ
)
∗
we have chosen to produce a failure of the algorithm
to represent, in some sense, a failure of the formula
verification. Now the rules are explained by case anal-
ysis:
• dia
1
, dia
2
. These rules are applicable when the
previously examined logical operator is not a box
one. The rule dia
1
considers the action α be an of-
fered communication, while dia
2
considers α as a
communication inside p. If α is preceded by a
sequence γ of actions not in R
τ
, q must perform
an equal sequence of corresponding dual actions;
obviously, if α = τ
l
no corresponding action is re-
quired of q. Note that when more than one move
exists for p, each one produces the specification
of a different set of candidate processes q. It is
out of the scope of this paper the definition of a
possible strategy for choosing the ”most suitable”
set of candidate processes.
• dia
3
, dia
4
. When the last examined formula oper-
ator is a box one, the sequence γ of actions must be
performed in all paths of q before performing α, if
different from τ
l
. Otherwise only the sequence γ
must be performed in all paths. In such a way the
connected behaviors of p and q are synchronized.
• box
1
, box
2
. These rules take account of the abil-
ity of p of performing k actions α: for each one a
branch of the tableau is opened to verify the for-
mula ϕ.
• and. The rule says that the constructions of the
two sub-formulae are carried on separately, and
the results are composed.
• or
1
and or
2
: straightforward.
A sequent S = hp, L ,x
ψ
j
,B i ⊢
E
i
ϕ, S can be ei-
ther a successful or an unsuccessful terminal. The
successful/unsuccessful terminals are clearly defined
in Table 2. A tableau is successful if it is fi-
nite and all of its leaves are successful terminals.
If hp
1
,L ,x
ψ
j
1
,B i ⊢
E
i
1
ϕ
1
·· · hp
n
,L ,x
ψ
j
n
,B i ⊢
E
i
n
ϕ
n
are all the leaves of the tableau for the goal
hp, L ,x
ψ
0
,noi ⊢
E
0
ϕ, and they are also successful
terminals, then the solution is the formula ψ
0
, con-
tained in all the environments of the leaves and re-
cursively obtained by substituting the right hand side
of each equation ψ
k
= ψ
′
(taken from any terminal
environment) each time ψ
k
exists in some environ-
ment. When ψ
′
is a SHML formula the procedure
terminates. It is worth noting that, while the name ψ
k
can appear more than once in the terminal environ-
ments, its definition is unique, i.e., in only one leaf
environment we have ψ
k
= ψ
′
.
The following theorem states the soundness of our
approach.
Theorem 3.1. Consider a CCS process p and
a SHML formula ϕ. Any tableau for the goal
hp, L ,x
ψ
0
,B
0
i ⊢
E
0
ϕ, defines the formula ψ
0
such
that: q |= ψ
0
=⇒ (p | q)\L |= ϕ.
Proof. The proof can be done by induction on the
length of the formula ϕ.
4 AN APPLICATION OF THE
METHODOLOGY
In the design of a web service composition, the imple-
mentation details of the candidate component services
are hidden, but, attached to their WSDL interface de-
scriptions, one may luckily have their ”abstract” WS-
BPEL processes (Andrews et al., 2003), represent-
ing the interaction protocol for their usage. Indeed,
this assumption is in line with the facet-based publi-
cation process supported by the SeCSE platform, an
outcome of the European project SeCSE (Di Penta et
al., 2008). In this context, given a set of processes,
described, for example in WS-BPEL, which we can
translate into CCS processes, and a global formula to
be satisfied by the integrated system (that one can fi-
nally realize as a choreographyin the WS-CDL (W3C
Working Group, 2005) specification language), the
approach can be used to deduce the behavioral spec-
ification of the missing partner, i.e., a partner provid-
ing the operations required by the existing part of the
A FORMULA DRIVEN INCREMENTAL CONSTRUCTION OF WEB SERVICE COMPOSITIONS
17
system, to correctly satisfy the global formula.
