
USER PROFILE-BASED SERVICE DISCOVERY for eHEALTH
Tesfa Tegegne
1
, Benjamin Kanagwa
2
and Theo van der Weide
1
1
Institute for Computing and Information Sciences, Radboud University, Nijmegen, Netherlands
2
School of Computing and Information Technology, Makerere University, Kampala, Uganda
Keywords:
Personalization, eHealth, Service Discovery, SOA.
Abstract:
Personalization is not very common in Service-oriented Architecture and Service discovery in practice, yet
very important as it enables to find more specific and relevant services. This is especially true in the case of
complex service, where the system tries to find an optimal combinations of services that together can satisfy a
(complex) request. We describe the relation between personalization and service discovery in general, and then
concretize this in the proposed Service Discovery Framework (SDF). Personalization effectively improves the
quality of the discovery algorithm in SDF. As an application, we show its benefits in the context of eHealth.
1 INTRODUCTION
Personalization is regarded as one of the most com-
pelling features of service-oriented systems (Papa-
zoglou et al., 2007) and mobile computing (see (Wang
et al., 2008)) disciplines. Personalization refers to a
set of preferences, data, rules and settings that are
used by a device or service to deliver a customized
version of capabilities to the user (Kobsa, 2007; So
et al., 2009; Wagner et al., 2002) as a means of pro-
viding user-centered services. User-centered and per-
sonalization support customers in selecting their pre-
ferred service from the rapidly increasing publishing
of services.
In the past few years, personalization has been
used in various application areas such as e-commerce,
e-learning to assists users in finding, adapting and us-
ing services that fulfil their needs, given their personal
profile, mobility and context (see (Lankhorst et al.,
2002)). Personalization is concerned with matching
and negotiation between user requirements and abili-
ties on the one hand and service offerings and result-
ing adaptation of network and application level ser-
vices on the other hand (Lankhorst et al., 2002).
In the realm of service discovery, we see person-
alization as an advanced form of service discovery: a
set of services that meet the core requirements of a
user are further scrutinized for compliance with the
user personal desires and constraints. Consequently,
personalization offers a quality user profile and an ac-
curate representation of the user’s physical and emo-
tional behavior (Lankhorst et al., 2002). To build and
maintain effective personalization, appropriate user
preferences, interests, and behaviors are required (see
(Ghosh and Dekhil, 2009)). In a way, personalization
covers all functionality regarding discovery and man-
agement of users with respect to their preferences, de-
mands and wishes. Therefore, it is important that per-
sonalization should be transparently incorporated as
one of the main components of service discovery in
addition to context-awareness and semantics.
A user profile is often used to classify users into
predefined user segments (such as, by demograph-
ics or tastes) or to capture their behavior including
their private interests and preferences (see (Shmueli-
Scheuer et al., 2010)). One of the key challenges
pointed by (Ramanathan and Kapoor, 2009) is to con-
struct accurate user models containing demographic
interests, preferences, intent and behavior informa-
tion. A user profile can be obtained in various ways.
It can be explicitly defined by the user, such as dur-
ing registration for a service. Additional information
about the user can be obtained through user profiling:
the process of implicitly learning user characteristics
from data associated with that user. Data sources for
user profiling include among others the user browsing
sessions, the user’s own generated content, the user’s
social interactions with friends in the user’s social net-
work (e.g. the user’s discussions with others), click-
through data extracted from search logs, or even other
user profiles using collaborative filtering techniques
(Shmueli-Scheuer et al., 2010). Personalized systems
employ various personalization methods like machine
learning, information retrieval, bayesian networks see
(Wang, 2010; Kobsa, 2007) to derive additional as-
sumptions about users. Generally, the more informa-
337
Tegegne T., Kanagwa B. and van der Weide T..
USER PROFILE-BASED SERVICE DISCOVERY for eHEALTH.
DOI: 10.5220/0003630003370346
In Proceedings of the 6th International Conference on Software and Database Technologies (ACT4SOC-2011), pages 337-346
ISBN: 978-989-8425-76-8
Copyright
c
2011 SCITEPRESS (Science and Technology Publications, Lda.)

tion is collected about users, the better the quality of
personalization will be. As a result, the process of
personalization usually consists of user modeling and
adaptation. User modeling (Wang, 2010) is concerned
with building user models, while adaptation creates
personalized services based on the user profile.
The contribution of this paper is formalized
context-aware profile-based service discovery with
particular emphasis to eHealth services. In addi-
tion, we address user authentication and authoriza-
tion methods for user profile and services. We as-
sess the impact of personalization on facilitating ser-
vice discovery, service selection and service match-
ing. We exemplify our work within the domain of
eHealth services motivated by the fact that it is not
common to find identical health cases with similar
context, particularly in developing countries that are
usually synonymous with wider variations in culture,
beliefs and general living conditions. Such variations
occasions added importance for personalization espe-
cially in eHealth services that are core to developing
countries.
This paper is organized as follows. Section 2 ex-
plains related work. We overview personal profile in
section 3. In section 4 we present the proposed service
discovery framework. We discuss personalization on
eHealth in section 5. Finally, we conclude in section
6 where we highlight some of the future research di-
rections.
2 RELATED WORK
the last couple of years various researchers have
addressed the problem of personalization for dif-
ferent applications (for example e-learning and e-
commerce, etc). The rapid growth and deployment of
services and information makes personalization one
of the important research topics. However, the appli-
cation of personalization in service discovery has not
been widely studied. Semantic and contextualization
of service was given more emphasis in the process of
service discovery than personalized service discovery.
