
Constructing Secure-channel Free Searchable Encryption
from Anonymous IBE with Partitioned Ciphertext Structure
Keita Emura
1
and Mohammad Shahriar Rahman
2
1
Network Security Research Institute, Security Architecture Laboratory,
National Institute of Information and Communications Technology (NICT), Tokyo, Japan
2
Department of Computer Science and Engineering, University of Asia Pacific, Dhaka, Bangladesh
Keywords:
Adaptive Secure-channel Free Public Key Encryption Scheme with Keyword Search, IBE with Partitioned
Ciphertext Structure.
Abstract:
As an extension of public key encryption with keyword search (PEKS), secure channel free PEKS (SCF-
PEKS) has been considered. Generic construction of SCF-PEKS (with adaptive security) from strongly ex-
istentially unforgeable one-time signature, selective-tag CCA secure tag-based encryption (TBE) and anony-
mous identity-based encryption (IBE) has been proposed in ISC2011. Since this construction follows the
double encryption, where a ciphertext of anonymous IBE is encrypted by TBE, hybrid encryption is applied
because usually the ciphertext space of IBE is not equal to the plaintext space of TBE. In this paper, we
show that hybrid encryption is not necessary as long as previously-known anonymous IBE schemes are used
as a building tool of adaptive SCF-PEKS. Our result leads to a composability of IBE schemes whether they
can be applied for constructing adaptive SCF-PEKS or not. Moreover, since we can exclude DEM part, our
construction is efficient compared to the original one.
1 INTRODUCTION
1.1 Research Background
Any encryption scheme is required to be secure in
the following sense: no information of plaintext is
revealed from the corresponding ciphertext. There-
fore, it seems hard to achieve to realize a searchable
functionality against encrypted data. Due to such re-
quirement, Public key Encryption scheme with Key-
word Search (PEKS) has been proposed (Boneh et al.,
2004b). In PEKS, a receiver makes a trapdoor t
ω
for
a keyword ω, and uploads it on a server. A sender
makes a ciphertext of a keyword ω
′
by using the re-
ceiver’s public key, and sends it to the server. The
server outputs 1 if ω = ω
′
, by using t
ω
, and 0 other-
wise. Moreover, Secure-Channel Free PEKS (SCF-
PEKS) have been proposed (Baek et al., 2008; Fang
et al., 2009; Gu and Zhu, 2010; Gu et al., 2007;
Khader, 2007) as an extension of PEKS. In SCF-
PEKS, the server has a public/secret key pair, and the
sender makes a ciphertext of a keyword ω
′
(which is
encrypted by using both the server’s public key and
the receiver’s public key), and sends it to the server.
The server outputs 1 if ω = ω
′
by using the trapdoor
t
ω
and its own secret key, and 0 otherwise. Even if t
ω
is sent via an insecure channel, no entity (except the
server) can run the test procedure. Note that a ma-
licious receiver can use the server as the test oracle
according to the following way (see Fig.1).
1. A malicious receiver computes (or eavesdrops on)
a trapdoor, and uploads it to the server.
• From the viewpoint of the server, this is the
same as uploading a trapdoor from a valid re-
ceiver.
2. The malicious receiver computes (or eavesdrops
on) a SCF-PEKS ciphertext, and sends it to the
server.
• This is the same as sending a ciphertext from a
valid sender.
3. The malicious receiver can obtain the result of the
test algorithm.
To capture such circumstance, Emura et
al. (Emura et al., 2011) consider a strong security
notion of SCF-PEKS, called adaptive SCF-PEKS,
where a “malicious-but-legitimate” receiver can
be admitted to issue test queries adaptively, and
show that adaptive SCF-PEKS implies timed-release
encryption (Matsuda et al., 2010). Moreover,
84
Emura K. and Shahriar Rahman M..
Constructing Secure-channel Free Searchable Encryption from Anonymous IBE with Partitioned Ciphertext Structure.
DOI: 10.5220/0004022700840093
In Proceedings of the International Conference on Security and Cryptography (SECRYPT-2012), pages 84-93
ISBN: 978-989-8565-24-2
Copyright
c
2012 SCITEPRESS (Science and Technology Publications, Lda.)

Server (=Test Oracle)
Malicious Receiver
1. Uploading a trapdoor
2. Sending a SCF-PEKS ciphertext
3. Getting the corresponding
test result
Figure 1: Instantiation of test queries in the real world.
they also gave a generic construction of adaptive
SCF-PEKS based on anonymous IBE, selective-tag
chosen-ciphertext (IND-stag-CCA) secure tag-based
encryption (TBE), and strongly existentially un-
forgeable (sUF) one-time signature (OTS). Briefly,
this construction follows the double encryption,
where a ciphertext of anonymous IBE is encrypted
by TBE. Since usually the ciphertext space of IBE
is not equal to the plaintext space of TBE, they
applied the KEM/DEM framework (Shoup, 2000)
(a.k.a. hybrid encryption), where KEM stands for
key encapsulation mechanism, and DEM stands for
data encapsulation mechanism.
1.2 Our Contribution
In this paper, we investigate the usage of hy-
brid encryption in the original construction, and
show that hybrid encryption is not necessary as
long as previously-known anonymous IBE schemes
(e.g., (Boneh and Franklin, 2003; Boyen and Wa-
ters, 2006; Camenisch et al., 2009; Caro et al., 2010;
Ducas, 2010; Gentry, 2006; Seo et al., 2009)) are used
as its building tools. Our result leads to a compos-
ability of IBE schemes whether they can be applied
for constructing adaptive SCF-PEKS or not. We de-
fine IBE with Partitioned Ciphertext Structure (PCS-
IBE), where for any common message M and distinct
identities ID and ID
′
(ID 6= ID
′
), a part of ciphertext
can be “commonly” used for both ciphertexts if the
“same random number” is used for both encryptions.
Technically, this ciphertext shareability is the most
significant point of the security proof, and such novel
simulation technique has not been pointed out so far.
Moreover, since we can exclude the DEM part of pre-
vious adaptive SCF-PEKS construction, our construc-
tion is efficient compared to the original one. Espe-
cially, we can reduce the ciphertext size. Note that
the size of DEM part is at least the same size of
IBE ciphertext, and the ciphertext size is bottleneck
point of adaptive SCF-PEKS constructions compared
to the concrete constructions. Finally, we instantiate
an adaptive SCF-PEKS scheme which achieves the
similar level efficiency for the costs of the test pro-
cedure and encryption compared to the (non-adaptive
secure) SCF-PEKS scheme without random oracles
proposed by Fang et al (See Table 1). Since we do not
care about the keyword guessing attacks (Byun et al.,
2006; Jeong et al., 2009; Rhee et al., 2009b; Yauet al.,
2008), it can be an interesting future work.
2 PRELIMINARIES
In this section, we give the definitions of the building
tools and adaptive SCF-PEKS.
2.1 Definitions of IND-stag-CCA Secure
TBE
In the following, T AG and M
TBE
are a tag space of
TBE and a plaintext space of TBE, respectively.
Definition 1 (Syntax of TBE). A TBE scheme (Kiltz,
2006) Π consists of the following three algorithms,
TBE.KeyGen, TBE.Enc and TBE.Dec:
TBE.KeyGen(1
κ
) : This algorithm takes as an input
the security parameter κ ∈ N, and returns a public
key pk and a secret key sk.
TBE.Enc(pk,t,M) : This algorithm takes as inputs
pk, a message M ∈ M
TBE
with a tag t ∈ T AG,
and returns a ciphertext C
TBE
.