As an example, let us consider the following sce-
nario, described in (Bertoli et al., 2007), which we
have slightly modified to realize it as a choreography:
The employee of a firm is organizing a work trip. He
presents a ticket request to the employer’s adminis-
tration, complete with ticket details. He has gathered
these data by first interacting with on-line informa-
tion service. The administration will either accept
or refuse such a proposal, and in the former case, it
will try to pay for the ticket of the employee, either by
credit card, or by cheque, through some payment ser-
vice. The employee will eventually get the ticket, or a
cancel message by the administration due to payment
problems, or else a refusal. The aim is to provide the
firm with a service-centric system that automates this
process. The authors had identified five services that
could be used:
• the Administration service: implementing the firm
internal process of employees’ work trip manage-
ment;
• the InfoTrains and InfoFlights services: providing
tickets information over train/flight routes, and
ticket booking/buying services; and
• the BuyCheque and BuyCard services: enabling
payment by cheque or card respectively.
We added the Travel service as the interface with the
user. The main requirement for this composition is
flexibility with respect to the services that will be ac-
tually used at run-time, that is, possibility to seam-
lessly replace a service with another one (e.g., the
transport or payment services). Examples of CCS de-
scriptions of ”skeleton” services for this scenario are
given in Table 3.
Supposing fixed the Travel and Administration
services interfaces, any compatible transport service
must provide: (i) an operation to search for available
seats with respect to the data provided in the query;
(ii) an operation for booking a selected travel, with-
out further data (e.g., payment information); (iii) an
operation to be notified of the payment. Instead, a
payment service consists of an operation to accept
the data for the specific payment mean (either card
or cheque), and it is required to notify the interested
service of the payment in case of success, or to send
an error message back to the requestor.
We show how the presented approach can be ap-
plied to automatically derive properties to be satisfied
by any transport and payment services, given some
global objectives to be ensured by the composition.
Let us first consider the following formula:
ϕ
1
= hτ
fSearch
i
/
0
tt ∧ [τ
fSearch
]
/
0
hτ
book
i
/
0
(hτ
buy
i
/
0
tt ∨ [−]
{τ
fSearch
}
ff)
which says: it is possible to search for flights and
whenever this operation is required, it is possible to
first book a travel and then either buying the ticket or
to start another search.
Suppose that we want this formula to hold for the
composition: S
def
=(TS|AD|TInfo|X|BC|BCH)\L
where X is the missing service interface to be speci-
fied, providing the flights information, and L contains
all the actions of the CCS process components.
The application of the approach leads to the fol-
lowing (sub)formula providing a characterization of
the flights service:
ψ
1
= h fSearchi
/
0
tt ∧ [ fSearch]
L
ψ
11
ψ
11
= event seq( fSearchStarted.
flights,L,hbooki
L
ψ
12
)
ψ
12
= hbuyi
L
tt ∨ [−]
{ fSearch}∪L
ff
The formula, other than requiring the booking and
buying operations from the service to add, ensures
that the communication with that service is correct,
that is, the booking operation is actually reachable.
We note that the FInfo process in Table 3 satisfies ψ
1
,
and so it is a solution for X, whereas the following
process does not:
FInfoBad
def
= fSearch. fsearchStarted.
flights.(FInfoBad + BOOKBad)
BOOKBad
def
= book.(buy.ticket.FIn foBad+
cancel.FIn f oBad)
as it requires to explicitly cancel the booking. Now
suppose that we want to replace the service BC with
another one, without affecting the composition. Thus,
we consider the system:
S
′
def
=(TS|AD|TInfo|FInfo|X|BCH)\L
where X is the missing card payment service, and the
global formula:
ϕ
2
= hτ
ticket
i
/
0
tt ∧ hτ
cancel
i
/
0
tt
which says: either the user will finally get the ticket or
the selected trip is cancelled, that is, both results must
be possible. We note that none of the actions of the
formula are required from the missing service, that
only needs to provide a correct interaction protocol in
S
′
to the satisfaction of ϕ
2
. In this case, the following
formulais derived, satisfied by the service BC in Table
3:
ψ
2
= hcardPayi
L
hreceipti
L
hbuyi
L
tt
∧hcardPayi
L
hinvalidi
L
tt.
