
AN IDENTITY BASED RING SIGNCRYPTION SCHEME WITH
PUBLIC VERIFIABILITY
S. Sharmila Deva Selvi, S. Sree Vivek, Sakhi S. Anand and C. Pandu Rangan
Theoretical Computer Science Lab, Indian Institute of Technology, 600036, Chennai, India
Keywords:
Ring signcryption, Adaptive chosen ciphertext attack, Bilinear pairing, Random oracle model, Public verifia-
bility.
Abstract:
Signcryption is a cryptographic primitive which offers authentication and confidentiality simultaneously with
a cost lower than signing and encrypting the message independently. Ring signcryption enables a user to
anonymously signcrypt a message on behalf of a set of users including himself. Thus a ring signcrypted
message has anonymity in addition to authentication and confidentiality. Ring signcryption schemes have no
centralized coordination: any user can choose a ring of users, that includes himself and signcrypt any message
without any assistance from the other group members. Ring Signcryption is useful for leaking trustworthy
secrets in an anonymous, authenticated and confidential way.
To the best of our knowledge, ten identity based ring signcryption schemes are reported in the literature.
Three of them were proved to be insecure in (Li et al., 2008a), (Zhang et al., 2009a) and (Vivek et al., 2009).
Four of them were proved to be insecure in (Selvi et al., 2009). In this paper, we show that one among the
remaining three schemes, (Zhang et al., 2009b) is not secure against confidentiality, existential unforgeability
and anonymity attacks. We propose a new anonymous ring signcryption scheme which is an extension to
(Selvi et al., 2009) and give formal security proofs for our system in the random oracle model. Our scheme is
publicly verifiable which none of the existing unbroken schemes can achieve.
1 INTRODUCTION
Let us consider a scenario, where a member of the
cabinet wants to leak a very important and juicy in-
formation, regarding the president of the nation to the
press. He has to leak the secret in an anonymous way,
else he will be black spotted in the cabinet. The press
will not accept the information unless it is authenti-
cated by one of the members of the cabinet. Here,
if the information is so sensitive and should not be
leaked until the authorities in the press receives it,
we should have confidential transmission of informa-
tion. Thus, we require anonymity to safeguard the
cabinet member who sends the information, authen-
tication for the authorities in the press to believe the
information and confidentiality until the information
reaches the hands of the right person in the press. All
the three properties are together achieved by a single
primitive called “Ring Signcryption”. The first iden-
tity based ring signcryption scheme was proposed by
Huang et al.(Huang et al., 2005). Subsequently, sev-
eral schemes appeared in the literature((Zhang et al.,
2008), (Li et al., 2008b), (Li et al., 2008a), (Yu et al.,
2008), (Zhu et al., 2008), (Zhun and Zhang, 2008),
(Huang et al., 2005), (Selvi et al., 2009), (Zhang
et al., 2009a) and (Zhang et al., 2009b)). However,
the weaknesses of (Zhang et al., 2008), (Li et al.,
2008b), (Zhang et al., 2009a) were shown in (Li et al.,
2008a), (Vivek et al., 2009) and (Zhang et al., 2009b)
respectively. The insecurities of the schemes (Li et al.,
2008a), (Yu et al., 2008), (Zhu et al., 2008) and (Zhun
and Zhang, 2008) were shown in (Selvi et al., 2009).
In this paper, we show that (Zhang et al., 2009b)
is insecure against confidentiality, unforgeability and
anonymity attacks.
Typically, signcryption σ is generated by a sender
to a specific receiver and only the receiver can ver-
ify the validity of σ and recover the message from
σ. However, in some practical scenarios, verification
may have to be carried out by an entity other than the
receiver but the verifier should not obtain the mes-
sage. We call this property as public verifiability. For
instance, firewalls are one of the most useful and ver-
satile tools available for securing a LAN and other
applications such as constructing secure private vir-
tual networks. They are typically operated as a fil-
362
Sharmila Deva Selvi S., Sree Vivek S., S. Anand S. and Pandu Rangan C. (2010).
AN IDENTITY BASED RING SIGNCRYPTION SCHEME WITH PUBLIC VERIFIABILITY.
In Proceedings of the International Conference on Security and Cryptography, pages 362-371
DOI: 10.5220/0002981203620371
Copyright
c
SciTePress

tering gateway at the LAN-WAN interface, usually a
router. A signcryption scheme used in a LAN should
satisfy the public verifiability property. This requires
that any third party should be able to verify the origin
of the signcryption without knowledgeof the message
and without getting any additional information from
the intended recipient. Even, in the scenario men-
tioned above, a press authority may receive several
ring signed messages and it is only appropriate that
the filtering gateway is equipped with public verify-
ing capabilities of the ring signcryptions.
2 PRELIMINARIES
2.1 Bilinear Pairing
Let G
1
be an additive cyclic group generated by P,
with prime order q, and G
2
be a multiplicative cyclic
group of the same order q. A bilinear pairing is a map
ˆe : G
1
× G
1
→ G
2
with the following properties.
• Bilinearity. For all P,Q,R ∈
R
G
1
and a,b ∈
R
Z
∗
q
– ˆe(P+ Q, R) = ˆe(P,R)ˆe(Q,R)
– ˆe(P,Q+ R) = ˆe(P,Q) ˆe(P, R)
– ˆe(aP,bQ) = ˆe(P, Q)
ab
• Non-degeneracy. There exist P,Q ∈ G
1
such that
ˆe(P,Q) 6= I
G
2
, where I
G
2
is the identity element of
G
2
.
• Computability. There exists an efficient algo-
rithm to compute ˆe(P,Q) for all P,Q ∈ G
1
.
2.2 Computational Bilinear
Diffie-Hellman Problem (CBDHP)
Given (P, aP,bP,cP) ∈ G
4
1
, for unknown a,b,c ∈ Z
∗
q
,
the CBDH problem in G
1
is to compute ˆe(P, P)
abc
∈
G
2
.
The advantage of any probabilistic polynomial
time algorithm A in solving the CBDH problem in
G
1
is defined as
Adv
CBDH
A
= Pr
h
A (P,aP,bP,cP) = ˆe(P, P)
abc
|a,b,c ∈ Z
∗
q
i
The CBDH Assumption is that, for any proba-
bilistic polynomial time algorithm A , the advantage
Adv
CBDH
A
is negligibly small.
2.3 Computation Diffie-Hellman
Problem (CDHP)
Given (P, aP,bP) ∈ G
3
1
, for unknown a,b ∈ Z
∗
q
, the
CDH problem in G
1
is to compute abP.
The advantage of any probabilistic polynomial time
algorithm A in solving the CDH problem in G
1
is de-
fined as
Adv
CDH
A
= Pr
A (P,aP, bP) = abP | a,b ∈ Z
∗
q
The CDH Assumption is that, for any probabilistic
polynomial time algorithm A , the advantage Adv
CDH
A
is negligibly small.
