
ANONYMOUS SOCIAL STAMPS
Authenticating Anonymous Statements to Friends with Privacy
Sandeep S. Kumar
Information and System Security Group, Philips Research Laboratories, Eindhoven, The Netherlands
Keywords:
Privacy, Trust, Social network.
Abstract:
Numerous online services and applications for smart devices exist today on the internet which claim almost
similar functionalities. This inevitably leads to the problem of being able to choose the right one which is
mostly done today by trial-and-error. However this gets tricky if it involves sharing privacy sensitive infor-
mation with the service e.g. in the case of health and well-ness services. A customer’s trust in a new online
service is known to increase based on testimonials (or observable behavior) of people within a social distance
(friends, friends-of-friends etc). Linking testimonials to users requires releasing one’s social network infor-
mation which by itself is privacy invasive. The paper presents the concept of an anonymous social stamp
which can be assigned to anonymous statements and help prove that the statement was made by a particular
member of an external social networking site. Trust can then be derived based on the social distance between
the persons concerned: the person who made the statement and the person verifying the statement. A possible
implementation of the concept is shown with the existing infrastructure of RSA keys already in use by social
networking sites. The concept is applicable for the new services that can create confidence in new users by
revealing anonymous data sharing configurations of other users with the service.
1 INTRODUCTION
An incredible amount of choice exists today in web
services and applications that can be used online or
downloaded onto various smart devices. With this
incredible choice comes the problem of determining
which of them are useful and actually deliver what
they claim. These services and applications can range
from simple productivity applications like collabora-
tive text-processing to more advanced applications for
health and well-ness like tracking vital bodily sig-
nals. Most of these applications require sharing cer-
tain amount of privacy sensitive information. This
makes it evenmore important to make an educated de-
cision on which applications to install and how much
information to share with such services.
It is well known that people tend to use testimo-
nials and advices provided on various aggregation
sites like epinions (Epinions, 2010) while choosing
services. The main idea behind such reputation sys-
tems (Resnick et al., 2000) is that the majority of the
crowd can help filter out scrupulous service providers.
However the concern is that such systems are easy to
manipulate since ratings are provided by people with
no prior trust relationship. Therefore most of these
trust and reputation systems (Josang et al., 2007) are
faced with the problem of linking pseudonyms to peo-
ple one can trust. Another concern is that such meth-
ods do not help identify services that would best fit
to one’s individual needs but rather on average to a
wider group.
Health and well-ness services is one of the ar-
eas that urgently require trusted statements and help
in making educated decision of using different ap-
plications. Health and well-ness has become a buz-
zword that is increasingly being used by many fraud-
ulent services to attract new customers. Such services
mostly don’t work or are sometimes even not safe for
some consumers. The increasing numbers of such
incidents have even lead the Federal Trade Commis-
sion (FTC, 2010a) to set up a dedicated information
site for consumers to detect misleading and decep-
tive health claims at Who Cares (FTC, 2010b). The
European Healthcare Fraud and Corruption Network
(EHFCN) has recognized that one of the reasons that
fraud happens is when providers could have conflicts
of interest that affect their judgement (EC, 2010a).
Customers that have either experienced or heard/read
about these much publicized frauds are very reluctant
to use any new heath and well-ness services. There-
183
S. Kumar S. (2010).
ANONYMOUS SOCIAL STAMPS - Authenticating Anonymous Statements to Friends with Privacy.
In Proceedings of the International Conference on Security and Cryptography, pages 183-188
DOI: 10.5220/0002993401830188
Copyright
c
SciTePress

fore, creating trust in the new heath and well-ness ser-
vices would be a very important requirement for new
service providers. Additionally, customers need to be
confident to share vast amounts of sensor data and pri-
vate medical information that would be needed to pro-
vide the service. Legislation like the Unfair Commer-
cial Practices Directive (Directive 2005/29/EC) (EC,
2010b) can only deter certain amount of misleading
claims from service providers but cannot create con-
fidence in the services as being beneficial.
1.1 Our Contribution
Knowledge about the social distance of a new cus-
tomer with existing consumers of a service is impossi-
ble to determine without access to the social network
of the new and existing customers. However, this data
is readily available at the numerous social networking
sites. These social networks have evolved into an im-
portant source of communication and trust building
on the internet. These trust relationships can either
be the individuals trust relationships in the physical
world or new ones based on virtual interactions.