ICSOFT 2009 - 4th International Conference on Software and Data Technologies
18
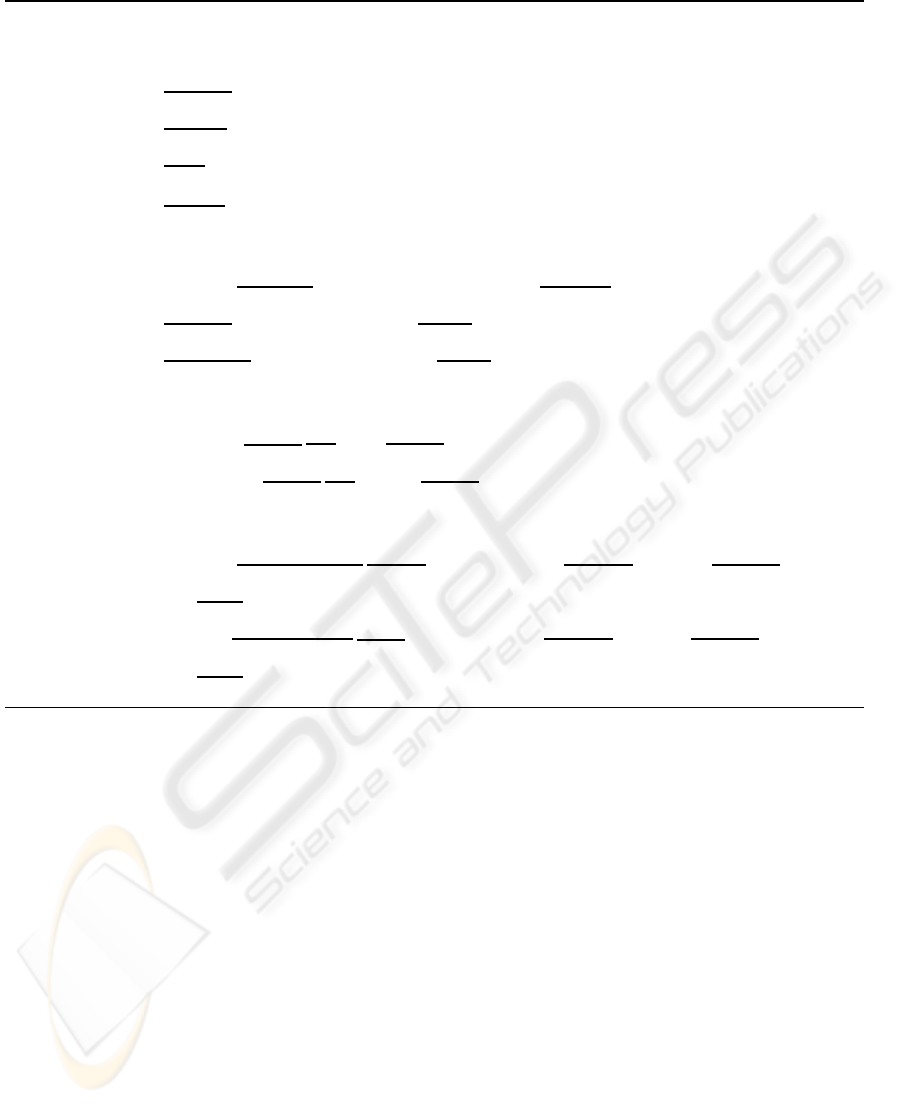
Table 3: Travel management choreography.
