
CONTEXT BASED WATERMARKING OF SECURE JPEG-LS
IMAGES
A. V. Subramanyam and Sabu Emmanuel
School of Computer Engineering, Nanyang Technological University, Singapore, Republic of Singapore
Keywords:
Compressed domain watermarking, Context based watermarking, JPEG-LS watermarking.
Abstract:
JPEG-LS is generally used to compress bio-medical or high dynamic range images. These compressed images
sometime needs to be encrypted for confidentiality. In addition, the secured JPEG-LS compressed images
may need to be watermarked to detect copyright violation, track different users handling the image, prove
ownership or for authentication purpose. In the proposed technique, watermark is embedded in the context of
the compressed image while the Golomb coded bit stream is encrypted. The extraction of watermark can be
done during JPEG-LS decoding. The advantage of this watermarking scheme is that the media need not be
decompressed or decrypted for embedding watermark thus saving computational complexity while preserving
the confidentiality of the media.
1 INTRODUCTION
The digital media is often embedded with watermarks
for various purposes such as fingerprinting, copyright
violation detection, proof of ownership, authentica-
tion and tamper proofing. And is often distributed in
a secured manner, for e.g in Digital Rights Manage-
ment (DRM) Systems or Clinical Information Sys-
tems (CIS). High dynamic range images in DRM
systems, and Biomedical images in CIS systems are
generally compressed using JPEG-LS. JPEG-LS is
commonly used to compress these images as the
compression efficiency is better and also facilitates
near-lossless compression than JPEG and JPEG2000
(Fang, 2009).
In DRM systems, the media providers often
compress the media and distribute it after encrypt-
ing the compressed media via multilevel distributors
(Thomas et al., 2009). In the distribution process the
media is transmitted from owners to the consumers
through different level of distributors. In this sce-
nario, the distributors are entitled only to distribute
the compressed encrypted media to the end user and
as such cannot access the plain content (un-encrypted
content). Distributors request the license server in
the DRM system to distribute the associated licence
containing the decryption keys to open the encrypted
content to the consumers. However, each distributor
sometime needs to watermark the content for traitor
tracing or proving the distributorship. Thus they need
to watermark in the compressed encrypted domain it-
self.
In biomedical field, CIS often manages the pa-
tient related media in a compressed and confidential
way in different Healthcare Establishments (Blobel,
2004). In such a communication, different patient
records can be shared between different profession-
als either for subject’s treatment purpose or for a case
study. Thus it becomes necessary to preserve the con-
fidentiality of the distributed media, to prove the own-
ership and also track the user who is dealing with the
record. Therefore the watermark needs to be inserted
in the secured compressed media itself.
In this paper we focus on robust watermarking for
copyright violation protection and fingerprinting. Al-
though a robust irreversible watermark can be used
for this purpose but it degrades the quality of the im-
age which is not desirable in the applications spec-
ified above. Therefore it should be watermarked in
such a domain which does not create any undesir-
able distortion in the image. In literature some of
the irreversible algorithms have been proposed for en-
crypted domain watermarking in general, and also for
watermarking of JPEG-LS. In (Caldelli et al., 2006),
Caldelli et. al. proposed a watermarking scheme for
authentication using the prediction error of the pixels
during JPEG-LS encoding . Some techniques have
been proposed where watermarking is done on cer-
161
Subramanyam A. and Emmanuel S..
CONTEXT BASED WATERMARKING OF SECURE JPEG-LS IMAGES.
DOI: 10.5220/0003446201610166
In Proceedings of the International Conference on Signal Processing and Multimedia Applications (SIGMAP-2011), pages 161-166
ISBN: 978-989-8425-72-0
Copyright
c
2011 SCITEPRESS (Science and Technology Publications, Lda.)

tain subbands/bitplanes while encrypting certain other
subbands/bitplanes (Cancellaro et al., 2008), (Lian
et al., 2006). Some of the encrypted domain algo-
rithms are proposed in (Bianchi et al., 2010), (Piva
et al., 2010), (Zhao et al., 2010), (Katzenbeisser et al.,
2008). However, these algorithms cause irreversible
distortion which might not be desirable especially in
case of biomedical images. Thus, here we propose
a technique for watermarking of encrypted JPEG-LS
compressed images, where the compressed bitstream
is encrypted while watermark is embedded using con-
texts (explained in section 2). This paper is organized
as follows. Section 2 gives the preliminaries. In sec-
tion 3, we present the embedding and detection pro-
cess. We discuss the experimental results in section 4.
