An Application of a Group Signature Scheme with Backward
Unlinkability to Biometric Identity Management
Julien Bringer
1
, Herv´e Chabanne
1,2
and Alain Patey
1,2
1
Morpho, Issy-Les-Moulineaux, France
2
T´el´ecom ParisTech, Identity and Security Alliance (The Morpho and T´el´ecom ParisTech Research Center), Paris, France
Keywords:
Group Signatures, Identity Management, Derivation, Cascade Revocation, Biometrics, Anonymity.
Abstract:
We introduce a new identity management process in a setting where users’ identities are credentials for anony-
mous authentications. Considering identity domains organized in a tree structure, where applying for a new
identity requires to previously own the parent identity, we enable a cascade revocation process that takes into
account this structure while ensuring anonymity for non-revoked users, in particular, towards the providers of
other identity domains. Our construction is based on the group signature scheme of (Bringer and Patey, 2012).
1 INTRODUCTION
In this paper we consider a scenario where users have
access to a kind of federation of identity management
systems with different identity providers that have
some dependencies between them: To each identity
provider corresponds an identity domain and the set
I of these domains is structured as a tree. When one
wants to apply for a new identity in an identity domain
I
l
, one has to own a valid identity for the parent do-
main I
k
. These dependencies also imply that it should
be possible to automatically revoke across different
domains. To this aim, the new identity is derived from
the previous ones in order to maintain a link with the
identities above. Contrary to what is done in central-
ized federated identity management, one important is-
sue is then to ensure the privacy of this link. We call
this property Cross-Unlinkability
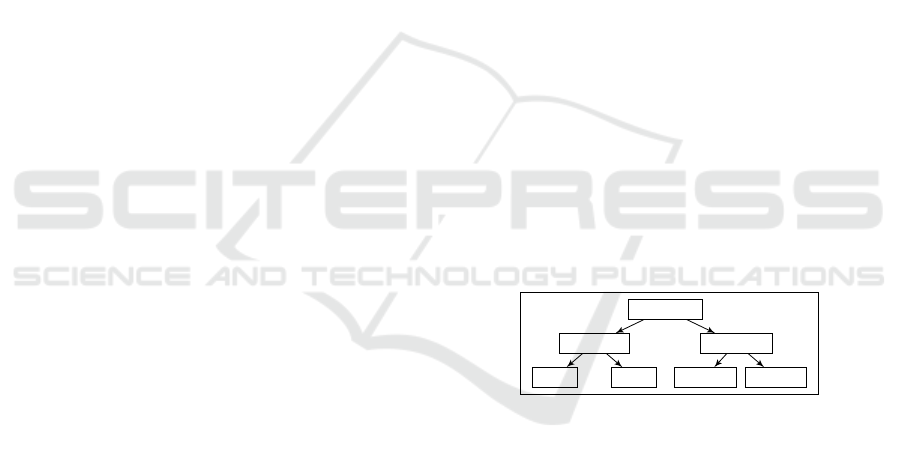
Let us give an example of application of our pro-
posal. Consider the identity domain (sub-)tree de-
scribed in Figure 1. We assume that a government
sets up an identity management system, used for in-
stance to access services. In this example, applying
for an identity stating that you own a car insurance re-
quires to previously own an identity in the domain of
users with driver’s licenses. We also wish that, when
a user uses his student identity, anonymity of this user
is guaranteed against the providers of all other do-
mains, including the managers of the parent domain
(National Identity), the children domains (Colleges)
or the sibling domains (Driver’s license).
We use as elementary component of our system a
National Identity
Student Identity
College 2College 1
Driver’s License
Car Insurance HGV License
Figure 1: An example of an identity domain tree I.
biometric anonymousauthentication scheme (Bringer
et al., 2008) (BCPZ) based on Verifier-Local Revo-
cation (VLR) group signatures (see Figure 2). This
protocol enables members of a group, managed by a
Group Manager GM, to authenticate, using an elec-
tronic device, to a service provider while proving
nothing more than their belonging to the group. The
use of biometrics guarantees that the legitimate user
uses the device and this, combined to the use of a
group signature scheme, leads to an anonymous re-
mote authentication. We can see the group considered
in such a scheme as an identity domain I
l
, where the
identity provider IP is the GM. The keys that are is-
sued by IP are actually credentials that are associated
to the issued identity. In the following, these creden-
tials will be assimilated to the identities. The users
that obtained an identity from IP can prove its validity
to service providers that rely on this identity domain.
