
An Improved Public-key Tracing Scheme with Sublinear Ciphertext Size
Chiara Valentina Schiavo and Andrea Visconti
Dipartimento di Informatica e Comunicazione, Universit´a degli Studi di Milano, via Comelico 39/41, 20135 Milano, Italy
Keywords:
Traitor Tracing Schemes, Piracy, Digital Content Distribution Systems, Pirate Decoders, Traitors.
Abstract:
To overcome the piracy problem in digital content distribution systems, a number of traitor tracing schemes
have been suggested by researchers. The goal of these schemes is to enable the tracer to identify at least
one of the traitors. In this context, Matsushita and Imai (2004) proposed a black-box tracing scheme with
sublinear header size that is able to perform tracing of self-defensive pirate decoders. Kiayias and Pehlivanoglu
(2009) proved that this scheme is vulnerable to an attack which allows an illicit decoder to recognize normal
ciphertext to tracing ones and distinguish two consecutive tracing ciphertexts. For making the scheme no
more susceptible to such attack, authors modified the encryption phase and assumed that traitors belong to the
same user group. In this paper, we present a solution that has no traitors restrictions, repairing the scheme
totally. In particular, we modified the tracing scheme proving that (a) a pirate decoder is not able to recognize
normal ciphertext to tracing ones with sufficiently high probability, and (b) the statistical distance between two
consecutive tracing operations is negligible under Decision Diffie Hellman assumption.
1 INTRODUCTION
Secure distribution of digital contents plays a key
role in many applications such as Pay-TV systems,
streaming media distributions, copyrighted material,
etc. in which only authorized users should be able
to use them. Since the main model for digital con-
tent distribution is virtual and not physical, malicious
users may decrypt and redistribute digital content,
disclose their personal key to unauthorized users, or
build a pirate decoder. Therefore, the piracy prob-
lem needs to be addressed and traitor tracing can
help us to mitigate this unwanted behavior. In a
first high-level scenario, a broadcaster, or data sup-
plier, encrypts the digital contents using a session key,
blinds such key into the header, and then sent en-
crypted contents and headers to users. Authorized
users, the subscribers, by means of a decoder, can re-
trieve the session key and subsequently decrypt the
digital contents. On the other hand, malicious sub-
scribers, the traitors, may build a pirate decoder with
their own personal keys, allowing unauthorized users,
also called pirates, to illegally decrypt the copyrighted
material. In order to identify users involved in con-
structing a pirate decoder, a number of traitor trac-
ing schemes have been suggested (Dodis and Fazio,
2002), (Kiayias and Yung, 2001), (Naor and Pinkas,
2010), (Naor and Pinkas, 1998), (Chor et al., 2000),
(Kiayias and Pehlivanoglu, 2011). All such schemes
enable a broadcaster to trace at least one traitor of the
coalition. In 1994 Chor, Fiat and Naor (1994) intro-
duced the concept of traitor tracing schemes to pre-
vent the piracy. Boneh and Franklin (1999) suggested
a deterministic public key traitor tracing scheme, ap-
plying error correcting techniques, while Kurosawa
and Desmedt (1998) described a multiple-use trace-
ability scheme which use small keys and short cipher-
text. Taking into account memory capabilities and
the ability of triggering self-defense mechanisms, Ki-
ayias and Yung (2001) classified pirate decoders into
four non-disjoint categories — i.e. resettable, history-
recording, abrupt, and available. Moreover, authors
introduced the concept of list-tracing, and presented a
traitor tracing scheme that is successful against abrupt
and resettable decoders. Dodis and Fazio (2002) de-
scribed a public key broadcast encryption scheme for
stateless receivers which reduces the public key size
and user’s storage. Unfortunately, such scheme is
not effective against pirate decoder which are able
to trigger a self-defense mechanism. Dwork, Lots-
piech and Naor (1996), suggested the notion of self-
enforcement for combating leakage of keys and deter-
ring users from revealing sensitive information. An
efficient revocation scheme based on secret sharing
enhanced with traitor tracing and self-enforcement
properties has been suggested by Naor and Pinkas
(2010). In (Matsushita and Imai, 2004), the idea
of Matsushita (2002) of the key generation method
302
Valentina Schiavo C. and Visconti A..
An Improved Public-key Tracing Scheme with Sublinear Ciphertext Size.
DOI: 10.5220/0004074003020307
In Proceedings of the International Conference on Security and Cryptography (SECRYPT-2012), pages 302-307
ISBN: 978-989-8565-24-2
Copyright
c
2012 SCITEPRESS (Science and Technology Publications, Lda.)

has been applied to (Kurosawa and Yoshida, 2002).