3 IDENTITY BASED RING
SIGNCRYPTION
3.1 Framework
A generic identity based ring signcryption scheme
consists of the following four algorithms.
Setup(κ). Given a security parameter κ, the private
key generator (PKG) generates the systems public
parameters params and the corresponding master
private key msk that is kept secret by PKG.
Extract(ID
i
). Given a user identity ID
i
by user U
i
,
the PKG computes the corresponding private key
D
i
and sends D
i
to ID
i
through a secure channel.
Signcrypt(m, L , ID
S
, D
S
, ID
R
). This algorithm
takes a message m ∈ M , an ad-hoc group of ring
members L = {U
1
,U
2
,...U
n
} with identities
{ID
1
, . . . , ID
n
}, the sender identity ID
S
, the
sender private key D
S
and the receiver identity
ID
R
as input and outputs the ring signcryption
C. This algorithm is executed by the sender with
identity ID
S
∈ L . ID
R
may or may not be in L .
Unsigncrypt(C, L , ID
R
, D
R
). This algorithm takes
the ring signcryption C, the ring members L =
{U
1
,U
2
,...U
n
} and the private key D
R
of the re-
ceiver U
R
with identity ID
R
as input and produces
the plaintext m, if C is a valid ring signcryption of
m from the ring L to ID
R
or “Invalid”, if C is an
invalid ring signcryption.
3.2 Security Notion
The formal security definition of signcryption was
given by Baek et al.(Baek et al., 2002). The security
of ID-based signcryption scheme was first defined
by Malone-Lee (Malone-lee, 2002) that satisfies in-
distinguishability against adaptive chosen ciphertext
attacks and unforgeability against adaptive chosen
message attacks.
Definition 1 (Confidentiality). An identity based
ring signcryption (IRSC) is indistinguishable against
AN IDENTITY BASED RING SIGNCRYPTION SCHEME WITH PUBLIC VERIFIABILITY
363

adaptive chosen ciphertext attacks (IND-IRSC-
CCA2) if there exists no polynomially bounded adver-
sary having non-negligibleadvantagein the following
game:
1. Setup Phase. The challenger C runs the Setup
algorithm with the security parameter κ as input
and sends the system parameters params to the
adversary A and keeps the master private key msk
secret.
2. Phase-I. A performs polynomially bounded num-
ber of queries to the oracles provided to A by C .
The description of the queries in the phase-I are
listed below:
Key Extraction Query. A produces an identity
ID
i
corresponding to U
i
and receives the pri-
vate key D
i
corresponding to ID
i
.
Signcryption Query(m, L , ID
S
, ID
R
). A pro-
duces a message m, a sender group L =
{U
i
}
(i=1 to n)
, a sender identity ID
S
and a
receiver identity ID
R
to the challenger C . Then
C signcrypts m from ID
S
to ID
R
with D
S
and
sends the result to A .
Unsigncryption Query(C, L , ID
R
). A produces
the sender group L = {U
i,(i=1 to n)
, a receiver
identity ID
R
, and a ring signcryption C. C gen-
erates the private key D
R
by querying the Key
Extraction oracle. C unsigncrypts C using D
R
and returns m if C is a valid ring signcryption
from L to ID
R
, else outputs “Invalid”.
A queries the various oracles adaptively, i.e. the
current oracle requests may depend on the re-
sponse to the previous oracle queries.
3. Challenge. A chooses two plaintexts {m
0
,
m
1
} ∈ M of equal length, a set of n users L
∗
=
{U
i
∗
}
(i=1 to n)
and a receiver identity ID
R
∗
and
sends them to C . A should not have queried the
private key corresponding to ID
R
∗
in the Phase-I.
C now chooses a bit δ ∈
R
{0, 1} and computes the
challenge ring signcryption C
∗
of m
δ
and sends
C
∗
to A .
4. Phase-II. A performs polynomially bounded
number of requests just like the Phase-1, with the
restrictions that A cannot make Key Extraction
query on ID
R
∗
and should not query for unsign-
cryption query on C
∗
. It should be noted that ID
R
∗
can be included as a ring member in L
∗
, but A
cannot query the private key of ID
R
∗
.
5. Guess. Finally, A produces a bit δ
′
and wins the
game if δ
′
= δ. The success probability is defined
by:
Succ
A
IND−IRSC−CCA2
(κ) =
1
2
+ ε.
Here, ε is called the advantage for the adversary
in the above game.
Remark. The security model described here deals
with insider security, since the adversary is as-
sumed to have access to the private key of a user
who belong to to ring U
∗
chosen for Challenge phase.
Definition 2 (Unforgeability). An identity based
ring signcryption scheme (IRSC) is said to be exis-
tentially unforgeable against adaptive chosen mes-
sage attack (EUF-IRSC-CMA), if no polynomially
bounded adversary has non-negligible advantage in
the following game:
1. Setup Phase. The challenger C runs the Setup al-
gorithm with the security parameter κ to generate
the system parameters params and the master se-
cret key msk. C gives params to the adversary A
and keeps msk secret.
2. Training Phase. A performs polynomially
bounded number of queries as described in
Phase-I of Definition 1.
3. Existential Forgery. Finally, A produces a new
triple (U
∗
, ID
∗
R
, C
∗
) (i.e. this triple that was not
produced as output by the signcryption oracle),
where the private keys of the users in the ring L
∗
were not queried during the training phase. A
wins the game if the result of the Unsigncryption
(L
∗
, ID
∗
R
, C
∗
) is not “Invalid” in other words, C
∗
is a valid signcryption of some message m ∈ M .
It should be noted that ID
∗
R
can also be member
of the ring L and in that case, the private key of
ID
∗
R
should not be queried by A . However, if ID
∗
R
/∈ L
∗
, A may query the private key of ID
∗
R
.
Remark. The security model described here deals
with insider security since the adversary is assumed
to have access to the private key of the receiver
of a signcryption used for generation of C
∗
. This
means that the unforgeability is preserved even if a
receiver
′
s private key is compromised.
Definition 3 (Anonymity). An ID-based ring sign-
cryption scheme is unconditionally anonymous if for
any group of n members(n ≥ 3) with identities L =
ID
i
(1 ≤ i ≤ n), any message m and Ciphertext C,
any adversary cannot identify the actual signcrypter
with probability better than a random guess.
That is, A outputs the identity of actual signcrypter
with probability 1/n if he is not the member of L ,
and with probability 1/(n - 1) if he is the member of L .
Definition 4 (Public Verifiability). An ID-based ring
signcryption scheme is publicly verifiable if given a
SECRYPT 2010 - International Conference on Security and Cryptography
364

ciphertext C, ring L , and receiver R, anyone can ver-
ify that C is a valid signcryption by some member of
the ring L to the specified receiver R, without know-
ing the receiver
′
s private key.
4 ATTACK ON SIGNCRYPTION
SCHEME BY ZHANG ET AL.
(Zhang et al., 2009b)
In this section, we review the scheme in (Zhang
et al., 2009b) and demonstrate various attacks on the
scheme. We propose attacks on confidentiality, un-
forgeability and anonymity of (Zhang et al., 2009b).