The concept of a user profile (personalization)
usually refers to a set of preferences, information,
rules and settings that are used by a device or ser-
vice to deliver a customized version of capabilities to
the user ((So et al., 2009)). To capture user prefer-
ence and interest, ontology based user modeling has
widely been adopted. Ontology helps to develop an
effective mechanism for user query contextualization
based on both current and previous search history (So
et al., 2009).
According to Petersen (Petersen et al., 2009), a
user profile contains information on the goals, the
needs, the preferences and the intentions of that user.
The user profile provides an interface to access this
user information, including its static profile, prefer-
ences, context information (location, presence, device
capabilities, etc), service specific personal informa-
tion and the history of service usage and so on. The
provided function will be used to discover the services
requested by the user.
Typically a user profile includes her/his individ-
ual preferences together with technical constraints of
his/her means of communication (devices and equip-
ments) and his environment (Wagner et al., 2002).
Based on semantically enriched service descriptions
a service request management is then performed in-
cluding a service discovery and execution. During
service discovery and selection, decisions that have
to be made will not necessarily lead to one definitive
outcome. Requirements could be met not by just one
service or service component, but by a set of them, or
none at all (Wagner et al., 2002). Therefore (Wagner
et al., 2002) state that the process of service discovery
can take the personal user preferences, semantically
rich user profile and context information of the user
into account.
2.1 Context-aware Models for
Personalization
Context-awareness refers to systems that are able to
adapt their services to the user context. Services can
be selected according to both the current user con-
text and her/his preferences for this context. Context-
aware profiles aim at indicating which service is rel-
evant for a user when he is in a given situation. The
main idea of the context based profile (Mehta et al.,
2005) is to allow users to define the profiles and po-
tential context in which these profiles should be used.
Context can be thought of as the “extra” often im-
plicit, information (i.e. associations, facts, assump-
tions), which makes it possible to fully understand an
interaction, communication or knowledge representa-
tion (Mehta et al., 2005). They propose the use of a
common ontology based user context model as a ba-
sis for the exchange of user profiles between multiple
systems and, thus, as a foundation for cross-system
personalization.
In our model the user context can be obtained in
two ways: the user announces her current profile in
her request or the context manager dynamically gen-
erates the users context (location, weather, etc) from
the context provider devices such as GPS, sensors etc.
A user context (as summarized in Figure 1) con-
sists of two categories (static and dynamic). The static
ICSOFT 2011 - 6th International Conference on Software and Data Technologies
338
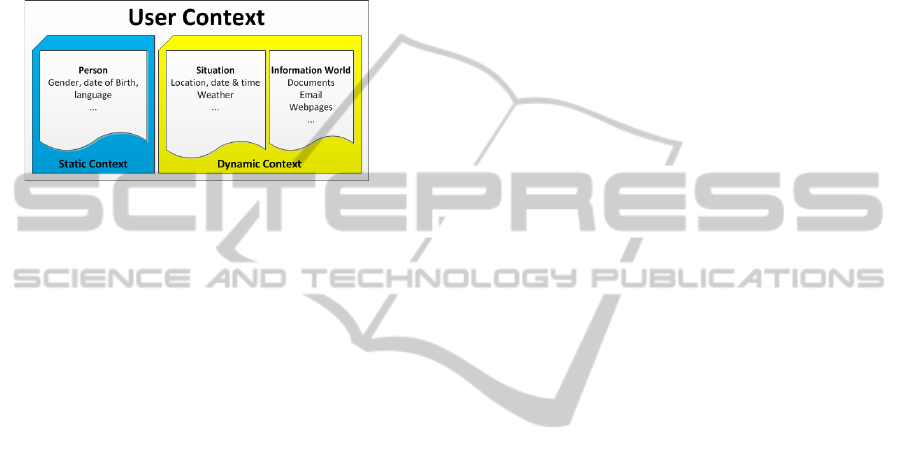
category describes the demographic data of the mo-
bile user. These are user data about name, gender,
age, language etc. The dynamic further classified as
environmental and information world. The environ-
ment category provides situational context informa-
tion like the actual location and the environment. The
third category captures the user’s “information world”
e.g. read documents and visited Web pages - thus re-
flecting the user’s interests (Kuck and Gnasa, 2007).
Figure 1: Context of mobile user (Kuck and Gnasa, 2007).
Some of the advantages of using context-
awareness in healthcare domain are large number
of situations and related tasks, mobility of patients,
health professionals and some equipments; limited fi-
nancial and human resources; and the need to cut cost
while improving the quality of service to an increase
number of people. In addition, the expectation to ac-
cess, process, and modify the healthcare information
anywhere and anytime using handheld devices is an-
other reason to use context-awareness. Alike other
systems, contextualization encounters different chal-
lenges such as how often the contextual information
needs to be collected, when is some information is
old, not reliable, missing, or just plain wrong? Is it
the same for normal, abnormal and emergency cases?
Health professionals and patients are involved in a
variety of tasks and processes and their information
needs vary based on their location, time, environment
and involved activity. The knowledge of their current
activity may assist in deciding which of the health-
care professionals should be reached for some medi-
cal tasks or decision making.
2.2 Personalization and Service
Discovery
Personalized search is seen by the research commu-
nity as a means to decrease search ambiguity and re-
turn results that are more likely to be interesting to
a particular user and thus providing more effective
and efficient information access (Sieg et al., 2007;
Park et al., 2009). One of the key factors for accu-
rate personalization information access is user pro-
file and user context. There are many factors that
contribute for the delineation of personalization such
as: the user’s short-term information need, such as a
query or localized context of current activity, seman-
tic knowledge about the domain being investigated,
and the user’s profile that captures long-terminterests.