They suggested an efficient black-box tracing scheme
against abrupt pirate decoders, keeping the size of the
header sublinear in the number of receivers. In a sub-
sequent work Matsushita and Imai (2006) extended
their previous scheme presented in (Matsushita and
Imai, 2004) in order to reduce the header size. Ki-
ayias and Pehlivanoglu (2009) showed that the traitor
tracing scheme of Matsushita and Imai (2004) is sus-
ceptible to an attack that allows an illicit decoder to
avoid tracing and accuse an innocent user. In this pa-
per, we analyze the attack described by Kiayias and
Pehlivanoglu (2009) which (a) exploits the distance
between normal ciphertext from tracing ones and (b)
is able to distinguish two consecutive tracing cipher-
text with non-negligible probability. We improve the
black-box tracing algorithm described by Matsushita
and Imai (2004), showing that the restriction on the
geometry of traitors suggested in (Kiayias and Pehli-
vanoglu, 2009) can be omitted. In particular, we sug-
gest a way to repair the black-box tracing algorithm
(Matsushita and Imai, 2004) in order to reduce the
distance between normal and tracing ciphertext and
moreover close the gap between two consecutive trac-
ing ciphertext, making the scheme no more suscepti-
ble to the attack.
The paper is organized as follows. In Section 2
we recall the attack proposed by Kiayias and Pehli-
vanoglu (2009) on the Matsushita and Imai protocol.
In Section 3, we suggest a new solution that repairs
the scheme totally. Finally, in Section 4, a security
proof of the protocol is presented.
2 THE ATTACK
Due to space limitations, the authors do not describe
the Matsushita and Imai protocol (Matsushita and
Imai, 2004). However, we briefly introduce the main
parameters used in such protocol Let n be the number
of users and k be the maximum number of traitors in a
coalition. Let p and q be two primes such that q | p−1
and q ≥ n+ 2k− 1. G
q
is a subgroup of Z
∗
p
of order q,
g is a generator of subgroup G
q
and U = {u
1
,...,u
n
}
is the set of all user where U ⊆ Z
q
\{0}. Let ctr
j
be a counter used in the tracing phase in order to
decide if the considered user u
j
is a traitor or not. For
generating the public key and users’ private keys, the
protocol splits the set of user U in ℓ disjoint subset
U
0
,U
1
,...,U
ℓ−1
, |U
i
| = 2k with i = 0,...,ℓ − 1
and chooses a
0
,a
1
,...,a
2k−1
,b
0
,b
1
,...,b
ℓ−1
∈
R
Z
q
. The public key will be e =
(p,q,g,g
a
0
,...,g
a
2k−1
,g
b
0
,...,g
b
ℓ−1
) =
(p,q,g,y
0,0
,...,y
0,2k−1
,y
1,0
,...,y
1,l−1
). The pri-
vate key of user u ∈ U
i
, with 0 ≤ i ≤ ℓ − 1, is
(u,i, f
i
(u)), where f
i
(u) =
∑
2k−1
j=0
a
i, j
u
j
mod q with
a
i, j
= a
j
if j 6= i mod 2k or a
i, j
= b
i
otherwise. The
encrypted headers sent to users can be represented
as H = (H
0
,H
1
,...,H
ℓ−1
). Each group U
i
receives
the header H
i
= (
ˆ
h
i
,h
i,0
,...,h
i,2k−1
) where
ˆ
h
i
= g
r
i
with r
i
∈ {R
0
,R
1
} where R
0
,R
1
∈
R
Z
q
are random
numbers. It is important to note that the header H
i
can contain either the blinded session key s ∈
R
G
q
—chosen by the data supplier— or a revoking value
—computed using a random value z
i
∈
R
Z
q
—.
In (Kiayias and Pehlivanoglu, 2009), authors showed
that the public-key black-box traitor tracing scheme
in (Matsushita and Imai, 2004) is vulnerable to
self-defense mechanism. The attack (Kiayias and
Pehlivanoglu, 2009) relies on the possibility to
distinguish normal ciphertext from tracing ones,
monitoring the headers H
i
=
ˆ
h
i
,h
i,0
,...,h
i,2k−1
sent
to a coalition of k non-revoked traitors that belong to
different subgroups U
i
, i > t. When tracing is dis-
abled, each subgroup of users U
i
receives
ˆ
h
i
= g
r
i
—
recall that r
i
∈ {R
0
,R
1
} uniformly at random. On the
other hand, when tracing is enabled, these subgroups
of users receive
ˆ
h
i
= g
R
0
. Therefore, the probability
that k traitors receive the same
ˆ
h
i
is 1/2
k
when normal
ciphertext is sent, while is 1 when tracing. The statis-
tical distance between these probability distribution
converges to 1 when the number of traitors grows
(see (Kiayias and Pehlivanoglu, 2009), Theorem 1).
Monitoring header H
i
, a pirate decoder is able to
distinguish these distributions with a non-negligible
probability and trigger a self-defensive mechanism.
Moreover, the pirate decoder is able to distinguish
the gap between two consecutive tracing ciphertexts
CTrace(e, j − 1,s) and CTrace(e, j,s) when j = 1
mod 2k. In the first case, i.e. CTrace(e, j − 1,s), all
subgroups U
0
,...U
ℓ−1
will receive either r
i
= R
0
or r
i
= R
1
at random. In the second case, i.e.
