
ANONYMOUS SERVICES
Enhancing End-user Privacy Exploiting Anonymous Networks
Giovanni Cabiddu, Emanuele Cesena and Davide Vernizzi
Dip. di Automatica e Informatica, Politecnico di Torino, Torino, Italy
Keywords:
Privacy, Anonymous service, Anonymous network.
Abstract:
The large number of online services poses serious problems to users’ privacy. The sole confidentiality of data
exchanged is not enough for complete privacy because an external observer may learn sensitive information
simply by observing the communication channel, even if it is not possible to access the actual data transmitted.
In this position paper, we propose a solution where user privacy is guaranteed by providing anonymous access
to the services. Our solution is based on a service gateway, an anonymous credential system, an authentication
protocol and an anonymous network. We designed the solution to be cost-effective and scalable; moreover,
we employ existing standard protocols whenever possible to facilitate development and deployment.
1 INTRODUCTION
In the last few years we have faced an increasing dif-
fusion of distributed services. In particular, taking
advantage of fast and reliable Internet connections,
the paradigm of cloud computing is gradually gaining
widespread acceptance. As usage of online services
grows, the privacy of the users becomes a big issue.
More and more people tend to upload, elaborate and
store online personal data such as emails, pictures and
contacts, but also appointments and medical data.
In this context, providing user anonymity is the
ideal solution for enhancing privacy, but in practice,
complete anonymity is difficult to achieve. Protect-
ing the confidentiality of data transmitted on a net-
work channel is fundamental for user privacy, but it
is not enough. Indeed, the sole knowledge that the
user accesses a particular service might disclose sen-
sitive information. For instance, let us consider a user
that repetitively accesses a medical service: an ex-
ternal observer may correlate the repetitive accesses
to some kind of medical problem (and possibly may
reveal this information to a medical insurance com-
pany) even without being able to observe the actual
traffic (e.g., due to a protected channel between user
and service).
We focus on network communication and in par-
ticular on the access to the services by proposing a
solution for enhanced user privacy based on anony-
mous services. We implement our solution basing it
on 1) a service gateway, 2) an anonymous credential
system 3) an authentication protocol and 4) an anony-
mous network.
Related Work. Basically, to achieve user privacy,
two different approaches are possible. The first pro-
tects the source (i.e. the user), while the latter at-
tempts to protect the destination (i.e. the service).
Source privacy protection is usually achieved by
means of anonymous networks. A plausible candidate
for an anonymous network is Tor (Dingledine et al.,
2004) since it is actually available and already used in
many applications. In these solutions, the anonymous
network is used to hide the user, anonymizing its net-
work connections.
On the other hand, we focus on destination pri-
vacy protection by using the anonymous network on
the service side, instead of the user side (cf. Sec. 4),
implying less requirements on the client’s platform.
Moreover, anonymity is usually provided by travers-
ing multiple nodes. While this provides anonymity
and ensures against a single attacker, it also greatly
reduces the bandwidth available, indeed, in networks
of this type, the bandwidth available is lesser or equal
to the minimal band offered by traversed nodes (Wen-
dolsky et al., 2007). By moving the anonymous net-
work to the services, we can expect the anonymous
network to exploit high-bandwidth nodes, therefore
leading to higher performance. Furthermore, we pro-
vide an access-control feature, both on users and ser-
vices, which is missing in anonymous networks such
as Tor.
221
Cabiddu G., Cesena E. and Vernizzi D. (2010).
ANONYMOUS SERVICES - Enhancing End-user Privacy Exploiting Anonymous Networks.
In Proceedings of the International Conference on Security and Cryptography, pages 221-225
DOI: 10.5220/0003032202210225
Copyright
c
SciTePress

There are other works that provide destination
protection. To our knowledge, SAGE (Lin et al.,
2009) is the one which has the most similar archi-
tecture to ours. However, we provide bidirectional
communication while SAGE only allows communica-
tion from user to service. In addition, we note that in
SAGE most of the security lies in a trusted authority
which may revoke user anonymity, while in our sce-
nario the trusted third party has a more limited role.