We recall that group signatures enable authorized
users to sign anonymously on behalf of a group. We
only consider the case of VLR group signatures. The
VLR property (Boneh and Shacham, 2004) guaran-
tees that only the public parameters and a revocation
list RL are required to check a signature. Concretely,
when a user is revoked, a revocation token derived
421
Bringer J., Chabanne H. and Patey A..
An Application of a Group Signature Scheme with Backward Unlinkability to Biometric Identity Management.
DOI: 10.5220/0004123904210425
In Proceedings of the International Conference on Security and Cryptography (SECRYPT-2012), pages 421-425
ISBN: 978-989-8565-24-2
Copyright
c
2012 SCITEPRESS (Science and Technology Publications, Lda.)

from his signing key is added to RL. It is used by ver-
ifiers to prevent revoked users from further signing.
To reach our goal of Cross-Unlinkability, we use
the group signature introduced in (Bringer and Patey,
2012) (which patches and extends (Chen and Li,
2010)) that satisfies Backward Unlinkability. This
property enables users to sign at different time peri-
ods using the same keys, while maintaining unlinka-
bility between signatures issued at different periods,
even if the user is revoked at one of these periods. In
our proposal, we no more consider these periods as
time periods but as children of a given identity in the
identity domain tree. Thus, authentications in two dif-
ferent domains are impossible to link if the user is not
revoked from both. Moreover, the cascade revocation
process that we describe does not threaten the security
properties that we guarantee.
2 THE CL AND BP GROUP
SIGNATURES
In this section, we describe the model of group sig-
natures presented in (Bringer and Patey, 2012). We
instantiate this model using two schemes introduced
in (Bringer and Patey, 2012): a patched version of the
(Chen and Li, 2010) scheme, denoted by CL, and an
extension of this patched version with Backward Un-
linkability (BU), denoted by BP. Notice that both can
be used with the same parameters.
2.1 Components
There are three types of entities: a Group Manager
GM, a set of members and a set of verifiers. A BP
or a CL Group Signature Scheme consists of the fol-
lowing algorithms. (Moreover, in the BP scheme, be-
cause of BU, all algorithms but KeyGen depend on
the current time period j and one revocation list RL
j
per time period has to be used (see also Remark 1)).
KeyGen. The group manager outputs the group pub-
lic parameters gpk. He also chooses a secret key msk
and its public counterpart mpk. gpk and mpk are pub-
lished. GM also publishes an empty revocation list
RL.
Join. This algorithm is an interactive protocol be-
tween GM and a member M
i
. M
i
gets a secret key
sk
i
= (x
i
, A
i
, f
i
) where f
i
is chosen by M
i
, x
i
by GM
and A
i
is computed by GM using msk, x
i
and some
information about f
i
. GM only gets x
i
and A
i
, he also
derives a revocation token rt
i
from x
i
.
Revoke. GM runs this algorithm to prevent a member
M
i
from further making valid signatures. It outputs an
updated revocation list RL.
Sign. This algorithm, run by a member M
i
, takes as
input a message m, M
i
’s key sk
i
and a message m. It
outputs a signature σ.
Verify. This algorithm, run by a verifier takes as input
a message m, its signature σ and the Revocation List
RL. It checks if the message has been signed by an un-
revoked group member, without revealing the signer’s
identity. The possible outputs are valid and invalid.
Open. This algorithm is run by GM. It takes a sig-
nature σ on a message m as input, together with all
revocation tokens of the group members. It reveals
the identity of the signer.
2.2 Security Properties
We describe the security properties fulfilled by the
group signature schemes. Both BP and CL schemes
satisfy Correctness, Selfless-Anonymity, Traceability
and Exculpability. The BP scheme moreover satisfies
Backward Unlinkability.
(a) Correctness. Every check of a well-formed sig-
nature, made by an unrevoked user, returns valid.
(b) Selfless-Anonymity. A member can say if he pro-
duced a particular signature. If it was not him, he has
no information about the user who produced it.
(c) Traceability. No attacker (or group of attackers)
is able to forge a signature that can not be traced to
one of the corrupted users which participated in its
forgery.
