
ANALYSIS OF AD HOC ROUTING PROTOCOLS
FOR EMERGENCY AND RESCUE SCENARIOS
Liliana Enciso Quispe
1
, Rommel Torres Tandazo
1
and Luis Mengual Galan
2
1
Research Institute of Computer Science, Technical University of Loja, San Cayetano alto, Loja, Ecuador
2
Department of Computing, Politechnical University of Madrid, Monte de Boadilla, Madrid, Spain
Keywords:
Ad Hoc Networks, MANET, Routing, Mobility Models, AODV, DSDV, CBRP.
Abstract:
A mobile ad hoc network MANET is a collection of wireless mobile nodes that can dynamically configure a
network without a fixed infrastructure or centralized administration. This makes it ideal for emergency and
rescue scenarios where information sharing is essential and should occur as soon as possible. This article
discusses which of the routing strategies for mobile ad hoc networks: proactive, reactive and hierarchical,
have a better performance in such scenarios. Using a real urban area being set for the emergency and rescue
scenario, we calculate the density of nodes and the mobility model needed for validation. The NS2 simulator
has been used in our study. We also show that the hierarchical routing strategies are beffer suited for this type
of scenarios.
1 INTRODUCTION
Mobile Ad Hoc Networks(MANET), are self config-
uring and temporary networks . Their nodes can be
the source, destination and bridge information.
In case of emergency and rescue scenario, the to-
pography is different in the amount of obstacles that
may arise due to the occurrence of a undesired events
causing the normal mobility pathways to alter. There-
fore, the algorithm of motion is determined according
to the topography, and the corresponding nodes must
be moved depending on the obstacles. The number
of nodes depends if the MANET network is in an ur-
ban or in a rural area. When an unwanted event has
occurred, it changes the pathways of normal mobil-
ity. Therefore new routes for evacuation and or rescue
should be calculated.
When MANET are used in emergency and res-
cue scenarios, the choice of robust network protocol
is essential, because it involves indirect integrity of
the person using the mobile device. If a device is not
reachable by the network, the events of personal seach
and rescue should be desconected from the device.
The main objetive of this paper is to determine
wich one of the ad hoc routing strategies proactive, re-
active and hierarchical performs better in emergency
and rescue operations. For this reasor we have chosen
en area of the city of Loja Ecuador to simulate these
protocols supported by the NS2 tool.
2 RELATED WORK
2.1 Routing Protocols for Mobile Ad
Hoc Networks
The network layer (Ali et al., 2008), with respect to
the OSI reference model, is where one performs and
identifies the processes of ad hoc networks. There-
fore, any improvement effort in this layer is directly
visible in the upper layers.
The routing protocols of ad hoc networks are gen-
erally grouped into proactive, reactive and hierarchi-
cal routing (Overview and Selangor, 2007).
2.1.1 Proactive Routing
Proactive routing protocols maintain information on
all routes throughout the network even if they are not
required so each node maintains routes to all nodes
in the network. These protocols exchange control in-
formation between nodes on a regular basis which
keeps updated routes for each node in the network.
These protocols react when a new node appears or
another node, is no longer within the network topol-
ogy. The known protocols are: Destination-Sequence
Distance-Vector DSDV (Perkins and Bhagwat, 1994)
and Optimized Link State Routing OLSR (rfc3626).
781
Enciso Quispe L., Torres Tandazo R. and Mengual Galan L..
ANALYSIS OF AD HOC ROUTING PROTOCOLS FOR EMERGENCY AND RESCUE SCENARIOS.
DOI: 10.5220/0003941107810786
In Proceedings of the 8th International Conference on Web Information Systems and Technologies (WEBIST-2012), pages 781-786
ISBN: 978-989-8565-08-2
Copyright
c
2012 SCITEPRESS (Science and Technology Publications, Lda.)

Figure 1: Clustered ad hoc network.
2.1.2 Reactive Routing
Reactive routing protocols allow updating of the ta-
bles on demand, for example, when a node wants to
exchange information with another node in the net-
work. They usually have two components: route dis-
covery, which occurs when a node wants to commu-
nicate with a specific destination and route mainte-
nance, used to manage the path failure caused by the
mobility of the nodes.