To find the most appropriate services, service dis-
covery protocols should exploit context. The most
appropriate service is not always the nearest or the
highest quality rather, it varies according to the user’s
preferences. More importantly, user criteria change
with their context. A user might generally prefer to
use the most popular services, but in a particular case,
might want to use only high-quality services (Park
et al., 2009). A service discovery starts from the local
service repository/registory. If it fails to find an ap-
propriate service in the local repository or registry, it
propagates request/discovery queries to other appro-
priate repositories/registries. If the requested service
is found, the matchmaking process will be performed
to select the appropriateservice based on the user con-
text and user preference (profile) (Park et al., 2009).
Discovery corresponds to the activity of locating
a service that meets certain functional criteria. Selec-
tion is related to the activity of evaluating and ranking
the discovered services to identify the ones that fulfill
a set of non-functionalproperties and user preferences
requested by the actual user. Most of the existing
techniques rely on syntactic descriptions of services
interfaces to find services with disregard to non func-
tional service parameters (Badr et al., 2008). Incorpo-
rating user contexts and user preferences in the pro-
cess of service discovery brings quality service dis-
covery that can improve search results and provides
a better means for user to identify their service infor-
mation needs (Badr et al., 2008; Park et al., 2009).
3 USER PROFILE
The main purpose of user profile is to keep track of
the user related information to control its availability
and facilitate service access for its users, and to real-
ize a better user experience. Besides, personalization
helps to identify a service delivery mechanism (text,
audio, video, etc.), to choose the type of service to
be delivered with respect to user preferences (physi-
cal, psychological, environmental, and so on) and to
create a global personalization scheme (ETSI, 2005).
User profile may contain many individual data items
(information, preference and rules) coming from dif-
ferent sources (Choi and Han, 2008; Petersen et al.,
2009; ETSI, 2005). When a user wishes to have the
behavior of services personalized to his/her require-
ments a profile will be required (ETSI, 2005). The
USER PROFILE-BASED SERVICE DISCOVERY for eHEALTH
339

value of some of these items will (1) either not change
(static) or (2) change very irregularly and (dynamic)
and (3) some may be individuallychanged by the user.
A single user may be associated with multiple pro-
files. It is therefore important that users have the flex-
ibility to decide on the profile to use or better, the
system should automatically detect the current pro-
file. For instance, a user may move from office to
a meeting room requiring him to access services on
a small device. Users can often control the type of
service provided, as well as the look and feel of the
interface, by indicating their choice through their pro-
file. In (Petersen et al., 2009) a user plays a number
of roles in personalization system. A typical user in
personalization will have at least two roles such as the
user role and the administrator role.
User profile can be segmented into private and
group (clustered). The private profile contains only
individual data i.e. personal data, and preferences.
Group profile is generated from the private profile
from the users who share similar interests and pref-
erences. For example, for healthcare works we can
group users based on their job or educational sta-
tus: specialist, general practitioners, nurses, pharma-
cist, etc.; and patients can be grouped or clustered by
the disease type: HIV patient, TB patient, diabetic,
etc. This type of clustering improves the service se-
lection and service matchmaking process since they
share similar information. Furthermore, this segmen-
tation assists to push (broadcast) some information to
the users with the same preferences (for instance, for
healthcare workers new disease break out, new vac-
cination, training etc. and for patents medical time,
consultation and education etc).
User profile determines the method of service de-
livery. For example a vision impaired person wishes
to get the service in audio and the hearing impaired
user wishes to receive in text rather than audio (Choi
and Han, 2008; Petersen et al., 2009; ETSI, 2005).
Additionally, user profiles may require to be priori-
tized to avoid conflicting profiles. A user may have
several preferences, however, services might not be
available for the preferences to match. Hence, after
filtering out the relevant needs of the users prefer-
ence required to be prioritized. The priority of user
preferences will help to relax the matchmaking pro-
cess. In line to this (Petersen et al., 2009; ETSI, 2005)
stated eHealth profiles to be allocated higher priorities
than non-eHealth profiles. eHealth profiles are con-
sidered as more important than personal profiles (nor-
mal profiles) as they contain information (extracted
from electronic health records) and preferences (Choi
and Han, 2008; Petersen et al., 2009; ETSI, 2005).
Generally, the user profile should address the fol-
lowing questions: where a user is located, what her
job/ profession is, what her preferences (interest) is,
what the context of the user is, who the provider of
the service is, the cost and availability of the service
(Petersen et al., 2009; ETSI, 2005).
3.1 Challenges of User Profile
Personalization (personal profile) is not without chal-
lenges. Some of the challenges are: how can per-
sonal informationbe gathered, howis this information
stored in a persistent and ubiquitous manner (this is
applicable for infrastructure-less networks), how can
the changes always be reflected in the services ren-
dering process? In addition, privacy is the other bot-
tleneck in personalization. In regard to gathering in-
formation, we propose pull and push model as well as
manual and automatic information gathering. Man-
ually, the user will fill in the form and continuously
update the profile whenever there is a change whereas
in automatic information gathering especially, in mo-
bile ad hoc networks, every node can broadcast its
profile to the immediate neighbor node and gathering
information from profile providers and devices such
as sensors, GPS, etc. In the case of user profile pri-
vacy, in our framework, we proposed user authentica-
tion and authorization model to secure the user profile
from privacy threat.
