
WATERMARKING OF COMPRESSED VIDEO BASED ON DCT
COEFFICIENTS AND WATERMARK PREPROCESSING
Samira Bouchama
Research Center on Scientific and Technical Information,5 rue des trois freres Aissou, Ben Aknoun, Algiers, Algeria
Latifa Hamami
National Polytechnic School, 10 Hassen Badi Avenue, BP 182, El-Harrach, Algiers, Algeria
Hassina Aliane
Research Center on Scientific and Technical Information,5 rue des trois freres Aissou, Ben Aknoun, Algiers, Algeria
Keywords: Video watermarking, H.264/AVC standard, Quantized DCT coefficients, Intercorrelation function.
Abstract: Considering the importance of watermarking of compressed video, several watermarking methods have
been proposed for authentication, copyrights protection or simply for a secure data carrying through the
Internet. Applied to the H.264/AVC video standard, in most of cases, these methods are based on the use of
the quantized DCT coefficients often experimentally or randomly selected. In this paper, we introduce a
watermarking method based on the DCT coefficients using two steps: the first one consists in a watermark
pre-processing based on similarity measurement which can allow to adapt the best the watermark to the
carrying coefficients of low frequencies. A second step takes advantage from the coefficients of high
frequencies in order to maintain the video quality and reduce the bitrate. Results show that it is possible to
achieve a very good compromise between video quality, embedding capacity and bitrate.
1 INTRODUCTION
Today, with the progress in network services and
multimedia applications, the interest of
watermarking compressed documents is becoming
more and more important due to the easy
transmission of data and all the issues that follow.
With the availability of video sharing and
dissemination services through Internet, it becomes
important to develop appropriate tools for
authentication or copyright protection or just to offer
a secure data transmission service without using
additional channels.
Indeed, dealing with compressed video, several
watermarking methods have been proposed for the
H.264/AVC, the newest video coding standard
which is known for its coding
efficiency (Richardson, 2003), ( ITU-T, 2005).
These methods generally use the motion vectors or
the quantized discrete cosine transform (DCT)
coefficients in order to propose fragile or robust
video watermarking solutions.
Most of methods that use the DCT coefficients
exploit the human visual properties to reduce the
degradation caused by the watermark embedding.
This degradation is propagated by the inverse
quantization and the inverse DCT operations at the
decoding step, and also by the Intra and Inter
predictions. Thus, the video quality can be improved
by selecting the appropriate areas that respond to
some constraints such as embedding the watermark
according to the choice of the coding mode or other
DCT blocks’ properties.
In this context, we have worked on designing a
watermarking method for the video codec
H.264/AVC, useful for video authentication in order
to ensure the protection of data against unauthorized
modification, to check credibility and the origin
source of the video and respond this way to the need
for reliable information.
114
Bouchama S., Hamami L. and Aliane H..
WATERMARKING OF COMPRESSED VIDEO BASED ON DCT COEFFICIENTS AND WATERMARK PREPROCESSING.
DOI: 10.5220/0003321601140119
In Proceedings of the International Conference on Imaging Theory and Applications and International Conference on Information Visualization Theory
and Applications (IMAGAPP-2011), pages 114-119
ISBN: 978-989-8425-46-1
Copyright
c
2011 SCITEPRESS (Science and Technology Publications, Lda.)

However, video watermarking methods cannot
be designed without thinking of three important
constraints: embedding capacity, video quality, and
video bitrate. Our main motivation, though, is to
arrive at a compromise between these constraints
and if possible reduce the bitrate for a better use
within the network applications.
The idea of decreasing the bitrate was suggested
in (Wang and Hsu, 2008) where the authors
proposed a fragile watermarking algorithm for JPEG
image, based on modifying the last nonzero
coefficient in each DCT quantized block. The
proposed algorithm provides an authentication
capability, and decreases the size of JPEG
compressed-domain images with no visual impact.