4.1 Overview of the Scheme in (Zhang
et al., 2009b)
Here, we review the ring signcryption scheme pro-
posed in (Zhang et al., 2009b), which was proposed
as an improvement to the scheme in (Zhang et al.,
2009a). They claim that the scheme remedies the
weaknesses of J.H Zhang et al.’s scheme (Zhang et al.,
2009a) and it satisfies the semantic security, unforge-
ability, sender identity
′
s ambiguity, and public au-
thenticity. The scheme (Zhang et al., 2009b) consists
of the following algorithms.
1. Setup. Given a security parameter κ, the PKG
chooses groups G
1
and G
2
of prime order q >
2
k
(with G
1
-additive group and G
2
-multiplicative
group), bilinear map ˆe : G
1
× G
1
→ G
2
, a gen-
erator P of G
1
. PKG randomly picks the master
key s ∈ Z
∗
q
and computes P
pub
= sP. Next, PKG
chooses three cryptographic hash functions: H
1
:
{0, 1}
∗
→ G
1
, H
2
: G
2
→ {0, 1}
n
1
, H
3
: {0, 1}
l
× G
1
→ Z
∗
q
, where n
1
and l are the sizes of plain-
text and ciphertext respectively. The PKG keeps
the master private key s secret and publishes the
system parameters params = hG
1
, G
2
, ˆe, P, P
pub
,
H
1
, H
2
, H
3
i.
2. Key Extract. Given an identity ID
i
, PKG com-
putes user public key Q
i
= H
1
(ID
i
) and corre-
sponding private key D
i
= sQ
i
.
3. AnonymousSigncrypt. Let L = {U
i
}
(i=1,...,n)
be a
set of n users including the actual signcrypter ID
S
.
To signcrypt a message m on behalf of the group
L to receiver ID
R
, ID
S
performs the following:
(a) For i = 1,...,n(i 6= S), randomly picks x
i
∈ Z
∗
q
and computes R
i
= x
i
P.
(b) For the actual sender S, randomly picks x
S
∈ Z
∗
q
and computes ω = e(P
pub
,
n
∑
i=1
x
i
Q
R
), and sets
c = H
2
(ω) ⊕ m.
(c) Computes R
S
= x
S
Q
S
-
n
∑
i=1,i6=S
(H
3
(c, R
i
)Q
i
+
R
i
) and U =
n
∑
i=1
x
i
P.
(d) Computes S = (x
S
+ H
3
(c, R
S
))D
S
.
(e) Finally, outputs the ciphertext C = hc, S, U, R
1
, ..., R
n
i.
4. UnSigncrypt. Upon receiving the ciphertext C =
(c, S, U, R
1
,...,R
n
), the receiver U
R
with identity
ID
R
uses his private key D
R
to recover and verify
the message as follows:
(a) Checks whether ˆe(S, P)
?
= ˆe(P
pub
,
n
∑
i=1
(R
i
+
H
3
(c, R
i
)Q
i
)). If the test passes, computes
ω
′
= e(U, D
B
), then recovers plaintext m = c ⊕
H
2
(ω
′
); otherwise outputs “Invalid”.
Attack on Confidentiality of the Scheme. During
the Challenge phase, let { m
0
,m
1
} be the messages
chosen by the adversary A and sent to the challenger
C . Assume that C chooses δ ∈
R
{0,1} and computes
challenge ring signcryption on m
δ
as C
∗
= (c
∗
, S
∗
, U
∗
,
R
1
∗
, ..., R
n
∗
) for the receiver ID
∗
R
and sends C
∗
to A .
Now A can find the message used for generating C
∗
by generating a newC
′
derived fromC
∗
but with a dif-
ferent sender group. A performs the following steps
to find if C
∗
is a signcryption of m
0
or m
1
, during the
second phase of oracle queries.
1. A forms a new group L
′
= {U
′
1
, . . . , U
′
η
}
with η members who are totally different from the
users in L
∗
present in the challenge ring signcryp-
tion. The private key D
′
E
of user U
′
E
, is known
to A , where U
′
E
∈ L
′
.
2. For i = 1, ..., η(i 6= E), A randomly picks x
′
i
∈ Z
q
∗
and computes R
′
i
= x
′
i
P.
3. For i = E, A randomly picks x
′
E
∈ Z
q
∗
, computes
R
′
E
= x
′
E
Q
′
E
-
η
∑
i=1,i6=E
(H
3
(c
∗
,R
′
i
)Q
′
i
+ R
′
i
).
4. A computes S
′
= (x
′
E
+ H
3
(c
∗
, R
′
E
))D
′
E
.
5. A constructs a ring signcryption C
′
=
(c
∗
,S
′
,U
∗
,R
′
1
,...,R
′
η
) generated by U
′
E
using
the ring L
′
to the receiver ID
∗
R
.
6. During the second phase of training, A requests
the unsigncryption of C
′
to C . Now C computes
ω
′
= e(U
∗
, D
∗
R
), then recovers plaintext m
δ
= c
∗
⊕ H
2
(ω
′
). Note that c
∗
and U
∗
components of C
∗
are not altered in C
′
.
7. C responds with M = m
δ
as the output to A .
8. A now obtains M and thus correctly identifies the
message in the challenge ring signcryption C
∗
.
AN IDENTITY BASED RING SIGNCRYPTION SCHEME WITH PUBLIC VERIFIABILITY
365

The newC
′
will pass the validation test as a valid sign-
cryption of m
δ
from ring L
′
to the same receiver ID
∗
R
.
This can be shown by
RHS = ˆe(P
pub
,
n
∑
i=1
(R
′
i
+ H
3
(c
∗
,R
′
i
)Q
′
i
))
= ˆe(sP,
n
∑
i=1,i6=E
(R
′
i
+ H
3
(c
∗
,R
′
i
)Q
′
i
) + R
′
E
+
H
3
(c
∗
,R
′
E
)Q
′
E
)
= ˆe(sP, (x
′
E
Q
′
E
+ H
3
(c
∗
,R
′
E
)Q
′
E
)
= ˆe(P, S
′
)
= LHS
This clearly shows that S
′
will pass the verification
test during unsigncryption.
Attack on unforgeability of the scheme. The
scheme in (Zhang et al., 2009b) is not secure against
forgeability attacks. The forger F aims to generate
the signcryption of the message m by ID
S
using the
ring L = {ID
1
, ID
2
,..., ID
S
, ...ID
n
} to a receiver ID
R
.
The details of the attack are as follows.
1. During the training phase, F queries the H
1
oracle
for the identities ID
B
, ID
R
and {ID
1
, ID
2
,...ID
n
}
and F does not execute KeyExtract queries on
the above identities.
2. F gives a signcryption query on a message m
from the sender ID
S
to the receiver ID
B
.
3. If the signcryption oracle returns σ as the result
of the previous query, F can submit σ as a valid
signcryption from ID
S
to ID
R
.