3.2 User Profile Privacy
Personalization is beneficial for service consumers
and service providers. However, its benefit may be
counteracted by privacy constraints. Personalized
systems need to address the privacy constraints, in-
cluding user personal privacy preferences, the pri-
vacy law and the regulation of the company or in-
dustry (Wang, 2010; Kobsa, 2007). Similarly, it has
been tacitly acknowledged for many years that per-
sonalized interaction and user modeling have signif-
icant privacy implications, due to the fact that per-
sonal information about users needs to be collected
to perform personalization (Kobsa, 2007). Mobile de-
vices can provide useful personalized services that are
based on usage patterns and the current user location.
Both are tracked in central servers, which creates new
privacy problems.
According to literature (Kobsa, 2007; Wang and
Kobsa, 2009; Wang, 2010), a significant number of
people revealed their concern of disclosing personal
data to the Internet. This implies that if users are not
given guarantees of keeping their personal informa-
tion secured, then they are not willing to disclose this
kind of information.
ICSOFT 2011 - 6th International Conference on Software and Data Technologies
340

The personalized system tends to provide users to
block the privacy from any unauthorized entities. For
example the X-ray images and other important pa-
tients data can be blocked from the service providers,
even only authorized healthcare workers can get ac-
cess to the specified medical information.
An important issue of the proposed system is
user authentication and authorization. Authentication
checks the identity of the user. Authorization deals
with role based access control. Privilege will be given
to the users (human or systems) with the respect to
the role they played. For example, PERMIS (for more
details (Chadwick et al., 2008)) is one of eminent role
based access control (authorization) system used in
many applications.
3.3 Working Example
John works in non governmental charity organization.
After a few days in a charity work he feels a little dis-
comfort. He has fever, headache and nausea. The
village health extension worker (HEW) diagnoses a
laboratory examination (blood, stool, etc), however,
all the results are negative. The HEW makes addi-
tional examination to find the cause to administer the
appropriate treatment. But the case of John cannot be
resolved in the health post as there is only one small
laboratory and there is no specialist. Thus the HEW
decides to access the health system to get additional
help. After logging into the system, the HEW fills
the form, entering the diagnosis made, the admin-
istered medication, the patient’s symptoms, the pa-
tient’s history, John’s preferences and the location of
the hospital. After accessing John’s medical history
(Electronic Health Record) remotely, the HEW learns
that John has a mild hypertension case and is aller-
gic for antibiotics, and John prefers not to have an
injection. Based on this information, some services
are retrieved from the repository. After the system re-
ceives the information, it forwards all this information
to John’s family doctor (if any) and the emergency
dispatch center (emergency dispatch center is a spe-
cialized or referral hospital near by the given location
area). This dispatch centers which has good medical
facilities and a number of specialists. While receiving
this emergency request the system will forward the
cases to the appropriate specialist to assist the patient
remotely. These emergency team will communicate
the patient’s private doctor and forward the prescrip-
tion to the attending healthcare worker to administer
the treatment.
As shown in Figure 2 a user may use two ways
of requesting a service: (1) using voice and (2) us-
ing text or/and video (depending on the bandwidth in
Figure 2: Personalized user service request.
developing countries context). As most of the popu-
lation in developing countries is illiterate, especially
in the rural areas, voice based communication will
increase the number of eHealth system users. Fur-
thermore, users who own a smart phones and can use
the features of the smart phone or PDA, can query
service using text and video (if the infrastructure al-
lows). As depicted in the Figure 2, the user can
press a button and send a voice request. The voice
server (VoiceXML) converts the voice data into text
data, and forward the converted request to the appli-
cation server. After receiving the request, the appli-
cation server will forward the request to the appropri-
ate emergency dispatch centers (EDC) based on the
location. EDC is a center which is set up based on
the geographical location. This center should have
a number of specialist doctors, good health facilities
and services. After evaluating the user request, the
EDC forwards the request to the appropriate special-
ists. The specialists evaluate the user request, verify
and access the patient’s history (EHR), communicate
with the family doctor (if any) of the patient, and ac-
cess the service repository. Finally, the treatment and
its procedure is forwarded to the mobile of the re-
questing HEW.
A voice based querying services has its own chal-
lenges. But in the case of Ethiopia it is very im-
portant since the majority of the population does not
speak English rather can they use their own language.
Choosing the language to be localized is another chal-
lenge since many languages are spoken in Ethiopia.
In our project we plan to use Amharic and English as
a medium of communication in our system. The for-
mer is understood by many of the people and is the
working language of the country and the latter is used
as a medium of instruction for secondary and tertiary
education.
