
A METHOD FOR PORTFOLIO MANAGEMENT
AND PRIORITIZATION
An Incremental Funding Method Approach
Gustavo Taveira, Antonio Juarez Alencar and Eber Assis Schmitz
Informatics Graduate Program, Institute of Mathematics and Electronic Computing Center
Federal University of Rio de Janeiro, Rio de Janeiro, Brazil
Keywords:
Portfolio management, Incremental funding method, Minimum marketable features, Principles of choice, De-
cision theory.
Abstract:
In today’s very competitive business environment, making the best possible use of limited resources is crucial
to achieve success and gain competitive advantage. To accomplish such a goal organizations have to maxi-
mize the return provided by their portfolio of future investments, choosing very carefully the IT projects they
undertake and the risks they are willing to accept, otherwise they are bound to waste time and money, and
still be likely to fail. This article introduces a method that enables managers to better evaluate the investment
to be made in a portfolio of IT projects. The method favors the identification of common parts, avoiding the
duplication of work efforts, and the selection of the implementation order that yields the highest payoff con-
sidering a given risk exposure policy. Moreover, it extends Denne and Cleland-Huang’s ideas on minimum
marketable feature modules and uses both Decision Theory and the Principles of Choice to guide the decisions
made under uncertainty.
1 INTRODUCTION
In today’s dynamic business environment where most
organizations strive to gain competitive advantage
over a myriad of competitors, the use of information
technology (IT) is seen as a crucial tool to achieve
such a goal. With its growing strategic importance,
the expenditure on IT keeps on increasing rapidly and
has become a dominant part of the capital budget of
organizations in many markets (Chen et al., 2007).
Although businesses have invested enormous
sums in IT, these investments have often proved to
be unsuccessful, exceeded budget, and even harmed
companies (Bingi et al., 1999; Chen, 2001; Somers
and Nelson, 2003). Because of that, while IT projects
are becoming more complex, due to the uncertainty
about their economic impact, technological complex-
ity, rapid obsolescence, implementation challenges,
and so forth, the pressure imposed on managers to
keep the balance between risk and payoff on their
decision making is getting even bigger (Chen et al.,
2007; S. Dewan, 2007).
To make information technology investment deci-
sions easier McFarlan suggests that portfolio theory
should be used to analyze and manage the money to
be spent on IT (McFarlan, 1981).
An important lesson that comes from portfolio
theory is the understanding that the values of invest-
ments or assets within a portfolio are often highly
correlated. In other words, investment decisions are
seldom taken in isolation (Markowitz, 1952; Sil-
vius, 2008). Hence, project portfolio management
(PPM) has been receiving increasing attention from
both practitioners and researchers, as PPM practices
advocate that the entire portfolio of projects have to
be considered before a decision is reached on which
projects should be given priority on implementation
and which ones should be added or removed from
the portfolio (Jeffery and Leliveld, 2004; Reyck et al.,
2005).
This article introduces a method that enables
decision makers to better evaluate the investments
to be made in a portfolio of IT projects. Based on
an organization risk taking or risk averse culture the
method identifies the implementation order that yields
the highest payoff and avoid the duplication of work.
The method extends Denne and Cleland-Huang’s
Incremental Funding Method (IFM) and their
modularization ideas of minimum marketable
features. Also, it uses both the Decision Theory
23
Taveira G., Juarez Alencar A. and Assis Schmitz E. (2010).
A METHOD FOR PORTFOLIO MANAGEMENT AND PRIORITIZATION - An Incremental Funding Method Approach.
In Proceedings of the 12th International Conference on Enterprise Information Systems - Information Systems Analysis and Specification, pages 23-33
DOI: 10.5220/0002873400230033
Copyright
c
SciTePress
and the Principles of Choice to support the decision
making process under uncertainty.
The reminder of this article is organized as
follows. Section 2 presents the conceptual framework
the paper is based upon. Section 3 introduces the
Incremental Funding Portfolio Management Method
(IFPMM) with the help of a real world inspired exam-
ple. Section 4 presents a discussion on the impact of
the IFPMM on IT portfolio management and business
strategy. Finally, section 5 presents the conclusion.
2 CONCEPTUAL FRAMEWORK
2.1 The Incremental Funding Method
The Incremental Funding Method (IFM) is a finan-
cially informed approach to software development
that uses the Functional Class Decomposition con-
cept (Chang et al., 2001) to decompose the system
to be constructed into small self-contained software
units that can be delivered quickly and whose fea-
tures have value to business. This kind of units are
called minimum marketable features, or MMF for
short (Denne and Cleland-Huang, 2003; Denne and
Cleland-Huang, 2004).
Besides MMFs, projects usually have an archi-
tectural infrastructure they may rely upon. As
claimed by the IFM, this infrastructure can also be
decomposed into self-contained deliverable units,
which are meant to be constructed and delivered on
demand (Denne and Cleland-Huang, 2003; Denne
and Cleland-Huang, 2004). Such units are called
architectural elements (AEs).
By decomposing a project into units that can
be managed as “miniprojects”, the IFM increases
the likelihood of success for large-scale development
efforts (Denne and Cleland-Huang, 2004). The
benefits of this approach to software development
projects are numerous:
• Large and complex systems can be developed
from a relatively smaller investment,
• Bring financial discipline into software develop-
ment practice,
• Return on investment is maximized,
• Demand for shorter investment periods and
payback time are addressed,
• Favor faster time-to-market of projects that
depends upon software development, and
• Position the software development process as a
value creation activity in which business analysis
is an integral part of it.
In the IFM, once the MMFs and AEs are identi-
fied, a window of opportunity is established in which
these units are developed and provide value to busi-
ness. When the window closes the software units are
replaced by a more valuable alternative or discarded
altogether.
Although MMFs and AEs are self-contained units,
it is often the case that they can only be developed
after other MMFs or AEs have been completed. This
creates a dependency relation among such units,
constraining the order in which they can be
developed, thus limiting project sequencing
options (Denne and Cleland-Huang, 2005).
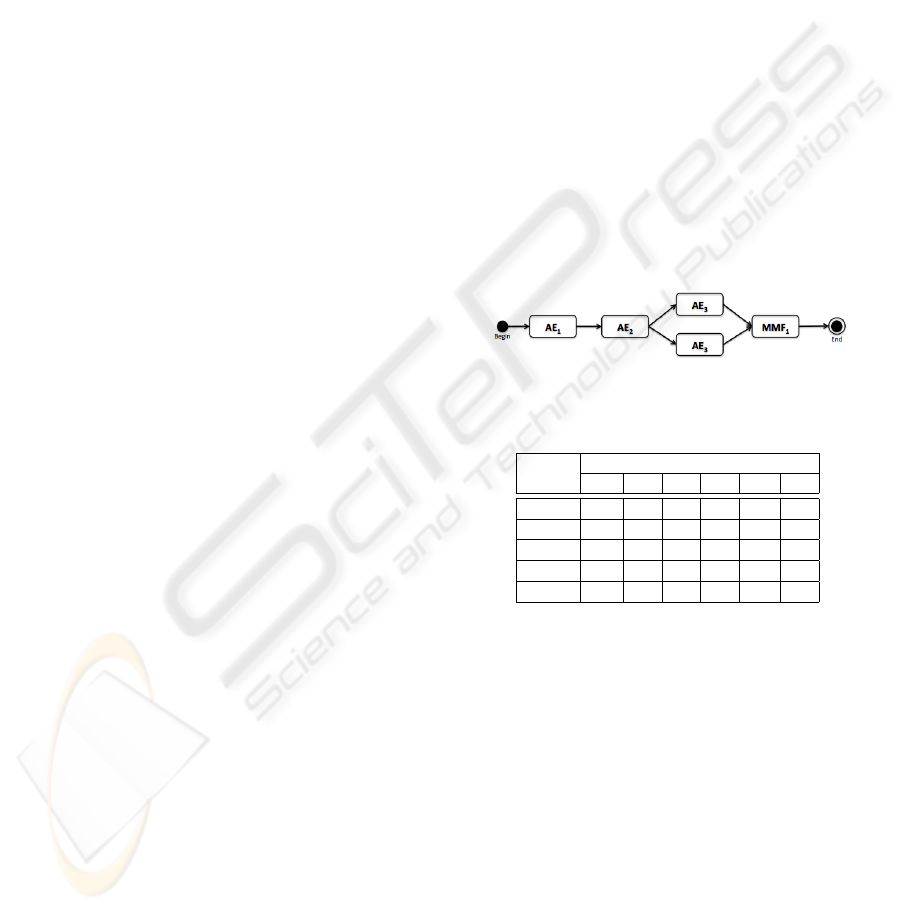
For example, consider the set of MMFs and AEs
whose development schedule is constrained by the
precedence graph introduced in Figure 1. In that
figure an arrow going from one unit to another, e.g.