CTrace(e, j, s), there exists a subgroup U
t
, which
contains u
j
, such that X ∩ U
t
6=
/
0 and X ∩ U
t
6= U
t
.
Hence, subgroup U
t
will receive r
i
= R
1
, subgroups
U
0
...U
t−1
receive r
i
= R
0
or r
i
= R
1
at random,
and finally, subgroups U
t+1
...U
ℓ−1
receive r
i
= R
0
.
Exploiting the gap between CTrace(e, j − 1,s) and
CTrace(e, j, s), a pirate decoder is able to recognize
two consecutive tracing ciphertexts and trigger
a self-defense mechanism. As consequences of
such mechanism, counter ctr
j
of traitor u
j
will be
not increased, the probability that the difference
ctr
j−1
− ctr
j
gets the maximum value is dramatically
reduced, tracing is avoided, and an innocent user
is in fact accused with a non-negligible probability
(see (Kiayias and Pehlivanoglu, 2009), Corollary
1). The main problem of the Matsushita and Imai
AnImprovedPublic-keyTracingSchemewithSublinearCiphertextSize
303

protocol is the possibility to recognize normal and
tracing operations, exploiting the statistical distance
between two probability distributions. For reducing
such distance, Kiayias and Pehlivanoglu (Kiayias and
Pehlivanoglu, 2009) introduce a random cutoff point
d that is the switch point between r
i
= R
0
to r
i
= R
1
.
In particular, if i ≤ d then they set r
i
= R
1
, otherwise
r
i
= R
0
. While encrypting, the data supplier selects
a random integer d ∈ {0,...,ℓ − 1} and generates ℓ
headers H
i
, i = 0,...,ℓ − 1, one for each subset of
users U
i
, as follows
ˆ
h
i
= g
r
i
(1)
h
i, j
=
(
y
r
i
0, j
j 6= i mod 2k
sy
r
i
1, j
j = i mod 2k
3 AN IMPROVED SCHEME
The introduction of a random cutoff point ensures
that, monitoring the headers H
i
, traitors are not able to
distinguish normal ciphertext from tracing ones. This
new approach fixes one problem, however, the gap be-
tween two consecutive tracing ciphertexts — i.e. the
gap between CTrace(e, j − 1, ·) and CTrace(e, j,·)
— still remain. In order to make traitors unable to
recognize tracing activities, in (Kiayias and Pehli-
vanoglu, 2009) authors assume that all traitors are in
the same user group U
i
and they apply the tracing al-
gorithm in parallel to U
0
...U
ℓ−1
. For mitigating all
these problems, we present a solution that repair the
scheme totally without restriction on the geometry of
traitors. In order to reduce the gap between two prob-
ability distributions, we suggest to modify the black
box tracing phase, thereby preserving the encryption
phase. In particular, when there exists a subset U
t
with 0 ≤ t ≤ ℓ − 1 such that X ∩U
t
6=
/
0, X ∩U
t
6= U
t
,
we suggest to modify the construction of the header
H
i
for i 6= t as follows
ˆ
h
i
= g
r
i
, r
i
= R
0
or R
1
h
i, j
=
y
R
0
0, j
( j 6= i mod 2k,r
i
= R
0
)
g
c
j
y
R
1
0, j
( j 6= i mod 2k,r
i
= R
1
)
sy
R
0
1,i
( j = i mod 2k,X ∩ U
i
=
/
0,r
i
= R
0
)
sg
c
j
y
R
1
1,i
( j = i mod 2k,X ∩ U
i
=
/
0,r
i
= R
1
)
g
z
i
( j = i mod 2k,X ∩ U
i
= U
i
)
This new black box tracing phase ensures that traitors
are not able to distinguish normal ciphertext from
tracing ones, and at the same time, fixes the gap be-
tween two consecutive tracing ciphertexts. Tables 1
and 2 can help us to figure out the improvements sug-
gested. In particular, first and second rows of Table
1 show the statistical gap between CTrace(e, j − 1, ·)
and CTrace(e, j,·) in Matsushita-Imai protocol while
third and fourth rows show how our solution closes
such gap, making two consecutive tracing ciphertext
indistinguishable. Table 2 shows how traitors can ex-
ploit the Matsushita-Imai distribution of r
i
in order
to distinguish tracing activities and how our approach
avoids this unwanted behavior. It is not hard to show
that in the improved scheme a set of users U
i
— i.e.
users that are not chosen to be revoked — are able to
compute the session key s. In fact, suppose there ex-
ists a subgroup U
t
with 0 ≤ t < ℓ such that X ∩U
t
6=
/
0
and X ∩ U
t
6= U
t
. Then, for i 6= t users residing in
the subset U
i
such that X ∩ U
i
=
/
0 and r
i
= R
1
are
able compute the session key s using the header H
i
as
shown in Equation 2
(
h
i,0
× h
u
i,1
× · · · × h
u
2k−1
i,2k−1
ˆ
h
f
i
(u)
i
)
1/u
i mod 2k
(2)
=
(
s
u
i mod 2k
g
∑
2k−1
j=0
c
j
u
j
g
R
1
(
∑
2k−1
j=0
a
j
u
j
+b
i
u
i
−a
i
u
i
)
g
r
i
f
i
(u)
)
1/u
i mod 2k
=
n
s
u
i mod 2k
o
1/u
i mod 2k
= s
4 PROOF OF SECURITY
The security proof of the improved tracing algorithm
relies on the Decision Diffie-Hellman (DDH) prob-
lem (Boneh, 1998). For this reason, we will introduce
(a) M
DDH
, a probabilistic polynomial time (p.p.t.)
algorithm which solve the DDH problem in G
q
and
(b) three lemmas which can help us to show that the
traitor tracing scheme we propose is able to identify
at least one traitor of a coalition with non-negligible
probability.