Our proposal is based on the quantized
significant DCT coefficients where both of the
coefficients of low and high frequencies are used in
order to obtain a sufficient embedding capacity and
maintain or reduce the bitrate. A watermark
preprocessing is performed by applying a rotation
several times in order to find the best position of the
watermark in the video and maintain the video
quality.
In the next section we describe the different
stages of our method. Results are presented in
section 3. Finally, we give the conclusion in
section 4.
2 RELATED WORK
Several watermarking methods based on the DCT
coefficients and watermark preprocessing were
proposed for the H.264/AVC video codec (figure 1).
However, they are different in the choice of the
block and the DCT coefficients for the watermark
embedding and in the appropriate watermark
processing. The aim is to respond to the application
needs in terms of robustness or fragility, video
quality and bitrate. Among these works, Quan and
Hong (2008) proposed a real time video
watermarking method based on the low frequencies
DCT coefficients features in I frame on H.264 to
generate the watermark information. Middle
frequencies of 4x4 DCT blocks are used to embed
the watermark, and the blocks with a DC coefficient
equal to zero are avoided; the aim is to maintain the
compromise between robustness and invisibility.
Chen, Lai and Chang (2009) proposed a video
watermarking method based on two algorithms for
low and high energy blocks of Intra frame in order
to consider the high frequency noise attack and the
low-pass filter attack. The watermark is
preprocessed by an encryption using a
Torus
Automorphisms algorithm and the Secret Image
Sharing technology to increase robustness.
Another robust video watermarking scheme is
based on the choice of one middle frequency in the
4x4 DCT blocks for the embedding process. In order
to accommodate the computational complexity of
the video codec, the 2 D 8 bits watermark undergo a
preprocessing based on five steps (DCT
decomposition and zigzag scanning, normalization,
frequency masking, transformation, reduction of the
level) transforming it to a simple 1D sequence
(
Zhang, Ho, Qiu and Marziliano, 2007).
Figure 1: General scheme of embedding watermark in
DCT coefficients of the H.264 video codec.
Our method is also based on the quantized
significant DCT coefficients where two coefficients
are used per block: the coefficients of low
frequencies would ensure the necessary embedding
capacity for the application, and the coefficients of
high frequencies would reduce the bitrate and
maintain the video quality. Embedding the
watermark is performed after an initial step which
consists in preprocessing the Watermark by applying
a rotation several times and calculating each time the
intercorrelation coefficient between the watermark
signal and the carrying coefficients transformed to a
binary signal. The aim is to find the best position of
the watermark in the video so that the introduced
distortion is reduced.
3 DESCRIPTION OF THE
METHOD
3.1 Embedding Position and Formula
In a first step, we choose among the significant
quantized DCT coefficients, the position of the
coefficients which would carry the watermark.
Choosing the low frequencies would allow to satisfy
the embedding capacity required for the application,
thus, to embed the watermark, the significant
coefficients in position k= 4 according to the zigzag
scan, are selected as illustrated in figure 2.
Input
signal
(Macroblock)
Watermark
Watermark
pre-
processing
Prediction
(Intra/inter)
Transf.
(Integer DCT)
and Quant.
