
Detecting Infeasible Traces in Process Models
Zhaoxia Wang
1,2,3,4,5
, Lijie Wen
1,3,4
, Xiaochen Zhu
1,2,3,4
, Yingbo Liu
1,3,4
and Jianmin Wang
1,3,4
1
School of Software, Tsinghua University, Beijing 100084, China
2
Department of Computer Science & Technology, Tsinghua University, Beijing 100084, China
3
Key Lab for Information System Security, Ministry of Education, Beijing 100084, China
4
National Laboratory for Information Science and Technology, Beijing 100084, China
5
Logistical Engineering University, Chongqing 400016, China
Keywords:
Infeasible Traces, Process Models, Workflow Analysis.
Abstract:
Workflow testing is an important method of workflow analysis in design time. A challenging problem with
trace-oriented test data generation in particular and trace-based workflow analysis in general is the existence
of infeasible traces for which there is no input data for them to be executed. In this paper we build on the
theory of workflow nets and introduce workflow nets where transitions have conditions associated with them.
We then demonstrate that we can determine which execution traces, that are possible according to the control-
flow dependencies, are actually possible taking the data perspective into account. This way we are able to
more accurately determine in design time the infeasible traces caused by the correlation between transition
conditions along this trace. Finally, we provide a solution to automatically detecting the shortest infeasible
trace.
1 INTRODUCTION
Workflow testing is an important method of workflow
analysis in design time (van der Aalst and ter Hofst-
ede, 2000). However, test data generation is an ex-
tremely complicated and time-consuming task as it
requires a careful analysis and understanding of the
source code and knowledge of the underlying con-
cepts of the testing criterion. For this reason, automa-
tion of test data generation may provide a significant
cost and time reduction for workflowtesting. In trace-
oriented test data generation, a set of traces is selected
which satisfies one or more coverage criteria and test
data are generated to exercise these traces. A chal-
lenging problem with trace-oriented test data genera-
tion in particular and trace-based workflowanalysis in
general is the existence of infeasible traces for which
there is no input data for them to be executed. In this
case, considerable effort might be wasted in trying to
generate data for infeasible traces.
In software engineering domain, detection of
branch condition and branch correlation is a kind of
important methods in path feasibility analysis(Ngo
and Tan, 2008). Here, inspired by the approaches of
detecting the infeasible paths in software engineering
domain we propose an approach to detect the infeasi-
ble traces in process model.
For instance, for the simplified example model for
loan process (shown in Figure 1), the traces t
1
t
2
(t
3
t
2
)∗
t
4
t
5
t
8
t
10
and t
1
t
2
(t
3
t
2
) ∗t
4
t
6
t
9
become infeasible when
transition conditions are taken into account. The rea-
son of traces t
1
t
2
(t
3
t
2
) ∗ t
4
t
5
t
8
t
10
non-existing is that
the conjunctive transition conditions c
3
∧c
4
on transi-
tion t
10
along t
1
t
2
(t
3
t
2
)∗t
4
t
5
t
8
t
10
are not satisfied, they
are then non-executable (that is, they are infeasible
traces).
In this paper, we build on the theory of work-
flow nets and introduce workflow nets where transi-
tions have conditions associated with them. This way
we are able to more accurately determine in design
time the infeasible traces caused by the correlation be-
tween transition conditions.
The rest of this paper is organized as follows. First
a formal definition of workflow nets with transition
conditions or WTC-nets for short is given and we pro-
pose a reachability analysis approach based on the
behavioural semantic of WTC-nets to detect the in-
feasible traces in process models (Section 2). We im-
plement a tool to support the proposed approach and
this tool is used to apply the approach to a number of
real-life models (Section 3). Section 4 discusses the
related work and Section 5 concludes the paper.
212
Wang Z., Wen L., Zhu X., Liu Y. and Wang J..
Detecting Infeasible Traces in Process Models.