The difficulty with these protocols is the latency
to initiate communications, they also have a slower
reaction to detect changes in the network topology.
Among the best known protocols are the Dynamic
Source Routing (DSR rcf4728) and Ad Hoc Demand
Distance Vector AODV (Perkins et al., 2003).
2.1.3 Hierarchical Routing
Hierarchical routing protocols divide the network into
subsets of nodes called clusters, where a cluster head
node is used to concentrate and distribute the informa-
tion generated within the cluster. An example of this
type of protocol is the Cluster Based Routing Protocol
(CBRP) (Jiang et al., 1999). Figure 1 shows the ba-
sic components of a hierarchical routing protocol or
cluster.
There are some studies (Agarwal and Motwani,
2009; Biradar and Patil, 2006), that identify and
group the hierarchical routing algorithms or cluster-
ing. These protocols and hierarchical routing strate-
gies focus on the task of choosing the cluster head
and cluster maintenance. For example, (Er and Seah,
2004; Er and Seah, 2005); focus on the choice of clus-
ter based solely on the property of the node mobil-
ity. In turn, (Jiang et al., 1999; Gerla and chieh Tsai,
1995; Amis et al., 2000); perform cluster head elec-
tion used as the deciding factor node identification.
(Chen et al., 2002) uses the distance between nodes or
the degree of connectivity for the election.(McDonald
and Znati, 1999) makes the choice of cluster head pe-
riodically in order to save energy. The protocols pro-
posed in (Er and Seah, 2004; Basagni et al., 2001;
Chatterjee et al., 2001) made the choice of cluster
head based on the combined weights of the charac-
teristics of each node.
2.2 Mobility Models for Mobile Ad Hoc
Networks
Mobility models are important because they deter-
mine the behavior of mobile nodes (MN) on stage
(Camp et al., 2002). They can be classified into two
types: those based on traces (logs of actual move-
ments) [14] and the synthetic (emulate reality by
mathematical equations). Some authors classify mo-
bility models into three groups (Camp et al., 2002):
models based on strokes (work with real mobility),
models based on topology restrictions (real scenario
simulations) and statistical models (study from ran-
domness).
Ad hoc networks do not work yet on models based
on traces on the network characteristics. Howerer, it
is expected that study will expand in future on the ap-
plication of these models (Camp et al., 2002). There-
fore, models of synthetic mobility are used fogether
with simulated scenarios. In order to prove this form
of controlled mobility, certain parameters are used,
which allow to obtain quantifiable date and thus to
transform them into useful informaties.
The synthetic models are classified according to
their relationship with the representation of human
mobility: synthetic mobility models unrealistic, for
example: random models (Divecha et al., 2007) (Ran-
dom Walk Mobility Model, Random Waypoint Mo-
bility Model), temporal dependency models (Hong
et al., 1999; Divecha et al., 2007) (Boundless Simu-
lation Area Mobility Model, Gauss-Markov Mobility
Model, Smooth Random Mobility Model) and real-
istic synthetic mobility models such as: spatial de-
pendence models (Hong et al., 1999; Chenchen et al.,
2010; Chenchen et al., 2010)(Reference Point Group
Mobility, Column Mobility Model, Pursue Mobility
Model, Nomadic Mobility Model) Geographic Re-
striction Models (Chenchen et al., 2010; Aschenbruck
et al., 2008) (Pathway Models, Obstacle Models, Hu-
man Obstacle Mobility Model).