AE
4
→ MMF
1
, indicates that the development of
the former (AE
4
) must precede the development of
the latter (MMF
1
). Table 1 shows the cash flow
elements of these software units within their window
of opportunity.
Figure 1: The project precedence graph.
Table 1: AEs and MMFs cash flow elements (US$1,000).
Period
Unit 1 2 3 4 · · · 30
AE
1
-27 0 0 0 · · · 0
AE
2
-70 0 0 0 · · · 0
AE
3
-40 0 0 0 · · · 0
AE
4
-14 0 0 0 · · · 0
MMF
1
-12 25 28 35 · · · 80
Note that while the AEs require some
initial investment to be developed, they do not
generate any revenue during the project lifecycle. For
instance, AE
1
can be developed in just one period,
requires US$ 27 thousand to be completed, and yield
no revenue until the window of opportunity closes 29
periods later.
Although MMFs also requires some initial
investment to be developed, once deployed
they provide revenue to business over a certain
number of periods. For instance, MMF
1
can also be
developed in just one period, requires US$ 12 thou-
sand to be completed, and generates US$ 25 thousand
in the second period, US$ 28 thousand in the third,
and so on and so forth. The revenue returned by an
MMF is often the result of cost savings, competitive
differentiation, brand-name projection, and enhanced
customer loyalty (Denne and Cleland-Huang, 2003;
ICEIS 2010 - 12th International Conference on Enterprise Information Systems
24
Denne and Cleland-Huang, 2004).
Counterpointing to the IFM objective, looking
at just one single project at a time and optimiz-
ing its Net Present Value (NPV) is not quite the
main goal of most organizations, which usually have
limited resources, several investment options and
prefer to benefit from the analysis of portfolios of IT
projects instead (Jeffery and Leliveld, 2004; Reyck
et al., 2005).
Moreover, the way the cash-flow elements of
MMF and AEs are calculated by Denne and Cleland-
Huang (op. cit.) prevent them from adequately
reflecting real world circumstances, where it is often
the case that the investment required to develop a
software unit and the revenue it generates cannot be
precisely determined in advance.
To deal with real world situations, one has to
consider the inherent uncertainty associated to
future values of cash-flow elements. Besides, the
literature has repeatedly indicated software develop-
ment as a complex and risky activity (Westerman
and Hunter, 2007). Hence, as results obtained under
uncertainty can be quite different, the valuation of
software projects should always take uncertainties
into account (Abdellaoui and Hey, 2008; Barbosa
et al., 2008; Schmitz et al., 2008).
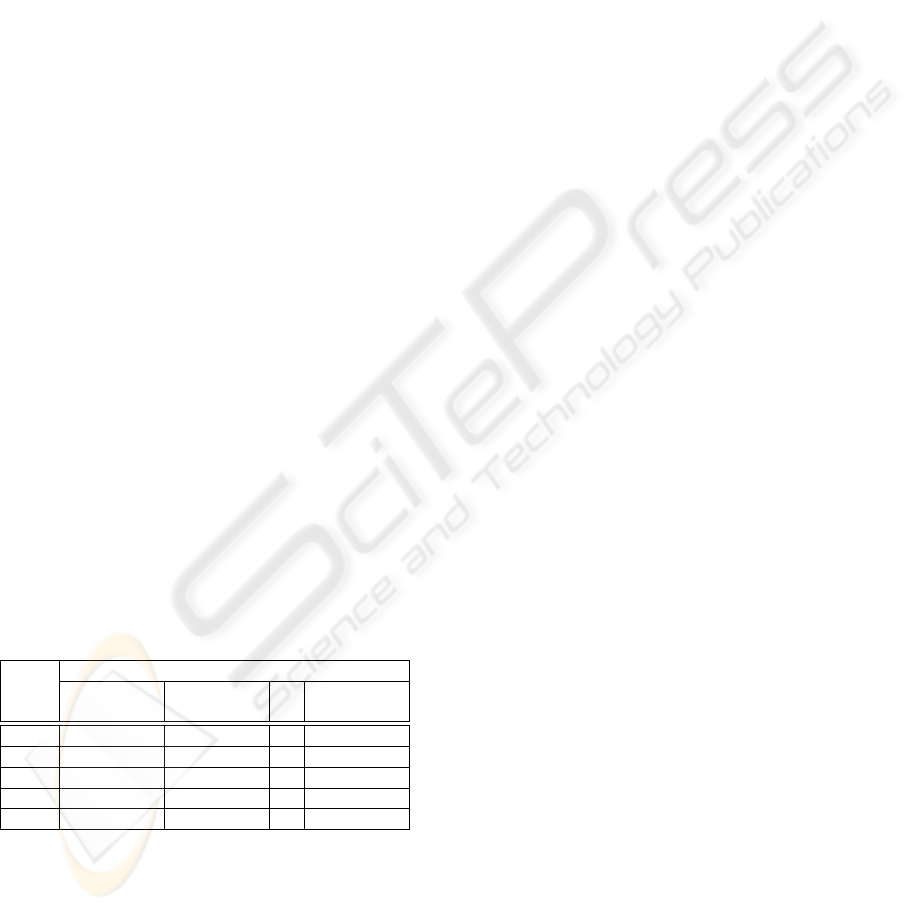
In many circumstances, a triangular probability
density function (TPDF) is used to represent the
uncertainty described in cash flow elements. This
TPDF is obtained by estimating a lower bound (Min),
an upper bound (Max) and the most likely value (ML )
for each period, as presented in Table 2. According
to Hubbard (Hubbard, 2007), the lower bound,
most likely and upper bound values are more easily
obtained considering the worst, most likely and best
case among all reasonable scenarios.
Table 2: Cash flow streams under uncertainty (US$ 1,000).
Period
Unit 1 2 · · · 30
(Min,ML,Max) (Min,ML,Max) (Min,ML,Max)
AE
1
(-35,-24,-20) (0, 0, 0) · · · (0, 0, 0)
AE
2
(-80,-75,-60) (0, 0, 0) · · · (0, 0, 0)
AE
3
(-50,-35,-30) (0, 0, 0) · · · (0, 0, 0)
AE
4
(-18,-12,-10) (0, 0, 0) · · · (0, 0, 0)
MMF
1
(-15,-12,-10) (20,23,30) · · · (70, 85, 90)
2.2 Decision Making under Uncertainty
When all the possible alternatives have known out-
comes and their consequences can be described using
a single measure, then making a choice among them
is an easy task. Otherwise, whenever any sort of
uncertainty is present, the choice becomes more
difficult.
As presented by Holloway (Holloway, 1979),
there are four characteristics that can increase the
difficulty of making choices, turning decision
problems into complex decision problems, namely:
• a large number of factors – which is often the
case for financial problems, such as investments
decision making;
• more than one decision maker – a common situa-
tion to most of the existing business;
• multiple attributes – whenever more than one
aspect is needed to describe the outcome of a
decision and one has to balance between them,
such as profit and risk; and
• uncertainty – which is inherent to any kind of
IT project and to the dynamic environment that
surrounds software development.
When handling portfolios of IT projects and
analyzing the resulting investment options, an orga-
nization usually faces all these difficulties. As the
variables of interest incorporate uncertainty, they
become random variables and, consequently, may
be represented as Probability Density Functions
(PDF) (Kotz and van Dorp, 2004).