DOI: 10.5220/0003989002120217
In Proceedings of the 14th International Conference on Enterprise Information Systems (ICEIS-2012), pages 212-217
ISBN: 978-989-8565-12-9
Copyright
c
2012 SCITEPRESS (Science and Technology Publications, Lda.)

[c
1
]
[c
2
]
t
2
t
3
i
w: d
2
,d
3
p
1
p
2
t
4
The set of condition variables
d
1
: info_complete d
2
: loan amount d
3
: risk
The set of transitions T
t
1
: receive_application t
2
: verify_application t
3
: modify_application
t
4
: check_loan amount t
5
: check risk t
7
: modify-loan
t
9
: approve by manager t
10
: approve by officer t
6
, t
8
: silent task
t
1
w: d
1
w: d
3
[c
4
]
t
5
p
3
[c
3
]
t
6
[c
6
]
t
7
p
4
p
5
t
8
[c
4
]
t
9
[c
3
]
o
t
10
[c
5
]
w: d
2
The set of conditions
c
1
: ¬d
1
c
2
: d
1
c
3
: d
2
>50,000 c
4
: d
2
<=50,000 c
5
: d
3
c
6
: ¬d
3
Figure 1: A workflow model for the simplified loan process.
2 PRELIMINARIES
In this section we briefly introduce workflow nets
with transition conditions (for short, WTC-nets).
WTC-nets are based on Petri nets and workflow nets.
In order to make the paper self-contained, some well-
known definitions are introduced first.
2.1 Background
Below, we define Petri nets first. For an overview of
Petri nets and an extensive bibliography the reader is
referred to (Murata, 1989).
Definition 1 (Petri net). A Petri net N is a tuple
(P,T, F) where P is a finite set of places, T is a fi-
nite set of transitions such that P∩T = ∅, P∪T 6= ∅,
and F ⊆ (P× T) ∪ (T × P) is the flow relation.
For each node x, i.e. a place or a transition, we
use •x to denote its pre-set - the set of nodes which
are input of x - i.e. •x = {y|(y, x) ∈ F}, and x• for its
post-set - the set of nodes which are output of x - i.e.
x• = {y|(x, y) ∈ F}.
Definition 2 (Marking). Let N = (P, T, F) be a Petri
net, a marking M of N is a function from its places to
the set of natural numbers, i.e. M : P → N.
Transitions can change the marking of a Petri net
if they are fired. van der Aalst defines workflow nets
by imposing certain syntactical restrictions on Petri
nets (van der Aalst, 1998).
Definition 3 (Workflow net). A Workflow net P is a
Petri net (P, T, F) such that there is a unique source
place i, •i = ∅, a unique sink place o, o• = ∅, and
such that every node x ∈ P∪ T is on a path from i to
o.
The initial marking for a workflow net, or WF-
net for short, corresponds to one token in its initial
place and thus formally corresponds to i. The desired
final marking is the marking that has one token in the
output place o and no tokens in any other places.
2.2 Workflow Nets with Transition
Conditions
Central to WTC-nets is the notion of a condition. Here
we only informally describe condition class cond. A
condition c is an instance of cond.
The expression form of the class cond is a logical
expression. The operators used in cond include com-
parison operators (eg. le, leq, ge, geq,eq), arithmeti-
cal operators (eg. plus, minus, times, frac, mod, div),
boolean operators (eg. neg, and, or, implies). The data
type in cond contains int, real and bool. For a vari-
able v used in a cond, the domain of v is a set of val-
ues that v can hold. The notion var is used as the set
of all variables as well as the notion VAR is used as the
set of all possible assignments of types to varianbles.
In addition, function V
var
() is applied to a condition
to yield the variables that are used in this condition.
A WF-net with transition conditions, or WTC-net
for short, is a WF-net where the transitions are as-
signed conditions. We give an assumption that the
variables that a transition can write to, may take on
any value as a result of its execution.
Definition 4 (Workflow net with transition condi-
tions). A workflow net with transition conditions W
is a tuple (P ,V,C, G,W, TV), such that:
• P = (P, T, F) is a WF-net;
• V ⊆ var is a set of net variables;
DetectingInfeasibleTracesinProcessModels
213

• C ⊆ cond is a set of transition conditions with
∪
c∈C
V
var
(c) ⊆ V;
• G : T → C is a function assigning conditions to
transitions;
• W : T → 2
V
is a function that yields the variables
that transitions can write to;
• TV ∈ VAR is a function assigning a type to each
net variable.