3 PROPOSED SCENARIO
3.1 Emergency and Rescue Scenario for
Centre of the City of Loja
Random obstacles have been defined in this area of
WEBIST2012-8thInternationalConferenceonWebInformationSystemsandTechnologies
782
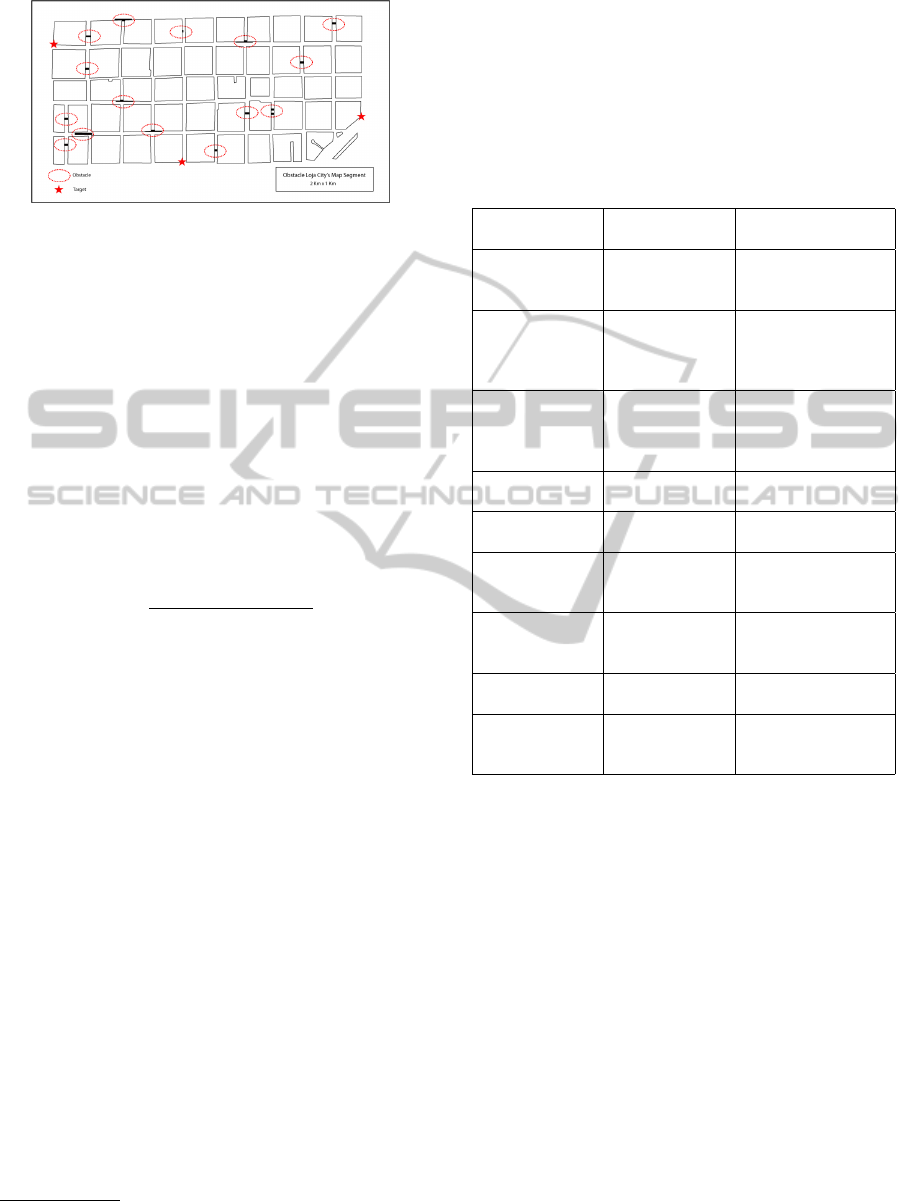
Figure 2: Loja city map without obstacles.
1000mx500m of the city Loja is used in Ecuador, Fig-
ure 2, that disrupt normal mobility pathways of the
nodes.
3.2 Node Density
The calculation of the node density P
node
is supported
by information obtained from the census of Ecuador
in 2010.
1
An important factor for the calculation of
the nodes is the percentage of the PEA (Economically
Active Population).
To calculate the density of nodes the following
formula has been proposed:
P
nodes
=
zu
l
∗ F
uel
∗ F
PEA
∗ F
us
A
zu
∗ A
s
(1)
P
nodes
= 97 (2)
Where:
• zu
l
- Number of people in the urban areas is 70%
(128910)
• zr
l
- Number of people in the rural areas is 30%
(85940).