Lemma 4.1 (Indistinguishability of an input). The
computational complexity for k non revoked sub-
scribers to distinguish a valid input from an invalid
one is as hard as DDH in G
q
.
Proof. Let C be a set of k non-revoked subscribers
and D
dist
C
be a p.p.t. algorithm used by users in C to
distinguish a valid from an invalid one. Let M
DDH
be
a p.p.t. algorithm that is able to solve the DDH prob-
lem in G
q
. In particular, the p.p.t. algorithm M
DDH
inputs a 4-tuple (g
1
,g
2
,g
3
,g
4
) and outputs whether
such tuple is a Diffie-Hellman tuple or a Random tu-
ple. We prove that D
dist
C
⇔ M
DDH
for any C such
that X ∩ C =
/
0 and |C| = k. It is straightforward to
prove that M
DDH
⇒ D
dist
C
, therefore we prove that
D
dist
C
⇒ M
DDH
. Split the set of subscribers U into
SECRYPT2012-InternationalConferenceonSecurityandCryptography
304
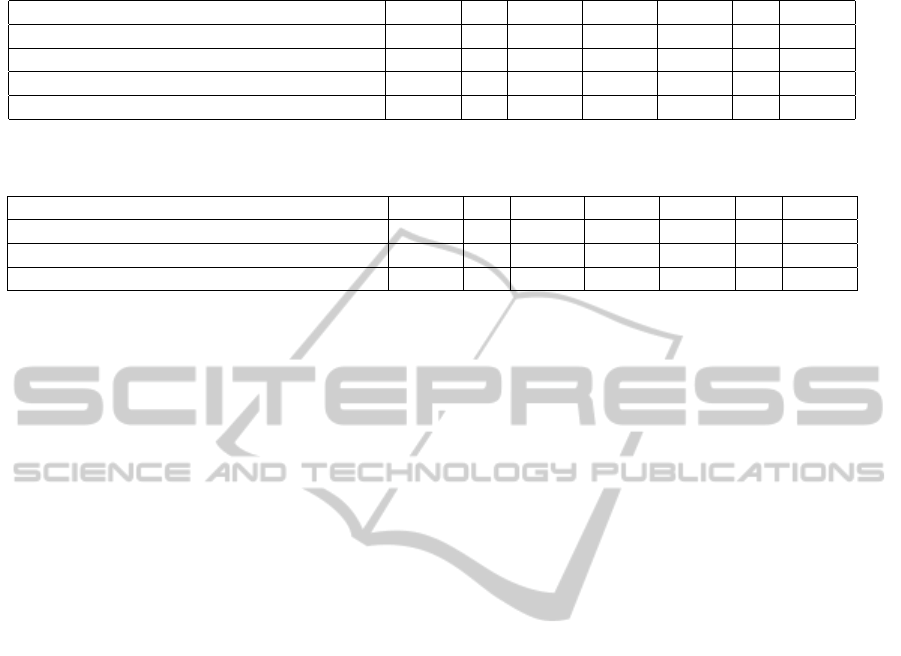
Table 1: Distribution of r
i
, case CTrace(e, j −1,·) and CTrace(e, j, ·).
U
0
... U
t−1
U
t
U
t+1
... U
ℓ−1
Matsushita-Imai scheme: CTrace(e, j − 1,·) R
0
/R
1
... R
0
/R
1
R
0
/R
1
R
0
/R
1
... R
0
/R
1
Matsushita-Imai scheme: CTrace(e, j,·) R
0
/R
1
... R
0
/R
1
R
1
R
0
... R
0
Our scheme: CTrace(e, j − 1, ·) R
0
/R
1
... R
0
/R
1
R
0
/R
1
R
0
/R
1
... R
0
/R
1
Our scheme: CTrace(e, j,·) R
0
/R
1
... R
0
/R
1
R
1
R
0
/R
1
... R
0
/R
1
Table 2: Distribution of r
i
with Normal Ciphertext (1st row) and Tracing Ciphertext (2nd, 3rd rows— case: ∃U
t
(0 ≤ t ≤ ℓ−1)
such that X ∩ U
t
6= 0 and X ∩ U
t
6= U
t
).