Definition 5 (Marking of WTC-net). For a WTC-
net W = (P ,V,C, G,W, TV), a marking M is a tu-
ple (M, σ), where M is a marking of WF-net P , and
σ ∈ T
∗
is a sequence of transitions.
The initial marking of this net M
0
is defined as
(i, ε), where i is the unique source place of W , ε is
empty sequence.
Subsequently we formally define whether transi-
tion condition is satisfied in the context of a particular
assignment of values to variables. Given an assign-
ment as an environment e and the set of all possible
environments as ENV. The set of all possible values
is denoted as Val and it is defined as the union of all
integers, reals, and booleans, i.e. Val = Z ∪ R ∪ B.
Definition 6 (Satisfiability of conditions). Let TV :
var → Types be an assignment of types to variables
and let c be a condition in the context of type as-
signment TV, i.e., c ∈ cond, e : var → Val an as-
signment of values to variables, and the function
V
holds
: cond × ENV → bool can be applied to deter-
mine whether in the context of a given environment a
condition holds.
In order to evaluate if in the context of a transition
sequence σ a given transition condition φ hold, we
need to take into account the variables that are used
in the transition conditions of transitions in σ and in
φ as well as the order in which variables may be writ-
ten by transitions in σ. To solve this problem, we in-
troduce fresh variables as replacements for variables
used in transition conditions of transitions whenever
it turns out that these variables could have received a
new value through the execution of preceding transi-
tions. Fresh variables in a transition sequence σ take
the form v
n
t
where t is a transition which could write
v, i.e. v ∈ W(t), and n is a natural number, which for
a particular occurrence of transition t in σ represents
the number of previous occurrences of t in σ (this is
required in order to be able to deal with loops). We
assume that variables of the form v
n
t
do not occur as
net variables in a WTC-net, so that indeed they will
be fresh whenever introduced. We also assume that
given a renaming function ψ : var var and a con-
dition c ∈ cond, c[ψ] denotes condition c where for
every variable v ∈ V
var
(c)∩ dom(ψ) each of its occur-
rences has been replaced by ψ(v).
Definition 7 (Conjunctive transition conditions). Let
W = (P ,V,C, G,W, TV) be a WTC-net, σ ∈ T
∗
a
transition sequence (possibly empty, i.e. σ = ε), ψ :
var var a renaming of variables, G(t)[ψ] chang-
ing transition condition according to this renaming,
n : T → N an assignment of natural numbers to transi-
tions, and b is any boolean expression. The conjunc-
tive transition conditions along sequence with vari-
ables renaming ρ
ψ, n
(σ, b) is defined by:
ρ
ψ, n
(ε, b) = b
ρ
ψ, n
(tσ, b) = ρ
ψ
′
, n
′
(σ, b∧ G(t)[ψ]) where
ψ
′
= ψ ⊕ {(v, v
n(t)
t
) | v ∈ W(t)} and n
′
= n⊕
{(t, n(t) + 1)}
We are now in a position to formally define when
a transition in a WTC-net is enabled in the context of
a given marking.
Definition 8 (Enabled transition in WTC-net). Let
W = (P ,V,C, G,W, TV) be a WTC-net, M = (M, σ)
be a marking of this net, and t ∈ T a transi-
tion in this net. Let b be a conjunctive transition
conditions with variables renaming defined by b =
ρ
∅, {(t, 0) | t∈T}
(σ,true). Transition t is enabled in
marking M , M [t >, iff an environment e : V
var
(b) →
Val can be found such that V
holds
(b, e, TV).
Definition 9 (Firing). Let W = (P ,V,C, G,W, TV) be
a WTC-net, M = (M, σ) be a marking of this net,
and t ∈ T an enabled transition. Firing transition t
in marking M results in marking M
′
= (t • ∪(M\ •
t), σt). As per usual, we write M
t
→ M
′
.
Table 1: Deriving the conjunctive form of transition condi-
tions along sequence t
1
t
2
t
3
t
2
t
4
for WTC-net in Figure 1.