This attack is possible due to the lack of binding
between the signature part of the signcryption and the
receiver.
Attack on Anonymity of the Scheme. We show that
the scheme in (Zhang et al., 2009b) does not provide
anonymity. Any passive observer including the re-
ceiver, who is in possession of a ring signcryption can
correctly identify the sender of the ring signcryption.
This can be demonstrated as follows.
Let C = hc, S, U, R
1
, ..., R
n
i be the ring signcryp-
tion on some message m from the ring L = {ID
1
,
ID
2
,...ID
n
} to ID
R
and let ID
S
∈ L be the actual
sender. On receiving the ring signcryption C, anyone
can do the following operations to identify the actual
sender ID
S
∈ L .
1. Compute R =
n
∑
i=1
(R
i
+ (h
i
Q
i
)), where h
i
=
H
3
(c,R
i
)
2. For j = 1 to n, compute M
j
= R - h
j
Q
j
M
j
=
x
S
Q
S
; if j = S;
x
S
Q
S
+ h
S
Q
S
− h
j
Q
j
; if j 6= S;
.
3. For j = 1 to n, compute N
j
=
n
∑
i=1,i6= j
R
i
N
j
=
n
∑
i=1,i6= j
x
i
P; if j = S;
x
S
Q
S
− x
j
P−
n
∑
j=1, j6=S
h
j
Q
j
; if j 6= S;
4. For j = 1 to n, compute X
j
= ˆe(M
j
, P) and Y
j
=
ˆe(N
j
, Q
j
).
5. For j = 1 to n, compute Z
j
= X
j
Y
j
.
Z
j
=
ˆe(U, Q
S
);if j = S;
ˆe(Q
S
,P)
x
S
+h
S
ˆe(Q
j
,P)
−(x
j
+h
j
)
ˆe(Q
j
,Q
S
)
x
S
∏
i6=S
ˆe(Q
i
,Q
j
)
−h
i
;if j 6= S;
Using the steps 1 to 5, the sender U ∈ L can be iden-
tified.
5 IDENTITY BASED RING
SIGNCRYPTION SCHEME
WITH PUBLIC VERIFIABILITY
In this section, we present a new identity based ring
signcryption scheme incorporating public verifiability
property. The scheme consists of the following algo-
rithms.
1. Setup(κ). This algorithm is executed by the PKG
to setup the system by taking the security param-
eter κ as input.
(a) Selects G
1
an additive cyclic group and G
2
a multiplicative cyclic group, both with same
prime order q > 2
κ
and a random generator P
∈ G
1
.
(b) Selects s ∈
R
Z
q
∗
as the master private key and
sets P
pub
= sP as the master public key.
(c) Selects a CPA-secure symmetric key encryp-
tion system (E,D).
(d) Picks a bilinear map ˆe : G
1
× G
1
→ G
2
.
(e) Selects five cryptographic hash functions
i. H
1
: {0, 1}
∗
→ G
1
ii. H
2
: G
2
→ { 0, 1}
∗
iii. H
3
: { 0, 1}
|M |
× G
1
× G
1
× G
1
× {0, 1}
∗
→
Z
q
∗
iv. H
4
: G
1
× G
2
× {0, 1}
|M |
→ {0, 1}
|M |
v. H
5
: {0, 1}
|M |
× G
1
× G
1
× {0, 1}
∗
→ G
1
(f) The public parameters of the scheme are set to
be params = hG
1
, G
2
, ˆe, P, P
pub
, H
1
, H
2
, H
3
,
H
4
, H
5
, q i.
2. Keygen(ID
i
). This algorithm takes ID
i
, the iden-
tity of a user U
i
as input. The PKG who executes
this algorithm computes the private key and pub-
lic key for the user with identity ID
i
as follows:
SECRYPT 2010 - International Conference on Security and Cryptography
366

(a) The public key is computed as Q
i
= H
1
(ID
i
).
(b) The corresponding private key, D
i
= sQ
i
.
(c) PKG sends D
i
to user U
i
via a secure channel.
3. Signcrypt(m, L , ID
S
, D
S
, ID
R
). Let L = {U
i
}(i
= 1, 2,..., n) be a set of n users including the actual
signcrypter ID
S
. To signcrypt a message m on be-
half of the group L to receiver ID
R
, ID
S
executes
as follows:
(a) Picks a random x ∈ Z
q
∗
and computes U = xP.
(b) Computes ω = ˆe(xP
pub
, Q
R
), k= H
2
(ω) and sets
σ
1
= E
k
(m).
(c) For i = 1 to n, i 6= S
• Chooses R
i
∈
R
G
1
• Computes h
i
= H
3
(σ
1
, R
i
, U, Q
R
, L ).
(d) For i = S
• Chooses x
S
∈
R
Z
q
∗
• Computes R
S
= x
S
Q
S
-
n
∑
i=1,i6=S
(R
i
+ h
i
Q
i
)
• Computes h
S
= H
3
(σ
1
, R
S
, U, Q
R
, L ).
(e) Computes R =
n
∑
i=1
R
i
, σ
2
= H
4
(R, ω, m), S
1
= (x
S
+ h
S
)D
S
, and S
2
= xH
5
(σ
1
, R, Q
R
, L ).
(f) Finally the sender outputs the ciphertext as C =
hσ
1
, σ
2
, S
1
, S
2
, U, R
1
, ..., R
n
i to the receiver.
4. Unsigncrypt(C = h σ
1
, σ
2
, S
1
, S
2
,U, R
1
,...,R
n
i, L ,
ID
R
, D
R
). Upon receiving the ciphertext C, ID
R
uses his private key D
R
to recover the message
and verify the signcryption as follows.
• ω
′
= ˆe(U, D
R
), k
′
= H
2
(ω
′
), m
′
= D
k
′
(σ
1
).
• Check σ
2
?
= H
4
(R, ω
′
,m
′
)
5. Public-verifiability(C = h σ
1
, σ
2
, S
1
, S
2
, U,
R
1
,...,R
n
i, L ). Upon receiving the ciphertext C,
the receiver or any third-party can verify the sign-
cryption for sender authenticity as follows:
• For i = 1 to n ,h
i
= H
3
(σ
1
, R
i
, U, Q
R
, L )
• H = H
5
(σ
1
, R, Q
R
, L )
• ˆe(S
1
, P)
?
= ˆe(P
pub
,
n
∑
i=1
(R
i
+h
i
Q
i
))
• ˆe(S
2
, P)
?
= ˆe(U, H)
• If the above validity checks fail, outputs “In-
valid” ;
6 CORRECTNESS AND
SECURITY ANALYSIS
6.1 Correctness
If the ciphertext C is generated in the way described
as above algorithm, it has
ω
′
= ˆe(U, D
R
)
= ˆe(xP, sQ
R
)
= ˆe(xP
pub
,Q
R
)
= ω.