U
0
... U
t−1
U
t
U
t+1
... U
ℓ−1
Matsushita-Imai scheme - Normal ciphertext R
0
/R
1
... R
0
/R
1
R
0
/R
1
R
0
/R
1
... R
0
/R
1
Matsushita-Imai scheme - Tracing ciphertext R
0
/R
1
... R
0
/R
1
R
1
R
0
... R
0
Our scheme - Tracing ciphertext R
0
/R
1
... R
0
/R
1
R
1
R
0
/R
1
... R
0
/R
1
ℓ disjoint subset U
0
,...,U
ℓ−1
. Let X be the set of
subscribers, or users, chosen to be revoked such that
X ⊆ U . Choose C = {x
1
,...,x
k
} a set of k sub-
scribers such that X ∩ C =
/
0. Choose k − 1 distinct
elements x
k+1
,...,x
2k−1
∈
R
Z
q
\ C and random num-
bers β
1
,..., β
k
,λ,µ,ψ
t
,ω
t
∈
R
Z
q
, k + 1 ≤ t ≤ 2k − 1.
There exists a unique polynomial α(x) = α
0
+ α
1
x+
··· + α
2k−1
x
2k−1
mod q such that g
α
0
1
= g
λ
1
g
µ
2
and
(α(x
1
),.. .,α(x
2k−1
))
T
= (β
1
,.. ., β
2k−1
)
T
= (α
0
,.. .,α
0
)
T
+V(α
1
,.. .,α
2k−1
) mod q
(α
1
,.. .,α
2k−1
)
T
= V
−1
(β
1
− α
0
,.. .,β
2k−1
− α
0
)
T
mod q
where g
β
t
1
= g
ψ
t
1
g
ω
t
2
, k + 1 ≤ t ≤ 2k − 1, and V is the
Vandermonde matrix. Let (v
m,1
,...,v
m,2k−1
) be the
mth row of V
−1
matrix, then compute α
m
, 1 ≤ m ≤
2k− 1, as follows:
α
m
= v
m,1
β
1
+ ··· + v
m,2k−1
β
2k−1
− α
0
(v
m,1
+ ··· + v
m,2k−1
) mod q
hence g
α
m
1
= g
v
m,1
β
1
+···+v
m,2k−1
β
2k−1
1
/(g
λ
1
g
µ
2
)
v
m,1
+···+v
m,2k−1
.
For computing users’ personal key (x
j
,i
j
,d
j
), we (a)
choose a user x
j
∈ U
i
j
where 1 ≤ j ≤ k and i
j
∈
{0,...,ℓ − 1} , (b) define a set I = {i
j
|1 ≤ j ≤ k, x
j
∈
U
i
j
}, (c) randomly choose λ
i
,µ
i
∈
R
Z
q
for each i,
0 ≤ i ≤ ℓ − 1, and δ
i
j
∈
R
Z
q
for all elements i
j
∈ I .
For each i
j
∈ I , there exists an element γ
i
j
∈
R
Z
q
such
that δ
i
j
= b
i
j
+ γ
i
j
− α
i
j
mod 2k
and g
b
i
1
= g
λ
i
1
g
µ
i
2
, there-
fore we can compute last parameter of the key d
j
as
follows: d
j
= α(x
j
) + δ
i
j
x
i
j
mod 2k
j
. Since the user’s
private key is (u, i, f
i
(u)), we impose that d
j
= f
i
(u),
computing coefficients a
0
,...,a
2k−1
as follows. Con-
sider the set {0,...,2k− 1} \ {i
j
mod 2k|i
j
∈ I }. It is
possible to select k elements from this set which can
be represented as θ
1
,..., θ
k
. Compute g
α
′
θ
1
1
,...,g
α
′
θ
k
1
such that g
∑
τ∈{θ
1
,...,θ
k
}α
′
τ
x
τ
j
1
= g
γ
i
j
x
i
j
mod 2k
j
1
. In order to
compute the public key e, it is necessary to calculate
g
a
m
1
with 0 ≤ m ≤ 2k − 1 as follows,
g
a
m
1
=
(
g
α
m
1
m 6∈ {θ
1
,.. .,θ
k
}
g
α
m
1
g
α
′
m
1
m ∈ {θ
1
,.. .,θ
k
}
and the public key e will be e =
(g
1
,g
a
0
1
,.. .,g
a
2k−1
1
,g
b
0
1
,.. .,g
b
ℓ−1
1
). Let s ∈
R
G
q
be
the session key and r ∈
R
Z
q
be a random number. For
each i, 0 ≤ i ≤ ℓ − 1, if U
i
∩X =
/
0 or U
i
∩X = U
i
set
B
i
= 0 or B
i
= 1, otherwise, set B
i
= 1. It is possible
to identify eight compact headers H. Four are related
to case ∃U
l
such that U
l
∩ X 6=
/
0 and U
l
∩ X 6= U
l
,
0 ≤ l ≤ ℓ − 1, while the remaining when such U