TBE.Dec(sk,t,C
TBE
) : This algorithms takes as in-
puts sk, t, and C
TBE
, and returns M or ⊥.
Correctness is defined as follows: For all
(pk,sk) ← TBE.KeyGen(1
κ
), all M ∈ M
TBE
, and all
t ∈ T AG, TBE.Dec(sk,t,C
TBE
) = M holds, where
C
TBE
← TBE.Enc(pk,t,M).
Next, we define the security requirement of TBE
under selective-tag CCA (IND-stag-CCA) as follows.
Definition 2 (IND-stag-CCA). For any PPT adver-
sary A and the security parameter κ ∈ N, we define
the experiment Exp
IND-stag-CCA
Π,A
(1
κ
) in Figure 2, and
ConstructingSecure-channelFreeSearchableEncryptionfromAnonymousIBEwithPartitionedCiphertextStructure
85
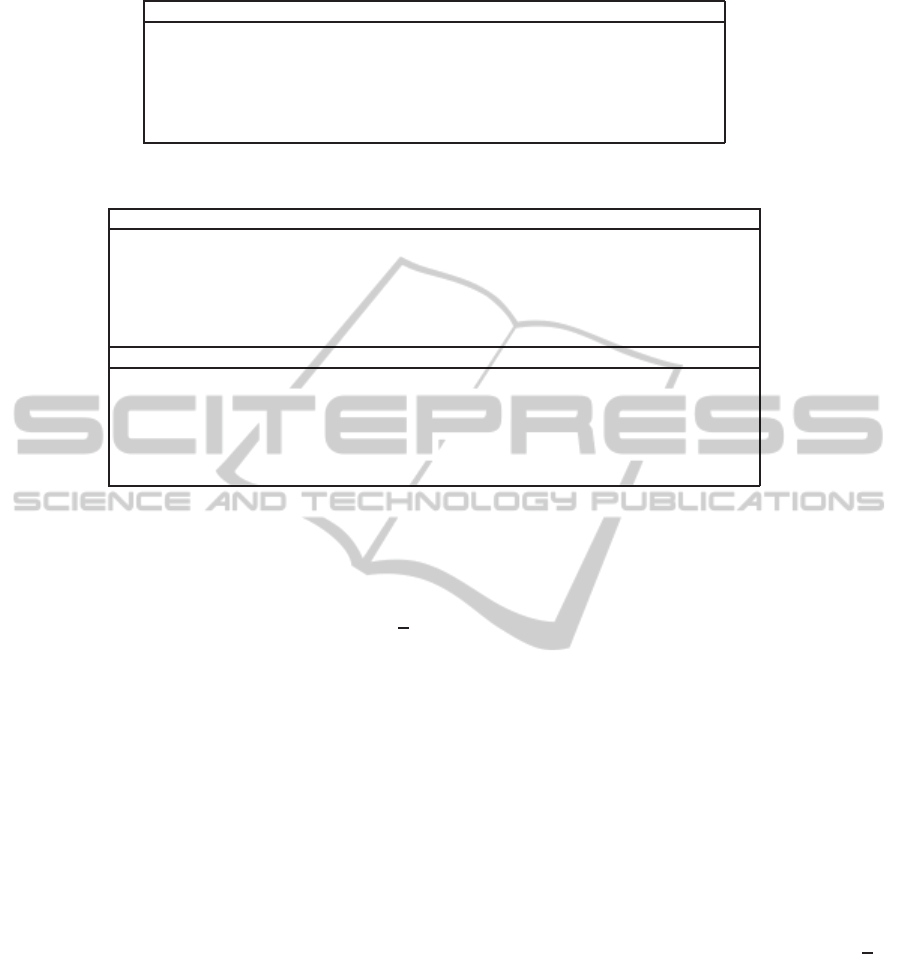
IND-stag-CCA
Exp
IND-stag-CCA
Π,A
(1
κ
) :=
(t
∗
,State) ← A(1
κ
); (pk, sk) ← TBE.KeyGen(1
κ
);
(M
∗
0
,M
∗
1
,State) ← A
DE C
(find, pk,State); µ
$
← {0,1};
C
∗
TBE
← TBE.Enc(pk,t
∗
,M
∗
µ
); µ
′
← A
DE C
(guess,C
∗
,State);µ = µ
′
]
Figure 2: TBE experiment.
IBE-IND-CPA
Exp
IBE-IND-CPA
Π,A
(1
κ
) :=
(pk, mk) ← IBE.Setu p(1
κ
);
(M
∗
0
,M
∗
1
,ID
∗
,State) ← A
EX T R AC T
(find, pk); µ
$
← {0,1};
C
∗
IBE
← IBE.Enc(pk, ID
∗
,M
∗
µ
); µ
′
← A
EX T R AC T
(guess,C
∗
IBE
,State) µ = µ
′
IBE-ANO-CPA
Exp
IBE-ANO-CPA
Π,A
(1
κ
) :=
(pk, mk) ← IBE.Setu p(1
κ
);
(ID
∗
0
,ID
∗
1
,M
∗
,State) ← A
EX T R ACT
(find, pk); µ
$
← {0,1};
C
∗
IBE
← IBE.Enc(pk, ID
∗
µ
,M
∗
); µ
′
← A
EX T R AC T
(guess,C
∗
IBE
,State); µ = µ
′
Figure 3: IBE experiments.
define the advantage of A Adv
IND-stag-CCA
Π,A
(1
κ
) as fol-
lows.
Adv
IND-stag-CCA
Π,A
(1
κ
) :=
Pr
Exp
IND-stag-CCA
Π,A
(1
κ
)
−
1
2
Here, DEC is the decryption oracle for any tag
t 6= t
∗
, where for input of a ciphertext (C
TBE
,t) 6=
(C
∗
TBE
,t
∗
),
it returns the corresponding plaintext M. Note that
(C
∗
TBE
,t
∗
) is not allowed as input to DEC.
A TBE scheme Π is said to be IND-stag-CCA se-
cure if the advantage Adv
IND-stag-CCA
Π,A
(1
κ
) is negligi-
ble.
2.2 Definitions of Anonymous IBE
In the following, I D and M
IBE
are an identity space
and a plaintext space of IBE, respectively.
Definition 3 (Syntax of IBE). IBE scheme Π con-
sists of the following four algorithms, IBE.Setup,
IBE.Extract, IBE.Enc and IBE.Dec:
IBE.Setup(1
κ
) : This algorithm takes as an input the
security parameter κ ∈ N, and returns a public
key pk and a master key mk.
IBE.Extract(pk,mk,ID) : This algorithm takes as in-
puts an identity ID ∈ I D, and mk, and returns a
secret key corresponding to ID sk
ID
.
IBE.Enc(pk, ID, M) : This algorithm takes as inputs
pk, ID ∈ I D, and a message M ∈ M
IBE
, and re-
turns a a ciphertext C
IBE
.
IBE.Dec(sk
ID
,C
IBE
) : This algorithm takes as inputs
sk
ID
and C
IBE
, and returns M or ⊥.
Correctness is defined as follows: For all
(pk,mk) ← IBE.Setup(1
κ
), all M ∈ M
IBE
, and
all ID ∈ I D, IBE.Dec(sk
ID
,C
IBE
) = M holds,
where C
IBE
← IBE.Enc(pk,ID,M) and sk
ID
←
IBE.Extract(pk,mk,ID).
Next, we define the security requirement of IBE
under chosen plaintext attack (IBE-IND-CPA) as fol-
lows.