• F
uel
- urban factor specified for the simulation area
• A
z
u - Urban area - 6Km x 12Km = 72Km
2
.
• F
PEA
- LOJA - PEA is 62% for urban area.
• F
us
- urban smartphone factor is 25% .
• A
s
- Chosen area for simulation 0.5km
2
.
It is important to describe the city of Loja for
which this study has been done, it is a city in the
southern part of Ecuador. Populatio it the city in-
creases during the holidays, and it grows also due to
arriving of tourists attracted by its location and biodi-
versity. Given this premise, we established percent-
ages of 25.75% (F
us
)and 30.8% (F
us
) to calculate the
other two densities nodes P
nodes
, substituting these
values into the formula(1) we find that the rearsong
1
National Institute of Statistics and Censuses (INEC).
http://www.inec.gob.ec
nodes are equal to 100 (25.75%) and 120 ( 30.8%),
respectiving.
Consequently the number of nodes for the simula-
tion is: 97, 100 and 120.
3.3 General Parameters for Simulation
Table 1: General parameters for the simulation of protocols
AODV, DSDV and CBRP.
Parameter Value Observations and
related works
Simulation area 500m x 1000m Area established
within the centre of
the city of Loja
Mobility model Obstacle Mod-
els
Obstacle models
(Chenchen et al.,
2010; Aschenbruck
et al., 2008)
Number of
nodes
97,100 and 120 To determine the
behaviour of pro-
tocols for different
node density
Number of con-
nections
20, 40 random connec-
tions
Time of simula-
tion
150 In seconds
Network layer
protocols
CBRP, DSDV
and AODV
Hierarchical,
proactive and
reactive protocols
Transport layer
protocols
Transmission
control proto-
col (TCP)
A connection-
oriented communi-
cation is needed
Propagation
model
TwoRayGround For flat and unob-
structed scenarios.
Type of antenna Omnidirectional Indispensable qual-
ity of mobile net-
work nodes
To define the simulation scenarios were used as
the basis used in (Kurkowski et al., 2007a; Kurkowski
et al., 2007b). The values of each one of these values
are shown in the Table 1.
In order to analyze results, some authors have re-
vised set of indicators. For our research we select
some particular indicaters from (Chenna Reddy and
ChandraSekhar Reddy, 2006; Corson and Macker,