l
does not exist. In particular, if U
l
exists then compact
header H will be computed as follow,
1. if B
i
= 0 for i < l, and B
i
= 0 for i > l,
*
g
r
1
,g
a
0
r
1
,.. .,g
a
2k−1
r
1
g
3
,g
a
0
3
,.. .,g
a
2k−1
3
sg
b
0
r
1
,.. .,sg
b
l−1
r
1
,sg
λ
l
3
g
µ
l
4
,sg
b
l+1
r
1
,.. .,sg
b
ℓ−1
r
1
+
2. if B
i
= 1 for i < l, and B
i
= 0 for i > l,
*
g
r
1
,g
a
0
r
1
,.. .,g
a
2k−1
r
1
g
3
,g
a
0
3
,.. .,g
a
2k−1
3
sg
λ
0
3
g
µ
0
4
,.. .,sg
λ
l−1
3
g
µ
l−1
4
,sg
λ
l
3
g
µ
l
4
,sg
b
l+1
r
1
,.. .,sg
b
ℓ−1
r
1
+
3. if B
i
= 0 for i < l, and B
i
= 1 for i > l,
*
g
r
1
,g
a
0
r
1
,.. .,g
a
2k−1
r
1
g
3
,g
a
0
3
,.. .,g
a
2k−1
3
sg
b
0
r
1
,.. .,sg
b
l−1
r
1
,sg
λ
l
3
g
µ
l
4
,sg
λ
l+1
3
g
µ
l+1
4
,.. .,sg
λ
ℓ−1
3
g
µ
ℓ−1
4
+
4. if B
i
= 1 for i < l, and B
i
= 1 for i > l,
*
g
3
,g
a
0
3
,.. .,g
a
2k−1
3
sg
λ
0
3
g
µ
0
4
,.. .,sg
λ
ℓ−1
3
g
µ
ℓ−1
4
+
If such U
l
does not exist, then U
i
∩ X = U
i
, or U
i
∩
X =
/
0, 1 ≤ i ≤ ℓ − 1. Hence, compact header H will
be computed as follow,
AnImprovedPublic-keyTracingSchemewithSublinearCiphertextSize
305

5. if B
i
= 0 for U
i
∩X = U
i
and B
i
= 1 for U
i
∩X =
/
0, then the header H is computed as in case 3
6. if B
i
= 1 for U
i
∩X = U
i
and B
i
= 1 for U
i
∩X =
/
0, then the header H is computed as in case 4
7. if B
i
= 0 for U
i
∩X = U
i
and B
i
= 0 for U
i
∩X =
/
0,
*
g
r
1
,g
a
0
r
1
,.. .,g
a
2k−1
r
1
sg
b
0
r
1
,.. .,sg
b
ℓ−1
r
1
+
8. if B
i
= 1 for U
i
∩X = U
i
and B
i
= 0 for U
i
∩X =
/
0,
*
g
r
1
,g
a
0
r
1
,.. .,g
a
2k−1
r
1
g
3
,g
a
0
3
,.. .,g
a
2k−1
3
sg
λ
0
3
g
µ
0
4
,.. .,sg
λ
l−1
3
g
µ
l−1
4
,sg
b
l
r
1
,sg
b
l+1
r
1
,.. .,sg
b
ℓ−1
r
1
+
Knowing that
g
a
j
3
=
(
g
α
j
3
j 6∈ {θ
1
,.. .,θ
k
}
g
α
j
3
g
α
′
j
3
j ∈ {θ
1
,.. .,θ
k
}
and g
∑
τ∈{θ
1
,...,θ
k
}α
′
τ
x
τ
z
3
=
g
δ
i
z
3
g
α
i
z mod 2k
3
/g
λ
i
z
3
g
u
i
z
4
x
i
z
mod 2k
z
with 1 ≤ z ≤ k, it is not hard to note that the
compact headers described above behaves as nor-
mal encryption headers when (g
1
,g
2
,g
3
,g
4
)-tuple
is a Diffie-Hellman tuple, and as tracing header
when (g
1
,g
2
,g
3
,g
4
)-tuple is a random tuple in which
traitors in C are not revoked. Public key e, private
keys (x
1
,i
1
,d
1
),... ,(x
k
,i
k
,d
k
) and compact header H
input D
dist
C
. The p.p.t. algorithm decides weather
header H is a valid input or an invalidone, and outputs
“Diffie-Hellman tuple” or “Random tuple”. Since
D
dist
C
is able to distinguish a valid input from an in-
valid one, C chosen arbitrarily such that X ∩ C =
/
0
and |C| = k, we constructed M
DDH
using D
dist
C
, hence
M
DDH
can solve the DDH problem. We can conclude
that D
dist
C
⇒ M
DDH
for any C arbitrarily chosen.
Lemma 4.2 (Secrecy of a Session Key in an Invalid
Input). The computational complexity to compute the
session key, for k subscribers revoked that received an
invalid input, is as hard as DDH in G
q
.