Travel Service
TS
def
= FClient + TClient
FClient
def
= f Search. fsearchStarted. flights.(BOOK + TS)
TClient
def
= tSearch.tsearchStarted.trains.(BOOK+ TS)
BOOK
def
= book.(bookOK.ADClient + bookKO.TS)
ADClient
def
= request.(accepted.(ticket.TS+ cancel.TS) + rejected.TS)
Administration Service
AD
def
= request.(accepted.(CPClient +CHPClient) + rejected.AD)
CPClient
def
= cardPay.(receipt.AD+ invalid.cancel.AD)
CHPClient
def
= chequePay.(receipt.AD+ invalid.cancel.AD)
Payment Services
BC
def
= cardPay.(receipt.buy.BC + invalid.BC)
BCH
def
= chequePay.(receipt.buy.BCH + invalid.BCH)
Transport Services
FIn fo
def
= f Search. fsearchStarted. flights.(FInfo+ book.(bookOK.FBUY + bookKO.FIn f o))
FBUY
def
= buy.ticket.FIn fo+ FInfo
TInfo
def
= tSearch.tsearchStarted.trains.(TInfo+ book.(bookOK.TBUY + bookKO.TInfo))
TBUY
def
= buy.ticket.TIn fo + TIn fo
5 CONCLUSIONS AND RELATED
WORK
In this paper, given an incomplete system (say p) and
a requirement described by the logic formula ϕ, an
automatic procedure is defined to identify a formula
ψ such that, for each q satisfying ψ, we have that
the parallel composition between p and q satisfies ϕ.
For the sake of clarity, only requirements expressed
in the Selective Hennessy-Milner Logic (SHML) are
used. The extension to full selective mu-calculus can
be easily defined. The procedure can be incorporated
in an implementation of a model checker for the Con-
currency Workbench of the New Century (CWB-NC)
(Cleaveland and Sims, 1996), a tool for the automated
analysis of concurrent systems.
In (Andersen, 1995), an automatic method is pro-
posed, sound and complete for the full mu-calculus,
able to determine the formula ψ; such method al-
ways includes in ψ all the possible behaviors of p,
so producing a formula whose complexity depends
on the number of states of p. Our aim is, even at
the price of non-completeness of the method, to de-
fine a more efficient formula ψ for q, that is a formula
containing only the corresponding actions of the in-
complete communications of p. Indeed, simplicity of
the derived property ψ and scalability of the verifica-
tion process, are necessary for applying the method to
both incremental design and system evolution scenar-
ios where p is already in place, realizing some func-
tionality, and one needs to understand the specifica-
tion of the functionality of the new component that
would behave correctly with p. Scalability problems
are also tackled, in our work, by using a local model
checking methodology combined with the SHML that
provides an abstraction technique as shown in (Bar-
buti et al., 1999).
The formal problem we face in this paper could
A FORMULA DRIVEN INCREMENTAL CONSTRUCTION OF WEB SERVICE COMPOSITIONS
19

be alternatively solved under the well known assume-
guarantee theoretical framework. This provides infer-
ence rules that permit to deduce the global validity of
a formula for a system, by verifying correctness of a
given component under a set of assumptions on the
environment (a report on this technique is contained
in (Furia, 2005)). The most difficult part here is the
generation of the assumptions, a job that for long has
been left (at least partially) to the developer ((Pasare-
anu et al., 1999), (Inverardi et al., 2000)). Starting
from the paper (Giannakopoulou et al., 2002), a num-
ber of works use a learning algorithm for regular lan-
guages (Angluin, 1987) to automatically derive the
weakest assumptions for the component at hand to
satisfy a safety property. This approach requires both
the component and the formula be modelled as deter-
ministic finite state machines and model checking is
used iteratively (until convergence of the algorithm)
to identify states and transitions of the environment.
In this respect, our approach, that works for all prop-
erties expressible in SHML (both safety and liveness)
and includes non-determinism, is more efficient as it
is based on local model checking and does not even
require to construct the state transition system of the
component.