1999) in order to measure behavior of protocols.
These indicators are: performance, protocol over-
head, packet loss, average delay and the variation of
the delay or jitter. These indicators are compared
with those of the following protocols: CBRP(Jiang
et al., 1999), AODV(Perkins et al., 2003) and
DSDV(Perkins and Bhagwat, 1994).
ANALYSISOFADHOCROUTINGPROTOCOLSFOREMERGENCYANDRESCUESCENARIOS
783
4 SIMULATION RESULTS
The NS2 simulator (NS, 2012) is used to determine
the protocols behaviour with the data shown in Ta-
ble 1. In order to determine which is the best protocol,
we used the following indicators for comparison:
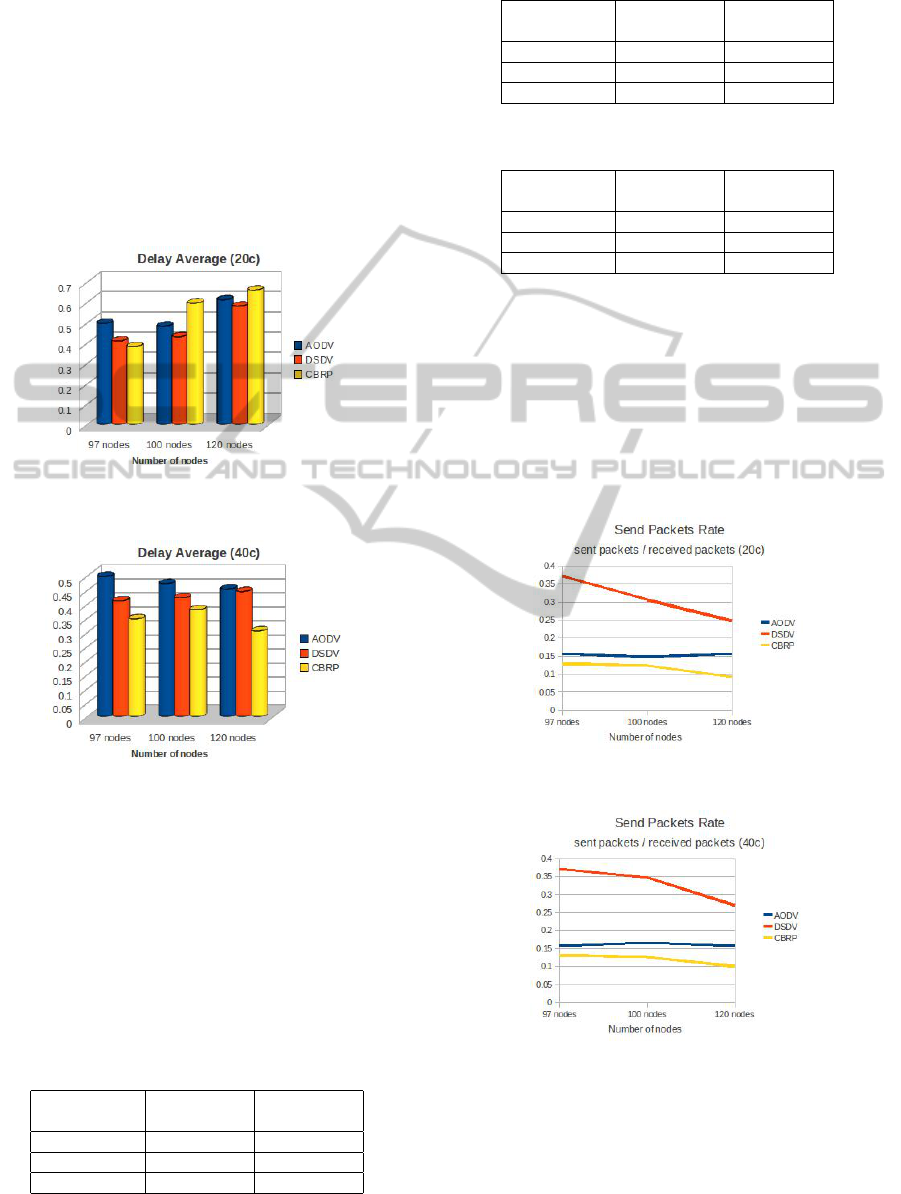
• Average Delay: This is very significant to mea-
sure for our purpose because there is a need to
send and receive network managment information
as fast as possible.
Figure 3: Delay average - TCP - 20 connections.
Figure 4: Delay average - TCP - 40 connections.
In this parameter as shown in Figure 3 to 20 con-
nections with 97 nodos the 3 protocols behaviour
optimal according to their characteristics, but 100
and 120 nodes CBRP protocol suffers small de-
lay. Instead with 40 connections as seen in Fig-
ure 4 already panorama changes to demonstrate
advantage that protocol CBRP regarding proto-
cols AODV and DSDV. Data in Table 2, Table 3,
Table 4.
Table 2: AODV protocols analysis - delay average.
Number of
nodes
AODV(20c) AODV(40c)
97 0.498009 0.498009
100 0.483952 0.471993
120 0.613480 0.452916
Table 3: DSDV protocols analysis - delay average.
Number of
nodes
DSDV(20c) DSDV(40c)
97 0.411367 0.411367
100 0.432102 0.421802
120 0.582582 0.444208
Table 4: CBRP protocols analysis - delay average.
Number of
nodes
CBRP(20c) CBRP(40c)
97 0.383271 0.346918
100 0.597227 0.379617
120 0.660971 0.303840
• Packets Sent Rate: The rate obtained by the
number of packets sent to the number of pack-
ets received. For the formation and maintenance
the cluster needs the exchange of packets to have
updated information. As shown in Figure 5 and
Figure 6. The protocol that best responds to this
parameter is the CBRP protocol for both 20 as for
the 40 connections.
Figure 5: Send packet rate 20 connections.