TS
1
VR
2
TCT
3
CTC
4
t
1
d
2
1
t
1
, d
3
1
t
1
t
2
d
1
1
t
2
t
3
¬d
1
1
t
2
¬d
1
1
t
2
t
2
d
1
2
t
2
¬d
1
1
t
2
t
4
d
1
2
t
2
¬d
1
1
t
2
∧ d
1
2
t
2
1
Transition Sequence.
2
Variable Renaming.
3
Transition Condition Transformation.
4
Conjunctive Transition Conditions.
Example. Assuming for the WTC-net sample in
the Figure 1, given a current marking (p
2
,t
1
t
2
t
3
t
2
),
let us consider transition t
4
can be enabled or not.
Firstly, we observe how to derive the conjunctive
form of transition conditions for transition t
4
along
the sequence t
1
t
2
t
3
t
2
t
4
. As shown in the first col-
umn of Table 1, variable d
1
is written twice by tran-
sition t
2
. Once each writing operation happens, d
1
ICEIS2012-14thInternationalConferenceonEnterpriseInformationSystems
214

is mapped into a new fresh variable as shown in the
second column of Table 1. For example, variable d
1
is mapped into d
1
1
t
2
and d
1
2
t
2
respectively along the
sequence t
1
t
2
t
3
t
2
. The corresponding transition con-
dition is then changed based on the closest preced-
ing variable renaming as shown in the third column
in Table 1. For instance, the transition condition of
transition t
3
in the sequence is changed as ¬d
1
1
t
2
fol-
lowing the closest preceding variable renaming d
1
1
t
2
.
The fourth column in Table 1 describes the dynamic
evolution of the conjunctive form of transition condi-
tions along the sequence. For the conjunctive form of
transition conditions ¬d
1
1
t
2
∧ d
1
2
t
2
, there is at least an
assignment of value false to d
1
1
t
2
and value true to d
1
2
t
2
which make the conjunctive form hold. Therefore,
transition t
4
is enabled and then fired in the current
marking (p
2
,t
1
t
2
t
3
t
2
).
Definition 10 (Reachable marking). Let W =
(P ,V,C, G,W, TV) be a WTC-net, a marking (M, σ)
with σ=t
1
. . .t
n
is reachable iff a sequence of reach-
able markings M
0
M
1
. . . M
n
exists such that (i, ε)
t
1
→
(M
1
,t
1
)
t
2
→ (M
2
,t
1
t
2
)
t
3
→ . . .
t
n−1
→ (M
n−1
,t
1
. . .t
n−1
)
t
n
→
(M
n
,t
1
. . .t