Section 5 concludes the paper.
2 PRELIMINARIES
In this section we briefly discuss the JPEG-LS com-
pression algorithm (Weinberger et al., 2000), and the
challenges in watermarking a compressed-encrypted
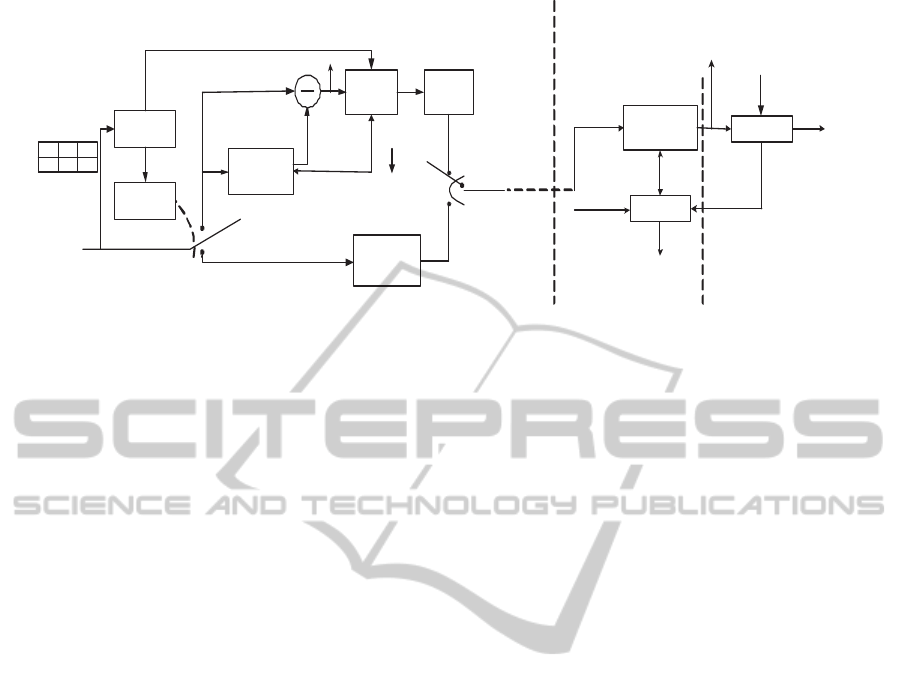
JPEG-LS image. In figure 1-a, an initialcontext is
computed in the Gradient block using the pixels a,
b, c and d. This initialcontext is a positive quantity
and is mapped into equal negative and positive values
using a classmap. For e.g., let the initialcontext be
denoted as Q ∈ [0,728] (Weinberger et al., 2000). Let
us denote Q
neg
∈ [−1, −364] and Q
pos
∈ [1, 364] and
let classmap f (.) denote the function which maps Q
to Q
neg
or Q
pos
or 0, i.e, f : Q → {Q
pos
,Q
neg
,0}. In
the regular mode, the current sample x is predicted in
Predictor block using a finite past pixel set compris-
ing of pixels a, b and c. Generally the fixed prediction
has some bias in it which is canceled out using the
context in which pixel occurs. Finally, the prediction
residual between the corrected (bias canceled) pre-
dicted value and the original pixel is Golomb coded.
Further each pixel (of a M x N image) occurs under
Q
px[ j]
∈ {Q
pos
,Q
neg
,0} while encoding, where px[ j]
denotes the pixel at position j, ∀ j = 1, 2, ..., M x
N and Q
px[ j]
denotes its context. Also, the Golomb
coded bit stream can be encrypted using a secure ci-
pher scheme such as RC4 (Schneier, 1996) for confi-
dentiality, which can then be distributed.
Now, modifying such a randomized bitstream
to insert watermark faces certain limitations. The
Golomb coded bitstream is highly sensitive to bit er-
rors. Even if one bit gets corrupted, the rest of the
decoding can be compromised. Therefore, we choose
the context of the encoded image for embedding wa-
termark without requiring any decryption or decom-
pression. Next we discuss the proposed algorithm.