4 SERVICE DISCOVERY
FRAMEWORK
In this section we first introduce the discovery prob-
lem, and then describe the SDF framework to handle
this problem. This framework extends the description
USER PROFILE-BASED SERVICE DISCOVERY for eHEALTH
341
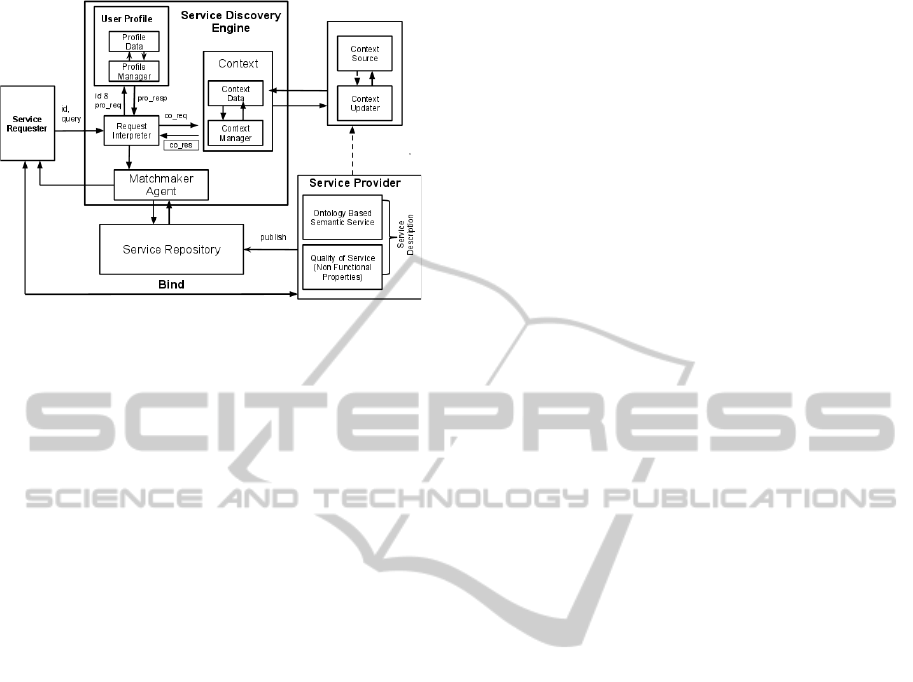
Figure 3: The Service discovery framework (SDF).
from previous section, see Figure 2.
4.1 The Profiled Discovery Problem
Service discovery is about functional matching of
atomic services. The service composition problem
can be described as the problem of finding an opti-
mal combination that together can satisfy a (complex)
request. We use the term complex discovery for the
combination of service discovery and service com-
position. We follow the approach from (Kanagwa,
2009), and shortly overview the approach. Services
are described by their effect in terms of how they
transform their input message into an output mes-
sage. We use the convenience of Hoare Logic (He and
Hoare, 1998) and write {P}S{Q} to describe that ser-
vice S will transform an input satisfying condition P
into an output satisfying condition Q. We assume a
set
S
of so-called elementary services. Services may
be combined to form new services. For example, the
service S
1
;S
2
is the service in which the execution of
service S
1
is followed by S
2
. The semantics of this
compound service is derived as follows:
{P}S
1
;S
2
{Q}⇔∃
R
[{P}S
1
{R} ∧ {R}S
2
{Q}]
Other ways to combine services are optional, repeti-
tive and parallel execution.
Let
S
+
contain all elementary services from
S
and be closed under the composition operators dis-
cussed above. A request q is described as a com-
bination q = (Pre, Post). A profiled request (q, P) is
the combination of a request q and a preference pro-
file P. The solution space for request q is: Sol(q) =
S ∈
S
+
{Pre}S{Post}
From this set Sol(q) the
cheapest solution is selected:
argmax
S∈Sol(q)
Pref(S, q, P)
where Pref(S, q, P) indicated how well solution S in
the context of question q is to be preferred given
profile P. This problem however is computationally
intractable. In (Kanagwa, 2009) a similarity calcu-
lus is described that evaluates the similarity Sim(q, S)
between a request q and service S as an estimation
of its successfulness in satisfying request q, by in-
troducing a similarity calculus for predicates. So
Sim(Pre, Pre(S)) expresses the similarity of the re-
quested precondition Pre with the advertised precon-
dition of service S. Analogously, Sim(Post(S), Post)
expresses the similarity the advertised post condition
with the requested one. The similarity calculus is used
to select a set of candidates for further investigation to
find a proper solution.
We will therefore define the solution space as a
mapping that indicates the correctness of solutions:
Sol(q) :
S
+
→ [0, 1] which may be defined for request
q = (Pre, Post) as follows:
Sol((Pre, Post))(S)
= Sim(Pre, Pre(S)) · Sim(Post(S), Post)
Here Sim(Pre, Pre(S) expresses to what extent the pre-
condition of request q satisfies the precondition of ser-
vice S. In (Kanagwa, 2009) the similarity between
predicates P and Q is defined as the likelihood of the
implication P⇒Q, or: Sim(P, Q) = Val(P⇒Q). For
more information on the function Val, see (Kanagwa,
2009).
Notice that in (Kanagwa, 2009) some heuristics
are described to find a most suitable compound ser-
vice. As suggested in (Paolucci et al., 2002) we
consider three stages of capability matchmaking (in-
cluding user context, service context, user preferences
etc.):
1. Exact match: Both output and input of a service S
are equivalent to the request:
Pre(S) = Pre ∧ Post(S) = Post
2. Plug-in match: The outputs of service S are more
specific than requested, or its inputs require less
information than the requested:
Pre⇒Pre(S) ∨ Post(S)⇒Post
3. Subsumed match: The output of a service S can
only partial fulfill the request, or the input re-
quired by the service are more specific than the
request provides:
Pre(S) ⇒Pre ∨Post⇒Post(S)
4. Not match: if non of the above are applicable.
The ultimate goal of match making is to deter-
mine the contents that satisfied user preferences and
interests. For this, the matching algorithm starts with
the most specific expression which best fits the user’s
wishes and in the case that no matching can be found,
the user query required to be relaxed (expanded).