Entropy
coding
Bit-
stream
WATERMARKING OF COMPRESSED VIDEO BASED ON DCT COEFFICIENTS AND WATERMARK
PREPROCESSING
115
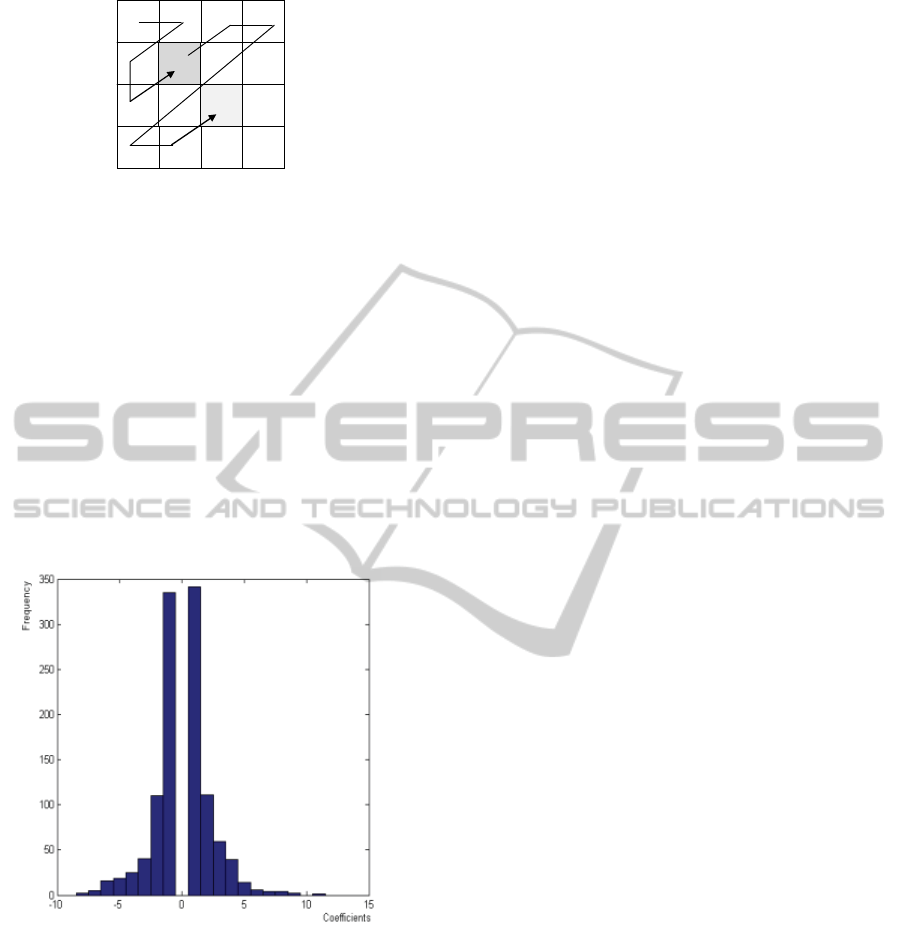
Figure 2: A zigzag scan in a block of DCT coefficients.
Coefficients equal to 1 are not used because of
the serious increase in bitrate they may cause. This
is because 1 have a special processing in the
entropy coding stage of the video codec
(Richardson, 2003). The DC coefficients are avoided
because of the high degradation they may introduce,
as well as the high frequencies coefficients because
they are mainly composed from values equal to 0
or 1.
In this case the majority of coefficients planned
for embedding the watermark would be even
coefficients. An example of a video histogram of
significant DCT coefficients of the position k = 4 is
given in figure 3.
Figure 3: Histogram of the quantized significant DCT
coefficients of position k=4 of Container sequence.
For the embedding process, simple methods are
preferred such as the Least Significant Bit (LSB)
method, in which the LSB of the coefficient is
replaced by the watermark bit. That means that the
bit 0 is preferebly embedded in an even value in
order not to change the original value of the
coefficient. However , the watermark may be
composed of bits “1” more than “0”, and because we
deal with more even coefficients than with odd ones
as mentionned previousely; it may be better to
change the embedding formula so that the LSB of
the coefficient is replaced, not by the watermark bit,
but by its complement. In this case we need to
reserve one bit during the embedding process to
know wich formula has been used.
3.2 Watermark Pre-processing
We suppose that our watermark has been encrypted
to ensure its security. Our objective is to find the
best transformation of the watermark in order to
correspond - as much as possible- the bits “0” to
even coefficients and the bits “1” to the odd ones.
To do so, we apply a rotation by one several
times to the watermark. In each rotation, the last bit
of the watermark becomes the first one and in each
time we calculate the intercorrelation coefficient
between the watermark signal (W) and the
coefficients (transformed to binary signal C).