3 PROPOSED ALGORITHM
The proposed algorithm involves encryption of
Golomb coded bit stream while embedding water-
mark through context. Encryption is performed on the
output bit stream of JPEG-LS compression (figure 1-
a). The encryption algorithm that we propose to use
is RC4 cipher (Schneier, 1996). The encryption does
not result in any increase in compressed file size as
the encryption is done using a stream cipher. The en-
crypted bit stream along with classmap f and context
frequencies is sent to the watermark embedder (figure
1-b) where the watermark embedding takes place.
The first step in watermarking process involves
finding the frequency or number of occurrences of
each context Q ∈ Qpos. Then according to the dy-
namic range of highest frequency contexts, the wa-
termark signal is divided into smaller length seg-
ments. Further Euclidean distance between the se-
lected contexts against the watermark segments is
computed. The contexts which give minimum dis-
tance will represent watermark information. Finally
contexts involved in computing Euclidean distance
are exchanged with the other contexts which does not
belong to highest occurring contexts. The main pur-
pose behind selecting highest occurring contexts is
that the higher the dynamic range, the more number of
watermark signal bits can be embedded. We describe
the watermark embedding procedure next.
3.1 Embedding Process
Let Q
p
j
∀ j = 0, 1, ....,L − 1 be the L highest occur-
ring contexts which are selected from Q
pos
for Eu-
clidean distance criteria. Here, L is chosen such that
L ≤ max(Q
pos
)/2, for e.g. in our case max(Q
pos
) =
364. Let freq
j
represent the frequency of Q
p
j
∀ j =
0,1,....,L − 1. Now, let us arrange freq
j
∀ j =
0,1,....,L − 1 in ascending order as shown in fig-
ure 2 and different freq
j
’s are then grouped in range
R
i
, where range R
i
∀ i = 0, 1,....,K − 1 represent
the i
th
range, such that K ≤ L. Although it would
be easy to range the frequencies in uniform inter-
vals, this may not be a good idea as it will increase
detection error rate as the dynamic range of fre-
quencies in range will vary too much. Therefore,
we choose unequal range lengths, with range limits
[freq
R
i
,freq
R
i+1
− 1] ∈ R
i
∀ i = 0, 1, ....,K − 1. Let
b
i
∀ i = 0,1,....,K − 1 be the minimum number of
bits used to represent the elements present in i
th
range
R
i
∀ i = 0,1,....,K − 1. Let their be E
i
number of fre-
quency elements (and hence number of contexts) in
i
th
range R
i
∀ i = 0,1,....,K − 1. The values of the
parameters K and b
i
used for simulation purpose are
SIGMAP 2011 - International Conference on Signal Processing and Multimedia Applications
162
Gradients
Flat?
Predictor/
bias
cancellation
Context
Modeler
Golomb
coder
Run
Counter/
Coder
regular
run
Mode
Context
Input Image
(I)
Samples
c b d
a x
Image Samples
Classmap f
Qpos, Qneg, 0
Encrypted compressed
bitstream
Watermarked
context (Q
w
)
Decoder
S
d
Detection
Classmap f
w
Watermark
Detected (Y/N)
Watermark
embedding
Classmap f
Encrypted compressed bitstream
+ Classmap f
w
Image Samples
Predicted
Values
Prediction Errors
Classmap f +
(a) (b) (c)
Contexts (frequencies) +
I
w
JPEG-LS encoder Watermark embedder JPEG-LS decoder
EK
Compressed
stream
Encryption
Figure 1: (a)JPEG-LS encoding (b) Watermark embedding/detection (c) Decoding (watermarked context generation).
given in section 4.
Further watermark signal W of length L
w
is also
segmented. Corresponding to the number of fre-
quency elements in i
th
range R
i
, the length E
i
b
i
of
watermark bits is divided into E
i
number of segments,
denoted by w
i j
∀ j = 0,1,...,E
i
−1, with each segment
of length b
i
bits. This is done corresponding to each
range of figure 2. Also the watermark length L
w
is
chosen such that,
L
w
=
K−1
∑
i=1
b
i
E
i
(1)
Now the watermark can be represented as W =
w
00
||...||w
i j
∀ i = 0,1,....,K − 1; j = 0,1,...,E
i
− 1.