(d) Exculpability. Nobody, even the Group Manager,
is able to produce another user’s signature.
(e) Backward Unlinkabilty. (encompasses Selfless-
Anonymity) The valid signatures remain anonymous,
even after the signer’s revocation. Revoked users can
come back after their revocation into the group and
use their previous keys without any loss of anonymity.
Remark 1. (Backward Unlinkability) To enable BU,
the BP scheme divides time into periods. Instead of a
unique revocation list RL, there is one revocation list
RL
j
for each period j. Similarly, each member M
i
has
a revocation token rt
ij
for each period j instead of a
unique rt
i
. Usually, for every time period j, a random
token h
j
is chosen. The period revocation token is
then obtained as follows: rt
ij
= h
rt
i
j
. Thus, two tokens
rt
ij
and rt
ij
′
of the same user at different time periods
are unlinkable, which guarantees BU.
Remark 2 (BCPZ Anonymous Authentication). We
describe in Figure 2 how to adapt the BCPZ anony-
mous authentication scheme using the CL scheme. We
refer the reader to (Bringer et al., 2008) for further
details. Notice that in our adaptation, we use the
SECRYPT2012-InternationalConferenceonSecurityandCryptography
422

Human user H
Sensor S
Service Provider P
b
′
∼
?
b, f
i
= H(b)
σ =Sign
CL
(m, sk
i
, gpk, mpk)
Verify
CL
(m, σ, gpk, mpk, RL)
challenge message m
b
′
(Scanning)
b, x
i
, A
i
(from card)
σ
Figure 2: The BCPZ authentication scheme.
property of Exculpability enabled by the CL scheme
and we do not give any biometric data to the GM.
3 OUR PROPOSAL
3.1 The Model
We assume that identity domains are organized as a
tree I with a root I
0
. When one wants to acquire a
new identity from a domain I
l
, one has to prove that
one owns a valid identity for its parent domain I
k
in I.
Each identity domain I
l
has an identity provider IP
l
and we will denote by k ≺ l the fact that the identity
domain I
k
is the parent of the identity domain I
l
.
For each identity that they own, the authorized
users possess the necessary keys to authenticate
anonymously following the principle of the BCPZ
scheme. The corresponding IP is in fact the group
manager for the underlying group signature scheme.
The functionalities of our protocol are the following.
KeyGen. This is run by the IP’s. IP
0
first returns the
public parameters gpk for all the domains. Then each
IP
l
creates a secret/public key pair (msk
l
, mpk
l
) and
publishes mpk
l
.
Enrolment. For a domain I
l
, this algorithm is jointly
run by the identity provider IP
l
and a user M
i
. The
input for the user is a fresh acquisition b
i
of a biomet-
ric trait B and for IP
l
is his secret key msk
l
. It returns
a new secret key sk
l
i
= (x
l
i
, A
l
i
, f
l
i
) for M
i
for the iden-
tity domain I
l
. f
l
i
is only knownfrom M
i
and the other
parts x
l
i
and A
l
i
are known from both. x
l
i
is in particular
used as a revocation token rt
l
i
for M
i
for this domain.
Derivation. For a domain I
l
, this algorithm is jointly
run by a user M
i
requiring to get a new identity for
the domain I
l
and the identity provider IP
l
of I
l
. The
input for M
i
is his secret key for the parent domain I
k
of I
l
in I and the input for IP
l
is his secret key msk
l
.
It returns the result of the enrolment of M
i
to I
l
if M
i
successfully proves to IP
l
that he owns a valid (and
non revoked) identity for I
k
.
Authentication. For a domain I
l
, this is jointly run
by a user M
i
and a service provider requiring a valid
identity from I
l
. The input of M
i
is his secret sk
l
i
and
a fresh biometric acquisition b
′
i
. The service provider
only needs gpk and mpk
l
. It returns a boolean denot-
ing the acceptance or the reject of the authentication.
Revocation. This recursive algorithm is run by the
identity provider IP
l
of I
l
who wants to revoke a mem-
ber M
i
of I
l
. It takes as input the revocation token rt
l
i
of the user M
i
and the revocation list RL
l
.
• Local Revocation: It returns an updated RL
l
where the revocation token of M
i
for I
l
is added.
• Downwards Revocation (compulsory): The
newly published revocation token rt
l
i
is sent to the
IP’s of the domains that are children of I
l
, who then
run the Revocation algorithm.