Figure 6: Send packet rate 40 connections.
• Packet Delay Variation: It is the difference
in delay between communications end-to-end se-
lected packets. It serves to measure the network
stability and convergence, in Ad Hoc networks.
This parameter is related to the mean fluctuation
WEBIST2012-8thInternationalConferenceonWebInformationSystemsandTechnologies
784
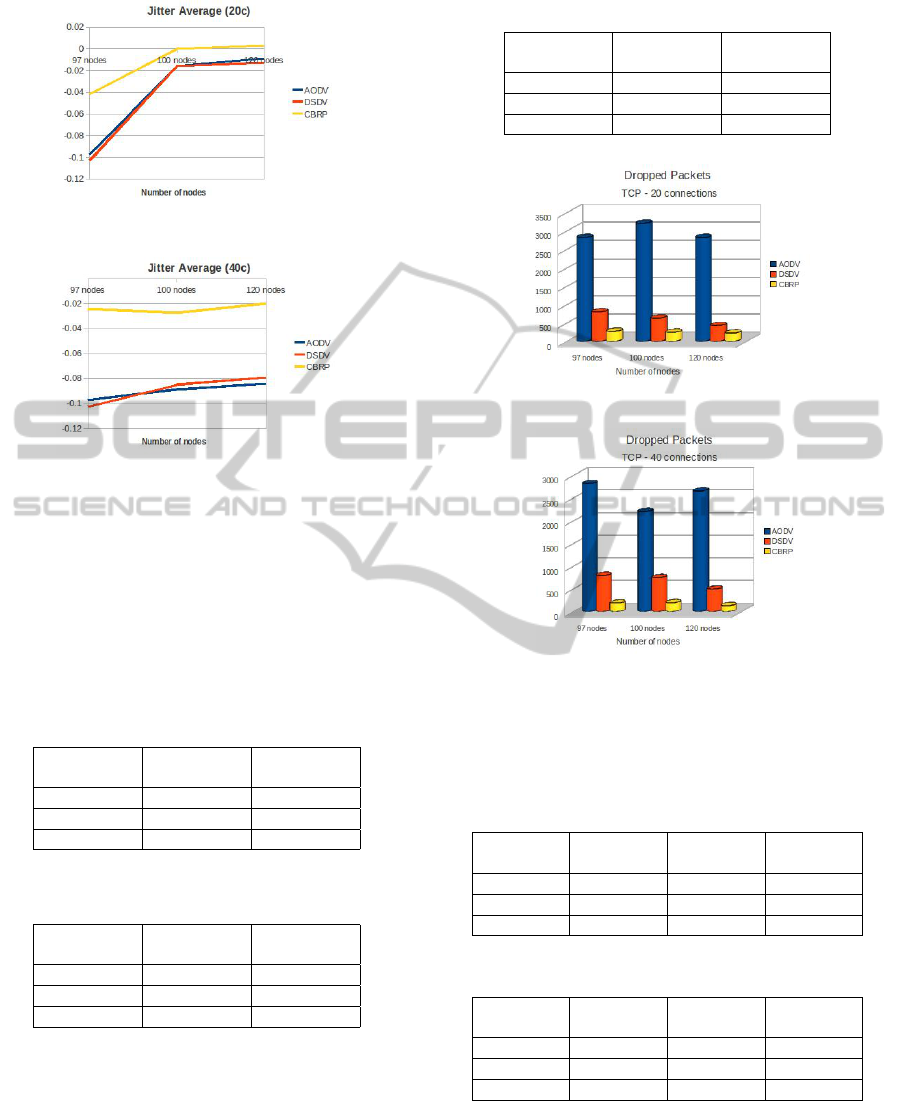
Figure 7: Jitter average TCP 20 connections.
Figure 8: Jitter average TCP 40 connections.
and helps us to determine which of the three pro-
tocols would be the most appropriate at the time
to emergency and rescue. as we can see that this
parameter as the two above parameters shows that
the protocol is nearest zero consequently has jitter
lower the protocol CBRP as seen in Figure 7 and
Figure 8. The simulation results are set to Table 5,
Table 6, Table 7.
