
A VIDEO SURVEILLANCE MODEL INTEGRATION IN SMALL
AND MEDIUM ENTERPRISES
Dan Benta and Stefan Ioan Niţchi
Faculty of Economics and Business Administration, Babeş Bolyai University, Teodor Mihali 58-60, Cluj Napoca, Romania
Keywords: Video Surveillance, Wireless, Standards, Model, Integration, Small and Medium Enterprises.
Abstract: Rapid evolution of the Internet inevitably leads toward adapting to new technologies. To survive in the
increasingly fierce competition, companies must keep pace with new trends and developments. Software
solutions should be adapted to not change the structure of the company. A common case is the classical
surveillance and monitoring system that switch from analogue to digital and from a system accessed from
inside the company to a system accessed via IP. Wireless technologies are used on a large scale, are flexible,
cheap, and accessible and without wiring systems or elements that disturb. The evolution of wireless
communications was done in close dependence with the development of communication networks. A video
surveillance and monitoring system (VSaMS) is a good tool that offers secure targets or premises or to
monitor the activity of the perimeter. Access to the system will allow real time monitoring, recording and
accessing records. Using a standard depends on the location and the geographical area and equipment. The
aim of this paper is to highlight existing standards and solution and to propose a model for a VSaMS. Also,
experimental results are presented.
1 INTRODUCTION
Evolution and diversification of the companies’
activity led them to adapt to new web technologies.
These inevitably force the companies to adapt and to
find solutions to allow communication and progress.
A video surveillance and monitoring system
accessed via IP allows to view live images or to
access the records without the person to move from
one place to another.
In a complex work Kruegle (2007) concludes
that there has been an evolution of security
integration from guard, to guard and security system.
This evolution has changed from a “hands on”
security system using the guard as the primary
source for security to one with a complex and
sophisticated electronic system that removes much
of the decision-making from the guard. Much of the
human decision-making has been transferred to and
is accomplished by the security subsystems.
The security system integration consists of layers
of integration. If the security system is all at one site,
it is easy to connect the various security subsystems
via cable to the control console. This transmission
can be accomplished using copper wire (coaxial,
twisted-pair, multi-conductor), fiber optic or in
special cases wireless transmission. If a site is
remote or there are multi-sites, the communication
link is very important. If the transmission occurs
outside the boundaries of the organization, it is
important that the network outside the facility is
secure and that proper protection is provided so that
no outsiders can tap into the communications. To
obtain this, protection usually takes some form of
signal scrambling or encryption (Kruegle, 2007).
A lot of authors agree that video analysis and
video surveillance are active areas of research. The
key technologies are video-based detection and
tracking, video-based person identification, and
large scale surveillance systems. A significant
percentage of basic technologies for video-based
detection and tracking were developed under a U.S.
government-funded program called Video
Surveillance and Monitoring (Tian, Brown,
Hampapur, Lu, Senior and Shu, 2008).
We propose a VSaMS integration for small and
medium enterprises (SMEs). The financial crisis has
turned the interest of companies to a good cost
management. Implementation of this system comes
to support SMEs to survive in the competitive
environment.
In the second section of this paper, we present
5
Benta D. and Nitchi S. (2010).
A VIDEO SURVEILLANCE MODEL INTEGRATION IN SMALL AND MEDIUM ENTERPRISES.
In Proceedings of the 5th International Conference on Software and Data Technologies, pages 5-9
DOI: 10.5220/0002930800050009
Copyright
c
SciTePress
the system modules and functionalities; in the third
section we present the model standards and
implementation. The fourth section is for system
analyzes and system benefits. Finally, we present
our conclusions.