For a health and well-ness service provider, cre-
ating and administrating yet another social network
would not be preferred option but to have a mecha-
nism that allows tapping into the existing information
at the social networks to give the assurance of the so-
cial distance between two parties. However, revealing
a person’s static identity at a social networking site or
openly revealing one’s social network is privacy inva-
sive. Therefore external sites that would like to create
trust in their services through recommendations from
friend’s network, need a mechanism to link into the
social networks without invading privacy. The mech-
anism should provide enough flexibility such that in-
dividuals are not forced to reveal their social networks
openly if they do not desire. Additionally, the social
networking site should not be able to gather and learn
about the various external services that the individual
subscribes to based on this mechanism.
The main idea of the paper is an anonymous social
stamp (created using existing RSA key certificates of
the social networking sites) that individuals can attach
to a statement (reviews, advices, configurations, etc.)
on service providers web-site or other review aggre-
gation sites for others to view. A new customer of the
service or application can view this statement and if
within a social distance can verify it.
The paper is organized as follows, in Section 2 we
clearly define the setting and the various parties in-
volved. In Section 3 the security and privacy require-
ments for our solution is described. Section 4 presents
the construction of our anonymous social stamp solu-
tion. The various interactions for initialization, gen-
eration and verification of the stamp is also presented.
In Section 5, we present other useful applications of
the anonymous stamp and end with conclusions in
Section 6.
2 SCENARIO
As mentioned previously, testimonials and advices to
use new services can have additional value if it can be
proved that they are written by someone within a so-
cial distance like friends-of-friends. This would pro-
vide some amount of trust in these statements com-
pared to statements made from total strangers. We
use a social networking site as a way to determine
this social distance. To make clear the setting, we
first present the various parties in the system and their
roles. Then we discuss the security and privacy re-
quirements for the different parties involved.
2.1 System Model
We present the relevant parties with an example as
shown in Figure 1. Alice is the party providing an
anonymous testimonial (or rating) of a service. How-
ever she would like to attach a proof (stamp) that can
help others viewing the testimonial to derive some
amount of trust in that statement, if they are related
within a social distance. Bob is a new customer who
would like to use the service and make an educated
decision based on the testimonials (one of which is
from Alice). He retrieves the testimonial and uses
the anonymous social stamp to contact the social net-
working site to know if the anonymous testimonial
writer is within a certain social distance of him. Based
on this information he can decide to either trust the
testimonial or ignore it.
3 SECURITY AND PRIVACY
REQUIREMENTS
For the anonymous social stamp to work as shown in
the scenario it has to fulfill certain security and pri-
vacy requirements as mentioned below:
• Verifiability. The social stamp can prove to a ver-
ifier (Bob) with the help of the social networking