Table 5: AODV protocols analysis - jitter average.
Number of
nodes
AODV(20c) AODV(40c)
97 -0.097499 -0.097499
100 -0.015795 -0.088908
120 -0.009072 -0.084256
Table 6: DSDV protocols analysis - jitter average.
Number of
nodes
DSDV(20c) DSDV(40c)
97 -0.102806 -0.102806
100 -0.015821 -0.085109
120 -0.01274 -0.079349
• Packet Loss: This is the amount of packets
dropped by intermediate nodes due to the effects
produced by the mobility of these nodes, timer ex-
pires, unreachable or erased destination by ARP
(Address Resolution Protocol).
The objective of the simulation was to determine
which of these three protocols behave better in emer-
gency and rescue scenarios and how we can seen in
Table 7: CBRP protocols analysis - jitter average.
Number of
nodes
CBRP(20c) CBRP(40c)
97 -0.041516 -0.024319
100 -0.000214 -0.027638
120 0.003136 -0.019921
Figure 9: Dropped packets - 20 connections.
Figure 10: Dropped packets - 40 connections.
Figure 9 Figure 10 CBRP protocol clears least pack-
ets with 20 connections and even better with 40 con-
nections. The data are shown in Table 8 y Table 9.
Table 8: Dropped packets - 20 connections.
Number of
nodes
AODV(20c) DSDV(20c) CBRP(20c)
97 2820 799 269
100 3207 631 245
120 2819 429 222
Table 9: Dropped packets - 40 connections.
Number of
nodes
AODV(40c) DSDV(40c) CBRP(40c)
97 2820 799 187
100 2206 751 196
120 2659 496 133
5 CONCLUSIONS
• Traditional routing algorithms cannot satisfy re-
quirements of an ad hoc networks, because of to-
ANALYSISOFADHOCROUTINGPROTOCOLSFOREMERGENCYANDRESCUESCENARIOS
785

pology dynamics and limited bandwidth charac-
terizing these networks. Consequently, there area
lot of investigation related to existing routing al-
gorithms land there is discovering of new routing
algorithms, which are more efficient.
• This study evaluate and compare CBRP, AODV
and DSDV for emergency and rescue scenarios.
The experimental results show that the best pro-
tocol is CBRP that losses only few packets for
routing, where is the sending and receiving rate
of packets is stable. The mean fluctuation and the
delay is much smaller in relation to the other two
protocols. This would support determine that us-
ing the protocol CBRP people in a disaster area
could be evacuated to more efficiently support
points as would be placed promptly.
REFERENCES
Agarwal, R. and Motwani, M. (2009). Survey of clustering
algorithms for manet.
Ali, N. Z., Ahmad, R. B., and Aljunid, S. A. (2008).
Link Availability Estimation for Routing Metrics in
MANETs : An Overview. Time, pages 6–8.
Amis, A., Prakash, R., Vuong, T., and Huynh, D. (2000).
Max-min d-cluster formation in wireless ad hoc net-
works. In INFOCOM 2000. Nineteenth Annual Joint
Conference of the IEEE Computer and Communica-
tions Societies. Proceedings. IEEE, volume 1, pages
32 –41 vol.1.
Aschenbruck, N., Gerhards-Padilla, E., and Martini, P.
(2008). A survey on mobility models for performance
analysis in tactical mobile networks.
Basagni, S., Turgut, D., and Das, S. (2001). Mobility-
adaptive protocols for managing large ad hoc net-
works. In Communications, 2001. ICC 2001. IEEE
International Conference on, volume 5, pages 1539
–1543 vol.5.
Biradar, R. and Patil, V. (2006). Classification and compari-
son of routing techniques in wireless ad hoc networks.
In Ad Hoc and Ubiquitous Computing, 2006. ISAUHC
’06. International Symposium on, pages 7 –12.
Camp, T., Boleng, J., and Davies, V. (2002). A survey of
mobility models for ad hoc network research. Wire-
less Communications & Mobile Computing (WCMC):
Special Issue on Mobile Ad Hoc Networking: Re-
search, Trends and Applications, 2:483–502.