n
) with M
n
= M.
With the behavioural semantics of a WTC-net sys-
tem, we propose an extended coverability graph Al-
gorithm based on that Finkel has proposed in (Finkel,
1991). The constructed graph of Figure 1 is shown
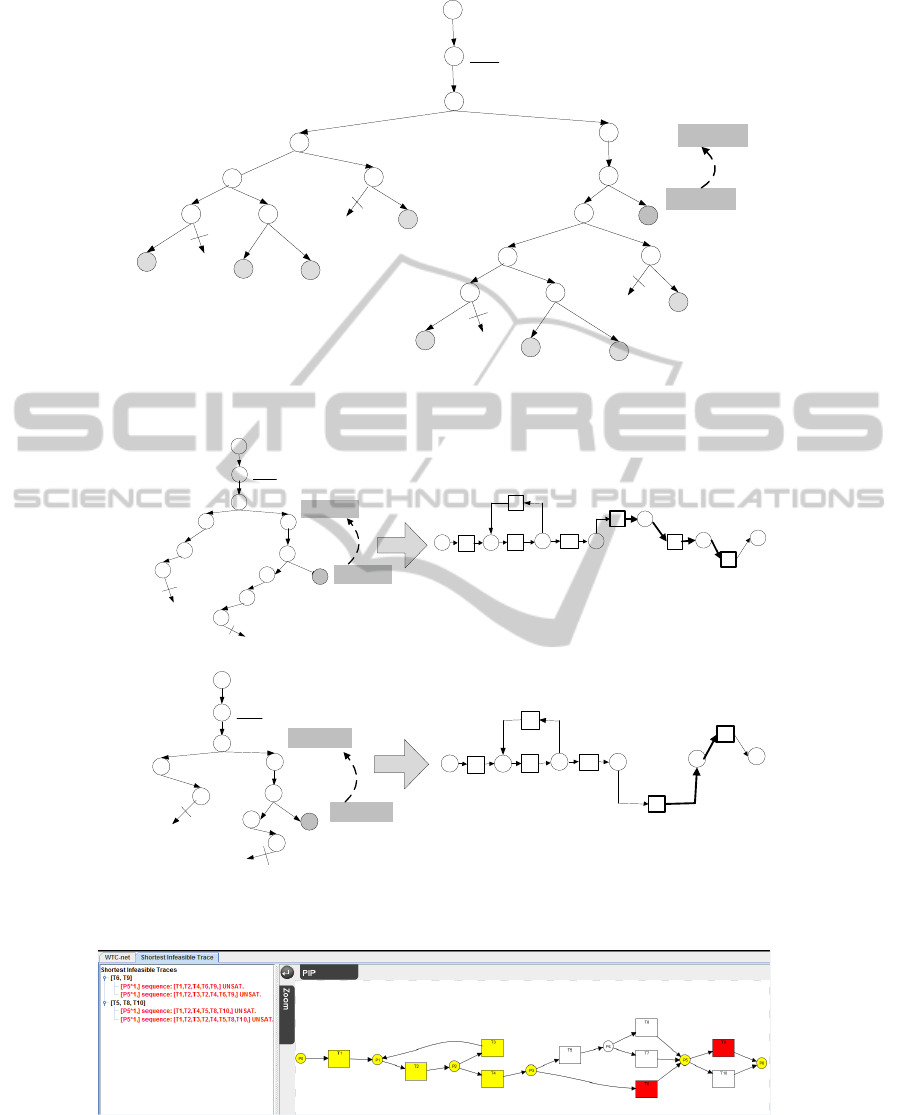
in Figure 2 [An aside: any node with gray cycle is a
dead node, node 2 (p
1
,t
1
) is the start state of the first
cyclic execution t
2
t
3
, node 4 and node 9 labeled with
(p
1
, {(t
3
, c
1
)}) are the start state of the second round
and third round of cyclic execution t
2
t
3
respectively,
Thus, the repeating of the cyclic executions is termi-
nated in the start state of the third round by merging
the node 9 to node 4 with the directed dotted arc].
2.3 Infeasible Trace of WTC-net
In this section, we will describe formally the seman-
tics of the infeasible traces of WTC-nets.
Definition 11 (Infeasible Trace). Let W =
(P ,V,C, G,W, TV) be a WTC-net, (M, σ) be a
marking of W , t be a transition with guard function
G(t), σ = t
1
...t
n
is the executable prefix of transition
t as well as trace σ·t is infeasible, iif:
i. M[t >, and
ii. there is an environment e : var ∪ ran(ψ) Val
such that for all 1 ≤ i ≤ |σ|,
V
holds
(ρ
∅, {(t, 0) | t∈ T }
(σ,true), e, TV), and
¬(V
holds
(ρ
∅, {(t, 0) | t∈T}
(σ.t, true), e, TV)).
Definition 12 (Correlation between transition condi-
tions). Given two transition conditions c
1
and c
2
as-
signed to guard function of t
1
and t
2
respectively. They
are correlated, iif:
(1) c
1
and c
2
reference common condition variables,
i.e, they have common condition variable set V
c
=
(v
1
, v
2
, ..., v
m
),
(2) there is a trace from t
1
to t
2
such that at least one
variable in V
c
isn’t written.
Subsequently, we propose a backward search
algorithm on the generated coverability graph to
search the shortest infeasible trace [An aside: in
view of the limitation of space, for full details about
the algorithms we proposed the readers are referred
to http://laudms.thss.tsinghua.edu.cn/trac/Test/wiki/
chengguo/ICEIS2012.pdf].