Technically speaking, both Tor and SAGE define
their own application protocols, while we make use
of standard protocols whenever possible. We believe
that this approach makes it easier to change the un-
derlying technology, thus increasing resiliency to spe-
cific attacks (e.g. eavesdropping by exit nodes in Tor).
Moreover, not being bound to a specific technology
leads to easier deployment, especially in corporate
scenarios. Finally, this choice supports heterogeneous
services which are based on different network tech-
nology.
In addition, anonymous network, another key
component of our solution is the anonymous creden-
tial system which is used to provide anonymous ac-
cess control. These (see, e.g. (Chaum, 1985; Ca-
menisch and Lysyanskaya, 2001)) are cryptographic
tools that allow users to obtain credentials from an
issuer and can use them to access services, but their
communication remains unlinkable even when the
services collude with the issuer. Building on such sys-
tems, it is possible to extend classical authentication
primitives to take into account the privacy aspects of
the users. A particular noteworthy anonymous cre-
dential system is the Direct Anonymous Attestation
(DAA) (Brickell et al., 2004): thanks to its flexibility
its usage has already been proposed in practical so-
lutions based on Transport Layer Security (TLS) and
IPsec (Balfe et al., 2005; Cesena et al., 2010).
Organisation. This work is organised as follows:
Sec. 2 describes our model and assumptions, while
Sec. 3 lists the requirements we want to fulfill. In
Sec. 4 we present our solution which implements
anonymous services. We conclude in Sec. 5.
A full version of this paper containing a more
elaborated discussion of the solution is available at
http://security.polito.it/tc/anon-services/.
2 MODEL AND ASSUMPTIONS
In this section we present the actors that play a role in
our solution, explaining their goals, and we describe
the underlying assumptions.
To describe our problem we introduce a model
which defines the following participants:
• Service (S
i
). This is an entity that offers a ser-
vice. Usually they are provided by companies or
organizations (e.g., banks, hospitals).
• User (U). This is any authorized entity that wants
to access the service S
i
.
• Router (R ). This is an entry point for U to the
Internet. It is controlled by the Internet Service
Provider chosen by U. It is capable of seeing all
the traffic generated and received by U.
• Introduction Points (IP). This is the set of entry
points for U to the service S
i
. Each of them allows
S
i
to be anonymously accessed, namely without
using a direct connection between U and S
i
.
• Gateway (G). This is a gateway which notifies
services that a user want to access a particular S
i
without disclosing any sensitive information.
The attacker is a third party that is able to read,
modify or drop messages between U and S
i
and col-
lect sensitive information. In addition, it can person-
ify one of the participants. It could be the Service
Provider that provides R or another entity which has
physical access to the network.
We base our solution on the following assump-
tions:
Anonymous Network (AN). A network capable of
providing anonymous connections to the services is
available. In particular this network allows a node
to connect to external entities so that no information
that may lead to its identification is revealed. Protec-
tion of privacy of data exchanged is easily provided
by a secure channel. On the other hand, preventing an
observer from gaining information by observing the
connection is much harder. Therefore, in this con-
text, we do not consider the data exchanged, but we
use the anonymous network to protect the information
that an external observer may extract by observing the
connection.
Hidden Services. The anonymous network allows
a node inside the network to offer services to external
entities anonymously. Using this feature, a service
inside AN, can be anonymously contacted by external
entities through some Introduction Points (IP).
Broadcasting. AN is capable of reliably delivering
broadcast messages to its nodes. This feature ensures
that any broadcast message sent by an external entity
is delivered to the nodes without specific delays that
may reveal which node has received the message.