Then the Euclidean distance between each watermark
segment w
i j
∀ i = 0,1,....,K − 1; j = 0,1, ..., E
i
− 1
is computed against frequencies of the selected con-
texts.
argmin
i j,k
(w
i j
,freq
k
) ∀ k = 0,1,....,L − 1 (2)
min
Qorder
k
= Q
p
k
(3)
where, min
Qorder
represents the context whose
frequency is closest to the watermark segment. Now,
the contexts represented in Q
p
are exchanged with the
contexts which are not involved in Euclidean distance
criteria for watermarking. Now without loss of gen-
erality, let Q
′
p
and Q
′′
p
denote these contexts such that
Q
p
∪
Q
′
p
∪
Q
′′
p
= Q
pos
. Also let Q
n
, Q
′
n
and Q
′′
n
denote
the corresponding negative contexts of Q
p
, Q
′
p
and Q
′′
p
i.e., Q
n
= −Q
p
, Q
′
n
= −Q
′
p
and Q
′′
n
= −Q
′′
p
respec-
tively, such that Q
n
∪
Q
′
n
∪
Q
′′
n
= Q
neg
. Also Q
p
and
Q
′
p
, and, Q
n
and Q
′
n
are chosen equilength.
In JPEG-LS encoding, initialcontext Q is mapped
through f as, f : Q → {Q
p
,Q
′
p
,Q
′′
p
,Q
n
,Q
′
n
,Q
′′
n
,0}.
Then, to embed watermark, this mapping is changed
by changing f to f
w
such that, f
w
: Q →
{Q
′
p
,Q
p
,Q
′′
p
,Q
′
n
,Q
n
,Q
′′
n
,0}. The mapping can be
done as, for e.g., Q
′
p
j
↔ min
Qorder
j
∀ j = 0,1,...., L −
1, where ’↔’ denotes one-to-one mapping i.e., each
element of Q
′
p
j
is mapped to an element of min
Qorder
j
.
However, this mapping is secret, can be randomized
using a secret embedding key EK, and does not affect
the watermarked image quality (explained in section
4.2). Thus Q
p
occurring during encoding is replaced
with Q
′
p
for watermarking. Q
n
and Q
′
n
should also be
exchanged correspondingly in order to maintain the
relation between Q
pos
and Q
neg
((Weinberger et al.,
2000)). Since only the classmap f and context fre-
quencies are used for embedding, the encrypted bit
stream remains intact. The compressed-encrypted bit
stream along with f
w
is then sent to the consumer (fig-
ure 1-c). Next we discuss the detection algorithm.
3.2 Detection Process
The detection is done while decoding the Golomb
coded bit stream. The context map f
w
which is sent
to the end user generates watermarked context while
decoding. The extraction involves f
w
, EK, min
Qorder
and the decryption key. Then the frequencies of the
exchanged contexts in place of contexts occurring in
min
Qorder
are computed, which are then correlated
against different watermarks. The original watermark
gives the highest correlation, in case if it is present.
Now, min
Qorder
gives us the order in which the
contexts represent the watermark segments. Using
EK the context mapping is retrieved and, f
w
gives
us the corresponding context which should be looked
for in place of the contexts present in min
Qorder
. Us-
ing f
w
(which gives the mapping of the contexts),
the watermarked contexts can be retrieved as, Q
w
i
:
min
Qorder
i
→ Q
′
p
i
∀ i = 0,1,....,L − 1 i.e, searching
CONTEXT BASED WATERMARKING OF SECURE JPEG-LS IMAGES
163

R
K-1
Frequencies in ascending order
freq
R0
freq
R1
freq
RK-2
freq
RK-1
freq
RK
R
1
R
0
R
k-2
freq
R2
Figure 2: Frequencies arranged in ascending order and grouped.
for the contexts in Q
′
p
which are mapped to contexts
in min
Qorder
. The frequencies of Q
w
in the water-
marked contexts will then represent the frequencies of
min
Qorder
in the original contexts. Let the estimated
watermark be
ˆ
W = ˆw
0
||...|| ˆw
k
∀ k = 0, 1, ....,L − 1,
where ˆw
k
is given by,
ˆw
k
= freq
Q
w
k
∀ k = 0,1, ...., L − 1 (4)
The detection involves correlating the estimated
watermark
ˆ
W against different watermarks
ˇ
W
i
∀ i =
1,2,....,n
w
, where n
w
denotes the number of water-
marks. Correlation is given by,
corr(
ˆ
W ,
ˇ
W
i
) =
E[(
ˆ
W − µ
ˆ
W
)(
ˇ
W
i
− µ
ˇ
W
i
)]
σ
ˆ
W
σ
ˇ
W
i
∀ i = 1,....,n
w
(5)
where corr(.,.) denote the correlation measure, E[.]
denote the expectation operator, µ denote the mean,
σ denote the variance. The correlation value is then
subjected to a threshold T (explained in section 4) to
detect the presence of watermark.