ICSOFT 2011 - 6th International Conference on Software and Data Technologies
342

4.2 Preference Calculus
Input and output based matching alone can not guar-
antee the retrieved service is usable. Taking the pro-
file P into account, we get for each service S ∈
S
+
the
suitability score Suit(S, q, P):
Suit(S, q, P) = Sol(q)(S) ·Sim(P, S) (1)
The handling of user preferences may be modified
for those cases where preferences are not easily deter-
mined as exact numbers. A discrete set of values is
more appropriate for such cases. A naive approach in
such a case is to only register whether there is a pref-
erence for a service or not. However, we feel such
a boolean approach will be too restrictive for general
application. We therefore propose to use a fuzzy ap-
proach, and consider preference as a linguistic vari-
able that can take, according to the MoSCoW Prior-
itization scheme for project management (Clegg and
Barker, 2004) one of the following values: (1) Must
have (2) Should have (if at all possible), (3) Could
have (if it does not effect anything else) and (4) Won’t
have (this time but would like in the future), extended
with the value (5) Don’t want. The value of Sim(P, S)
then is expressed as such a MoSCoW value.
Referring to Formula (1), we have to combine
the outcome of Sol(q)(S) with the MoSCoW value.
A very simple approach is to convert the MoSCoW
values to numbers as follows: m(Must have) =
1, m(Should have) = 0.75, m(Could have) = 0.50,
m(Won’t have) = 0.25 and m(Don’t want) = 0. This
leads to:
Suit(S, q, P) = Sol(q)(S) · m(Sim(P, S)) (2)
4.3 The Architecture
The framework presented in our previous work
(Tegegne et al., 2010), see Figure 3, depicts an over-
all process of service discovery. A user may send a
request to the request interpreter. The profile agent
personalizes the request, while the context agent will
add context specific extensions to the request. Then
the enriched request is forwarded to the matchmaker
agent. The matchmaker agent selects the best candi-
date for the submitted request as described in the pre-
vious subsection, using the service repository agent
to supply the base knowledge (their identity and their
semantics) of the elementary agents (
S
). The result
is transmitted to the service requester to be communi-
cated with the requester.
The profile manager (PM) gets the user request.
Upon first usage, a user may have to supply some
base information to set up a profile. The profile man-
ager updates the profile repository. After completion,
the PM will send the user a registration conformation
message. In the meantime, the profile manager sends
the new user information to the authorization and au-
thentication module. Then the user will be provided
a certificate. If the user is a registered user, the PM
will request an authorization certificate from the au-
thentication and authorization module. The PM also
checks the validity of the certificate and checks if the
certificate is given by a trust security manager. If the
certificate fulfills the above requirements, the PM up-
dates the user profile (preference, interest, context (if
exist)). After that the PM will send the user request
plus the current user profile to the matchmaking agent
(and/or the user if necessary).
All profile data are held in a profile database,
which is only accessible via the PM. The PM permits
to read or write data only if the requesting application
can prove sufficient access rights with a certificate.
To enhance security for sensible data, profile entries
in the database are encrypted by the PM.
4.4 The Matchmaker
In this section we elaborate the match making func-
tionality from sections 4.1 and 4.2 in some more de-
tail, in terms of the architecture described in 4.3. The
function of the match maker is to find the most suit-
able compound service S given a request q and a pro-
file P, using Suit(S, q, P) as suitability measure. The
match maker thus ensures that the user will receive
the service that is pertinent with user preferences and
interests.
Figure 4: Profile-based service discovery and selection.
In Figure 4 we present the general architecture for
the match making process. First, it receives the user
profile and preferences from the query interpreter and
it combines with service ontology in service reposi-
tory/registry. After that the match maker selects the
advertised (i.e. atomic) services that match with the
request. The extracted services will be forwarded to
the reasoning module to find the best matching com-
pound services, and rank them according to their ap-
plicability. After the matching the reasoning agent
will strengthen the matching with extra criteria (QoS,
USER PROFILE-BASED SERVICE DISCOVERY for eHEALTH
343

cost etc.). Later the ranking module ranks the ex-
tracted services (matched services) based on user
preferences, user context and non functional proper-
ties of services. Finally, the services with maximal
rank will be presented to the requestor. The match
maker will further perform consistency check and va-
lidity of the user profile and quality of service (Alam
et al., 2009).
Algorithm 1: ServiceDiscovery.
Request Negotiate:
GetRequest (user,req,pref,context);
Request Interpreter:
Update Profile (user, req, pref out req, pref);
Update Context (context out context);
P := prefs ⊕ context;
Matchmaker:
evaluate function Sol(req);
if for all S we have Sol(req)(S) < δ then
failure;
else
return argmax
S
Suit(S, req,P)
end if
This discovery process is summarized in algo-
rithm ( 1) and in Figure 4. Finally some remarks
about authentication and authorization. In the archi-
tecture of Figure 4 the user requests services. The
query interpreter will send the query to the profile
manger. The profile manager checks whether the user
is authenticated and authorized. After that, the pro-
file manager retrieves any available user preferences
from the profile repository. Finally the user informa-
tion will be forwarded to the query interpreter. The
query interpreter transfers the service request and the
user profile (user data and preferences) to the match
maker to process service matching.
5 eHealth PERSONALIZATION
Advances in service orientation, mobile and ubiqui-
tous computing, and continuous progress in medical
devices and diagnosis methodology are enabling per-
sonalized healthcare services to be delivered to indi-
viduals at any place and any time (Zhang et al., 2004).
These advances deviate from the ”One size fits all”
paradigm in healthcare as is common in traditional
hospitals, clinics and healthcare centers. Personal-
ized healthcare ensures that healthcare services pro-
visioned to individuals are customized to their pre-
vailing healthcare needs. In most developed coun-
tries, personalized healthcare is provided for citizens
through home care, wearable devices, online treat-
ment and consultation. In developing countries per-
sonalized healthcare could provide an opportunity to
compensate for the shortage of professional health-
care workers as well as poor healthcare infrastruc-
tures.