• Upwards Revocation (optional): IP
l
sends an in-
formation rt
k≺l
i
to IP
k
, where I
k
is the parent of I
l
,
who can then decide to revoke (in that case we will
say that the upwards revocation has been accepted) or
not the user, using rt
k≺l
i
to retrieve the user’s identity
for I
k
.
Remark 3 (Revocation). This corresponds to the cas-
cade revocation capability. The goal of the down-
wards revocation process it to ensure that once a user
is revoked of a given domain I
l
then this user is also
revoked from all identity domains that are derived
from I
l
, i.e. the children of I
l
in I, the children of these
children, and so on. The optional upwards revocation
is there to give the possibility for a domain to signal
to the parent domain that a user has been revoked. If
this is not executed, IP
k
does not learn anything on
the identity of the user revoked by IP
l
.
3.2 Security
The main security property that we require from our
scheme is that an authentication in a given domain re-
mains anonymous even for the providers of the other
identity domains, for instance of the sibling domains
in I. We insist on the fact that, in case of revocation,
if IP
l
does not inform the provider IP
k
of the parent
identity I
k
of I
l
that a given user is revoked from I
l
,
then IP
k
is not able to know about the identity of this
user. We call this property Cross-Unlinkability (CU).
CU is an adaptation of Selfless-Anonymity. Addition-
ally, we directly adapt the security properties a), c)
and d) of VLR group signature to our setting of iden-
tity management.
3.3 The Construction
We instantiate our algorithms using the CL and BP
group signatures, as follows.
AnApplicationofaGroupSignatureSchemewithBackwardUnlinkabilitytoBiometricIdentityManagement
423

KeyGen. IP
0
runs the KeyGen
BP
algorithm of the BP
group signature to generate the public parameters gpk
of the scheme. Then each IP
l
, including IP
0
, creates
a key pair (mpk
l
, msk
l
) compatible with gpk. The
msk
l
’s are kept secret by the IP’s. gpk and all the
msk
l
’s are published. The IP’s also agree on a set of
period tokens h
k≺l
, that are used for the Derivation
from I
k
to I
l
. We need, for each internal node I
k
in
the tree I, to set one period “k ≺ l” per child I
l
of I
k
.
Enrolment. We assume that M
i
has fulfilled all the
conditions to acquire an identity from the domain I
l
.
The enrolment phase is then the same as in the BCPZ
scheme. M
i
is acquired a biometric trait b
l
i
. This trait
is hashed to form a first part f
l
i
= Hash(b
l
i
) of his new
secret key. M
i
and IP
l
then jointly run the Join
CL
al-
gorithm. If I
l
6= I
0
, x
l
i
is not chosen randomly by the
IP, as in the Join
CL
algorithm, but it uses the output
of the Derivation algorithm as the choice for x
l
i
, to
enable the revocation process. At the end of this algo-
rithm, M
i
stores x
l
i
, A
l
i
and his biometric reference b
l
i
.
IP
l
knows x
l
i
and A
l
i
and derives the revocation token
for M
i
for domain I
l
: rt
l
i
= x
l
i
.
Authentication. The authentication for a member M
i
to a service provider P requiring to belong to I
l
is
merely a BCPZ authentication using the group signa-
ture parameters for the domain I
l
. Concretely, when
a user wants to prove to P that he owns an identity, he
selects his associated device, connects it to a trusted
sensor that communicates with P. The sensor checks
using biometricsthat the legitimate person is using the
card, reads the keys on the card and signs a challenge
message sent by P.
Derivation. We now explain how to derive identi-
ties. Let I
k
be the parent domain of I
l
in I and let
us assume that a user M
i
owns an identity for I
k
and
wants to acquire an identity for the domain I
l
. M
i
has
to engage a specific authentication process with the
identity provider IP
l
.
First, the user authenticates to IP
l
, viewed as a ser-
vice provider for I
k
to prove validity of his identity in
I
k
However, he uses the BP signature at period k ≺ l
instead of the CL scheme. M
i
also sends the revo-
cation token rt
k≺l
i
corresponding to the k ≺ l period.