Definition 4 (IBE-IND-CPA). For any PPT adver-
sary A and the security parameter κ ∈ N, we define
the experiment Exp
IBE-IND-CPA
Π,A
(1
κ
) in Figure 3, and
define the advantage of A Adv
IBE-IND-CPA
Π,A
(1
κ
) as fol-
lows.
Adv
IBE-IND-CPA
Π,A
(1
κ
) :=
Pr
Exp
IBE-IND-CPA
Π,A
(1
κ
)
−
1
2
Here, EX T R AC T is the extraction oracle for in-
put of an identity ID it returns the corresponding se-
cret key sk
ID
. Note that ID
∗
is not allowed as input to
EX T R AC T in the IBE-IND-CPA experiment.
An IBE scheme Π is said to be IBE-IND-CPA se-
cure if the advantage Adv
IBE-IND-CPA
Π,A
(1
κ
) is negligible.
Next, we define anonymity experiment of IBE under
CPA (IBE-ANO-CPA).
Definition 5 (IBE-ANO-CPA). For any PPT adver-
sary A and the security parameter κ ∈ N, we define
the experiment Exp
IBE-ANO-CPA
Π,A
(1
κ
) in Table 3, and
SECRYPT2012-InternationalConferenceonSecurityandCryptography
86

one-time sUF-CMA
Exp
one-time sUF-CMA
Π,A
(1
κ
) :=
(K
s
,K
v
) ← Sig.KeyGen (1
κ
); (M, State) ← A(K
v
);
σ ← Sign(K
s
,M);(M
∗
,σ
∗
) ← A(State,σ); (M
∗
,σ
∗
) 6= (M,σ);Verify(K
v
,σ
∗
,M
∗
) = 1]
Figure 4: OTS experiment.
define the advantage of A Adv
IBE-ANO-CPA
Π,A
(1
κ
) as fol-
lows.
Adv
IBE-ANO-CPA
Π,A
(1
κ
) :=
Pr
Exp
IBE-ANO-CPA
Π,A
(1
κ
)
−
1
2
ID
∗
0
and ID
∗
1
are not allowed as input to
EX T R AC T in the IBE-ANO-CPA experiment. An
IBE scheme Π is said to be IBE-ANO-CPA secure if
the advantage Adv
IBE-ANO-CPA
Π,A
(1
κ
) is negligible.
Definition 6 (Anonymous IBE). An IBE scheme is
said to be anonymous IBE if the IBE scheme is both
IBE-IND-CPA secure and IBE-ANO-CPA secure.
2.3 Definitions of sUF OTS
In the following, M
Sig
is a message space of OTS.
Definition 7 (Syntax of OTS). A strongly existen-
tially unforgeable (sUF) OTS against adaptively cho-
sen message attack (CMA) (e.g., (Bellare and Shoup,
2007)) consists of the following three algorithms,
Sig.KeyGen, Sign and Verify:
Sig.KeyGen(1
κ
) : This algorithm takes as an input
a security parameter 1
κ
(κ ∈ N), and returns a
signing/verification key pair (K
s
,K
v
).
Sign(K
s
,M) : This algorithm takes as inputs K
s
and
a message M ∈ M
Sig
, and returns a signature σ.
Verify(K
v
,σ,M) : This algorithm takes as inputs K
v
,
σ, and M, and returns 1 if σ is a valid signature
of M, and 0 otherwise.
Correctness is defined as follows: For all
(K
s
,K
v
) ← Sig.KeyGen(1
κ
) and all M ∈ M
Sig
,
Verify(K
v
,σ,M) = 1 holds, where σ ← Sign(K
s
,M).
Definition 8 (one-time sUF-CMA). For any PPT
adversary A and the security parameter κ ∈ N,
we define the experiment Exp
one-time sUF-CMA
Π,A
(1
κ
)
in Figure 4, and define the advantage of A
Adv
one-time sUF-CMA
Π,A
(1
κ
) as follows.
Adv
one-time sUF-CMA
Π,A
(1
κ
) := Pr
Exp
one-time sUF-CMA
Π,A
(1
κ
)
A signature scheme Π is said to be one-time sUF-
CMA secure if the advantage Adv
one-time sUF-CMA
Π,A
(1
κ
)
is negligible.
2.4 Definitions of Adaptive SCF-PEKS
Here, we introduce security requirements of SCF-
PEKS defined in (Emura et al., 2011). In the follow-
ing, K is a keyword space.
Definition 9 (Syntax of SCF-PEKS.). An SCF-PEKS
scheme Π consists of the following five algo-
rithms, SCF-PEKS.KeyGen
S
, SCF-PEKS.KeyGen
R
,
SCF-PEKS.Trapdoor, SCF-PEKS.Enc and
SCF-PEKS.Test:
SCF-PEKS.KeyGen
S
(1
κ
) : This server key genera-
tion algorithm takes as input the security param-
eter 1
κ
(κ ∈ N), and returns a server public key
pk
S
and a server secret key sk
S
.
SCF-PEKS.KeyGen
R
(1
κ
) : This receiver key gener-
ation algorithm takes as input the security param-
eter 1
κ
(κ ∈ N), and returns a receiver public key
pk
R
and a receiver secret key sk
R
.
SCF-PEKS.Trapdoor(sk
R
,ω) : This trapdoor gener-
ation algorithm takes as input sk
R
and a keyword
ω ∈ K , and returns a trapdoor t
ω
corresponding
to keyword ω.
SCF-PEKS.Enc(pk
S
, pk
R
,ω) : This encryption algo-
rithm takes as input pk
R
, pk
S
, and ω, and returns
a ciphertext λ.
SCF-PEKS.Test(λ,sk
S
,t
ω
) This text algorithm takes
as input λ, sk
S
, and t
ω
, and returns 1 if ω = ω
′
,
where ω
′
is the keyword which was used for com-
puting λ, and 0 otherwise.
Correctness is defined as follows: For all
(pk
S
,sk
S
) ← SCF-PEKS.KeyGen
S
(1
κ
), all
(pk
R
,sk
R
) ← SCF-PEKS.KeyGen
R
(1
κ
), and all
ω ∈ K , SCF-PEKS.Test(λ,sk
S
,t
ω
) = 1 holds,
where λ ← SCF-PEKS.Enc(pk
R
, pk
S
,ω) and
t
ω
← SCF-PEKS.Trapdoor(sk
R
,ω).
Next, we state two security requirements “consis-
tency” and “keyword privacy”.
Definition 10 (Consistency). For any PPT adversary
A and the security parameter κ ∈ N, we define the
experiment Exp
SCF-PEKS-CONSIST
Π,A
(1
κ
) in Figure 5, and
define the advantage of A Adv
SCF-PEKS-CONSIST
Π,A
(1
κ
) as
follows.