Therefore, a method to analyze these PDFs and
make investment decisions under uncertainty is a
“must have” for every single IT decision maker. The
methods of direct choice under uncertainty are clas-
sified in three groups (Holloway, 1979): probabilistic
dominance, summary measures and aspiration-level.
As stated by the probabilistic dominance crite-
rion, in circumstances where the probability of one
of the alternatives achieving any value is greater than
or equal to the probability of any other alternative
achieving that value, then this alternative probabilisti-
cally dominates all the others.
Hence, probabilistic dominance is a compelling
reason for choosing one alternative over another.
Figure 2 presents an example where alternative 1
probabilistically dominates alternative 2.
However, it is not often the case that probabilistic
dominance can be applied. In circumstances where
dominance does not exist, each alternative must be
analyzed regarding its risks and payoffs. During this
analysis, it is very important to consider whether
one is dealing with a risk-taken or risk-averse orga-
nization. Figure 3 presents the cumulative density
function of three alternatives, namely A, B and C,
where none of them probabilistically dominates the
others.
Despite trying to assimilate the entire probability
distributions, the analysis and further comparisons of
alternatives can be done through the use of Summary
A METHOD FOR PORTFOLIO MANAGEMENT AND PRIORITIZATION - An Incremental Funding Method Approach
25
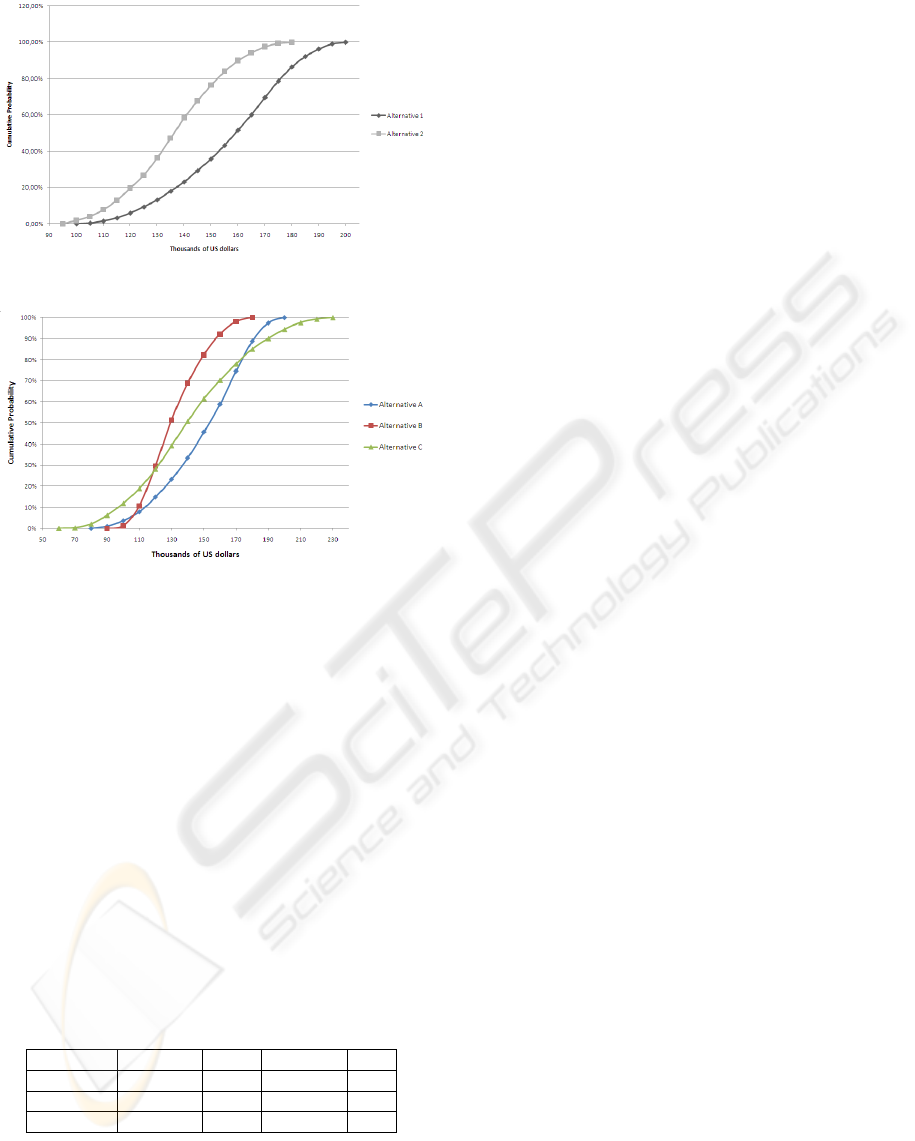
Figure 2: CDF with probabilistic dominance.
Figure 3: CDF without probabilistic dominance.
Measure Criterion, which consider values such as
mean, minimum, and maximum, among others (Hol-
loway, 1979). According to the decision theory (Lang
and Merino, 1993; White, 2006), the following prin-
ciples are used to take decisions under uncertainty
based on summary measures:
• Maximin or Minimax Principle – this principle
always considers the worst case scenario in the
decision making process, choosing the alterna-
tive that has the highest minimum revenue or the
lowest maximum cost, depending on the criterion
one is using. To analyze the example introduced
in Figure 3, the organization would compare the
minimum values presented in Table 3, choosing
alternative B as the best investment option, which
yields at least a US$ 90,000.00 profit.
Table 3: Return of each investment option (US$ 1,000).
Alternative Minimum Mean Maximum H
CV
A 80 150 200 164
B 90 132 180 153
C 65 142 230 179
• Maximax or Minimin Principle - In contrast to
the previous principle, the Maximax and Min-
imin principle always consider the best case sce-
nario in the decision making process, choosing the
alternative that has the highest maximum revenue
or the lowest minimum cost. Using the Max-
imax principle within the example of Figure 3,
the organization would consider the maximum
values presented in Table 3, selecting C as the best
investment option, which can yield a revenue as
high as US$ 230,000.00.
• Equal Likelihood (Laplace) Principle – this
principle assumes that all possible outcomes are
equally likely to occur. Based on this assump-
tion, it considers the mean value of all the possible
alternatives and selects the highest one. Table 3
also presents the mean values from the alterna-
tives within the Figure 3 example. By using the
Laplace principle, the organization would choose
the alternative A as the best investment option.
• Hurwicz Principle – instead of making decisions
based on just one summary measure such as
the previous principles, Hurwicz combines both
minimum and maximum values, creating a
balance between them. Such a balance is achieved
by using an index of optimism (α), which is
estimated by specialists and vary from
organization to organization. Once α is defined,
the Hurwicz criterion value (H
CV
) is given by
Equation 1.
H
CV
= α ∗ Max(Profit) + (1 − α) ∗ Min(Profit)
(1)
Table 3 presents the H
CV
of each alternative
within the example, considering α equal to
70%. In this scenario, an organization using the
Hurwicz principle would prefer alternative C to
any other investment option.
• Minimax Regret (Savage) Principle - analogous
to the Hurwicz principle, it also considers both
minimum and maximum values to analyze each
one of the alternatives, but in a completely
different manner. The objective is to compare
these two values and compute the maximum
regret of each alternative, which is calculated
considering the difference between the best and
the worst outcome that it can achieve. The
maximum regret table from the Figure 3 example
is presented in Table 4. Once the maximum regret
is computed, this principle chooses the alternative
that minimizes it. In this case, the decision maker
would choose alternative B as the best investment
option.