Figure 3 shows the result of this detecting algo-
rithm. The set of infeasible traces t
1
t
2
(t
3
t
2
)
∗
t
4
t
5
t
8
t
10
is caused by correlation relationship between transi-
tion condition c
3
on t
5
and transition condition c
4
on
t
10
as well t
1
t
2
(t
3
t
2
)
∗
t
4
t
6
t
9
caused by correlation re-
lationship between transition condition c
4
on t
6
and
transition condition c
3
on t
9
.
3 EXPERIMENTS
We implemented the proposed approach for detecting
the infeasible traces of WTC-nets. We made use of a
well-known, open-source process analysis framework
(ProM) (van der Aalst et al., 2009) and developed our
tool as a ProM 6 analysis plug-in
1
. Figure 4 shows
the returned result of detecting the infeasible traces in
Figure 1.
Subsequently, we illustrate the applicability of our
approach to real process models by carrying out ex-
periments that are based on process models and data
information related with transition conditions found
in the TiPLM system
2
. These 29 collected real pro-
cess models are divided into 4 types: engineering de-
sign and review (DR), process engineeringand chang-
ing (PC), release management (RM), and applica-
tion management (AM). Firstly, we transformed the
TiPLM workflow models and the extracted data in-
formation from TiPLM database into WTC-net mod-
els. We then used the implemented tool to detect the
infeasible traces.
1
The ProM framework can be downloaded from
http://www.processmining.org/
2
TiPLM is a product life-cycle management solu-
tion, which is developed by THsoft InfoTech company
(http://www.thit.com.cn) and widely used in Mainland
China (well over 100 companies in the manufacturing in-
dustry in China adopted the TiPLM system).
DetectingInfeasibleTracesinProcessModels
215
(i, ε)
(p
1
, t
1
)
(p
2
, t
1
t
2
)
(p
1
, t
1
t
2
t
3
)
(p
3
, t
1
t
2
t
4
)
(p
4
, t
1
t
2
t
4
t
5
)
(p
5
, t
1
t
2
t
4
t
6
)
(o, t
1
t
2
t
4
t
6
t
10
)
t
8
(p
5
, t
1
t
2
t
4
t
5
t
8
)
t
7
(p
5
, t
1
t
2
t
4
t
5
t
7
)
t
10
(o,t
1
t
2
t
4
t
5
t
7
t
10
)
(o, t
1
t
2
t
4
t
5
t
7
t
10
)
t
9
(o,t
1
t
2
t
4
t
5
t
8
t
9
)
1
2
3
5
4
7
8
12
13
11
16
17
18
t
9
t
10
t
10
t
1
t
2
t
4
t
5
t
6
t
3
(p
4
, t
1
t
2
t
3
t
2
t
4
t
3
)
(p
5
,t
1
t
2
t
3
t
2
t
4
t
6
)
(o, t
1
t
2
t
3
t
2
t
4
t
6
t
10
)
t
8
(p
5
, t
1
t
2
t
3
t
2
t
4
t
3
t
8
)
t
7
(p
5
,
t
1
t
2
t
3
t
2
t
4
t
3
t
7
)
t
10
(o,t
1
t
2
t
3
t
2
t
4
t
3
t
7
t
10
)
(o, t
1
t
2
t
3
t
2
t
4
t
3
t
7
t
10
)
t
9
(o,t
1
t
2
t
3
t
2
t
4
t
3
t
8
t
9
)
14
15
20
21
19
22
23
24
t
9
t
10
t
10
t
6
(p
2
, t
1
t
2
t
3
t
2
)
6
t
2
10
t
4
(p
1
, t
1
t
2
t
3
t
2
t
3
)
9
t
3
(p
3
, t
1
t
2
t
3
t
2
t
4
)
t
5
t
9
t
9
(p
1
,{(t
3
, c
1
)})
(p
1
,{(t
3
, c
1
)})
Figure 2: The coverability graph of the WTC-net in Figure 1.