Adv
Π,A
SCF-PEKS-CONSIST
(1
κ
) :=
Pr
Exp
SCF-PEKS-CONSIST
Π,A
(1
κ
)
ConstructingSecure-channelFreeSearchableEncryptionfromAnonymousIBEwithPartitionedCiphertextStructure
87

Consistency
Exp
SCF-PEKS-CONSIST
Π,A
(1
κ
) :=
(pk
S
,sk
S
) ← SCF-PEKS.KeyGen
S
(1
κ
); (pk
R
,sk
R
) ← SCF-PEKS.KeyGen
R
(1
κ
);
(ω,ω
′
) ← A(pk
S
, pk
R
);ω 6= ω
′
; λ ← SCF-PEKS.Enc(pk
S
, pk
R
,ω); t
ω
′
← SCF-PEKS.Trapdoor(sk
R
,ω
′
);
SCF-PEKS.Test
λ,sk
S
,t
ω
′
= 1
IND-CKA-SSK
Exp
IND-CKA-SSK
Π,A
(1
κ
) :=
(pk
S
,State) ← A(1
κ
); (pk
R
,sk
R
) ← SCF-PEKS.KeyGen
R
(1
κ
);
(ω
∗
0
,ω
∗
1
,State) ← A
T R AP
(find, pk
R
,State); µ
$
← {0,1};
λ
∗
← SCF-PEKS.Enc(pk
S
, pk
R
,ω
∗
µ
);µ
′
← A
T R AP
(guess,λ
∗
,State); µ = µ
′
Adaptive-IND-CKA-AT
Exp
Adaptive-IND-CKA-AT
Π,A
(1
κ
) :=
(pk
S
,sk
S
) ← SCF-PEKS.KeyGen
S
(1
κ
); (pk
R
,State) ← A(1
κ
);
(ω
∗
0
,ω
∗
1
,State) ← A
T E ST
(find, pk
S
,State); µ
$
← {0,1};
λ
∗
← SCF-PEKS.Enc(pk
S
, pk
R
,ω
∗
µ
);µ
′
← A
T E ST
(guess,λ
∗
,State); µ = µ
′
Figure 5: SCF-PEKS experiments.
The SCF-PEKS scheme Π is said to be
computationally consistent if the advantage
Adv
SCF-PEKS-CONSIST
Π,A
(1
κ
) is negligible.
Next, we state two security notions for keyword
privacy, “indistinguishability against chosen keyword
attack with the server’s secret key” (IND-CKA-SSK
for short) and “indistinguishability against chosen
keyword attack with all trapdoors” (IND-CKA-AT for
short). In the IND-CKA-SSK experiment, an adver-
sary A is assumed to be a malicious server. Note
that A computes (pk
S
,sk
S
), and gives pk
S
to the chal-
lenger. So, we omit sk
S
in the IND-CKA-SSK exper-
iment.
Definition 11 (IND-CKA-SSK). For any PPT adver-
sary A and the security parameter κ ∈ N, we define
the experiment Exp
IND-CKA-SSK
Π,A
(1
κ
) in Figure 5, and
define the advantage of A Adv
IND-CKA-SSK
Π,A
(1
κ
) as fol-
lows.
Adv
IND-CKA-SSK
Π,A
(1
κ
) :=
Pr
ExpΠ,A
IND-CKA-SSK
(1
κ
)
−
1
2
Here, T R AP is the trapdoor oracle for an in-
put keyword ω, it returns a trapdoor t
ω
. Note that
A cannot query the challenge keywords ω
∗
0
and ω
∗
1
to
T R AP .
An SCF-PEKS scheme Π is said to be IND-CKA-
SSK-secure if the advantage Adv
IND-CKA-SSK
Π,A
(1
κ
) is
negligible.
Next, we define the adaptive-IND-CKA-AT experi-
ment. In this experiment, an adversary A is assumed
to be a malicious-but-legitimate receiver or outsider.
Note that A computes (pk
R
,sk
R
), and gives pk
R
to
the challenger. So, we omit sk
R
in the Adaptive-IND-
CKA-AT experiment.
Definition 12 (Adaptive-IND-CKA-AT). For any
PPT adversary A and the security parameter κ ∈ N,
we define the experiment Exp
Adaptive-IND-CKA-AT
Π,A
(1
κ
)
in Figure 5, and define the advantage of A
Adv
Adaptive-IND-CKA-AT
Π,A
(1
κ
) as follows.
Adv
Adaptive-IND-CKA-AT
Π,A
(1
κ
) =
Pr
Exp
Adaptive-IND-CKA-AT
Π,A
(1
κ
)
−
1
2
Here, T EST is the test oracle for an input (λ,t
ω
)
which satisfies (λ,t
ω
) 6∈ {(λ
∗
,t
ω
∗
0
),(λ
∗
,t
ω
∗
1
)}, it re-
turns the result of the test algorithm.
An SCF-PEKS scheme is said to be
adaptive-IND-CKA-AT-secure if the advantage
A Adv
Adaptive-IND-CKA-AT
Π,A
(1
κ
) is negligible.
3 PREVIOUS ADAPTIVE
SCF-PEKS CONSTRUCTION
In this section, we introduce the original generic con-
struction of adaptive SCF-PEKS based on anonymous
IBE, IND-stag-CCA TBE, and sUF OTS. In this con-
struction, a ciphertext of an anonymous IBE scheme
(sayC
IBE
) is used as a “plaintext” of a TBE scheme to
hide keyword information from an adversary. From
the result of the decryption of the TBE scheme, the
SECRYPT2012-InternationalConferenceonSecurityandCryptography
88

ciphertext C
IBE
must be obtained. In addition, usu-
ally, C
IBE
6∈ M
TBE
. By using TBE KEM (e.g., Sec-
tion 6 of (Kiltz, 2006)), compute (K
TBE
,C
TBE
) ←
TBE.Enc(pk,t), and encrypt C
IBE
as a plaintext of
the CCA secure DEM such that C
DEM
= E
K
(C
IBE
).
Therefore, they assumed C
IBE
∈ M
TBE
, and C
DEM
=
E
K
(C
IBE
) is implicitly included in C
TBE
(i.e., C
IBE
is
obtained from the decryption of C
TBE
). However, for
the sake of clarity, we explicitly include C
DEM
into
the ciphertext.
Let H
tag
: {0,1}
∗
→ T AG be a target collision re-
sistant (TCR) hash function (Bellare and Rogaway,
1997). We set M
Sig
= C
TBE
× M
IBE
, where C
TBE
is
a ciphertext space of the underlying TBE.
Protocol 1 (Previous Adaptive SCF-PEKS Construc-
tion (Emura et al., 2011)).
SCF-PEKS.KeyGen
S
(1
κ
): Run (pk
S
,sk
S
) ←
TBE.KeyGen(1
κ
), and output (pk
S
,sk
S
).
SCF-PEKS.KeyGen
R
(1
κ
): Run (pk
R
,sk
R
) ←
IBE.KeyGen(1
κ
), and output (pk
R
,sk
R
).
SCF-PEKS.Trapdoor(sk
R
,ω): Run t
ω
←
IBE.Extract(sk
R
,ω), and output t
ω
.
SCF-PEKS.Enc(pk
S
, pk
R
,ω): Generate (K
s
,K
v
)
$
←
Sig.KeyGen, compute t = H
tag
(K
v
), choose
R
$
← M
IBE
, run C
IBE
← IBE.Enc(pk
R
,ω,R),
(K
TBE
,C
TBE
) ← TBE.Enc(pk
S
,t,C
IBE
),
C
DEM
= E
K
TBE
(C
IBE
), and σ ← Sign(K
s
,
(C
TBE
,C
DEM
,R)), and output λ = (C
TBE
,C
DEM
,
K
v
,σ).
SCF-PEKS.Test(λ,sk
S
,t
ω
): Let λ =
(C
TBE
,C
DEM
,K
v
,σ). Compute t = H
tag
(K
v
),
run K
TBE
← TBE.Dec(sk
S
,t,C
TBE
), C
′
IBE
←
D
K
TBE
(C
DEM
), and R
′
← IBE.Dec(t
ω
,C
′
IBE
).
Output 1 if 1=Verify(K
v
,σ,(C
TBE
,R
′
)), and 0
otherwise.
4 IBE WITH PARTITIONED
CIPHERTEXT STRUCTURE
(PCS-IBE)
The role of the KEM/DEM framework in the origi-
nal adaptive SCF-PEKS construction is that an IBE
ciphertext is regarded as a TBE plaintext to hide key-
word information from an adversary who has mk in
the Adaptive-IND-CKA-AT experiment. In this sec-
tion, we define a class of IBE, called IBE with parti-
tioned ciphertext structure (PCS-IBE) to avoid hybrid
encryption
1
.