Proof. The proof of Lemma 4.2 follows step by step
the proof provided in (Matsushita and Imai, 2004,
p. 269,270). However it is necessary to replace the
following condition: - if X ∩ U
i
=
/
0, then compute H
as:
ˆ
h
i
= g
r
3
h
i, j
=
(
g
a
j
r
3
( j 6= i mod 2k)
s(g
λ
i
3
g
µ
i
4
)
r
( j = i mod 2k)
with this: - if X ∩ U
i
=
/
0, set B
i
= 0 or 1 and compute
H
i
as follows:
ˆ
h
i
=
(
g
r
3
(B
i
= 0)
g
x
1
g
y
3
(B
i
= 1)
h
i, j
=
g
a
j
r
3
( j 6= i mod 2k,B
i
= 0)
(g
x
1
g
y
3
)
a
j
( j 6= i mod 2k,B
i
= 1)
s(g
λ
i
3
g
µ
i
4
)
r
( j = i mod 2k,B
i
= 0)
s(g
λ
i
1
g
µ
i
2
)
x
(g
λ
i
3
g
µ
i
4
)
y
( j = i mod 2k,B
i
= 1)
Lemma 4.3 (Indistinguishability of a Suspect).
Given a subscriber u
j
, the computational complexity
for a coalition of k subscribers to distinguish an in-
valid input in which the user u
j
is not revoked — i.e.
X = {u
1
,...,u
j−1
} — from another one in which u
j
is
revoked — i.e. X = {u
1
,...,u
j
} — is as hard as DDH
in G
q
.
Proof. Let C be the set of k colluders. Let A
dist
C
be
a p.p.t. algorithm used by the coalition C to distin-
guish two invalid input, one in which a given user
is revoked and the other one in which the user is
not revoked. We prove that A
dist
C
⇔ M
DDH
for any
coalition C such that |C | = k. Firstly, it is clear that
M
DDH
⇒ A
dist
C
for any coalition C. Secondly, we
prove that A
dist
C
⇒ M
DDH
for any C by construct-
ing M
DDH
using A
dist
C
as a subroutine. The algorithm
M
DDH
takes in input a challenge tuple (g
1
,g
2
,g
3
,g
4
)
and outputs “Diffie-Hellman tuple” or “Random tu-
ple”. The construction of the algorithm is as follows.
Split the set of subscribers U into ℓ disjoint subset
U
0
,...,U
ℓ−1
. Let X a set of revoked subscribers.
Choose k users which form the set C and choose a
user u
j
which has to be a subscriber who does not
belong to the set of colluders, i.e., u
j
∈
R
U \ C . We
suppose that user u
j
∈ U
t
. We also suppose that for
i = 0, . . .,t − 1 sets U
i
are such that U
i
∩ X = U
i
and
for i = t+1,...,ℓ −1 sets U
i
are such that U
i
∩X =
/
0.
According to its relation with the set of revoked users,
the set U
t
can be such that:
1. U
t
∩ X 6= U
t
and U
t
∩ X 6=
/
0. This case has to be
considered both when u
j
∈ X and when u
j
6∈ X .
2. U
t
∩X =
/
0 when u
j
6∈ X and U
t
∩X = {u
j
} when
u
j
∈ X .
3. U
t
∩X = U
t
\{u
j
} when u
j
6∈ X and U
t
∩X = U
t
when u
j
∈ X .
Now, choose C = {x
1
,...,x
k
} a set of k sub-
scribers. Consider the user x
j
∈ U
i
j
and com-
pute its personal key (x
j
,i
j
,d
j
) and public key e =
SECRYPT2012-InternationalConferenceonSecurityandCryptography
306

(g
1
,g
a
0
1
,...,g
a
2k−1
1
,g
b
0
1
,...,g
ℓ−1
1
) using the same pro-
cedure of Lemma 4.1. Construct the header H =
(H
0
,...,H
ℓ−1
) executing the following procedure for
0 ≤ i ≤ ℓ − 1. The single header H
i
for the group U
i
will be H
i
= (
ˆ
h
i
,h
i,0
,...,h
i,2k−1
) where the single el-
ements in H
i
are computed as follows:
• if X ∩ U
i
=
/
0, set B
i
= 0 or 1:
ˆ
h
i
=
(
g
r
3
(B
i
= 0)
g
x
1
g
y
3
(B
i
= 1)
h
i, j
=
g
a
j
r
3
( j 6= i mod 2k,B
i
= 0)
(g
x
1
g
y
3
)
a
j
( j 6= i mod 2k,B
i
= 1)
s(g
λ
i
3
g
µ
i
4
)
r
( j = i mod 2k,B
i
= 0)
sg
b
i
y
3
(g
λ
i
1
g
µ
i
2
)
x
( j = i mod 2k,B
i
= 1)
• if X ∩ U
i
= U
i
, set B
i
= 0 or 1 and compute H
i
as
follows, selecting each time a random z
i
∈
R
Z
q
.
ˆ
h
i
=
(
g
r
3
(B
i
= 0)
g
x
1
g
y
3
(B
i
= 1)
h
i, j
=
(
h
′
i, j
( j 6= i mod 2k)
g
z
i
1
( j = i mod 2k)
where h
′
i, j
is computed in two different ways de-
pending on the existence of a subset U
t
with 0 ≤
t ≤ ℓ − 1 such that X ∩ U
t
6=
/
0 and X ∩ U
t
6= U
t
.