Furthermore,
ˆe(P
pub
,
n
∑
i=1
(R
i
+ h
i
Q
i
))
= ˆe(sP,
n
∑
i=1,i6=S
(R
i
+ h
i
Q
i
) + R
S
+ h
S
Q
S
)
= ˆe(sP, (x
S
+ h
S
)Q
S
)
= ˆe(P, S
1
).
6.2 Security Analysis
Theorem 1 (Confidentiality).If an IND-IBRSC-
CCA2 adversary A has an advantage ε against
IBRSC scheme, asking q
H
i
(i = 1, 2,3,4,5) hash
queries to random oracles O
H
i
(i = 1,2,3,4, 5), q
e
extract queries (q
e
= q
e1
+ q
e2
, where q
e1
and q
e2
are the number of extract queries in the first phase
and second phase respectively), q
sc
signcryption
queries and q
us
unsigncryption queries, then there
exist an algorithm C that solves the CBDH problem
with advantage ε(
1
q
H
1
q
H
2
).
Proof. The challenger C is challenged with an in-
stance (P, aP, bP, cP) of the CBDHP. Assume
that there is an adversary A capable of breaking
the IND − IBRSC − CCA2 security of IBRSC with
non-negligible advantage. C makes use of A to
solve the CBDHP instance. C simulates the system
with the various oracles O
H
1
, O
H
2
, O
H
3
, O
H
4
, O
H
5
,
O
Signcryption
, O
Unsigncryption
and allows A to make
polynomially bounded number of queries, adaptively
to these oracles. The game between C and A is
demonstrated below:
Setup Phase. C simulates the system by setting up
the system parameters in the following way.
• C chooses the groups G
1
and G
2
and the generator
P ∈ G
1
as given in CBDHP instance.
• Sets the master public key P
pub
= aP, here C does
not know a. C is using the aP value given in the
instance of the CBDHP.
• Models the five hash functions as random oracles
O
H
1
, O
H
2
,O
H
3
, O
H
4
and O
H
5
.
• Selects a bilinear pairing ˆe : G
1
× G
1
→ G
2
.
• Delivers G
1
, G
2
, ˆe, P, P
pub
to A .
Phase I . To handle the oracle queries, C maintains
five lists L
i
, (i = 1,2, 3, 4,5) which keeps track of
the responses given by C to the corresponding oracle
(O
H
1
, O
H
2
, O
H
3
, O
H
4
, O
H
5
) queries. A adaptively
AN IDENTITY BASED RING SIGNCRYPTION SCHEME WITH PUBLIC VERIFIABILITY
367

queries the various oracles in the first phase, which
are handled by C as given below:
O
H
1
Oracle Query. Assume that A queries the
O
H
1
oracle with distinct identities in each query.
There is no loss of generality due to this assumption,
because, if the same identity is repeated, the oracle
consults the list L
1
and gives the same response.
Thus, we assume that A asks q
H
1
distinct queries for
q
H
1
distinct identities. Among this q
H
1
identities, a
random identity has to be selected as target identity
and it is done as follows.
C selects a random index γ, where 1 ≤ γ ≤ q
H
1
.
C does not reveal γ to A . When A asks the γ
th
query
on ID
γ
, C decides to fix ID
γ
as target identity for the
challenge phase. C responds to A as follows:
• If it is the γ
th
query, then C sets Q
γ
= bP, returns
Q
γ
as the response to the query and stores
hID
γ
, Q
γ
, ∗i in the list L
1
. Here, C does not know
b. C is simply using the value bP given in the
instance of the CBDHP.
• For all other queries, C chooses x
i
∈
R
Z
q
∗
and sets
Q
i
= x
i
P and stores h ID
i
, Q
i
, x
i
i in the list L
1
.
C returns Q
i
to A .
O
H
2
Oracle Query. When A makes a query to this
oracle with ω as input, C retrieves h
2
from list L
2
and
returns h
2
to A , if the tuple exists in the list; else,
chooses a new h
2
randomly, stores hω, h
2
i in L
2
and
returns h
2
to A .
O
H
3
Oracle Query. When A makes a query to
this oracle with (c, R
i
, U, Q
R
, L ) as input, C retrieves
h
i
(3)
from list L
3
and returns h
i
(3)
to A if the tuple
exists in the list ; else, chooses a new
h
i
(3)
∈
R
Z
q
∗
randomly, stores h c, R
i
, U, Q
R
, L , h
i
(3)
i,
in the list L
3
and returns h
i
(3)
to A .
O
H
4
Oracle Query. When A makes a query to
this oracle with (R,ω,m) as input, C retrieves ψ from
list L
4
and returns ψ to A if the tuple exists in the list;
else, chooses ψ ∈ { 0, 1}
|M |
, stores hR, ω, m, ψi in L
4
and returns ψ to A .
O
H
5
Oracle Query. When A makes a query to
this oracle with (σ
1
, R, Q
i
, L ) as input, C retrieves h
from list L
5
and returns h to A if the tuple exists in
the list; else, chooses r ∈
R
G
1
, computes h = r, if
ID
i
6= ID
γ
, and computes h = rP
pub
if ID
i
= ID
γ
. The
tuple hσ
1
, R, Q
i
, L , hi is stored in list L
5
and returns
h to A .
Extract Query. On getting a request for the private
key of user U
i
with identity ID
i
, C aborts if ID
i
=
ID
γ
. Else, C retrieves hQ
i
, x
i
i from list L
1
and returns
D
i
= aQ
i
= x
i
aP to A .
O
Signcryption
Query. A chooses a message m, a
set of n potential senders and forms an ad-hoc
group L by fixing a sender ID
S
and a receiver ID
R
and sends them to C . To respond correctly to the
signcryption query on the plaintext m chosen by A , C
does the following:
C proceeds according to the signcryption algo-
rithm when ID
S
6= ID
γ
. This is possible as C knows
the private key D
S
of the sender ID
S
.
If the sender’s identity ID
S
= ID
γ
(i.e. when C does
not know the private key corresponding to ID
S
), C
cooks up a response as explained below:
• Chooses a random x ∈ Z
q
∗
, computes U = xP, ω
= ˆe(xP
pub
, Q
R
) and sets σ
1
= E
k
(m).
• For i = 1 to n, i 6= S, chooses R
i
∈ G
1
and com-
putes h
i
(3)
= H
3
(c, R
i
, U, Q
R
, L ).
• For i = S,
– Chooses x
S
, h
S
(3)
∈ Z
q
∗
.
– Computes R
S
= x
S
P - h
S
(3)
Q
S
-
n
∑
i=1,i6=S
(R
i
+
h
i
Q
i
).
– Adds the tuple hc, R
S
, U, Q
S
, L , h
S
(3)
i to the
list L
3
.
(Note. Here h
S
(3)
is not computed by C , instead it
is chosen at random and set as the output for the
random oracle query h
S
(3)
= H
3
(c, R
S
, U, Q
R
, L )
This is possible because the random oracles are
manipulated by C ).