Definition 13 (PCS-IBE). IBE is said to be PCS-
IBE if its ciphertext C
IBE
can be split into two parts
C
IBE
:= (C
IBE,1
,C
IBE,2
) with the following properties.
• C
IBE,1
∈ M
TBE
.
– Kiltz (Kiltz, 2006) proposed a TBE scheme
with M
TBE
= G and M
TBE
= G
T
, respectively,
where (G,G
T
) is a bilinear group. So, it is
enough to require that C
IBE,1
is a single group
element.
• C
IBE,1
only includes an identity ID (i.e., C
IBE,2
is
independent of ID).
• For any common message M and dis-
tinct identities ID and ID
′
(ID 6= ID
′
),
C
IBE,2
can be commonly used for
(C
IBE,1
,C
IBE,2
) ← IBE.Enc(pk,ID,M;s) and
(C
′
IBE,1
,C
IBE,2
) ← IBE.Enc(pk,ID
′
,M;s) if
the same random number s is used for both
encryptions.
– That is, both (C
IBE,1
,C
IBE,2
) and
(C
′
IBE,1
,C
IBE,2
) are valid ciphertexts.
This structure is used for computing the chal-
lenge ciphertext in the proof of the adaptive IND-
CKA-AT. In the proof, no matter which plaintext
(C
0,IBE,1
,C
1,IBE,1
) is encrypted, both C
0,IBE,2
and
C
1,IBE,2
can be used as a part of the challenge cipher-
text, since C
0,IBE,2
= C
1,IBE,2
due to the PCS property.
Here, we explain the above structure in the Gentry
IBE (Gentry, 2006) case as follows: for a message
M and an identity ID, a ciphertext (C
IBE,1
,C
IBE,2
)
is described as C
IBE,1
= (g
′
g
−ID
)
s
and C
IBE,2
=
e(g,g)
s
,M · e(g,h)
−s
. So, for the common mes-
sage M, an another identity ID
′
, and the same random
number s, (C
′
IBE,1
,C
IBE,2
) is also a valid ciphertext,
where C
′
IBE,1
= (g
′
g
−ID
′
)
s
.
5 OUR ADAPTIVE SCF-PEKS
CONSTRUCTION BASED ON
PCS-IBE
In this section, we give our adaptive SCF-PEKS con-
struction based on PCS-IBE, IND-stag-CCA secure
TBE, and sUF OTS.
5.1 Proposed Construction
Let a ciphertext space of the underlying PCS-IBE be
C
IBE
= C
IBE,1
× C
IBE,2
. We set C
IBE,1
= M
TBE
and
M
Sig
= C
IBE,2
× C
TBE
× M
IBE
.
1
Note that our partitioned requirement is different from
that of partitioned IBKEM (Abe et al., 2010).
ConstructingSecure-channelFreeSearchableEncryptionfromAnonymousIBEwithPartitionedCiphertextStructure
89

Protocol 2 (Our Adaptive SCF-PEKS Construction
w/o Hybrid Encryption).
SCF-PEKS.KeyGen
S
(1
κ
): Run (pk
S
,sk
S
) ←
TBE.KeyGen(1
κ
), and output (pk
S
,sk
S
).
SCF-PEKS.KeyGen
R
(1
κ
): Run (pk
R
,sk
R
) ←
IBE.KeyGen(1
κ
), and output (pk
R
,sk
R
).
SCF-PEKS.Trapdoor(sk
R
,ω): Run t
ω
←
IBE.Extract(sk
R
,ω), and output t
ω
.
SCF-PEKS.Enc(pk
S
, pk
R
,ω): Generate (K
s
,K
v
)
$
←
Sig.KeyGen, compute t = H
tag
(K
v
), choose R
$
←
M
IBE
, run (C
IBE,1
,C
IBE,2
) ← IBE.Enc(pk
R
,ω,R),
C
TBE
← TBE.Enc(pk
S
,t,C
IBE,1
), and
σ ← Sign(K
s
,(C
IBE,2
,C
TBE
,R)), and output
λ = (C
IBE,2
,C
TBE
,K
v
,σ).
SCF-PEKS.Test(λ,sk
S
,t
ω
): Let λ =
(C
IBE,2
,C
TBE
,K
v
,σ). Compute t = H
tag
(K
v
),
and run C
′
IBE,1
← TBE.Dec(sk
S
,t,C
TBE
) and
R
′
← IBE.Dec(t
ω
,(C
′
IBE,1
,C
IBE,2
)). Output 1
if 1=Verify(K
v
,σ,(C
IBE,2
,C
TBE
,R
′
)), and 0
otherwise.
Note that non-adaptive SCF-PEKS, where no test
query is considered in the IND-CKA-AT experiment,
can be constructed by reducing the one-time signa-
ture part and replacing the TBE part with CPA-secure
PKE as follows: Let the underlying IBE be PCS (i.e.,
C
IBE,1
∈ M
PKE
), then a ciphertext is (C
IBE,2
,C
PKE
,R),
where (C
IBE,1
,C
IBE,2
) ← IBE.Enc(pk
R
,ω,R) and
C
PKE
← PKE.Enc(pk
S
,C
IBE,1
).
In the original adaptive SCF-PEKS construc-
tion (Emura et al., 2011), the DEM part C
DEM
=
E
k
(C
IBE
) is included in the ciphertext. On the con-
trary, since the size of C
DEM
is at least the same size
of C
IBE
, by excluding the DEM part, the size of ci-
phertext of our construction is smaller than that of the
first one. Concretely, let λ
1
be a ciphertext of the orig-
inal construction, and λ
2
be a ciphertext of our con-
struction. Then, |λ
1
| ≥ |λ
2
|+|C
IBE,1
| holds. Since the
ciphertext size is bottleneck point of adaptive SCF-
PEKS constructions compared to the concrete con-
structions, we can say that our adaptive SCF-PEKS
construction is more efficient than the previous one,
although is not fully generic.
5.2 Security Analysis
In this section, we show the security proofs of our
construction. Note that the proofs of consistency and
IND-CKA-SSK are same as these of the original ones
presented in (Emura et al., 2011). So, we omit these
proofs.
Theorem 1. The SCF-PEKS scheme constructed by
our method is computationally consistent if the un-
derlying IBE scheme is IBE-IND-CPA secure.
Theorem 2. The SCF-PEKS scheme constructed by
our method is IND-CKA-SSK secure if the underlying
IBE scheme is IBE-ANO-CPA secure.
Next, we give the proof of the following theorem.
Theorem 3. The SCF-PEKS scheme constructed by
our method is adaptive-IND-CKA-ATsecure if the un-
derlying TBE scheme is IND-stag-CCA secure, the
underlying signature is one-time sUF-CMA secure,
and H
tag
is a TCR hash function.
Proof. We show that there exists an algorithm B that
breaks the IND-stag-CCA security of the underlying
TBE scheme using an adversary A who breaks the
adaptive-IND-CKA-AT security of SCF-PEKS. Let
C be the challenger of the IND-stag-CCA experi-
ment. B runs (K
∗
s
,K
∗
v
) ← Sig.KeyGen(1
κ
), and sends
t
∗
:= H
tag
(K
∗
v
) to C as the challenge tag. C runs
TBE.KeyGen(1
κ
), and gives pk to B. B sets pk as
pk
S
. A runs (pk
R
,sk
R
) ← IBE.Setup(1
κ
), and gives
pk
R
to B. Let (SCF-PEKS.Enc(pk
S
, pk
R
,ω
j
) :=
(C
IBE,2
,C
TBE
,K
v
,σ),t
ω
j
) be a T EST query, where
ω
j
∈ I D. B computes t = H
tag
(K
v
), and answers as
follows:
t 6= t
∗
: B can use the DEC oracle of the underlying
TBE scheme as follows.