Introducing ICT in the healthcare sector is a hot is-
sue, both in developed and developing countries. Sev-
eral researchers have been conducting researches how
to use ICT in supporting healthcare. Many organiza-
tions are involved producing in electronic healthcare
standards. For example, Health Level 7 is a health
informatics standard organization. The main purpose
of this organization is developing, publishing and pro-
moting a comprehensive framework for the develop-
ment of health informatics standards and the employ-
ment of the framework to produce protocol specifica-
tions for health data interchange, integration, storage
and retrieval among diverse data acquisition, process-
ing, and handling systems.
Similarly, the European Telecommunications
Standards Institute (ETSI) is an ICT standard organi-
zation. ETSI, recently released a first draft personal-
ization on eHealth standard. This draft standard will
help to manage the user profiles for personalization
of eHealth systems and services according to the user
preferences and needs. This profile is an extension of
the ‘user profile management(UPM)’ standard devel-
oped by ETSI.
5.1 eHealth Service Discovery
Framework
Adapting an eHealth system to the individual user is
essential for making it safe and easy to deploy and
to use as an effective support to independent living.
Personalization can thus enhance the user’s trust in
the eHealth systems, and make them more readily ac-
cepted.
The case for personalization of health informa-
tion is supported by studies in health communication
which have shown that health-education material can
be much more effective if customized for the individ-
ual patient in accordance with their medical condi-
tion, demographic variables, personality profile, and
other relevant factors (DiMarco et al., 2009). Accord-
ing to (DiMarco et al., 2009), little work is being done
on what we consider the most important factor: tailor-
ing the information to individual needs, experiences,
and communication style.
One of the most important aspects needed in sys-
tem building is information about the intended user
goals, needs, moods, preferences, intentions, etc.
This information can be acquired through an explicit
and implicit process called user modeling. Modeling
a user means interpreting user actions within a given
ICSOFT 2011 - 6th International Conference on Software and Data Technologies
344

system or application. The user model is usually re-
stricted to some characteristics that are supposed to
be the most meaningful in the context of the user in-
teraction with the system.
5.2 Key Benefits
Personalization in eHealth has twofold advantages;
for the health workers it provides information (such
as training, professional guidance and assistance) on
the basis of their educational background and job de-
scriptions. On the side of the patient, it provides the
necessary patient-oriented health information systems
like patient preference, informed consent, self-care
and shared patient-doctor decision making.
The main aim of personalizing eHealth is to ac-
quire and capture factual information about the pa-
tient, their condition, current treatments, their pref-
erences. This information can be obtained from the
patient record except the user contextual information.
Personalizing eHealth besides informing, en-
abling decision making and persuading the patients,
it will give users access to medical treatment and con-
sultation services on the basis of their needs. The
health workers also benefit from this personalization
in two ways, first they strictly consult their patients
based on their preferences, and second the health
worker can fetch any information from the personal-
ized system. Patients can get information about the
treatment, background information about their condi-
tions (the cause, symptoms, its consequences and so
on) and alternative treatment and its effect.
In most of the previous personalized eHealth, the
interaction between the system and the patient was
fixed and simple (Cawsey et al., 2007). Personal-
ized email or text messages have also been used.
This type of personalization does not consider indi-
vidual preferences and interests. For example if a cen-
tralized HIV/AIDS prevention and controlling office
sends an instant message to HIV/AID patients to take
their medicine on a specified regular time. However
this system does not address the individual preference
rather it implies “one size fits all” notion.
Service personalization in eHealth will help to de-
sign a personalized user interface based on user’s abil-
ities, interests and needs. This will create an oppor-
tunity in addressing heterogeneous preferences of in-
dividual users. For instance, for an illiterate mobile
user, it is possible to create an audio based user inter-
face that can be accessed by pressing a single key.
6 CONCLUSIONS
Efficient and accurate service discovery is one of the
key challenges of service-oriented systems. In this
paper we concretize the use of user profile provided
more refined service discovery. To address the privacy
concerns that relate to use of user profiles, we have in-
tegrated privacy (authentication and authorization) in
service personalization. The intended deployment is
in transition countries where voice via mobile phone
is the most widespread communication mechanism.
Consequently, part of the future work is to implement
the framework using voice technology based on mo-
bile phone platform as well as developing a corpus
for local languages (such as the Ethiopian Amharic)
in the healthcare domain.
REFERENCES
Alam, S., Iqbal, Z., Noll, J., and Chowdury, M. (2009). Se-
mantic personalization framework for connected set
top box environment. In Second International Confer-
ence on Advances in Human-Oriented and Personal-
ized Mechanisms, Technologies, and Services, CEN-
TRIC, pages 97–102.
Badr, Y., Abraham, A., Biennier, F., and Grosan, C. (2008).
Enhancing web service selection by user preferences
of non-functional features. In NWESP, IEEE, 4th In-
ternational Conference on Next Generation Web Ser-
vices Practices, pages 60–65.
Cawsey, A., Grasso, F., and Paris, C. (2007). Adaptive
information for consumers of healthcare. Springer-
Verlag Berlin Heidelberg.
Chadwick, D., Zhao, G., Otenko, S., Laborde, R., Su, L.,
and Nguyen, T. (2008). Permis: A modular authoriza-
tion infrastructure. Concurrency and Computation:
Practice & Experience, 20(11):1341–1357.