2 THE MODEL MODULES
A video surveillance and monitoring system must
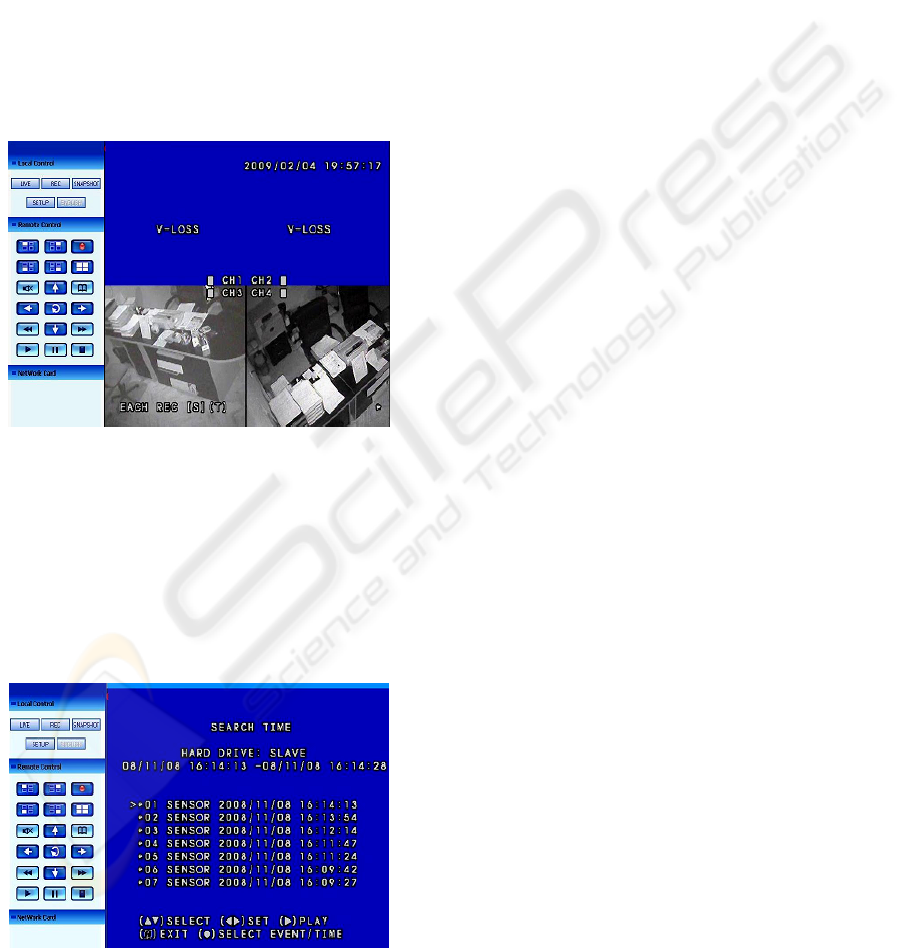
contain some elementary modules as: live view
module (Figure 1), recording schedule, records
access (Figure 2), motion detect module, real time
snapshot and recording module, system log and
users management.
Figure 1: Live view module, a system using a DVD and IR
cameras.
The Internet connection is an essential factor in
terms of video and audio transmission via IP.
Internet connection is very important in terms of
data transitions. In the case of video surveillance and
monitoring via IP it becomes an essential factor. We
can also register on our personal computer. It is very
important that the time to be listed on records.
Figure 2: Playback system module, a system using a DVD
and IR cameras.
Other options are also active in the system.
Another important element of the system is that the
system can be connected to an alarm sensor.
The key to a successful security plan is to choose
the right equipment and service company, one that is
customer oriented and knowledgeable about reliable,
technologically superior products that satisfy the
customer needs (Kruegle, 2007).
The application and integration of video into
safety and security systems has come of age as a
reliable, cost-effective means for assessing and
responding to terrorist attacks and other life-
threatening situations. Video is an effective means
for deterring crimes and protecting assets and for
apprehending and prosecuting offenders.
The integration of video, intrusion-detection
alarms, access control, and security guards increases
the overall security asset protection and employee
safety at a facility. If the security plan calls for a
simple system with potential for later expansion the
equipment should be modular and ready to accept
new technology as it becomes available. Many
larger manufacturers of security equipment
anticipate this integration and expansion requirement
and design their products accordingly.
Integration of security technology is a worldwide
trend providing increased security benefits at a lower
cost. Security integration projects often involve
single or multiple sites. Security dealers, integrators,
consultants, architect, and engineers, etc. must
understand the technology required to effectively
integrate security subsystems. There are essentially
two levels of integration function: (1) security
system and (2) security system plus building control
system (fire, HVAC, etc.). The highest level of
integration combines the security system with
building control: the fire, heating, ventilation, air-
conditioning (HVAC), lighting, and all facility
communication functions (Kruegle, 2007).
Wireless networks have an increasing role and
represents a variant which should not be neglected
when you wish to achieve a network. Wireless
equipment have been developed rapidly and presents
viable solutions for interconnecting computers and
other equipment to transfer data or to transfer video
and audio, from the classical data transfer and files
transfer to interactive and real-time applications via
IP. The Internet was not designed for transmission of
video and audio in real time so you will need to take
into account several factors and when it comes to a
video surveillance and monitoring system (VSaMS),
the Internet connection is very important. When
network performances are lower and the network
operates under certain parameters, the use of such
ICSOFT 2010 - 5th International Conference on Software and Data Technologies
6

applications via IP is impossible. Unlike the transfer
of files, transmission of video and audio is much
more demanding.
Resources assurance is very important and the
quality of service must be optimal and the network
must work properly. Resource assurance is very
important and a main factor in many applications via
IP. Optimal allocation of resources to ensure
efficient functioning of an application via IP has
become a difficult challenge.