1. B forwards (C
TBE
,t) to C as a DEC query of
the TBE scheme.
2. C answers C
′
IBE,1
← TBE.Dec(sk,t,C
TBE
).
• Note that if t is not the legitimate tag of C
TBE
,
then C answers ⊥. In this case, B answers 0.
3. B computes R
′
←
IBE.Dec(t
ω
j
,(C
′
IBE,1
,C
IBE,2
)).
4. If Verify(K
v
,σ,(C
IBE,2
,C
TBE
,R
′
)) = 1, then B
returns 1, and 0 otherwise.
t = t
∗
: If K
v
6= K
∗
v
, then B breaks the TCR property
of H
tag
. If K
v
= K
∗
v
(we call this a forge
1
event),
then B gives a random answer in C, and aborts.
In the Challenge phase, A sends the challenge
keywords ω
∗
0
and ω
∗
1
to B. B chooses R
∗
$
← M
IBE
,
and computes the challenge ciphertext (by using the
PCS property) as follows:
1. B computes (C
0,IBE,1
,C
0,IBE,2
) ←
IBE.Enc(pk
R
,ω
∗
0
,R
∗
) and (C
1,IBE,1
,C
1,IBE,2
) ←
IBE.Enc(pk
R
,ω
∗
1
,R
∗
) using the same random
number (i.e., C
0,IBE,2
= C
1,IBE,2
). B sets
C
∗
IBE,2
:= C
0,IBE,2
.
SECRYPT2012-InternationalConferenceonSecurityandCryptography
90

• Note that both (C
0,IBE,1
,C
∗
IBE,2
) and
(C
1,IBE,1
,C
∗
IBE,2
) are valid ciphertexts of
the underlying IBE scheme. This is the reason
we require anonymous “PCS”-IBE.
2. B sends (M
∗
0
,M
∗
1
) := (C
0,IBE,1
,C
1,IBE,1
) to C as
the challenge messages.
3. C gives C
∗
TBE
← TBE.Enc(pk
S
,t
∗
,M
∗
µ
) to B,
where µ ∈ {0,1} is the challenge bit.
4. B computes σ
∗
← Sign(K
∗
s
,(C
∗
IBE,2
,C
∗
TBE
,R
∗
)),
and sends λ
∗
= (C
∗
IBE,2
,C
∗
TBE
,K
∗
v
,σ
∗
) to A.
Then, λ
∗
is a valid ciphertext due to the PCS prop-
erty.
Again, let (SCF-PEKS.Enc(pk
S
, pk
R
,ω
j
) :=
(C
TBE
,K
v
,σ),t
ω
j
) be a T EST query, where
ω
j
∈ I D. B computes t = H
tag
(K
v
), and answers as
follows:
In the case t
ω
j
∈ {t
ω
∗
0
,t
ω
∗
1
} :
t = t
∗
: If K
v
6= K
∗
v
, then B breaks the TCR prop-
erty of H
tag
. If K
v
= K
∗
v
(we call this a forge
2
event), then B gives a random answer in C , and
aborts.
t 6= t
∗
: Then B can use the DEC oracle of the
underlying TBE scheme as follows. .
1. B forwards (C
TBE
,t) to C as a DEC query of
the TBE scheme.
2. C answers C
′
IBE
← TBE.Dec(sk,t,C
TBE
).
• Note that if t is not the legitimate tag ofC
TBE
,
then C answers ⊥. In this case, B answers 0.
3. B computes R
′
←
IBE.Dec(t
ω
j
,(C
′
IBE
,C
IBE,2
)).
4. If Verify(K
v
,σ,(C
IBE,2
,C
TBE
,R
′
)) = 1, then B
returns 1, and 0 otherwise.
In the case t
ω
j
6∈ {t
ω
∗
0
,t
ω
∗
1
} :
(C
IBE,2
,C
TBE
,K
v
,σ) = (C
∗
IBE,2
,C
∗
TBE
,K
∗
v
,σ
∗
) : B
returns 0, since (C
∗
IBE,2
,C
∗
TBE
,K
∗
v
,σ
∗
) is an
SCF-PEKS ciphertext of either ω
∗
0
or ω
∗
1
.
(C
IBE,2
,C
TBE
,K
v
,σ) 6= (C
∗
IBE,2
,C
∗
TBE
,K
∗
v
,σ
∗
) : B
runs the same simulation as in the find stage.
If B does not abort, then our simulation is perfect.
Finally, B outputs µ
′
, where µ
′
∈ {0, 1} is the output of
A. Moreover, since we can construct an algorithm B
′
which can win the sUF game with probability at least
Pr[forge] := Pr[forge
1
∨ forge
2
], Pr[forge
1
∨ forge
2
] is
negligible.
5.3 The GKBS Construction
Here, we instantiate an adaptive SCF-PEKS scheme
based on the Gentry (PCS) anonymous IBE (Gentry,
2006), the Kiltz IND-stag-CCA-secure TBE (Kiltz,
2006), and the Bellare-Shoup sUF one-time signa-
ture (Bellare and Shoup, 2007). We call it the GKBS
construction by picking up the authors’ name.
Let G and G
T
be cyclic groups of prime order p, e
be an efficiently computable bilinear map e : G ×G →
G
T
, and H
sig
: {0,1}
κ
× {0, 1}
∗
→ Z
p
be a CR hash
function, where each κ-bit key K specifies a particular
hash function H(K,·) with domain {0,1}
∗
.
Protocol 3. An adaptive SCF-PEKS scheme without
random oracles (the GKBS construction)
SCF-PEKS.KeyGen
S
(1
κ
): Choose g
1
$
← G and
x
1
,x
2
,y
1
,y
2
$
← Z
p
. Choose g
2
,z ∈ G with g
x
1
1
=
g
x
2
2
= z. Compute u
1
= g
y
1
1
and u
2
= g
y
2
2
. Output
(pk
S
,sk
S
) =
(g
1
,g
2
,z,u
1
,u
2
),(x
1
,x
2
,y
1
,y
2
)
.
SCF-PEKS.KeyGen
R
(1
κ
): Choose g,h
$
← G
and α
$
← Z
p
, compute g
′
= g
α
, and output
(pk
R
,sk
R
) =
(g
′
,h,e(g,g),e(g,h)),α
.
SCF-PEKS.Trapdoor(sk
R
,ω): For a keyword ω ∈
Z
p
, choose r
ω
$
← Z
p
, compute h
ω
= (hg
−r
ω
)
1
α−ω
,
and output t
ω
= (r
ω
,h
ω
).
SCF-PEKS.Enc(pk
S
, pk
R
,ω): Choose R
$
← G
T
,
s,r
1
,r
2
,x,y
$
← Z
p
, and K
$
← {0, 1}
κ
. Compute
X = g
x
, Y = g
y
, set K
v
= (K,X,Y), and com-
pute t = H
tag
(K
v
), C
IBE,1
= (g
′
g
−ω
)
s
, C
IBE,2
=
e(g,g)
s
,R· e(g,h)
−s
, C
TBE
=
g
r
1
1
,g
r
2
2
,(z
t
u
1
)
r
1
,
(z
t
u
2
)
r
2
,C
IBE,1
· z
r
1
+r
2
, c = H
sig
K,Y||(C
IBE,2
,
C
TBE
,R)
, and σ = c + yx mod p. Output
λ = (C
IBE,2
,C
TBE
,σ,K
v
).