Another useful criterion to be applied is to base
the comparison on some aimed output value that is
very important to the organization. The Aspiration-
Level Criterion maximizes the probability of achiev-
ing such a value. To illustrate, assume that in the
ICEIS 2010 - 12th International Conference on Enterprise Information Systems
26
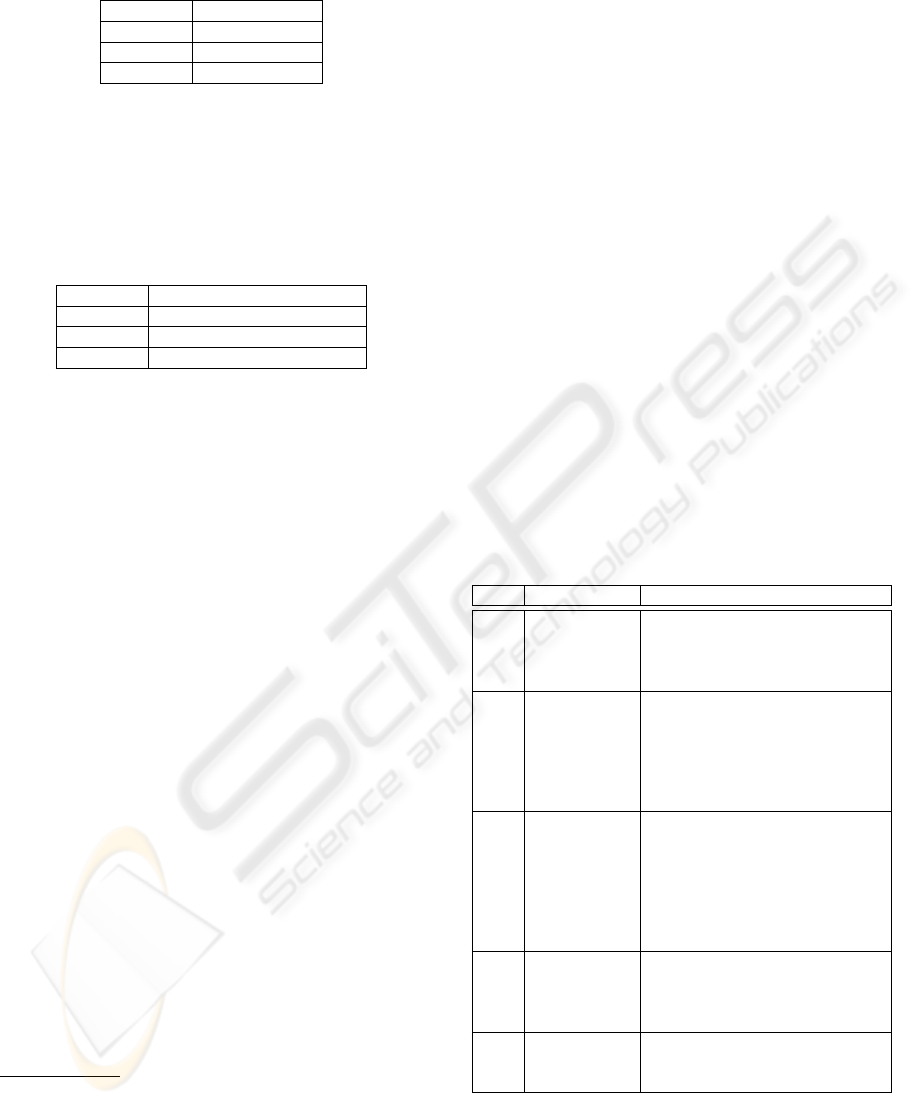
Table 4: Maximum regret per alternative.
Alternative Maximum Regret
A US$ 120,000.00
B US$ 90,000.00
C US$ 165,000.00
Figure 3 example the decision maker defines that it is
extremely important to have at least a US$ 120,000.00
profit. Table 5 presents the probability of achieving
a profit equal to or greater than US$ 120,000.00 for
each alternative. Using the aspiration-level criterion,
alternative A would be chosen.
Table 5: Probability of achieving the aspiration level.
Alternative Prob. of US$ 120,000.00 or more
A 85%
B 70%
C 72%
As aforementioned, it is up to organizations to
define which is the most suitable criterion to be used
in their decision making process under uncertainty.
This criterion of choice may vary from organization
to organization, depending on their objectives and
predefined risk-exposure policy.
3 THE METHOD
For better understanding, the method proposed in
this paper is introduced and explained step-by-step
throughout this section with the help of a real-world
inspired example
1
.
Step 0: Context Information. Consider a large mo-
bile telecommunication carrier such as AT&T, Ver-
izon, Sprint, T-Mobile, Vodafone, Telef
´
onica and
many others, which have millions of subscribers and
provide different kinds of services for voice, data, and
broadband. For the purpose of this paper this organi-
zation is called World Mobile Telecom Corporation,
or WMTC for short.
Technology advances in telecommunications have
brought significant changes in the services provided
by mobile carriers around the world. As a result,
WMTC’s competitors are struggling for strategic
advantages that would enable them to gain market
share and even surpass WMTC.
1
The data used to obtain the results presented in this pa-
per is closely related to real data provided by one of the
Latin America’s largest mobile network operator. Because
the data reflects the current portfolio of on-going IT projects
of this organization and, as a result, part of its business strat-
egy, the authors have been kindly requested not to disclose
its name.
Furthermore, a growing number of customers con-
scious of their bargaining power are demanding for
better products and services for reduced prices, so the
need for innovation and differentiation is increasing
rapidly. Therefore, as WMTC wants to advance its
position as a major player in the mobile telecommu-
nication business, it must undertake the right tactical
and strategic projects, making the best possible use of
its limited human and financial resources.
Considering that there is not enough resources to
run all projects that are necessary to increase its mar-
ket share, WMTC Board of Directors became firmly
convinced that the company has to adopt decision
theory and principles of choice to get the most out
of its investment in IT.
However, due to shortage of funds caused by the
world financial crises, WMTC was forced to reduce
drastically its number of employees. Counting on just
one development team, they need to ensure that the
company concentrates their efforts on maximizing the
benefits of their diversified portfolio of IT projects.
Table 6 presents the projects comprising WMTC’s
portfolio, which are meant to support a strategic move
against growing competition in its market.
Table 6: WMTC’s portfolio of strategic IT projects.
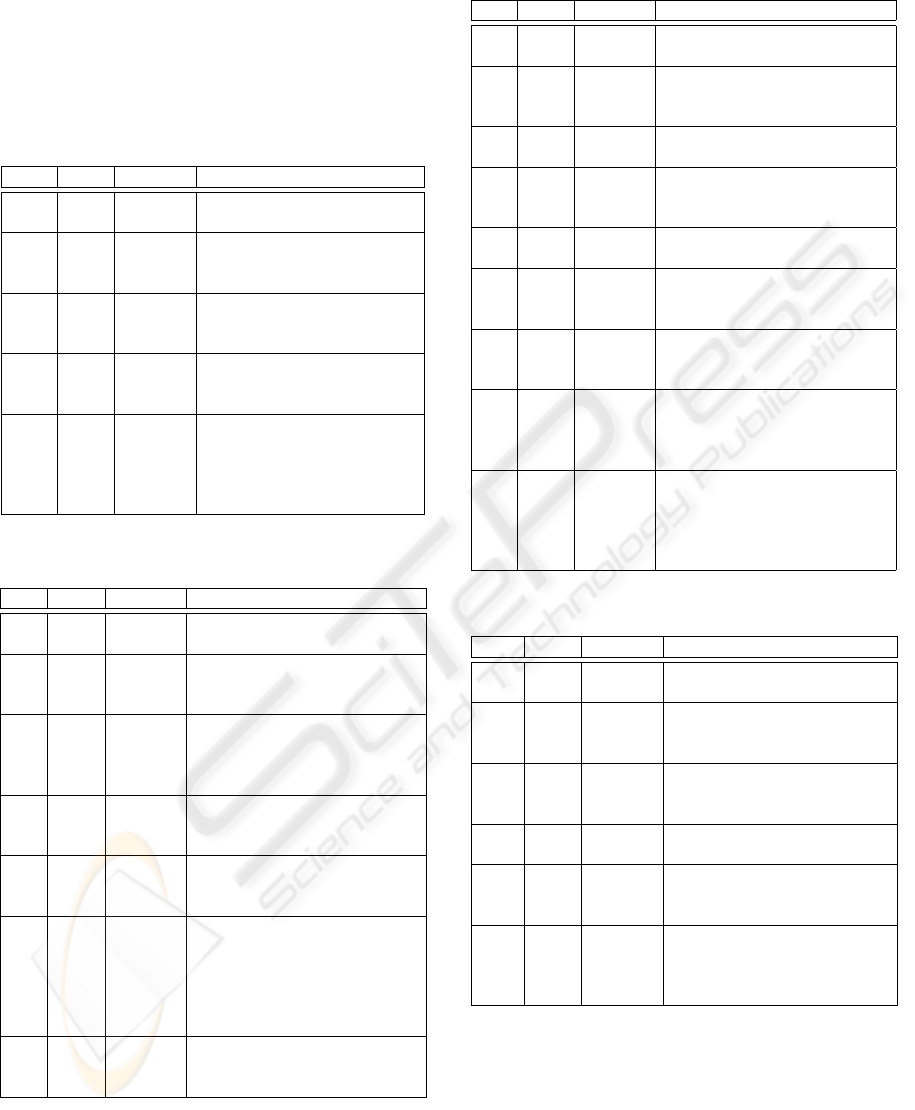
Id Project Description
GSP GOODS AND
SERVICES
PURCHASE
Allows subscribers can go shopping with
nothing else but their mobile phones, us-
ing it as a credit card to pay for goods
and services in associated stores.