4 EXPERIMENTAL RESULTS
AND DISCUSSIONS
Experiments are carried out on gray scale biomedical
images. The parameters K = 5, b
1
= 4, b
2
= 5, b
3
=
6, b
4
= 8 and b
5
= 10 are used. These parameters are
selected based on the frequency range and number of
contexts occurring in each group. The b
i
is chosen
to maximize the capacity and minimize the detection
error rate. In Table I, the embedding capacity, PSNR,
SSIM, and side information for images of different
resolutions is given.
4.1 Embedding Capacity
It can be seen from the Table I that the capacity in-
creases with increasing image size. This happens be-
cause the larger the image, the higher the frequency
of occurrence of contexts. And the higher the fre-
quency, more number of bits are required to represent
as compared to lesser frequency. However, the image
Brain gives lesser capacity, this is because the occur-
rence of all the contexts is uniform as compared to our
assumption of highest occurring frequencies used for
watermarking. This leads to lesser number of bits re-
quired for representing the frequencies of the contexts
involved in Euclidean distance criteria and hence less
capacity.
4.2 Watermarked Image Quality
The image quality does not get affected by the water-
marking process which is explained as follows. Since
the context is used for bias cancelation, section 2, we
analyze the affect of context exchange on bias estima-
tion and establish the fact that, changing the context
according to the proposed scheme does not affect bias
estimation and hence decoded image quality. The bias
is estimated based on prediction errors accumulated
in the context. Let at position px
j
a pixel x occurs in
context A with accumulated error A
pe
, and B
pe
be the
accumulated error in context B. Let the contexts A and
B occur A
f
and B
f
times respectively until this point.
Now, the bias is given as
Bias
A
= ⌈A
pe
/A
f
⌉ (6)
Bias
B
= ⌈B
pe
/B
f
⌉ (7)
The bias for the predicted value of pixel x is can-
celed as
ˆx = ˆx + Bias
A
(8)
where ˆx represent predicted value of pixel x.
Let us now calculate the bias in case when the con-
texts are exchanged i.e., A is exchanged with B. In this
case, B occurs A
f
times while, A occurs B
f
times. The
prediction error accumulated remains same as that in
case of no exchange. Now, the bias is given as,
Bias
B
= ⌈A
pe
/A
f
⌉ (9)
Bias
A
= ⌈B
pe
/B
f
⌉ (10)
The bias cancelation is now given as,
ˆx = ˆx + Bias
B
(11)
SIGMAP 2011 - International Conference on Signal Processing and Multimedia Applications