SCF-PEKS.Test(λ,sk
S
,t
ω
): Parse sk
S
=
(x
1
,x
2
,y
1
,y
2
), t
ω
= (r
ω
,h
ω
), C
IBE,2
= ( f
1
, f
2
),
C
TBE
= (v
1
,v
2
,v
3
,v
4
,v
5
), and K
v
= (K,X,Y).
Compute t = H
tag
(K
v
), and check v
tx
1
+y
1
1
?
= v
3
and v
tx
2
+y
2
2
?
= v
4
. If not, then output 0. Oth-
erwise, compute C
′
IBE,1
= v
5
/(v
x
1
1
· v
x
2
2
), R
′
=
f
r
ω
1
· e(C
′
IBE,1
,h
ω
) · f
2
, and c = H
sig
K,Y||(C
IBE,2
,
C
TBE
,R
′
)
, and check g
z
?
= YX
c
. If not, then
output 0. Otherwise, output 1.
We assume the difficulty of the one-more-discrete-log
(omdl) problem (Bellare et al., 2003), the decisional
augmented bilinear Diffie-Hellman exponent (deci-
sional ABDHE) problem (Gentry, 2006), and the gap
decision linear (gap DLIN) problem (Kiltz, 2006),
and the collision resistance of H
tag
and H
sig
. Then,
ConstructingSecure-channelFreeSearchableEncryptionfromAnonymousIBEwithPartitionedCiphertextStructure
91
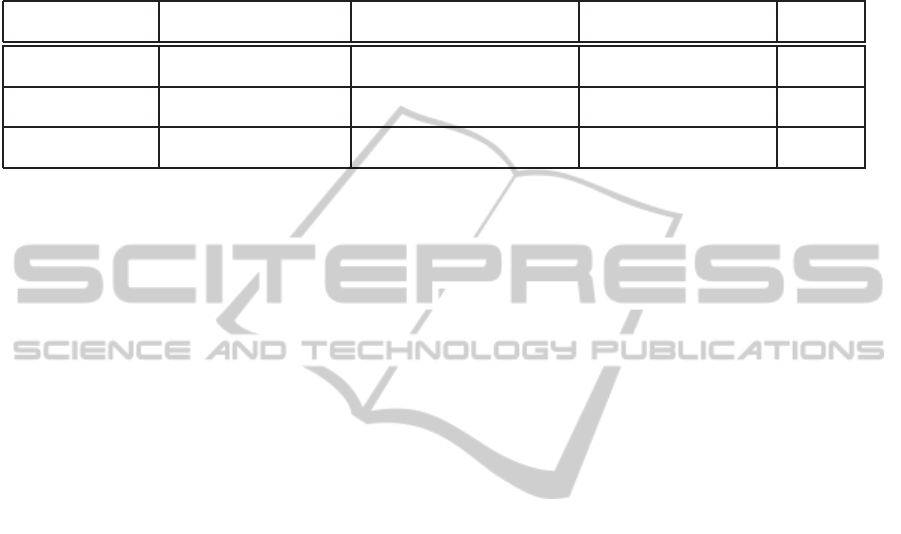
Table 1: Comparison between our constructions and the Fang et al. SCF-PEKS.
Let ME(G) and ME(G
T
) be the computational costs of multi-exponentiation in G and G
T
, respectively, BM be that of one
bilinear map computation, and |G|, |G
T
|, and
Z
p
be the bit-length of the representation of a element of G, G
T
, and Z
p
,
respectively. More precisely, we assume that the security parameter κ = 170. So, p is a 170 bits prime, |G| = 171 bits and
|G
T
| = 1020 bits, i.e., we assume that G be an elliptic curve defined over finite field F
p
and G
T
be a multiplicative group on
finite field F
×
p
k
with the embedded degree k = 6. In this case, the computational complexity over G
T
is approximately three
times higher than that of G. So, we estimate ME(G
T
) = 3ME(G), and write them in Table 1 in parentheses.
Comp. λ Comp. Test Length of λ Adaptive
Security
Fang et al. 2ME(G) + 3ME(G
T
) ME(G) + 2ME(G
T
) + 2BM 2|G| + 2|G
T
| No
(Fang et al., 2009) (11ME(G)) (7ME(G) + 2BM) (2382 bits)
GBBS 4ME(G) + 2ME(G
T
) ME(G) + ME(G
T
) + BM 3|G| + 3|G
T
| No
construction (10ME(G)) (4ME(G) + BM) (3573 bits)
GKBS 8ME(G) + 2ME(G
T
) 5ME(G) + ME(G
T
) + BM 7|G| + 2|G
T
| + |Z
p
| + κ Yes
construction (14ME(G)) (8ME(G) + BM) (3577 bits)
the above SCF-PEKS instantiation is adaptive secure
in the standard model.
5.4 Comparison
In this section, we estimate the efficiency of the
GKBS construction. Although concrete SCF-PEKS
schemes have been proposed (Baek et al., 2008; Gu
and Zhu, 2010; Gu et al., 2007; Rhee et al., 2009a),
these schemes are provedin the random oracle model.
So, we focus on SCF-PEKS schemes proposed by
Fang et al. (Fang et al., 2009) and Khader (Khader,
2007), respectively, which are secure in the stan-
dard model. Khader (Khader, 2007) shows that
PEKS and SCF-PEKS can be constructed by using
k-resilient IBE (Heng and Kurosawa, 2006) (which
is an IBE scheme, where an adversary can obtain
at most k private keys of IDs). Since k-resilient
IBE (Heng and Kurosawa, 2006) is designed by ap-
plying DDH-hard group without pairings, Khader
PEKS/SCF-PEKS also enables pairing-free construc-
tions. Unfortunately, Khader PEKS/SCF-PEKS re-
quire k-dependent large number of public keys and
high encryption costs. So, here we compare our
GKBS construction to the Fang et al. SCF-PEKS
scheme (Fang et al., 2009) in Table 1. Moreover, we
instantiate a non-adaptive SCF-PEKS scheme called
the GBBS construction which is based on the Gentry
IBE (Gentry, 2006) and linear encryption presented
by Boneh, Boyen, and Shacham (Boneh et al., 2004a).
We give the actual construction of this non-adaptive
SCF-PEKS scheme in the Appendix. The GBBS con-
struction achieves the same security level of the Fang
et al. construction.
Although in the GKBS construction the length of
the ciphertext is larger than that of the Fang et al.
construction, the computation of the Test algorithm
is faster (if BM > ME(G) which usually holds). So,
there is not much difference between our GKBS con-
struction and the Fang et al. scheme in terms of ef-
ficiency, even though our construction supports adap-
tive security.
6 CONCLUSIONS
In this paper, we show that adaptive SCF-PEKS
can be constructed without relying on hybrid en-
cryption by using PCS-IBE. Since previously-known
anonymousIBE schemes have PCS-IBE property, our
adaptive SCF-PEKS construction works as long as
previously-known anonymous IBE schemes are used.
Since we can exclude the DEM part, our construction
is efficient compared to the original one.
REFERENCES
Abe, M., Cui, Y., Imai, H., and Kiltz, E. (2010). Efficient
hybrid encryption from ID-based encryption. Des.
Codes Cryptography, 54(3):205–240.
Baek, J., Safavi-Naini, R., and Susilo, W. (2008). Public key
encryption with keyword search revisited. In ICCSA
(1), pages 1249–1259.