EP MOBILE
ENTERTAINMENT
PASS
Lets subscribers to search for movies,
plays and shows, browse their synopsis
and buy tickets directly from their mo-
bile phones. Subsequently to purchasing
a ticket, subscribers receive an SMS with
a queue avoiding electronic ticket.
M
+
MESSAGE+ Enables subscribers to have an e-mail
browser experience when handling SMS
(short message service) and MMS (mul-
timedia message service). Users can
store, search, send, forward, redirect,
auto reply, copy, and also maintain an e-
address book of their contacts.
VM VIDEOMAIL Make it possible for subscribers to re-
ceive, store and retrieve messages when-
ever they can not answer an incoming
video call.
VoIP VOIP SERVICE Delivers voice over internet protocol to
subscribers who already have an unlim-
ited data plan.
Step 1: Identifying the MMFs and AEs within
WMTC’s Portfolio of IT Projects. If one is will-
ing to take advantage of Denne and Cleland-Huang’s
ideas on minimum marketable features (op. cit.), the
A METHOD FOR PORTFOLIO MANAGEMENT AND PRIORITIZATION - An Incremental Funding Method Approach
27
projects in the WMTC portfolio have to be decom-
posed into AEs and MMFs, so that they can be in-
crementally delivered to customers as “miniprojects”.
Tables 7, 8, 9, 10 and 11 introduce the AEs and MMFs
identified by the WMTC’s Project Management Of-
fice (PMO).
Table 7: Goods and services purchase MMFs.
Id Type Name Description
GSP
1
AE Service
subscription
Allows customers to subscribe to
and unsubscribe from the service
GSP
2
AE Credit
analysis
Figures the likelihood of a customer
paying a debt according to pre-
established dates and values
GSP
3
AE M-Payment Lets customers pay for goods and
services they want to buy in associ-
ated stores
GSP
4
AE Refund Allows customers to be refunded
when returning goods and services
they bought in associated stores
GSP
5
MMF Shopping Entitles customers to shop for goods
and services in associates stores.
This includes paying and on occa-
sion being refunded for the goods
and services they have bought
Table 8: Mobile entertainment pass MMFs.
Id Type Name Description
EP
1
AE Service
subscription
Allows customers to subscribe to and
unsubscribe from the service
EP
2
AE Credit
analysis
Figures the likelihood of a customer
paying a debt according to pre-
established dates and values
EP
3
MMF Search
movie
Allows customers to search for
movies, plays and shows based on
multiple criteria such as: title, cast,
district, theater and genre
EP
4
MMF Browse
synopsis
Make it possible for customer to
browse among movie, play and show
synopses
EP
5
AE Captures
customer
location
Gathers information about the cur-
rent customer location (GPS or tower
based)
EP
6
MMF Buy
ticket
Allows customers to choose which
specific theater or showroom seat they
would like to purchase, charges the
ticket value to the customer’s account
and provides a queue avoiding elec-
tronic ticket
EP
7
MMF Browse
nearby
places
Provides information on all theaters
and showrooms in the vicinity of the
current customer location
Step 2: Establishing the Precedence between
identified Software Units. One of the main ben-
efits of organizing MMFs and AEs in a port-
folio is the possibility of more easily identify-
Table 9: Message+ MMFs.
Id Type Name Description
M
+
1
AE Service
subscription
Allows customers to subscribe to and
unsubscribe from the service
M
+
2
AE Credit
analysis
Figures the likelihood of a customer
paying a debt according to pre-
established dates and values
M
+
3
AE Store
messages
Stores SMS and MMS messages re-
ceived by customers
M
+
4
AE Organize
inbox
Allows customers to order messages
by different parameters, delete mes-
sages and search for specific messages
M
+
5
AE Reply Allows customers to edit a text and use
it to reply to a message
M
+
6
AE Send &
Forward
Sends a new and an existing message
to a given address (email or phone
number) or a set of addresses
M
+
7
MMF Manage
inbox
Allows customers to organize their
message boxes, send, reply to and for-
ward messages
M
+
8
MMF Auto
reply &
redirect
While “on” automatically replies to
any received message or redirects all
received messages to a given address
(email or phone number)
M
+
9
MMF Use
contacts
info
Lets customers to use informations
from their contact lists when sending
or forwarding messages, such as con-
tact name, phone number and email
address
Table 10: VideoMail MMFs.
Id Type Name Description
VM
1
AE Service
subscription
Allows customers to subscribe to and
unsubscribe from the service
VM
2
AE Credit
analysis
Figures the likelihood of a customer
paying a debt according to pre-
established dates and values
VM
3
AE Recorder Lets callers to record a video message
when their incoming video calls are
not answered
VM
4
AE Password
input
Authenticates subscribers, granting
access to their VIDEOMAIL accounts
VM
5
MMF Listen to
video mails
Allows customers to retrieve a
recorded video message from their
mail boxes
VM
6
MMF Manage
video mails
Allows subscribers to store or delete a
video message, change their VIDEO-
MAIL welcome message and also re-
trieve the caller’s id
ing common software units. By factoring out
such units one may reduce the portfolio’s time-to-
market and cost, at the same time that increases
quality (Pressman, 2009).
When analyzing the portfolio of strategic IT
projects, the WMTC PMO identified two software
units that are common to two or more projects, i.e.
“Service subscription” (CSU
1
) and “Credit analysis”
(CSU
2
).