site that the statement indeed belongs to a specific
user of the social networking site. The real iden-
tity or pseudonym at the social networking site
is not revealed but only the social distance is re-
vealed by the social networking site based on the
SECRYPT 2010 - International Conference on Security and Cryptography
184
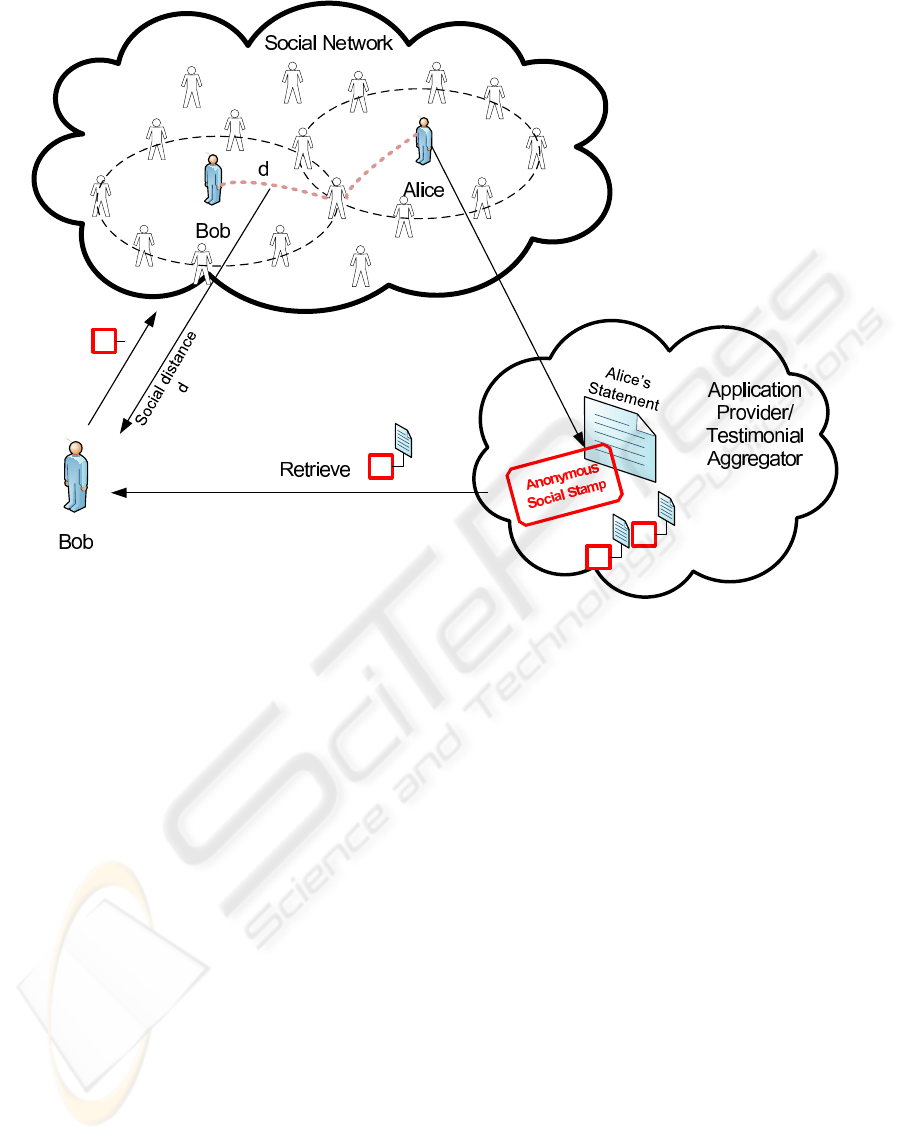
Figure 1: Implementation scenario for the anonymous social stamp.
verifier’s (Bob) social distance to the statement
creator’s (Alice) at the networking site.
• Secure Binding. The stamp is publicly visible
to everyone and therefore should not be possible
to copy to a different pseudonym or statement by
anyone.
• Privacy of the Creator. The stamp by itself does
not reveal the identity of the creator (Alice) to
anyone except to the social networking site.
• Unlinkability of the Creator. The stamps alone
do not enable linking the creator (Alice) across
different sites.
• Privacy of the Verifier. The verification of the
stamp does not require the verifier to show the so-
cial networking site the statement or the site from
which it was obtained. This is minimize the so-
cial networking site from knowing the different
services he is interested in.
4 THE ANONYMOUS SOCIAL
STAMP
Before we present the technical details of the Anony-
mous Social Stamp, we first assume the following ter-
minology:
• The external service can be uniquely identified as
W. This could be the unique url or the SSL cer-
tificate of the service.
• The statement (review, advice, etc.) to which
the social stamp needs to be attached at W be
represented as T
i
, and uniquely identified by the
pair T
i
,W. For practical purposes, we assume
that the pair T
i
,W can be converted to a single
value h using a publicly known hash function, i.e,
h
i
= Hash(T
i
,W).
• The social networking site is represented as N.
• The user that creates the social stamp (Alice) has
the pseudonym I
N
at the social networking site
N. She also has a shared secret S
I
N
with social
networking site (e.g. a hashed password).
• The verifier’s (Bob) identity at the social network-
ing site N be V
N
.
ANONYMOUS SOCIAL STAMPS - Authenticating Anonymous Statements to Friends with Privacy
185

• The social network N possesses the RSA public-
private key pair {P
N
,S
N
}. Based on (Rivest et al.,
1978), the keys P
N
and S
N
exhibits the following
property:
g
(P
N
.S
N
)
mod n = g (1)
for any g and for public n as defined in (Rivest
et al., 1978). The method to generate these RSA
keys and their properties are well known and will
not be described further here. However note that
all operations shown further are done mod n
even when not explicitly mentioned.
We now describe how the anonymoussocial stamp
can be created for a statement and verified. Figure 2
shows the various phases from initialization, genera-
tion and verification of the stamp. We describe each
step in detail and show the correctness of the protocol.
4.1 Initialization Phase
The first step is the initialization phase where the
user Alice at the social networking sites is provided
with keys to create any number of anonymous social
stamps. The social networking site generates a large
random g. This g is fixed for each social network and
known publicly. Alice who possess the identity I
N
at
the social networking site, is given the two keys K
N
and K
I
N
derived as follows:
• K
N
= g
P
N
, which is same for all users and need
not be kept secret since it is created using a public
key.