Bellare, M., Namprempre, C., Pointcheval, D., and Se-
manko, M. (2003). The one-more-RSA-inversion
problems and the security of chaum’s blind signature
scheme. J. Cryptology, 16(3):185–215.
Bellare, M. and Rogaway, P. (1997). Collision-resistant
hashing: Towards making UOWHFs practical. In
CRYPTO, pages 470–484.
Bellare, M. and Shoup, S. (2007). Two-tier signatures,
strongly unforgeable signatures, and Fiat-Shamir
without random oracles. In Public Key Cryptography,
pages 201–216.
Boneh, D., Boyen, X., and Shacham, H. (2004a). Short
group signatures. In CRYPTO, pages 41–55.
Boneh, D., Crescenzo, G. D., Ostrovsky, R., and Persiano,
SECRYPT2012-InternationalConferenceonSecurityandCryptography
92

G. (2004b). Public key encryption with keyword
search. In EUROCRYPT, pages 506–522.
Boneh, D. and Franklin, M. K. (2003). Identity-based en-
cryption from the weil pairing. SIAM J. Comput.,
32(3):586–615.
Boyen, X. and Waters, B. (2006). Anonymous hierarchical
identity-based encryption (without random oracles).
In CRYPTO, pages 290–307.
Byun, J. W., Rhee, H. S., Park, H.-A., and Lee, D. H.
(2006). Off-line keyword guessing attacks on recent
keyword search schemes over encrypted data. In Se-
cure Data Management, pages 75–83.
Camenisch, J., Kohlweiss, M., Rial, A., and Sheedy, C.
(2009). Blind and anonymous identity-based encryp-
tion and authorised private searches on public key en-
crypted data. In Public Key Cryptography, pages 196–
214.
Caro, A. D., Iovino, V., and Persiano, G. (2010). Fully
secure anonymous HIBE and secret-key anonymous
IBE with short ciphertexts. In Pairing, pages 347–
366.
Ducas, L. (2010). Anonymity from asymmetry: New con-
structions for anonymous HIBE. In CT-RSA, pages
148–164.
Emura, K., Miyaji, A., and Omote, K. (2011). Adaptive
secure-channel free public-key encryption with key-
word search implies timed release encryption. In ISC,
pages 102–118.
Fang, L., Susilo, W., Ge, C., and Wang, J. (2009). A se-
cure channel free public key encryption with keyword
search scheme without random oracles. In CANS,
pages 248–258.
Gentry, C. (2006). Practical identity-based encryption with-
out random oracles. In EUROCRYPT, pages 445–464.
Gu, C. and Zhu, Y. (2010). New efficient searchable en-
cryption schemes from bilinear pairings. International
Journal of Network Security, 10(1):25–31.
Gu, C., Zhu, Y., and Pan, H. (2007). Efficient public key en-
cryption with keyword search schemes from pairings.
In Inscrypt, pages 372–383.
Heng, S.-H. and Kurosawa, K. (2006). k-resilient identity-
based encryption in the standard model. IEICE Trans-
actions, 89-A(1):39–46.
Jeong, I. R., Kwon, J. O., Hong, D., and Lee, D. H. (2009).
Constructing PEKS schemes secure against keyword
guessing attacks is possible? Computer Communica-
tions, 32(2):394–396.
Khader, D. (2007). Public key encryption with keyword
search based on k-resilient IBE. In ICCSA (3), pages
1086–1095.
Kiltz, E. (2006). Chosen-ciphertext security from tag-based
encryption. In TCC, pages 581–600.
Matsuda, T., Nakai, Y., and Matsuura, K. (2010). Effi-
cient generic constructions of timed-release encryp-
tion with pre-open capability. In Pairing, pages 225–
245.
Rhee, H. S., Park, J. H., Susilo, W., and Lee, D. H. (2009a).
Improved searchable public key encryption with des-
ignated tester. In ASIACCS, pages 376–379.
Rhee, H. S., Susilo, W., and jeong Kim, H. (2009b). Secure
searchable public key encryption scheme against key-
word guessing attacks. In IEICE Electronics Express
Vol 6 (5), pages 237–243.
Seo, J. H., Kobayashi, T., Ohkubo, M., and Suzuki, K.
(2009). Anonymous hierarchical identity-based en-
cryption with constant size ciphertexts. In Public Key
Cryptography, pages 215–234.
Shoup, V. (2000). Using hash functions as a hedge against
chosen ciphertext attack. In EUROCRYPT, pages
275–288.
Yau, W.-C., Heng, S.-H., and Goi, B.-M. (2008). Off-line
keyword guessing attacks on recent public key encryp-
tion with keyword search schemes. In ATC, pages
100–105.
Appendix
Protocol 4 (A non-adaptive SCF-PEKS scheme (the
GBBS construction)).
SCF-PEKS.KeyGen
S
(1
κ
): Choose x, y ∈ Z
p
and
u,v,z ∈ G with u
x
= v
y
= z. Output (pk
S
,sk
S
) =
(u,v,z),(x,y)
.
SCF-PEKS.KeyGen
R
(1
κ
): Choose g,h
$
← G
and α
$
← Z
p
, compute g
′
= g
α
, and output
(pk
R
,sk
R
) =
(g
′
,h,e(g,g),e(g,h)),α
.
SCF-PEKS.Trapdoor(sk
R
,ω): For a keyword ω ∈
Z
p
, choose r
ω
$
← Z
p
, compute h
ω
= (hg
−r
ω
)
1
α−ω
,
and output t
ω
= (r
ω
,h
ω
).
SCF-PEKS.Enc(pk
S
, pk
R
,ω): Choose R
$
← G
T
and
s,r
1
,r
2
$
← Z
p
. Compute C
IBE,1
= (g
′
g
−ω
)
s
,
C
IBE,2
=
e(g,g)
s
,R · e(g,h)
−s
, and
C
PKE
=
u
r
1
,v
r
2
,C
IBE,1
· z
r
1
+r
2
. Output
λ = (C
IBE,2
,C
PKE
,R).
SCF-PEKS.Test(λ,sk
S
,t
ω
): Parse sk
S
= (x, y),
t
ω
= (r
ω
,h
ω
), C
IBE,2
= ( f
1
, f
2
), and
C
PKE
= (v
1
,v
2
,v
3
). ComputeC
′
IBE,1
= v
3
/(v
x
1
·v
y
2
)
and R
′
= f
r
ω
1
· e(C
′
IBE,1
,h
ω
) · f
2
. Check R
′
?
= R. If
not, then output 0. Otherwise, output 1.
The GBBS construction is secure if the decisional
ABDHE assumption and DLIN assumption hold.
Note that the GBBS construction is not adaptive se-
cure, since there is a trivial attack as follows. Let
λ
∗
= (e(g,g)
s
∗
,R
∗
· e(g,h)
−s
∗
,C
∗
PKE
,R
∗
) be the chal-
lenge ciphertext. Then, choose R
′
∈ G
T
, and com-
pute R
′
·
R
∗
· e(g,h)
−s
∗
and R
′
· R
∗
. Then λ
′
=
(e(g,g)
s
∗
,R
′
·R
∗
·e(g,h)
−s
∗
,C
∗
PKE
,R
′
·R
∗
) is a valid ci-
phertext. Therefore, A can issue a test query (λ
′
,t
ω
∗
1
),
and outputs 1 if the answer to this query is 1, and 0
otherwise. To avoid such an attack, TBE and OTS are
required in our adaptive SCF-PEKS constructions.
ConstructingSecure-channelFreeSearchableEncryptionfromAnonymousIBEwithPartitionedCiphertextStructure
93