164
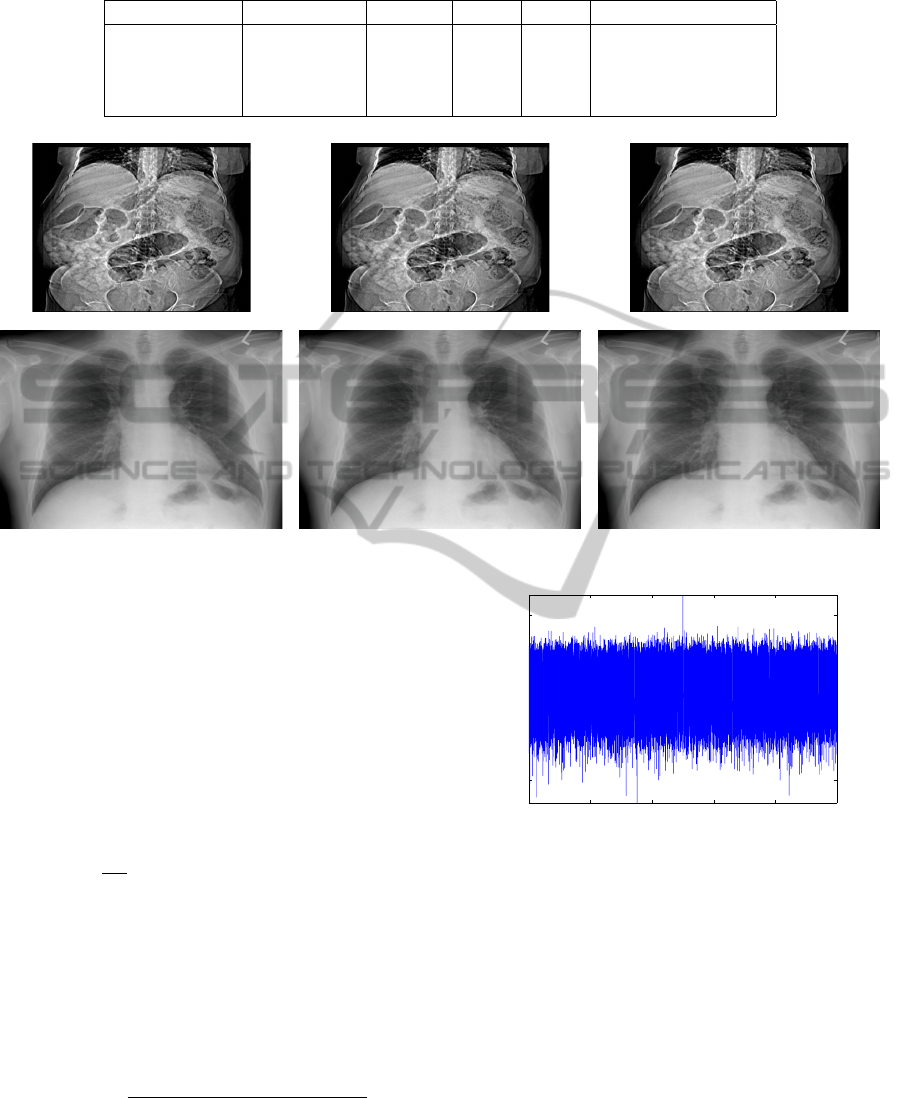
Table 1: Image, Resolution, Embedding capacity, PSNR, SSIM, Side information.
(percentage of (in bits) compressed filesize)
Chest1 373 x 387 1147 53.42 .9981 .148
Abdominal 636 x 614 1735 53.33 .9913 .038
Brain 800 x 600 1426 53.59 .9862 .078
Chest2 2048 x 2494 2448 52.84 .9992 .003
Figure 3: First and second row : original image, decompressed image , watermarked-decompressed image respectively.
From equations 8 and 11, it is clear that watermark-
ing through contexts does not affect the prediction of
pixels and hence the image quality.
Figure 3 gives the original image, decompressed
image and watermarked decompressed image respec-
tively.
From this figure 3 it is clear that the watermark
does not effect the quality of the image as watermark-
ing is performed on the context of the image. PSNR
is given in Table I, and is computed as,
MSE =
1
mn
m−1
∑
i=0
n−1
∑
j=0
(I(i, j) − I
w
(i, j))
2
(12)
PSNR = 10 log
10
(255
2
/MSE) (13)
Mean square error (MSE), is the sum of squares of
difference between the original image I and water-
marked decompressed image I
w
. The Structural Sim-
ilarity Index (SSIM) measures the similarity between
I and I
w
and is given in Table I. SSIM is given as,
SSIM(I, I
w
) =
(2µ
I
µ
I
w
+ c
1
)(2σ
II
w
+ c
2
)
(µ
2
I
+ µ
2
I
w
+ c
1
)(σ
2
I
+ σ
2
I
w
+ c
2
)
(14)
where, µ
(.)
denotes mean, σ
(.)
denotes standard devia-
tion, c
1
= 6.5 and c
2
= 58.5 are constants. PSNR and
SSIM measures show that the decompressed image
quality remains intact even after being watermarked.
0 2 4 6 8 10
x 10
4
10
−0.4
10
−0.3
10
−0.2
10
−0.1
Figure 4: Detection against random watermarks (positive
upward spike at center corresponds to embedded water-
mark)
4.3 Detection Performance
The detection performance is given in figure 4. For
simulation 100000 watermarks are generated ran-
domly and the average is reported for 10 randomly
generated context set. It is evident from the fig-
ure 4 that the correct embedded watermark gives the
highest correlation against the extracted watermark.
On the experimental basis we find that a threshold
T > 0.8 does not give any error in detection.
The watermark embedding takes place through
context mapping. Since context values can only be
CONTEXT BASED WATERMARKING OF SECURE JPEG-LS IMAGES
165

exchanged with other contexts, attacks like additive
noise, scaling, cropping, filtering or other attacks can-
not be performed as these attacks will change the con-
text value randomly further not rendering decoding.