• K
I
N
= g
(S
I
N
.S
N
)
, which needs to be kept secret by
Alice. However Alice can verify that it indeed is
key based on her shared secret decrypting it using
the public key P
N
.
The social networking site stores the pair {K
I
N
,I
N
}
in a lookup table. This is useful to perform a reverse
look-up of the user identity from K
I
N
.
4.2 Stamp Generation Phase
Now, if the user Alice wishes to attach a social stamp
to a statement uniquely identified as {T
i
,W} on an
external site, then the following steps are perfomed:
1. Create the hash h
i
= Hash(T
i
,W).
2. Generate a large random number r
i
, keep it secret.
3. Create the Binding stamp: B
i
= K
I
N
.g
(r
i
.h
i
)
4. Create the Helper stamp: H
i
= (K
N
)
r
i
5. Assign the tuple {N,B
i
,H
i
} as the anonymous so-
cial stamp to the statement T
i
,W.
Note that the stamp is bound to the statement only
in such a way as to prevent copying the stamp on to a
different statement. It however does not prevent any-
one else to copy the statement and create their own
stamp for it. This should however not affect the secu-
rity requirements since our intention is to verify if a
statement can be linked to Alice, irrelevant of the fact
if she had copied that statement from someone else.
4.3 Stamp Verification Phase
When a new customer Bob would like to verify the
stamp {N,B
i
,H
i
} attached to the statement {T
i
,W}
then he should be an existing member of the social
networking site N. Assuming he too is a member at
N with the identity V
N
, he can perform the following
steps to verify the stamp and get the social distance:
1. Create the hash h
i
= Hash(T
i
,W).
2. Transform the helper stamp so that the verifier
Bob can be sure that the stamp is indeed bound
to h
i
by performing the following operation:
¯
H
i
= H
h
i
= g
(P
N
.r.h)
3. Now contact the social networking site N with the
tuple {V
N
,B
i
,
¯
H
i
} to verify the binding and get the
social distance.
On receiving the tuple {V
N
,B
i
,
¯
H
i
} the social net-
working site performs the following operation
1. Use the RSA secret key pair of S
N
to generate a
de-binder from the new helper stamp as follows:
¯
B
i
=
¯
H
S
N
i
= (K
I
N
.g
(r
i
.h
i
)
)
S
N
= (g
P
N
.r
i
.h
i
)
S
N
= (g
P
N
.S
N
)
(r
i
.h
i
)
= g
(r
i
.h
i
)
The result is due to the property of the RSA keys
as shown in Equation 1.
2. Use the de-binder
¯
B
i
to remove the statement re-
lated hashed values from the binding stamp by
performing:
B
i
/
¯
B
i
= (K
I
N
.g
(r
i
.h
i
)
)/g
(r
i
.h
i
)
= K
I
N
This operation also verifies that indeed the bind-
ing was for the statement h
i
it was intended for,
otherwise the generated key will not be right.
3. The social network can now perform a reverse
user identity lookup for K
I
N
in its lookup table
to map to the identity I
N
of Alice as the creator of
the stamp. The social network neither knowswhat
the statement was about or where it was posted.
SECRYPT 2010 - International Conference on Security and Cryptography
186

1. Assumptions:
• Communication channel between all parties are authenticated (for e.g. using pseudonym and password)
• All operations performed mod n as in Equation 1
2. Initialization Phase:
Alice: pseudonym I
N
Social Network N: RSA key pair {P
N
,S
N
}
Shared secret: S
I
N
Generate a random g (public)
{K
N
,K
I
N
}
K
N
= g
P
N
K
I
N
= g
(S
I
N
.S
N
)
Secret keys {K
N
,K
I
N
} Store pair {K
I
N
,I
N
}
3. Anonymous Social Stamp Generation Phase:
Alice: creates statement T
i
Service Provider W
h
i
= Hash(T
i
,W)
Generate random r
i
(secret)
Binding stamp:B
i
= K
I
N
.g
(r
i
.h
i
)
Helper stamp:H
i
= K
r
i
N
T
i
,{N,B
i
,H
i
}
- Publishes statement: T
i
Social Stamp: {N,B
i
,H
i
}
4. Anonymous Social Stamp Verification Phase:
Bob Service Provider W
Retrieve: T
i
,{N,B
i
,H
i
}
T
i
,{N,B
i
,H
i
}
Published: T
i
,{N,B
i
,H
i
}
h
i
= Hash(T
i
,W)
¯
H
i
= H
h
i
i
Bob:pseudonym V
N
Social Network N
Authenticate to N
Verify bind and social distance
V
N
,{B
i
,
¯
H
i
}
-
¯
B
i
=
¯
H
S
N
i
B
i
/
¯
B
i
= K
I
N
Reverse lookup K
I
N
→ I
N
Distance d between V
N
and I
N
Bind: Yes/No and distance d
Figure 2: Anonymous social stamp interactions.