ICEIS 2010 - 12th International Conference on Enterprise Information Systems
28
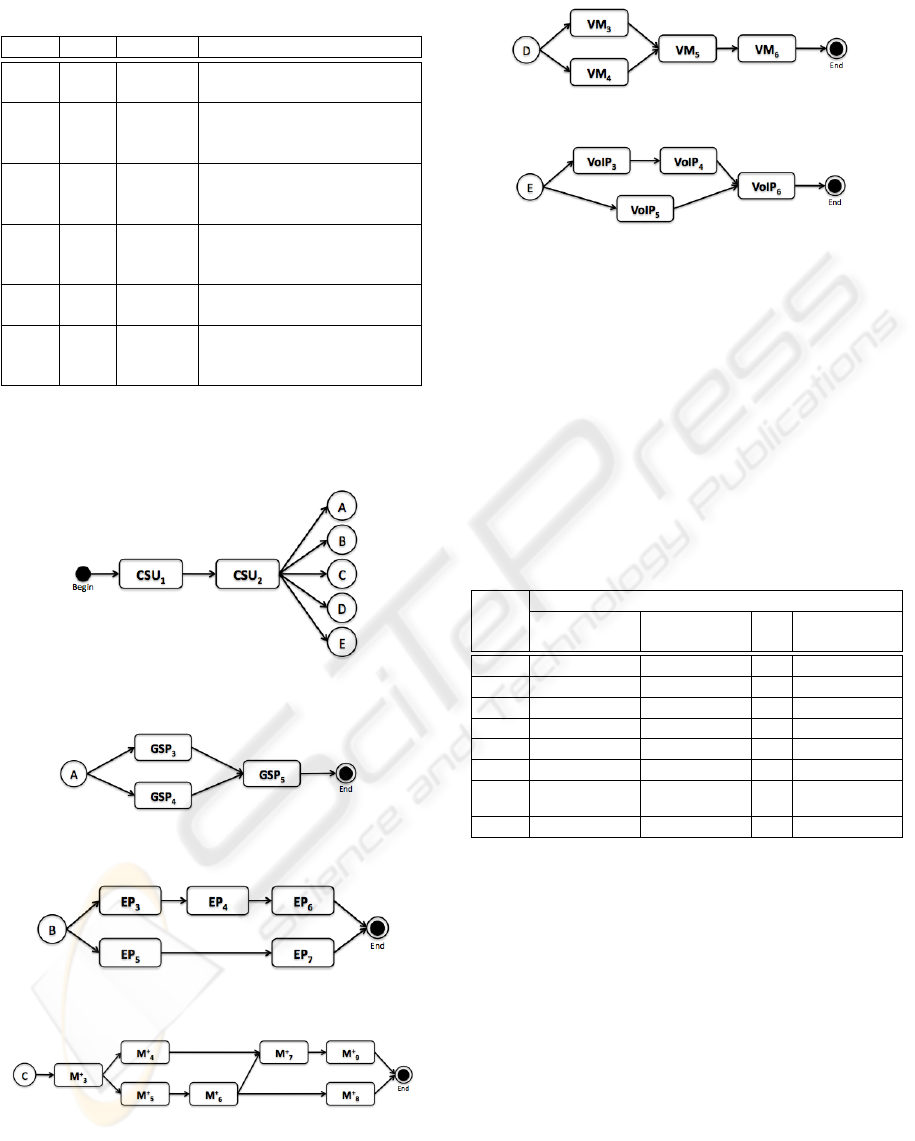
Table 11: VoIP service MMFs.
Id Type Name Description
VoIP
1
AE Service
subscription
Allows customers to subscribe to
and unsubscribe from the service
VoIP
2
AE Credit
analysis
Figures the likelihood of a customer
paying a debt according to pre-
established dates and values
VoIP
3
AE Manage
buddies
Allow subscribers to search, add
and delete buddies from their buddy
list
VoIP
4
MMF Call buddy Call a buddy directly from the
buddy list using voice over internet
protocol (VoIP)
VoIP
5
AE Link buddy
and contact
Link a VoIP buddy to an existing
contact in the subscriber contact list
VoIP
6
MMF Call contact Call a buddy directly from the con-
tact list, using the link between the
contact and the VoIP buddy
Figure 4, together with Figures 5, 6, 7, 8 and 9,
introduce the precedence graph of all software units
in the WMTC’s portfolio of strategic IT projects.
Figure 4: WMTC’s portfolio precedence graph.
Figure 5: Goods and service purchase precedence graph.
Figure 6: Mobile entertainment pass precedence graph.
Figure 7: Message+ precedence graph.
Step 3: Forecasting the Inflows and Outflows
of Software Units within the WMTC Portfolio.
Once the AEs and MMFs have been identified and
arranged into a precedence graph, their estimated
Figure 8: VideoMail precedence graph.
Figure 9: VoIP service precedence graph.
costs and revenues should be calculated and, subse-
quently, analyzed over the window of opportunity that
defines the portfolio lifecycle. See (Hubbard, 2007)
for guidelines on how IT project cost and revenue may
be properly calculated.
To take uncertainty into account WMTC decided
to consider the worst (Min), the best (Max), and the
most likely (ML) scenario for the value of each MMF
and AE cash flow element. Then, these elements were
modeled as triangular probability density functions.
Table 12 presents these values.
Table 12: WMTC’s AEs and MMFs cash flow (US$ 1,000).
Period
Unit 1 2 · · · 30
(Min,ML,Max) (Min,ML,Max) (Min,ML,Max)
CSU
1
(-35,-24,-20) (0, 0, 0) · · · (0, 0, 0)
CSU
2
(-80,-75,-60) (0, 0, 0) · · · (0, 0, 0)
GSP
3
(-50,-35,-30) (0, 0, 0) · · · (0, 0, 0)
GSP
4
(-18,-12,-10) (0, 0, 0) · · · (0, 0, 0)
GSP
5
(-15,-12,-10) (20,23,30) · · · (70, 85, 90)
EP
3
(-34,-29,-25) (15,17,25) · · · (45, 58, 60)
.
.
.
.
.
.
.
.
. · · ·
.
.
.
VoIP
6
(-20,-16,-10) (10,13,20) · · · (0, 0, 0)
Step 4: Generating Scenarios and selecting
the Best Sequencing Options. Once the port-
folio’s precedence graph is built and their
unit’s cash flows are estimated, the PMO must
identify the most attractive sequencing option,
together with its net present value (NPV).
Considering that their cash flow elements are
statistically correlated and that this correlation exists
both between elements of the same cash flow stream
(CFS) and elements of different CFSs within the
portfolio, the NPV can not be approximated by
Laplace’s Central Limit Theorem (CLT), which is
only suitable to a sum of n independent random vari-
ables. However, good computational approximations
can be obtained using sampling procedures like the
Monte Carlo method (Robert and Casella, 2005).
Using a Monte Carlo simulation tool, the WMTC
A METHOD FOR PORTFOLIO MANAGEMENT AND PRIORITIZATION - An Incremental Funding Method Approach
29
PMO decided to sample values for each cash flow
element based on its triangular distribution to gener-
ate one possible scenario and then use these values,
together with the branch and bound algorithm,
to obtain the optimal portfolio sequencing option,
which is the one that yields the maximum NPV.
See (Alencar et al., 2008) for guidelines on how to
use the the branch & bound algorithm to compute the
optimal implementation order in IT projects.
Posterior to the generation of 10,000 scenarios,
there was a total of ten sequencing options that were
chosen as optimal in one or more scenarios. Table 13
presents these sequences.
Table 13: Selected sequencing options.
Id Sequence
Seq
1
CSU
1
, CSU
2
, EP
3
, EP
4
, EP
6
, VoIP
3
, VoIP
4
, EP
5
, EP
7
, GSP
3
,
GSP
4
, GSP
5
, VM
3
, VM
4
, VM
5
, VoIP
5
, VoIP
6
, VM
6
, M
+
3
,
M
+
4
, M
+
5
, M
+
6
, M
+
8
, M
+
7
, M
+
9
Seq
2
CSU
1
, CSU
2
, EP
3
, EP
4
, EP
6
, EP
5
, EP
7
, VoIP
3
, VoIP
4
, GSP
3
,
GSP
4
, GSP
5
, VM
3
, VM
4
, VM
5
, VoIP
5
, VoIP
6
, VM
6
, M
+
3
,
M
+
4
, M
+
5
, M
+
6
, M
+
8
, M
+
7
, M
+
9
.
.
.
.
.
.
Seq
6
CSU
1
, CSU
2
, EP
3
, EP
4
, EP
6
, EP
5
, EP
7
, VoIP
3
, VoIP
4
, GSP
3
,
GSP
4
, GSP
5
, VoIP
5
, VoIP
6
, VM
3
, VM
4
, VM
5
, VM
6
, M
+
3
,
M
+
4
, M
+
5
, M
+
6
, M
+
7
, M
+
9
, M
+
8
.
.
.
.
.
.
Seq
10
CSU
1
, CSU
2
, EP
3
, EP
4
, EP
6
, EP
5
, EP
7
, VoIP
3
, VoIP
4
, VoIP
5
,
VoIP
6
, GSP
3
, GSP
4
, GSP
5
, M
+
3
, M
+
4
, M
+
5
, M
+
6
, M
+
7
, M
+
9
,
M
+
8
, VM
3
, VM
4
, VM
5
, VM
6
Step 5: Resampling the Selected Sequencing Op-
tions. As the number of sequencing options gener-
ated in Step 4 is quite small and some of them did not
have enough values to generate the cumulative density
function (CDF) of their NPV, all of them were taken
through a resampling, generating another 10,000 sce-
narios.