Chatterjee, M., Das, S. K., and Turgut, D. (2001). Wca: A
weighted clustering algorithm for mobile ad hoc net-
works.
Chen, G., Nocetti, F., Gonzalez, J., and Stojmenovic, I.
(2002). Connectivity based k-hop clustering in wire-
less networks. In System Sciences, 2002. HICSS.
Proceedings of the 35th Annual Hawaii International
Conference on, pages 2450 – 2459.
Chenchen, Y., Xiaohong, L., and Dafang, Z. (2010). An ob-
stacle avoidance mobility model. In Intelligent Com-
puting and Intelligent Systems (ICIS), 2010 IEEE In-
ternational Conference on, volume 3, pages 130 –134.
Chenna Reddy, P. and ChandraSekhar Reddy, P. (2006).
Performance analysis of adhoc network routing pro-
tocols. In Ad Hoc and Ubiquitous Computing, 2006.
ISAUHC ’06. International Symposium on, pages 186
–187.
Corson, S. and Macker, J. (1999). Mobile Ad hoc Network-
ing (MANET): Routing Protocol Performance Issues
and Evaluation Considerations. RFC 2501 (Standard).
Divecha, B., Abraham, A., Grosan, C., and Sanyal, S.
(2007). Impact of node mobility on manet routing pro-
tocols models.
Er, I. and Seah, W. (2004). Mobility-based d-hop cluster-
ing algorithm for mobile ad hoc networks. In Wireless
Communications and Networking Conference, 2004.
WCNC. 2004 IEEE, volume 4, pages 2359 – 2364
Vol.4.
Er, I. and Seah, W. (2005). Clustering overhead and conver-
gence time analysis of the mobility-based multi-hop
clustering algorithm for mobile ad hoc networks. In
Parallel and Distributed Systems, 2005. Proceedings.
11th International Conference on, volume 2, pages
130 –134.
Gerla, M. and chieh Tsai, J. T. (1995). Multicluster, mo-
bile, multimedia radio network. Journal of Wireless
Networks, 1:255–265.
Hong, X., Gerla, M., Pei, G., and Chiang, C.-C. (1999). A
group mobility model for ad hoc wireless networks. In
Proceedings of the 2nd ACM international workshop
on Modeling, analysis and simulation of wireless and
mobile systems, MSWiM ’99, pages 53–60. ACM.
Jiang, M., Li, J., and Tay, Y. C. (1999). Cluster based rout-
ing protocol (cbrp) functional specification, internet
draft, manet working group.
Kurkowski, S., Navidi, W., and Camp, T. (2007a). Con-
structing manet simulation scenarios that meet stan-
dards. In Mobile Adhoc and Sensor Systems, 2007.
MASS 2007. IEEE Internatonal Conference on, pages
1 –9.
Kurkowski, S., Navidi, W., and Camp, T. (2007b). Dis-
covering variables that affect manet protocol perfor-
mance. In Global Telecommunications Conference,
2007. GLOBECOM ’07. IEEE, pages 1237 –1242.
McDonald, A. and Znati, T. (1999). A mobility-based
framework for adaptive clustering in wireless ad hoc
networks. Selected Areas in Communications, IEEE
Journal on, 17(8):1466 –1487.
NS (2012). The Network Simulator NS-2.
http://www.isi.edu/nsnam/ns/.
Overview, R.-A. and Selangor, U. P. M. S. (2007). Exist-
ing MANET routing protocols and metrics used to-
wards the efficiency and reliability- an overview. In
2007 IEEE International Conference on Telecommu-
nications and Malaysia International Conference on
Communications, pages 231–236. Ieee.
Perkins, C., Belding-Royer, E., and Das, S. (2003). Ad
hoc on-demand distance vector (aodv) routing. United
States. RFC Editor.
Perkins, C. E. and Bhagwat, P. (1994). Highly dynamic
destination-sequenced distance-vector routing (dsdv)
for mobile computers. pages 234–244.
WEBIST2012-8thInternationalConferenceonWebInformationSystemsandTechnologies
786