Considering W and C two binary sequences of
the same length N:
W={W1=1, W2, .. , WN}, C={C1=1,C2,.. , CN}.
The intercorrelation function for positive delays
is given by:
(
,
)
=
∑
, = 0,1,2, … , − 1 (1)
In our case d=0.
To clarify this point an example is given:
Let’s consider the sequences of dimension N= 8.
C
4
is composed from coefficients of position k=4 in
the block and W is the Watermark.
C
4
={2, -3, 6, 4, 5, 2,-2,3}, W={0,0,1,0,1,1,0,1}.
The preprocessing consists in the following
steps:
- C
4
is replaced by the binary sequence :
C’
4
= {1,-1,1,1,-1,1,1,-1}, 1 for even coefficients
and -1 for odd coefficients.
- If we consider that the bit 0 is preferably
embedded in an even coefficient, we transform
the watermark W to W1={1,1,-1,1,-1,-1, 1,-1} ,
where the bit 1 replaces 0 and -1 replaces 1, then
we apply a rotation (N-1) times to obtain:
W2={-1,1,1,-1,1,-1,-1, 1 },
W3={1,-1,1, 1,-1,1, -1, -1},
…,
W8= {1,-1,1,-1,-1, 1,-1,1}.
The highest value of the correlation coefficient is
given for W3 or W6 (Cor = 6). The watermark
corresponding to W3 is: W’={0,1,0,0,1,0,1,1}.
After the embedding process (using the LSB
method) the watermarked DCT coefficients become
Cw
4
={2, -3, 6,4,5,2,-3,3} where only one coefficient
is modified. Besides, we can check that if we had
k=0
k=4
k=11
IMAGAPP 2011 - International Conference on Imaging Theory and Applications
116

embedded the signature without preprocessing we
would have about four coefficients modified in the
sequence
C
4
.
During the embedding process we need to
reserve coefficients to save the rotation dimension
(three, in the example) so that we can deduce W
from W’ at the detection stage. Of course, the
reserved coefficients won’t be involved in the
intercorrelation calculation. In our case, their
number is experimentally estimated to 11
coefficients.
3.3 Video Quality Improvement
and Bitrate Reduction
After the watermark preprocessing and the
embedding process as described in the previous
section, the coefficients of C
4
for which the
watermark bits are causing a modification, are
restored to their initial value after modifying the
coefficients of position k=11 (C
11
) instead of C
4
.
The modification consists of transforming all the
coefficients of the position k=11 to even values for
those corresponding to the unchanged coefficients
C
4
, and C
11
become odd for those corresponding to
the coefficients of C
4
supposed to be modified by the
bit embedding. The idea is to exploit C
11
to make the
difference between the unchanged coefficients and
the restored ones, and because of the position of C
11
comparing to C
4
in the block (figure 2), we expect
that the modification of C
11
would introduce a
smaller degradation.
The only coefficients of C
4
that won’t be
restored are those corresponding to the coefficients
C
11
=0. The embedding and extracting processes are
presented in the next section.
3.4 Watermark Embedding/ Extracting
Embedding and extracting the watermark may be
summarized as follows:
- Extract the sequence of M significant DCT
quantized coefficients used for the
watermarking, and transform it to a binary
signal composed of 1.
- Reserve about 12 bits for the additional
information.
- Apply the watermark preprocessing:
Transform the watermark signal W (composed of 0
and 1) to binary signal composed of 1.
Apply a rotation (N-1) times, with N= M-12, and
calculate the correlation coefficient between the
watermark and the binary signal representing the
coefficients, using the formula (1).
Deduce the new watermark W’ to embed from the
rotation dimension giving the highest
intercorrelation coefficient.
The embedding and extracting algorithms are
given bellow:
Cw
4
(i) is the i
th
watermarked coefficient and 0≤i<N.