In the service-oriented computing area, formal
methods have been used to define unambiguous se-
mantics for the languages WS-BPEL and WS-CDL,
to describe service compositions and interaction pro-
tocols (called choreography). An overview of the
various formalisms proposed, including process alge-
bras, is contained in (Breugel and Koshkina, 2006).
Once a formal model of the system is available, one
can check properties such as deadlock-freeness and
correctness of conversationswith the services (see (Fu
et al., 2005) and (Kazhamiakin et al., 2006)). Con-
versely, given a set of service interfaces and a chore-
ography to be realized, one may ask whether service
behaviors may be deduced generating conversations
that, at global level, are all admissible by the chore-
ography. In (Fu et al., 2005), sufficient conditions for
realizability of a choreography are given, and the ser-
vice behaviors are deduced through projection of the
global conversations (i.e., removing messages that do
not involve the specific service). In our work, we are
given a partial choreography already ”realized” that
needs to be extended with an additional service, so
to satisfy a global requirement expressed by a SHML
formula. Our method allows us to eventually deduce
another formula that is used to discover a class of ser-
vice implementations all able to complete the realiza-
tion of the extended choreography. In (Lohmann et
al., 2007) the authors propose to attach an operational
description to a service P, automatically computed,
characterizing services whose composition with P
is deadlock-free or satisfies specific behavioral con-
straints. Finally, the Open Workflow Nets formalism,
a special class of Petri Nets, is used both to describe
the processes and the constraints. As we consider all
properties that can be expressed in SHML, our ap-
proach is more general, and we can check constraints
satisfaction by model checking. Finally, the paper
(Martinelli and Matteucci, 2007) presents a simpli-
fied version of Andersen’s partial model checking al-
gorithm with the aim of applying it to the definition of
web service orchestrations: given a parallel composi-
tion of processes, all known, the specification of the
orchestrator is deduced. They may avoid the formula
explosion of the original Andersen’s method as they
just need to generate a process, containing only com-
munication actions, to make sure that these happen in
the right order. Indeed, differently from Andersen’s
and ours, their method only works if the construc-
tion of the transition system of the parallel processes
is feasible. As a future work, we intend to develop
a service discovery tool integrating the approach and
analyze its efficiency and usefulness compared to the
existing methods.
REFERENCES
Andersen, H. R. (1995). Partial Model Checking (Extended
Abstract). In LICS’95, Proc. 10th Annual IEEE Sym-
posium on Logic in Computer Science, San Diego,
California, USA, 26-29 June. IEEE. 398–407.
Andrews, T. and Curbera, F. and Dholakiam, H. and
Goland, Y. and Klein, J. and Leymann, F. and
Liu, K. and Roller, D. and Smith, D. and Thatte,
S. and Trickovic, I. and Weerawarana, S. Busi-
ness Process Execution Language for Web Services.
(http://www.ibm.com/developerworks/library/
specification/ws-bpel/).
Angluin, D. (1987). Learning regular sets from queries
and counterexamples. Information and Computation
75(2). 87–106.
Bao, L. and Zhang, W. and Zhang, X. (2006). Describ-
ing and Verifying Web Service Using CCS. In PD-
CAT06, Seventh Int. Conf. on Parallel and Distributed
Computing, Applications and Technologies, Washing-
ton, DC, USA. IEEE. 421–426.
Barbuti, R. and De Francesco, N. and Santone, A. and
Vaglini, G. (1999). Selective mu-calculus and
Formula-Based Abstractions of Transition Systems.
Journal of Computer and System Sciences 59(3).
537–556.
Bertoli, P. and Hoffmann, J. and Freddy, L. and Pistore, M.