3 THE MODEL STANDARDS
AND INTEGRATION
We think that standard IEEE 802.11g standard
(IEEE, 2010), with speeds of 54Mbps, is sufficient
and fully meet the requirements of users of small
networks, networks between two or more neighbors
or networks in small companies. Rapid evolution of
telecommunications will require the WiMAX
standard, but the jump will be slower compared with
the jump in technology from 802.11b standard to
802.11g standard. Devices with both standards
(802.11b and 802.11g) are widely spread in the
market.
Network performance is given by the slowest
component of the network. For this reason is
preferred to use wireless components of the same
manufacturer and with the same standard, preferably
802.11g.
During the time, video standards have been
improved to adapt them to new needs and demands
of the market. In the video market there are SECAM
(SECAM, 2010), NTSC (NTSC, 2010) and PAL
(PAL, 2010) standards.
A number of authors agree that the rapid
development of sensors, network communications
and computational systems forces the researchers
working in the field of advanced surveillance
systems to design and develop innovative solutions
for building “intelligent” systems able to support
human operators in the task of making complex
decisions (Micheloni, Lestuzzi and Foresti, 2008).
There are a lot of ways to choose the best
VSaMS. Standards are very important because
standards give the network and the system
performance. It is very difficult to say that a system
is better than other; it depends of a lot of factors like
Internet connection, equipment, standards, locations,
resources.
The presented model offers a real solution for
any company at an accessible cost. For Infrared (IR)
Cameras is used PAL Standard and for wireless
network is recommended 802.11 g Standard (Figure
3).
IR Cameras are connected to a Capture Card
mounted in a computer. IR Cameras are connected
using BNC cable. The cameras can be connected
using wireless technology but it is not recommended
for large areas that’s why BNC cable is used. There
are used 12V current transformer and metal
catchment systems that allows cameras to monitor
the optimal angle of the perimeter.
Figure 3: Standards in a video surveillance and monitoring
system (VSaMS) using a computer.
A main application for VSaMS is installed on
computer and VSaMS is configured. The Computer
is wireless connected to a wireless router using a
wireless LAN Card with 802.11g Standard. The
router is connected to the Internet and configured to
allow via IP access to VSaMS.
The VSaMS can be accessed via IP for real time
monitoring or to access records. To access the
VSaMS can be used a computer connected to the
wireless router or connected directly to the Internet,
can be used a mobile phone with WLAN using
802.11 b/g standard connected to the wireless router
or connected directly to the Internet or can be used a
notebook connected wireless with 802.11 b/g
standard or directly to the Internet.
The applications are diverse and can be adapted
to any company. Motion detect module can start
recording only when detects movement or activity,
otherwise does not use storage space for records.
Via IP access allows us to view live images or
access recordings. To grant access to view live
images or to access records we must log into the
system using a username and a password. The
username and the password are saved in system
configuration when we install the main application.
A VIDEO SURVEILLANCE MODEL INTEGRATION IN SMALL AND MEDIUM ENTERPRISES
7

The IP and the port of the system/camera are set up
in camera configuration.
The proposed model represents a solution for any
company that wants to monitor or supervise the
work of a perimeter. Costs are affordable and allow
existing technologies and refining a model for such a
system.
Video technology has evolved rapidly from
analog to digital. New technologies and equipment
allow storing data and then to access them by adding
a DVR and a HDD (Figure 4). This system allows
quick access to records and an easy way to use
equipment, the system is limited only by the HDD
capacity. If you do not want to store data for a long
term you may enable to overwrite the HDD.
Figure 4: Video surveillance/monitoring system using
DVD.
4 THE MODEL BENEFITS AND
ANALYZES
Continuing our work, wireless technology and
current standards were used to develop an optimal
system. The system was implemented in a few
companies from different fields like: sales, IT,
consulting, accounting, production (Benta, 2009).
From our analyses, the system was a great tool
for property and employees safety, for the manager
satisfaction and also for monthly productivity per
employee.
First of all, the system offers an increased
security plan. The system can be connected to an
alarm sensor and at a phone line. The access via IP
and from a cell phone is useful for company
managers. Also, the employees are concerned to
work and not to waste time with other activities and
the monthly productivity is increased (Figure 5).
Some authors conclude that a video system
cannot be easily applied in remote areas with
difficult access. The main problems are associated
with (1) providing a long-lasting source of energy,
and (2) frequent maintenance of the system (e.g.
having to change videotapes). Although electric
power can be supplied for several days by 12-V car
batteries, changing the videotapes in a non-stop
running system is a time- and labour-intensive
undertaking (Pechacek, 2005).
Figure 5: Video surveillance/monitoring system benefits.