SECRYPT 2010 - International Conference on Security and Cryptography
222

Network connection
Logical path
Anonymous
Network
Figure 1: Overview of the anonymous network (AN); a
generic user may contact a service using the related Intro-
duction Point (IP).
Trusted Computing Assumptions. Nodes that
compose the AN can be trusted platforms, equipped
with a trustworthy Trusted Computing Base (TCB) in-
cluding a Trusted Platform Module (TPM) (Trusted
Computing Group, 2007). The TCB protects criti-
cal data and access to authentication credentials from
remote attacks. Moreover, the TCB ensures the be-
haviour of some trusted components (e.g., network
stack) and is capable of vouching for the integrity of
the trusted components to external entities.
An abstract representation of this network is pro-
vided in Fig. 1.
3 REQUIREMENTS
We want to design a system capable of addressing the
following functional and security requirements:
User Privacy. A user U may connect to a certain
service S
r
being ensured that no one, except himself
and S
r
, is capable of discovering which service is ac-
cessed. This is the central requirement of this work.
Access Control. Only authorized services can ac-
cess the system. This means that a service that did not
correctly joined the system must not be able to pro-
vide its services (even if it collude with users). This
requirement leads to a business model for G where
services pay for joining the system.
Cost-effectiveness. The system is designed to be
cost-effective. In particular, since a single G serves
multiple users and services, its effort is required to be
minimal. This requirement increases the expectations
of deploying the system.
Compliance to existing Standards. Wherever pos-
sible, the system employs standard and diffused pro-
tocols. This requirement facilitates the integration
and the deployment of the system and makes its de-
velopment affordable.
Scalability. The system is designed to scale well to
a large number of users and services. This require-
ment is crucial since the anonymity level grows with
the number of services.
4 OUR SOLUTION
This section describes our solution in detail. A dis-
cussion on how the security requirements are fulfilled
and additional considerations on the feasibility of the
solution are presented in the full version of this paper.
Our solution is based on five network protocols
that lead to the establishment of an interaction be-
tween a user U and a required remote service S
r
in
a fashion so that no external entity can identify which
service is accessed by U.
Service-initiated Protocols. Before any interaction
with U may happen, S
r
must join the system. In order
to do this, it runs the following protocol:
• Join: This protocol is run between a service S
i
and G and results in the admittance of S
i
to the
group of allowed services. During this phase S
i
fulfils the conditions required by G (e.g., pay-
ment). Moreover, G and S
i
set up all the creden-
tials required by the anonymous credential system
used. In the case of a DAA-based anonymous cre-
dential system, this phase corresponds to the DAA
Join protocol.
User-initiated Protocols. For accessing the re-
quired service S
r
, U runs the following protocols:
• Setup: This protocol is run between U and the
required service S
r
and results in an agreement
between U and S . The two participants ex-
change a shared secret that will be used later in the
Wake − up and the Authentication protocol.
In the shared secret lies most of the privacy of
our solution and, therefore, it must be strongly
protected; for simplicity, we consider this proto-
col out-of-band. However, this protocol strongly
depends upon the type of service offered by S
r
.
For instance, it is possible to conceive an online
shared secret distribution (based on a TTP), as
long as it still provides the same level of privacy
and confidentiality.