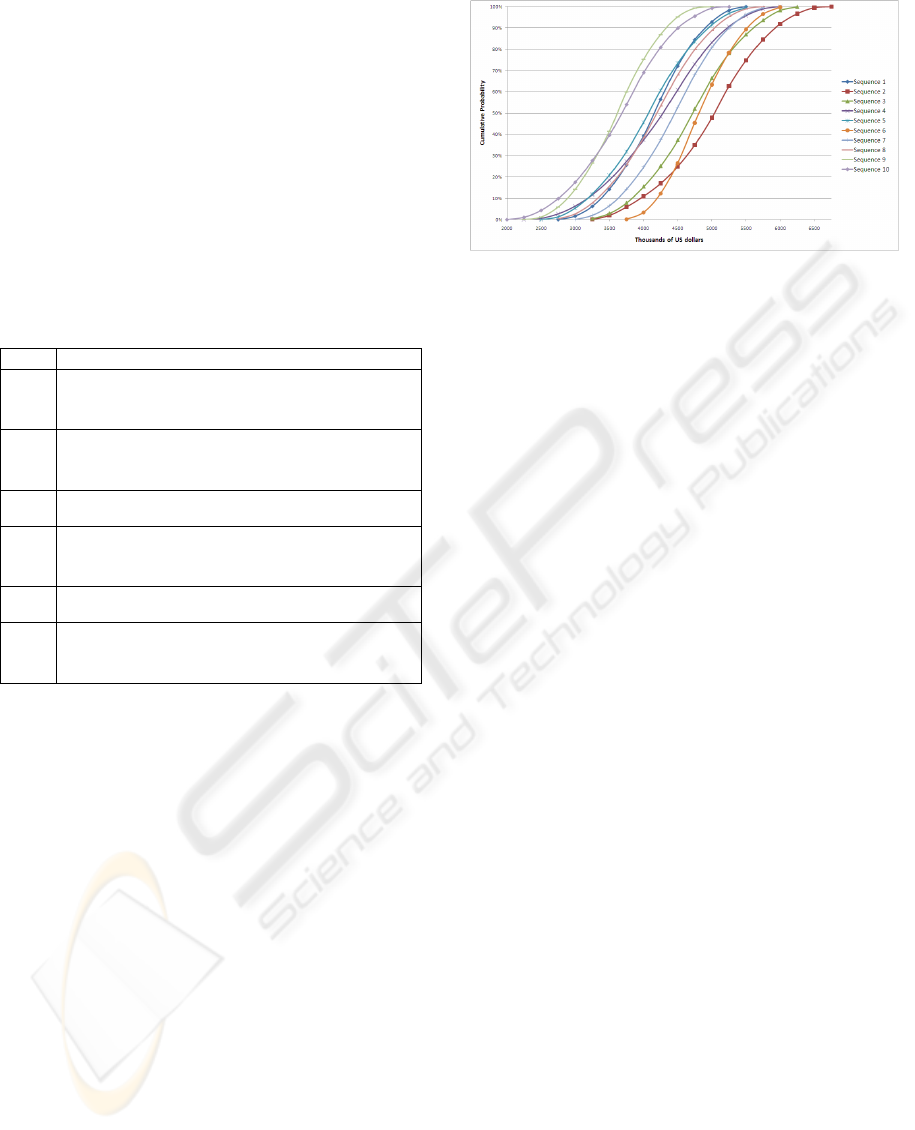
The data collected in these new scenarios was
used by WMTC to built the CDF of the NPV from se-
lected sequences and reach the required error margin,
within a predefined confidence interval. Figure 10
presents these results.
Step 6: Choosing the Best Sequencing Option. Af-
terward, WMTC PMO compared all the simulation
results obtained in Step 5 to decide which is the best
implementation order, considering all the sequencing
options.
As the WMTC’s board of directors has defined
that the organization needs to generate at least a US$
4,000,000.00 revenue from the portfolio to advance
its position as a major player in the mobile telecom-
munication business and also to reach the Latin
Figure 10: Portfolio’s NPV for the selected sequences.
America’s leadership on the last key performance
indicator, which is the average revenue per user
(ARPU). Considering this aspiration, the PMO has
decided to maximize the probability of attaining such
a goal.
In the first step, making use of the Probabilistic
Dominance criterion, the PMO was able to restrict
even more the number of sequencing options which
should be compared. This was accomplished by
eliminating sequences 1, 4, 5, 7, 8, 9 and 10, which
were outperformed and probabilistically dominated
by sequences 2, 3 and 6.
Applying the Aspiration Level criterion on the
comparison of the remaining options, the PMO stated
that sequences 2, 3 and 6 have, respectively, 89%,
84% and 97% probability of achieving an actual
revenue equal to or higher than the targeted one. For
that reason, the PMO defined that Seq
6
was the best
implementation order for the WMTC’s portfolio.
These results were presented by the PMO to the
WMTC board of directors, who decided to undertake
the presented strategy as a guidance to manage their
portfolio and prioritize their projects.
In fact, it should be noted that Seq
2
, which
presents the best results under the mean value, is
outperformed by Seq
6
when taking uncertainties
into account and considering the Aspiration Level
criterion with the values previously defined by the
WMTC’s board of directors.
4 DISCUSSION
At the outset of this paper the authors presented
a method that provides a comprehensive way to
analyze investment options, balance their expected
return against their risk, and decide how to prioritize
the IT projects within one’s portfolio, enabling
organizations to maximize their payoffs. In this
section, some of the key questions regarding the
ICEIS 2010 - 12th International Conference on Enterprise Information Systems
30

use and implications of the proposed method are
addressed.
A. Why have MMF and AE’s Cash Flow Elements
been Extended?
As presented in the IFM (Denne and Cleland-Huang,
2003), each one of the cash flow elements should
be estimated using the cost and revenues projections
made by the development team and the customer,
respectively.
The literature has stated that that IT projects are
provenly high-risk investments and have high rate of
failure (Whittaker, 1999; Biehl, 2007; Westerman and
Hunter, 2007). When the proposed method considers
the worst (Min), the most likely (ML) and the best
case (Max) scenarios to each cash flow element, it
automatically includes the inherent uncertainty from
real world circumstances, where there is an associated
risk to each cost and revenue projection.
Consequently, the method transforms each one of
the cash flow elements into random variables (Kotz
and van Dorp, 2004), which are presented as a
triangular probability density functions that are to
be used to balance between risks and benefits of a
given module’s cash flow stream (Hubbard, 2007;
Schniederjans et al., 2004).
B. How to define the Most Suitable Decision making
Criterion?
After the resampling, there are some scenarios that are
possible to be presented. Depending on the organiza-
tion’s risk-tolerance policy, a different method is to be
used in their decision making process. These methods
and corresponding situations where they shall be
applied are presented below:
1. Probabilistic Dominance – it is a compelling
reason for choosing one sequencing option over
another, despite of being a risk-taken or risk-
averse organization.
2. Maximin Principle – comparing the worst case
of alternatives, this is a pessimistic decision
making and it is usually used by extremely conser-
vative organizations, which are willing to choose
the alternative that would have the lowest impact
in case of going wrong.
3. Maximax Principle – comparing just the best
outcomes, this method should be considered
by organizations that are risk-seeking, with the
objective of having the highest possible return on
investment.
4. Laplace Principle – whenever all the attainable
outcomes have the same probability to occur, the
comparison of alternatives using their mean is
a reasonable approach for risk-neutral decision
makers.
5. Hurwicz Principle – balancing between methods
that are either too optimistic or too pessimistic,
it should be considered by risk-neutral organiza-
tions that are able to define the index of optimism
in which this principle relies on.
6. Savage Principle – considered a risk-averse
method, its main objective is to minimize the risks
and choose the alternative that yields the lowest
variance, which is an alternative for the Maximin
principle for conservative decision makers.