The variables:
Restore1, Restore2, Restore3, Restore4,
NoRestore, initialized to 0, are introduced to identify
the cases where the coefficients of C
4
are changed or
not. “abs” is the absolute value and “mod” is the
modulo operation.
if (k=4 and abs(C
4
(i))≠ 1) then
{
if (C
4
(i) > 0 ) then { if (C
4
(i) mod 2=1)
then {if (W’(i)=0) then { Cw
4
(i)= C
4
(i) – 1,
Restore1=1}
else {Cw
4
(i) = C
4
(i) ,
NoRestore=1}}
else {if (W’(i)=1) then {C w
4
(i)= C
4
(i) + 1,
Restore2=1}
else {Cw
4
(i)= C
4
(i) , NoRestore=1
}}
}
if (C
4
(i) < 0 ) then { If (abs(C(i)) mod 2=1)
then {if (W’(i)=0) then {Cw
4
(i) = C (i) + 1,
Restore3=1}
else {Cw
4
(i)= C
4
(i) , NoRestore=1
}}
else {if (W’(i)=1) then { Cw
4
(i) = C(i) – 1,
Restore4=1}
else {Cw
4
(i) = C
4
(i) , NoRestore=1
}}
}
}
Concerning the values of C
11
, they are
transformed to even or odd values depending on the
modifications that the coefficients of C
4
have
undergone. The coefficient C
4
(i) is then restored if
it has been changed unless C
11
(i) was initially equal
to 0. The corresponding algorithm is the following:
if (k=11) then
{
if (NoRestore = 1 and C
11
(i)> 0) then
{ if (C
11
(i)
mod
2 =0 ) then Cw
11
(i)
= C
11
(i),
else Cw
11
(i)
= C
11
(i) - 1 }
if (NoRestore = 1 and C
11
(i)< 0) then
{if (abs(C
11
(i)) mod 2 =0) then Cw
11
(i) = C
11
(i) ,
else Cw
11
(i)
= C
11
(i) + 1}
if (Restore1 = 1 or Restore2 = 1 or Restore3 = 1
or Restore4 = 1) then
{
if ((C
11
(i)) > 0) then
{ if (C
11
(i)
mod 2 =1 ) then Cw
11
(i) = C
11
(i),
else Cw
11
(i)= C
11
(i)- 1 }
if ((C
11
(i)) < 0) then
WATERMARKING OF COMPRESSED VIDEO BASED ON DCT COEFFICIENTS AND WATERMARK
PREPROCESSING
117
{ if (abs(C
11
(i)) mod 2 =1) then Cw
11
(i) = C
11
(i) ,
else Cw
11
(i)= C
11
(i)+ 1}
}
if (Restore1=1 or Restore4=1) then Cw
4
(i) = Cw
4
(i) +1
if (Restore2=1 or Restore3=1) then Cw
4
(i)= Cw
4
(i)-1
}
For the detection stage, the coefficients C
4
(i) and
C
11
(i) are first extracted. The even values of C
11
correspond to the cases where the watermark bits
didn’t introduce a modification in C
4
or they may be
a modification in case C
11
(i)=0, in this case the
watermark bit corresponds to the LSB of the
coefficient C
4
(i). For odd values of C
11
, the
watermark bit corresponds to the complement of the
LSB of the coefficient C
4
(i). The corresponding
algorithm is:
for i=0 to N do
{
if ( abs(Cw
11
(i)) mod 2 = 0)) then
{if (abs(Cw
4
(i)) mod 2 = 0) then W’(i)=0 else W’(i)=1 }
if ((abs(Cw
11
(i)) mod 2 = 1)) then
{if (abs(Cw
4
(i)) mod 2 = 1) then W’(i)=0 else W’(i)=1 }
}
W is then deduced from W’. The 12 bits
containing the additional information used for
reconstructing the watermark (see section 3.1 and
3.2) are embedded in 12 blocks reserved for that
aim, in low frequencies using the LSB method, and
extracted using the expression:
if (abs(C
4
(i)) mod 2 = 0) then W(i)=0 else W(i)=1.