• Wake − up: This protocol is run among U, G
and S and results in a notification to S
r
that U
requires access. During this protocol, U sends
an authentication request for the service S
r
to G
who will then broadcast the request to the ser-
vices associated; the correct S
r
is, hence, informed
ANONYMOUS SERVICES - Enhancing End-user Privacy Exploiting Anonymous Networks
223
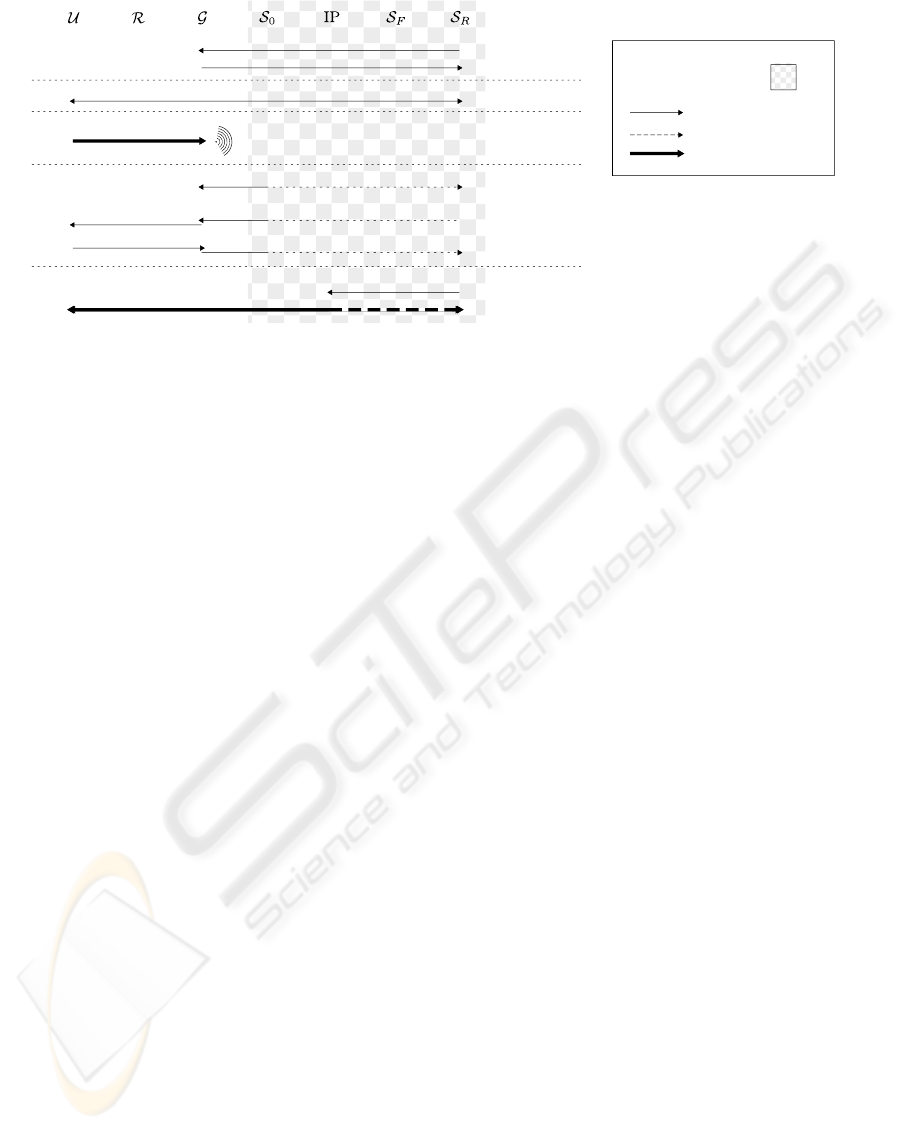
Register + DAA Join
Anonymous credentials
Out-of-band: establish shared secret
Wake-up ID
Authenticates using anonymous credential system
Access Request(with list of IP)
AR (with IP)
JOIN
SETUP
SERVICE
WAKE-UP
SERVICE
AUTHENTICATION
Access Response (with selected IP)
Access Response (with selected IP)
AN: open anonymous service
Service accessService access
HIDDEN SERVICE
ACCESS
Broadcast
ID
Anonymous connections
Normal connections
Protected connections
IP: Introduction Point
AN: Anonymous Network
Figure 2: Our solution to provide anonymous services: details on the five protocols involved.
that U is requiring access and can prepare for the
Authentication phase. We anticipate that the
authentication request sent by U derives from the
shared secret established in the Setup phase (e.g.,
by using hash functions).