Choi, O. and Han, S. (2008). Personalization of rule-based
web services. Sensors, 8(4):2424–2435.
Clegg, D. and Barker, R. (2004). Case Method Fast-Track:
A RAD Approach. Addison-Wesley.
DiMarco, C., Wiljer, D., and Hovy, E. (2009). Self-
managed access to personalized healthcare through
automated generation of tailored health educational
materials from electronic health records. In Virtual
Healthcare Interaction: Papers from the AAAI Fall
Symposium (FS-09-07,, AAAI Fall Symposium Se-
ries), pages 4–7.
ETSI (2005). Human factors (hf); user profile management.
In ETSI EG 202 325 V1.1.1, ETSI Guide, pages 1–
100.
Ghosh, R. and Dekhil, M. (2009). Discovering user pro-
files. In International World Wide Web Conference,
Proceedings of the 18th international conference on
World wide web, pages 1233–1234.
He, J. and Hoare, C. A. R. (1998). Unifying theories of
programming. In RelMiCS, pages 97–99.
USER PROFILE-BASED SERVICE DISCOVERY for eHEALTH
345

Kanagwa, B. (2009). Design, Discovery and Construction
of Service-Oriented Systems. Siks dissertation series:
2009-09, Radboud University, Nijmegen.
Kobsa, A. (2007). Generic user modeling systems. In Lec-
ture Notes in Computer Scinence, Modeling technolo-
gies, The adaptive web: methods and strategies of web
personalization, pages 136–154.
Kuck, J. and Gnasa, M. (2007). Context-sensitive service
discovery meets information retrieval.
Lankhorst, M., Kranenburg, H. v., Salden, A., and Pedde-
mors, A. (2002). Enabling technology for personaliz-
ing mobile services. In HICSS-35/02, Proceedings of
the 35th Hawaii International Conference on System
Sciences, pages 87–2.
Mehta, B., Niederee, C., Stewart, A., Degemmis, M., Lops,
P., and Semeraro, G. (2005). Ontologically-Enriched
Unified User Modeling for Cross-System Personaliza-
tion. Springer Berlin / Heidelberg.
Paolucci, M., Kawamura, T., Payne, T. R., and Sycara, K.
(2002). Semantic matching of web services capabili-
ties. In ISWC 2002, pages 333 –347.
Papazoglou, M. P., Traverso, P., Dustdar, S., and Leymann,
F. (2007). Service-oriented computing: State of the
art and research challenges. Computer, 40(11):38–45.
Park, K., Yoon, U., and Ki, S. (2009). Personalized service
discovery in ubiquitous computing environments. Per-
vasive Computing, 8(1):58–65.
Petersen, F., Bartolomeo, G. andPluke, M., and Kovacikova,
T. (2009). Context sensitive personalization uti-
lizing user profiles: Standardization work at euro-
pean telecommunications standards institute (etsi. In
ETSI, Second International Conference on Advances
in Human-Oriented and Personalized Mechanisms,
Technologies, and Services, pages 20–25.
Ramanathan, K. and Kapoor, K. (2009). Creating user pro-
files using wikipedia. In Conceptual Modeling - ER
2009 Springer-Verlag Berlin Heidelberg, 28th Inter-
national Conference on Conceptual Modeling, Gra-
mado, Brazil, November 9-12, 2009., pages 415–427.
Shmueli-Scheuer, M., Roitman, H., Carmel, D., Mass, Y.,
and Konopnicki, D. (2010). Extracting user profiles
from large scale data. In ACM International Con-
ference Proceeding Serie, Proceedings of the 2010
Workshop on Massive Data Analytics on the Cloud,
page Article No. 4.
Sieg, A., Mobasher, B., and Burke, R. (2007). Web search
personalization with ontological user profiles. In
ACM, Proceedings of the sixteenth ACM conference
on Conference on information and knowledge man-
agement, pages 525–534.
So, C., Lai, C., and Lau, R. (2009). Ontological user profil-
ing and language modeling for personalized informa-
tion services. In IEEE Computer Society, 2009 IEEE
International Conference on e-Business Engineering,
pages 559–564.
Tegegne, T., Kanagwa, B., and Weide, T. v. d. (2010). An
ehealth service discovery framework for a low infras-
tructure context. In 2nd Int. Conf. on Computer Tech-
nology and Development, Nov 2-4, Cairo, Egypt.
Wagner, M., Balke, T., Hirschfeld, R., and Kellerer,
W. (2002). A roadmap to advanced person-
alization of mobile services. In Workshops
DOA/ODBASE/CoopIS, IRvine, CA, In Proc. of the
Int. Federated Conferences DOA/ODBASE/CoopIS
(Industry Program). Irvine, CA, 2002.
Wang, H., Shi, X., Li, Y., Chang, H., Chen, W., and Tang,
J. (2008). User profile management for personalized
telecom service. In IEEE Computer Society, The 9th
International Conference for Young Computer Scien-
tists, pages 1087–1092.
Wang, Y. (2010). A framework for privacy-enhanced per-
sonalization. In PhD Dissertation, University of Cal-
ifornia, Irvine, PhD Dissertation.
Wang, Y. and Kobsa, A. (2009). Performance Evaluation
of a Privacy-Enhancing Framework for Personalized
Websites. Springer Verlag.
Zhang, D., Yu, Z., and Chin, X. (2004). Context-aware in-
frastructure for personalized healthcare. The Interna-
tional Workshop on Personalized Health, December
13-15, Belfast, Northern Ireland.
ICSOFT 2011 - 6th International Conference on Software and Data Technologies
346