• Computes S
1
= x
S
P
pub
and S
2
= xH
5
(σ
1
, R, Q
R
,
L ).
• Computes R = ΣR
i
and queries σ
2
from O
H
4
.
Finally, C outputs the ring signcryption C = hσ
1
, σ
2
,
S
1
, S
2
, U, R
1
,...,R
n
i to A as the signcryption of m.
The signcryption C = hσ
1
, σ
2
, S
1
, S
2
, U, R
1
,...,R
n
i is
considered as valid by A because C passes the verifi-
cation tests as shown below.
From the definition of R
S
,
n
∑
i=1
(R
i
+h
i
Q
i
) = x
S
P. Thus,
ˆe(P
pub
,
n
∑
i=1
(R
i
+ h
i
Q
i
))= ˆe(aP, x
S
P)
= ˆe(P, x
S
aP)
= ˆe(P, x
S
P
pub
)
= ˆe(P,V)
O
Unsigncryption
Query. Upon receiving an unsigncryp-
tion query on a ring signcryption
C = hσ
1
, σ
2
, S
1
, S
2
, U, R, R
1
,..., R
n
i with ID
R
as re-
ceiver, C proceeds as follows:
SECRYPT 2010 - International Conference on Security and Cryptography
368

C proceeds as per the unsigncryption algorithm, when
ID
R
6= ID
γ
. Here, C can directly use the unsigncryp-
tion algorithm because, C knows the private key D
R
of the receiver ID
R
.
If the receiver identity ID
R
= ID
γ
(i.e. When C does
not know the private key corresponding to ID
R
), C
generates the response as explained below:
1. For i = 1 to n, Compute h
i
= O
H
3
(c, R
i
, U,
Q
R
, L ) and check whether ˆe(S
1
, P)
?
= ˆe(P
pub
,
n
∑
i=1
(R
i
+h
i
Q
i
)).
2. If the above equation holds,then for each pair (m,
ω) in the list L
4
, the challenger C performs the
following:
(a) Computes k
′
= O
H
2
(ω).
(b) Computes R = ΣR
i
(c) Retrieves the message as m
′
= E
k
′
(c).
(d) Checks whether ω
?
= ˆe(S
1
, Q
R
).
(e) Checks whether m
′
?
= m and σ
?
= O
H
4
(R, ω
′
,
m
′
).
3. The first time when all the above checks passes, C
outputs the corresponding m
′
and halts.
4. If every (m, ω) pair fails the check in step(2) then
C outputs “Invalid” and halts.
Challenge Phase. Finally, A chooses two plaintexts
m
0
, m
1
∈ M , the set of ring members
L = ID
i
(i = 1 to n), a sender identity ID
S
∈ L
and a receiver identity ID
R
on which A wants to be
challenged and sends them to C . A should not have
queried the private key corresponding to ID
R
in the
first phase. C aborts, if ID
R
6= ID
γ
; else, C chooses a
bit δ ∈
R
{0,1} and computes the challenge ring sign-
cryption C of m
δ
as follows :
• Sets U
∗
= cP. Here C is using the value cP given
in the instance of CBDHP.
• Chooses {R
i
∗
}
(i=1 to n)
, S
∗
1
, S
∗
2
∈
R
G
1
and σ
1
∗
∈
R
{0,1}
|M|
, σ
2
∗
∈
R
Z
∗
q
, and outputs C
∗
= h σ
∗
1
,
σ
∗
2
, S
∗
1
, S
∗
2
, U
∗
, R
∗
, R
∗
1
, ..., R
∗
n
i.
Phase II. On getting the challenge ring signcryption
C
∗
, A is allowed to interact with C as in the first
phase. But this time, A is not given access to the pri-
vate key of ID
R
and is also restricted from querying
the decryption oracle for the ring unsigncryption of
C
∗
.
Guess. At the end of the Phase II, A returns its
guess. C ignores the answer from A , picks a ran-
dom tuple (ω, h
2
) from list L
2
and returns the corre-
sponding ω as the solution to the CBDHP instance.
Thus, any adversary that has advantage in the real
IND − IBRSC−CCA2 game must necessarily recog-
nize with probability ε at least that the challenge ci-
phertext provided by C is incorrect. For A to find that
C
∗
is not a valid ciphertext, A should have queried the
O
H
2
oracle with ω = ˆe(U
∗
, D
γ
). Here D
γ
is the private
key of the target identity and it is a(Q
γ
) = abP. Also C
has set U
∗
= cP. Hence ω = ˆe(U
∗
, D
γ
) = ˆe(cP,abP) =
ˆe(P,P)
abc
. With probability
1
q
H
2
, the value of ω cho-
sen by C from list L
2
will be the solution to CBDHP
instance.
We now consider C ’s probability of success. The
events in which C aborts the IND − IBRSC−CCA2
game are,
1. E
1
- when A queries the private key of the target
identity ID
γ
and its probability, Pr[E
1
] =
q
e
q
H
1
.
2. E
2
- when A does not choose the target identity
ID
γ
as the receiver during the challenge phase and
its probability, Pr[E
2
] =
1−
1
q
H
1
− q
e
.
The probability that C does not abort the IND −
IBRSC−CCA2 game is given by
(Pr[¬E
1
∧ ¬E
2
]) =
1−
q
e
q
H
1
1
q
H
1
− q
e
=
1
q
H
1
.
The probability that, the ω chosen randomly from L
2
by C , being the solution to CBDHP is
1
q
H
2
.
Therefore, the probability of C solving CBDHP
is given by, Pr[C(P,aP,bP,cP)= ˆe(P, P)
abc
] =
ε
1
q
H
1
q
H
2
.
Since ε is non-negligible, the probability of C solving
CBDHP is also non-negligible.
Theorem 2 (Unforgeability). If an
EUF − IBRSC − CMA forger A exists against
IBRSC scheme, then there exist an algorithm C that
solves the CDHP with advantage ε
1
q
H
1
.
Proof. The challenger C is challenged to solve an
instance of the CDHP. C interacts with adversary
A which is capable of breaking the EUF − IBRSC−
CMA security of the new scheme, to solve the CDHP
instance. On receiving the instance (P,aP,bP) of
the CDHP as input, C begins the interaction with A
to compute the value abP. C simulates the system
with the various oracles O
H
1
, O
H
2
, O
H
3
, O
H
4
, O
H
5
,
O
Signcryption
, O
Unsigncryption
and allows A to adaptively
ask polynomially bounded number of queries to these
oracles.
Setup Phase. C simulates the system by setting up
the system parameters in the following way.
AN IDENTITY BASED RING SIGNCRYPTION SCHEME WITH PUBLIC VERIFIABILITY
369

• C chooses the groups G
1
and G
2
and the generator
P ε G
1
as given in CDHP instance.
• Sets the master public key P
pub
= aP, here C does
not know a. C is using the aP value given in the
instance of the CDHP.
• Models the five hash functions as random oracles
O
H
1
, O
H
2
, O
H
3
, O
H
4
and O
H
5
.