(i, ε)
(p
1
, t
1
)
(p
2
, t
1
t
2
)
(p
1
, t
1
t
2
t
3
)
(p
3
, t
1
t
2
t
4
)
(p
4
, t
1
t
2
t
4
t
5
)
t
8
(p
5
, t
1
t
2
t
4
t
5
t
8
)
1
2
3
5
4
8
13
t
10
t
1
t
2
t
4
t
5
t
3
(p
4
, t
1
t
2
t
3
t
2
t
4
t
3
)
t
8
(p
5
, t
1
t
2
t
3
t
2
t
4
t
3
t
8
)
15
21
t
10
(p
2
, t
1
t
2
t
3
t
2
)
6
t
2
10
t
4
(p
1
, t
1
t
2
t
3
t
2
t
3
)
9
t
3
(p
3
, t
1
t
2
t
3
t
2
t
4
)
t
5
(p
1
,{(t
3
, c
1
)})
Infeasible trace set:
t
1
t
2
(t
3
t
2
)*t
4
t
5
t
8
t
10
Shortest infeasible trace
t
5
t
8
t
10
[c
1
]
[c
2
]
t
2
t
3
i
w: d
2
,d
3
p
1
p
2
t
4
t
1
w: d
1
w: d
3
t
5
p
3
[c
3
]
[c
6
]
p
4
P
5
t
8
[c
4
]
o
t
10
Projecting of Shortest infeasible trace in process model
(p
1
,{(t
3
, c
1
)})
(a) Sample 1 for shortest infeasible traces
(i, ε)
(p
1
, t
1
)
(p
1
, t
1
t
2
t
3
)
(p
3
, t
1
t
2
t
4
)
(p
5
, t
1
t
2
t
4
t
6
)
1
2
3
5
4
7
t
9
t
1
t
2
t
4
t
6
t
3
(p
5
,t
1
t
2
t
3
t
2
t
4
t
6
)
14
t
9
t
6
(p
2
, t
1
t
2
t
3
t
2
)
6
t
2
10
t
4
(p
1
, t
1
t
2
t
3
t
2
t
3
)
9
t
3
(p
3
, t
1
t
2
t
3
t
2
t
4
)
(p
2
, t
1
t
2
)
[c
1
]
[c
2
]
t
2
t
3
i
w: d
2
,d
3
p
1
p
2
t
4
t
1
w: d
1
[c
4
]
p
3
t
6
P
5
t
9
[c
3
]
o
Infeasible trace set:
t
1
t
2
(t
3
t
2
)*t
4
t
6
t
9
Shortest infeasible trace
t
6
t
9
Projecting of Shortest infeasible trace in process model
(p
1
,{(t
3
, c
1
)})
(p
1
,{(t
3
, c
1
)})
(b) Sample 2 for shortest infeasible traces
Figure 3: Backwards detecting shortest infeasible trace.
Figure 4: The screenshot of the detecting result of the shortest infeasible traces.
Table 2 shows that there are 8 (27.6%) process
models among the 29 transformed WTC-net models.
We compared the detection results with other mea-
sures including manual analysis. It turned out that
our approach was always able to correctly detect the
correlation relationship of the process definitions. All
ICEIS2012-14thInternationalConferenceonEnterpriseInformationSystems
216

Table 2: The detecting result of infeasible traces for real process models
*
.
PM DR-1 DR-2 DR-3 DR-4 DR-5 DR-6 DR-7 DR-8 DR-9 DR-10
SIT
#
0 2 26 0 0 0 1 0 0 0
PM DR-11 PC-1 RM-1 RM-2 RM-3 RM-4 RM-5 RM-6 RM-7 RM-8
SIT
#
11 0 0 2 1 0 0 0 0 0
PM RM-9 RM-10 RM-11 RM-12 RM-13 AM-1 AM-2 AM-3 AM-4
SIT
#
0 0 0 1 0 0 1 0 0
∗
PM describes process model, SIT
#
denotes the number of the set of infeasible traces possessing the same shortest infeasible traces
examples for experiments can be downloaded from
http://laudms.thss.tsinghua.edu.cn/trac/Test/wiki/che-
ngguo/Test%20Data.zip.