If such a set exists then
h
′
i, j
=
(
g
a
j
r
3
(B
i
= 0)
g
c
j
1
(g
x
1
g
y
3
)
a
j
(B
i
= 1)
Otherwise:
h
′
i, j
=
(
g
a
j
r
3
(B
i
= 0)
(g
x
1
g
y
3
)
a
j
(B
i
= 1)
• if X ∩U
i
6=
/
0 and X ∩ U
i
6= U
i
, the header H
t
will
be constructed as follows. First, construct a poly-
nomialC(x) =
∑
2k−1
j=0
c
j
x
j
such that for u ∈ U with
u 6= u
j
, C(u) ≡ 0 mod q if and only if it holds that
u ∈ (U
t
\ X ). We also suppose that for the user u
j
it holds that C(u
j
) ≡ 0 mod q. Then:
ˆ
h
i
= g
x
1
g
y
3
h
i, j
=
(
g
c
j
1
(g
x
1
g
y
3
)
a
j
( j 6= i mod 2k)
sg
c
j
1
g
b
i
y
3
(g
λ
i
1
g
µ
i
2
)
x
( j = i mod 2k)
Note that if (g
1
,g
2
,g
3
,g
4
) is a Diffie-Hellman tuple,
the subscriber u
j
is not revoked in the header H, oth-
erwise, if (g
1
,g
2
,g
3
,g
4
) is a Random tuple then the
subscriber u
j
is revoked. Run the algorithm A
dist
C
, by
giving in input to it u,H,e,(x
1
,i
1
,d
1
),... ,(x
k
,i
k
,d
k
).
This algorithm is able to distinguish invalid input in
which the subscriber u
j
is not revoked from an in-
valid input in which u
j
is revoked. Since we have
constructed M
DDH
using A
dist
C
as a subroutine, we
can conclude that M
DDH
can solve the DDH prob-
lem.
Theorem 4.4. Given the traitor tracing scheme de-
scribed in Section 3 and a pirate decoder constructed
by a coalition of k traitors, a tracer is able to identify
at least one of the traitors with non-negligible proba-
bility.
REFERENCES
Boneh, D. (1998). The Decision Diffie-Hellman Problem.
In ANTS, volume 1423 of LNCS, pages 48–63.
Boneh, D. and Franklin, M. K. (1999). An efficient public
key traitor tracing scheme. In CRYPTO, volume 1666
of LNCS, pages 338–353.
Chor, B., Fiat, A., and Naor, M. (1994). Tracing traitors. In
CRYPTO, volume 839 of LNCS, pages 257–270.
Chor, B., Fiat, A., Naor, M., and Pinkas, B. (2000). Tracing
traitors. In IEEE Transactions on Information Theory,
volume 46, pages 893–910.
Dodis, Y. and Fazio, N. (2002). Public key broadcast en-
cryption for stateless receivers. In DRM Workshop,
volume 2696 of LNCS, pages 61–80.
Dwork, C., Lotspiech, J. B., and Naor, M. (1996). Digital
signets: Self-enforcing protection of digital informa-
tion. In STOC, pages 489–498.
Kiayias, A. and Pehlivanoglu, S. (2009). On the security
of a public-key traitor tracing scheme with sublinear
ciphertext size. In DRM Workshop, pages 1–10. ACM.
Kiayias, A. and Pehlivanoglu, S. (2011). Attacking traitor
tracing schemes using history recording and abrupt
decoders. In ISC, volume 7001 of LNCS, pages 17–31.
Kiayias, A. and Yung, M. (2001). On crafty pirates and foxy
tracers. In DRM Workshop, volume 2320 of LCNS.
Kurosawa, K. and Desmedt, Y. (1998). Optimum traitor
tracing and asymmetric schemes. In EUROCRYPT,
pages 145–157.
Kurosawa, K. and Yoshida, T. (2002). Linear code implies
public-key traitor tracing. In Public Key Cryptogra-
phy, volume 2274 of LNCS, pages 172–187.
Matsushita, T. (2002). A flexibly revocable key-distribution
scheme for efficient black-box tracing. In ICICS, vol-
ume 2513 of LNCS, pages 197–208.
Matsushita, T. and Imai, H. (2004). A public-key black-box
traitor tracing scheme with sublinear ciphertext size
against self-defensive pirates. In ASIACRYPT,volume
3329 of LNCS, pages 260–275.
Matsushita, T. and Imai, H. (2006). Hierarchical key as-
signment for black-box tracing with efficient cipher-
text size. In ICICS, volume 4307 of LNCS, pages 92–
111.
Naor, M. and Pinkas, B. (1998). Threshold traitor tracing.
In CRYPTO, volume 1462 of LNCS, pages 502–517.
Naor, M. and Pinkas, B. (2010). Efficient trace and revoke
schemes. Int. J. Inf. Sec., 9(6):411–424.
AnImprovedPublic-keyTracingSchemewithSublinearCiphertextSize
307