(2007). Integrating Discovery and Automated Com-
position: from Semantic Requirements to Executable
Code. In ICWS 2007, International Conference on
ICSOFT 2009 - 4th International Conference on Software and Data Technologies
20

Web Services, Salt Lake City, Utah, USA, July 9-13
2007. IEEE. 815–822.
Breugel, F. and Koshkina, M. (2006). Models and verifica-
tion of BPEL.
(http://www.cse. yorku.ca/ franck/research/drafts/
tutorial.pdf)
Clarke, E.M. and Grumberg, O. and Peled, D. (2000).
Model Checking. MIT press.
Cleaveland, R. (1989). Tableau-Based Model Checking
in the Propositional Mu-Calculus. Acta Informatica
27(8). 725–747.
Cleaveland, R. and Sims, S. (1996). The NCSU Concur-
rency Workbench. In CAV’96, Eighth International
Conference on Computer-Aided Verification. Lecture
Notes in Computer Science 1102. 394–397.
Di Penta, M. and Bastida, L. and Sillitti, A. and Baresi,
L. and Ripa, G. and Melideo, M. and Tilly, M. and
Spanoudakis, G. and Maiden, N. and Gorroogoitia
Cruz, J. and Hutchinson, J. (2008). SeCSE - Service
Centric System Engineering: an overview. In At your
service: Service Engineering in the Information Soci-
ety Technologies Program. MIT Press. ISBN: 978-0-
262-04253-6.
Fu, X. and Bultan, T. and Su J. (2005). Synchronizability
of Conversations among Web Services. IEEE Trans.
Software Eng., 31(12). 1042–1055.
Furia, C.A. (2005). A compositional world: a survey of
recent works on compositionality in formal methods.
Technical Report 2005.22, Dipartimento di Elettron-
ica e Informazione, Politecnico di Milano.
Giannakopoulou, D. and Pasareanu, C. and Barringer, H.
(2002). Assumption Generation for Software Com-
ponent Verification. In ASE 2002, 17th International
Conference on Automated Software Engineering, 23-
27 September 2002, Edinburgh, Scotland, UK. 3–12.
Inverardi, P. and Yankelevich, D. and Wolf, A. L. (2000).
Static Checking of Systems Behaviors Using Derived
Component Assumptions. ACM Transactions on Soft-
ware Engineering and Methodology 9(3). 239–272.
Kazhamiakin, R. and Pistore, M. and Santuari, L. (2006).
Analysis of communication models in web service
compositions. In WWW’06, 15th international con-
ference on World Wide Web. 267–276.
Lohmann, N. and Massuthe, P. and Wolf, K. (2007). Behav-
ioral Constraints for Services. In BPM 2007, 5th In-
ternational Conference on Business Process Manage-
ment, Brisbane, Australia, Sept. 24-28. Lecture Notes
in Computer Science 4714. Springer. 271–287.
Martinelli, F. and Matteucci, I. (2007). Synthesis of Web
Services Orchestrators in a Timed Setting. In WS-FM
2007, 4th International Workshop on Web Services
and Formal Methods, Sept. 28-29. Lecture Notes in
Computer Science 4937. Springer. 124–138.
Milner, R. (1989). Communication and Concurrency.
Prentice-Hall.
Pasareanu, C. and Dwyer, M. and Huth, M. (1999).
Assume-guarantee model checking of software: A
comparative case study. In 6th SPIN Workshop. Lec-
ture Notes in Computer Science 1680. 168–183.
Stirling, C. (1991). An Introduction to Modal and Temporal
Logics for CCS. In UK/Japan workshop on Concur-
rency : theory, language, and architecture, Oxford,
UK. Springer-Verlag. 2–20.
W3C Working Group (2005). Web Services Chore-
ography Description Language Version 1.0.
(http://www.w3.org/TR/ws-cdl-10/).
W3C Working Group (2007). Web Services De-
scription Language (WSDL) Version 2.0.
(http://www.w3.org/TR/wsdl20-primer/).
APPENDIX
Operational semantics of CCS.