4. The social network can now inform the verifier
Bob (after he has properly authenticated to the so-
cial network), the social distance between I
N
and
V
N
.
This social distance allows Bob to assign a certain
amount of trust to the statement rather than assuming
it to be a complete stranger. Alice does not have to
worry about revealing her interactions at other sites
to the social networking site or to be linked across
the different sites based on her stamp. Thus all the
security and privacy requirements laid down before
can be met using anonymous social stamps and still
provide the functionality that is required.
More advanced features can be built around this
main idea in which the social network allows users to
classify users to be more trustworthy only if they are
connected through a branch of a particular friend, etc.
ANONYMOUS SOCIAL STAMPS - Authenticating Anonymous Statements to Friends with Privacy
187

5 ADDITIONAL APPLICATIONS
Here we present an extension of the above social
stamp concept where the main aim had been to au-
thenticate that a statement had originated from a per-
son in the social network. However, the technique
can also be used if the user wants to hide information
which can only be read by people within a social dis-
tance. Thus additional information can be revealed if
the person viewing the statement is within a certain
social distance.
To enable the hiding of information, the statement
T
i
needs to be encrypted with the key Key = K
(r
i
.h
i
)
I
N
.
Then the same steps for generation of the stamp is
followed as before for the pair {T
i
,W} .
During verification of the stamp, the social net-
working site performs all the steps as before to iden-
tify the user as I
N
. Once the user is identified, the
social network knows the shared secret S
I
N
and there-
fore can also re-create the key by performing the fol-
lowing operation:
Key =
¯
B
(S
I
N
.S
N
)
i
= (g
r
i
.h
i
)
(S
I
N
.S
N
)
= (g
S
I
N
.S
N
)
(r
i
.h
i
)
= K
(r
i
.h
i
)
I
N
The user I
N
can configure the minimal social dis-
tance that needs to be satisfied for the social network-
ing site to release this Key. If V
N
is within this social
distance then he receives the Key from social network
and decrypt the message T
i
.
6 CONCLUSIONS
We presented the concept of an anonymous social
stamp which can be assigned to anonymous state-
ments and help prove that the statement was made by
a particular member of an external social networking
site. Trust can then be derived based on the social
distance between the persons concerned: the person
who made the statement and the person verifying the
statement. A possible implementation of the concept
is shown with the existing infrastructure of RSA keys
already in use by social networking sites.
This should enable a serious health and well-ness
service provider to show testimonials, advices and
configurations which can be verified by new cus-
tomers to belong to people that they would consider
trustworthy based on their social distance within a
particular social network of their choice. Customers
can use any social network of their choice and trust.
Service providers would be able to use the trust that
people have created by the social networks without
having to create a social network of their own.
Additionally we extend the concept to hide infor-
mation that can be decrypted only by people within a
social distance.
REFERENCES
EC (2010a). European healthcare fraud & corrup-
tion network (ehfcn). http://www.ehfcn.org/fraud-
corruption/fraud-and-corruption-in-healthcare/.
EC (2010b). The unfair commercial practices directive di-
rective 2005/29/ec. http://ec.europa.eu/consumers/
rights.
Epinions (2010). http://www.epinions.com.
FTC (2010a). Federal trade commission: Health claims.
http://www.ftc.gov/bcp/menus/consumer/health.shtm.
FTC (2010b). Who cares? sources of infor-
mation about healthcare products and services.
http://www.ftc.gov/bcp/edu/microsites/whocares/
index.shtml.
Josang, A., Ismail, R., and Boyd, C. (2007). A survey of
trust and reputation systems for online service provi-
sion. Decis. Support Syst., 43(2):618–644.
Resnick, P., Kuwabara, K., Zeckhauser, R., and Friedman,
E. (2000). Reputation systems. Commun. ACM,
43(12):45–48.
Rivest, R. L., Shamir, A., and Adelman, L. (1978). A
method for obtaining digital signatures and public-
key cryptosystems. Communications of the ACM,
21(2):120–126.
SECRYPT 2010 - International Conference on Security and Cryptography
188