IP
l
checks the validity of the signature using Ver-
ify
CL
and checks that the token is the good one using
Verify
BP
with a revocation list set as {rt
k≺l
i
} (which
should fail during the Revocation Check). If all tests
succeed, IP
l
computes x
l
i
= Hash(msk
l
||rt
k≺l
i
), which
is then used as input for the Enrolment algorithm.
This derivation process is described in Figure 3.
Remark 4 (Explanations on the Derivation Process).
The BU property of the BP scheme prevents from link-
ing revocation tokens of the same user at different
User M
i
Identity Provider for I
l
h
k≺l
, challenge message m
Derivation Phase
h
k≺l
, m
σ
k
=Sign
BP
(gpk, mpk
k
, sk
k
i
, m, H
l
)
σ
k
, rt
k≺l
i
=h
rt
k
i
k≺l
Verify
CL
(gpk, mpk
k
, m, σ
k
, RL
k
)
Verify
BP
(gpk, mpk
k
, m, σ
k
, k ≺ l, RL = {rt
k≺l
i
})
Derive x
l
i
= rt
l
i
=Hash(msk
l
||rt
k≺l
i
)
Fresh acquisition b
l
i
f
l
i
=Hash(b
l
i
)
Enrolment Phase
Enrolment to I
l
using f
l
i
and x
l
i
Store b
l
i
, x
l
i
and A
l
i
Store (rt
k≺l
i
, rt
l
i
) on DB
I
l
Figure 3: The derivation process.
time periods. Here, periods do not represent time, but
the different children identities of a given identity do-
main. Thus, the identities of one user for different do-
mains will not be linkable. Furthermore, the copy of
rt
k≺l
i
kept by IP
l
is used in the revocation process de-
scribed below. We consequently achieve our property
of Cross-Unlinkability while maintaining a cascade
revocation process.
Notice also that this derivation process at the
same time takes into account the parent identities and
preserves consistency with the original biometric ref-
erences, since the new acquisitions have to match with
the previous ones.
Revocation. Let us assume that the identity provider
IP
l
of the identity domain I
l
wants to revoke a user
M
i
. He proceeds as follows.
Local Revocation: IP
l
takes as input the revocation list
RL
l
and the revocation token rt
l
i
of M
i
, then adds rt
l
i
to RL
l
: RL
l
= RL
l
∪ {rt
l
i
}. The new RL
l
is published.
Downwards Revocation: This direction is automatic.
All providers for the identity domains (I
m
)
m∈M
that
are children of I
l
learn the revocation token rt
l
i
. They
all compute h
rt
l
i
l≺m
and look in their databases DB
I
m
’s if
this token is present. If it is, they start the Revocation
algorithm for the associated user, using the revocation
token rt
m
i
associated to rt
l≺m
i
in DB
I
m
.
Upwards Revocation: We recall that this part of the
Revocation algorithm is optional. IP
l
can report to
the provider of the parent domain I
k
the user M
i
if he
thinks that IP
k
should revoke him too. He sends to IP
k
the item rt
k≺l
i
associated to M
i
in DB
I
l
. If IP
k
wishes
to discover to whom it corresponds, he computes h
rt
k
i
′
j
for all the M
i
′
’s that belong to I
k
. When h
rt
k
i
′
j
= rt
k≺l
i
,
the associated user M
i
′
is the user M
i
that was revoked
by IP
l
. IP
k
can then, if he desires, revoke M
i
′
from I
k
.
SECRYPT2012-InternationalConferenceonSecurityandCryptography
424

ACKNOWLEDGEMENTS
This work is partially funded under the European FP7
FIDELITY project (SEC-2011-284862).
REFERENCES
Boneh, D. and Shacham, H. (2004). Group signatures with
verifier-local revocation. In ACM Conference on Com-
puter and Communications Security, pages 168–177.
Bringer, J., Chabanne, H., Pointcheval, D., and Zimmer, S.
(2008). An application of the Boneh and Shacham
group signature scheme to biometric authentication.
In IWSEC, pages 219–230.
Bringer, J. and Patey, A. (2012). VLR group signatures:
How to achieve both backward unlinkability and effi-
cient revocation checks. In SECRYPT.
Chen, L. and Li, J. (2010). VLR group signatures with in-
disputable exculpability and efficient revocation. In
SocialCom/PASSAT, pages 727–734.
AnApplicationofaGroupSignatureSchemewithBackwardUnlinkabilitytoBiometricIdentityManagement
425