• Selects a bilinear pairing ˆe : G
1
× G
1
→ G
2
.
• Delivers G
1
, G
2
, ˆe, P, P
pub
to A .
Training Phase. A adaptivelyperformspolynomially
bounded number of queries to the various oracles in
this phase. The queries may be Hash Queries, Ex-
tract Queries, O
Signcryption
Queries and O
Unsigncryption
Queries, which are handled by C .
All Hash oracle queries are same as that in the
confidentiality game discussed above.
Forgery. Finally, A produces a forged signcryption
C
∗
= hσ
1
∗
, σ
2
∗
, S
1
∗
, S
2
∗
, U
∗
, R
1
∗
, ...,R
n
∗
i on the mes-
sage m
∗
(i.e. C
∗
was not produced by the Signcryption
Oracle as an output for the ring signcryption query on
the message m with an ad-hoc set of users U
∗
and the
receiver ID
R
),where the private keys of the users who
are in the group U
∗
were not queried in the training
phase. C aborts if U
∗
do not contain the target iden-
tity. Else, C can very well unsigncrypt and verify the
validity of the forged ring signcryption C
∗
(as done in
unsigncrypt oracle).
Using forking lemma, we obtain two valid ring
signcryptions C
∗
= hσ
1
∗
, σ
2
∗
, S
1
∗
, S
2
∗
, U
∗
, R
∗
,
R
1
∗
,...,R
n
∗
i and C
′
= hσ
1
′
, σ
2
′
, S
1
′
, S
2
′
, U
∗
, R
∗
,
R
1
∗
,...,R
n
∗
i. On getting two valid ring signcryptions
on m
∗
, C will be able to retrieve D
S
= abP as follows:
• Here S
1
′
= (x
S
+ h
S
′
)D
S
and S
1
∗
= (x
S
+ h
S
∗
)D
S
(since they have the same randomness)
• Thus, S
1
′
- S
1
∗
= (h
S
′
- h
S
∗
)D
S
Since C knows the hash values h
S
′
and h
S
∗
, C can
compute D
S
= (S
1
′
- S
1
∗
)(h
S
′
- h
S
*)
−1
. This means, C
can compute abP because D
S
= abP. In other words,
C is capable of solving CDHP, which is not possi-
ble. Hence, IBRSC is secure against EUF − IBRSC−
CMA.
Theorem 3 (Anonymity). The IBRSC scheme is fully
anonymous.
The proof is based on the approach used in (Chow
et al., 2005).
Since
S
i6=S
{R
i
} and x
′
S
is randomly generated,
S
n
i=1
{R
i
} values are uniformly distributed. All other
components of C except S
1
does not contain any iden-
tity information bound to them. So we need to check
only whether S
1
= (x
S
+ h
S
)D
S
leaks information
about the actual signer. We have S
1
- h
S
D
S
= x
S
D
S
.
Anyone can compute the value of x
S
Q
S
by x
S
Q
S
=
R
S
+
n
∑
i=1,i6=S
(R
i
+ h
i
Q
i
). As bilinearity can relate x
S
D
S
and x
S
Q
S
, by checking whether ˆe(x
S
D
S
, P) = ˆe(x
S
Q
S
,
P
pub
), it may be possible to see if ID
j
is the actual
signcrypter by checking whether the following equal-
ity holds:
ˆe(R
j
+
∑
i6= j
(R
i
+ h
i
Q
i
), P
pub
)
?
= ˆe(S
1
, P)/ˆe(h
j
Q
j
,
P
pub
).
But this method is of no use, as the above equality
holds ∀ j values. i.e. the signature is symmetric. The
above equality is just the same as the equality to be
checked in the verification algorithm.
ˆe(R
j
+
∑
i6= j
(R
i
+ h
i
Q
i
), P
pub
)
= ˆe(
∑
i6=S
R
i
+ R
S
+
∑
i6= j
h
i
Q
i
, P
pub
)
= ˆe(
∑
i6=S
R
i
+ x
S
Q
S
−
∑
i6=S
{R
i
+ h
i
Q
i
} +
∑
i6= j
h
i
Q
i
, P
pub
)
= ˆe(x
S
Q
S
−
∑
i6=S
{h
i
Q
i
} +
∑
i6= j
h
i
Q
i
, P
pub
)
= ˆe(x
S
Q
S
+ h
S
Q
S
− h
j
Q
j
, sP)
= ˆe(x
S
D
S
+ h
S
D
S
− h
j
D
j
, P)
= ˆe(S
1
− h
j
D
j
, P)
= ˆe(S
1
, P)/ˆe(h
j
D
j
, P)
= ˆe(S
1
, P)/ˆe(h
j
Q
j
, P
pub
)
So, we can conclude that even an adversary with un-
bounded computing power has no advantage in iden-
tifying the actual signcrypter over random guessing.
7 CONCLUSIONS
As a concluding remark we summarize the work in
this paper. In this paper we showed the security weak-
ness of an identity based ring signcryption scheme in
the literature. We showed that (Zhang et al., 2009b)
does not provide security against adaptive chosen ci-
phertext attacks (CCA2), existential unforgeability at-
tacks and anonymity attacks. We proposed a new
identity based ring signcryption scheme as an exten-
sion to (Selvi et al., 2009) for which we proved the
security against chosen ciphertext attack and existen-
tial unforgeability in the random oracle model. We
also proved anonymity property of our scheme. Fu-
ture research direction includes designing an identity
based ring signcryption scheme with constant cipher-
text length. We provide the comparison of our Iden-
tity Based Ring Signcryption Scheme with the exist-
ing secure schemes in the following tables.