4 RESULTS AND ANALYSIS
In this section we present the experimental results
obtained by applying our watermarking proposal to
various CIF video sequences including Walk,
Bridge, Flower, Coast guard, Foreman (with
Siemens logo) and Container. Using the base-line
profile, the first 50 frames of the video clips are
coded at the quantizer parameter (Qp=28), at a frame
rate of 30 pictures/s. The proposed watermarking
algorithm has been integrated into the H.264 JM
reference software.
The watermark used for tests is a pseudo random
binary sequence which is embedded only in the first
frame (Intra coded frame) of the video clip. The
objective is to assess the impact of the watermark
embedding on the video quality and the bitrate.
Results corresponding to the embedding capacity,
the average of PSNR of 50 frames and the bitrate are
tabulated in table 1.
The embedding capacity depends on the picture
content and the choice of the coefficients used for
embedding the watermark (C
4
in our case). It varies
between 174 and 1484 bits/ I frame corresponding to
sequences of Foreman and Flower respectively. We
recall that in this embedding capacity there are about
12 bits reserved to carry information about the
watermark (such as the rotation dimension, the
embedding formula) and are necessary for its
recovery; this is why it is important to ensure that
the remaining embedding capacity is enough for the
application.
In table 1 is also reported the average of PSNR
of the 50 coded frame of the test sequences. The
reduction in PSNR varies between 0.73 and 3.38 dB
corresponding to Flower and foreman respectively.
However, for all the test sequences, the
subjective quality is preserved and maintained
throughout the frames as presented in an example of
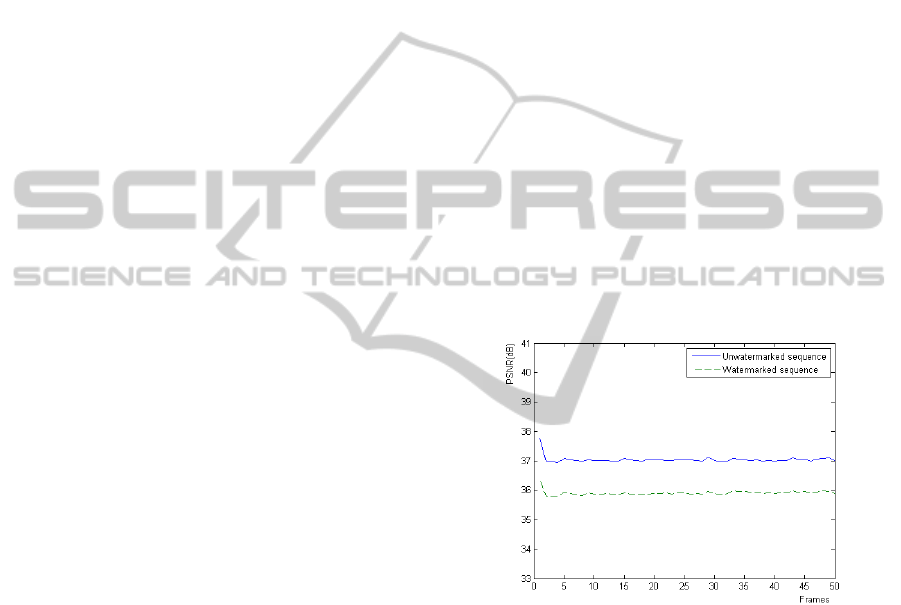
the PSNR graph of Bridge sequence in figure 4.
Figure 5 shows three examples of unwatermarked I
frames and the corresponding watermarked frames.
Figure 4: PSNR of unwatermarked and watermarked
Bridge sequence.
Regarding the bitrate, it is maintained or reduced
in most of cases and the most important reduction in
bitrate is 0.91 kbit/s observed for Flower sequence.