One of the biggest challenges of developing a
commercial video surveillance system according to
Haering, Venetianer and Lipton (2008) is that the
system, once deployed, has to operate robustly 24/7
in a completely uncontrolled environment, in a wide
range of scenarios. Casaca, Silva, Grilo, Nunes,
Presutto and Rebelo (2007) showed that a VSaMS is
a great solution to resolve airport problems because
airport congestion is also becoming an increasing
problem for ground movements.
We also agree that a real problem for via IP
access is the bandwidth because the Internet was not
developed for video live streaming.
5 CONCLUSIONS
Choosing the best choices for a VSaMS depends on
the location and area where it will be mounted and
also from the technology on the market. We suggest
the use of compatible equipment that does not affect
the proper functioning of the system and its
performance.
The performance of a system is given by the
weakest component of the system. For the proper
ICSOFT 2010 - 5th International Conference on Software and Data Technologies
8

functioning of such a system is recommended to
meet the standards and requirements of the system.
Wireless networks are easy to achieve compared
with wired networks, but require greater attention in
terms of transmission and security. Any security and
any network system are not entirely sure. Any
system connected to the Internet can become a target
for a potential attack.
A VSaMS is a great way to monitor an area or
activity in an area in real time or to view records
accessing the system.
Standards are varied so it is recommended to
choose standard and the standards that will adapt
best to the area concerned and to give maximum
performance of the system.
Optimal choice depends on many factors,
depends on financial factors, geographical area, the
existing technologies, customer needs, the impact of
the system. No need to use an expensive system that
is not used to its maximum performance.
The system must match the customer needs and
demands and provide more in terms of safety and
security. Access via IP allows viewing of live
images so we do not have to be present in that place,
travel costs are eliminated.
Also, the Internet connection is very important
because the connection will guarantee proper
functioning of the system and via IP access to the
system.
ACKNOWLEDGEMENTS
This work was supported by Romanian National
Authority for Scientific Research under the grant no.
PN2 92-100/2008 SICOMAP and Investing in
people! PhD scholarship, Project co-financed by the
SECTORAL OPERATIONAL PROGRAMME
HUMAN RESOURCES DEVELOPMENT 2007 -
2013, Priority Axis 1 "Education and training in
support for growth and development of a knowledge
based society", Key area of intervention 1.5:
Doctoral and post-doctoral programmes in support
of research, Contract POSDRU 6/1.5/S/3 –
„DOCTORAL STUDIES: THROUGH SCIENCE
TOWARDS SOCIETY", Babeş-Bolyai University,
Cluj-Napoca, Romania
REFERENCES
Benta, D. (2009). WiFi technologies for video
surveillance, Knowledge Engineering: Principles And
Techniques Proceedings of the International
Conference on Knowledge Engineering, Principles and
Techniques, Volume III, Studia Universitatis Babes-
Bolyai, Cluj-Napoca: Cluj University Press.
Casaca, A., Silva, T., Grilo, A., Nunes, M., Presutto, F.
and Rebelo. I. (2007). The use of wireless networks for
the surveillance and control of cooperative vehicles in
an airport, Telecommun Syst 36: 141–151, Springer
Science+Business Media.
Haering, N., Venetianer, P. L. and Lipton, A. (2008). The
evolution of video surveillance: an overview, Machine
Vision and Applications 19:279–290, Springer-Verlag
Kruegle, H. (2007). CCTV surveillance: analog and
digital video practices and technology, Elsevier Inc.,
ISBN-13: 978-0-7506-7768-4.
Micheloni, C., Lestuzzi, M. and Foresti, G. L. (2008).
Adaptive video communication for an intelligent
distributed system: Tuning sensors parameters for
surveillance purposes, Machine Vision and
Applications 19:359–373, Springer-Verlag.
Pechacek, P. (2005). Use of non-stop video surveillance to
monitor breeding activity of primary cavity nesters in
remote areas, Acta Ethol 8: 1–4, Springer-Verlag and
ISPA.
Tian, Y., Brown, L., Hampapur, A., Lu, M., Senior, A. and
Shu, F. (2008). IBM smart surveillance system (S3):
event based video surveillance system with an open
and extensible framework, Machine Vision and
Applications 19:315–327, Springer-Verlag.
IEEE (2010), Retrieved January 15, 2010, from
http://standards.ieee.org/reading/ieee/interp/802.11g-
2003.html.
NTSC (2010), Retrieved January 15, 2010, from
http://ro.wikipedia.org/wiki/NTSC.
PAL (2010), Retrieved January 15, 2010, from
http://ro.wikipedia.org/wiki/PAL.
SECAM (2010), Retrieved January 15, 2010, from
http://ro.wikipedia.org/wiki/SECAM.
A VIDEO SURVEILLANCE MODEL INTEGRATION IN SMALL AND MEDIUM ENTERPRISES
9