The watermark can be attacked by changing the
mapping f
w
. Here for detection purpose, the water-
mark embedder can request the owner for the decryp-
tion key. Further decrypting the bit stream, the orig-
inal contexts can be generated. Since the position of
original context is known, the corresponding water-
marked context position is also known. Thus the wa-
termarked context can be retrieved and the detection
follows similar to the process described in section 3.2.
In this case the detection performance is similar as
with the case of unattacked watermarked copy. This is
because the absolute
context
value cannot be changed
but only replaced with other context.
Another possible attack is collusion attack. In this
case different watermarked copy holders may collude
to extract or destroy the watermark. Colluders may
get the highest frequency contexts and thus the cor-
responding watermarked contexts. However, this nei-
ther gives any information about the mapping used
for watermarking nor the order in which context fre-
quencies should be used (as the watermark is embed-
ded using Euclidean distance criteria). Thus the at-
tacker has to perform brute force attack to extract wa-
termark.
4.4 Side Information
The side information i.e., the contexts and its frequen-
cies occurring in original image is also given in Ta-
ble I. It is clearly evident that the percentage of side
information required is far less than the compressed
filesize.
5 CONCLUSIONS
In this paper we propose a novel technique to em-
bed a robust watermark in the JPEG-LS compressed
and encrypted images. The algorithm is simple to
implement as it is performed on the context of re-
ceived compressed-encrypted media and does not re-
quire any decompression or decryption. Also the wa-
termark is detected correctly in case of different at-
tacks. The quality of the media is preserved as the wa-
termark does not affect the pixel values itself, rather
only the context classmap is changed. The side infor-
mation required for watermarking is also very low as
compared to the compressed filesize.
REFERENCES
Bianchi, T., Piva, A., and Barni, M. (2010). Composite
signal representation for fast and storage-efficient pro-
cessing of encrypted signals. IEEE Transactions on
Information Forensics and Security, 5(1):180–187.
Blobel, B. (2004). Authorisation and access control for
electronic health record systems. International Jour-
nal of Medical Informatics, 73(3):251–257.
Caldelli, R., Filippini, F., and Barni, M. (2006). Joint near-
lossless compression and watermarking of still im-
ages for authentication and tamper localization. Signal
Processing: Image Communication, 21(10):890–903.
Cancellaro, M., Battisti, F., Carli, M., Boato, G., De Na-
tale, F., and Neri, A. (2008). A joint digital water-
marking and encryption method. In Security, Foren-
sics, Steganography, and Watermarking of Multime-
dia Contents X. Proc of the SPIE, volume 6819, pages
68191C–68191C, 2008.
Fang, T. (2009). On performance of lossless compression
for HDR image quantized in color space. Signal Pro-
cessing: Image Communication, 24(5):397–404.
Katzenbeisser, S., Lemma, A., Celik, M., van der Veen,
M., and Maas, M. (2008). A buyer–seller water-
marking protocol based on secure embedding. IEEE
Transactions on Information Forensics and Security,
3(4):783–786.
Lian, S., Liu, Z., Zhen, R., and Wang, H. (2006). Com-
mutative watermarking and encryption for media data.
Optical Engineering, 45:1–3.
Piva, A., Bianchi, T., and De Rosa, A. (2010). Secure
client-side ST-DM watermark embedding. Informa-
tion Forensics and Security, IEEE Transactions on,
5(1):13–26.
Schneier, B. (1996). Applied Cryptography. John Wiley
and Sons, New York.
Thomas, T., Emmanuel, S., Subramanyam, A., and Kankan-
halli, M. (2009). Joint watermarking scheme for
multiparty multilevel DRM architecture. IEEE
Transactions on Information Forensics and Security,
4(4):758–767.
Weinberger, M., Seroussi, G., and Sapiro, G. (2000). The
LOCO-I lossless image compression algorithm: prin-
ciples andstandardization into JPEG-LS. IEEE Trans-
actions on Image Processing, 9(8):1309–1324.
Zhao, B., Kou, W., Li, H., Dang, L., and Zhang, J. (2010).
Effective watermarking scheme in the encrypted do-
main for buyer-seller watermarking protocol. Infor-
mation Sciences, pages 4672–4684.
SIGMAP 2011 - International Conference on Signal Processing and Multimedia Applications
166