SECRYPT 2010 - International Conference on Security and Cryptography
370
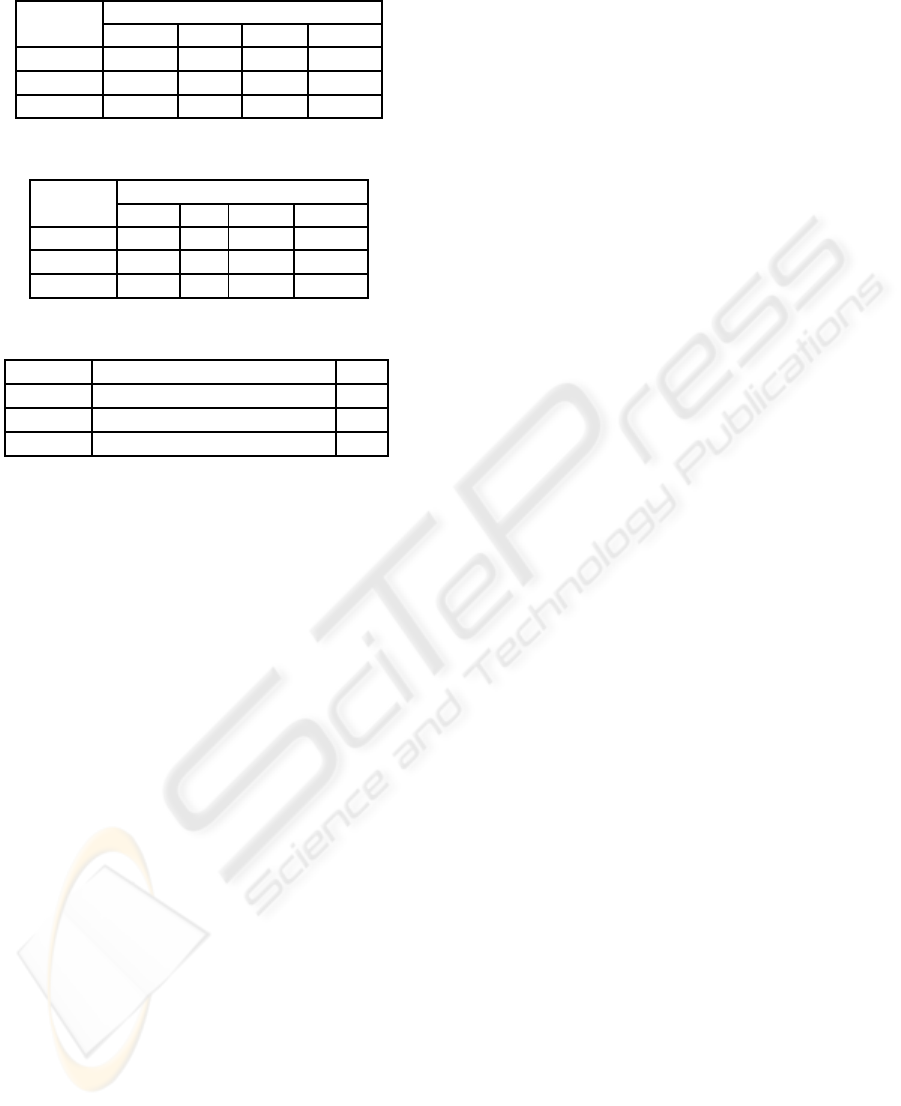
Table 1: Efficiency comparison - Signcryption.
Scheme Signcryption
SPM BP G
2
M PA
A
∗
2n+ 2 n+ 2 1 2n
B n+ 2 1 − 2n− 2
C n+ 3 1 − 2n− 2
Table 2: Efficiency comparison - Unsigncryption.
Scheme Unsigncryption
SPM BP G
2
M PA
A
∗
n 3 n+ 1 n
B n 3 − 2n− 1
C n 5 − 2n− 1
Table 3: Ciphertext size and public verifiability.
Scheme Ciphertext Size PV
A 2|M | + (n+ 1)|G
1
| + n|Z
∗
q
| No
B 2|M | + (n+ 2)|G
1
| No
C 2|M | + (n+ 4)|G
1
| Yes
A-Huang et al.(Huang et al., 2005), B- Sharmi et al.(Selvi et al., 2009), C-
IBRSC, PV- Public Verifiability, SPM - Scalar Point Multiplication, BP -
Bilinear Pairing, G
2
M - Multiplication of two G
2
elements and PA - Point
Addition.
* This scheme cannot be considered as a provably secure scheme as the
proof given for the model is incorrect.
REFERENCES
Baek, J., Steinfeld, R., and Zheng, Y. (2002). Formal proofs
for the security of signcryption. In PKC 2002: Pro-
ceedings of the 5th International Workshop on Prac-
tice and Theory in Public Key Cryptography, volume
2274 of Lecture Notes in Computer Science, pages
80–98. Springer-Verlag.
Chow, S. S. M., Yiu, S.-M., and Hui, L. C. K. (2005). Effi-
cient identity based ring signature. In ACNS, volume
3531, pages 499–512.
Huang, X., Susilo, W., Mu, Y., and Zhang, F. (2005).
Identity-based ring signcryption schemes: Crypto-
graphic primitives for preserving privacy and authen-
ticity in the ubiquitous world. In AINA ’05: Pro-
ceedings of the 19th International Conference on
Advanced Information Networking and Applications,
pages 649–654. IEEE Computer Society.
Li, F., Shirase, M., and Takagi, T. (2008a). Analysis
and improvement of authenticatable ring signcryption
scheme. In International Conference ProvSec-08, Pa-
per appears in Journal of Shanghai Jiaotong Univer-
sity (Science), volume 13-6, pages 679–683.
Li, F., Xiong, H., and Yu, Y. (2008b). An efficient id-based
ring signcryption scheme. In International Confer-
ence on Communications, Circuits and Systems, 2008.
ICCCAS 2008., pages 483–487.
Malone-lee, J. (2002). Identity-based signcryption. Cryp-
tology ePrint Archive, Report 2002/098.
Selvi, S. S. D., Vivek, S. S., and Rangan, C. P. (2009).
On the security of identity based ring signcryption
schemes. In ISC, 12th International Conference, ISC
2009, Pisa, Italy, September 7-9, 2009. Proceedings,
volume 5735 of Lecture Notes in Computer Science,
pages 310–325. Springer.
Vivek, S. S., Selvi, S. S. D., and Rangan, C. P. (2009). On
the security of two ring signcryption schemes. In SE-
CRYPT 2009, pages 219–224. INSTICC Press.
Yu, Y., Li, F., Xu, C., and Sun, Y. (2008). An effi-
cient identity-based anonymous signcryption scheme.
Wuhan University Journal of Natural Sciences, Vol-
ume: 13, Number: 6, December, 2008:670–674.
Zhang, J., Gao, S., Chen, H., and Geng, Q. (2009a). A
novel id-based anonymous signcryption scheme. In
APWeb/WAIM, volume 5446 of Lecture Notes in Com-
puter Science, pages 604–610. Springer.
Zhang, M., Yang, B., Zhu, S., and Zhang, W. (2008). Ef-
ficient secret authenticatable anonymous signcryption
scheme with identity privacy. In PAISI, PACCF and
SOCO ’08: Proceedings of the IEEE ISI 2008 PAISI,
PACCF, and SOCO international workshops on In-
telligence and Security Informatics, pages 126–137.
Springer-Verlag.
Zhang, M., Zhong, Y., Yang, B., and Zhang, W. (2009b).
Analysis and improvement of an id-based anonymous
signcryption model. In ICIC (1), volume 5754 of
Lecture Notes in Computer Science, pages 433–442.
Springer.
Zhu, Z., Zhang, Y., and Wang, F. (Pages 649-654,
http://dx.doi.org/10.1016/j.csi.2008.09.023, 2008).
An efficient and provable secure identity based ring
signcryption scheme. In Computer Standards &
Interfaces.
Zhun, L. and Zhang, F. (2008). Efficient identity based ring
signature and ring signcryption schemes. In Interna-
tional Conference on Computational Intelligence and
Security, 2008. CIS ’08., volume 2, pages 303–307.
AN IDENTITY BASED RING SIGNCRYPTION SCHEME WITH PUBLIC VERIFIABILITY
371