• Authentication: This protocol is run between
S
r
and U and results in the authentication of the
service and in a session key which will be used
in the Access phase; note that this session key
must depend on the shared secret exchanged in the
Setup.
In this protocol G acts as a pass-through entity
which forwards messages between S
r
and U. Be-
fore allowing S
r
to proceed to the next phase, G
exploits the anonymous credential system to ver-
ify that S
r
is one of the services entitled to use the
service. During this protocol, S
r
authenticates to
U. Moreover, it provides this latter with a list of
possible Introduction Points (IP) that can be used
to contact S
r
through the anonymous network and
U replies, specifying the chosen IP.
A common choice for authentication protocol in
point-to-point scenarios is EAP: in EAP a suppli-
cant uses an authenticator to access an authentica-
tion server. In our case S
r
acts as EAP supplicant,
G as authenticator and U as authentication server.
• Access: In this phase U connects to S
r
through
the IP previously specified. The channel between
U and S
r
is protected with the shared key previ-
ously negotiated and is anonymised by the anony-
mous network.
In Fig. 2 we provide an example of the five pro-
tocols where DAA is used as anonymous credential
system and EAP is used as authentication.
5 CONCLUSIONS
In this paper we present a novel proposal for enhanc-
ing user privacy by anonymizing the services that are
used by users. Indeed, we claim that an external ob-
server may derive a lot of information about a user by
only inspecting his communication, even when this is
protected by cryptographic means. We propose a so-
lution which can be adapted to existing technology,
indeed, we assume that an anonymous network ca-
pable of providing hidden services is present and we
build our solution on top of this, but we do not as-
sume any specific anonymous network. Furthermore,
we assume that if an anonymous credential system is
available, we can provide access control, but, again,
we do not require any specific technology.
REFERENCES
Balfe, S., Lakhani, A. D., and Paterson, K. G. (2005). Se-
curing peer-to-peer networks using Trusted Comput-
ing. In Trusted Computing, pages 271–298. IEEE
Press.
Brickell, E., Camenisch, J., and Chen, L. (2004). Direct
Anonymous Attestation. In CCS’04, 11th ACM Con-
ference on Computer and Communications Security,
pages 132–145. ACM Press.
Camenisch, J. and Lysyanskaya, A. (2001). An efficient
system for non-transferable anonymous credentials
with optional anonymity revocation. In Advanced in
Cryptology – EUROCRYPT 2001, volume 2045 of
LNCS, pages 93–118. Springer.
Cesena, E., L
¨
ohr, H., Ramunno, G., Sadeghi, A.-R., and
Vernizzi, D. (2010). Anonymous authentication with
TLS and DAA. In To appear in TRUST 2010, 3rd
International Conference on Trust and Trustworthy
Computing.
SECRYPT 2010 - International Conference on Security and Cryptography
224

Chaum, D. (1985). Security without identification: Trans-
action systems to make big brother obsolete. Com-
mun. ACM, 28(10):1030–1044.
Dingledine, R., Mathewson, N., and Syverson, P. (2004).
Tor: The second-generation onion router. In 13th
USENIX Security Symposium, pages 303–320.
Lin, X., Lu, R., Shen, X., Nemoto, Y., and Kato, N. (2009).
SAGE: a strong privacy-preserving scheme against
global eavesdropping for ehealth systems. IEEE J. on
Sel. Areas Comm., 27(4):365–378.
Trusted Computing Group (2007). TPM main spec-
ification level 2, version 1.2, revision 103.
https://www.trustedcomputinggroup.org/.
Wendolsky, R., Herrmann, D., and Federrath, H. (2007).
Performance comparison of low-latency anonymisa-
tion services from a user perspective. In PET 2007,
7th International Symposium on Privacy Enhancing
Technologies, volume 4776 of LNCS, pages 233–253.
Springer.
ANONYMOUS SERVICES - Enhancing End-user Privacy Exploiting Anonymous Networks
225