7. Aspiration Level – it is often the case where an
organization defines a result that is very important
to obtain. To maximize the probability of having
an actual result equal to or higher than the desired
one, this method shall be used.
C. How do Organizations benefit from the Method?
As technology investments are inherently risky and
are becoming the dominant part of many organiza-
tions’ expenditures, IT projects are becoming even
more complex and difficult to undertake. Therefore,
the use of a comprehensive investment management
tool – to effectively allocate the resources and priori-
tize IT projects within a portfolio – is a “must have”.
By decomposing IT projects into self-contained
software units that can be managed as “miniprojects”,
analyzing their risk-return information, and provid-
ing insights into the existing sequencing options, the
proposed method unveils the power of combining
together the IFM (Denne and Cleland-Huang, 2003),
Decision Theory (Holloway, 1979) and Principles of
Choice (Lang and Merino, 1993; White, 2006) to
maximize the investments’ efficiency. The benefits of
this approach to PPM are numerous:
• Enable portfolios comprised of large and
complex IT projects to be managed with a
relatively smaller initial investment,
• Identify units that are common to different
projects, remove duplication and improve quality,
• Bring financial discipline into the IT portfolio
management,
• Identify risks and investment prioritization
options,
• Identify the most suitable investment option to
each organization,
• Maximize the efficiency of investments in portfo-
lios of IT projects,
• Demand for shorter investment periods and
payback time are addressed,
A METHOD FOR PORTFOLIO MANAGEMENT AND PRIORITIZATION - An Incremental Funding Method Approach
31

• Favor faster time-to-market of the portfolio, and
• Position the IT portfolio management as a value
creation activity in which business analysis is an
integral part of it.
5 CONCLUSIONS
To the best of our knowledge, this work is the first
to create a portfolio management method based upon
the Incremental Funding Method (IFM).
The Incremental Funding Portfolio Management
Method (IFPMM) extends the IFM to decom-
pose software projects into self-contained software
units, including the inherent uncertainty of software
development process into their cash flow streams
and considering the whole portfolio of IT projects,
rather than making investments decisions in isolation.
Besides, it uses decision theory together with
principles of choice to analyze each unit risk-
return information and prioritize their implementa-
tion, defining the best sequencing option considering
the organization’s risk tolerance.
The IFPMM provides crucial insights into the
business value of IT portfolios, facilitating the
decision making process and considering the
organization approach to business. Besides, it also
provides a technique to assure that investment
choices are always as efficient as possible, permit-
ting portfolios comprised of large and complex IT
projects to be managed with a relatively smaller
initial investment, demanding for shorter investment
periods, and also providing shorter payback times
and faster time-to-market.
REFERENCES
Abdellaoui, M. and Hey, J. D. (2008). Advances in Decision
Making Under Risk and Uncertainty. Springer, New
York, NY, USA.
Alencar, A. J., Schmitz, E. A., and de Abreu, E. P. (2008).
Maximizing the business value of software projects:
A branch & bound approach. In 10th International
Conference on Enterprise Information Systems, vol-
ume ISAS-2, pages 162–169, Barcelona, Spain. In-
stitute for Systems and Technologies of Information,
Control and Communication.
Barbosa, B. P., Schmitz, E. A., and Alencar, A. J. (2008).
The case for managerial flexibility in mmf-based
software development projects. In Workshop on
Business-driven IT Management, 2008. BDIM 2008.
3rd IEEE/IFIP International, pages 114–115, Sal-
vador, Bahia, Brazil. IEEE.
Biehl, M. (2007). Success factors for implementing global
information systems. Commun. ACM, 50(1):52–58.
Bingi, P., Sharma, M. K., and Godla, J. K. (1999). Critical
issues affecting an erp implementation. Information
System Management, 16(3):7–14.
Chang, C. K., Cleland-Haung, J., Hua, S., and Kuntzmann-
Combelles, A. (2001). Function-class decomposition:
A hybrid software engineering method. Computer,
34:87–93.
Chen, I. L. (2001). Planning for erp systems: analysis and
future trend. Business Process Management Journal,
7(5):374–386.
Chen, T., Zhang, J., Huang, W. W., and Zeng, Y. (2007).
Evaluating information technology investment under
multiple sources of risks. In the Proceedings of
the International Conference on Wireless Communi-
cations, Networking and Mobile Computing, pages
6111–6114, White Plains, NY, USA. IEEE Press.
Denne, M. and Cleland-Huang, J. (2003). Software by Num-
bers: Low-Risk, High-Return Development. Prentice
Hall.
Denne, M. and Cleland-Huang, J. (2004). The incremental
funding method: Data-driven software development.
IEEE Software, 21(3):39–47.
Denne, M. and Cleland-Huang, J. (2005). Financially in-
formed requirements prioritization. In Proceedings
of the 27th international conference on Software En-
gineering, pages 710–711, St Louis, Missouri, USA.
ACM New York, NY, USA.
Holloway, C. A. (1979). Decision Making Under Uncer-
tainty: Models and Choices. Prentice Hall, Engle-
wood Cliffs, NJ.
Hubbard, D. W. (2007). How to Measure Anything: Finding
the Value of ”Intangibles” in Business. John Willey &
Sons, Inc, Hoboken, NJ, USA.
Jeffery, M. and Leliveld, I. (2004). Best practices in it port-
folio management. MIT Sloan Management Review,
45(3):41–49.
Kotz, S. and van Dorp, J. R. (2004). Beyond Beta: Other
Continuous Families Of Distributions With Bounded
Support And Applications. World Scientific Publish-
ing Co., Hackensack, NJ.
Lang, H. J. and Merino, D. N. (1993). The selection process
for capital projects. Wiley-Interscience.
Markowitz, H. (1952). Portfolio slection. The Journal of
Finance, 7(1):77–91.
McFarlan, F. W. (1981). Portfolio approach to information
systems. Harvard Business Review, pages 142–151.
Pressman, R. S. (2009). Software Engineering: A Practi-
tioner’s Approach. MacGraw-Hill, 7th edition.
Reyck, B. D., Grushka-Cockayne, Y., Lockett, M.,
Calderini, S. R., Moura, M., and Sloper, A. (2005).
The impact of project portfolio management on infor-
mation technology projects. International Journal of
Project Management, 23(5):534–537.
Robert, C. P. and Casella, G. (2005). Monte Carlo Statisti-
cal Methods. Springer.
ICEIS 2010 - 12th International Conference on Enterprise Information Systems
32

S. Dewan, C. Shi, V. G. (2007). Investigating the risk-
return relationship of information technology invest-
ment: Firm-level empirical analysis. Management
Science, 53(12):1829–1842.
Schmitz, E. A., Alencar, A. J., and de Azevedo, C. M.
(2008). A method for defining the implementation or-
der of software projects under uncertainty. In SAC ’08:
Proceedings of the 2008 ACM symposium on Applied
computing, pages 844–845, Fortaleza, Ceara, Brazil.
ACM.
Schniederjans, M. J., Hamaker, J. L., and Schniederjans,
A. M. (2004). Information Technology Investment:
Decision-Making Methodology, volume 1. World Sci-
entific Publishing Co., River Edge, NJ.
Silvius, A. J. G. (2008). The business value of it a concep-
tual model for selecting valuation method. Communi-
cations of the IIMA, 8(3):57–66.
Somers, T. M. and Nelson, K. G. (2003). The impact
of strategy and integration mechanisms on enterprise
system value: empirical evidence from manufactur-
ing firms. European Journal of Operational Research,
146(2):315–338.
Westerman, G. and Hunter, R. (2007). IT Risk: turning
business threats into competitive advantages. Harvard
Business School Press, Boston, MA, USA.
White, D. J. (2006). Decision Theory. Aldine Transaction.
Whittaker, B. (1999). What went wrong? unsuccessful in-
formation technology projects. Information Manage-
ment & Computer Security, 7(1):23–30.
A METHOD FOR PORTFOLIO MANAGEMENT AND PRIORITIZATION - An Incremental Funding Method Approach
33