4 RELATED WORK
In recent years, there are well-developed formalisms
for workflow modeling taking data perspective into
account based on WF-nets proposed in (van der Aalst,
1998).
In (Fan et al., 2007), a model called Dual Work-
flow Nets (DWF-nets) was proposed, which can ex-
plicitly model both the control flow and the data flow
as well as their interactions. WFD-nets was proposed
in (Trˇcka et al., 2009) to extend WF-nets with data el-
ements for soundness verification. However, both of
DWF-nets and WFD-nets don’tconsider the effects of
concrete guard functions as well as their propagation
explicitly.
For us, WTC-net is proposed for studying work-
flow nets where routing may be determined by transi-
tion conditions. Further, the shortest infeasible trace
is detected based on the correlation between transi-
tions while the works in (Fan et al., 2007) and (Trˇcka
et al., 2009) focusing on the correctness of the auto
execution of workflow models.
5 CONCLUSIONS
In this paper, we have defined workflow net with tran-
sition conditions WTC-net and its behavior semantics
with the influence of transition condition in detail. In
addition, we have presented an approach to detect in-
feasible trace and a tool has been implemented based
on the approach.
In the future work, we will consider how to verify
process model considering with transition condition
in quantity.
ACKNOWLEDGEMENTS
This paper is supported by the 863 High-Tech De-
velopment Program of China (No. 2009AA043401),
the National Science Foundation of China (No.
61003099, 61073005) and the National Sci-
ence and Technology Major Project, China (No.
2010ZX01042-002-002-01).
REFERENCES
Fan, S., Dou, W., and Chen, J. (2007). Dual work-
flow nets: Mixed control/data-flow representation for
workflow modeling and verification. In Chang, K. C.-
C., Wang, W., 0002, L. C., Ellis, C. A., Hsu, C.-H.,
Tsoi, A. C., and Wang, H., editors, Advances in Web
and Network Technologies, and Information Manage-
ment, APWeb/WAIM 2007 International Workshops:
DBMAN 2007, WebETrends 2007, PAIS 2007 and
ASWAN 2007, Huang Shan, China, June 16-18, 2007,
Proceedings, volume 4537 of Lecture Notes in Com-
puter Science, pages 433–444. Springer.
Finkel, A. (1991). The minimal coverability graph for petri
nets. In Rozenberg, G., editor, Applications and The-
ory of Petri Nets, volume 674 of Lecture Notes in
Computer Science, pages 210–243. Springer.
Murata, T. (1989). Petri nets: Properties, analysis and ap-
plications. Proceedings of the IEEE, 77(4):541–580.
Ngo, M. N. and Tan, H. B. K. (2008). Heuristics-based
infeasible path detection for dynamic test data gener-
ation. Inf. Softw. Technol., 50(7-8):641–655.
Trˇcka, N., van der Aalst, W., and Sidorova, N. (2009). Data-
flow anti-patterns: Discovering data-flow errors in
workflows. In van Eck, P., Gordijn, J., and Wieringa,
R., editors, Advanced Information Systems Engineer-
ing, 21st International Conference, CAiSE 2009, Am-
sterdam, The Netherlands, June 8-12, 2009. Proceed-
ings, volume 5565 of Lecture Notes in Computer Sci-
ence, pages 425–439. Springer-Verlag.
van der Aalst, W. (1998). The application of Petri nets to
workflow management. Journal of Circuits, Systems,
and Computers, 8(1):21–66.
van der Aalst, W. and ter Hofstede, A. H. M. (2000). Veri-
fication of workflow task structures: A Petri-net-baset
approach. Inf. Syst., 25(1):43–69.
van der Aalst, W., van Dongen, B., G¨unther, C., Rozinat, A.,
Verbeek, H., and Weijters, A. (2009). ProM: The pro-
cess mining toolkit. In de Medeiros, A. and Weber, B.,
editors, Proceedings of the Business Process Manage-
ment Demonstration Track (BPMDemos 2009), Ulm,
Germany, September 8, 2009, volume 489 of CEUR
Workshop Proceedings. CEUR-WS.org.
DetectingInfeasibleTracesinProcessModels
217