The operational semantics (see for the standard ver-
sion (Milner, 1989)) is given by the relation −→ ⊆
P × A × P , where A is the set {a,a,τ
a
,b,b,τ
b
,...};
this relation is the least one defined by the rules in Ta-
ble 4 (we omit the symmetric rule of Sum and Par).
Since we consider abstract WS-BPEL process, where
all actions are communications, we modify the stan-
dard CCS semantic rule for the operator ” | ” so that
the produced action be τ
l
, different for each visible
action l. These new visible actions can be used in the
global formulae. Each relabelling function f has the
property that f(τ
l
) = τ
l
for each visible action l.
Satisfaction of a Selective mu-calculus Logic
Formula.
The precise definition of the satisfaction of the closed
formula ϕ by the process p is given in Table 5 where
the transition relation =⇒
I
, parametric with respect
to I ⊆ A , is used. By p
α
=⇒
I
q we express the fact
that it is possible to pass from p to q by performing
a (possibly empty) sequence of actions not belonging
to I (i.e., non-interesting actions belonging to A − I)
and then the action α in I. Note that =⇒
A
= −→.
Definition 5.1. Let p be a CCS pro-
cess and I ⊆ A , for each α ∈ I,
p
α
=⇒
I
q iff p
γα
−→q, for some γ ∈ (A − I)
∗
.
From now on, the following abbreviations will be
used:
[α
1
,. . . ,α
n
]
R
ϕ = [{α
1
,. . . ,α
n
}]
R
ϕ
[−]
R
ϕ = [A ]
R
ϕ
[−K]
R
ϕ = [A − K]
R
ϕ
Example 5.1. Some examples of selective mu-
calculus formulae are given.
ϕ
1
= hbi
{c}
tt: “it is possible to perform b without
performing c before”;
ϕ
2
= νZ.[a]
/
0
(Z∧[a]
{c}
ff): ”it always holds that two
successive occurrence of a are not possible if not in-
terleaved by an occurrence of c”.
A FORMULA DRIVEN INCREMENTAL CONSTRUCTION OF WEB SERVICE COMPOSITIONS
21
Table 4: Operational semantics of CCS.
Act
α.p
α
−→ p
Sum
p
α
−→ p
′
p+ q
α
−→ p
′
Con
p
α
−→ p
′
x
α
−→ p
′
x
def
= p
Par
p
α
−→ p
′
p|q
α
−→ p
′
|q
Com
p
l
−→ p
′
, q
l
−→q
′
p|q
τ
l
−→ p
′
|q
′
Rel
p
α
−→ p
′
p[ f]
f(α)
−→ p
′
[ f]
Res
p
α
−→ p
′
p\L
α
−→ p
′
\L
α,α 6∈ L
Table 5: Satisfaction of a closed formula by a process.
p 6|=
ff
p |=
tt
p |= ϕ∧ ψ iff p |= ϕ and p |= ψ
p |= ϕ∨ ψ iff p |= ϕ or p |= ψ
p |= [K]
R
ϕ iff ∀p
′
∀α ∈ K p
α
=⇒
K∪R
p
′
implies p
′
|= ϕ
p |= hKi
R
ϕ iff ∃p
′
∃α ∈ K.p
α
=⇒
K∪R
p
′
and p
′
|= ϕ
p |= νZ.ϕ iff p |= νZ
n
.ϕ for all n
p |= µZ.ϕ iff p |= µZ
n
.ϕ for some n
where, for each n, νZ
n
.ϕ and µZ
n
.ϕ are defined as:
νZ
0
.ϕ = tt µZ
0
.ϕ = ff
νZ
n+1
.ϕ = ϕ[νZ
n
.ϕ/Z] µZ
n+1
.ϕ = ϕ[µZ
n
.ϕ/Z]
and ϕ[ψ/Z] indicates the substitution of ψ for each free occurrence of Z in ϕ.
ICSOFT 2009 - 4th International Conference on Software and Data Technologies
22