This was expected because of the formula used
to transform the odd values of C
11
to even values.
Indeed, the reduction of the coefficients “C
11
(i)= 1”
to the value “0” is responsible of this reduction of
the bitrate. Fortunately, it was possible to maintain
the video quality because the number of the
significant coefficients of C
11
remains limited and
both of the coefficients of low and high frequencies
were involved in the embedding process.
The proposed scheme may be considered as a semi
fragile one because the watermark is being
embedded during compression it is not easy to erase
IMAGAPP 2011 - International Conference on Imaging Theory and Applications
118

it from the video stream and preserve the file
content. Indeed any attack of the stream would cause
an error in the decoding stage. However, if the
watermarked video stream is decoded and re-
encoded the watermark is lost which
wouldconstitute a proof of the file manipulation
while checking the authenticity.
Table 1 : The PSNR, the bitrate and the embedding
capacity of the test sequences.
Sequences / Embedding
Capacity (Bits /I frame)
a. Unwatermarked seq.
b. watermarked seq.
Average
PSNR
(dB)
of 50 frames
Bitrate
(kbits/s)
Walk / 295
a 39.05 1111.15
b 36.41 1111.15
Bridge / 301
a 37.04 515.65
b 35.90 515.44
Flower / 1484
a 36.63 1457.63
b 34.78 1456.67
Coast guard /
315
a 38.33 1339.66
b 37.54 1339.65
Foreman / 174
a 39.65 365.02
b 36.27 364.84
Container / 457
a 39.02 186.43
b 36.91 186.30
5 CONCLUSIONS
This paper describes a video watermarking method
applied to the video codec H.264/AVC. The
objective was to embed data in the video with the
necessary amount of information for the video
authentication. The watermarking process should
preserve the video quality and reduce the bitrate
which would constitute a boon for network
applications.
The proposed method combines between the use
of low and high frequencies to achieve a good
compromise between the embedding capacity, the
video quality and the bitrate. A watermark
preprocessing helps considerably in improving the
video quality.
Promising results have been obtained, however,
while preserving this bitrate and quality, it would be
interesting to increase the embedding capacity
exploiting additional DCT coefficients and involving
the P and B frames in the watermarking process. It is
in this sense that our future work will focus.
Figure 5: (a), (b) and (c) are the I frames of the
unwatermarked sequences of Foreman, Container and
Flower respectively and (a’), (b’) and (c’) are the
corresponding watermarked frames respectively.
REFERENCES
Chen, W-M., Lai, C-J., Chang, C-C., 2009, H.264 video
watermarking with secret image sharing. In BMSB
'09, IEEE International Symposium on Broadband
Multimedia Systems and Broadcasting Bilbao, Spain,
pp. 1-7 .
ITU-T, 2005, Recommendation H.264: Advanced video
coding for generic audiovisual services.
Quan, L., Hong, L., 2008, Robust video watermarking
algorithm based on H.264. In WICOM’08, IEEE 4
th
International Conference on Wireless
communications, Networking and Mobile Computing,
Dalian, China, pp. 1-3.
Richardson, I. E. G., 2003, H.264 and Mpeg-4 video
compression: video coding for next-generation
multimedia, Wiley.
Wang, C-C., Hsu, Y-C. , 2008, New watermarking
algorithm with data authentication and reduction for
JPEG image. J.Electron. Imaging, vol. 17, pp.1-8.
Zhang, J., Ho, A. T. S., Qiu, G., Marziliano,P., 2007,
Robust video watermarking of H.264/AVC. In IEEE
transactions on circuits and systems II: express briefs,
vol. 54, no. 2, pp. 205-209.
(a)
(b)
(a’)
(b’)
(c)
(c’)
WATERMARKING OF COMPRESSED VIDEO BASED ON DCT COEFFICIENTS AND WATERMARK
PREPROCESSING
119
